Let's learn about Data Privacy via these 379 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
“If you put a key under the mat for the cops, a burglar can find it, too. Criminals are using every technology tool at their disposal to hack into people’s accounts. If they know there’s a key hidden somewhere, they won’t stop until they find it.” – Tim Cook
1. OIP: The Protocol that’s Taking on the Google Search Index Monopoly
 Google’s closed search index makes their control indomitable in the space and shields them from scrutiny. OIP wants to change that.
Google’s closed search index makes their control indomitable in the space and shields them from scrutiny. OIP wants to change that.
2. Mutual Human Authorization: A New Standard in Data Privacy
 Mutual Human Authorization is a digital communication protocol that SharePass is pioneering to help address persistent data privacy and security gaps.
Mutual Human Authorization is a digital communication protocol that SharePass is pioneering to help address persistent data privacy and security gaps.
3. What Is the Best Browser for Your Privacy?
 How to pick out the right web browser when you're focused on privacy and functionality.
How to pick out the right web browser when you're focused on privacy and functionality.
4. Google’s Data-Hungry Ecosystem is Threatening Your Privacy. Here’s How.
 Google rewards data brokers for violating your privacy. Understand the hidden relationship between the #1 search engine and information brokers.
Google rewards data brokers for violating your privacy. Understand the hidden relationship between the #1 search engine and information brokers.
5. The Facebook Business Model Might Die
 This article is in reply to "How Much Internet Regulation Does Facebook Support?"
This article is in reply to "How Much Internet Regulation Does Facebook Support?"
6. AI and Personal Data: Does GPT-3 Know Anything About Me?
 What do AI's know about you and can you opt out? Large Language Models are going to be used in search engine outputs and it's time to prepare!
What do AI's know about you and can you opt out? Large Language Models are going to be used in search engine outputs and it's time to prepare!
7. 4 Ways Cities Are Utilizing Data for Public Safety
 Cities have been using data for public safety for years. What new technology is emerging in public safety, and how does it affect you?
Cities have been using data for public safety for years. What new technology is emerging in public safety, and how does it affect you?
8. Why You Should Never Store Passwords in Web Browsers

9. Analyzing the 12/31/2022 Slack Security Incident
 On December 31, 2022, Slack reported a security breach that affected some of its customers.
On December 31, 2022, Slack reported a security breach that affected some of its customers.
10. Why Private Search Engines Are The Future...
 Private search engines aren't just for people wearing tinfoil hats anymore. Over the years these search engines have improved their search results and added new features to make the experience better for their users.
Private search engines aren't just for people wearing tinfoil hats anymore. Over the years these search engines have improved their search results and added new features to make the experience better for their users.
11. Don't Let Them Fool You: Manipulative Strategies Used By Big Tech Companies To Sell You Stuff
 Do you know how your apps work? Are you aware of what tech companies are doing in the back with your data? And what’s more revealing: do you know which of your action are actually influenced by those apps? When you take a trip with Uber, buy stuff on Amazon, or watch a movie on Netflix: when are you consciously deciding and when are you being heavily influenced?
Do you know how your apps work? Are you aware of what tech companies are doing in the back with your data? And what’s more revealing: do you know which of your action are actually influenced by those apps? When you take a trip with Uber, buy stuff on Amazon, or watch a movie on Netflix: when are you consciously deciding and when are you being heavily influenced?
12. Orchestrating Identity in Web3.0
 Identity needs a major re-think for Web 3.0. We need private and effective, dynamic authorization - but no, I am not talking about blockchain.
Identity needs a major re-think for Web 3.0. We need private and effective, dynamic authorization - but no, I am not talking about blockchain.
13. Privacy Enhancing Technologies: Top 3 Use Cases
 Security and risk management leaders can apply privacy-enhancing tech in AI modelling, cross-border data transfers, and data analytics to manage constraints.
Security and risk management leaders can apply privacy-enhancing tech in AI modelling, cross-border data transfers, and data analytics to manage constraints.
14. Facebook Has Your Children's Info Thanks to This Hospital Network
 One of the largest pediatric networks in the country was sending personal information about children and their parents to Facebook, The Markup found.
One of the largest pediatric networks in the country was sending personal information about children and their parents to Facebook, The Markup found.
15. Is WhatsApp Safe?
 WhatsApp is the most popular messenger owned by Facebook. According to the official stats, the number of WhatsApp active users has reached 1 billion in 2020. Just imagine, approximately 65 million messages are sent via this social app daily. Since the app is so popular, it’s very attractive for hackers. In this article, I’ll tell you about the major WhatsApp security threats, which will help you protect your chats and shared media from hackers, WhatsApp spy apps, and keylogging software.
WhatsApp is the most popular messenger owned by Facebook. According to the official stats, the number of WhatsApp active users has reached 1 billion in 2020. Just imagine, approximately 65 million messages are sent via this social app daily. Since the app is so popular, it’s very attractive for hackers. In this article, I’ll tell you about the major WhatsApp security threats, which will help you protect your chats and shared media from hackers, WhatsApp spy apps, and keylogging software.
16. Decentralized Platforms: An Answer to EU Digital Markets and the DSA
 EU targets digital markets and services with new restrictive legislation, could it be that decentralized digital markets and services are compliant by default?
EU targets digital markets and services with new restrictive legislation, could it be that decentralized digital markets and services are compliant by default?
17. Why your Company Needs a Virtual Chief Information Security Officer
 Why should your company hire a virtual CISO to increase security?
Why should your company hire a virtual CISO to increase security?
18. Bringing Back Data Ownership to Humans With Decentralizion
 Are we ready as humans to take the data ownership back? Here is a use case for you.
Are we ready as humans to take the data ownership back? Here is a use case for you.
19. The ZEE5 User Data Leak That The Media Didn't Report On

20. How Does Ransomware Work? A Step-by-Step Breakdown

21. Protecting Your Online Privacy: 7 Simple Steps You Can Take Today
 What people wish to share is their prerogative, yet to unconsciously give away your private information is very different to making an active choice.
What people wish to share is their prerogative, yet to unconsciously give away your private information is very different to making an active choice.
22. Why Linux-Based Brands Are So Desirable
 I'll start off by dating myself... it was the year 2000. I was in college and the brand new Mini Disk MP3 player had just come out. Superior audio to CD's and the ability to hold hundreds of songs on 1 little disk. Being a broke college kid, it took me about 6 months to make the purchase. Just when I got used to looking cool with my MD player, a wild flash of cool came across the analog airways via a commercial from a company that was only recently regaining its cool with a crappy multicolor desktop PC called the iMac. Of course, I'm talking about Apple. The product was the iPod. I was defeated and nearly threw away my MD player on the spot.
I'll start off by dating myself... it was the year 2000. I was in college and the brand new Mini Disk MP3 player had just come out. Superior audio to CD's and the ability to hold hundreds of songs on 1 little disk. Being a broke college kid, it took me about 6 months to make the purchase. Just when I got used to looking cool with my MD player, a wild flash of cool came across the analog airways via a commercial from a company that was only recently regaining its cool with a crappy multicolor desktop PC called the iMac. Of course, I'm talking about Apple. The product was the iPod. I was defeated and nearly threw away my MD player on the spot.
23. 2 Ways to Access WhatsApp Conversations
 In this article, you'll find the best ways to hack WhatsApp chats including syncing the app with the web version or exporting a txt file of the chat.
In this article, you'll find the best ways to hack WhatsApp chats including syncing the app with the web version or exporting a txt file of the chat.
24. Millennials Need Decentralized Social Media - Here's Why
 It’s time for decentralized social apps to take over
It’s time for decentralized social apps to take over
25. How to Activate Disappearing Messages on Instagram
 In this post, you will get complete knowledge of how to hide Instagram messages without deleting them.
In this post, you will get complete knowledge of how to hide Instagram messages without deleting them.
26. Data Sovereignty Comes Closer To Reality For EU Residents
 Data privacy, security, and sovereignty issues have gained significant attention over recent years.
Data privacy, security, and sovereignty issues have gained significant attention over recent years.
27. 4 Tips To Become A Successful Entry-Level Data Analyst
 Companies across every industry rely on big data to make strategic decisions about their business, which is why data analyst roles are constantly in demand.
Companies across every industry rely on big data to make strategic decisions about their business, which is why data analyst roles are constantly in demand.
28. Handle Sensitive Data Securely with Skyflow
 You don’t need to be a data privacy expert in order to implement best practices.
You don’t need to be a data privacy expert in order to implement best practices.
29. What to Consider When Choosing Between Self-Hosting and Cloud
 One of the biggest challenges of cloud computing is the issue of data sovereignty and how it affects business based on the individual countries regulations.
One of the biggest challenges of cloud computing is the issue of data sovereignty and how it affects business based on the individual countries regulations.
30. iOS 14 Privacy Features: It's Time to Rethink Advertising & Marketing Strategies
 Two of the world’s most powerful tech titans are on course for a collision.
Two of the world’s most powerful tech titans are on course for a collision.
31. End-to-End Encryption Basics

32. Current Web3 Development is Similar to the Internet Boom of the Late 90s
 SIMBA Chain started working on its first blockchain projects for organizations like the US Navy, Boeing, and other defence contractors.
SIMBA Chain started working on its first blockchain projects for organizations like the US Navy, Boeing, and other defence contractors.
33. How to Improve Data Quality in 2022
 Poor quality data could bring everything you built down. Ensuring data quality is a challenging but necessary task. 100% may be too ambitious, but here's what y
Poor quality data could bring everything you built down. Ensuring data quality is a challenging but necessary task. 100% may be too ambitious, but here's what y
34. TikTok: A Ticking Time Bomb?
 One of the most popular apps of 2019, TikTok ruled the download charts in both the Android and Apple markets. Having more than 1.5 billion downloads and approximately half a billion monthly active users, TikTok definitely has access to a trove of users. With that large user base comes a hidden goldmine: their data.
One of the most popular apps of 2019, TikTok ruled the download charts in both the Android and Apple markets. Having more than 1.5 billion downloads and approximately half a billion monthly active users, TikTok definitely has access to a trove of users. With that large user base comes a hidden goldmine: their data.
35. Securing Sensitive Customer Information in the Age of Data
 Featured Image Source: Pixabay
Featured Image Source: Pixabay
36. Microsoft SEAL and the Dawn of Homomorphic Encryption
 Homomorphic encryption is making its way from academia to production use cases. Kick the tires on it with C# and a privacy minded fitness tracker.
Homomorphic encryption is making its way from academia to production use cases. Kick the tires on it with C# and a privacy minded fitness tracker.
37. Why Cybersecurity Must Start with Company Culture
 Cyberattacks, though frequently thought of as ‘sophisticated’, are often anything but. They are actually surprisingly straightforward and mostly financially motivated. We often see the media reporting on large-scale cyberattacks that have managed to breach complex security protocols, at a substantial financial cost to the business involved.
Cyberattacks, though frequently thought of as ‘sophisticated’, are often anything but. They are actually surprisingly straightforward and mostly financially motivated. We often see the media reporting on large-scale cyberattacks that have managed to breach complex security protocols, at a substantial financial cost to the business involved.
38. Humans As Data Points: Here's Why You Need Better Privacy
 “Arguing that you don't care about the right to privacy because you have nothing to hide is no different than saying you don't care about free speech because you have nothing to say." - Edward Snowden
“Arguing that you don't care about the right to privacy because you have nothing to hide is no different than saying you don't care about free speech because you have nothing to say." - Edward Snowden
39. Is it Safe to Store Credit Card Information on Google Chrome?
 Do not store your credit card information on Google Chrome! This article discusses why it's not safe to store your credit card information on Google chrome.
Do not store your credit card information on Google Chrome! This article discusses why it's not safe to store your credit card information on Google chrome.
40. Opinion: There’s Nothing Wrong With Being Tracked by Google
 Why you should be happy about companies collecting your data.
Why you should be happy about companies collecting your data.
41. Technical Approaches to Keep Health Data Secure
 The use of technology in the healthcare industry increases, so it is more important than ever to concentrate on securing patient data.
The use of technology in the healthcare industry increases, so it is more important than ever to concentrate on securing patient data.
42. Smart Cities: Cybersecurity in the Era of IoT
 A smart city is representative of urbanization in the digital world. The infrastructure of smart cities is built on embedded Internet of Things (IoT) technology. The smart city promises new opportunities and growth in the urban world. These opportunities include better connectivity, productivity, agility, and innovation. However, it is a known fact that with opportunities come challenges.
A smart city is representative of urbanization in the digital world. The infrastructure of smart cities is built on embedded Internet of Things (IoT) technology. The smart city promises new opportunities and growth in the urban world. These opportunities include better connectivity, productivity, agility, and innovation. However, it is a known fact that with opportunities come challenges.
43. FinTech Security Needs To Be Taken More Seriously Than It Is
 Cyberattacks the biggest barrier to financial innovation
Cyberattacks the biggest barrier to financial innovation
44. Privacy protection and how Nym can help
 Privacy is a broad term, but, briefly speaking, it is the ability to share what you want with whom you want and how you want to do it. So, privacy is about the
Privacy is a broad term, but, briefly speaking, it is the ability to share what you want with whom you want and how you want to do it. So, privacy is about the
45. Understanding the Zero-Knowledge Proof Method
 One of the biggest advantages of blockchain technology is the degree of information transparency it offers.
One of the biggest advantages of blockchain technology is the degree of information transparency it offers.
46. How can we make social media better platforms?
 Cloud has some benefits and some downsides. Hard Drives also have some benefits and some downside. Blockchain combines the both, leaving out the downside
Cloud has some benefits and some downsides. Hard Drives also have some benefits and some downside. Blockchain combines the both, leaving out the downside
47. Businesses are Tackling Data Privacy Restrictions with Hybrid Cloud
 If a business deals with personal data, it inevitably faces data protection and privacy legislation issues. Here is how the hybrid cloud helps address those.
If a business deals with personal data, it inevitably faces data protection and privacy legislation issues. Here is how the hybrid cloud helps address those.
48. Useful Digital Tools for Nonprofit Attorneys
 We've identified some potential pain points for nonprofit attorneys, where a lack of effective tech can slow down processes or leave holes in security practice.
We've identified some potential pain points for nonprofit attorneys, where a lack of effective tech can slow down processes or leave holes in security practice.
49. What Apple And Spotify Know About Me
 Unsurprisingly, the data that our apps have collected about us is both impressive and concerning, though it can be very interesting to review and explore it.
Unsurprisingly, the data that our apps have collected about us is both impressive and concerning, though it can be very interesting to review and explore it.
50. Why There is No Digital Future Without Blockchain
 Blockchain will transform the internet and the way we use it. From digital freedom to data protection; the reasons are becoming more important every day.
Blockchain will transform the internet and the way we use it. From digital freedom to data protection; the reasons are becoming more important every day.
51. Cloud Data Security and the Need for Confidential Containers
 Why should you choose Confidential Containers for your business and how do they stand out from the "vanilla" version? Check it out in our article!
Why should you choose Confidential Containers for your business and how do they stand out from the "vanilla" version? Check it out in our article!
52. How To Prevent Ransomware Attacks: A Threat That’s Real
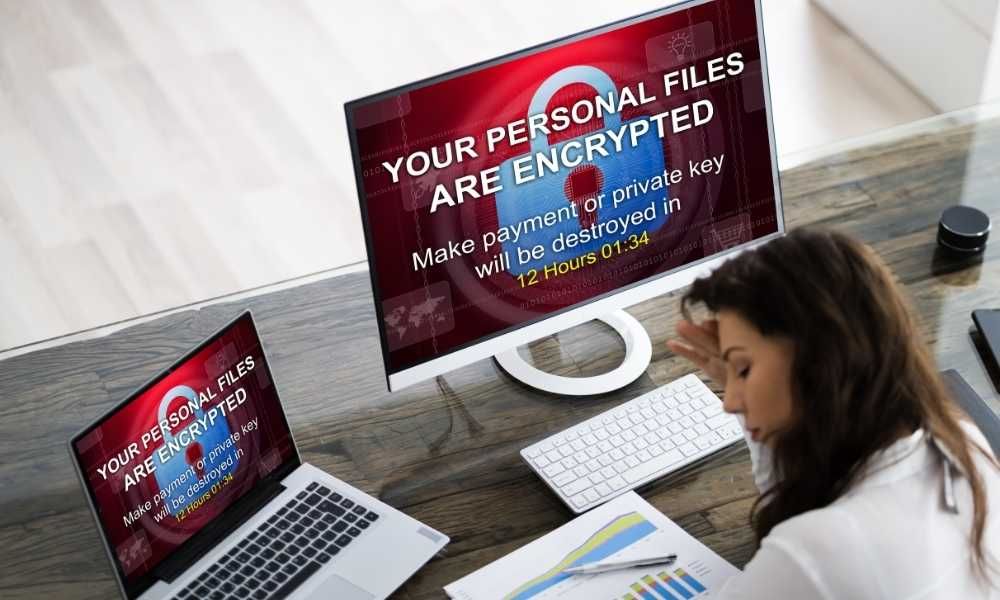 Ransomware works by encrypting the user’s data, making it unreadable. If a user wants their data back, a ransom must be paid. Keep reading to learn more
Ransomware works by encrypting the user’s data, making it unreadable. If a user wants their data back, a ransom must be paid. Keep reading to learn more
53. 5 Reasons Why VPNs are not Safe in 2021
 All good things must come to an end, which may be true for the VPN in 2021. VPNs have been a useful enterprise tool for companies since they started in the 90s,
All good things must come to an end, which may be true for the VPN in 2021. VPNs have been a useful enterprise tool for companies since they started in the 90s,
54. COVID-19 Tracing: Protect Your Privacy
 As the COVID-19 pandemic goes on, life for some around the world is beginning to look a little more like it did before, except with some more distancing, and more people wearing masks. What doesn’t look the same, is how technology is being used to monitor and track cases, infection rates, and outbreaks.
As the COVID-19 pandemic goes on, life for some around the world is beginning to look a little more like it did before, except with some more distancing, and more people wearing masks. What doesn’t look the same, is how technology is being used to monitor and track cases, infection rates, and outbreaks.
55. What Are The Challenges of Monetizing and Selling Data?
 There have been great advancements in monetization opportunities in the last decade, but there are still challenges when it comes to generating big data analyti
There have been great advancements in monetization opportunities in the last decade, but there are still challenges when it comes to generating big data analyti
56. The Biggest Problems with WhatsApp's Privacy Practices
 A new report now claims that Whatsapp messages are not end-to-end encrypted.
A new report now claims that Whatsapp messages are not end-to-end encrypted.
57. 6 Years Later, My Google Spreadsheet Is Now an App Called Taonga
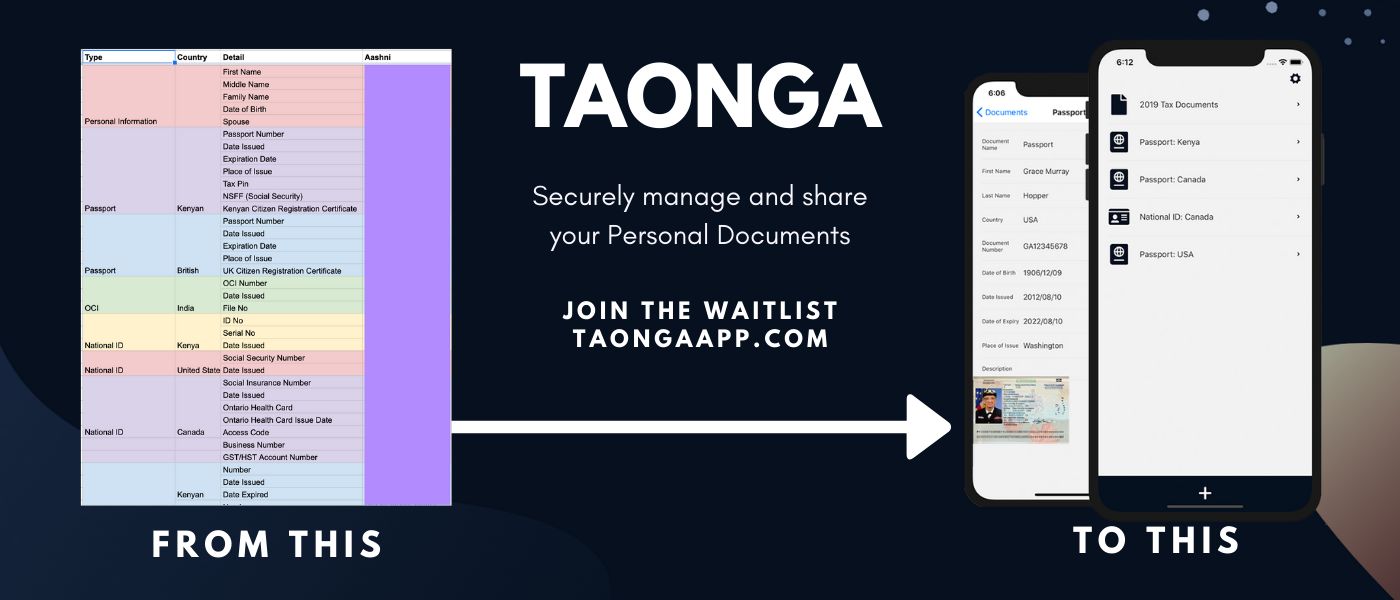 With Taonga, I'm working to build the easiest way to securely manage and share your personal documents, like your passport. It’s built using privacy-by-design and consent-by-design concepts, making sure the user has full control over their personal documents. The idea for Taonga stemmed from an ad-hoc Google Spreadsheet I created 6 years ago, and I’d love to share that story with you here.
With Taonga, I'm working to build the easiest way to securely manage and share your personal documents, like your passport. It’s built using privacy-by-design and consent-by-design concepts, making sure the user has full control over their personal documents. The idea for Taonga stemmed from an ad-hoc Google Spreadsheet I created 6 years ago, and I’d love to share that story with you here.
58. Sorry, Folks. Blockchain ≠ Automatic Privacy
 Not all blockchain ecosystems are truly private -- we spoke to privacy blockchain Panther Protocol to learn more.
Not all blockchain ecosystems are truly private -- we spoke to privacy blockchain Panther Protocol to learn more.
59. An Intro to Zero-Knowledge Proofs (ZKP) and Identity
 Learn about Zero Knowledge claims and how they can help in securing your Identity.
Learn about Zero Knowledge claims and how they can help in securing your Identity.
60. Distributed Governance and Anonymity: A Bad Idea
 One of the big debates in the Genesis DAO started by DAOstack was the question of anonymity. Should people be able to make proposals and ask for budgets without providing a real identity?
One of the big debates in the Genesis DAO started by DAOstack was the question of anonymity. Should people be able to make proposals and ask for budgets without providing a real identity?
61. Data Masking: How it Can be Implemented Correctly

