Let's learn about Vpn via these 167 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
VPN stands for Virtual Private Network. It gives you another layer of protection.
1. How to Create a Personal Residential Proxy to Bypass Geo Restrictions
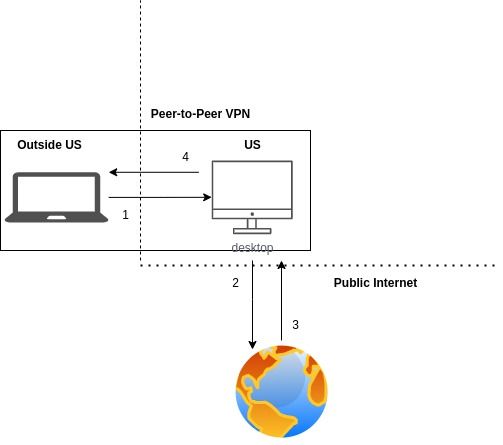 By setting up a peer-to-peer(P2P) VPN and connecting my laptop and desktop to it, I was able to route the traffic of my laptop in India to my desktop in the US.
By setting up a peer-to-peer(P2P) VPN and connecting my laptop and desktop to it, I was able to route the traffic of my laptop in India to my desktop in the US.
2. Proxy Vs. VPN Vs. SmartDNS [A Comparison]

3. 5 Best Free Proxy Servers To Visit Sites Anonymously In 2020
 A proxy server will assist you to mask your identity on the web. Perhaps you wish to access suspicious websites, bypass net censorship in your country or on your office/school network having a proxy website among your reach is very important.
A proxy server will assist you to mask your identity on the web. Perhaps you wish to access suspicious websites, bypass net censorship in your country or on your office/school network having a proxy website among your reach is very important.
4. Ghost the Internet Like It Is Your Ex
 Combine your VPN with crypto payments and the result is a truly anonymous and global browsing experience.
Combine your VPN with crypto payments and the result is a truly anonymous and global browsing experience.
5. 4 Signs You Make it Easy For Someone to Hack You
 Hacking can happen on any device and to any person—and hackers are only getting smarter by the minute.
Hacking can happen on any device and to any person—and hackers are only getting smarter by the minute.
6. How You Can Protect Your Online Privacy: Easy Steps for Daily Activities
 (Image by Reimund Bertrams from Pixabay)
(Image by Reimund Bertrams from Pixabay)
7. Top 5 Myths About VPNs and Why They’re Wrong
 A VPN, or Virtual Private Network, is a service that protects your online privacy by connecting your device to the Internet through an “encrypted tunnel. While this may sound simple, in reality encryption is notoriously difficult--and misunderstood. As a result, many misconceptions have sprung up about VPNs, leading to faulty and distorted ideas about what they are--and aren’t.In this article, we’ll address the five top myths about VPNs, explain why they’re wrong, and highlight how VPNs can make your online life safer and easier.
A VPN, or Virtual Private Network, is a service that protects your online privacy by connecting your device to the Internet through an “encrypted tunnel. While this may sound simple, in reality encryption is notoriously difficult--and misunderstood. As a result, many misconceptions have sprung up about VPNs, leading to faulty and distorted ideas about what they are--and aren’t.In this article, we’ll address the five top myths about VPNs, explain why they’re wrong, and highlight how VPNs can make your online life safer and easier.
8. Thinking of Moving to Germany? Here's What to Expect Working as a Software Developer in Germany
 Germany offers ample opportunities for developers to find fulfilling & well-paid jobs. Most developer jobs in Germany require Java, Python, SQL, and JavaScript.
Germany offers ample opportunities for developers to find fulfilling & well-paid jobs. Most developer jobs in Germany require Java, Python, SQL, and JavaScript.
9. Why Network Security is an Integral Part of Any Internet-Connected Business
 Network security is vital for any internet-connected company. Without it, hackers can steal all the data the business has. Bad network security causes problems
Network security is vital for any internet-connected company. Without it, hackers can steal all the data the business has. Bad network security causes problems
10. How VPNs Can Complement The Blockchain to Enhance Privacy
 Across the globe, the talk has all been centered on privacy. This is expectedly so since both individuals and brands are at the receiving end of prying eyes.
Across the globe, the talk has all been centered on privacy. This is expectedly so since both individuals and brands are at the receiving end of prying eyes.
11. Exploring 3 Drawbacks To VPN Usage: Do VPNs Really Protect Your Privacy?
 Let’s take a look at the three key issues associated with Virtual Private Networks while questioning whether they’re really as private as we’re led to believe.
Let’s take a look at the three key issues associated with Virtual Private Networks while questioning whether they’re really as private as we’re led to believe.
12. 7 Ways to Secure Your Social Media Accounts
 In the world today, cybersecurity attacks happen every 39 seconds. 300,000 new malware is created every day; our beloved Facebook is attacked 100k+ a day; and, just very recently had a massive security breach.
In the world today, cybersecurity attacks happen every 39 seconds. 300,000 new malware is created every day; our beloved Facebook is attacked 100k+ a day; and, just very recently had a massive security breach.
13. Your VPN Might Be Tracking and Logging Your Browsing Habits

14. VPNs Leaked 1.2TB of Your Data and That is Pretty Awkward
 20 Million VPN users across seven different VPN services had their data compromised when it ended up on the dark web.
20 Million VPN users across seven different VPN services had their data compromised when it ended up on the dark web.
15. How Apple’s Upcoming Private Relay Feature Will Affect End Users and The VPN Market
 If Apple’s implementation of this new feature actually lives up to its lofty promises, then Private Relay will offer a high level of privacy.
If Apple’s implementation of this new feature actually lives up to its lofty promises, then Private Relay will offer a high level of privacy.
16. How IP Obfuscation Works for Streaming Geo-Restricted Content
 IP obfuscation is a process of making the geographic location of a user to be concealed or masked. IP obfuscation, which is also known as geo-spoofing, includes everything that makes a user's identity to be hidden or made anonymous with different methods.
IP obfuscation is a process of making the geographic location of a user to be concealed or masked. IP obfuscation, which is also known as geo-spoofing, includes everything that makes a user's identity to be hidden or made anonymous with different methods.
17. Seven things that slow down your VPN and What You Can Do About It
 Those accustomed to Virtual Private Networks probably know what a painful experience is slow connection speed. Paradoxically, VPNs are the #1 go-to software when talking about torrenting (where speed matters a lot), yet, due to their technicality, some sort of a speed drop is inevitable.
Those accustomed to Virtual Private Networks probably know what a painful experience is slow connection speed. Paradoxically, VPNs are the #1 go-to software when talking about torrenting (where speed matters a lot), yet, due to their technicality, some sort of a speed drop is inevitable.
18. What Does a Decentralized VPN Look Like?
 As far as the Internet is concerned one of the most significant hot-button issues has got to be the issue of privacy and restrictions. Currently, everyone seems to have an opinion over the prospect of providing restrictions and keeping other people from having access to some portions of the Internet-technology which, ideally, should have been for us all.
As far as the Internet is concerned one of the most significant hot-button issues has got to be the issue of privacy and restrictions. Currently, everyone seems to have an opinion over the prospect of providing restrictions and keeping other people from having access to some portions of the Internet-technology which, ideally, should have been for us all.
19. Automating User Management in the Company
 Have you ever faced the challenge of automating users in your company?
Have you ever faced the challenge of automating users in your company?
20. How to Change Location on Hulu
 Are you looking for a way to change location on Hulu? Then, you have come to the right place because this content will tell you the easiest way to change Hulu
Are you looking for a way to change location on Hulu? Then, you have come to the right place because this content will tell you the easiest way to change Hulu
21. Introduction: What Is a VPN?
 A virtual private network (VPN) is a technology that enables you to create a safe and encrypted connection over the internet.
A virtual private network (VPN) is a technology that enables you to create a safe and encrypted connection over the internet.
22. 7 Ways to Improve Cybersecurity when You Travel in 2022
 If you travel frequently, you should know how to safeguard your data. Think about these things before taking off on your next vacation.
If you travel frequently, you should know how to safeguard your data. Think about these things before taking off on your next vacation.
