Let's learn about Ransomware via these 66 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
1. Avoid Becoming a Victim to These Cybersecurity Threats in 2022
 With increased hacking activity focused on vulnerable businesses and at-home employees, cybersecurity has become a major business priority.
With increased hacking activity focused on vulnerable businesses and at-home employees, cybersecurity has become a major business priority.
2. How Getting Hacked Led me to a Job in CyberSecurity
 ReThink Cybersecurity - Cyber Wellness the New Healthly Livign Trend
ReThink Cybersecurity - Cyber Wellness the New Healthly Livign Trend
3. Cybersecurity in Times of International Conflicts: How to Protect Your Organization
 On June 28, the Baton Rouge General Medical Center in Louisiana lost its electronic medical record and patient system to a cyberattack
On June 28, the Baton Rouge General Medical Center in Louisiana lost its electronic medical record and patient system to a cyberattack
4. How Does Ransomware-as-a-Service Work?
 Ransomware is on the rise — and now anyone can buy the malware. Here's how ransomware became a service and how that service works.
Ransomware is on the rise — and now anyone can buy the malware. Here's how ransomware became a service and how that service works.
5. Ransomware: Early Signs, Protection, and Staying Ahead
 In this article, you will learn about the signs of ransomware and how you can identify them.
In this article, you will learn about the signs of ransomware and how you can identify them.
6. Endpoint Security Series: Top 5 Crucial Layers of Protection
 To help security professionals assess their options, we’ve listed five guiding principles for choosing optimal endpoint security solution in our previous blog.
To help security professionals assess their options, we’ve listed five guiding principles for choosing optimal endpoint security solution in our previous blog.
7. Beware That Ransomware Groups Can Operate as 'Legit' Businesses
 Ransomware has become one of the greatest cyber threats facing organizations in 2022.
Ransomware has become one of the greatest cyber threats facing organizations in 2022.
8. Ransomware-as-a-Service: SaaS' Evil Twin
 This article will educate you about RaaS groups and protective measures against ransomware attacks.
This article will educate you about RaaS groups and protective measures against ransomware attacks.
9. A Ring of Failure
