Let's learn about Phishing via these 87 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
1. MetaMask Users Targeted By Phishing Attack Impersonating Popular Metaverse Projects
 MetaMask users are being targeted in a series of phishing attacks where hackers impersonate popular metaverse project websites.
MetaMask users are being targeted in a series of phishing attacks where hackers impersonate popular metaverse project websites.
2. How to Identify a Fake Text Message in 2023
 Are you also frustrated by getting fake messages and want to identify that fake message? Then must move down for more detail about fake messages.
Are you also frustrated by getting fake messages and want to identify that fake message? Then must move down for more detail about fake messages.
3. Avast Secure Browser Gets Top Spot in AV-Comparatives' Anti-Phishing Protection Test
 Using Avast Secure Browser either as a primary or a secondary browser is easy and will give you a safer, and faster browsing experience across all your devices.
Using Avast Secure Browser either as a primary or a secondary browser is easy and will give you a safer, and faster browsing experience across all your devices.
4. Stop Phishing in its Tracks in the Coronavirus Economy: People are Your Greatest Asset
 Remember: people are your greatest asset.
Remember: people are your greatest asset.
5. Several Social Engineering Tricks
 The article is intended for white hats, professional pentesters, and heads of information security departments (CISO). Today, I want to share several methods of social engineering that can be used in targeted attacks, that is, in cases where a specific victim (person or company) is selected.
The article is intended for white hats, professional pentesters, and heads of information security departments (CISO). Today, I want to share several methods of social engineering that can be used in targeted attacks, that is, in cases where a specific victim (person or company) is selected.
6. What is URL Masking and How Does It Work?
 Be careful of the latest engineering technique called "URL Masking", it's quite dangerous.
Be careful of the latest engineering technique called "URL Masking", it's quite dangerous.
7. 4 Basic Ways To Keep Your Crypto Safe
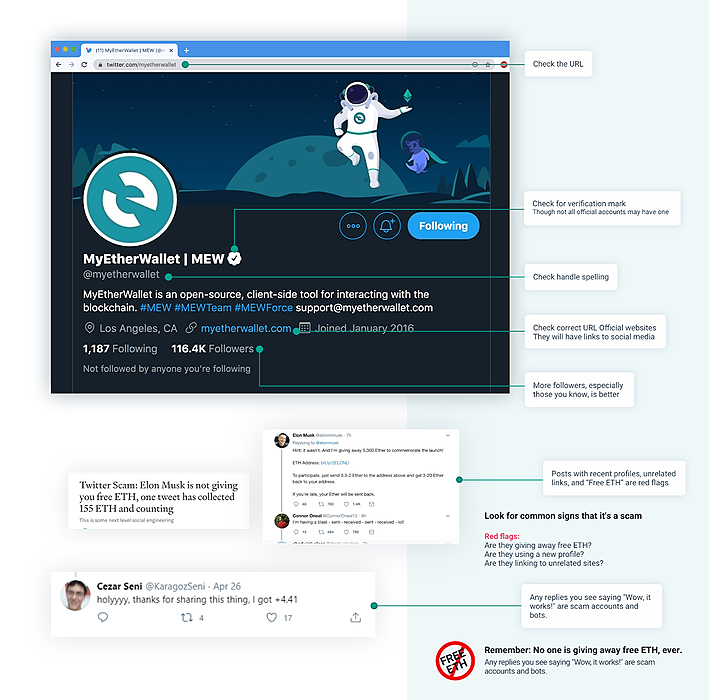 Just a week ago, Google removed 49 Chrome extensions imitating MEW, Ledger, Trezor, and other popular cryptocurrency wallets. Phishing attempts are on the rise, and in this stressful time, it’s also easy to make an irreversible mistake losing your crypto whether you’re new to crypto or an experienced hodler.
Just a week ago, Google removed 49 Chrome extensions imitating MEW, Ledger, Trezor, and other popular cryptocurrency wallets. Phishing attempts are on the rise, and in this stressful time, it’s also easy to make an irreversible mistake losing your crypto whether you’re new to crypto or an experienced hodler.
8. How To Find Out If A Hacker Has Attacked You
 Computer crimes are all those online attacks carried out by a hacker whose purpose is to breach a computer system in order to gain financial gain in some way
Computer crimes are all those online attacks carried out by a hacker whose purpose is to breach a computer system in order to gain financial gain in some way
9. Command and Control Frameworks in a Nutshell
 A glimpse over Command and Control attacks and frameworks, how they happen, and how they can affect our daily lives.
A glimpse over Command and Control attacks and frameworks, how they happen, and how they can affect our daily lives.
10. How Cryptojacking Hackers use Phishing and Software Vulnerabilities To Mine Crypto On Your Machines
 One way hackers can profit is crypto-jacking: they use social engineering and hacking to put the mining script on the victim's device and exploit its resources.
One way hackers can profit is crypto-jacking: they use social engineering and hacking to put the mining script on the victim's device and exploit its resources.
11. What are extortion emails and what can be done? By Jason Nelson
 What is an Extortion Email? An extortion email is one that claims to have access to usually pictures or videos showing users in a compromising situation or looking at something that may be a source of embarrassment.
