Let's learn about Passwords via these 64 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
1. How to Crack a Password Using Hashcat
 In this article, I discuss the best ways to crack passwords.
In this article, I discuss the best ways to crack passwords.
2. Exposing Secrets on GitHub: What to Do After Leaking Credentials and API Keys
 As a developer, if you have discovered that you have just exposed a sensitive file or secrets to a public git repository, there are some very important steps to follow.
As a developer, if you have discovered that you have just exposed a sensitive file or secrets to a public git repository, there are some very important steps to follow.
3. How Password Managers Can Protect You From Phishing
 Password managers are a convenient way to use strong, unique passwords everywhere. Another good thing about password managers is that they help protect you from malicious websites that attempt to "phish" passwords.
Password managers are a convenient way to use strong, unique passwords everywhere. Another good thing about password managers is that they help protect you from malicious websites that attempt to "phish" passwords.
4. PSA: LastPass Does Not Encrypt Everything In Your Vault
 As a software engineer and long time LastPass user, I’ve always been an advocate of password managers. With data breaches becoming more and more common these days, it’s critical that we take steps to protect ourselves online. However, over the past year LastPass has made some decisions that have made me question their motives and ultimately has recently caused them to lose my business.
As a software engineer and long time LastPass user, I’ve always been an advocate of password managers. With data breaches becoming more and more common these days, it’s critical that we take steps to protect ourselves online. However, over the past year LastPass has made some decisions that have made me question their motives and ultimately has recently caused them to lose my business.
5. Implementing 2FA: How Time-Based One-Time Password Actually Works [With Python Examples]
 If you care about your security on the web, you probably use a Two-Factor authentication (2FA) method to protect your accounts. There are various 2FA methods available out there, a combination of password + fingerprint, for example, is one of them. However, since not so many people have a fingerprint reader available all the time, one of the most popular 2FA methods today is to use an authenticator app on your cellphone to generate a temporary password that expires within a minute or even less. But, how does this temporary password, called Time-Based One-Time Password (TOTP) works, and how can I implement that on my own service?
If you care about your security on the web, you probably use a Two-Factor authentication (2FA) method to protect your accounts. There are various 2FA methods available out there, a combination of password + fingerprint, for example, is one of them. However, since not so many people have a fingerprint reader available all the time, one of the most popular 2FA methods today is to use an authenticator app on your cellphone to generate a temporary password that expires within a minute or even less. But, how does this temporary password, called Time-Based One-Time Password (TOTP) works, and how can I implement that on my own service?
6. Build your own User-friendly Cross-platform Password Manager
 I use a local password manager on my computer: I just stick with a password, which is the only password I memorize.
I use a local password manager on my computer: I just stick with a password, which is the only password I memorize.
7. How To Create Secure Registration Flow with PHP and Password Hashing
 Building a secure user registration form with PHP seems like a scary task. How do I protect myself from MySQL injection and other methods of hacking. Surprisingly, with only a few steps and precautions, you can greatly reduce the chance of success for attacks.
Building a secure user registration form with PHP seems like a scary task. How do I protect myself from MySQL injection and other methods of hacking. Surprisingly, with only a few steps and precautions, you can greatly reduce the chance of success for attacks.
8. Why Your Browser's Built-In Password Manager Isn't Enough
 You may ask, "My web browser already has a built-in password manager, why do I need to install a new one?" There's actually a number of good reasons to install a password manager.
You may ask, "My web browser already has a built-in password manager, why do I need to install a new one?" There's actually a number of good reasons to install a password manager.
9. The Elimination of Cybersecurity's Status Quo – Passwords
 According to a report by the World Economic Forum, in the year 2020, cybercrime cost the world economy a staggering $2.9million every minute. According to another report, every single day, enterprises lose about 5 million records containing sensitive data due to vulnerability in their system or a human factor failure.
According to a report by the World Economic Forum, in the year 2020, cybercrime cost the world economy a staggering $2.9million every minute. According to another report, every single day, enterprises lose about 5 million records containing sensitive data due to vulnerability in their system or a human factor failure.