 A wise person learns from the mistakes of others. So let’s accumulate some wisdom and go over the biggest failures in the history of software.
A wise person learns from the mistakes of others. So let’s accumulate some wisdom and go over the biggest failures in the history of software.
10. Linux Ransomware, Cryptojacking, and Cobalt Strike Are Targeting Multi-Cloud Infrastructure
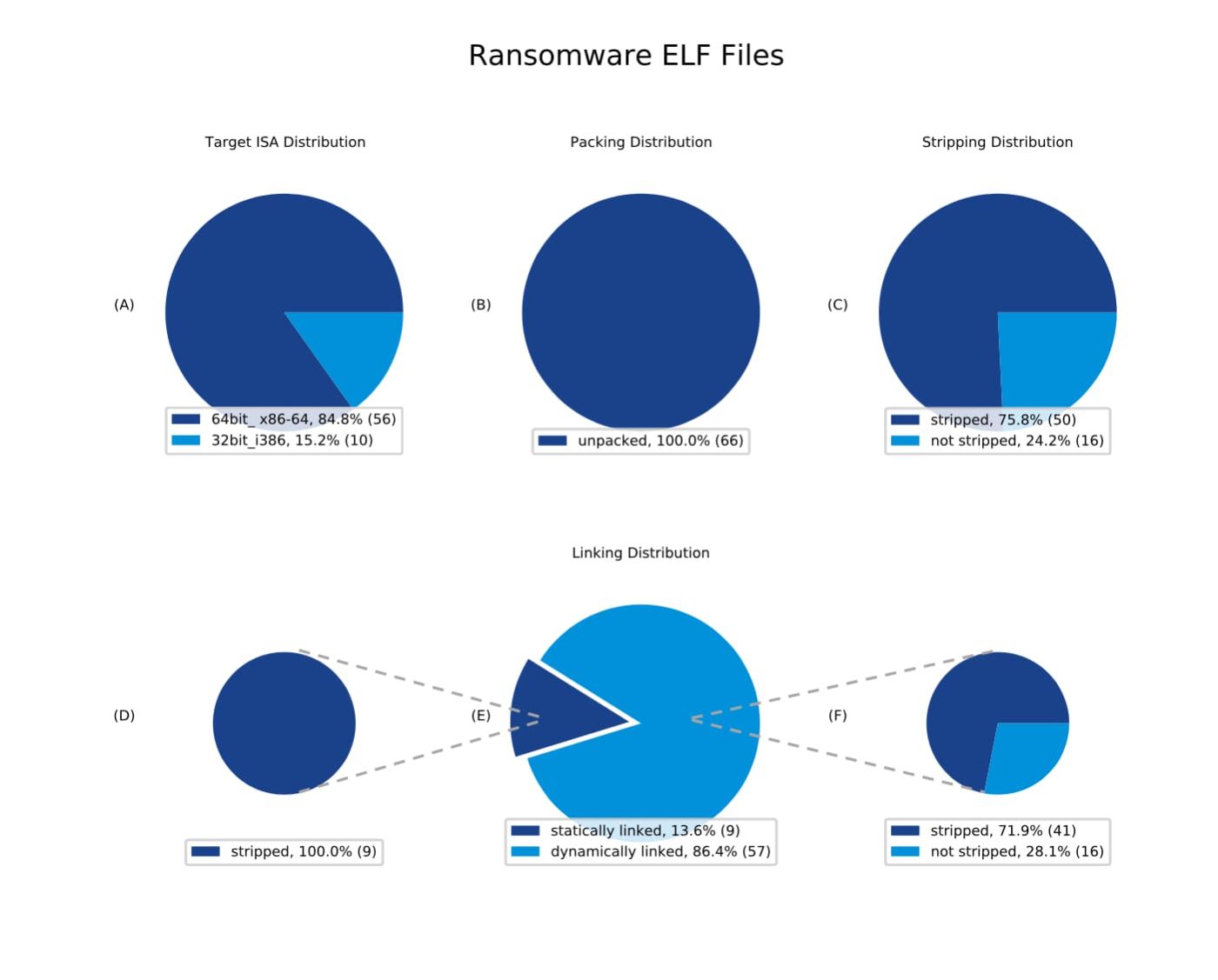 Linux systems are being increasingly targeted by ransomware, cryptojacking, and other malicious attacks, according to a recent report.
Linux systems are being increasingly targeted by ransomware, cryptojacking, and other malicious attacks, according to a recent report.
11. Using Immutable Storage to Protect Data Against Ransomware
 The number of ransomware attacks reaches new heights, making businesses believe that there’s no effective weapon in this fight. But there is. Immutable storage
The number of ransomware attacks reaches new heights, making businesses believe that there’s no effective weapon in this fight. But there is. Immutable storage
12. A Data-Backed Look At the Post-Coronavirus Cybersecurity Landscape
 Not so long ago, the buzz in cybersecurity circles was all about COVID-19 and how malicious actors were exploiting the panic via a wave of targeted phishing attempts. Well, much to everyone's relief, the trend didn't last long. Some of that is due to security firms getting the word out so quickly, and some of it is due to the general public becoming more aware of potential threats and behaving with more care as they encounter suspicious situations.
Not so long ago, the buzz in cybersecurity circles was all about COVID-19 and how malicious actors were exploiting the panic via a wave of targeted phishing attempts. Well, much to everyone's relief, the trend didn't last long. Some of that is due to security firms getting the word out so quickly, and some of it is due to the general public becoming more aware of potential threats and behaving with more care as they encounter suspicious situations.
13. The Beginners Guide To Ransomware Prevention in 2021
 Ransomware is a sort of malware that cybercriminals use to extort cash. It holds information to ransom with encryption or by keeping users out of their devices.
Ransomware is a sort of malware that cybercriminals use to extort cash. It holds information to ransom with encryption or by keeping users out of their devices.
14. The Looming Threat of Ransomware [Infographic]
 A look at how to prevent ransomware before it happens.