23. 5 Reasons Why Your Startup or SMB needs a VPN
 Conversations about VPN servers for business applications usually come down to on-premises solutions for large corporations with several international offices and thousands of employees who require access to shared intranet. On the other hand, cloud-based VPN services often cater to private customers looking to stream their favourite TV shows while travelling, or to circumvent the Great Firewall.
Conversations about VPN servers for business applications usually come down to on-premises solutions for large corporations with several international offices and thousands of employees who require access to shared intranet. On the other hand, cloud-based VPN services often cater to private customers looking to stream their favourite TV shows while travelling, or to circumvent the Great Firewall.
24. The Easiest Way to Access the Dark Web on an iPhone
 Learn how to access the dark web on your iPhone with these simple steps. Stay anonymous and protect your privacy while browsing the hidden web.
Learn how to access the dark web on your iPhone with these simple steps. Stay anonymous and protect your privacy while browsing the hidden web.
25. A Majority of Aussies Not Motivated to Pursue Content Further After Facing Blocked Pirate Sites
 Research commissioned by the Australian government says 59% of people faced with a blocked pirate site are more likely to simply give up than try other means.
Research commissioned by the Australian government says 59% of people faced with a blocked pirate site are more likely to simply give up than try other means.
26. How Can VPNs Protect You From Spying?
 What programs can safeguard your computer from malware? In today’s article, we will take a look at VPNs and what it can do to protect you from spying.
What programs can safeguard your computer from malware? In today’s article, we will take a look at VPNs and what it can do to protect you from spying.
27. VPNs Do Not Slow You Down, They Make You Better
 VPNs started trending in this new wave of security breaches and fear for privacy.
VPNs started trending in this new wave of security breaches and fear for privacy.
28. 5 Reasons Why VPNs are not Safe in 2021
 All good things must come to an end, which may be true for the VPN in 2021. VPNs have been a useful enterprise tool for companies since they started in the 90s,
All good things must come to an end, which may be true for the VPN in 2021. VPNs have been a useful enterprise tool for companies since they started in the 90s,
29. How to Spoof Your GPS Location on iPhone
 Learn how to easily fake your iPhone's GPS location without jailbreaking! Follow this step-by-step guide to spoof your GPS location on any iOS device.
Learn how to easily fake your iPhone's GPS location without jailbreaking! Follow this step-by-step guide to spoof your GPS location on any iOS device.
30. Why Google Entering The VPN Marketplace Means it’s Time to Take Mobile Security Seriously
 VPNs are sometimes seen as an optional luxury when it comes to safeguarding your personal information online, but with Google entering the fray with its own service will mobile VPNs finally get noticed?
VPNs are sometimes seen as an optional luxury when it comes to safeguarding your personal information online, but with Google entering the fray with its own service will mobile VPNs finally get noticed?
31. How to Get Lifetime VPN Coverage and Cybersecurity Training
 Right now, VPN Unlimited & Infosec4TC Platinum Cyber Security Course Membership Lifetime Access is on sale for just $89.99.
Right now, VPN Unlimited & Infosec4TC Platinum Cyber Security Course Membership Lifetime Access is on sale for just $89.99.
32. The Occam’s Razor of Newsletter Subscriptions
 Subscribe to the HackerNoon newsletter with ease.
Subscribe to the HackerNoon newsletter with ease.
33. Why you will Still Need a VPN in 2022
 Some people say that the VPN is becoming obsolete. But is it really so?
Some people say that the VPN is becoming obsolete. But is it really so?
34. Being 'Chief Geek' and Running 15 Websites with Noonies Nominee Mathias Hellquist
 So who TF is Mathias Hellquist and what is a "Chief Geek"? Read this interview to find out.
So who TF is Mathias Hellquist and what is a "Chief Geek"? Read this interview to find out.
35. Common Misconceptions About Why VPNs Are Used
 There are some misconceptions about why VPNs are used such as the extent of the privacy that they offer and how well such systems can keep users anonymous.
There are some misconceptions about why VPNs are used such as the extent of the privacy that they offer and how well such systems can keep users anonymous.
36. NFL Going Against VPN Sites For ‘Promoting’ Illegal Streaming
 Several takedown notices, reportedly sent on behalf of the NFL, are asking Google to remove VPN-related URLs. According to a recent request, these sites promote the use of VPN services "to illegally stream NFL games." While many of the pages show how VPNs can bypass geographical restrictions, Google has left most URLs in its search results.
Several takedown notices, reportedly sent on behalf of the NFL, are asking Google to remove VPN-related URLs. According to a recent request, these sites promote the use of VPN services "to illegally stream NFL games." While many of the pages show how VPNs can bypass geographical restrictions, Google has left most URLs in its search results.
37. 5 Best VPN Services for Routers
 What are some of the best VPNs that can be installed directly onto a router?
What are some of the best VPNs that can be installed directly onto a router?
38. Internet Region Hopping Your Way to The American Version of Netflix
 After getting free from work and finishing the house chores, all a normal human being desires (in Lucifer’s voice) is to relax and unwind. We sink into the couch, grab our favorite munchies, and hit the “Netflix” button on our TV remotes. It may sound a little sad, but we live for that temporary escape and freedom offered by Netflix.
After getting free from work and finishing the house chores, all a normal human being desires (in Lucifer’s voice) is to relax and unwind. We sink into the couch, grab our favorite munchies, and hit the “Netflix” button on our TV remotes. It may sound a little sad, but we live for that temporary escape and freedom offered by Netflix.
39. NordVPN Prices vs. ExpressVPN Prices: What is the Better Deal?
 Which users will find more value out of ExpressVPN, and which users will prefer NordVPN's prices?
Which users will find more value out of ExpressVPN, and which users will prefer NordVPN's prices?
40. What Personal Details Are You Sharing Without Knowing?
 Unless you have changed your web browser default settings it is quite likely you are leaking personal details as you move around online. But just how much?
Unless you have changed your web browser default settings it is quite likely you are leaking personal details as you move around online. But just how much?
41. Privacy vs Secrecy and Your Right to Both
 If you’ve ever neglected your online privacy because you know you “have nothing to hide!”, this article might make you think twice.
If you’ve ever neglected your online privacy because you know you “have nothing to hide!”, this article might make you think twice.
42. 5 Best VPN Services for Chromebook
 A Chromebook is very useful to have when out and about. It combines the best features of a tablet and laptop, allowing for maximum portability and functionality. However, this portability can lead to some problems with security, as users might be tempted to connect to open networks. Malicious hackers might try to use those networks to steal sensitive information and launch attacks, making such connections especially risky. Anyone looking to maximize their security on the go should consider checking out the 5 best VPN services for Chromebook.
A Chromebook is very useful to have when out and about. It combines the best features of a tablet and laptop, allowing for maximum portability and functionality. However, this portability can lead to some problems with security, as users might be tempted to connect to open networks. Malicious hackers might try to use those networks to steal sensitive information and launch attacks, making such connections especially risky. Anyone looking to maximize their security on the go should consider checking out the 5 best VPN services for Chromebook.
43. How to Set Up a Windows IPv4 Client With an Ubuntu WireGuard Server
 Step-by-step tutorial to correctly configure a Windows client to work with an Ubuntu WireGuard VPN server.
Step-by-step tutorial to correctly configure a Windows client to work with an Ubuntu WireGuard VPN server.
44. 5 Best Free VPN Services for Netflix (VPNs w/Free Trials)
 VPN services can bypass Netflix restrictions, but some of them have better speed and reliability than others.
VPN services can bypass Netflix restrictions, but some of them have better speed and reliability than others.
45. 5 Best VPN Services Supporting Multiple Devices
 Learn about the best VPNs with support for multiple devices!
Learn about the best VPNs with support for multiple devices!
46. VPNs vs. Streaming Platforms: The Never-Ending War
 Why are VoDs not banning users for VPN usage on their platform? Read about the never-ending battle between VPN services and streaming platforms.
Why are VoDs not banning users for VPN usage on their platform? Read about the never-ending battle between VPN services and streaming platforms.
47. 7 Reasons Why Everyone Should Use a VPN
 A VPN can do so much more than giving you access to geo-restricted content. Check out why everyone should use a VPN.