10. HMAC and MAC Explained: How To Build Secure Authentication With JWTs
 HMACs and MACs are authentication codes and are often the backbone of JWT authentication systems. Let's take a look at how they work!
HMACs and MACs are authentication codes and are often the backbone of JWT authentication systems. Let's take a look at how they work!
11. Security.org Knows 15 Million Americans Will Be Buying Cryptocurrency in the Next Year
 Twelve years after the Bitcoin network came into existence in 2009, we asked nearly 1,300 U.S adults about their familiarity, ownership, and confidence in cryptocurrencies, from Dogecoin to Ethereum, and everything in between. One highlight? Nearly 15 million Americans plan to purchase crypto for the first time in the next year.
Twelve years after the Bitcoin network came into existence in 2009, we asked nearly 1,300 U.S adults about their familiarity, ownership, and confidence in cryptocurrencies, from Dogecoin to Ethereum, and everything in between. One highlight? Nearly 15 million Americans plan to purchase crypto for the first time in the next year.
12. Cryptography Trends and News for 2020
 Quantum Computing
Quantum Computing
13. An Introduction to Key Derivation Functions: Argon2, Scrypt, and PBKDF2
 A key derivation function, or KDF, derives one or many secret keys from a secret value. Therefore, If you've ever needed to store a password in a database or create a private key from a password, you may have used a KDF.
A key derivation function, or KDF, derives one or many secret keys from a secret value. Therefore, If you've ever needed to store a password in a database or create a private key from a password, you may have used a KDF.
14. How Big Tech is Working Towards a Password-Free Future
 A 2019 research conducted by HYPR showed that 78% of people forgot their passwords and required a reset within the last 90 days. Passwords aren’t just difficult to manage, they are inconvenient, insecure, and expensive because passwords are just too easy to guess, hack or intercept and what’s more, the legacy of password reuse is leading to constant attack and account vulnerabilities.
A 2019 research conducted by HYPR showed that 78% of people forgot their passwords and required a reset within the last 90 days. Passwords aren’t just difficult to manage, they are inconvenient, insecure, and expensive because passwords are just too easy to guess, hack or intercept and what’s more, the legacy of password reuse is leading to constant attack and account vulnerabilities.
15. Password Managers Should be A Mandatory Part of Everyone’s Digital Life

16. How Machine Learning Prevents Identity Theft

17. The Importance of Proper Password Security in 2022
 A look at the importance of proper password security in 2022
A look at the importance of proper password security in 2022
18. How to Protect Folders And Files in Windows using Passwords
 Sometimes, we need to apply a bit of extra protection to the data on our computers. We might want to protect our tax records from prying eyes, or lock away business plans from our competitors. Or we might just want to ensure that any children with access to our device can't access inappropriate content.
Sometimes, we need to apply a bit of extra protection to the data on our computers. We might want to protect our tax records from prying eyes, or lock away business plans from our competitors. Or we might just want to ensure that any children with access to our device can't access inappropriate content.
19. 7 Ways How Hackers Crack Your Passwords
 DISCLAIMER: The article is intended to be used and must be used for informational purposes only.
DISCLAIMER: The article is intended to be used and must be used for informational purposes only.
20. Passwords Are a Weak Security Link and Stolen Credentials Is Big Business
 Stolen credentials are big business thanks to poor password management from users and even nefarious actors on the Dark Web creating demand for stolen passwords
Stolen credentials are big business thanks to poor password management from users and even nefarious actors on the Dark Web creating demand for stolen passwords
21. Mechanism of Password Protection
 While there are security risks associated with the use of password protection, it is very important to know that there have been cases of stolen passwords.
While there are security risks associated with the use of password protection, it is very important to know that there have been cases of stolen passwords.