A look at how to prevent ransomware before it happens.
15. What Organizations Should Learn From the Colonial Pipeline Breach
 The Colonial Pipeline Breach has shown us that ransomware attacks are not going away anytime soon and having been increasing due to the COVID-19 pandemic.
The Colonial Pipeline Breach has shown us that ransomware attacks are not going away anytime soon and having been increasing due to the COVID-19 pandemic.
16. Understanding BadUSB Devices
 How an innocent-looking USB device can deliver ransomware to a user's computer through an open USB port.
How an innocent-looking USB device can deliver ransomware to a user's computer through an open USB port.
17. Cybersecurity Lessons from the Netflix Series La Casa De Papel
 Can a TV show teach us how to take more care of our cybersecurity?
Can a TV show teach us how to take more care of our cybersecurity?
18. Ransomware Guide: An Explanation and How to Defend Against It
 Ransomware is a common and potentially devastating form of cyberattack on organizations of every kind.
Ransomware is a common and potentially devastating form of cyberattack on organizations of every kind.
19. New-Age Threats to Your Online Privacy and Cybersecurity
 Cybersecurity seems like a never-ending journey: you patch one flaw, another appears. You download one top-notch security tool, and soon realize that it is no longer enough.
Cybersecurity seems like a never-ending journey: you patch one flaw, another appears. You download one top-notch security tool, and soon realize that it is no longer enough.
20. Logistics Security: 5 ways to protect the Supply Chain Against Cybersecurity Attacks
 This article explains how to protect the supply chain sector against cybersecurity attacks.
This article explains how to protect the supply chain sector against cybersecurity attacks.
21. Automated Offline Backups Can Save the World
 Ransomware is worse than malware: Systems and data are all locked up, and backups are all encrypted, too.
Ransomware is worse than malware: Systems and data are all locked up, and backups are all encrypted, too.
22. How to Secure Office 365 & Windows from Ransomware Attacks
 It’s no secret that we’re living in uncertain times. Many countries are under partial or full lockdown for the past few weeks, making work from home the new norm for the foreseeable future, at least.
It’s no secret that we’re living in uncertain times. Many countries are under partial or full lockdown for the past few weeks, making work from home the new norm for the foreseeable future, at least.
23. Let's Talk About Ransomware-as-a-Service
 Ransomware-as-a-service is a subscription-based model of ransomware developed to enable novice hackers to execute sophisticated ransomware attacks.
Ransomware-as-a-service is a subscription-based model of ransomware developed to enable novice hackers to execute sophisticated ransomware attacks.
24. Why Bitcoin is Not an "Ideal" Ransomware Currency
 Bitcoin ain't a ticket to “cyber gangsta’s paradise.”
Bitcoin ain't a ticket to “cyber gangsta’s paradise.”
25. How Hacks Happen: Views on the July 4th Ransomware Attack
 Over the Fourth of July weekend, a ransomware attack by a Russian hacker group REvil left hundreds of companies' information susceptible.
Over the Fourth of July weekend, a ransomware attack by a Russian hacker group REvil left hundreds of companies' information susceptible.
26. Ransomware Attacks: How to Protect Enterprises and Critical Infrastructure
 With Ransomware attacks increasing rapidly, it ahs become more important for companies to ensure that their network infrastructure is protected from attacks.
With Ransomware attacks increasing rapidly, it ahs become more important for companies to ensure that their network infrastructure is protected from attacks.
27. What is Causing the Worrisome Increase in Ransomware
 Ransomware has become a much more common crime online in recent days. But why is this the case and what can people even do about this massive problem?
Ransomware has become a much more common crime online in recent days. But why is this the case and what can people even do about this massive problem?