A VPN can do so much more than giving you access to geo-restricted content. Check out why everyone should use a VPN.
48. A Single Speed Test is Fun — Hundreds of Them, May Actually be More Accurate
 Releasing the first internal build of the NordVPN apps that included NordLynx – our brand new protocol built on the backbone of WireGuard® – was an exciting moment for the team. Everyone started posting their speed test results on Slack and discussing the variance. While most of the time NordLynx outperformed other protocols, there were some cases with slightly worse speed results.
Releasing the first internal build of the NordVPN apps that included NordLynx – our brand new protocol built on the backbone of WireGuard® – was an exciting moment for the team. Everyone started posting their speed test results on Slack and discussing the variance. While most of the time NordLynx outperformed other protocols, there were some cases with slightly worse speed results.
49. Introduction to Residential Proxy Servers
 Identify what is the residential proxy and prevent proxies from accessing geo-blocked content
Identify what is the residential proxy and prevent proxies from accessing geo-blocked content
50. How To Deploy Algo VPN with NextDNS on UpCloud [Video]
 Hi Guys !!
Hi Guys !!
51. 5 Best VPN Services With No Lag
 One of the hardest parts about choosing a VPN is finding one that won’t impact the speed of your online connection. VPNs reroute your traffic through distant servers, making any online requests or downloads take longer than they usually would no matter what. Some services are better about this than others, mostly by providing a massive number of servers that users can test to find the fastest connection while keeping their privacy secure. Those looking for the best of both worlds should consider checking out the 5 best VPN services with no lag — or, at least, as little lag as possible.
One of the hardest parts about choosing a VPN is finding one that won’t impact the speed of your online connection. VPNs reroute your traffic through distant servers, making any online requests or downloads take longer than they usually would no matter what. Some services are better about this than others, mostly by providing a massive number of servers that users can test to find the fastest connection while keeping their privacy secure. Those looking for the best of both worlds should consider checking out the 5 best VPN services with no lag — or, at least, as little lag as possible.
52. Are Private Search Engines Truly Private?
 As of January 2020, 59% of the global population is connected to the internet.
As of January 2020, 59% of the global population is connected to the internet.
53. 5 Best Linux VPN Services: Take Control of Your Security
 Thanks to the rise of portable devices like the Steam Deck, Linux is gaining more popularity as an operating system than ever before. The platform is built by users, for users, aiming to give them complete control over the software and features on their machine. Unfortunately, this means they’ll have access to fewer popular applications that are available on Windows and Mac — possibly including VPNs. Those having trouble with figuring out how to start should take a look at the 5 best VPN services on Linux, though they might be surprised at how many options they truly have.
Thanks to the rise of portable devices like the Steam Deck, Linux is gaining more popularity as an operating system than ever before. The platform is built by users, for users, aiming to give them complete control over the software and features on their machine. Unfortunately, this means they’ll have access to fewer popular applications that are available on Windows and Mac — possibly including VPNs. Those having trouble with figuring out how to start should take a look at the 5 best VPN services on Linux, though they might be surprised at how many options they truly have.
54. 5 Best VPNs for School or University (Free and Paid)
 Today, VPNs are becoming more prevalent than ever. While some advocates of these services would go as far as recommending users to create their own, there’s one group that simply won’t have that option. Kids trying to enjoy their time at school might not have much luck if they’re especially strict about which webpages are allowed to be visited.
Today, VPNs are becoming more prevalent than ever. While some advocates of these services would go as far as recommending users to create their own, there’s one group that simply won’t have that option. Kids trying to enjoy their time at school might not have much luck if they’re especially strict about which webpages are allowed to be visited.
55. How to Protect Your Netflix Account from Getting Hacked
 Netflix accounts getting hacked are the least bit of anyone’s concern. Not because it doesn’t mean anything to us, but we anticipate little harm from it. After all, what more can a hacker do than to watch a few titles, get to see their favorite shows or movies? But that’s not always the case. We have left this issue unsupervised for far too long, and there is harm more significant than we give credit for.
Netflix accounts getting hacked are the least bit of anyone’s concern. Not because it doesn’t mean anything to us, but we anticipate little harm from it. After all, what more can a hacker do than to watch a few titles, get to see their favorite shows or movies? But that’s not always the case. We have left this issue unsupervised for far too long, and there is harm more significant than we give credit for.
56. Three Pillars of Online Defense: How to Stay Safe (and Productive) Online
 The article examines three crucial (and simple) ways to protect yourself online, and how to choose an effective service for the job.
The article examines three crucial (and simple) ways to protect yourself online, and how to choose an effective service for the job.
57. 5 Best VPN Services for Fire Stick
 Learn about 5 VPN services that work great for streaming on Amazon Fire Stick!
Learn about 5 VPN services that work great for streaming on Amazon Fire Stick!
58. Why You Should Be Using a VPN in 2019 ?
 VPNs has grown in demand in recent years among individuals are using it to secure their information and data to prevent hackers or for other misuses.
VPNs has grown in demand in recent years among individuals are using it to secure their information and data to prevent hackers or for other misuses.
59. The Case for The Defence: Securing The Future With VPN Technology
 According to statistics, hackers attack every 39 seconds - at a rate of 2,244 times each day. As the world begins to brace itself for another year set to be disrupted by Covid complications and more working from home, it seems essential that we do what we can to make sure our devices are as secure as possible as we work, study, and play away using our own servers.
According to statistics, hackers attack every 39 seconds - at a rate of 2,244 times each day. As the world begins to brace itself for another year set to be disrupted by Covid complications and more working from home, it seems essential that we do what we can to make sure our devices are as secure as possible as we work, study, and play away using our own servers.
60. 5 Best iPhone VPN Services: Secure Your iOS Devices
 iPhones are some of the most widely-used devices in the world. This also makes them some of the most targeted pieces of technology out there, with numerous vulnerabilities being exploited by malicious attackers as often as possible. For the sake of security, privacy, and avoiding content locks, it’s likely that many people will want to look into using a VPN on their device. But while many of these services are available for a wide range of operating systems, iPhones are unique in more ways than one. The question remains: what are the best VPN services for iPhone, and how do they differ from their desktop counterparts?
iPhones are some of the most widely-used devices in the world. This also makes them some of the most targeted pieces of technology out there, with numerous vulnerabilities being exploited by malicious attackers as often as possible. For the sake of security, privacy, and avoiding content locks, it’s likely that many people will want to look into using a VPN on their device. But while many of these services are available for a wide range of operating systems, iPhones are unique in more ways than one. The question remains: what are the best VPN services for iPhone, and how do they differ from their desktop counterparts?
61. Expert Web Security Tips for Digital Nomads
 Web security is the process of protecting systems, networks, programs, devices, and data from cyber-attacks. It aims to reduce or stop the risk of cyber-attacks and protect against the unauthorized hijacking of systems, networks, and technologies.
Web security is the process of protecting systems, networks, programs, devices, and data from cyber-attacks. It aims to reduce or stop the risk of cyber-attacks and protect against the unauthorized hijacking of systems, networks, and technologies.
62. VPN Leaks that Threaten Your Online Privacy Daily
 According to research by GlobalWebIndex, in 2018, around 25% of Internet users have used a VPN service. There are several reasons for this spike in popularity, which you can read about in my previous article. One of the main reasons is the ability to bypass geo-blocks and gain access to, for example, a full Netflix library.
According to research by GlobalWebIndex, in 2018, around 25% of Internet users have used a VPN service. There are several reasons for this spike in popularity, which you can read about in my previous article. One of the main reasons is the ability to bypass geo-blocks and gain access to, for example, a full Netflix library.
63. The Most Essential Password Manager Features For 2022
 Why We Added A Security Dashboard (And More) To our password manager
Why We Added A Security Dashboard (And More) To our password manager
64. These Password Essentials Will Keep Hackers At Bay
 One of the common ways hackers target online users is by cracking their passwords. In this article, I will share tips on how to ensure your passwords are secure to keep hackers at bay.
One of the common ways hackers target online users is by cracking their passwords. In this article, I will share tips on how to ensure your passwords are secure to keep hackers at bay.