22. Password Security in 2022 — A Complete Guide
 A comprehensive guide to password security for all IT managers (and everyone else!). Learn why it is important, the risks of insecure passwords and how you can
A comprehensive guide to password security for all IT managers (and everyone else!). Learn why it is important, the risks of insecure passwords and how you can
23. How Much Has Your Password Grown Up With You?
 If you are growing up with technology, your password should be grown up too.
If you are growing up with technology, your password should be grown up too.
24. From Passwords to Passwordless Authentication
 Passwordless authentication is gradually replacing the password-based authentication practice. The CIA triad of Cybersecurity is changing rapidly. Learn how.
Passwordless authentication is gradually replacing the password-based authentication practice. The CIA triad of Cybersecurity is changing rapidly. Learn how.
25. Common Web Security Vulnerabilities
 In the movies, hacking is like fast keyboard typing and hitting the Enter but in the real world, hackers find and exploit vulnerabilities to hack websites.
In the movies, hacking is like fast keyboard typing and hitting the Enter but in the real world, hackers find and exploit vulnerabilities to hack websites.
26. Configure Your Linux With Passwordless Sudo For A Specific User
 Linux follows tough rules when it comes to permission. Being a root user or sudo user gives you permission to do almost anything which normal user don’t have. Several commands need sudo keyword to run and each time you try to run sudo, Linux asks for a password, today we will configure a passwordless sudo.
Linux follows tough rules when it comes to permission. Being a root user or sudo user gives you permission to do almost anything which normal user don’t have. Several commands need sudo keyword to run and each time you try to run sudo, Linux asks for a password, today we will configure a passwordless sudo.
27. Saving Passwords with Relative Security [A Guide for Dummies]
 There is a mystical aura around password creation. Some kind of occult knowledge reached only by the distant cryptographic hermits who ascended to nirvana after decades of meditation on the Patagonian glaciers and liters of instant coffee. In this article, we will try to translate a few drops of this ancient wisdom so that we, mere mortals, have secure accounts to store pictures of cats and e-books that we will never read.
There is a mystical aura around password creation. Some kind of occult knowledge reached only by the distant cryptographic hermits who ascended to nirvana after decades of meditation on the Patagonian glaciers and liters of instant coffee. In this article, we will try to translate a few drops of this ancient wisdom so that we, mere mortals, have secure accounts to store pictures of cats and e-books that we will never read.
28. The Growing Cyber Risks of a Work From Home Workforce
 A recent Threatpost poll found that 40 percent of the companies transitioning to WFH experienced a spike in cyberattacks. The survey concluded that patching and updating are among the top challenges for employees when securing their remote footprint.
A recent Threatpost poll found that 40 percent of the companies transitioning to WFH experienced a spike in cyberattacks. The survey concluded that patching and updating are among the top challenges for employees when securing their remote footprint.
29. How Password Issues Plague Help Desk Calls
 A article on passwords, password security, and how businesses can train employees to handle passwords themselves.
A article on passwords, password security, and how businesses can train employees to handle passwords themselves.
30. How to Go Passwordless with idemeum JavaScript SDK
 One SDK, 10 minutes of your time, and you can bootstrap passwordless auth for your single-page app. With one SDK, you get all the flows: one-click, WebAuthn, an
One SDK, 10 minutes of your time, and you can bootstrap passwordless auth for your single-page app. With one SDK, you get all the flows: one-click, WebAuthn, an
31. How Hackers Can Brute-Force Passwords And Find A Correct Key?
 Brute force attackers guess passwords, passphrases, and private keys in an attempt to eventually get the right answer and crack the security of a system, but how do they know when they have the right key?
Brute force attackers guess passwords, passphrases, and private keys in an attempt to eventually get the right answer and crack the security of a system, but how do they know when they have the right key?
32. 3 Ways to Crack WinRAR Password Protected Files

33. GitHub Security: How To Protect Your Company From Credential Leakage
34. How to Protect Your Instagram Account from Being Hacked

35. 63% of data breaches exploit weak credentials - Cybersecurity to support remote workers
 A look at how to update the old passwords model to support the future of distributed work.
A look at how to update the old passwords model to support the future of distributed work.