What is an Extortion Email? An extortion email is one that claims to have access to usually pictures or videos showing users in a compromising situation or looking at something that may be a source of embarrassment.
12. She Was a Hacker, He Was a Botnet: A Phishing Love Story
 My hacker best friend decided to open Tinder. I was a bit reluctant about her decision. Unfortunately, she matches with a guy that gives her a phishing link.
My hacker best friend decided to open Tinder. I was a bit reluctant about her decision. Unfortunately, she matches with a guy that gives her a phishing link.
13. How Email Became the Weakest Link in Cybersecurity
 When did email become the weakest security link? Email was never intended to transmit sensitive information, but as with all technologies people began using it differently than it was intended to be used and it wasn’t long before hackers learned they could send malicious links and malware directly to a person’s computer via email. These days we know that email can contain malicious links, but we aren’t always trained to spot them, and sometimes we assume the spam filters will take care of it for us. Email has become the weakest link, and it’s costing businesses big time.
When did email become the weakest security link? Email was never intended to transmit sensitive information, but as with all technologies people began using it differently than it was intended to be used and it wasn’t long before hackers learned they could send malicious links and malware directly to a person’s computer via email. These days we know that email can contain malicious links, but we aren’t always trained to spot them, and sometimes we assume the spam filters will take care of it for us. Email has become the weakest link, and it’s costing businesses big time.
14. True Hackers and the Monsters we Invent
 Common misconceptions about hacking that makes you vulnerable and how to avoid them.
Common misconceptions about hacking that makes you vulnerable and how to avoid them.
15. On Cyberattacks and Data Security Solutions with Eyal Wachsman
 The US Government might be the latest victim of increasingly sophisticated global cyberattacks, but these breaches have long been a threat across all sectors.
The US Government might be the latest victim of increasingly sophisticated global cyberattacks, but these breaches have long been a threat across all sectors.
16. Crypto Fraud New Tricks: Victim's MetaMask Wallet Emptied by Resetting Apple ID
 By tricking victims into resetting their Apple ID and obtaining a 2FA one-time verification code, the scammers could access their MetaMask and drain the funds.
By tricking victims into resetting their Apple ID and obtaining a 2FA one-time verification code, the scammers could access their MetaMask and drain the funds.
17. Personal Security Online Is Not Complicated
 Well, if you want to hear something complicated, try to understand the relationship between Beyonce and Jay Z.
Well, if you want to hear something complicated, try to understand the relationship between Beyonce and Jay Z.
18. 6 Browser Extensions for Online Privacy in 2020
 A lot of things happened in 2019 that lead people talking and caring more about their privacy online. You might hear a lot of people saying that there isn’t such a thing as privacy online. Our actions online are being monitored, we get personalized ads, that are not just influencing us to buy something, but even influences our political views, influences our values, our actions.
A lot of things happened in 2019 that lead people talking and caring more about their privacy online. You might hear a lot of people saying that there isn’t such a thing as privacy online. Our actions online are being monitored, we get personalized ads, that are not just influencing us to buy something, but even influences our political views, influences our values, our actions.
19. Rethinking Email Threat Detection Models for Enterprises [A Deep Dive]
 Contrary to what millennial work and communication habits may suggest, email is not dead. It is still an important part of both personal and enterprise communications.
Contrary to what millennial work and communication habits may suggest, email is not dead. It is still an important part of both personal and enterprise communications.
20. Ransomware-as-a-Service: SaaS' Evil Twin
 This article will educate you about RaaS groups and protective measures against ransomware attacks.
This article will educate you about RaaS groups and protective measures against ransomware attacks.
21. Social Engineering and The Great Twitter Hack of 2020
 One of the most significant Twitter hacks of all time has people shook to their core. The attack targeted some of the most influential accounts on Twitter and led some to question the platform's security capabilities.
One of the most significant Twitter hacks of all time has people shook to their core. The attack targeted some of the most influential accounts on Twitter and led some to question the platform's security capabilities.
22. What is Subdomain Hijacking and How to Prevent it?
 Subdomain takeover or subdomain hijacking refers to a technique by which "unused" subdomains can be made to point to a location of the attacker's choice.
Subdomain takeover or subdomain hijacking refers to a technique by which "unused" subdomains can be made to point to a location of the attacker's choice.