65. WTF are VPN Protocols?
 Virtual Private Networks are compared in many aspects: some are judged by their speed, others by their server amount, and the reputation of all is put under the looking glass. However, only on rare occasion VPN protocols are brought into the light. And there are a few reasons for that.
Virtual Private Networks are compared in many aspects: some are judged by their speed, others by their server amount, and the reputation of all is put under the looking glass. However, only on rare occasion VPN protocols are brought into the light. And there are a few reasons for that.
66. Privacy protection and how Nym can help
 Privacy is a broad term, but, briefly speaking, it is the ability to share what you want with whom you want and how you want to do it. So, privacy is about the
Privacy is a broad term, but, briefly speaking, it is the ability to share what you want with whom you want and how you want to do it. So, privacy is about the
67. Military Grade Encryption Won’t Save You, or Your Business
68. How Can Your Startup Bypass GEO Restrictions?
 From a business front, the online world can give you all the insight you require to help grow your business towards a better path. Despite the online world being a good source, there are still restrictions being applied. You don't need a study to know: ‘’Cyber criminals are constantly finding new technologies to target victims."
From a business front, the online world can give you all the insight you require to help grow your business towards a better path. Despite the online world being a good source, there are still restrictions being applied. You don't need a study to know: ‘’Cyber criminals are constantly finding new technologies to target victims."
69. VPN And Cybersecurity Threats: How to be Safe Online
 Virtual Private Network (VPN) is a useful tool for accessing the web anonymously. It is steadily developing as an essential component of reducing the risks we are exposed to when going online. In fact, the impending growth of the VPN market, with the projected value set at $54 billion by 2024, demonstrates the potential of the industry.
Virtual Private Network (VPN) is a useful tool for accessing the web anonymously. It is steadily developing as an essential component of reducing the risks we are exposed to when going online. In fact, the impending growth of the VPN market, with the projected value set at $54 billion by 2024, demonstrates the potential of the industry.
70. Homeland Insecurity
 Innovation can solve a country’s problems, but it can also simultaneously put your private information into a hacker’s playbook.
Innovation can solve a country’s problems, but it can also simultaneously put your private information into a hacker’s playbook.
71. No Logs Policy: Do the Terms and Conditions of your VPN Really Mean It?
 When it comes to Virtual Private Networks (VPNs), no-logging policies are at the centre of privacy concerned customers attention. With the rise of social networks, Google and Facebook dominance, and Cambridge Analytica scandal, — netizen have become aware that their online data can be and is misused.
When it comes to Virtual Private Networks (VPNs), no-logging policies are at the centre of privacy concerned customers attention. With the rise of social networks, Google and Facebook dominance, and Cambridge Analytica scandal, — netizen have become aware that their online data can be and is misused.
72. 5 Ways to Ensure You Aren’t Sharing Your Workplace Data
 With so much of our lives online, it's too easy for us to make a mistake and accidentally share our workplace data. These easy methods keep your data safe.
With so much of our lives online, it's too easy for us to make a mistake and accidentally share our workplace data. These easy methods keep your data safe.
73. 8 Ways to Ensure Secure Remote Work Across Your Company
 As the world of work rapidly becomes “remote-first”, and our reliance on virtual tools grows daily, cybersecurity has emerged as an urgent priority for almost every employer.
As the world of work rapidly becomes “remote-first”, and our reliance on virtual tools grows daily, cybersecurity has emerged as an urgent priority for almost every employer.
74. Why you shouldn't trust all VPNs on Google Play Store
 There are over 250 apps in the Google Play Store that pop up when you search for VPN, but not all of them are worth downloading. Even more - most of them you should stay far away from, and never install on your device.
There are over 250 apps in the Google Play Store that pop up when you search for VPN, but not all of them are worth downloading. Even more - most of them you should stay far away from, and never install on your device.
75. A Short Guide to Digital Privacy for College Students
 Many learning management systems are compatible with Chrome, making it a challenge to maintain your digital privacy while getting your homework done.
Many learning management systems are compatible with Chrome, making it a challenge to maintain your digital privacy while getting your homework done.
76. Ditch the Subscription — Here's How to Build Your Own VPN in Five Minutes
 Build your own Wireguard VPN on an Amazon EC2 instance - for next to no cost!
Build your own Wireguard VPN on an Amazon EC2 instance - for next to no cost!
77. NordVPN Launches Password Manager, B2B Services And Storage Encryption Software
 This year has been big for the VPN market. Some buyers still remember last year’s Facebook data leaks; others have had enough with geo-blocks. And some, sadly, are threatened by governmental internet restrictions and turn to VPNs for help.
This year has been big for the VPN market. Some buyers still remember last year’s Facebook data leaks; others have had enough with geo-blocks. And some, sadly, are threatened by governmental internet restrictions and turn to VPNs for help.
78. Why Governments Use Mass Surveillance—And What To Do About It
 “I’m not a terrorist, why should I be worried about my data being monitored?”
“I’m not a terrorist, why should I be worried about my data being monitored?”
79. VPN Vs. Proxy: What's The Difference And Which One To Choose
 What are the main differences between Proxies and VPN's? Which one is best for me?
What are the main differences between Proxies and VPN's? Which one is best for me?
80. Tor Vs. VPN: Which is Better
 What is Tor
What is Tor
81. VPNs for Netflix: Benefits and Must-Have Features

82. Top 5 Gaming VPNs: Free, Trial, and Paid Options
 NordVPN, CyberGhost, and ExpressVPN are some of the best gaming VPNs on the market with free trials and affordable monthly rates. This article will explain why.
NordVPN, CyberGhost, and ExpressVPN are some of the best gaming VPNs on the market with free trials and affordable monthly rates. This article will explain why.
83. First-ever Global Live VPN Speed Test
 Comparing VPN providers can be time-consuming and not always accurate. A Live VPN Speed Test helps you solve the problem and shows you exactly which VPN is the fastest and the historical test data tells you how consistent the VPNs in the test are.
Comparing VPN providers can be time-consuming and not always accurate. A Live VPN Speed Test helps you solve the problem and shows you exactly which VPN is the fastest and the historical test data tells you how consistent the VPNs in the test are.
84. What Makes Zero Trust Better And Different From Traditional Security
 Traditional vs zero trust? Learn how zero trust outperforms the traditional model by delivering improved security, flexibility and reduced complexity.
Traditional vs zero trust? Learn how zero trust outperforms the traditional model by delivering improved security, flexibility and reduced complexity.
85. VPNs are No More Sufficient to Protect Your Privacy on the Web
 As criminals and central entities spoil our internet experience, people search for solutions to bypass the hurdles and enjoy the internet with ultimate freedom.
As criminals and central entities spoil our internet experience, people search for solutions to bypass the hurdles and enjoy the internet with ultimate freedom.
86. Why Using a VPN is the Best Way to Protect Your Personal Data When Surfing the Web
 The internet is an amazing place. It’s grown from a military network into a vast virtual universe populated by trillions of web pages. There are currently around 1.5 billion websites, but that figure is increasing daily. As the world’s population increases, so does this vast resource we call the internet.
The internet is an amazing place. It’s grown from a military network into a vast virtual universe populated by trillions of web pages. There are currently around 1.5 billion websites, but that figure is increasing daily. As the world’s population increases, so does this vast resource we call the internet.
87. In a Pandemic, Tech Workers Are Also Essential Workers
 Governments around the world have instituted lockdowns to try and slow the Covid-19 pandemic, saying that only essential workers should be still going into work. But that just raises the question: who is an essential worker in a pandemic?
Governments around the world have instituted lockdowns to try and slow the Covid-19 pandemic, saying that only essential workers should be still going into work. But that just raises the question: who is an essential worker in a pandemic?
88. Protect Your iPhone and iPad Better With These Security Tips

- Keep The Device Up To Date
89. Are VPNs Really Safe?
 Virtual Private Network (VPN) cloaks your online identity, and shielding your data from prying eyes.
Virtual Private Network (VPN) cloaks your online identity, and shielding your data from prying eyes.
90. What the Crypto World doesn’t understand about the dVPN
 Web3 is overlooking the dVPN, and thus it's hedge against heavy regulation and censorship of the cryptosphere by Big Government and Big Tech.