28. Ransomware Is Getting "User Friendly" To Victims
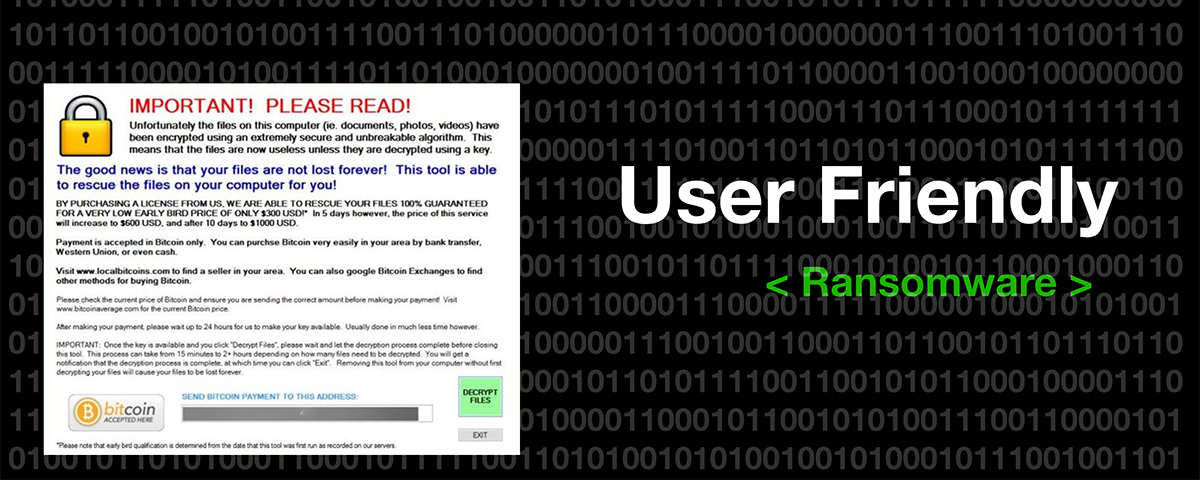 Cybersecurity risk regarding ransomware and how it is evolving with cryptocurrency.
Cybersecurity risk regarding ransomware and how it is evolving with cryptocurrency.
29. Impacts of Double Extortion Ransomware Attack on Enterprises and Mitigation
 Double Extortion Ransomware Attack is nefarious and seems unstoppable. However, it can be mitigated with some effective techniques.
Double Extortion Ransomware Attack is nefarious and seems unstoppable. However, it can be mitigated with some effective techniques.
30. Is It Worth Paying For Stolen Data On The Dark Web?
 Data breaches are increasingly common these days. It seems like every other week there is a new headline about a major company experiencing a threat.
Data breaches are increasingly common these days. It seems like every other week there is a new headline about a major company experiencing a threat.
31. Attacked by Ransomware? Here’s Why You Shouldn’t Pay Up
 If you have fallen victim to ransomware and there is no data backup, you aren’t very likely to get your files back unless you pay. In most cases, the only choice you can make is to pay with your money or with your data – that’s it. Obviously, neither option is suitable.
If you have fallen victim to ransomware and there is no data backup, you aren’t very likely to get your files back unless you pay. In most cases, the only choice you can make is to pay with your money or with your data – that’s it. Obviously, neither option is suitable.
32. How To Find Out If A Hacker Has Attacked You
 Computer crimes are all those online attacks carried out by a hacker whose purpose is to breach a computer system in order to gain financial gain in some way
Computer crimes are all those online attacks carried out by a hacker whose purpose is to breach a computer system in order to gain financial gain in some way
33. Be Resilient not Vulnerable to Ransomware Emails

34. Why Cybersecurity Firms Should Stop Bragging
 Antivirus company Bitdefender said it was “happy to announce” a startling breakthrough.
Antivirus company Bitdefender said it was “happy to announce” a startling breakthrough.
35. How Does Ransomware Work? A Step-by-Step Breakdown

36. Are Ransomware and Cryptocurrency Inextricably Linked?
 Ransomware hackers often ask for payment via cryptocurrency, but ransomware and crypto may not be as inextricably linked as they look.
Ransomware hackers often ask for payment via cryptocurrency, but ransomware and crypto may not be as inextricably linked as they look.
37. CIOs Need to Prioritize Digital Transformation and Cybersecurity in Their 2022 Budgets
 Digital transformation cannot be jettisoned for cybersecurity, a delicate balance must be reached by CIOs in their 2022 budgets for the two to co-exist.