23. Hacked Peruvian Government Servers are Sending Phishing Campaigns to Chase Bank Customers
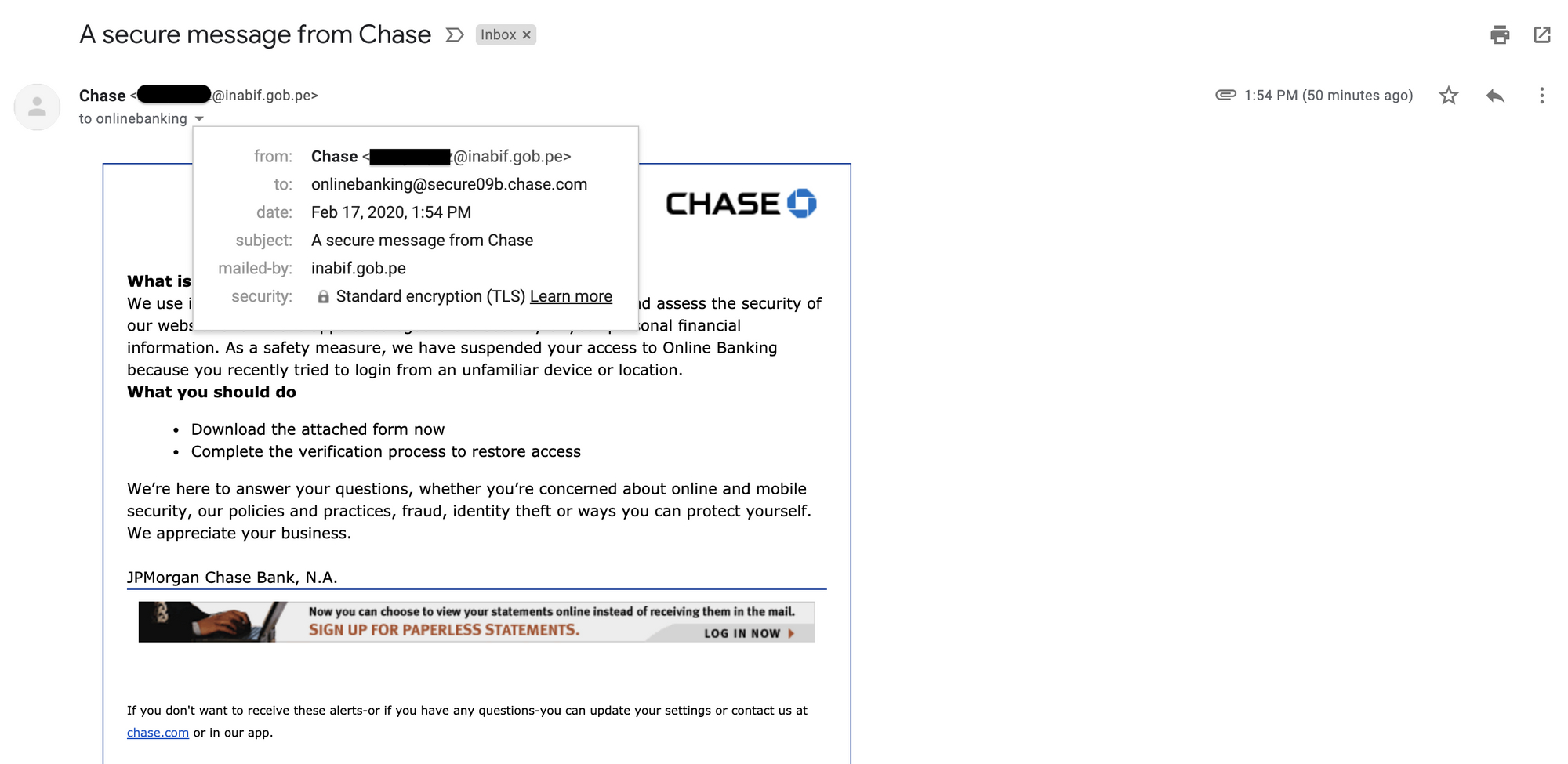 If you are a current or former Chase customer and familiar with those periodic "a secure message from Chase" email notifications, this one would've better caught your attention, if not your spam filter's. Thankfully for me, it was sent to a Gmail address I had not used with Chase online banking since 2014 or so. This instantly indicated the attackers had prior knowledge of my Gmail address having been used with Chase online banking in the past.
If you are a current or former Chase customer and familiar with those periodic "a secure message from Chase" email notifications, this one would've better caught your attention, if not your spam filter's. Thankfully for me, it was sent to a Gmail address I had not used with Chase online banking since 2014 or so. This instantly indicated the attackers had prior knowledge of my Gmail address having been used with Chase online banking in the past.
24. How You Can Protect Your Online Privacy: Easy Steps for Daily Activities
 (Image by Reimund Bertrams from Pixabay)
(Image by Reimund Bertrams from Pixabay)
25. Cybersecurity Defense Strategies Against Social Engineering
 Being steps ahead of cyber attackers matters a lot to companies. As good as this sounds, the required mechanism to deal with the cyber menace appreciates costs.
Being steps ahead of cyber attackers matters a lot to companies. As good as this sounds, the required mechanism to deal with the cyber menace appreciates costs.
26. How to Protect Yourself Against Smishing Attacks
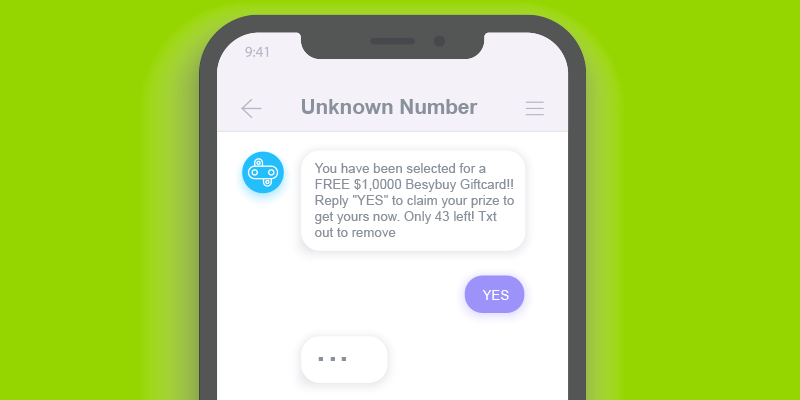 As the threat landscape encapsulating organizations and companies grows increasingly sophisticated, and harbors a growing number of threats and vulnerabilities- organizations are getting more accustomed to commonplace scams such as phishing.