Web3 is overlooking the dVPN, and thus it's hedge against heavy regulation and censorship of the cryptosphere by Big Government and Big Tech.
91. Warrant Canaries, Audits, and Linux-based Protocols Shake Up VPNs
 Over the past few years, VPNs have become a vital cog in the world of online privacy. Whether you’re looking to safeguard your data, browse anonymously, or simply bypass internet restrictions, there is so much more that VPNs can offer.
Over the past few years, VPNs have become a vital cog in the world of online privacy. Whether you’re looking to safeguard your data, browse anonymously, or simply bypass internet restrictions, there is so much more that VPNs can offer.
92. WireGuard Protocol and NordLynx, or why your VPN got a lot faster recently?
 Several years ago, a casual Internet user asked about VPNs would most likely scratch his or her head in uncertainty. Sure, VPNs have been around since Microsoft developed the PPTP protocol in 1996 and granted employees a somewhat safe remote access to confidential business resources on distant databases. But in 1996 there was a total amount of 36 million Internet users, and cybersecurity was an oblique idea for most of them.
Several years ago, a casual Internet user asked about VPNs would most likely scratch his or her head in uncertainty. Sure, VPNs have been around since Microsoft developed the PPTP protocol in 1996 and granted employees a somewhat safe remote access to confidential business resources on distant databases. But in 1996 there was a total amount of 36 million Internet users, and cybersecurity was an oblique idea for most of them.
93. The Ultimate Guide to Bypassing Geo-restrictions While Streaming
 Image source
Image source
94. VPNs vs. Proxies: Protecting Your Business from Cyber-Attacks
 Owning a business and wondering which – VPNs or proxies – could protect your brand better? Read this article and learn why VPN isn’t enough.
Owning a business and wondering which – VPNs or proxies – could protect your brand better? Read this article and learn why VPN isn’t enough.
95. All about Security Information and Event Management

96. The Coronavirus Cover-Up: A Closer Look At Internet Censorship in China

97. The Great Firewall of China is Not so Great, Afterall
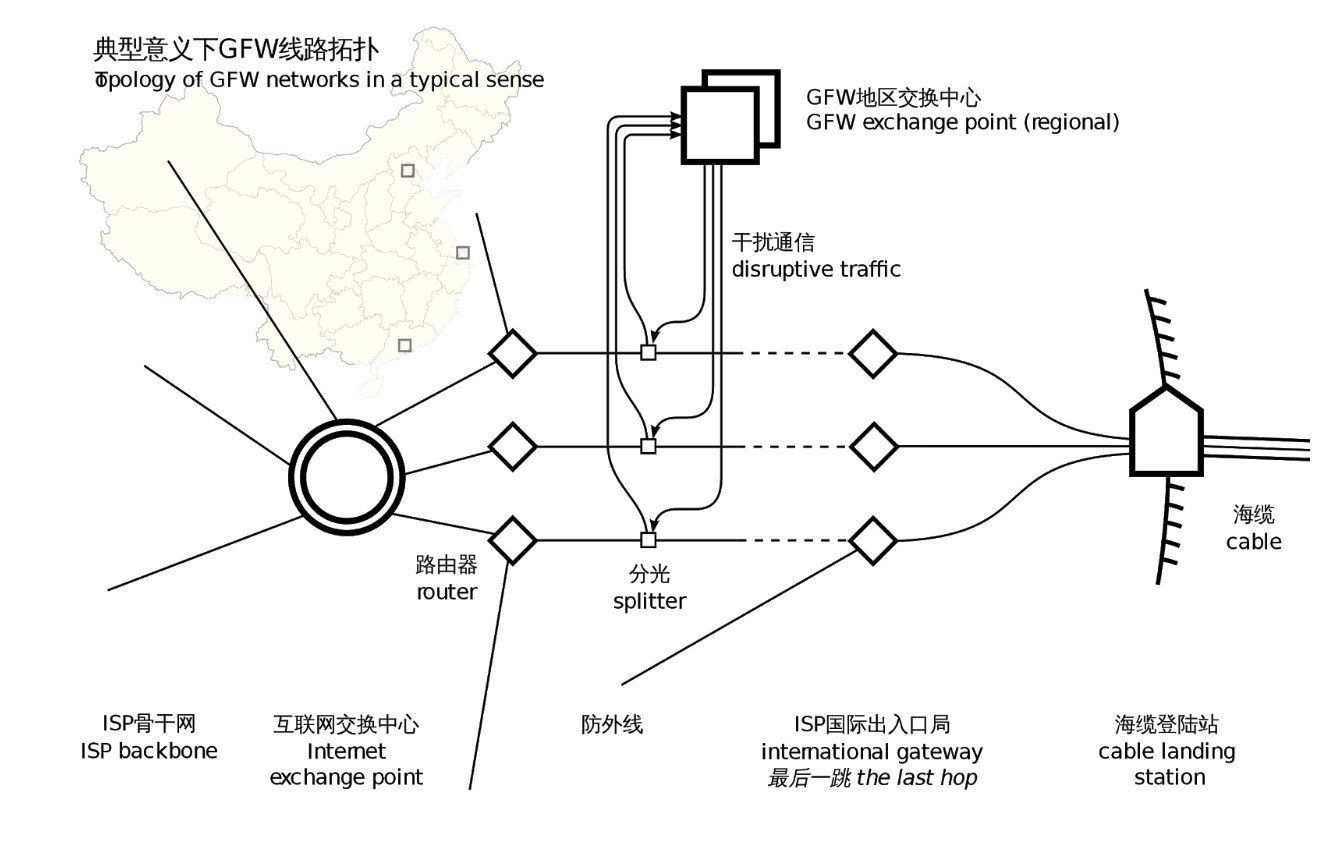 We crack open the technology that keeps 1.4 BILLION people walled in
We crack open the technology that keeps 1.4 BILLION people walled in
98. 5 Ways to Protect Your Facebook Account from Getting Hacked
 If you're wondering how to stop Facebook hackers, here are 5 easy ways to do so. This guide is beginner-friendly and all discussed methods are free.
If you're wondering how to stop Facebook hackers, here are 5 easy ways to do so. This guide is beginner-friendly and all discussed methods are free.
99. How to Protect Your Instagram Account from Being Hacked

100. Security and its Place in a Remote Working Era
 One of the consequences of COVID-19 has been our openness to remote work. By 2024, at least 40% of all remote access users will be served predominantly by ZTNA.
One of the consequences of COVID-19 has been our openness to remote work. By 2024, at least 40% of all remote access users will be served predominantly by ZTNA.
101. Hybrid-Working & Online Security: 7 Ways to Combat Threats in 2022
 Hybrid working model is the new norm and with its rise there is a dire need to keep your digital identity secure with some tested tips backed by research.
Hybrid working model is the new norm and with its rise there is a dire need to keep your digital identity secure with some tested tips backed by research.
102. What is a Man In The Middle Attack? Eavesdropping at its best.
 MitM attacks are the type of attacks where the attacker eavesdrop between two consequently communicating hosts by putting himself in between the point of data transmission. This allows the attacker to “Listen” to what the hosts are communicating and “Read” them. The Attacker here could gather the data, alter it and send the manipulated data to the receiver and vice versa.
MitM attacks are the type of attacks where the attacker eavesdrop between two consequently communicating hosts by putting himself in between the point of data transmission. This allows the attacker to “Listen” to what the hosts are communicating and “Read” them. The Attacker here could gather the data, alter it and send the manipulated data to the receiver and vice versa.
103. How to protect against cyberthreats while employees work from home
 With the COVID-19 pandemic, more and more employees have had to work from home, creating new cybersecurity challenges for businesses. Some workers will have to relearn everything about cybersecurity because they must keep their work documents and email secure even on their home network.
With the COVID-19 pandemic, more and more employees have had to work from home, creating new cybersecurity challenges for businesses. Some workers will have to relearn everything about cybersecurity because they must keep their work documents and email secure even on their home network.
104. A Beginner's Guide to the Dark Web and Online Anonymity
 If you have always wondered what’s the deal with the dark web and how to access it, or you just want to learn how to browse the web without spreading your information around, you’re at the right place.