62. Data Leak Prevention with Databunker
 We hear the horror stories of data leaks almost every day. Some require a sophisticated attack to gain shell access to the servers. Some happen over the web using the SQL injections in the web apps. As a result of this attack, your customer data can be dumped and personal data leaked.
We hear the horror stories of data leaks almost every day. Some require a sophisticated attack to gain shell access to the servers. Some happen over the web using the SQL injections in the web apps. As a result of this attack, your customer data can be dumped and personal data leaked.
63. 4 Privacy Tips for Distance Learning Students
 If you’re like millions around the world getting ready to head back to school this fall, you’re figuring our first, if your campus will even be open, and second, how to adjust to the idea of distance learning.
If you’re like millions around the world getting ready to head back to school this fall, you’re figuring our first, if your campus will even be open, and second, how to adjust to the idea of distance learning.
64. Facebook and Anti-Abortion Clinics Have Your Info
 Facebook is collecting ultrasensitive personal data about abortion seekers and enabling anti-abortion organizations to use that data
Facebook is collecting ultrasensitive personal data about abortion seekers and enabling anti-abortion organizations to use that data
65. How to Ensure Data Integrity in an Organization
 Ensuring data integrity is essential in an organization because it ensures data has not been altered or compromised. Understand how to preserve data integrity.
Ensuring data integrity is essential in an organization because it ensures data has not been altered or compromised. Understand how to preserve data integrity.
66. Organizing Your Business Statistics to Achieve Success
 It is not an easy task to keep your business data organized; however, it is an important thing to do. Organizing data includes a lot more than putting all your papers in place and clearing the clutter on your desk. To have your statistics well organized, you have to create a system and procedures for every department available in your company. The following are top ideas o0n how you can get your small business statistics that can help in increasing the productivity of the business.
It is not an easy task to keep your business data organized; however, it is an important thing to do. Organizing data includes a lot more than putting all your papers in place and clearing the clutter on your desk. To have your statistics well organized, you have to create a system and procedures for every department available in your company. The following are top ideas o0n how you can get your small business statistics that can help in increasing the productivity of the business.
67. Manage Your Emails Like You Manage Your Passwords
 Add an extra security layer for the protection of your emails.
Add an extra security layer for the protection of your emails.
68. The Black Market for Data is on the Rise
 Once the laughingstock of the Internet, hackers are now some of the most wanted criminals in the world.
Once the laughingstock of the Internet, hackers are now some of the most wanted criminals in the world.
69. 7 Serious Security Issues in Big Data and How to Address Them
 Businesses will be able to reach their ultimate aim of leveraging data for better customer experience and retention if they use Big Data effectively.
Businesses will be able to reach their ultimate aim of leveraging data for better customer experience and retention if they use Big Data effectively.
70. Data Engineering Tools for Geospatial Data
 Location-based information makes the field of geospatial analytics so popular today. Collecting useful data requires some unique tools covered in this blog.
Location-based information makes the field of geospatial analytics so popular today. Collecting useful data requires some unique tools covered in this blog.
71. Data Is Now a Luxury Good: Here’s Why (It Shouldn’t Be)

72. Signal Protocol — Open Source, Private, Encrypted Mobile Messaging App
 Signal doesn’t store any personal data and is highly transparent about their work because they are an open-source organization rather than a corporation.
Signal doesn’t store any personal data and is highly transparent about their work because they are an open-source organization rather than a corporation.
73. How to Protect Your Privacy From Hackers
 Web accounts are really easy to hack. All that the process really needs is patience.
Web accounts are really easy to hack. All that the process really needs is patience.
74. Announcing our Data Breach website on Data Privacy Day
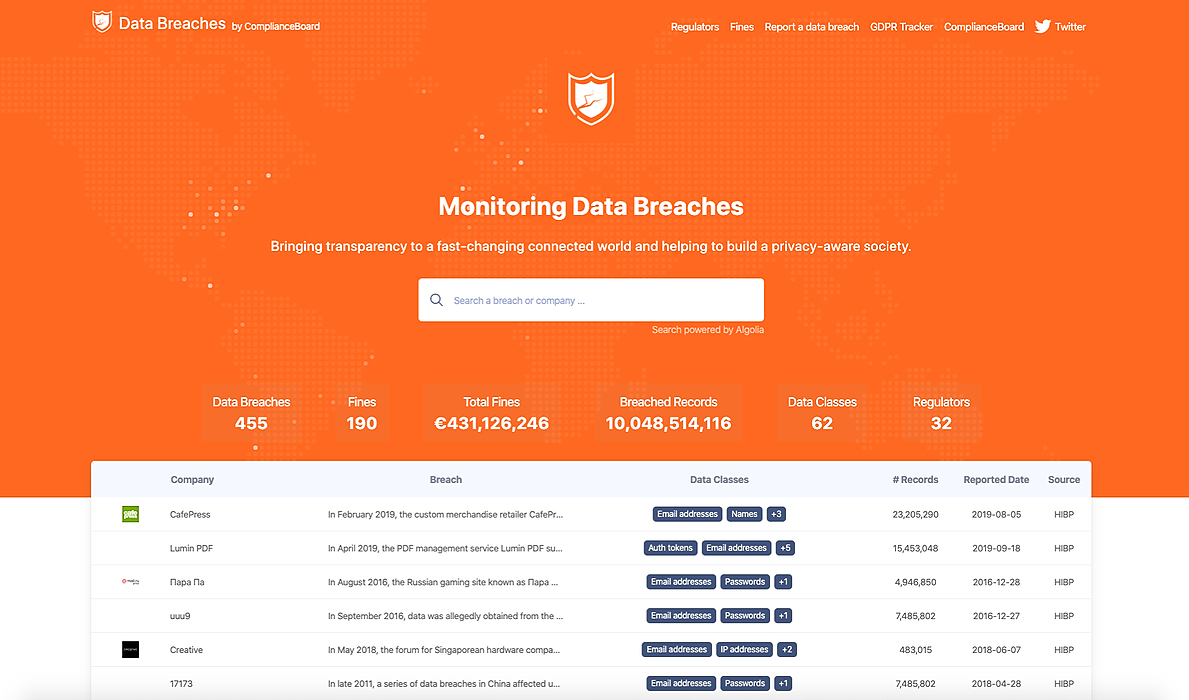 We are happy to announce our Data Breach website Databreach.es, our latest community project. With this project, we strive to create insights into global data breaches. Which companies have been breached, what kind of data got lost, what's the impact on your privacy and how did these companies handle the situation.
We are happy to announce our Data Breach website Databreach.es, our latest community project. With this project, we strive to create insights into global data breaches. Which companies have been breached, what kind of data got lost, what's the impact on your privacy and how did these companies handle the situation.
75. Is Women’s Data Safe in a Post-Roe v Wade America?
 Can women be prosecuted for Googling “abortion pills”? The TL;DR: women who are looking to end their pregnancy in the US have cause for concern.
Can women be prosecuted for Googling “abortion pills”? The TL;DR: women who are looking to end their pregnancy in the US have cause for concern.
76. How To Overcome All Challenges And Create A Great Password Manager App
 Creating a new product is never easy. From the moment you come up with a new idea to the moment you actually launch it, months--if not years--can pass. And after your product launches, you need to make sure that you never stop improving it, so you don’t fall behind your competition. KeepSolid has already brought several products to market, and each of them has had its own successes and challenges. Here’s the story of our journey to launch our latest product, Passwarden.
Creating a new product is never easy. From the moment you come up with a new idea to the moment you actually launch it, months--if not years--can pass. And after your product launches, you need to make sure that you never stop improving it, so you don’t fall behind your competition. KeepSolid has already brought several products to market, and each of them has had its own successes and challenges. Here’s the story of our journey to launch our latest product, Passwarden.
77. Are Zoom's Encryption Claims Deceptive?
 What do you do when your product isn’t encrypted? Change how encryption to is commonly understood.
What do you do when your product isn’t encrypted? Change how encryption to is commonly understood.
78. Enable Secure Sovereign Identity: Avatars by Metaverse
 Our identity is, without doubt, the most important asset we hold. In the digital age, our daily lives are fraught with dangers which undermine our identity or expose details of our personal lives we’d rather keep out of the public realm.
Our identity is, without doubt, the most important asset we hold. In the digital age, our daily lives are fraught with dangers which undermine our identity or expose details of our personal lives we’d rather keep out of the public realm.
79. How to Keep Sensitive Data Out of Your Logs
 Do you protect customer PII and PHI, keeping them out of your logs? Learn about why and how to isolate this sensitive data with a data privacy vault and API.
Do you protect customer PII and PHI, keeping them out of your logs? Learn about why and how to isolate this sensitive data with a data privacy vault and API.
80. Privacy in Crypto is Under Siege, We Need More Solutions to Protect Us
 Despite the crypto market is quite small, cryptocurrency assets are closely being watched by governments across the globe. The issue is that central banks view virtual assets like Bitcoin and the rest as a threat to their dominance over global finance.
Despite the crypto market is quite small, cryptocurrency assets are closely being watched by governments across the globe. The issue is that central banks view virtual assets like Bitcoin and the rest as a threat to their dominance over global finance.
81. Who is Life360 Selling Your Data to?
 Life360, a safety app, sold data to Cuebiq and X-Mode, two location-data brokers.
Life360, a safety app, sold data to Cuebiq and X-Mode, two location-data brokers.
82. Compartmentalisation As A Means For Ensuring Privacy [An Overview]
 It was originally used by the Greeks to keep the secret of Greek fire, but now it is used by people all around the world for lots of different reasons.
It was originally used by the Greeks to keep the secret of Greek fire, but now it is used by people all around the world for lots of different reasons.
83. What is an Email Alias and Why You Should Stop Using Your Real Email Address
 Learn how to declutter your mailbox and avoid spam by using email aliases. It's free, effective, and will save you hours of scanning through emails.
Learn how to declutter your mailbox and avoid spam by using email aliases. It's free, effective, and will save you hours of scanning through emails.
84. 10 Features of a Secure Website
 Website security is a primary consideration in web development but it is often not taken seriously by a lot of website owners. If you have built a secure website, then you must have sought out the services of a security expert who spots areas of weaknesses in your system and also carry out routine maintenance checks for new flaws and vulnerabilities. These are the minimum requirements for any safe website and I have grouped them into 10 must-have features for your website.
Website security is a primary consideration in web development but it is often not taken seriously by a lot of website owners. If you have built a secure website, then you must have sought out the services of a security expert who spots areas of weaknesses in your system and also carry out routine maintenance checks for new flaws and vulnerabilities. These are the minimum requirements for any safe website and I have grouped them into 10 must-have features for your website.
85. Will The New Wave of Data Laws Affect Fintech?
 Fintech, otherwise known as the financial technology market, is on a very strong growth trajectory, having already disrupted the banking world in a powerful way. From mobile payments, to artificial intelligence, insurance and investment services, Fintech has gradually transformed the way we bank since the day the US Federal Reserve introduced the Fedwire Funds Service back in 1918, which used morse code and telegraph to transfer funds electronically.
Fintech, otherwise known as the financial technology market, is on a very strong growth trajectory, having already disrupted the banking world in a powerful way. From mobile payments, to artificial intelligence, insurance and investment services, Fintech has gradually transformed the way we bank since the day the US Federal Reserve introduced the Fedwire Funds Service back in 1918, which used morse code and telegraph to transfer funds electronically.
86. Hospitals Remove Facebook Tracker but Questions Still Remain
 Meanwhile, developments in another legal case suggest Meta may have a hard time providing the Senate committee with a complete account of the health data.
Meanwhile, developments in another legal case suggest Meta may have a hard time providing the Senate committee with a complete account of the health data.
87. Privacy on Web 3.0 — Heaven or Pitfall?
 Unfortunately, companies like Facebook, Google, and Amazon do not simply track and funnel this data to IC.
Unfortunately, companies like Facebook, Google, and Amazon do not simply track and funnel this data to IC.
88. DuckDuckGo Is A Step In The Right Direction For User Privacy