Digital transformation cannot be jettisoned for cybersecurity, a delicate balance must be reached by CIOs in their 2022 budgets for the two to co-exist.
38. How Can Enterprises Prevent and Deal With Ransomware Attacks
 Check Point Software’s Incident Response Team's guide for enterprises on how to prevent and deal with ransomware attacks.
Check Point Software’s Incident Response Team's guide for enterprises on how to prevent and deal with ransomware attacks.
39. How To Prevent Trending Ransomware Attacks
 What is ransomware? Why is it so dangerous? Who can be affected? How to get rid of it…or maybe to prevent it?
What is ransomware? Why is it so dangerous? Who can be affected? How to get rid of it…or maybe to prevent it?
40. Should You Pay the Ransom if You're a Victim of a Ransomware Attack?
 Paying the ransom might not be the solution to your nightmare. Even if a company pays, there is no guarantee that attackers will return the data.
Paying the ransom might not be the solution to your nightmare. Even if a company pays, there is no guarantee that attackers will return the data.
41. Regardless of Their Size, Any Business Can Be a Victim of a Ransomware Attack
 A timeline of a medium sized businesses ransomware attack along with tips to prevent an attack for yourself.
A timeline of a medium sized businesses ransomware attack along with tips to prevent an attack for yourself.
42. 7 Deadly Digital Sins: Understanding the Main Types of Malware