36. Not All Password Managers Are Created Equal: Which is the Best?
 Web-based password managers have emerged as a response to the proliferation of web applications.
Web-based password managers have emerged as a response to the proliferation of web applications.
37. Death, Taxes, and Password Negligence: The Inevitability of Pwned Passwords
 The internet security slang pwned-- pronounced ‘poned’-- is mainly used to indicate administrative control over someone’s computer account or computer. A password that has been pwned is one that has been compromised in some kind of breach, and it means that it’s no longer safe to use.
The internet security slang pwned-- pronounced ‘poned’-- is mainly used to indicate administrative control over someone’s computer account or computer. A password that has been pwned is one that has been compromised in some kind of breach, and it means that it’s no longer safe to use.
38. Express.js Integration Guide for Passwordless Authentication with DID.app
 Just want the code? Find this example on github
Just want the code? Find this example on github
39. What Could Have Prevented 2020's Massive Twitter Hack?
 Attacks and account take-overs like the recent Twitter hack are completely avoidable. Enterprises must implement biometric multi-factor authentication to ensure that only the right users have access to the right systems at all times. If they don’t, users will continue being vulnerable to hacks and scams.
Attacks and account take-overs like the recent Twitter hack are completely avoidable. Enterprises must implement biometric multi-factor authentication to ensure that only the right users have access to the right systems at all times. If they don’t, users will continue being vulnerable to hacks and scams.
40. How Passwords Get Hacked
 Fernando Corbato pioneered the first computer password in 1960, being used as a personal point of entry on MIT's Compatible Time-Sharing System (CTSS). Just 2 years later, the CTSS was hacked and has been inspiring hackers ever since. There have been immense technological advancements since 1962 - how is it that today's hackers can get through 2-step authentication, biometrics, and security questions? Cryptographers predict a future that moves beyond passwords, but the issue seems to lie between cybersecurity and human nature.
Fernando Corbato pioneered the first computer password in 1960, being used as a personal point of entry on MIT's Compatible Time-Sharing System (CTSS). Just 2 years later, the CTSS was hacked and has been inspiring hackers ever since. There have been immense technological advancements since 1962 - how is it that today's hackers can get through 2-step authentication, biometrics, and security questions? Cryptographers predict a future that moves beyond passwords, but the issue seems to lie between cybersecurity and human nature.
41. Three Things the Coronavirus Confirmed About Enterprise Security

42. The Anatomy of A Strong Passphrase That Is Easy To Remember
 We all have hundreds of online accounts. Ideally, as many of those accounts as possible have unique passwords. Unique passwords however present a difficult problem: No one can remember hundreds of strong passwords.
We all have hundreds of online accounts. Ideally, as many of those accounts as possible have unique passwords. Unique passwords however present a difficult problem: No one can remember hundreds of strong passwords.
43. MFA Vs. 2FA: Which Is Better And More Secure

44. The Business Costs of Compromised Passwords
 Passwords and Their Ability to Bring Down Even the Largest of Enterprises
Passwords and Their Ability to Bring Down Even the Largest of Enterprises
45. Great Methods To Create A Password File To Prevent Brute-Force Attacks
 Brute-forcing a really important method that a hacker or a pentester must be aware of and he will use in various places.
Brute-forcing a really important method that a hacker or a pentester must be aware of and he will use in various places.
46. Authentication Vs. Authorization [Infographic]
 In online protection systems, authentication and authorization play an important role. They confirm the user's identity and grant your website or application access. In order to decide which combination of web tools best fits your security needs, it is important that you notice their differences.
In online protection systems, authentication and authorization play an important role. They confirm the user's identity and grant your website or application access. In order to decide which combination of web tools best fits your security needs, it is important that you notice their differences.
47. A Guide to Password Hashing: How to Keep your Database Safe
 Hashing algorithms are one-way functions. They take any string and turn it into a fixed-length “fingerprint” that is unable to be reversed. This means that if your data in your database is compromised, the hacker cannot get the user’s passwords if they were hashed well because at no point were they ever stored on the drive without being in their hashed form.