89. Top Biometrics Trends and How They Approach User Privacy
 Discover the main trends in biometrics and how they address user privacy.
Discover the main trends in biometrics and how they address user privacy.
90. How Machine Learning Prevents Identity Theft

91. A How-to Guide for Data Backup and VM Modernization
 Data is everywhere it is something that we all rely on. It is used by individuals and large organizations that collect and store hundreds of files a day.
Data is everywhere it is something that we all rely on. It is used by individuals and large organizations that collect and store hundreds of files a day.
92. What Hackers Do With Your Data
 4 ways your data is being used without your knowledge
4 ways your data is being used without your knowledge
93. Kris Adair, Mycroft AI CFO, On What It's Like Working In Currently The Fastest Adopted Technology
 Mycroft AI, startup of the year nominee, is the open source and privacy focused answer to voice assistants from Big Tech. Meet Kris Adair, CFO & co-founder.
Mycroft AI, startup of the year nominee, is the open source and privacy focused answer to voice assistants from Big Tech. Meet Kris Adair, CFO & co-founder.
94. How a Data Privacy Vault Protects PHI for Healthtech Users
 With healthcare apps and wearables that gather customer PHI, healthtech companies need a data privacy vault to ensure HIPAA compliance and build customer trust.
With healthcare apps and wearables that gather customer PHI, healthtech companies need a data privacy vault to ensure HIPAA compliance and build customer trust.
95. 8 Cloud Compliance Frameworks and Why Cloud-based Organizations Need Them
 Cloud compliance frameworks help an organization to keep its database secure and private. In this article, you will eight such frameworks that can guide you.
Cloud compliance frameworks help an organization to keep its database secure and private. In this article, you will eight such frameworks that can guide you.
96. Is 128 Bit Encryption Enough?
 There are a lot of cloud services that tout encryption strength as a measure of how well they guard your data. It is quoted in bits, which is the
size of the key. So you see services quoting 128 bit, 256 bit or even
2048 bit.
There are a lot of cloud services that tout encryption strength as a measure of how well they guard your data. It is quoted in bits, which is the
size of the key. So you see services quoting 128 bit, 256 bit or even
2048 bit.
97. Tackling Privacy Management with Aline Deparis, CEO of Privacy Tools
 I’m Aline Deparis and I’m the CEO of Privacy Tools, which aims to solve the global needs of transparency and compliance when talking about privacy matters.
I’m Aline Deparis and I’m the CEO of Privacy Tools, which aims to solve the global needs of transparency and compliance when talking about privacy matters.
98. Data Backup Strategy To Reduce Data Loss
 Backing up the data is one of the most important processes for businesses. It requires creating a copy of all your data and storing it.
Backing up the data is one of the most important processes for businesses. It requires creating a copy of all your data and storing it.
99. Why Data Privacy is Important for Users in the Web3 Ecosystem
 Interview discussing why data privacy is important for users in the web3 ecosystem
Interview discussing why data privacy is important for users in the web3 ecosystem
100. How Facebook Makes Money and Why You Should Worry
 Facebook sells ads, as Mark Zuckerberg famously and patiently explained to Congress, but it’s a little more complicated than that.
Facebook sells ads, as Mark Zuckerberg famously and patiently explained to Congress, but it’s a little more complicated than that.
101. How Software Accountability shifts Technology Dynamics for Today’s Startups
 For a long time now, software-based startups have been launching their products and thrived by having users’ data as the very foundation of their business models. Social media platforms are the perfect examples of how a business can profit from a well of consumer data. While users had traditionally been in the dark about how the information they share when interacting with digital products is used, various notorious scandals have changed the narrative.
For a long time now, software-based startups have been launching their products and thrived by having users’ data as the very foundation of their business models. Social media platforms are the perfect examples of how a business can profit from a well of consumer data. While users had traditionally been in the dark about how the information they share when interacting with digital products is used, various notorious scandals have changed the narrative.
102. Anonymous Web Browser: A Guide on Anti-Detect Technology
 Learn how anonymous web browser works with the help of antidetect technology.
Learn how anonymous web browser works with the help of antidetect technology.
103. Proposition 24: What you Need to Know About Data Privacy America
 Californians have spoken: Proposition 24 will soon expand data privacy protections in the largest state in America.
Californians have spoken: Proposition 24 will soon expand data privacy protections in the largest state in America.
104. How Drones Are Transforming Big Data Analytics
 The world is transforming right before our eyes. We’ve heard about drones for a long time now, especially with big companies like Amazon using them for more efficient package delivery, a major trend in modern e-commerce. Instead of your local delivery man, a drone may drop a package right on your doorstep. The true power of drones goes well beyond that, though. They provide businesses with data that’s difficult to collect otherwise. In addition to taking aerial photos and videos, drones can collect information about everything from the health of crops to thermal leaks in buildings.
The world is transforming right before our eyes. We’ve heard about drones for a long time now, especially with big companies like Amazon using them for more efficient package delivery, a major trend in modern e-commerce. Instead of your local delivery man, a drone may drop a package right on your doorstep. The true power of drones goes well beyond that, though. They provide businesses with data that’s difficult to collect otherwise. In addition to taking aerial photos and videos, drones can collect information about everything from the health of crops to thermal leaks in buildings.
105. Top Open Source Vulnerabilities to Watch Out
 Open Source packages are a mainstay for most software engineering projects. We are so accustomed as developers to run our
Open Source packages are a mainstay for most software engineering projects. We are so accustomed as developers to run our npm install (for Node developers) or
106. The Implications of the Amazon Fraud Detector
 Over the past 4 years, I have been exclusively operating on AWS as my cloud computing platform. AWS offers so many products, what I have used is a small portion. However, what never has stopped impressing me is each of these products I use is constantly getting improved. AWS also has established a mature eco-system, new offerings are taking advantage of the platform as a whole to greatly reduce customer's learning curves.
Over the past 4 years, I have been exclusively operating on AWS as my cloud computing platform. AWS offers so many products, what I have used is a small portion. However, what never has stopped impressing me is each of these products I use is constantly getting improved. AWS also has established a mature eco-system, new offerings are taking advantage of the platform as a whole to greatly reduce customer's learning curves.
107. Reconstruction Attacks: Examples of Invasion of Your Privacy Without Consent
108. The Markup Needs Your Help Investigating the Ed Tech Industry
 The Markup needs your help investigating educational technology companies.
The Markup needs your help investigating educational technology companies.
109. The Role of Blockchain and Decentralization in the Digital Economy
 Blockchain is a key emerging technology in realizing the full potential of the digital economy along with other emerging technologies and paradigms such as 5G, IoT, Cloud, AI, etc.
Blockchain is a key emerging technology in realizing the full potential of the digital economy along with other emerging technologies and paradigms such as 5G, IoT, Cloud, AI, etc.
110. Data Privacy and risks of the Remote Work Environment
 Digital Transformation in every field of our lives has led to the increased collection of our personal data on every device we touch from laptops to mobile phones, to tablets, leaving a digital trail. This data is then used for various purposes such as targeted advertising, research proposes or even corporate espionage. But boundaries need to be set to avoid corporate or other malicious parties taking advantage of this information or even corrupting it.
Digital Transformation in every field of our lives has led to the increased collection of our personal data on every device we touch from laptops to mobile phones, to tablets, leaving a digital trail. This data is then used for various purposes such as targeted advertising, research proposes or even corporate espionage. But boundaries need to be set to avoid corporate or other malicious parties taking advantage of this information or even corrupting it.
111. 10 Factors to Prepare for CCPA (California Consumer Privacy Act)
 Be ready for CCPA with these top 10 critical factors
Be ready for CCPA with these top 10 critical factors
112. Using Unmasked Production Data For Testing Leaves Your At Risk For Data Breaches
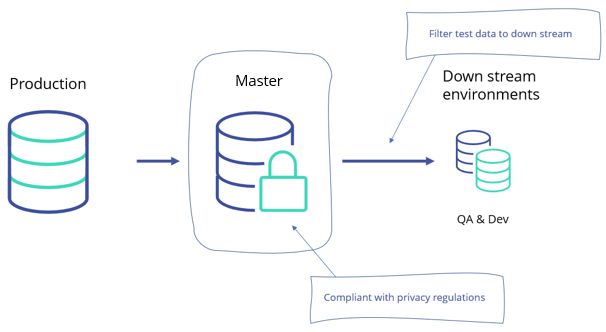
113. Voice is the Safest and Most Accurate for Emotion AI Analysis
 Voice is one of several unique, innate, and immutable biometric identifiers. Other identifiers include retinal scans, iris scans and facial geometry scans. As technology evolves, so does the public’s concern regarding issues of privacy. Consider, for example, the turmoil DNA evidence introduced to our legal system in the late 1990’s, or, the controversial introduction of fingerprint evidence in the 1910 murder trial of Clarence Hiller in Chicago, Illinois.
Voice is one of several unique, innate, and immutable biometric identifiers. Other identifiers include retinal scans, iris scans and facial geometry scans. As technology evolves, so does the public’s concern regarding issues of privacy. Consider, for example, the turmoil DNA evidence introduced to our legal system in the late 1990’s, or, the controversial introduction of fingerprint evidence in the 1910 murder trial of Clarence Hiller in Chicago, Illinois.
114. Is Your Messaging Truly Anonymous?
 Anonymous messaging is a lie
Anonymous messaging is a lie
115. Is Big Tech 'Targeting' the Elderly a Point of Concern?
 Elderly people, in recent years, have been using new tech more and more. While that is a good thing, it brings up the topic of privacy.
Elderly people, in recent years, have been using new tech more and more. While that is a good thing, it brings up the topic of privacy.
116. 4 Privacy Focused Raspberry Pi Projects
 4 do it yourself projects with a Raspberry Pi for the privacy minded user
4 do it yourself projects with a Raspberry Pi for the privacy minded user
117. Riddhiman Das, CEO TripleBlind, on Breaking Data Monopolies
 TripleBlind has created a new data privacy solution that enables highly-regulated enterprises to share data without ever decrypting it.
TripleBlind has created a new data privacy solution that enables highly-regulated enterprises to share data without ever decrypting it.
118. Anonymity and Privacy in Emerging Web3 Spaces Make the World go Round
 Considering previous legal theory & recent web3 events, it can be argued that the framework of privacy needs to be updated with an understanding of consent.
Considering previous legal theory & recent web3 events, it can be argued that the framework of privacy needs to be updated with an understanding of consent.
119. Why Are Businesses Raising Equity with Crowdfunding?
 Equity crowdfunding was not the easiest choice to make, but it kept us true to our core values of trust, transparency, and user-centricity.
Equity crowdfunding was not the easiest choice to make, but it kept us true to our core values of trust, transparency, and user-centricity.
120. Is There a Valid Cause for Using Facial Recognition Tools in Schools
 The deployment of facial recognition technology in a school in the US marks a disturbing trend with the protection of identity and the safety of students.
The deployment of facial recognition technology in a school in the US marks a disturbing trend with the protection of identity and the safety of students.
121. Your Personal Data: Its True Value, Power, and Why It Really Is The New Oil
122. Tech Companies Take a Stand: UK's Online Safety Bill Risks a Total Wipeout of Secure Messaging Apps
 With secure messaging apps willing to cease operations, UK's attempt to fight cybercrime with its Online Safety Bill has sparked the encryption debate again.
With secure messaging apps willing to cease operations, UK's attempt to fight cybercrime with its Online Safety Bill has sparked the encryption debate again.
123. Plausible is Paving the Way for Ethical Analytics
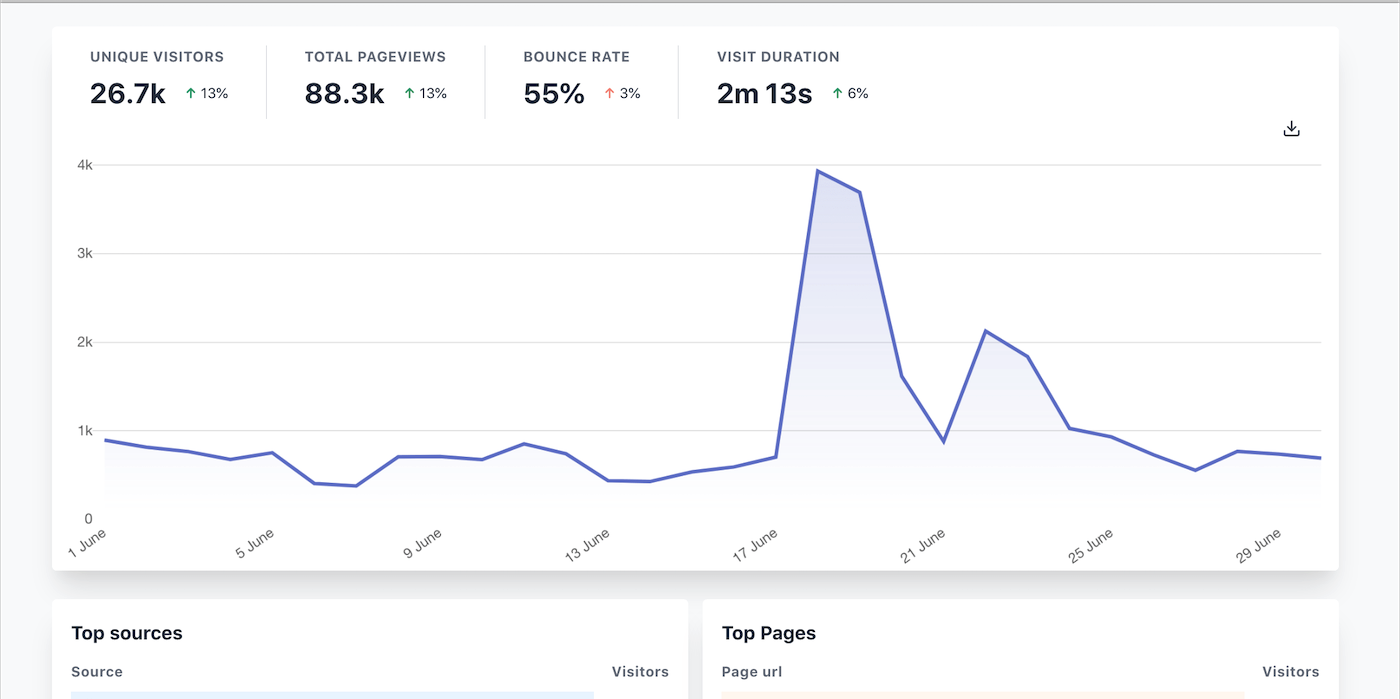 One of the trickiest things for companies or really anyone running a website is figuring out the success of their site, how many visits they are getting, and how they got them, while at the same time respecting their visitor’s privacy.
One of the trickiest things for companies or really anyone running a website is figuring out the success of their site, how many visits they are getting, and how they got them, while at the same time respecting their visitor’s privacy.
124. Have You Been the Victim of an Online Attack? Here's How to Take Action
 1 in every 3 Americans suffers from an online attack each year; a rate of about one attack every 39 seconds. It results in scams, fraud, and emotional trauma.
1 in every 3 Americans suffers from an online attack each year; a rate of about one attack every 39 seconds. It results in scams, fraud, and emotional trauma.
125. Can Blockchain Technology Help with Our Growing Privacy Problems?
 Since the Internet's introduction to the public from the academic world, privacy issues have existed. Blockchain technology may be able to change this.
Since the Internet's introduction to the public from the academic world, privacy issues have existed. Blockchain technology may be able to change this.
126. How to Reduce Your Chances of Being a Victim of Identity Theft
 The major causes of identity theft, along with some simple steps you can take to lower your risk of exposure dramatically.
The major causes of identity theft, along with some simple steps you can take to lower your risk of exposure dramatically.
127. The Digital Identity Phantom Menace
 Is decentralization of your digital identity possible, or is it yet another delusion being promoted by Web 3.0 cheerleaders?
Is decentralization of your digital identity possible, or is it yet another delusion being promoted by Web 3.0 cheerleaders?
128. The Difference Between Privacy and Security
 For many, privacy and security seem to be words that are interchangeable. Yet, you can have one without the other and users need to be aware of what they get.
For many, privacy and security seem to be words that are interchangeable. Yet, you can have one without the other and users need to be aware of what they get.
129. How to Avoid Becoming a Victim of Data Breach