 Malware is everywhere these days. You've probably been a victim at some stage, and you may well not even know it. From all-too-visible ransomware attacks to botnets and adware, it's a complex picture, and new variants are emerging all the time.
Malware is everywhere these days. You've probably been a victim at some stage, and you may well not even know it. From all-too-visible ransomware attacks to botnets and adware, it's a complex picture, and new variants are emerging all the time.
43. How To Prevent Ransomware Attacks: A Threat That’s Real
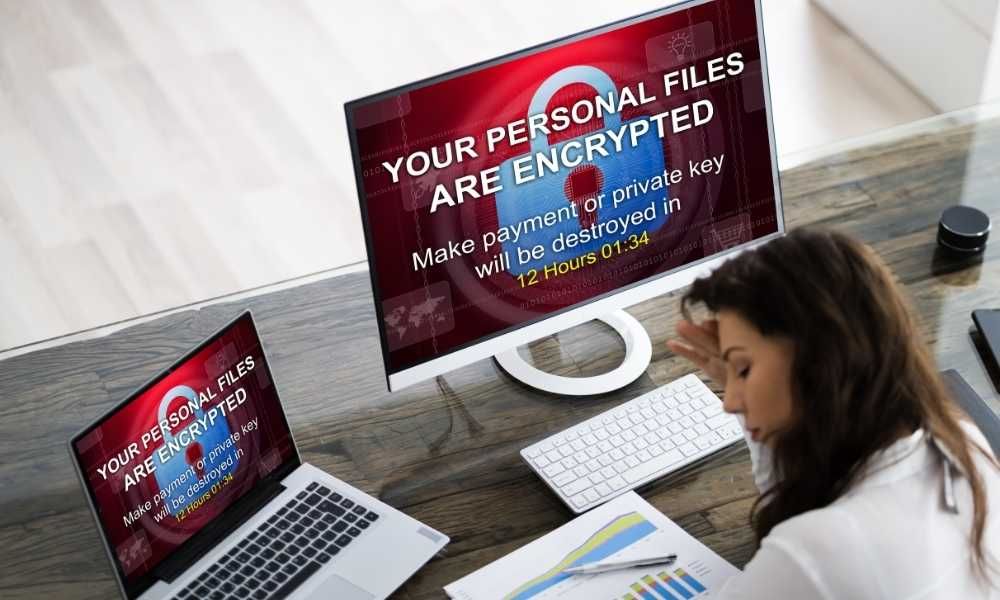 Ransomware works by encrypting the user’s data, making it unreadable. If a user wants their data back, a ransom must be paid. Keep reading to learn more
Ransomware works by encrypting the user’s data, making it unreadable. If a user wants their data back, a ransom must be paid. Keep reading to learn more
44. Netwalker Ransomware: Everything You Need to Know to Stay Safe
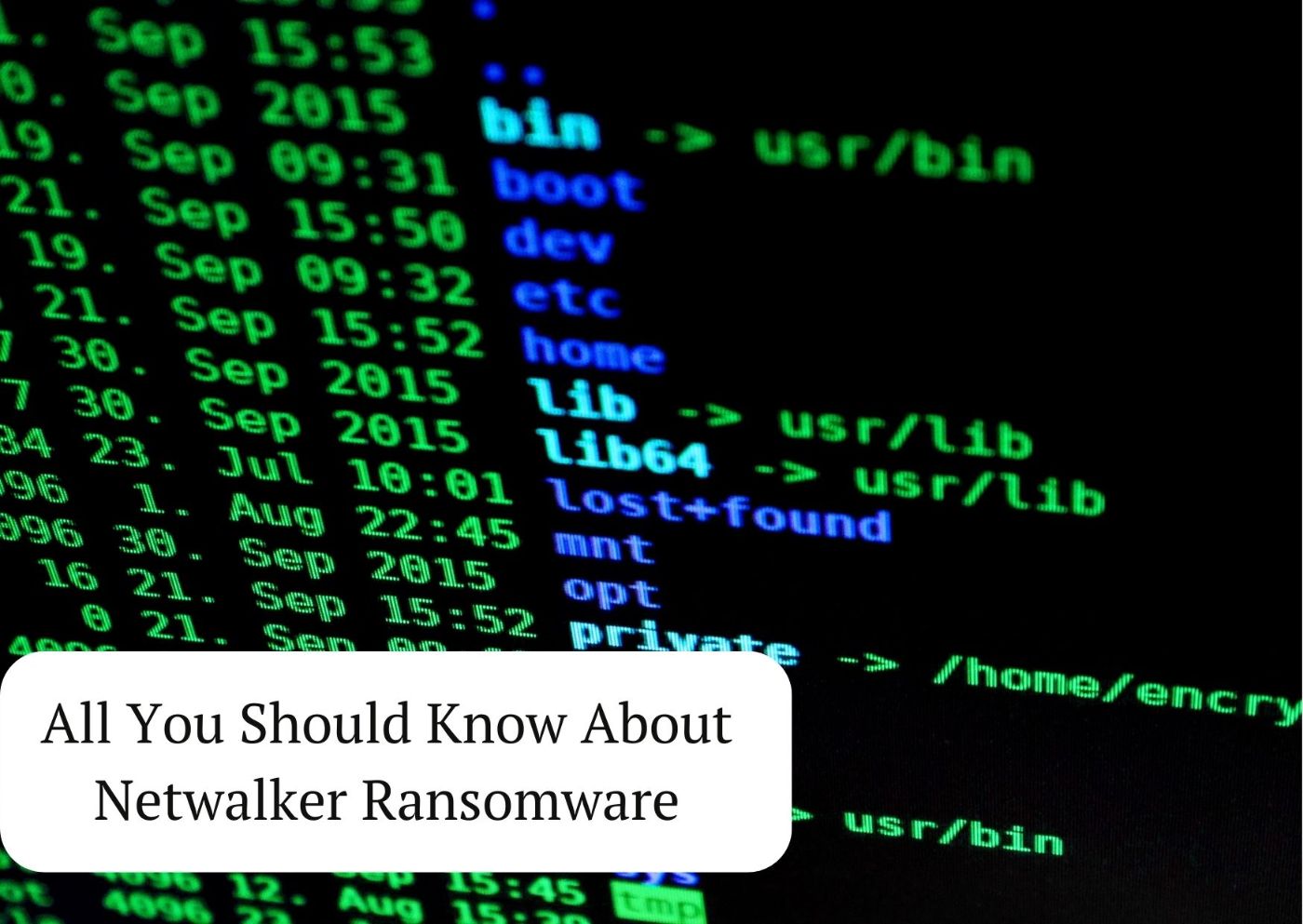 Ransomware analysis and knowing how Netwalker works are essential for understanding vulnerable points and protecting yourself against Netwalker attacks
Ransomware analysis and knowing how Netwalker works are essential for understanding vulnerable points and protecting yourself against Netwalker attacks
45. How to Secure Your Applications
 The CTO of a neo-brokerage FinTech shares tips on how to secure your app -from the front end to the backend. He also recommends tools to use in SDD lifecycle.