As the threat landscape encapsulating organizations and companies grows increasingly sophisticated, and harbors a growing number of threats and vulnerabilities- organizations are getting more accustomed to commonplace scams such as phishing.
27. 5 Most Common Phone Scams: How to Spot Them and Protect Yourself
 Phone scams, aka Vishing, is an easy and popular method hackers use to trick people into giving out their personal information. These are a few common scams
Phone scams, aka Vishing, is an easy and popular method hackers use to trick people into giving out their personal information. These are a few common scams
28. Spit Handshakes in the Age of Digital Identity
 While meeting in person with every potential business partner is probably the best way to confirm their identity, it is Impractical in our globalized economy.
While meeting in person with every potential business partner is probably the best way to confirm their identity, it is Impractical in our globalized economy.
29. Corporate Hacking: How It Happens and How to Protect Your Business
 In this article, we’re going to take a look at some of the most common ways that companies get hacked as well as some of the most famous examples.
In this article, we’re going to take a look at some of the most common ways that companies get hacked as well as some of the most famous examples.
30. The Growing Importance of Cybersecurity Awareness
 The protection of your computer is becoming very important as more and more hackers learn how to make smarter invasions that would not be noticed at first.
The protection of your computer is becoming very important as more and more hackers learn how to make smarter invasions that would not be noticed at first.
31. Phishing in the Era of Web3.0 — Here’s What Every User Needs to Know
32. Tech Can Only Do so Much to Prevent Today's Sophisticated Cyber Attacks
 As much as we’d like to think that tech will save us, the rapid advance of hacking capabilities shows that only a human approach is effective.
As much as we’d like to think that tech will save us, the rapid advance of hacking capabilities shows that only a human approach is effective.
33. The Disruption of Emotet and What we Know About it
 Emotet, which was once a Banking Trojan and became a full-blown botnet was the most successful and prevalent malware of 2020 by a long way.
Emotet, which was once a Banking Trojan and became a full-blown botnet was the most successful and prevalent malware of 2020 by a long way.
34. How I Learned To Stop Judging People for Falling Into Cybersecurity Traps
 It’s all too easy to feel superior to the rest of the world when you work in IT day in and day out. And it’s easy to judge “the common people” for falling victim to cybersecurity scams that your highly trained BS radars would flag in a hot second.
It’s all too easy to feel superior to the rest of the world when you work in IT day in and day out. And it’s easy to judge “the common people” for falling victim to cybersecurity scams that your highly trained BS radars would flag in a hot second.
35. 7 Sneaky Ways Hackers Are Using Machine Learning to Steal Your Data
 Machine learning is famous for its ability to analyze large data sets and identify patterns. It is basically a subset of artificial intelligence. Machine learning uses algorithms that leverages previous data-sets and statistical analysis to make assumptions and pass on judgments about behavior.
The best part, software or computers powered by machine learning algorithms can perform functions that they have not been programmed to perform.
Machine learning is famous for its ability to analyze large data sets and identify patterns. It is basically a subset of artificial intelligence. Machine learning uses algorithms that leverages previous data-sets and statistical analysis to make assumptions and pass on judgments about behavior.
The best part, software or computers powered by machine learning algorithms can perform functions that they have not been programmed to perform.
36. Cloud Phishing: New Tricks and the Crown Jewel
 Cloud Computing gives phishers a new playground. This article is about Cloud Phishing — whether using the Cloud to do it or targeting the Cloud.
Cloud Computing gives phishers a new playground. This article is about Cloud Phishing — whether using the Cloud to do it or targeting the Cloud.
37. How a New Cyber Espionage Weapon in Southeast Asian Government Got Detected
 A Chinese threat group managed to hack into a Southeast Asian government by using disguised files to take advantage of a backdoor in the computer infrastructure
A Chinese threat group managed to hack into a Southeast Asian government by using disguised files to take advantage of a backdoor in the computer infrastructure
38. Phishing: Top Threat to Our Online Security
 Phishing is a cheap technique for hackers to steal the victim’s data. Now I am telling you because it really happened to me. It took my most online privacy.
Phishing is a cheap technique for hackers to steal the victim’s data. Now I am telling you because it really happened to me. It took my most online privacy.
39. Safeguard Your KuCoin Account Against Phishing Attacks: A How-To Guide
 One of the most common and increasingly applied types of attacks relying on social engineering is phishing your kucoin account details such as passwords
One of the most common and increasingly applied types of attacks relying on social engineering is phishing your kucoin account details such as passwords
40. How To Avoid 5 Nagging Security Issues With Blockchain
 Blockchain is undeniably useful to businesses, but it also has substantial limitations owing to particular security concerns. Here are the top five with fixes.