130. Life360 Potentially Leaves Its Users’ Sensitive Data at Risk
 The family safety app Life360 doesn’t have some standard guardrails to prevent a hacker from taking over an account and accessing sensitive information.
The family safety app Life360 doesn’t have some standard guardrails to prevent a hacker from taking over an account and accessing sensitive information.
131. Finding The Privacy Balance - Is There Such Thing as Too Much Privacy?
 I've been a heavy advocate for using multiple tools and alternative services to protect your personal information for years. However, as I've seen people pile on one privacy tool after another I've realized that people have perhaps taken it too far.
I've been a heavy advocate for using multiple tools and alternative services to protect your personal information for years. However, as I've seen people pile on one privacy tool after another I've realized that people have perhaps taken it too far.
132. Your Planned Parenthood Data Is Being Collected, Analyzed, and Sold
 The Markup has found that location data company INRIX, which collects, and sells aggregated vehicle, traffic, and parking data includes Planned Parenthood.
The Markup has found that location data company INRIX, which collects, and sells aggregated vehicle, traffic, and parking data includes Planned Parenthood.
133. Public Computers Safety Tips: Interview with Cybersecurity Expert Ravi Bahethi
 With the amazing advances in cloud computing, many of us are finding that it is efficient to use a public or shared computer from time to time to check in on work and personal projects. Staying safe on a public computer is essential in keeping your data secure from cybercriminals. In this article, systems engineer and cybersecurity specialist Ravi Bahethi focuses on five tips to help you stay safe while using public computers.
With the amazing advances in cloud computing, many of us are finding that it is efficient to use a public or shared computer from time to time to check in on work and personal projects. Staying safe on a public computer is essential in keeping your data secure from cybercriminals. In this article, systems engineer and cybersecurity specialist Ravi Bahethi focuses on five tips to help you stay safe while using public computers.
134. Create Realistic and Secure Test Data with our Synthetic Data Platform
 Learn how to fully automate your test data creation efforts. Let our AI model privacy-protect your production data and figure out its business rules.
Learn how to fully automate your test data creation efforts. Let our AI model privacy-protect your production data and figure out its business rules.
135. Why We Should All Care About Privacy Online—Interview: Hanna Bozakov
 I interviewed Hanna Bozakov, Head of Marketing for secure email service Tutanota, about internet security, online privacy, the legality of encryption, and how Tutanota works to protect you. According to their homepage, "Tutanota is the world's most secure email service, easy to use and private by design".
I interviewed Hanna Bozakov, Head of Marketing for secure email service Tutanota, about internet security, online privacy, the legality of encryption, and how Tutanota works to protect you. According to their homepage, "Tutanota is the world's most secure email service, easy to use and private by design".
136. The Two Best Ways to Scan for PII in Your Data Warehouse
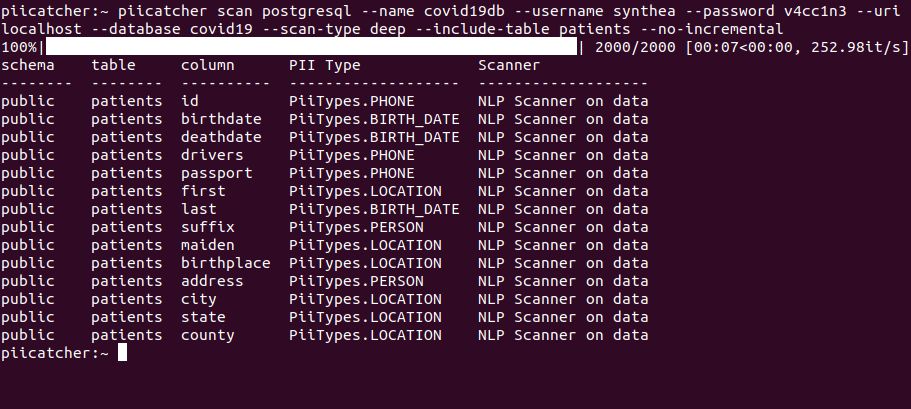 Find PII data by scanning column names and/or data in your data warehouse with these two easy to create methods and a step-by-step guide on how to do it.
Find PII data by scanning column names and/or data in your data warehouse with these two easy to create methods and a step-by-step guide on how to do it.
137. Apple Mail - Unmasking The Most Mysterious App In The World
 Revealing the mystery behind the Apple Mail App and why the small app has a wider role to play in Apple's wider privacy-first strategy and fight for the market
Revealing the mystery behind the Apple Mail App and why the small app has a wider role to play in Apple's wider privacy-first strategy and fight for the market
138. Why You Have No Choice But Care About Privacy?

139. Reimagining Marketing Teams: Why Creatives Should Embrace the Tech Side of the Business
 With the pace of the business world, it is increasingly important for marketers to embrace new technological breakthroughs to stay ahead of the curve.
With the pace of the business world, it is increasingly important for marketers to embrace new technological breakthroughs to stay ahead of the curve.
140. Have You Read Your Privacy Notice in Detail?
 Do you recall every company you have given consent to use your data as you browse a website or sign-up to a ‘free’ service? It's time we moved beyond consent
Do you recall every company you have given consent to use your data as you browse a website or sign-up to a ‘free’ service? It's time we moved beyond consent
141. What Does Privacy Mean in the Tech Industry?
 Privacy, as a concept, often lacks a clear definition. However, privacy-enhancing technologies can be generally categorized into two broad desiderata.
Privacy, as a concept, often lacks a clear definition. However, privacy-enhancing technologies can be generally categorized into two broad desiderata.
142. The Get Away From Google Guide
 If you want to to get away from Google and Big Tech these applications are what you will need
If you want to to get away from Google and Big Tech these applications are what you will need
143. Elusiv Raises $3.5 million in Seed Funding Round Co-led by LongHash Ventures to Build Web3 Privacy
 Elusiv, a privacy protocol that is Zero-Knowledge based and compliant, has raised $3.5 million in a seed investment round
Elusiv, a privacy protocol that is Zero-Knowledge based and compliant, has raised $3.5 million in a seed investment round
144. Be Resilient not Vulnerable to Ransomware Emails

145. How Fintech Companies Can Protect Data Privacy While Onboarding
 Taking advantage of these insights can empower fintechs to locate and approve new customers while mitigating friction and streamlining the customer journey.
Taking advantage of these insights can empower fintechs to locate and approve new customers while mitigating friction and streamlining the customer journey.
146. Is Apple Pay Secure? The Platform Security and Privacy Overview
 Apple Pay is a secure feature that uses multiple layers of encryption to protect users credit card information. Read to learn how to make Apple Pay more secure!
Apple Pay is a secure feature that uses multiple layers of encryption to protect users credit card information. Read to learn how to make Apple Pay more secure!
147. How to Deactivate or Delete a Facebook Account, Page, or Group
 How to deactivate or delete a Facebook user account, page, and group. You can do this by going to Settings and following simple steps mentioned in this guide.
How to deactivate or delete a Facebook user account, page, and group. You can do this by going to Settings and following simple steps mentioned in this guide.
148. The Protection of Rights in The Digital Age
 The identification of the right to privacy and the protection of personal data is the culmination of a long conceptual evolution.
The identification of the right to privacy and the protection of personal data is the culmination of a long conceptual evolution.
149. 23andMe and Other Sites are Selling Users' Genetic Data: How Safe is Your DNA?
 How genetic information from sites like 23andMe and Ancestry.com is being shared and sold.
How genetic information from sites like 23andMe and Ancestry.com is being shared and sold.
150. On Yang's Data Dividend Project and the Push to Treat Data as Property

151. The Difference Between Privacy Talkers and Privacy Doers
 I introduce the concept of storing and processing data focussing primarily on user privacy in my book, “Data is Like a Plate of Hummus”. I know many of you have read it – perhaps you're even thinking about it now ahead of the upcoming changes to Apple’s privacy settings which will block the attribution of users without consent.
I introduce the concept of storing and processing data focussing primarily on user privacy in my book, “Data is Like a Plate of Hummus”. I know many of you have read it – perhaps you're even thinking about it now ahead of the upcoming changes to Apple’s privacy settings which will block the attribution of users without consent.
152. What are File Permissions and Why do they Matter?
 Each and every file on a computer has what we call file permissions. These are attributes of the file that determine who has permission to access that file and what they can do to that file.
Each and every file on a computer has what we call file permissions. These are attributes of the file that determine who has permission to access that file and what they can do to that file.
To understand what file permissions are we first need to determine what exactly a file is.
153. Data-Driven Advertising and Its Impact On Our Privacy-Driven World
 Do we actually need so much data to do effective marketing?
Do we actually need so much data to do effective marketing?
154. 4 Ways to Upgrade the Privacy of Your Home Wi-Fi Network
 It doesn’t take a tech degree to make your personal Wi-Fi inaccessible to unwanted cyber snoops.
It doesn’t take a tech degree to make your personal Wi-Fi inaccessible to unwanted cyber snoops.
155. How Facebook Serves Targeted Ads by Big Pharma
 We found drug ads targeted at users interested in everything from bourbon to therapy on Facebook, with significant implications for privacy for users.
We found drug ads targeted at users interested in everything from bourbon to therapy on Facebook, with significant implications for privacy for users.
156. Effects a Data Breach Can Have on Your Business in the Long Term

157. Ghost the Internet Like It Is Your Ex
 Combine your VPN with crypto payments and the result is a truly anonymous and global browsing experience.
Combine your VPN with crypto payments and the result is a truly anonymous and global browsing experience.
158. Anonymity and Safety: How to Protect Information from Hackers
 The future belongs to information technologies that simultaneously provide proactive protection, backup, and data authenticity.
The future belongs to information technologies that simultaneously provide proactive protection, backup, and data authenticity.
159. On The Verge of Economic Change: An Interview with Dr Sebastian Bürgel
 It’s been over a year since COVID-19 appeared, and it’s still painfully apparent that this crisis is far from over. In fact, it may even trigger the largest economic change since World War Two. According to Arthur D. Little, a management consultancy firm, COVID-19 has been the impetus for an economic shift from a resources-driven to technology-focused economic model, one where the principles of “green” and tech go hand-in-hand. In essence, it will be data, not natural resources, which plays the fundamental role in keeping the global economy running. One possible implication of this is a full-scale transition to a digital economy. Data will be the fuel which powers our lives – and emerging technologies like the Internet of Things (IoT) and smart technologies will have to hit the ground running.
It’s been over a year since COVID-19 appeared, and it’s still painfully apparent that this crisis is far from over. In fact, it may even trigger the largest economic change since World War Two. According to Arthur D. Little, a management consultancy firm, COVID-19 has been the impetus for an economic shift from a resources-driven to technology-focused economic model, one where the principles of “green” and tech go hand-in-hand. In essence, it will be data, not natural resources, which plays the fundamental role in keeping the global economy running. One possible implication of this is a full-scale transition to a digital economy. Data will be the fuel which powers our lives – and emerging technologies like the Internet of Things (IoT) and smart technologies will have to hit the ground running.
160. Startpage is Still a Privacy-First Search Engine, says System1 CEO
 An interview with System1 CEO, Michael Blend, about the controversial partnership with Privacy-First search engine, Startpage.
An interview with System1 CEO, Michael Blend, about the controversial partnership with Privacy-First search engine, Startpage.
161. Meet The Entrepreneur: Gal Ringel, CEO, Mine PrivacyOps
 How Gal Ringel, co-founder and CEO of Mine Privacy Ops, deals with stress and tips that he has for other entrepreneurs trying to get their own startups going.
How Gal Ringel, co-founder and CEO of Mine Privacy Ops, deals with stress and tips that he has for other entrepreneurs trying to get their own startups going.
162. Why is Physical Security Such a Huge Threat?
 We’ve all heard about credit card skimming. This is the method by which skimmers attach devices to ATMs and gas pumps that capture your credit card number, and it’s often associated with a camera to catch you putting in your PIN. In 2018, credit and debit card fraud resulted in $28 billion in losses. This has prompted repeated calls for people to be on the lookout for things that are suspicious, cover their hands when they input their PIN numbers, and to only use “reputable” ATMs and gas pumps. Unfortunately the fraudsters are always one step ahead, and they are always coming up with new and creative ways to commit fraud.
We’ve all heard about credit card skimming. This is the method by which skimmers attach devices to ATMs and gas pumps that capture your credit card number, and it’s often associated with a camera to catch you putting in your PIN. In 2018, credit and debit card fraud resulted in $28 billion in losses. This has prompted repeated calls for people to be on the lookout for things that are suspicious, cover their hands when they input their PIN numbers, and to only use “reputable” ATMs and gas pumps. Unfortunately the fraudsters are always one step ahead, and they are always coming up with new and creative ways to commit fraud.
163. Don’t Fear The Cloud When it Comes to Data Integration
 Data loading speed, cloud applications, data security fears, and added costs & efforts are some of the reasons why businesses fear data integration.
Data loading speed, cloud applications, data security fears, and added costs & efforts are some of the reasons why businesses fear data integration.
164. Bye-bye Google Fonts: German Court Rules That Google Fonts Is Not in Compliance with GDPR
 Google Fonts is a data privacy concern. Learn why you should care.
Google Fonts is a data privacy concern. Learn why you should care.
165. An Intro to Privacy Enhancing Technologies (PET) and Why We Need Them
 After 2021, a year already marked by the amount - and the size - of data leaks and cyberattacks, PET will be one of the best defensive techniques.
After 2021, a year already marked by the amount - and the size - of data leaks and cyberattacks, PET will be one of the best defensive techniques.
166. How I Created a Zero Trust Overlay Network in my Home
 Enabling a secure home automation experience, by creating a zero trust overlay network to access #HomeAssistant.
Enabling a secure home automation experience, by creating a zero trust overlay network to access #HomeAssistant.
167. How Proactive API Visibility Could've Saved Optus From a Massive Data Breach
 On 22 September 2022, Australia's second-largest telecom company, Optus, announced that it had suffered a significant data breach.
On 22 September 2022, Australia's second-largest telecom company, Optus, announced that it had suffered a significant data breach.
168. Is Blockchain Technology Compatible With True User Privacy?
 Is blockchain technology compatible with data privacy when used in a corporate setting? What needs to change about it to make it perfectly compliant with it?
Is blockchain technology compatible with data privacy when used in a corporate setting? What needs to change about it to make it perfectly compliant with it?
169. Is Data Sovereignty Possible? In The European Union, It Soon Could Be
 Data privacy, security, and sovereignty issues have gained significant attention over recent years.
Data privacy, security, and sovereignty issues have gained significant attention over recent years.
170. Reasons Why Data Privacy Matters
 Data privacy is one of the hottest topics in tech conversation. But what's the deal with it? Is it good? Is It bad? Keep reading to find out.
Data privacy is one of the hottest topics in tech conversation. But what's the deal with it? Is it good? Is It bad? Keep reading to find out.
171. How the Blockchain Will Improve Data Security