If you have always wondered what’s the deal with the dark web and how to access it, or you just want to learn how to browse the web without spreading your information around, you’re at the right place.
105. Mimic: New Dimension in the VPN World
 VPN, or Virtual Private Networks has evolved and matured since it was originally envisioned. Meet Mimic protocol - a brand new dimension in the VPN world.
VPN, or Virtual Private Networks has evolved and matured since it was originally envisioned. Meet Mimic protocol - a brand new dimension in the VPN world.
106. What VPN services aren’t telling you about data logging
 Can you think of any popular VPN service out there that doesn’t have a big “NO LOGGING” tag attached right on front of it?
Can you think of any popular VPN service out there that doesn’t have a big “NO LOGGING” tag attached right on front of it?
107. We Open-Sourced our Encryption Software: Here's Why
 Can open-source software be profitable? Can you monetize open-source software? Forget numbers - your code cannot flourish in the dark.
Can open-source software be profitable? Can you monetize open-source software? Forget numbers - your code cannot flourish in the dark.
108. VPNs for beginners: what a VPN can and cannot do
 VPNs have become very popular in the last few years. Whether it’s the emergence of geographical restrictions, that VPNs help to bypass, or the evolution of cyber crime and privacy issues, — VPN market skyrocketed and is predicted to keep growing. This gave birth to a massive competition between VPN providers, and, sadly, some of them mislead their customers with false advertising and claims of security.
VPNs have become very popular in the last few years. Whether it’s the emergence of geographical restrictions, that VPNs help to bypass, or the evolution of cyber crime and privacy issues, — VPN market skyrocketed and is predicted to keep growing. This gave birth to a massive competition between VPN providers, and, sadly, some of them mislead their customers with false advertising and claims of security.
109. Proxy Vs. VPN: What Is Better For Data Protection in 2020
 If you are alive and functioning as a member of society in 2020, chances are you've used a VPN (Virtual Private Network) or a proxy server in the past. It may have been to stream a sports channel not available in your home country, to gain access to a foreign website, or to overcome the one-vote-per-IP address challenges associated with having multiple people in one household trying to do the same thing online.
If you are alive and functioning as a member of society in 2020, chances are you've used a VPN (Virtual Private Network) or a proxy server in the past. It may have been to stream a sports channel not available in your home country, to gain access to a foreign website, or to overcome the one-vote-per-IP address challenges associated with having multiple people in one household trying to do the same thing online.
110. The Impact of Live Streaming on Media and Entertainment Industry
 The growing popularity of live streaming is because it is interactive and engaging, and anyone can be a part of it.
The growing popularity of live streaming is because it is interactive and engaging, and anyone can be a part of it.
111. How to Install and Setup the Latest RouterOS – Quick and Secure!
 Introduction: What is Router OS?The operating system of MikroTik RouterBOARD hardware is MikroTik RouterOS. For those who prefer using a PC as their router,the software may be downloaded and installed on that machine, transforming it into an all-purpose router with all the functionality listed above.Since RouterOS is based on the Linux v2.6 kernel, we wanted to make it as simple as possible to set up and operate, so MikroTik developed it. By setting up your own vps routeros, you may create a safe, private connection between your devices and the Internet, as well as to your other resources.For how to install routeros, go to and get the CD image of RouterOSto get started now. No restrictions apply to the free trial version.
Introduction: What is Router OS?The operating system of MikroTik RouterBOARD hardware is MikroTik RouterOS. For those who prefer using a PC as their router,the software may be downloaded and installed on that machine, transforming it into an all-purpose router with all the functionality listed above.Since RouterOS is based on the Linux v2.6 kernel, we wanted to make it as simple as possible to set up and operate, so MikroTik developed it. By setting up your own vps routeros, you may create a safe, private connection between your devices and the Internet, as well as to your other resources.For how to install routeros, go to and get the CD image of RouterOSto get started now. No restrictions apply to the free trial version.
112. Our Product Was so Niche That The Hackathon Misspelled it On Our Prize Certificate: dVPNs
 Michael Astashkevich, CTO @ Smart IT (left) and Alex Solovyev, software engineer @ Smart IT (center)
Michael Astashkevich, CTO @ Smart IT (left) and Alex Solovyev, software engineer @ Smart IT (center)
113. Virtual Private Networks (VPNs): Why You Should be Using Them
 There was a time when we never come across the word VPN,
but today, it seems like we strongly need it to secure our internet connection.
There was a time when we never come across the word VPN,
but today, it seems like we strongly need it to secure our internet connection.
114. What Is a VPN and What Are Its Alternatives?
 Are VPNs really essential for an average user in 2021? Read on to find out about common issues with VPNs, as well as possible alternatives to them.
Are VPNs really essential for an average user in 2021? Read on to find out about common issues with VPNs, as well as possible alternatives to them.
115. 5 Best VPN Services and How to Choose Between Them
 The following are the 5 best VPN services: PIA VPN, ExpressVPN, NordVPN, ProtonVPN, and TunnelBear VPN, the plans each of them offer, and how to choose a VPN.
The following are the 5 best VPN services: PIA VPN, ExpressVPN, NordVPN, ProtonVPN, and TunnelBear VPN, the plans each of them offer, and how to choose a VPN.
116. VPNs are the Heroes of Our Time
 If you don’t like the way social media and other sites track you online ( and even offline), you should try a VPN.
If you don’t like the way social media and other sites track you online ( and even offline), you should try a VPN.
117. Is Decentralized Internet the Future of VPN & TCP/IP?
 Internet censorship is a contentious topic all over the world today. While some advocate it as a safety net restricting access to the dark and illegal portions of the internet, others consider it to be merely a tool used by governments and authorities to conceal information from citizens for religious or political purposes.
Internet censorship is a contentious topic all over the world today. While some advocate it as a safety net restricting access to the dark and illegal portions of the internet, others consider it to be merely a tool used by governments and authorities to conceal information from citizens for religious or political purposes.
118. The Splinternet is Coming, and How Decentralization Can Stitch It All Back Together Again
 The Opte Project, by Barrett Lyon, is a free, open-source initiative to create a visual representation of the metaphysical spaces of the internet.
The Opte Project, by Barrett Lyon, is a free, open-source initiative to create a visual representation of the metaphysical spaces of the internet.
119. Public WiFi is the Devil [Part 2]
 As the security of public WiFi is lax or non-existent, you should always double-check whether your information is safe.
As the security of public WiFi is lax or non-existent, you should always double-check whether your information is safe.
120. Be 100% Safe On The Internet Using These Strategies
 The Internet is full of opportunities, useful information, entertainment, and dangers as well. To protect yourself from the latter, you need to follow certain safety rules. Read on to learn how to properly use a home or public Wi-Fi to avoid dangerous malware and protect personal data, and what is the role of nect MODEM in helping you do so.
The Internet is full of opportunities, useful information, entertainment, and dangers as well. To protect yourself from the latter, you need to follow certain safety rules. Read on to learn how to properly use a home or public Wi-Fi to avoid dangerous malware and protect personal data, and what is the role of nect MODEM in helping you do so.
121. A Guide to the Best VPN For Your PS5
 Don’t freak out, but the moment we have all been waiting for so long has finally arrived. PlayStation 5 is here and ready to be played.
Don’t freak out, but the moment we have all been waiting for so long has finally arrived. PlayStation 5 is here and ready to be played.
122. Matthew Turner Is Pretty Excited With The Idea of Decentralized Utopia P2P Ecosystem
 You know that feeling when you work really hard on something for really long and it feels like nobody really notices? Hacker Noon’s Annual Tech Industry Awards, the 2020 Noonies, are here to help with that. Nominate YOUR best people and products today at NOONIES.TECH.
You know that feeling when you work really hard on something for really long and it feels like nobody really notices? Hacker Noon’s Annual Tech Industry Awards, the 2020 Noonies, are here to help with that. Nominate YOUR best people and products today at NOONIES.TECH.
123. 5 Best VPNs for Privacy and Security on the Dark Web
 A list of 5 powerful VPNs capable of handling Dark Web and onion nodes that will ensure your privacy and security.