Hashing algorithms are one-way functions. They take any string and turn it into a fixed-length “fingerprint” that is unable to be reversed. This means that if your data in your database is compromised, the hacker cannot get the user’s passwords if they were hashed well because at no point were they ever stored on the drive without being in their hashed form.
48. Introduction to Cryptography: Vigenère Cipher [Part 2]
 Hi again and welcome back to part 2 of the basic cryptography. Previously we discuss about what is cryptography and how fundamental and ancient problem it is in communication science. We talk about ceaser's cipher and how easy it is to break. We also talk about Substitution Cipher which was slight improvement to Ceaser' cipher but can easily be cracked using Frequency analysis technique.
Hi again and welcome back to part 2 of the basic cryptography. Previously we discuss about what is cryptography and how fundamental and ancient problem it is in communication science. We talk about ceaser's cipher and how easy it is to break. We also talk about Substitution Cipher which was slight improvement to Ceaser' cipher but can easily be cracked using Frequency analysis technique.
49. A Very Basic Intro to Hash Functions: SHA-256, MD-5, etc
 This is going to be a basic introduction to hash functions. I will assume most of my audience is here to gain an understanding of why hash functions are used and the basic idea of why they work. My goal is to explain it in a general sense, I will be omitting proofs and implementation details and instead focusing on the high-level principles.
This is going to be a basic introduction to hash functions. I will assume most of my audience is here to gain an understanding of why hash functions are used and the basic idea of why they work. My goal is to explain it in a general sense, I will be omitting proofs and implementation details and instead focusing on the high-level principles.
50. Salts and Hashes

51. Data Breaches: Why You Should Never Share Your Passwords
 Data Breaches: Why You Should Never Share Your Passwords
Data Breaches: Why You Should Never Share Your Passwords
52. Do Passwordless Technologies Have an Impact on Cybersecurity?
 Contrary to popular belief, traditional passwords are not the best way to protect sensitive information on our digital devices.
Contrary to popular belief, traditional passwords are not the best way to protect sensitive information on our digital devices.
53. How to Find Your Saved WiFi Password on iPhone and iPad
 Learn how to quickly find saved WiFi passwords on your iPhone. Our simple guide helps you retrieve forgotten passwords in just a few steps.
Learn how to quickly find saved WiFi passwords on your iPhone. Our simple guide helps you retrieve forgotten passwords in just a few steps.
54. Protecting Your Data Online Using Strong Passwords and Two-Factor Authentication: A Guide
 There's a growing need for better online security, with strong passwords and two-factor authentication. As more of our daily life moves online, more of our personal information is also being stored on the web, along with access details for our personal bank accounts and confidential work data. With cyberattacks on the rise, all of this information needs to be protected from unauthorized access by hackers.
There's a growing need for better online security, with strong passwords and two-factor authentication. As more of our daily life moves online, more of our personal information is also being stored on the web, along with access details for our personal bank accounts and confidential work data. With cyberattacks on the rise, all of this information needs to be protected from unauthorized access by hackers.
55. The Only 15 Apps I Downloaded and Keep on My MacBook 👨💻
 Today we'll be looking at my personal top 15 Mac apps. I'm actually quite a minimalist in installing and keeping apps, so these 15 are the only "extra" apps I'm using on my device.
Today we'll be looking at my personal top 15 Mac apps. I'm actually quite a minimalist in installing and keeping apps, so these 15 are the only "extra" apps I'm using on my device.
56. The Future of Authentication

57. Web Auth Standard: Guide to Web Authentication API
 Secure context
This feature is available only in secure contexts (HTTPS), in some or all supporting browsers.
Secure context
This feature is available only in secure contexts (HTTPS), in some or all supporting browsers.
58. BIP 32 Watch-Only Wallets
 Bitcoin improvement proposal 32 is, in my opinion, one of the most important BIPs we have. (Thanks Peter Wuille!) BIP 32 gave us Hierarchical Deterministic Wallets. That is, the ability to create a tree of keys from a single seed.