172. Data Sovereignty: The Importance of Keeping Your Data Safe
 Protect your personal data with data sovereignty. Learn the importance of keeping your information safe and secure in the digital age. Read our article to find
Protect your personal data with data sovereignty. Learn the importance of keeping your information safe and secure in the digital age. Read our article to find
173. Meet Noonies 2022 Winner Naina Emmanuel of Cybersecurity Awareness & Data Privacy
 Naina Emmanuel discusses winning a Noonie.
Naina Emmanuel discusses winning a Noonie.
174. 6 Tips to Safeguard Patrons' Privacy at Your Library
 Patron privacy is one of those topics that touches every aspect of a library's operations, and for good reason.
Patron privacy is one of those topics that touches every aspect of a library's operations, and for good reason.
175. What is CAPTCHA and Does Google Use it to Train AI?
 CAPTCHA was invented between 1997 and 2000. It was used to protect against spam requests received every day in the now-defunct AltaVista search engine.
CAPTCHA was invented between 1997 and 2000. It was used to protect against spam requests received every day in the now-defunct AltaVista search engine.
176. How to Generate Synthetic Data?
 A synthetic data generation dedicated repository. This is a sentence that is getting too common, but it’s still true and reflects the market's trend, Data is the new oil. Some of the biggest players in the market already have the strongest hold on that currency.
A synthetic data generation dedicated repository. This is a sentence that is getting too common, but it’s still true and reflects the market's trend, Data is the new oil. Some of the biggest players in the market already have the strongest hold on that currency.
177. How Verifiable Creds, Decentralized Identifiers and Blockchain Work Together for a Safer Internet
 The future of the internet will come with more risks to our data privacy. Fortunately, Blockchain and Decentralized Identifiers can work together to protect.
The future of the internet will come with more risks to our data privacy. Fortunately, Blockchain and Decentralized Identifiers can work together to protect.
178. The Role of Whistleblowers in Cybersecurity
 Whistleblowers are employees who report their companies for misconduct. As cybersecurity becomes increasingly important, what role do whistleblowers play?
Whistleblowers are employees who report their companies for misconduct. As cybersecurity becomes increasingly important, what role do whistleblowers play?
179. How Artificial Intelligence (AI) Can Help In CCPA Compliance?
 California Consumer Privacy Act (CCPA) was passed recently in the USA state of California and will be implemented by 2020. This new regulation is transforming the privacy policies of businesses dealing with the data of Californian users.
California Consumer Privacy Act (CCPA) was passed recently in the USA state of California and will be implemented by 2020. This new regulation is transforming the privacy policies of businesses dealing with the data of Californian users.
180. Privacy and Security, Though Distinct Concepts, Are Interdependent
 Security & Privacy are often confused, but are distinct. It’s important that we understand the difference so that we can protect ourselves
Security & Privacy are often confused, but are distinct. It’s important that we understand the difference so that we can protect ourselves
181. New Data Privacy Laws Are an Opportunity, Not a Threat

182. How to Develop a Human Centric Security Policy

183. IT Security Policies And Why Every Business Must Have Them
 If you want to run a thriving business in the digital age, you need proper IT Security Policies for your organization.
If you want to run a thriving business in the digital age, you need proper IT Security Policies for your organization.
184. Data Journalism 101: 'Stories are Just Data with a Soul'
 Gone are the days when journalists simply had to find and report news.
Gone are the days when journalists simply had to find and report news.
185. Top 3 Ways You Can Use Data Privacy Trends to Boost Your Growth
 A robust data privacy and protection program can boost your sales by improving customer service and trust.
A robust data privacy and protection program can boost your sales by improving customer service and trust.
186. Why a Privacy-First Ad Approach Promises a Better Future for All
 A privacy-driven future is coming. Is your ad business ready?
A privacy-driven future is coming. Is your ad business ready?
187. Are Smart Cities a Threat to Data Privacy?
 For smart cities to function, they must collect data. But is that good for citizens? Is true data privacy achievable for smart cities?
For smart cities to function, they must collect data. But is that good for citizens? Is true data privacy achievable for smart cities?
188. Best Practices for Implementing Test Data into Your CI/CD Pipeline
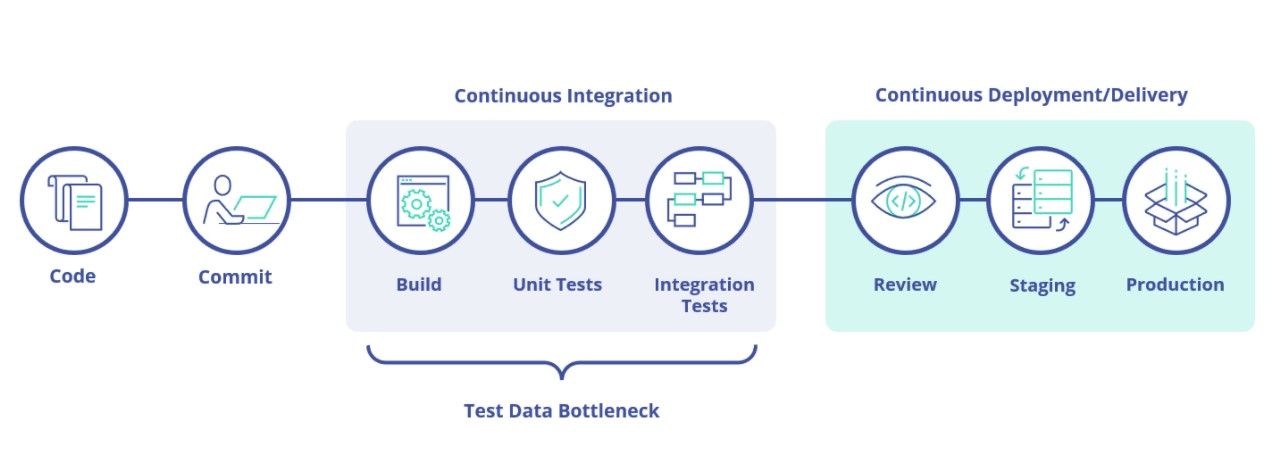 Test data as a part of software development is the poor relation that has been ignored for far too long. Butt’s one of the biggest bottlenecks.
Test data as a part of software development is the poor relation that has been ignored for far too long. Butt’s one of the biggest bottlenecks.
189. A New Study On Data Privacy Reveals Information About Cybersecurity Efforts
 A study revealed by Cisco shows that most organizations around the world were unprepared for the increase in remote work.
A study revealed by Cisco shows that most organizations around the world were unprepared for the increase in remote work.
190. Data Privacy In Social Media Matters and Here's Why
 In the past few years, privacy fears amongst social media users have augmented tremendously. Many users are reconsidering their interactions on social media and protecting their personal information due to the ever-increasing data infringement cases.
In the past few years, privacy fears amongst social media users have augmented tremendously. Many users are reconsidering their interactions on social media and protecting their personal information due to the ever-increasing data infringement cases.
191. Slack's Connect DM Feature Has A Security Flaw
 Slack recently rolled out its "Connect DM” feature that turned out to be a blunder. Know more about it here.
Slack recently rolled out its "Connect DM” feature that turned out to be a blunder. Know more about it here.
192. Why Did Today Feel like a Black Mirror Episode?
 Are the recent tech giant privacy policy updates of September 2022 pushing us further into dystopia? strfsh live report
Are the recent tech giant privacy policy updates of September 2022 pushing us further into dystopia? strfsh live report
193. Mz Stability's Near-Death Experience Started her Blockchain Journey
 Alyze Sam was a hospice nurse that was plowed by a semi truck, jumped into blockchain and became an accidental award winning and best selling author.
Alyze Sam was a hospice nurse that was plowed by a semi truck, jumped into blockchain and became an accidental award winning and best selling author.
194. Brave Browser, Brendan Eich, Digital Privacy, Web 3.0 and the Battle Against Surveillance Capitalism
 After becoming more and more paranoid about Google and other tech companies tracking me online, I learned about alternative options to more private web browsers.
After becoming more and more paranoid about Google and other tech companies tracking me online, I learned about alternative options to more private web browsers.
195. Your Website Knows Where Your Users Are—But Is It Keeping That Data Secret?

196. Data Tracking is Becoming Intrusive: Here's How Customer Data Platforms Can Help
 With the rise of big data comes the challenge of protecting customer data. Marketers must understand customers. Learn how the CDP can help us meet the challenge
With the rise of big data comes the challenge of protecting customer data. Marketers must understand customers. Learn how the CDP can help us meet the challenge
197. Maintain Anonymity Online With These 3 Actionable Steps
 The classic idea of the Internet is a virtual place where free speech and anonymity is possible; that has evolved. Here are 3 tips to maintain anonymity online.
The classic idea of the Internet is a virtual place where free speech and anonymity is possible; that has evolved. Here are 3 tips to maintain anonymity online.
198. Privacy is a human right: An Interview with Startpage founder, Robert E.G. Beens
 Startpage Founder and CEO Robert E.G. Beens explains what inspired him to start the world's first private search engine.
Startpage Founder and CEO Robert E.G. Beens explains what inspired him to start the world's first private search engine.
199. Did You Realize That You Paid Twice When You Bought An Alexa?
 In January 2019 Dave Limp, a senior vice president at Amazon, reported that more than 100 million Alexa powered devices had been sold to date. The 3rd gen Amazon Echo retails for $75 on (where else) Amazon.com and the Echo dot comes in at a very affordable $29.99.
In January 2019 Dave Limp, a senior vice president at Amazon, reported that more than 100 million Alexa powered devices had been sold to date. The 3rd gen Amazon Echo retails for $75 on (where else) Amazon.com and the Echo dot comes in at a very affordable $29.99.
200. 5 Best Practices for Tracking In-app Event Data
 This is the era of mobile apps. We get everything - from critical business information to entertaining videos and games - on our mobile devices. Information is right at our fingertips, and we are always striving to catch up with the outside world. As per App Annie, an average smartphone user has 80 apps installed.
This is the era of mobile apps. We get everything - from critical business information to entertaining videos and games - on our mobile devices. Information is right at our fingertips, and we are always striving to catch up with the outside world. As per App Annie, an average smartphone user has 80 apps installed.
201. On Zero-Knowledge Proofs (ZKPs) And Why They Matter
 There is a lot of enthusiasm for the application of zero-knowledge proof systems, at Dusk Network we’ve developed the open-source PLONK zero-knowledge proof system. It can be used for many things, and what better way to demonstrate its potential with an example!
There is a lot of enthusiasm for the application of zero-knowledge proof systems, at Dusk Network we’ve developed the open-source PLONK zero-knowledge proof system. It can be used for many things, and what better way to demonstrate its potential with an example!
202. Does Anonymization of Data Guarantees Privacy?
 Anonymization of data isn’t enough to guarantee privacy
Anonymization of data isn’t enough to guarantee privacy
203. ANSI X12 EDI Basics: A Guide to the ANSI X12 Standards
 ANSI X12 EDI is one of the most important concepts that you must be aware of prior to implementing EDI in your organization.
ANSI X12 EDI is one of the most important concepts that you must be aware of prior to implementing EDI in your organization.
204. Examining The Right To Be Forgotten Through The Prism Of Blockchain
 The right to be forgotten, that is set out in the new General Data Protection Regulation (GDPR) of the European Union (EU), mainly in article 17 and that already have come into force on 28th May 2017, nowadays empowers any person to correct or even delete his personal data and information that affects him (person) and stop being treated if this personal data are no longer necessary for the purposes collected or if a person has not withdrawn his consent.
The right to be forgotten, that is set out in the new General Data Protection Regulation (GDPR) of the European Union (EU), mainly in article 17 and that already have come into force on 28th May 2017, nowadays empowers any person to correct or even delete his personal data and information that affects him (person) and stop being treated if this personal data are no longer necessary for the purposes collected or if a person has not withdrawn his consent.
205. 10 Cybersecurity Books Every Business Owner Should Read
 Last year, according to MarketWatch.com, data breaches increased by 17%, which makes understanding cybersecurity an absolute must for all of us.
Last year, according to MarketWatch.com, data breaches increased by 17%, which makes understanding cybersecurity an absolute must for all of us.
206. How to Minimize Privacy Risks in AI/ML applications
 With the rise of data economy, data privacy has become even more important. Enterprises need to be privacy-first and invest in privacy enhancing technologies.
With the rise of data economy, data privacy has become even more important. Enterprises need to be privacy-first and invest in privacy enhancing technologies.
207. How the Taliban Will Increase Threat Actor Usage of Cryptocurrencies and CBDCs
 The Taliban’s return to power presents a distinct use case for cryptocurrencies and central bank digital currencies (CBDCs) alike.
The Taliban’s return to power presents a distinct use case for cryptocurrencies and central bank digital currencies (CBDCs) alike.
208. How a Data Privacy API Abstracts and Simplifies Privacy and Compliance
 Data privacy and compliance are hard! Let a data privacy API help.
Data privacy and compliance are hard! Let a data privacy API help.
209. Redefining Privacy and Data Ownership: An Interview with ARPA Founder, Felix Xu
 A conversation with Felix Xu, CEO of ARPA, on data utility and ownership, the NFT ecosystem, and much more.
A conversation with Felix Xu, CEO of ARPA, on data utility and ownership, the NFT ecosystem, and much more.
210. How to Scan Your Systems for Personal Data
 Learn the many different ways you can scan for personal data across your organisation's customer-facing online systems in this practical, how-to guide.
Learn the many different ways you can scan for personal data across your organisation's customer-facing online systems in this practical, how-to guide.
211. My Take on Decentralized Government on the Aleo Blockchain
 In this article, I will give my views on the prospects for the Aleo blockchain and its possible successors.
In this article, I will give my views on the prospects for the Aleo blockchain and its possible successors.
212. If You Wanna BYOD, You Gotta Get with Cybersecurity
 This article brings your attention to the sensitivity of Bringing Your Own Devices to work.
This article brings your attention to the sensitivity of Bringing Your Own Devices to work.
213. Everything Wrong with the WhatsApp Business Model
 The WhatsApp Business Model based around selling user data is predatory, exploitative, and not the only way to monetize an app, as Rakuten's VP explains.
The WhatsApp Business Model based around selling user data is predatory, exploitative, and not the only way to monetize an app, as Rakuten's VP explains.
214. How To Prevent Data Theft With Cybersecurity
 Technology has many advantages to offer businesses, but it also presents unique threats. Cyberattacks are levied at businesses and consumers alike, but companies are often directly targeted. This is because companies deal with large amounts of valuable data, including the personal information of customers and clients, and that can make for a veritable treasure trove for hackers. Protecting your company and your customers from bad actors on the world wide web should be a major priority. Here’s what you need to know.
Technology has many advantages to offer businesses, but it also presents unique threats. Cyberattacks are levied at businesses and consumers alike, but companies are often directly targeted. This is because companies deal with large amounts of valuable data, including the personal information of customers and clients, and that can make for a veritable treasure trove for hackers. Protecting your company and your customers from bad actors on the world wide web should be a major priority. Here’s what you need to know.
215. 🔮 Decoding 2020's Favourite Buzzword: "Machine Unlearning"

216. Life360 to Stop Selling Precise Location Data
 Life360, a safety app, claims it will stop selling precise location data.
Life360, a safety app, claims it will stop selling precise location data.
217. Why Password Managers Ignore Input Fields - trial:by:fire
 Creating login fields that work with password managers isn't as easy as it seems.
Creating login fields that work with password managers isn't as easy as it seems.
218. Podcast - When Machine Learning Meets Privacy
 This is the first episode of a podcast series on Machine Learning and Data privacy.
This is the first episode of a podcast series on Machine Learning and Data privacy.
219. Handling Sensitive Data: A Primer
 Properly securing sensitive customer data is more important than ever.
Properly securing sensitive customer data is more important than ever.
220. How To Protect Your Data While Working Remotely

221. Is Google Actually an Evil Corporation?
 When asked about Google, there has been a lot to say over the years. Google done some things right, and seemingly some things very wrong. As far as conspiracies go, Google does seem to have a CIA connection (see video below). This even roots back to potential government research, and missing gaps on how they have been funded in the early stage.
When asked about Google, there has been a lot to say over the years. Google done some things right, and seemingly some things very wrong. As far as conspiracies go, Google does seem to have a CIA connection (see video below). This even roots back to potential government research, and missing gaps on how they have been funded in the early stage.
222. "It's Only Fair That Users Retain Ownership Of Their Personal Data & Generate Value" -Sheridan Johns
 With just over 4,000 data brokers controlling the loosely regulated data economy, there are absolutely no guarantees when it comes to data protection, privacy, and ownership.
With just over 4,000 data brokers controlling the loosely regulated data economy, there are absolutely no guarantees when it comes to data protection, privacy, and ownership.
223. The Five Linux Distros Hackers Prefer

224. The State Of Data Privacy In 2020
 In 2020, there will be just one thing considered to be more important than product quality for consumers: data privacy. By this I refer not to user-controlled measures to add extra security for internet users, from the most classic one-time password, or two-factor authentication, to the most secure multi-factor authentication methods: but data privacy measures implemented by companies to ensure that peoples’ personal data is protected - no matter what.
In 2020, there will be just one thing considered to be more important than product quality for consumers: data privacy. By this I refer not to user-controlled measures to add extra security for internet users, from the most classic one-time password, or two-factor authentication, to the most secure multi-factor authentication methods: but data privacy measures implemented by companies to ensure that peoples’ personal data is protected - no matter what.
225. Your Children's Data Is Being Collected by Educational Technology Companies
 Vista Equity Partners is collecting data on children that go to school.
Vista Equity Partners is collecting data on children that go to school.
226. These Companies Are Collecting Data From Your Car
 Most drivers have no idea what data is being transmitted from their vehicles, let alone who exactly is collecting, analyzing, and sharing that data...
Most drivers have no idea what data is being transmitted from their vehicles, let alone who exactly is collecting, analyzing, and sharing that data...
227. Ongoing Challenges With Artificial Intelligence in Growth Marketing
 AI and machine learning are starting to hit their stride, but there are still many challenges ahead for the top industry trends for AI marketing.
AI and machine learning are starting to hit their stride, but there are still many challenges ahead for the top industry trends for AI marketing.
228. How AWS Misconception Resulted in Detection of 5 Million Personal Records
 A misconception of users had led to over five million records containing personal identifying information to be left on an AWS service, a serious leak.
A misconception of users had led to over five million records containing personal identifying information to be left on an AWS service, a serious leak.
229. The Importance of HIPAA Compliance to Protect Sensitive Data
 HIPAA Compliance mainly aims to prevent any kind of misuse or illegal disclosure of protected health information (PHI).
HIPAA Compliance mainly aims to prevent any kind of misuse or illegal disclosure of protected health information (PHI).
230. Keeping Your Privacy Secure in a Digital Jungle
 Privacy, cybersecurity and safety in the world of Social Media and constant surveillance. How can you protect yourself from the digital dangers?
Privacy, cybersecurity and safety in the world of Social Media and constant surveillance. How can you protect yourself from the digital dangers?
231. Could School Surveillance Tools Put Teens at Risk?
 Health advocates and civil rights groups are warning that school surveillance software can be weaponized against teens who seek reproductive care.
Health advocates and civil rights groups are warning that school surveillance software can be weaponized against teens who seek reproductive care.
232. Blueprint of an EFSS Phishing Attack