The CTO of a neo-brokerage FinTech shares tips on how to secure your app -from the front end to the backend. He also recommends tools to use in SDD lifecycle.
46. Cryptocurrencies Promote Secure Decentralization or Support Cyber Piracy: the Truth
 The odd symbiosis between hacking syndicates and cryptocurrency, and how they're powering each other's rise.
The odd symbiosis between hacking syndicates and cryptocurrency, and how they're powering each other's rise.
47. Cerber Ransomware Explained: How to Protect, Detect, and Recover
 This blog post covers Cerber ransomware, infection methods, the working principle, how to remove Cerber ransomware, and how to protect against Cerber.
This blog post covers Cerber ransomware, infection methods, the working principle, how to remove Cerber ransomware, and how to protect against Cerber.
48. Will Failing to Pay Ransoms Stop Ransomware Attacks?
 Compared to the ransomware of recent times, it has shifted toward high-value targets from well-funded threat actors. Let's find out more!
Compared to the ransomware of recent times, it has shifted toward high-value targets from well-funded threat actors. Let's find out more!
49. Tips for Safeguarding Your WordPress Website
 All websites are prone to cyber-attacks from hackers attempting to control website resources and users' data.
All websites are prone to cyber-attacks from hackers attempting to control website resources and users' data.
50. Is Configuring Access Control Effective When Defending Your Business Against Supercharged Ransom?
 As types of ransomware get more advanced and devastating, get to know more about some of the best ways to defend your business.
As types of ransomware get more advanced and devastating, get to know more about some of the best ways to defend your business.
51. Your Computers Are Not Really Yours - Part 1: BitLocker Is Kinda Ransomware
 if you’re using your personal computer - or if you’re a part of a small office that just bought and shipped the computer to you, you’re in the dock too…
if you’re using your personal computer - or if you’re a part of a small office that just bought and shipped the computer to you, you’re in the dock too…
52. Phishing: Top Threat to Our Online Security
 Phishing is a cheap technique for hackers to steal the victim’s data. Now I am telling you because it really happened to me. It took my most online privacy.
Phishing is a cheap technique for hackers to steal the victim’s data. Now I am telling you because it really happened to me. It took my most online privacy.
53. Things to Consider When Facing a Ransomware Scenario
 Getting your data locked by ransomware is a difficult situation to deal with. This is how you get out of the situation quickly and with minimal trouble.
Getting your data locked by ransomware is a difficult situation to deal with. This is how you get out of the situation quickly and with minimal trouble.
54. Ryuk Ransomware: What it is and How it's Harming the Healthcare Sector
 Organizations in the healthcare sector have been valiantly fighting to save lives since the COVID-19 pandemic began, but they’ve also had to shift focus to another type of viral attack. Since March, healthcare organizations in the U.S. have been hit with multiple cyberattacks from threat actors who want to take advantage of any vulnerability in their systems. The latest to join the ranks of healthcare network threats is Ryuk, a ransomware that has victimized several medical organizations since September.
Organizations in the healthcare sector have been valiantly fighting to save lives since the COVID-19 pandemic began, but they’ve also had to shift focus to another type of viral attack. Since March, healthcare organizations in the U.S. have been hit with multiple cyberattacks from threat actors who want to take advantage of any vulnerability in their systems. The latest to join the ranks of healthcare network threats is Ryuk, a ransomware that has victimized several medical organizations since September.
55. Australia's Ransomware Action Plan
 The new laws introduced by the government are meant to help businesses improve their cybersecurity and avoid any losses that would be incurred from cybercrime.