Blockchain is undeniably useful to businesses, but it also has substantial limitations owing to particular security concerns. Here are the top five with fixes.
41. 5 Effective Strategies To Identify Phishing Sites
 How to recognize phishing? Research studies show that users of different levels have a hard time figuring out if a website is real or fake. And how about you?
How to recognize phishing? Research studies show that users of different levels have a hard time figuring out if a website is real or fake. And how about you?
42. Protect Yourself Against The 440% Increase in Shipping-Related Phishing Emails
 The CDC (The Centers for Disease Control and Prevention) classified “shopping at crowded stores just before, on or after Thanksgiving” on its list
The CDC (The Centers for Disease Control and Prevention) classified “shopping at crowded stores just before, on or after Thanksgiving” on its list
43. 3 Ways CFOs can Prevent Phishing Attacks
 Whatever the size of your organization, cybersecurity should be at the forefront of your mind. Find out how CFOs can prevent phishing attacks with cybersecurity
Whatever the size of your organization, cybersecurity should be at the forefront of your mind. Find out how CFOs can prevent phishing attacks with cybersecurity
44. Fake Websites, Fake Companies, Fake Everything: What Can We Do to Protect Ourselves?
 Malware protection should act the same way, as a set of shields that protect the entire browser from any type of malware, not just traditional threats.
Malware protection should act the same way, as a set of shields that protect the entire browser from any type of malware, not just traditional threats.
45. Hosting Provider Cloud Clusters Inc. Potentially Exposed 63M Records
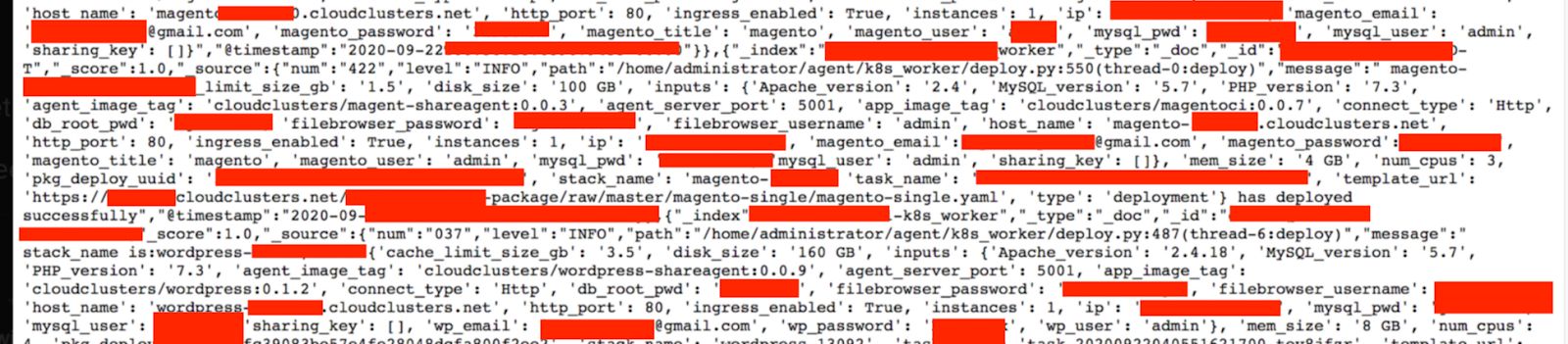 An exposed and unsecured database from Cloud Application Hosting company Cloud Clusters, Inc. was discovered on October 5, 2020, containing more than 63 million records.This discovery was made by Jeremiah Fowler from Securethoughts. Among the records were username and password credentials for Magento, WordPress, and MySql.
An exposed and unsecured database from Cloud Application Hosting company Cloud Clusters, Inc. was discovered on October 5, 2020, containing more than 63 million records.This discovery was made by Jeremiah Fowler from Securethoughts. Among the records were username and password credentials for Magento, WordPress, and MySql.
46. How Secure Are Blockchain Networks Today
 Blockchains are less likely to be hacked than other systems since they are not centralized.
Blockchains are less likely to be hacked than other systems since they are not centralized.