233. A Quick Introduction to Federated Learning of Cohorts [FloC]
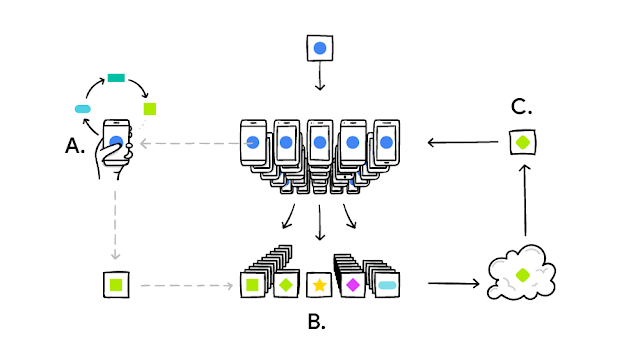 Federated Learning is a relatively new machine learning technique that decentralizes the training of data from one central machine to multiple devices.
Federated Learning is a relatively new machine learning technique that decentralizes the training of data from one central machine to multiple devices.
234. Putting the Blinders on AI
 Want to avoid an insurrection or genocide? Disconnect AI from centralized databases now!
Want to avoid an insurrection or genocide? Disconnect AI from centralized databases now!
235. Centralized vs Decentralized Networks
236. There Are More Risks Associated With SaaS Data Security Than Potential GDPR Fines
 The growing reliance on SaaS business calls for an improvement in security. On occasions, data security can be of existential importance to organizations.
The growing reliance on SaaS business calls for an improvement in security. On occasions, data security can be of existential importance to organizations.
237. Distributed Governance and Anonymity: A Bad Idea
 One of the big debates in the Genesis DAO started by DAOstack was the question of anonymity. Should people be able to make proposals and ask for budgets without providing a real identity?
One of the big debates in the Genesis DAO started by DAOstack was the question of anonymity. Should people be able to make proposals and ask for budgets without providing a real identity?
238. The Privacy Paradox: Do We Really Have Nothing to Hide?
 Privacy is not something we put a lot of attention or effort into keeping, but maybe we should.
Privacy is not something we put a lot of attention or effort into keeping, but maybe we should.
239. When Messenger Apps Adopt Fintech: Privacy Issues and Implications
 There are many ways in which the world is divided up: borders, differing cultures, and even vast masses of water serve to partition the globe. Preference per region for Messenger apps is one of the less initially visible ways this is done.
There are many ways in which the world is divided up: borders, differing cultures, and even vast masses of water serve to partition the globe. Preference per region for Messenger apps is one of the less initially visible ways this is done.
240. How Big Tech Influences Privacy Laws
 The Markup reviewed public hearing testimony in all 31 states that have considered consumer data privacy legislation since 2021 and found a campaign by Big Tech
The Markup reviewed public hearing testimony in all 31 states that have considered consumer data privacy legislation since 2021 and found a campaign by Big Tech
241. Can a Decentralized Social Network Give Facebook A Run for Its Money
 Not long ago, Apple’s co-founder Steve Wozniak said people should quit Facebook. Dissatisfaction with the world's biggest social network is growing as more issues regarding its privacy, data, and content policies are emerging.
Not long ago, Apple’s co-founder Steve Wozniak said people should quit Facebook. Dissatisfaction with the world's biggest social network is growing as more issues regarding its privacy, data, and content policies are emerging.
242. Smart Cities Raise Data Privacy Concerns
 Should you be excited about smart cities or concerned about your privacy and data? I go through three of the ten privacy principles (PIPEDA) and their effects.
Should you be excited about smart cities or concerned about your privacy and data? I go through three of the ten privacy principles (PIPEDA) and their effects.
243. Is COVID-19 Turning Into A War On Privacy?
 The old axiom that one should never waste a good crisis, appears to be the driving force behind one of Big-Tech's biggest rivalries seen in Google and Apple that are now working together in an unorthodox partnership to create the ultimate privacy buster - a coronavirus tracking app.
The old axiom that one should never waste a good crisis, appears to be the driving force behind one of Big-Tech's biggest rivalries seen in Google and Apple that are now working together in an unorthodox partnership to create the ultimate privacy buster - a coronavirus tracking app.
244. The Use of VPNs Is Spreading in New Zealand's Universities
 It's no secret that VPNs have become very popular lately, but... what very few people know is that the use of VPNs in universities has skyrocketed in recent times. As reported by vpnetic, VPN usage in New Zealand has almost doubled since the beginning of 2020.
It's no secret that VPNs have become very popular lately, but... what very few people know is that the use of VPNs in universities has skyrocketed in recent times. As reported by vpnetic, VPN usage in New Zealand has almost doubled since the beginning of 2020.
245. Data Storage Security: 5 Best Practices to Secure Your Data

246. 5 Data Breach Safety Measures That are Essential to Every Business
 Data breaches can tank even the most successful businesses. Here are the 5 most important things your business should do after a data breach.
Data breaches can tank even the most successful businesses. Here are the 5 most important things your business should do after a data breach.
247. Darkweb Community MagBO Sells Data Stolen From Over 20k Websites
 MagBO, the Russian-speaking dark web marketplace for trading in backdoored websites, continues to grow exponentially. In less than two years, the collection of leaks grew from around 3,000 in September 2018 to 26,605 in February 2020.
MagBO, the Russian-speaking dark web marketplace for trading in backdoored websites, continues to grow exponentially. In less than two years, the collection of leaks grew from around 3,000 in September 2018 to 26,605 in February 2020.
248. Data Lineage is Like Untangling a Ball of Yarn
 Data lineage is a technology that retraces the relationships between data assets. 'Data lineage is like a family tree but for data'
Data lineage is a technology that retraces the relationships between data assets. 'Data lineage is like a family tree but for data'
249. Artificial Intelligence and Online Privacy: Blessing and a Curse
 Artificial Intelligence (AI) is a beautiful piece of technology made to seamlessly augment our everyday experience. It is widely utilized in everything starting from marketing to even traffic light moderation in cities like Pittsburg. However, swords have two edges and the AI is no different. There are a fair number of upsides as well as downsides that follow such technological advancements.
Artificial Intelligence (AI) is a beautiful piece of technology made to seamlessly augment our everyday experience. It is widely utilized in everything starting from marketing to even traffic light moderation in cities like Pittsburg. However, swords have two edges and the AI is no different. There are a fair number of upsides as well as downsides that follow such technological advancements.
250. Deconstructing the Difference Between Web 2.0 and Web 3.0
 You may have heard the term web 3.0 and may have even heard it described, but you may not have seen real-life applications as of yet
You may have heard the term web 3.0 and may have even heard it described, but you may not have seen real-life applications as of yet
251. How Can You Minimize Your Online Footprint

252. 4 Technology Developments for the End of 2022 and Christmas
 A look at four technology developments for the end of 2022 and Christmas.
A look at four technology developments for the end of 2022 and Christmas.
253. How to Hack Text Messages via SMS Tracker Apps
 SMS tracker apps come with a wide range of valuable features, and they are usually quick and easy to install.
SMS tracker apps come with a wide range of valuable features, and they are usually quick and easy to install.
254. How Am I Being Tracked Online? A Story.
 How are users being tracked online even when taking privacy precautions? What tools are Meta and others using to target you with ads?
How are users being tracked online even when taking privacy precautions? What tools are Meta and others using to target you with ads?
255. The Need for Privacy Protection in Computer Vision Applications
 This article describes why privacy concerns should be top of mind while building or adopting computer vision based applications
This article describes why privacy concerns should be top of mind while building or adopting computer vision based applications
256. Data Science Teams are Doing it Wrong: Putting Technology Ahead of People
 Data Science and ML have become competitive differentiator for organizations across industries. But a large number of ML models fail to go into production. Why?
Data Science and ML have become competitive differentiator for organizations across industries. But a large number of ML models fail to go into production. Why?
257. How to Perform a Cyber Security Risk Assessment: A Step-by-Step Guide
258. A Complete Look at Profila & Zero-knowledge Advertising
 In this post we’ll look at how brands handle user data, the Profila platform, how it works and Zero-Knowledge Advertising.
In this post we’ll look at how brands handle user data, the Profila platform, how it works and Zero-Knowledge Advertising.
259. How Organizations Can Build Trust And Security Through Digital Identities
 Exploring how we can solve the issue of trust by securely identifying people online, while providing digital convenience and a seamless customer experience.
Exploring how we can solve the issue of trust by securely identifying people online, while providing digital convenience and a seamless customer experience.
260. Data and Analytics Predictions for 2020 [A Top 5 List]
 It would be no exaggeration to say that the capacity of technology to advance itself is proceeding at a faster rate than our ability to process these changes all at the same time. This is both amazing and alarming in the same breath.
It would be no exaggeration to say that the capacity of technology to advance itself is proceeding at a faster rate than our ability to process these changes all at the same time. This is both amazing and alarming in the same breath.
261. What's in Store for Privacy and Personal Data Protection in 2022?
 2021 saw many advancements in internet privacy, what does 2022 have in store?
2021 saw many advancements in internet privacy, what does 2022 have in store?
262. Personal Data Protection: Mission Impossible?
 4.1 user billion records exposed in the first half of 2019: how’s that for data protection?
4.1 user billion records exposed in the first half of 2019: how’s that for data protection?
263. Good Ways To Make Your Data More Secure
 Data security is a business challenge and a business opportunity, not a mere technical task for your IT department.
Data security is a business challenge and a business opportunity, not a mere technical task for your IT department.
264. Data Privacy is Becoming More Important for Users in 2022
 A look at how data privacy is becoming more important for users in 2022
A look at how data privacy is becoming more important for users in 2022
265. Confidential Computing: How Intel SGX is Helping to Achieve It
 Learn more about confidential computing and how Intel SGX is used to encrypt sensitive data in memory, enabling compliant collaboration between organizations.
Learn more about confidential computing and how Intel SGX is used to encrypt sensitive data in memory, enabling compliant collaboration between organizations.
266. Introduction to Account Aggregators: 8 Common Myths Debunked
 Just like UPI helps people share money between bank accounts seamlessly, the new Account Aggregator framework (AA) will help people share their financial data quickly and safely.
Just like UPI helps people share money between bank accounts seamlessly, the new Account Aggregator framework (AA) will help people share their financial data quickly and safely.
267. A Guide to Conducting Privacy Risk Assessments
 Let’s dive into the details of what a privacy risk assessment is, why it can benefit businesses, and how to conduct one.
Let’s dive into the details of what a privacy risk assessment is, why it can benefit businesses, and how to conduct one.
268. How to Revolutionize Data Security Through Homomorphic Encryption
 For decades, we have benefited from modern cryptography to protect our sensitive data during transmission and storage. However, we have never been able to keep the data protected while it is being processed.
For decades, we have benefited from modern cryptography to protect our sensitive data during transmission and storage. However, we have never been able to keep the data protected while it is being processed.
269. Technology: It Was Meant To Be Humanity's Best Friend, Not Worst Enemy
 Technology at its purest form should be beneficial to humanity. It should make our lives easier. It shouldn't be used for evil implications. I don't want to go on a whole philosophical rant here, but some things seem needed.
Technology at its purest form should be beneficial to humanity. It should make our lives easier. It shouldn't be used for evil implications. I don't want to go on a whole philosophical rant here, but some things seem needed.
270. Cybersecurity Takeaways From the Pandemic and Solutions for 2021
 In 2020, Cybersecurity has become more important than ever for businesses all over the world. Here's how to protect your data from cyberattacks going forward.
In 2020, Cybersecurity has become more important than ever for businesses all over the world. Here's how to protect your data from cyberattacks going forward.
271. The UK and Taiwanese Governments are Using AI as a Fundamental Cybersecurity Tool: How is it Used?
 The UK and Taiwanese Governments are Using AI as a Fundamental Cyber Security Tool.
The UK and Taiwanese Governments are Using AI as a Fundamental Cyber Security Tool.
272. Is There A Middle Ground Between Privacy and Convenience?