A list of 5 powerful VPNs capable of handling Dark Web and onion nodes that will ensure your privacy and security.
124. Decentralized VPN: The Evolution of Tor?
 VPN vs Tor vs dVPN - What are the real differences?
VPN vs Tor vs dVPN - What are the real differences?
125. Encryption vs. Surveillance in Hong Kong
 The Hong Kong national security law created a series of provisions that restrict the flow of information and suppress the civil unrest within the region. In the short term, this new law has had a profound impact on the business landscape, creating a series of winners who seek to expand their share in the local marketplace. In the long term, it will reform the technology landscape in Hong Kong for years to come
The Hong Kong national security law created a series of provisions that restrict the flow of information and suppress the civil unrest within the region. In the short term, this new law has had a profound impact on the business landscape, creating a series of winners who seek to expand their share in the local marketplace. In the long term, it will reform the technology landscape in Hong Kong for years to come
126. How the Security of Remote Work Has Evolved With the Rise of Zero Trust
 VPNs might be the most common way of creating network security for remote work but Zero Trust Network Access might be a better designed alternative for you.
VPNs might be the most common way of creating network security for remote work but Zero Trust Network Access might be a better designed alternative for you.
127. Zero-Log VPNs Fight for User Security -Is This Reality or A Myth?
 Over time, VPN usage surged to an unprecedented level, and “Zero-Logs VPN” is what every virtual private network claims to be.
Over time, VPN usage surged to an unprecedented level, and “Zero-Logs VPN” is what every virtual private network claims to be.
128. What You Should Know About Online Tracking

And that's not necessarily bad. Seeing relevant advertisements saves time and helps in making the correct purchase decision. However, the problem arises when collected data is misused, as was revealed during the Cambridge Analytica scandal when illegally obtained user-data was used to influence political landscapes. Another problem is user consent. Sadly, a lot of data is gathered without user permission.
129. Guess Who? Access Management Struggles in the Age of Remote Work
 In the age of remote work, access management has become one of the most important- and difficult- tasks for IT professionals.
In the age of remote work, access management has become one of the most important- and difficult- tasks for IT professionals.
130. 5 Secure Technologies That Protect Online Traders
 Keeping yourself safe on the world wide web is not difficult, but it needs a certain mindset.
Keeping yourself safe on the world wide web is not difficult, but it needs a certain mindset.
131. Geo-Blocking Should Be Illegal - Change My Mind
 Geoblocking has no longer become a method for business, but a veiled form of censorship. Our constant battle for free speech has become more obvious.
Geoblocking has no longer become a method for business, but a veiled form of censorship. Our constant battle for free speech has become more obvious.
132. In-Depth Guide to Connecting your AWS and Microsoft Azure Virtual Private Networks (VPN)
 Let’s say that you have spent the last 2 years developing your enterprise services in either of the two cloud providers and now you decide to start using the other one. A possible scenario that would bring about such a requirement could be a migration from one cloud service provided to the other.
Let’s say that you have spent the last 2 years developing your enterprise services in either of the two cloud providers and now you decide to start using the other one. A possible scenario that would bring about such a requirement could be a migration from one cloud service provided to the other.
133. How VPN Security Works and Why Use One for Safe Internet Connection
 Information security is today one of the priority tasks that arise in organizations. This is especially true for enterprises whose ventures, in one way or another, are associated with data. With VPN, companies can protect their data on the Internet.
Information security is today one of the priority tasks that arise in organizations. This is especially true for enterprises whose ventures, in one way or another, are associated with data. With VPN, companies can protect their data on the Internet.
134. Latest Updates from CISA and the NSA on How To Improve VPN Security
 The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the NSA recently released new guidance for improving the security of VPN solutions.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the NSA recently released new guidance for improving the security of VPN solutions.
135. The Unsettling Rise of Internet Censorship Around the World
 To those in the West, internet censorship is often thought of as something that happens ‘elsewhere’ - China or other despotic authoritarian regimes. But increasingly overbearing government regulations have begun to threaten internet freedoms in the West too.
To those in the West, internet censorship is often thought of as something that happens ‘elsewhere’ - China or other despotic authoritarian regimes. But increasingly overbearing government regulations have begun to threaten internet freedoms in the West too.
136. Private Browsing Technologies in 2020: A Brief Overview
 As cases of Internet censorship continue to grow globally, there has been a tremendous demand for VPN services over the last few months. In Belarus, citizens resorted to privacy apps when Internet services were disrupted to throttle the widespread protests after the disputed presidential election. On the other end of the spectrum, the impending ban on popular media platforms TikTok and WeChat in the United States has already seen a surge in the sales of VPN apps. A similar trend was seen in India, Hong Kong, and other regions which had imposed similar bans earlier.
As cases of Internet censorship continue to grow globally, there has been a tremendous demand for VPN services over the last few months. In Belarus, citizens resorted to privacy apps when Internet services were disrupted to throttle the widespread protests after the disputed presidential election. On the other end of the spectrum, the impending ban on popular media platforms TikTok and WeChat in the United States has already seen a surge in the sales of VPN apps. A similar trend was seen in India, Hong Kong, and other regions which had imposed similar bans earlier.
137. On The Verge of Economic Change: An Interview with Dr Sebastian Bürgel
 It’s been over a year since COVID-19 appeared, and it’s still painfully apparent that this crisis is far from over. In fact, it may even trigger the largest economic change since World War Two. According to Arthur D. Little, a management consultancy firm, COVID-19 has been the impetus for an economic shift from a resources-driven to technology-focused economic model, one where the principles of “green” and tech go hand-in-hand. In essence, it will be data, not natural resources, which plays the fundamental role in keeping the global economy running. One possible implication of this is a full-scale transition to a digital economy. Data will be the fuel which powers our lives – and emerging technologies like the Internet of Things (IoT) and smart technologies will have to hit the ground running.
It’s been over a year since COVID-19 appeared, and it’s still painfully apparent that this crisis is far from over. In fact, it may even trigger the largest economic change since World War Two. According to Arthur D. Little, a management consultancy firm, COVID-19 has been the impetus for an economic shift from a resources-driven to technology-focused economic model, one where the principles of “green” and tech go hand-in-hand. In essence, it will be data, not natural resources, which plays the fundamental role in keeping the global economy running. One possible implication of this is a full-scale transition to a digital economy. Data will be the fuel which powers our lives – and emerging technologies like the Internet of Things (IoT) and smart technologies will have to hit the ground running.
138. The Meaning of Anonymity in The Surveillance Era
 Is there such a thing as true anonymity anymore?
Is there such a thing as true anonymity anymore?
139. 23 Cybersecurity Tips to Level up Your Data Privacy Game
 It's important to keep yourself up-to-date on the latest security measures. Cybercrime has increased, secure your data.
It's important to keep yourself up-to-date on the latest security measures. Cybercrime has increased, secure your data.
140. Private Networks: How Tailscale Works
 People often ask us for an overview of how Tailscale works. We’ve been putting off answering that, because we kept changing it! But now things have started to settle down.
People often ask us for an overview of how Tailscale works. We’ve been putting off answering that, because we kept changing it! But now things have started to settle down.
141. Long "Unbiased" VPN Reviews That Give You The Short End of the Stick [Deep Dive]

142. 5 Best Free Trial VPN Services in 2023
 Trying to find the best VPN can be a daunting task, especially when there are so many to choose from. While free VPNs might seem like an easy way to dive into better security and bypass content locks, many of them are also likely to steal information and leave users in worse spots than they already were. Not every free VPN does this, but those wishing to truly be secure online will be much more comfortable with a paid service. Luckily, some of the best VPN services come with a free trial, and users would do very well to take advantage of them.
Trying to find the best VPN can be a daunting task, especially when there are so many to choose from. While free VPNs might seem like an easy way to dive into better security and bypass content locks, many of them are also likely to steal information and leave users in worse spots than they already were. Not every free VPN does this, but those wishing to truly be secure online will be much more comfortable with a paid service. Luckily, some of the best VPN services come with a free trial, and users would do very well to take advantage of them.
143. Stay Safe While Holiday Shopping Online
 Scammers go on the naughty list.
Scammers go on the naughty list.