47. Experts Warn: Amidst Budget Cuts, The Pandemic Calls for Stepping Up Security Efforts

48. #BLM Triggers Thousands Of Domain Registrations : What This Means
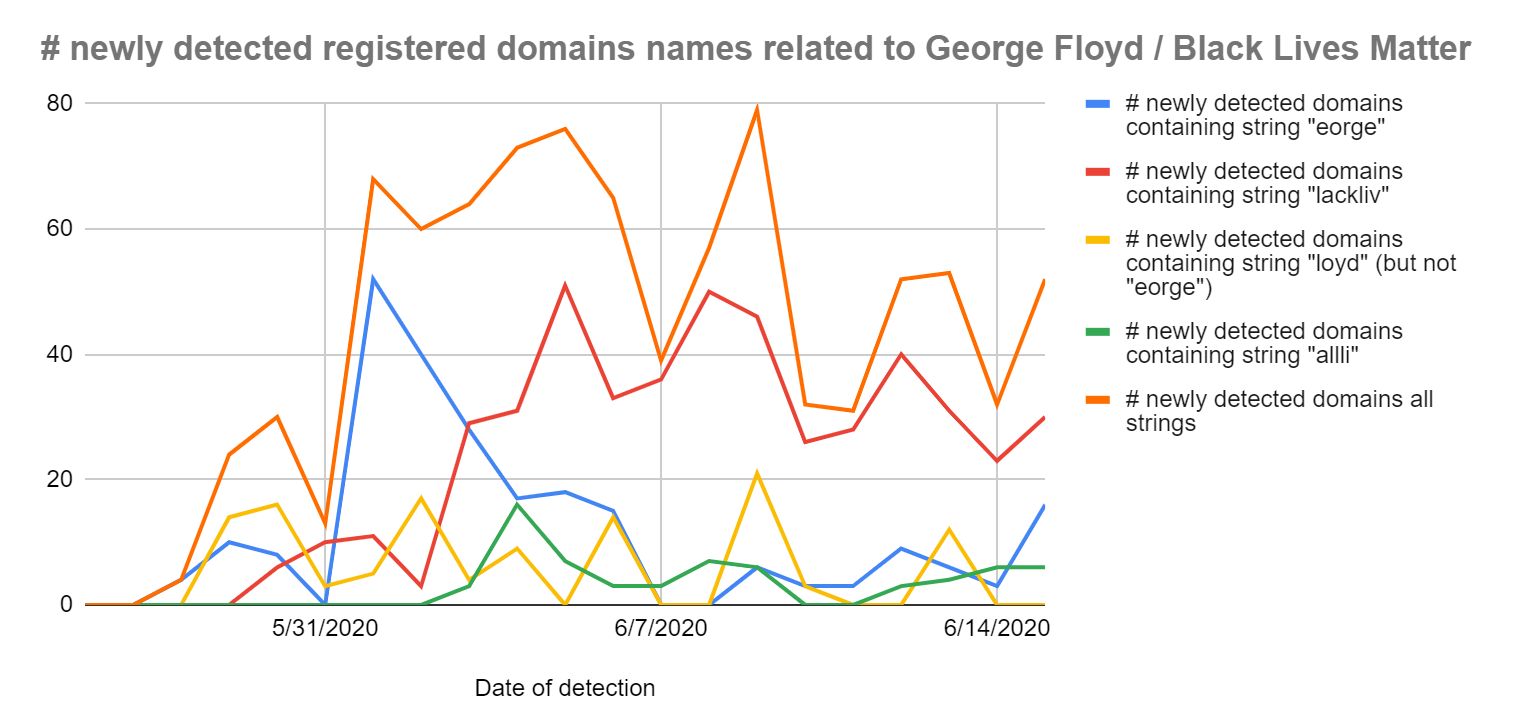 Coronavirus-themed new registered domains showed how domain name registration behaviors can be linked back to the news.
Coronavirus-themed new registered domains showed how domain name registration behaviors can be linked back to the news.
49. It's Zero-click! Pegasus Attack Don't Need Human Action
 Pegasus is the most sophisticated attack to date.
Pegasus is the most sophisticated attack to date.
50. Avoid Becoming a Victim to These Cybersecurity Threats in 2022
 With increased hacking activity focused on vulnerable businesses and at-home employees, cybersecurity has become a major business priority.
With increased hacking activity focused on vulnerable businesses and at-home employees, cybersecurity has become a major business priority.
51. A Ring of Failure
 A wise person learns from the mistakes of others. So let’s accumulate some wisdom and go over the biggest failures in the history of software.
A wise person learns from the mistakes of others. So let’s accumulate some wisdom and go over the biggest failures in the history of software.
52. How Password Managers Can Protect You From Phishing
 Password managers are a convenient way to use strong, unique passwords everywhere. Another good thing about password managers is that they help protect you from malicious websites that attempt to "phish" passwords.
Password managers are a convenient way to use strong, unique passwords everywhere. Another good thing about password managers is that they help protect you from malicious websites that attempt to "phish" passwords.
53. Israeli Ministry of Communications Might Be Inadvertently Exposing Israeli Citizens to Hackers
 While Israel faces massive cyber attacks, Israel’s Ministry of Communications debates transferring invoices from mail to e-mail.
While Israel faces massive cyber attacks, Israel’s Ministry of Communications debates transferring invoices from mail to e-mail.
54. How Artificial Intelligence is Transforming Fraud Detection in Financial Services
 In this article, you will find the common types of financial fraud and how artificial intelligence is transforming fraud detection in financial services.
In this article, you will find the common types of financial fraud and how artificial intelligence is transforming fraud detection in financial services.
55. Treat Your Cybersecurity Drills Like Fire Drills
 Employees know exactly how to act during a fire emergency, but what about a cybersecurity emergency? Here's how and why you should run cybersecurity drills.
Employees know exactly how to act during a fire emergency, but what about a cybersecurity emergency? Here's how and why you should run cybersecurity drills.
56. How to Prevent Fraudulent Credit Card Use
 A stolen credit card is unlikely to cost you huge monetary loss and will be a major hassle, which is why it’s critical to take precautions in the first place.