273. A Guide To Web Security Testing: Part 1 - Mapping Contents
 Beginners guide to web security testing for penetration testers and bug bounty hunters.
Beginners guide to web security testing for penetration testers and bug bounty hunters.
274. 5 Reasons Why Privacy by Design is More Critical Than Ever in 2023
 The more manual work is involved in managing data privacy, the greater the risk of costly data and compliance breaches.
The more manual work is involved in managing data privacy, the greater the risk of costly data and compliance breaches.
275. Ensuring Privacy with Zero-party Data
 Zero-party data is the future of data collection because it bridges the gap between advertising needs and consumers’ concerns about privacy.
Zero-party data is the future of data collection because it bridges the gap between advertising needs and consumers’ concerns about privacy.
276. This Online Abortion Pill Provider Used Tracking Tools That Gave Powerful Companies Your Data
 The trackers notified Google, Facebook’s parent company Meta, payments processor Stripe, and four analytics firms when users visited its site.
The trackers notified Google, Facebook’s parent company Meta, payments processor Stripe, and four analytics firms when users visited its site.
277. Using OSINT for Maritime Intelligence
 According to Naval Dome, the maritime industry has seen a 900% increase in cyber-attacks since 2017
According to Naval Dome, the maritime industry has seen a 900% increase in cyber-attacks since 2017
278. Great Methods To Create A Password File To Prevent Brute-Force Attacks
 Brute-forcing a really important method that a hacker or a pentester must be aware of and he will use in various places.
Brute-forcing a really important method that a hacker or a pentester must be aware of and he will use in various places.
279. Currency-As-A-Model for Reframing The Debate on Data Privacy: A Thought Experiment
 Using Currency as a Model for Reframing The Debate on Data Privacy. A thought experiment.
Using Currency as a Model for Reframing The Debate on Data Privacy. A thought experiment.
280. 5 Ways to Ensure You Aren’t Sharing Your Workplace Data
 With so much of our lives online, it's too easy for us to make a mistake and accidentally share our workplace data. These easy methods keep your data safe.
With so much of our lives online, it's too easy for us to make a mistake and accidentally share our workplace data. These easy methods keep your data safe.
281. Is Google Benefiting From Banning Third-party Cookies
 Google has announced the depreciation of third-party cookies will be delayed – again.
Google has announced the depreciation of third-party cookies will be delayed – again.
282. A GAN approach To Synthetic Time-Series Data
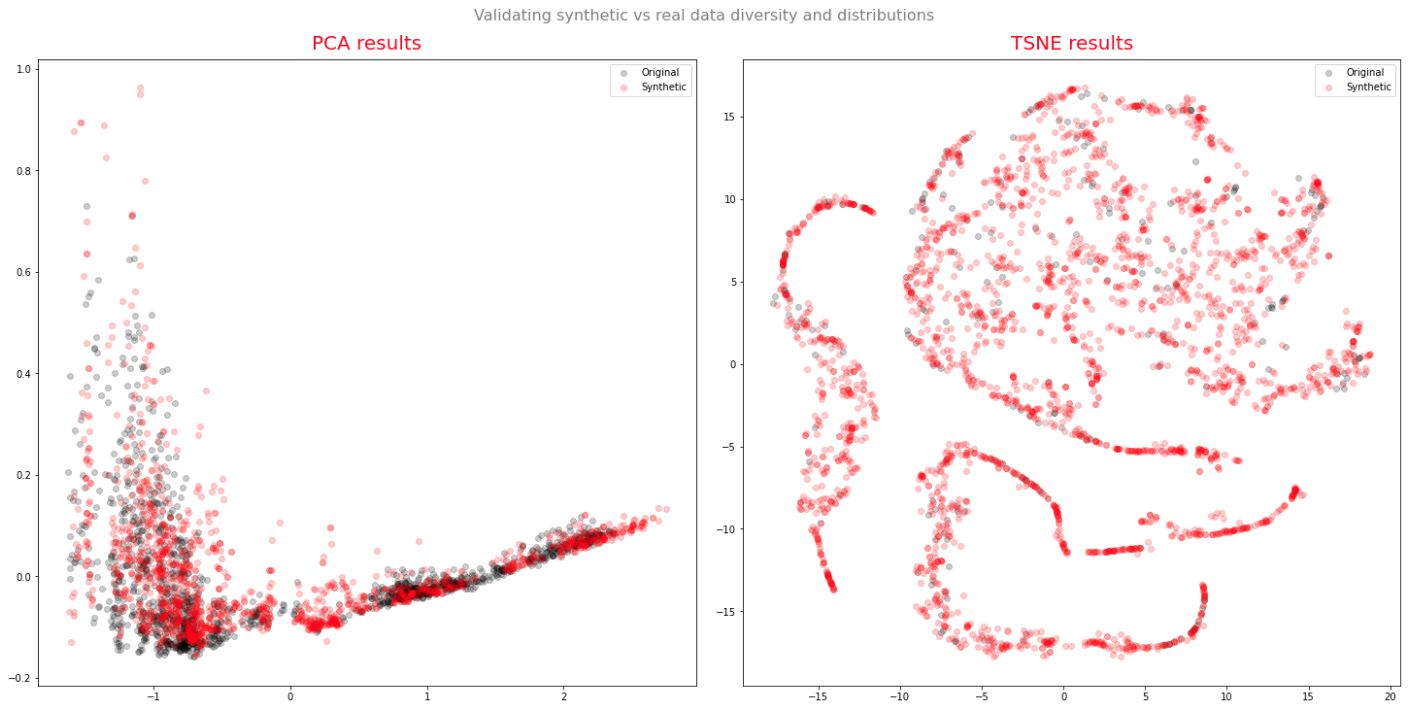 Although sequential data is pretty common to be found and highly useful, there are many reasons that lead to not leverage it
Although sequential data is pretty common to be found and highly useful, there are many reasons that lead to not leverage it
283. How to Protect Folders And Files in Windows using Passwords
 Sometimes, we need to apply a bit of extra protection to the data on our computers. We might want to protect our tax records from prying eyes, or lock away business plans from our competitors. Or we might just want to ensure that any children with access to our device can't access inappropriate content.
Sometimes, we need to apply a bit of extra protection to the data on our computers. We might want to protect our tax records from prying eyes, or lock away business plans from our competitors. Or we might just want to ensure that any children with access to our device can't access inappropriate content.
284. NextGen Open Blockchains Are Building New DeFi Security and Privacy Standards
 Next generation blockchains developing open, secure and privacy-preserving DeFi platforms
Next generation blockchains developing open, secure and privacy-preserving DeFi platforms
285. Everyone Works for Facebook and Google
 Imagine a car factory where nameless workers in a sprawling complex make expensive cars all day and all night. Thousands of shiny, new expensive cars move off the line every millisecond and are shipped instantly all over the world to wealthy buyers, generating $195 million of profit daily for the car company.
Imagine a car factory where nameless workers in a sprawling complex make expensive cars all day and all night. Thousands of shiny, new expensive cars move off the line every millisecond and are shipped instantly all over the world to wealthy buyers, generating $195 million of profit daily for the car company.
286. Consumer Identity Management is an important security tool for an IoT ecosystem
 The industry is just getting started with IoT design and deployment. Now is a good time to think about how CIAM fits with other security services you require.
The industry is just getting started with IoT design and deployment. Now is a good time to think about how CIAM fits with other security services you require.
[287. Differential Privacy with Tensorflow 2.0 : Multi class Text Classification
Privacy](https://hackernoon.com/differential-privacy-with-tensorflow-20-multi-class-text-classification-privacy-yk7a37uh)
 Introduction
Introduction
288. Revolutionizing the Value of Data with cheqd
 In this Slogging AMA, the team at Cheqd joined us to explain why and how their platform enables the average user and business to take control of their data.
In this Slogging AMA, the team at Cheqd joined us to explain why and how their platform enables the average user and business to take control of their data.
289. Web3.0 Powered Privacy: Decentralization for More Control and Transparency
 A look at the importance of data privacy in today's digital age, where personal information is being collected, used, and shared at an unprecedented rate.
A look at the importance of data privacy in today's digital age, where personal information is being collected, used, and shared at an unprecedented rate.
290. Italy Launches Contact Tracing App; Proves We Shouldn't Compromise On Privacy?
 Starting on the 15th of June, the Italian Government enabled nationwide downloads of their Contact Tracing app, Immuni. The app allows for effortless tracing of SARS-Cov-2 virus.
Starting on the 15th of June, the Italian Government enabled nationwide downloads of their Contact Tracing app, Immuni. The app allows for effortless tracing of SARS-Cov-2 virus.
291. What Could Have Prevented 2020's Massive Twitter Hack?
 Attacks and account take-overs like the recent Twitter hack are completely avoidable. Enterprises must implement biometric multi-factor authentication to ensure that only the right users have access to the right systems at all times. If they don’t, users will continue being vulnerable to hacks and scams.
Attacks and account take-overs like the recent Twitter hack are completely avoidable. Enterprises must implement biometric multi-factor authentication to ensure that only the right users have access to the right systems at all times. If they don’t, users will continue being vulnerable to hacks and scams.
292. Self-Sovereign Identity: What’s the Big Deal?
 Want to own your online data? Want to decide where it's stored and how it's used. Self-sovereign identity can do it for you. Read on to see why it's a big deal.
Want to own your online data? Want to decide where it's stored and how it's used. Self-sovereign identity can do it for you. Read on to see why it's a big deal.
293. How to Choose the Right Hyper-V Backup Strategy
 This post discusses the main data protection strategies that can help you keep your Hyper-V data secure at all times.
This post discusses the main data protection strategies that can help you keep your Hyper-V data secure at all times.
294. Our Social Media is Broken & No One Knows How to Fix It
 While I sit down to write, like any procrastinating writer of our times, I look for excuses that will keep me from the task at hand. It could be the windows and the weather (perhaps I need a pullover) or the more modern version of it – social media.
While I sit down to write, like any procrastinating writer of our times, I look for excuses that will keep me from the task at hand. It could be the windows and the weather (perhaps I need a pullover) or the more modern version of it – social media.
295. The Unrelenting Spies in your Pocket and How to Get Rid of Them
 Privacy...that mythical unicorn many chase but only a few manage to catch. Though elusive, privacy is a pressing issue in a hyper-connected world where a handful of companies control the information you consume and the information you produce.
Privacy...that mythical unicorn many chase but only a few manage to catch. Though elusive, privacy is a pressing issue in a hyper-connected world where a handful of companies control the information you consume and the information you produce.
296. How Decentralized Identifiers Will Shape the Future of Identity
 Exploring the W3C DID specification to enable Web3.0 identity solutions...
Exploring the W3C DID specification to enable Web3.0 identity solutions...
297. The New Mapique Perspective In TagSpaces 3.3: A Quick Guide
 Privacy focused geo-tagging, and location based file organisation in your favourite file manager.
Privacy focused geo-tagging, and location based file organisation in your favourite file manager.
298. Introducing CloseKnit: Healthy Community For Neighbours

299. Data Privacy: Why The Existing Architecture is in Dire Need of Evolution
 Data is to the 21st century what oil was for the 20th century. The importance of data in the 21st century is conspicuous. Data is behind the exponential growth witnessed in the digital age. Increased access to data, through the internet and other technologies, has made the world a global village.
Data is to the 21st century what oil was for the 20th century. The importance of data in the 21st century is conspicuous. Data is behind the exponential growth witnessed in the digital age. Increased access to data, through the internet and other technologies, has made the world a global village.
300. Understanding Russia’s Actions in Ukraine through the Digital Ruble
 Global government leaders can use the digital ruble as a digital framework to understand the context of Russia's current military actions against Ukraine.
Global government leaders can use the digital ruble as a digital framework to understand the context of Russia's current military actions against Ukraine.
301. True Privacy is When Users Decide Who Sees and Uses Their Data: Unhased #24
 Unhashed is a QnA series where I speak with top execs of new and established blockchain projects to unravel the mystery of blockchain & crypto.
Unhashed is a QnA series where I speak with top execs of new and established blockchain projects to unravel the mystery of blockchain & crypto.
302. What Is a VPN and What Are Its Alternatives?
 Are VPNs really essential for an average user in 2021? Read on to find out about common issues with VPNs, as well as possible alternatives to them.
Are VPNs really essential for an average user in 2021? Read on to find out about common issues with VPNs, as well as possible alternatives to them.
303. Identify Wechat's TxBugReport File on your PC Through These Simple Steps
 In this post, we will learn easy steps to turn off the txbugreport.exe process running in your Computer and occupying more memory and prevent this .exe file from sending automated bug reports to Tencent Computer Systems.
In this post, we will learn easy steps to turn off the txbugreport.exe process running in your Computer and occupying more memory and prevent this .exe file from sending automated bug reports to Tencent Computer Systems.
304. Online Privacy is Not an Option: It's a Necessity

305. More Secure Technology Can Backfire: Here's How to Avoid Security Fatigue
 4 ways to eliminate "security fatigue": simpler tech, biometrics as seamless authentication, password elimination, and "less is more"
4 ways to eliminate "security fatigue": simpler tech, biometrics as seamless authentication, password elimination, and "less is more"
306. How Facebook tracks you on Android (even if you don't have a Facebook account)
 Suppose you’ve picked up an Android phone on the street and you saw the 4 apps above. Can you guess the profile of the phone user?
Suppose you’ve picked up an Android phone on the street and you saw the 4 apps above. Can you guess the profile of the phone user?
307. Is Facebook Putting Digital Identity At Risk With Libra? Here’s Why It Raises Privacy Concerns
 Last month, Facebook finally disclosed details of its much-hyped cryptocurrency, Libra. After generating an immense amount of chatter, the company announced that the digital currency, set to launch in 2020, will enable people to buy things or send money to others with almost zero fees.
Last month, Facebook finally disclosed details of its much-hyped cryptocurrency, Libra. After generating an immense amount of chatter, the company announced that the digital currency, set to launch in 2020, will enable people to buy things or send money to others with almost zero fees.
308. "Don't Be Evil," They Said: Android Is Tracking Us With No Way to Opt-Out
 Researchers recently proved that the phrase is not just a slogan but crucial for protecting our privacy, considering that Google is everywhere for everyone now.
Researchers recently proved that the phrase is not just a slogan but crucial for protecting our privacy, considering that Google is everywhere for everyone now.
309. Account Aggregators: What Are They and How Will They Change the Fintech Ecosystem?
 Account Aggregators (AAs) are about to take the fintech market by storm. Remember how UPI completely changed how people send money? No more awkwardly splitting restaurant bills, or digging for exact change to pay off that friend who's been bugging you for months.
Account Aggregators (AAs) are about to take the fintech market by storm. Remember how UPI completely changed how people send money? No more awkwardly splitting restaurant bills, or digging for exact change to pay off that friend who's been bugging you for months.
310. You're Never Fully Protected Using iMessage
 This time, I would like to take a closer look at another popular messaging platform — Apple iMessage.
This time, I would like to take a closer look at another popular messaging platform — Apple iMessage.
311. California's Current Privacy Rights Under CCPA
 California recently passed a sweeping privacy law that makes it the most privacy forward state in the nation. But, until it gets implemented, there is this thing privacy framework (the CCPA) is the law of the land.
California recently passed a sweeping privacy law that makes it the most privacy forward state in the nation. But, until it gets implemented, there is this thing privacy framework (the CCPA) is the law of the land.
312. Attorney Adam Williams Gives Advice on Data Breaches and Class-Action Suits
 Technology is changing incredibly quickly, and as a consumer, it can often be difficult to stay on the front lines of keeping yourself secure while using all of the technological marvels that the world has to offer. Data breaches and privacy breaches are reported every day in the news, making the private information of thousands vulnerable to identity theft and the consequences that come with it.
Technology is changing incredibly quickly, and as a consumer, it can often be difficult to stay on the front lines of keeping yourself secure while using all of the technological marvels that the world has to offer. Data breaches and privacy breaches are reported every day in the news, making the private information of thousands vulnerable to identity theft and the consequences that come with it.
313. Do Paperless Offices Face More Security Risks?
 Going paperless is becoming increasingly possible for businesses, but are there risks involved? Here are the benefits and risks of going paperless.
Going paperless is becoming increasingly possible for businesses, but are there risks involved? Here are the benefits and risks of going paperless.
314. 3 Ways To Protect Company Data From Being Exposed By Your Own Employees
 When people think about data leaks, they tend to assume the cause of the threat came from outside the company.
When people think about data leaks, they tend to assume the cause of the threat came from outside the company.
315. Musk's Lawyers Repeatedly Accused Twitter of Failure to Disclose Data in Failed Attempt to Back Out
 Twitter v. Elon Musk Court Filing is part of our Legal PDF series. Part 18 of 31: FACTUAL ALLEGATIONS -Musk grasps for an out - Defendants’ lawyer letters
Twitter v. Elon Musk Court Filing is part of our Legal PDF series. Part 18 of 31: FACTUAL ALLEGATIONS -Musk grasps for an out - Defendants’ lawyer letters
316. How Does a VPN Work to Protect Your Privacy?
 VPNs secure your online activity. In this article, you can learn what the best VPN protocol is, how AES-256 encryption works, and what VPNs really protect from.
VPNs secure your online activity. In this article, you can learn what the best VPN protocol is, how AES-256 encryption works, and what VPNs really protect from.
317. The Decentralized Internet Is Bigger than Decentralized Money
 A look at why decentralized internet is bigger than decentralized money
A look at why decentralized internet is bigger than decentralized money
318. What Does Google's Third-Party Cookie Ban Mean to Your Privacy?
 Google is making the final push to completely ban third-party cookies on the most popular internet browser, Google Chrome, by 2022.
Google is making the final push to completely ban third-party cookies on the most popular internet browser, Google Chrome, by 2022.
319. Ensuring Security in Your SaaS Applications [An Overview]

320. Who are the Data Brokers Spending Big Bucks to Lobby Congress
 Data brokers’ millions of dollars in lobbying spending in 2020 rivaled that of some Big Tech firms with serious consequences for everyone else in the world.
Data brokers’ millions of dollars in lobbying spending in 2020 rivaled that of some Big Tech firms with serious consequences for everyone else in the world.
321. GDPR's Two-Tier Internet: One Year On
 It’s been over a year since the GDPR came into effect, and at least five since it was first debated seriously. For much of that time it was discussed as a global game-changer, yet the predicted earth-shaking effects of its implementation — billion-dollar fines, the end of data exploitation by rogue firms, high-profile court cases — have largely yet to materialize. Instead, the landscape of the internet has changed in more subtle and complex ways which could not have been predicted by pundits, and it’s affecting businesses of every size.
It’s been over a year since the GDPR came into effect, and at least five since it was first debated seriously. For much of that time it was discussed as a global game-changer, yet the predicted earth-shaking effects of its implementation — billion-dollar fines, the end of data exploitation by rogue firms, high-profile court cases — have largely yet to materialize. Instead, the landscape of the internet has changed in more subtle and complex ways which could not have been predicted by pundits, and it’s affecting businesses of every size.
322. How to Deal with Tech Trust Deficit
 We’re more dependent on tech and e-commerce than ever before, and customers want to know that brands are protecting their data and privacy.
We’re more dependent on tech and e-commerce than ever before, and customers want to know that brands are protecting their data and privacy.
323. How The Rise of Vulnerabilities Has Shaped Modern Patch Management Practices
 Vulnerabilities can seriously damage company’s operations and reputation, but you can protect it by automating live patching of infrastructures with KernelCare.
Vulnerabilities can seriously damage company’s operations and reputation, but you can protect it by automating live patching of infrastructures with KernelCare.
324. Understanding Usage Control in Smart Cities: Smart Health Use Case
 Usage control provides fine grained access to data and resources through restricting access to smart health resources.
Usage control provides fine grained access to data and resources through restricting access to smart health resources.
325. Government Adoption of Decentralized Technology
 Can decentralization exist in the governmental sector? Let's explore whether or not that's within the realm of possibility.
Can decentralization exist in the governmental sector? Let's explore whether or not that's within the realm of possibility.
326. 10 Reasons Wordpress Sites Get Hacked and How to Avoid Them
 WordPress, the most popular CMS platform among business owners, and hackers' most favorite platform to mess up.
There have been a lot of data breaches in recent times. Beyond the big names, even small business owners lost their value. Security breaches, unfortunately, are quite real.
WordPress, the most popular CMS platform among business owners, and hackers' most favorite platform to mess up.
There have been a lot of data breaches in recent times. Beyond the big names, even small business owners lost their value. Security breaches, unfortunately, are quite real.
327. The Future Of Email on The Blockchain Launches An IEO To Accelerate Its Development
 SafePost, the innovative and secure solution alternative to traditional emails and document storage (a market of more than $ 200 billion / year with more than 3.5 billion users), will hold its first-ever Initial Exchange Offering (IEO) through the P2PB2B launchpad from March
16th to April 19th, 2020.
SafePost, the innovative and secure solution alternative to traditional emails and document storage (a market of more than $ 200 billion / year with more than 3.5 billion users), will hold its first-ever Initial Exchange Offering (IEO) through the P2PB2B launchpad from March
16th to April 19th, 2020.
328. Healthcare Tech is Out-Of-Date: Identity Access Management Can Revive The Old-School System
 Healthcare professionals are still using paper-based systems in order to track and maintain patient records. That's where Identity Access Management can help.
Healthcare professionals are still using paper-based systems in order to track and maintain patient records. That's where Identity Access Management can help.
329. Will Mask-Scanning Tech Help Stop COVID or Create A Privacy Disaster?
 Will the surveillance measures we take to encourage protective behaviors and prevent the spread of disease ultimately expose us to even greater (privacy) risks?
Will the surveillance measures we take to encourage protective behaviors and prevent the spread of disease ultimately expose us to even greater (privacy) risks?
330. Why Compliance and Data Protection is Important in the Blockchain Space
 Interview discussing why compliance and data protection is important in the blockchain space
Interview discussing why compliance and data protection is important in the blockchain space
331. Cybersecurity is a Big Competitive Advantage. Secure Your Win.
 A majority of America's small business owners aren't worried about being the victim of a cyberattack. Why?
A majority of America's small business owners aren't worried about being the victim of a cyberattack. Why?
332. You’ve Never Heard Of These Sites, But They Know A Lot About You
 A Marriage And A Funeral
A Marriage And A Funeral
333. My Thoughts on Stocktwits, Censorship, and Online Harassment
 Stocktwits as a tool really excited me in the beginning, but I was awakened to a reality of things that are quite toxic. What inspired me, is that you seem to have had founders with an innovative vision in terms of creating a community for stocks and stock tickers. However, this community may have become a safe haven for trolling, internet harassment, defamation, stock dumping, privacy concerns, and much more. This isn't to personally come after the founders or anything like this, as I warrant a healthy discussion on how to improve big tech. We do need to look at the problems though.
Stocktwits as a tool really excited me in the beginning, but I was awakened to a reality of things that are quite toxic. What inspired me, is that you seem to have had founders with an innovative vision in terms of creating a community for stocks and stock tickers. However, this community may have become a safe haven for trolling, internet harassment, defamation, stock dumping, privacy concerns, and much more. This isn't to personally come after the founders or anything like this, as I warrant a healthy discussion on how to improve big tech. We do need to look at the problems though.
334. How to Share Google Docs Securely with a Google Apps Script
 Add Additional Data Protections to G Suite with the Virtru SDK
Add Additional Data Protections to G Suite with the Virtru SDK
335. Privacy In The Time of Coronavirus