The new laws introduced by the government are meant to help businesses improve their cybersecurity and avoid any losses that would be incurred from cybercrime.
56. There Are More Risks Associated With SaaS Data Security Than Potential GDPR Fines
 The growing reliance on SaaS business calls for an improvement in security. On occasions, data security can be of existential importance to organizations.
The growing reliance on SaaS business calls for an improvement in security. On occasions, data security can be of existential importance to organizations.
57. How to Protect Your Organization from Double Extortion Ransomware
 Ransomware attacks have affected organisations from missile developers to Manchester United. Protecting yourself from them is an important part of security
Ransomware attacks have affected organisations from missile developers to Manchester United. Protecting yourself from them is an important part of security
58. Ransomware Doesn't Arise in a Vacuum - Spotting the Early Sign of Ransomware Infection
 In some cases, ransomware deployment is just the last step in a network compromise and is dropped as a way to obfuscate previous post-compromise activities.
In some cases, ransomware deployment is just the last step in a network compromise and is dropped as a way to obfuscate previous post-compromise activities.
59. Ransoms Paid are at a 300% Increase From the Previous Year; CISA Launches StopRansomware.gov
 StopRansomware.gov provides relevant information to support organizations with answers on cybersecurity threats.
StopRansomware.gov provides relevant information to support organizations with answers on cybersecurity threats.
60. A Beginner's Guide on Ransomware: How To Identify and Prevent Attacks
 Ransomware is a different kind of malware. Find out how to identify and prevent its attacks that encrypt your files and demand a paid ransome for data access.
Ransomware is a different kind of malware. Find out how to identify and prevent its attacks that encrypt your files and demand a paid ransome for data access.
61. Digital Threats and Countermeasures: How Close are We to a Cyberwar?
 Cyberwar became a reality more than a decade ago. People not connected to the creation of cyberweapons can see only the tip of the iceberg.
Cyberwar became a reality more than a decade ago. People not connected to the creation of cyberweapons can see only the tip of the iceberg.
62. Ransomware Steals the Limelight, But It’s Not the Only Threat We Face
 Viewing ransomware as a virus isn’t correct from a technical standpoint. Ransomware is malware, meaning it’s meant to damage, disrupt, or hack a device.
Viewing ransomware as a virus isn’t correct from a technical standpoint. Ransomware is malware, meaning it’s meant to damage, disrupt, or hack a device.
63. What Is Triple Extortion Ransomware and How to Prevent It
 Ransomware is becoming more common and with it comes new threats. Triple Extortion Ransomware is a new form of attack that threatens companies across the world.
Ransomware is becoming more common and with it comes new threats. Triple Extortion Ransomware is a new form of attack that threatens companies across the world.
64. Cybersecurity Predictions For 2022
 This article will highlight the potential threat vectors and protections that may have a large-scale and global impact in 2022.
This article will highlight the potential threat vectors and protections that may have a large-scale and global impact in 2022.
65. How To Handle Every Ransomware Challenge With Ease Using These Tips
 There was nothing in particular that should have drawn attention to the two individuals sitting for drinks at the bar in Reno. Just two old colleagues catching up over some drinks.
There was nothing in particular that should have drawn attention to the two individuals sitting for drinks at the bar in Reno. Just two old colleagues catching up over some drinks.
66. 7 Sneaky Ways Hackers Are Using Machine Learning to Steal Your Data
 Machine learning is famous for its ability to analyze large data sets and identify patterns. It is basically a subset of artificial intelligence. Machine learning uses algorithms that leverages previous data-sets and statistical analysis to make assumptions and pass on judgments about behavior.
The best part, software or computers powered by machine learning algorithms can perform functions that they have not been programmed to perform.
Machine learning is famous for its ability to analyze large data sets and identify patterns. It is basically a subset of artificial intelligence. Machine learning uses algorithms that leverages previous data-sets and statistical analysis to make assumptions and pass on judgments about behavior.
The best part, software or computers powered by machine learning algorithms can perform functions that they have not been programmed to perform.
Thank you for checking out the 66 most read stories about Ransomware on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