Bitcoin improvement proposal 32 is, in my opinion, one of the most important BIPs we have. (Thanks Peter Wuille!) BIP 32 gave us Hierarchical Deterministic Wallets. That is, the ability to create a tree of keys from a single seed.
59. What devs need to know about Encoding / Encryption / Hashing / Salting / Stretching
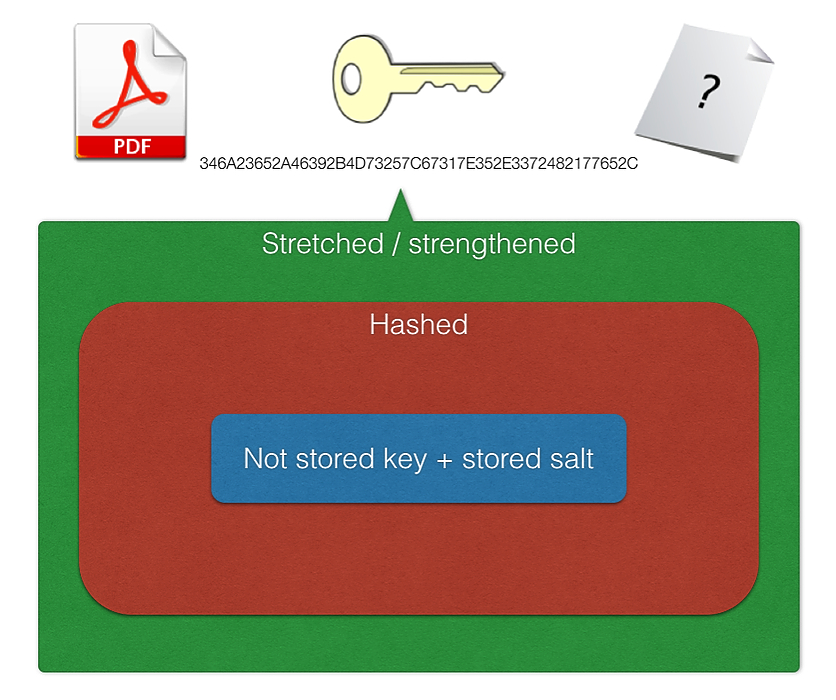 This is a typical exchange about encryption with someone willing to learn.
This is a typical exchange about encryption with someone willing to learn.
60. Passwords Suck: Here Are 4 Ways We Can Fix Them
 Passwords are a critical part of cybersecurity that individuals and businesses use every day.
Passwords are a critical part of cybersecurity that individuals and businesses use every day.
61. Things You Must Know About git-crypt To Successfully Protect Your Secret Data
 Many software projects use secrets - usually, keys to external APIs or credentials to access an external resource such as a database. Your application needs these keys at runtime, so you need to be able to provide them when you deploy your application, or as a step in preparing your deployment environment.
Many software projects use secrets - usually, keys to external APIs or credentials to access an external resource such as a database. Your application needs these keys at runtime, so you need to be able to provide them when you deploy your application, or as a step in preparing your deployment environment.
62. 5 Cybersecurity Mistakes You Probably Make Every Day (and How to Fix Them)
 A look at common cybersecurity mistakes that you are likely doing every day, and what you can to prevent them.
A look at common cybersecurity mistakes that you are likely doing every day, and what you can to prevent them.
63. Public Key Cryptography: RSA keys

64. 7 Ways to Protect Your Company from Insecure Credentials
 Verizon’s 2020 DBIR reports that more than 80% of hacking-related breaches involve brute force or the use of lost or stolen credentials— here’s how to prevent weak or compromised credentials from being used in your company’s applications and network
Verizon’s 2020 DBIR reports that more than 80% of hacking-related breaches involve brute force or the use of lost or stolen credentials— here’s how to prevent weak or compromised credentials from being used in your company’s applications and network
Thank you for checking out the 64 most read stories about Passwords on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