A stolen credit card is unlikely to cost you huge monetary loss and will be a major hassle, which is why it’s critical to take precautions in the first place.
57. Blueprint of an EFSS Phishing Attack

58. Expert Web Security Tips for Digital Nomads
 Web security is the process of protecting systems, networks, programs, devices, and data from cyber-attacks. It aims to reduce or stop the risk of cyber-attacks and protect against the unauthorized hijacking of systems, networks, and technologies.
Web security is the process of protecting systems, networks, programs, devices, and data from cyber-attacks. It aims to reduce or stop the risk of cyber-attacks and protect against the unauthorized hijacking of systems, networks, and technologies.
59. Tips to Ensure the Prevention of Spoofing, Phishing, and Spam in Google Workspace
 With increasing dependency on the web and modernization of the industries moving to the cloud, data security and vulnerability to scams have become a major poin
With increasing dependency on the web and modernization of the industries moving to the cloud, data security and vulnerability to scams have become a major poin
60. Security Threats Behind Gaming
 It is not all just fun and games.
It is not all just fun and games.
61. What Are The Different Types of Malware?
 A walkthrough the different types of malware - from viruses to botnets, ransomware and phishing. Learn more and get protected!
A walkthrough the different types of malware - from viruses to botnets, ransomware and phishing. Learn more and get protected!
62. Is Remote Work Responsible for Growing Cybersecurity Threats?
 A tech story centered around the looming issues of cybersecurity, cyber attacks, and the possible solutions in today's remote working ecosystem.
A tech story centered around the looming issues of cybersecurity, cyber attacks, and the possible solutions in today's remote working ecosystem.
63. Cybersecurity 101: How to Protect Your Data From Phishing Attacks
 Never click any links or attachments in suspicious emails. If you receive a suspicious message from an organization and worry the message could be legitimate.
Never click any links or attachments in suspicious emails. If you receive a suspicious message from an organization and worry the message could be legitimate.
64. Why Phishing is Still the Most Successful Hacking Technique
 The reality of this situation is, no one can stop phishing completely. For sure, there are multiple steps a company can use anti-phishing protection.
The reality of this situation is, no one can stop phishing completely. For sure, there are multiple steps a company can use anti-phishing protection.
65. How a Team of Hackers left Stolen Phishing Credentials up for Grabs
 Attackers initiated a phishing campaign with emails that masqueraded as Xerox scan notifications, prompting users to open a malicious HTML attachment.
Attackers initiated a phishing campaign with emails that masqueraded as Xerox scan notifications, prompting users to open a malicious HTML attachment.
66. A New LinkedIn Vulnerability Exposes Jobseekers to Phishing Attacks
 The latest LinkedIn vulnerability can be exploited by con artists for massive phishing attacks, identity theft, and employment-related scams.
The latest LinkedIn vulnerability can be exploited by con artists for massive phishing attacks, identity theft, and employment-related scams.
67. How To Build a Comprehensive Cybersecurity Strategy
 Is your business equipped to take on the escalating security threats of the digital age? If not, then a smart strategy is needed. Recent reports state that half of the businesses in the United States have reported a data breach.
Is your business equipped to take on the escalating security threats of the digital age? If not, then a smart strategy is needed. Recent reports state that half of the businesses in the United States have reported a data breach.
68. Prankster Turned Gamekeeper: Phishing and Whaling with James Linton
 In 2017, James Linton was working as a digital UX (User Experience) designer, with no idea what a few pranks over the next few months would lead to. Now, he wor
In 2017, James Linton was working as a digital UX (User Experience) designer, with no idea what a few pranks over the next few months would lead to. Now, he wor
69. The Browser in the Browser (BITB) Attack: Lies, Deceit, and CSS
 “Beware the Ides of March”, they say; and we should for good reason.
“Beware the Ides of March”, they say; and we should for good reason.
70. Social Engineering: How to Be a Craftsman of the Dark Arts
 So you've been forced by your program director to take a course you didn't want to do. Let's say said course starts with 'A' and ends with 'ED'. Well you think, consoling yourself, at least I will make some new friends...
So you've been forced by your program director to take a course you didn't want to do. Let's say said course starts with 'A' and ends with 'ED'. Well you think, consoling yourself, at least I will make some new friends...
71. The Sectors Most at Risk from Remote Work and How to Secure Them
 Making the transition to a work from home arrangement has been a heavy lift for a lot of organizations.
Making the transition to a work from home arrangement has been a heavy lift for a lot of organizations.
72. 6 Tools to Help SMBs Hack Productivity in 2020
 The approach of the new year is always a great time to revisit all the awesome things your SMB has achieved and pat yourself in the back about how great things are running.
The approach of the new year is always a great time to revisit all the awesome things your SMB has achieved and pat yourself in the back about how great things are running.
73. No-Click Malware Is Here: Why Enterprises Must Prioritize Identity-First Security
 David Mahdi gives advice on how identity-first security helps prevent no-click malware attacks from succeeding.
David Mahdi gives advice on how identity-first security helps prevent no-click malware attacks from succeeding.
74. GoDaddy Hit with Widespread Redirect Hack
 Over the last few days, website owners, specifically those hosting on GoDaddy, have been experiencing strange redirects to various websites.