144. A Sweater of Safety Wrapped Around My Internet Connection
 The story of how HQ VPN came to exist – privacy, security, and peace of mind
The story of how HQ VPN came to exist – privacy, security, and peace of mind
145. NordVPN's Meshnet Lets Users Create Their Own Private Networks
 Nord's Meshnet feature allows you to route your online traffic through another machine, creating your own VPN.
Nord's Meshnet feature allows you to route your online traffic through another machine, creating your own VPN.
146. Great News About Self-Regulation In VPN industry: i2Coalition’s VTI Essentials
 In the last decade, the VPN market has been steadily growing, and this growth was spiked even further in 2020. Two main reasons contributed to an even more expansive use of VPN software: 1) Covid-19, quarantine, and work from home set the needs for home network security; 2) cybercrime has been on the rise and cybersecurity became a more common issue.
In the last decade, the VPN market has been steadily growing, and this growth was spiked even further in 2020. Two main reasons contributed to an even more expansive use of VPN software: 1) Covid-19, quarantine, and work from home set the needs for home network security; 2) cybercrime has been on the rise and cybersecurity became a more common issue.
147. Data Breaches of 2022 and How They Could Have Been Prevented
 Despite our best efforts, cybersecurity continues to lag behind the creativity of cyber criminals. As we become more interconnected, the potential for a devastating data breach only grows.
Despite our best efforts, cybersecurity continues to lag behind the creativity of cyber criminals. As we become more interconnected, the potential for a devastating data breach only grows.
148. 10 Steps to Ensuring Cyber Security for a Small Business
 How can your small business avoid being a victim of a cyber fraud? Here are 10 cyber security steps for small business safety.
How can your small business avoid being a victim of a cyber fraud? Here are 10 cyber security steps for small business safety.
149. 13 Best Proxy Servers Review [Update Apr'22] - Top Proxy Service in 2021 [Free and Paid]

150. Security Trends in 2023 That Need Your Attention
 2022 saw a plethora of new, innovative cyber threats, and in order to keep your cybersecurity up to date and be prepared for what’s coming in 2023
2022 saw a plethora of new, innovative cyber threats, and in order to keep your cybersecurity up to date and be prepared for what’s coming in 2023
151. [Mythbusting] How to Choose the Right VPN Service?
 This is not a traditional bullshit article talking about common elements for finding the right VPN service. We will explore items like a VPN kill switch, IPv6 leak protection, or why the privacy policy matters.
This is not a traditional bullshit article talking about common elements for finding the right VPN service. We will explore items like a VPN kill switch, IPv6 leak protection, or why the privacy policy matters.
152. The Use of VPNs Is Spreading in New Zealand's Universities
 It's no secret that VPNs have become very popular lately, but... what very few people know is that the use of VPNs in universities has skyrocketed in recent times. As reported by vpnetic, VPN usage in New Zealand has almost doubled since the beginning of 2020.
It's no secret that VPNs have become very popular lately, but... what very few people know is that the use of VPNs in universities has skyrocketed in recent times. As reported by vpnetic, VPN usage in New Zealand has almost doubled since the beginning of 2020.
153. How Does a VPN Work to Protect Your Privacy?
 VPNs secure your online activity. In this article, you can learn what the best VPN protocol is, how AES-256 encryption works, and what VPNs really protect from.
VPNs secure your online activity. In this article, you can learn what the best VPN protocol is, how AES-256 encryption works, and what VPNs really protect from.
154. Setting Up a Guest Wi-Fi Network Internet Securer

155. How To Fool Prices: Price Discrimination in the Digital Economy

156. Understanding VPN Jurisdiction and International Privacy
 One of the essential features of a high-quality VPN service is a no-logs policy. For more than a decade, commercial VPN service providers have been spinning the online privacy angle to boost their sales. However, not all of them take their promises seriously.
One of the essential features of a high-quality VPN service is a no-logs policy. For more than a decade, commercial VPN service providers have been spinning the online privacy angle to boost their sales. However, not all of them take their promises seriously.
157. Superstore, Netflix, and VPNs: Should we Bring back the LaserDisc?
 This Slogging discussion is about Netflix via VPNs, DVD collecting in Japan, and Studio Ghibli.
This Slogging discussion is about Netflix via VPNs, DVD collecting in Japan, and Studio Ghibli.
158. Cybersecurity Essentials to Protect Remote Workers Online

159. How to Automate Your VPN Setup With Ansible
 Setting up a WireGuard VPN? Learn how to increase server uptime, relay traffic and more, with in-depth code examples.
Setting up a WireGuard VPN? Learn how to increase server uptime, relay traffic and more, with in-depth code examples.
160. Online Privacy/Security Advocate Muhammad Hamza Shahid on Growth
 The 2020 #Noonies are here, and they are both much greener and much bigger than last year! Among the 2,000+ deserving humans nominated across 5 categories for over 200 award titles, we discovered Muhammad Hamza Shahid from United States, who has been nominated as one of our Contributors of the Year in PRIVACY, based on the reading time generated by his Hacker Noon top story: Why Governments Use Mass Surveillance—And What To Do About It.
The 2020 #Noonies are here, and they are both much greener and much bigger than last year! Among the 2,000+ deserving humans nominated across 5 categories for over 200 award titles, we discovered Muhammad Hamza Shahid from United States, who has been nominated as one of our Contributors of the Year in PRIVACY, based on the reading time generated by his Hacker Noon top story: Why Governments Use Mass Surveillance—And What To Do About It.
161. Why Privacy Matters And How To Stop Online Harassment
 All the actions people perform on the Internet is a mass give-away. The content you post on Instagram, your e-shopping patterns, and search history is a precious data set – it transforms into a commodity. The frankest questions we ask is not to our friends, but Google!
All the actions people perform on the Internet is a mass give-away. The content you post on Instagram, your e-shopping patterns, and search history is a precious data set – it transforms into a commodity. The frankest questions we ask is not to our friends, but Google!
162. Top Free And Paid VPN Services In 2021
 The VPN creates a secure connection over the Internet. In the simplest terms, it works as a tunnel between a computer and a server. Every time you go online...
The VPN creates a secure connection over the Internet. In the simplest terms, it works as a tunnel between a computer and a server. Every time you go online...
163. Mobile Proxies: What Are They, When're They Needed, and Where to Buy Them
 There are many types of proxies: datacenter, residential, ISP and so on. Each type of IP address is used for a different purpose. For example, datacenter IPs are good when you need to bypass a ban, while residential proxies will be great for arbitrage bets.In this article we will talk about mobile proxies. You will find out what their features are, what tasks they are suitable for and where to buy them.So let’s start.
There are many types of proxies: datacenter, residential, ISP and so on. Each type of IP address is used for a different purpose. For example, datacenter IPs are good when you need to bypass a ban, while residential proxies will be great for arbitrage bets.In this article we will talk about mobile proxies. You will find out what their features are, what tasks they are suitable for and where to buy them.So let’s start.
164. How to Choose the Best Secure Browser in 2021
 Are you browsing securely? Find out how today’s leading browsers stack up in terms of security, privacy, and performance.
Are you browsing securely? Find out how today’s leading browsers stack up in terms of security, privacy, and performance.
165. IPVanish VPN Reviev 2021: Speed, Privacy and All You Need to Know

166. The Ultimate Guide to Privacy and Security Tools
 A while ago, Nora asked me if I had a list of privacy tools I use regularly. I didn't, so I wrote one with the help of lp1, and you're about to read it. These are the tools we’ve been using for a while and we recommend.
A while ago, Nora asked me if I had a list of privacy tools I use regularly. I didn't, so I wrote one with the help of lp1, and you're about to read it. These are the tools we’ve been using for a while and we recommend.
167. How Decentralized Can We Get in The Modern World? (Podcast Transcript)
 In this episode, Amy & Sharmini (CMO at Mysterium Network) chat about whether it's possible to achieve anonymity and decentralization from the modern Internet.
In this episode, Amy & Sharmini (CMO at Mysterium Network) chat about whether it's possible to achieve anonymity and decentralization from the modern Internet.
Thank you for checking out the 167 most read stories about Vpn on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