Over the last few days, website owners, specifically those hosting on GoDaddy, have been experiencing strange redirects to various websites.
75. Why Cybersecurity is Important For Small Businesses
 Source: Pexels
Source: Pexels
76. How a DNS Firewall Can Improve Networking Security for Your Business
 Business is driven by the well-calculated balance between spending and earning, and even the most successful companies are in a constant search for ways to cut costs. But what’s often a “nice to have” for larger companies can be a matter of survival for startups and small family businesses, who are usually only able to spend money on the essentials.
Business is driven by the well-calculated balance between spending and earning, and even the most successful companies are in a constant search for ways to cut costs. But what’s often a “nice to have” for larger companies can be a matter of survival for startups and small family businesses, who are usually only able to spend money on the essentials.
77. Three Things the Coronavirus Confirmed About Enterprise Security

78. How to Avoid Becoming a Cyber Victim
 More than 1,700 security breaches were reported in the first six months of 2021. This begs the question, are we actually safe on the internet?
More than 1,700 security breaches were reported in the first six months of 2021. This begs the question, are we actually safe on the internet?
79. A Breakdown of Today’s Phishing Epidemic
 “You’ve got mail,” doesn’t have the same ring as it used to. Today, we receive more electronic mail than ever; however, only a small amount of what’s received is expected to be there. Although securing the inbox has never been the primary purpose of electronic mail, platforms have begun taking initiatives to do so as phishing is on the rise. In the mind of a layman, terms such as “phishing,” “spam,” and “virus” are most likely interchangeable. While the terms are very similar, they are more-so layers of a cake- a domino effect. Today, phishing is on the rise, and at its peak use since its invention. The key to protecting your information from phishing is understanding it. Let’s begin with a few statistics.
“You’ve got mail,” doesn’t have the same ring as it used to. Today, we receive more electronic mail than ever; however, only a small amount of what’s received is expected to be there. Although securing the inbox has never been the primary purpose of electronic mail, platforms have begun taking initiatives to do so as phishing is on the rise. In the mind of a layman, terms such as “phishing,” “spam,” and “virus” are most likely interchangeable. While the terms are very similar, they are more-so layers of a cake- a domino effect. Today, phishing is on the rise, and at its peak use since its invention. The key to protecting your information from phishing is understanding it. Let’s begin with a few statistics.
80. How to Secure Your Crypto Wallet
 There are several reports of threats and attacks on crypto wallets every day. You must be on the lookout to keep your investment safe and secure from hackers.
There are several reports of threats and attacks on crypto wallets every day. You must be on the lookout to keep your investment safe and secure from hackers.
81. How to Avoid Online Phishing Scams this Holiday Season
 Despite billions of dollars being invested in cybersecurity technologies, the use of look-alike domains and counterfeit websites to trick people with phishing scams is on the rise. 🤷♂️
Despite billions of dollars being invested in cybersecurity technologies, the use of look-alike domains and counterfeit websites to trick people with phishing scams is on the rise. 🤷♂️
82. "Humans are the weakest link in cybersecurity"
 New Phishing Techniques and How to Avoid Them
New Phishing Techniques and How to Avoid Them
83. Phone Scams: What Is Vishing And How You Can Avoid It
 The attack combines a one-on-one phone call with credible-looking phishing sites where the user is required to fill in their credentials and their MFA codes.
The attack combines a one-on-one phone call with credible-looking phishing sites where the user is required to fill in their credentials and their MFA codes.
84. CIOs Need to Prioritize Digital Transformation and Cybersecurity in Their 2022 Budgets
 Digital transformation cannot be jettisoned for cybersecurity, a delicate balance must be reached by CIOs in their 2022 budgets for the two to co-exist.
Digital transformation cannot be jettisoned for cybersecurity, a delicate balance must be reached by CIOs in their 2022 budgets for the two to co-exist.
85. Be 100% Safe On The Internet Using These Strategies
 The Internet is full of opportunities, useful information, entertainment, and dangers as well. To protect yourself from the latter, you need to follow certain safety rules. Read on to learn how to properly use a home or public Wi-Fi to avoid dangerous malware and protect personal data, and what is the role of nect MODEM in helping you do so.
The Internet is full of opportunities, useful information, entertainment, and dangers as well. To protect yourself from the latter, you need to follow certain safety rules. Read on to learn how to properly use a home or public Wi-Fi to avoid dangerous malware and protect personal data, and what is the role of nect MODEM in helping you do so.
86. Phishing 101: A Beginner's Guide on Phishing Attacks
 You receive an email asking for your bank details or credit card information. It's urgent, but read this so that you do not become a victim of phishing.
You receive an email asking for your bank details or credit card information. It's urgent, but read this so that you do not become a victim of phishing.
87. What's A Spear-Phishing Attack and To Protect Yourself From It
 Do you know what is the most favorite methodology of hackers to break into your security? These are not highly sophisticated zero-days or Advanced Persistent Threats (APTs).
Do you know what is the most favorite methodology of hackers to break into your security? These are not highly sophisticated zero-days or Advanced Persistent Threats (APTs).
Thank you for checking out the 87 most read stories about Phishing on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