336. My Data! My Rules! How True is That?
 The Rise Of A New Data Governance Landscape In The Midst Of Heightened Data Privacy Concerns
The Rise Of A New Data Governance Landscape In The Midst Of Heightened Data Privacy Concerns
337. Meet the Writer: OneRep CEO Dimitri Shelest on Writing and Online Privacy
 OneRep CEO and Hackernoon contributor Dimitri Shelest shares his views on online privacy, his entrepreneurship experience, and the reasons that made him write.
OneRep CEO and Hackernoon contributor Dimitri Shelest shares his views on online privacy, his entrepreneurship experience, and the reasons that made him write.
338. Is the Data We Share with Pay Apps Private at all
 Using a payment app of any kind, no matter how privacy-preserving it is, always introduces a middleman: an agent that uses data to execute a demand.
Using a payment app of any kind, no matter how privacy-preserving it is, always introduces a middleman: an agent that uses data to execute a demand.
339. European User Data is Shared 376 Times Per Day on Average
 Violation of private data and its commercial exchange are recurrent issues in the online world. In this thread, our community discusses personal data share.
Violation of private data and its commercial exchange are recurrent issues in the online world. In this thread, our community discusses personal data share.
340. A Proposal for Bisq + Social Trading: My Thoughts and Ideas
 So quite a while ago, we have made a proposal Bisq. It got rejected, and to be honest, we don't blame them. We had an overarching goal to make a social trading integration within the Bisq platform and allow for this great use of blockchain tech and a decentralized financial ecosystem. It was all fairytales, and bliss, except for one thing. How will this possibly work?
So quite a while ago, we have made a proposal Bisq. It got rejected, and to be honest, we don't blame them. We had an overarching goal to make a social trading integration within the Bisq platform and allow for this great use of blockchain tech and a decentralized financial ecosystem. It was all fairytales, and bliss, except for one thing. How will this possibly work?
341. What Happens When You Get Sick Right Now?
 We are living in a weird time. Day by day we see more & more people coughing and getting sick, our neighbors, coworkers on Zoom calls, politicians, etc… But here’s when it becomes really, really scary — when you become one of “those” and have no clue what to do. Your reptile brain activates, you enter a state of panic, and engage complete freakout mode. That’s what happened to me this Monday, and I’m not sure I’m past this stage.
We are living in a weird time. Day by day we see more & more people coughing and getting sick, our neighbors, coworkers on Zoom calls, politicians, etc… But here’s when it becomes really, really scary — when you become one of “those” and have no clue what to do. Your reptile brain activates, you enter a state of panic, and engage complete freakout mode. That’s what happened to me this Monday, and I’m not sure I’m past this stage.
342. Main Security Concepts and the Importance of Data Privacy
 Trigger warning: authoritarianism, state surveillance, the Holocaust. If you want to avoid these topics, please jump to the last paragraph of this introduction, starting with ‘Enough about the depressing stuff.’
Trigger warning: authoritarianism, state surveillance, the Holocaust. If you want to avoid these topics, please jump to the last paragraph of this introduction, starting with ‘Enough about the depressing stuff.’
343. Sora Enables Shipping While Keeping Your Address Private
 Sora is a privacy-preserving, addressless shipping tool that enables individuals and businesses to send and receive packages without revealing their address.
Sora is a privacy-preserving, addressless shipping tool that enables individuals and businesses to send and receive packages without revealing their address.
344. How China and El Salvador's Stances on Digital Currencies Highlight Potentially Increasing Relations
 China and El Salvador's seemingly contrasting stances on digital currencies actually align both authoritarian regimes on many levels.
China and El Salvador's seemingly contrasting stances on digital currencies actually align both authoritarian regimes on many levels.
345. Bits and Bytes and Data Delights
 Limarc Ambalina, Ellen Stevens, and Amy Tom chat about data privacy ☠️ Humans are in loooove with the internet, and data production is becoming more rampant and
Limarc Ambalina, Ellen Stevens, and Amy Tom chat about data privacy ☠️ Humans are in loooove with the internet, and data production is becoming more rampant and
346. Exploring Ethical User Data with Datawallet’s New SDK
 On July 8, the Information Commissioner’s Office (ICO) announced the highest GDPR fine ever of £183 million over last year’s data breach at British Airways. The UK’s data watchdog elected to fine the airline as its “poor security arrangements” led to the breach of credit card information, names, addresses, travel booking details, and logins of around 500,000 customers. In recent years, consumers have become wearily accustomed to data breaches of this magnitude.
On July 8, the Information Commissioner’s Office (ICO) announced the highest GDPR fine ever of £183 million over last year’s data breach at British Airways. The UK’s data watchdog elected to fine the airline as its “poor security arrangements” led to the breach of credit card information, names, addresses, travel booking details, and logins of around 500,000 customers. In recent years, consumers have become wearily accustomed to data breaches of this magnitude.
347. How Geofence Warrants Are Affecting The Legal System
 Geofencing itself simply means drawing a virtual border around a predefined geographical area. Data can then be gathered on users who enter that area.
Geofencing itself simply means drawing a virtual border around a predefined geographical area. Data can then be gathered on users who enter that area.
348. Democratizing the New Data Economy in 2023: With Co-Founder of Seagate Technology, Finis Conner
 Big tech firms get their wealth & power from the data they freely collect from users. But new blockchain tech is about to destabilize the entire data landscape.
Big tech firms get their wealth & power from the data they freely collect from users. But new blockchain tech is about to destabilize the entire data landscape.
349. Are Private Search Engines Truly Private?
 As of January 2020, 59% of the global population is connected to the internet.
As of January 2020, 59% of the global population is connected to the internet.
350. What You Should Know About Zero-Party Data
 Zero-party data (ZPD) means a company only collects user data that is freely given. Period. But why would a modern business, raised on the wonders of Big Data, undertake such a foolish philosophy? Maybe because they aren’t fans of financial ruin.
Zero-party data (ZPD) means a company only collects user data that is freely given. Period. But why would a modern business, raised on the wonders of Big Data, undertake such a foolish philosophy? Maybe because they aren’t fans of financial ruin.
351. The Internet Doesn't Talk About The True Cost of Fraud: Here's How To Fix It (And Save >$1M)
 In today’s competitive landscape, businesses have the capacity to save over 1 million USD for every 100,000 users being verified - with processes that mitigate fraud and reduce friction. Here’s how.
In today’s competitive landscape, businesses have the capacity to save over 1 million USD for every 100,000 users being verified - with processes that mitigate fraud and reduce friction. Here’s how.
352. Simple Steps to Follow in Order to Ensure Greater Personal Internet Privacy
 An easy guide to getting started with online privacy.
An easy guide to getting started with online privacy.
353. The Independent Phone : More Privacy, Less Freedom?
 Freedom and privacy tend to go together, but there is a difference. With a more private phone, does it really mean you have more freedom?
Freedom and privacy tend to go together, but there is a difference. With a more private phone, does it really mean you have more freedom?
354. Should We Kick Hardware out of Blockchain?
 You may think blockchain has little to do with hardware. After all, from Bitcoin to Etherum, blockchains are all software-defined. The hardware-based solution is usually more centralized.
You may think blockchain has little to do with hardware. After all, from Bitcoin to Etherum, blockchains are all software-defined. The hardware-based solution is usually more centralized.
355. The Social Dilemma in 2021: Personal Data Privacy
 Big organizations and politicians have a structured data table of everyone's info. They often use your data to get more strategic and sell more to us.
Big organizations and politicians have a structured data table of everyone's info. They often use your data to get more strategic and sell more to us.
356. Understanding Data Usage Control in a Smart City
 Learn how data usage can be controlled in smart cities?
Learn how data usage can be controlled in smart cities?
357. Uber's Safety Woes In London Highlight The Critical Need For Stronger Authentication

358. Biometric Data and Privacy: Here’s What You Need to Know
 Biometrics are metrics that can be used to identify a person. This article discusses biometric data and its privacy concerns & how to protect biometric data.
Biometrics are metrics that can be used to identify a person. This article discusses biometric data and its privacy concerns & how to protect biometric data.
359. What is the Future of Crypto Wallets?
 Web3.0 will redefine how crypto wallets function and gives users more control over their wallets. Read how Web3.0 will shape the future of consumer wallets.
Web3.0 will redefine how crypto wallets function and gives users more control over their wallets. Read how Web3.0 will shape the future of consumer wallets.
360. The Most Expensive Things in Life are “Free of Charge” - Protect Your Data
 Digital Footprint is everywhere online. It is all the activities you do with keyboard and mouse, in addition to what we tap and swipe on our mobile devices.
Digital Footprint is everywhere online. It is all the activities you do with keyboard and mouse, in addition to what we tap and swipe on our mobile devices.
361. Why you will Still Need a VPN in 2022
 Some people say that the VPN is becoming obsolete. But is it really so?
Some people say that the VPN is becoming obsolete. But is it really so?
362. Facebook, WhatsApp, and Your Privacy: What You Need to Know
 Seated at computers in pods organized by work assignments, these hourly workers use special Facebook software to sift through millions of private messages
Seated at computers in pods organized by work assignments, these hourly workers use special Facebook software to sift through millions of private messages
363. How Tenant Screening Companies Can Use Your Speeding Ticket Against You
 Estimated 9/10 landlords, under pressure to ensure their properties are safe, use companies like Rentgrow to perform background checks on potential tenants.
Estimated 9/10 landlords, under pressure to ensure their properties are safe, use companies like Rentgrow to perform background checks on potential tenants.
364. Privacy Alert: How Far Personalization in Advertising Can Go
 Over the past decade, the public has heard it a thousand times:
Over the past decade, the public has heard it a thousand times:
365. Proxy Vs. VPN: What Is Better For Data Protection in 2020
 If you are alive and functioning as a member of society in 2020, chances are you've used a VPN (Virtual Private Network) or a proxy server in the past. It may have been to stream a sports channel not available in your home country, to gain access to a foreign website, or to overcome the one-vote-per-IP address challenges associated with having multiple people in one household trying to do the same thing online.
If you are alive and functioning as a member of society in 2020, chances are you've used a VPN (Virtual Private Network) or a proxy server in the past. It may have been to stream a sports channel not available in your home country, to gain access to a foreign website, or to overcome the one-vote-per-IP address challenges associated with having multiple people in one household trying to do the same thing online.
366. Personal Security Online Is Not Complicated
 Well, if you want to hear something complicated, try to understand the relationship between Beyonce and Jay Z.
Well, if you want to hear something complicated, try to understand the relationship between Beyonce and Jay Z.
367. Ditching Big Tech for a More Decentralised Life
 With privacy and security issues, daily ransomware attacks putting sensitive data at risk of being published - I decided to de-Facebook and de-Google my life.
With privacy and security issues, daily ransomware attacks putting sensitive data at risk of being published - I decided to de-Facebook and de-Google my life.
368. How Piwik built a Google Analytics alternative out of an open-source project
 We discuss Piwik, an open source analytics software and why marketing teams are choosing privacy-oriented alternatives to Google Analytics.
We discuss Piwik, an open source analytics software and why marketing teams are choosing privacy-oriented alternatives to Google Analytics.
369. Be 100% Safe On The Internet Using These Strategies
 The Internet is full of opportunities, useful information, entertainment, and dangers as well. To protect yourself from the latter, you need to follow certain safety rules. Read on to learn how to properly use a home or public Wi-Fi to avoid dangerous malware and protect personal data, and what is the role of nect MODEM in helping you do so.
The Internet is full of opportunities, useful information, entertainment, and dangers as well. To protect yourself from the latter, you need to follow certain safety rules. Read on to learn how to properly use a home or public Wi-Fi to avoid dangerous malware and protect personal data, and what is the role of nect MODEM in helping you do so.
370. 5 Most Important Directions In Which Tech Industry Develops In 2021
 Stay competitive within the COVID-19 landscape. Take a look at our findings on what trends will shape the IT industry in 2021.
Stay competitive within the COVID-19 landscape. Take a look at our findings on what trends will shape the IT industry in 2021.
371. Is Your Zoom Meeting Really End-to-End Encrypted?
 What do you do when your product isn’t encrypted? Change how encryption to is commonly understood.
What do you do when your product isn’t encrypted? Change how encryption to is commonly understood.
372. Understanding The Facebook Data Leak: 533,000,000 Facebook Records Were Leaked
 A user of a low-level hacking forum posted the records of hundreds of millions of Facebook users for free online on 3rd April.
A user of a low-level hacking forum posted the records of hundreds of millions of Facebook users for free online on 3rd April.
373. Everything You Ever Wanted To Know About Decentralized Identities
 There's no denying the benefits to mankind brought about by the digital age. The ease of which we can transfer, process, and apply information has led to many breakthroughs impacting all aspects of daily life.
There's no denying the benefits to mankind brought about by the digital age. The ease of which we can transfer, process, and apply information has led to many breakthroughs impacting all aspects of daily life.
374. SSI's Problem with Data Ownership

375. Data and DNA: Who Owns You?
 Data and DNA: With corporations able to accumulate information normally considered private on both of these fields, who should own that data and thus you?
Data and DNA: With corporations able to accumulate information normally considered private on both of these fields, who should own that data and thus you?
376. Testing the Perfornace and Privacy Settings of COVID-19 Vaccine Websites
 The government websites responsible for helping citizens get their COVID-19 Vaccines have been found to have less-than-ideal accessibility and privacy features.
The government websites responsible for helping citizens get their COVID-19 Vaccines have been found to have less-than-ideal accessibility and privacy features.
377. 10 Cybersecurity Tips Everyone Should Follow
 In a world where everything is connected to the internet, and yes I mean everything (NSFW), the threat of being hacked is always present. The most recent notable security leak was with Robinhood.
In a world where everything is connected to the internet, and yes I mean everything (NSFW), the threat of being hacked is always present. The most recent notable security leak was with Robinhood.
378. The 12 Key Requirements for Your Company’s Valid PCI-DSS Compliance Plan
 This article provides you the detailed information and also acts as a guide to help the IT managers, fintech managers, management executives, stakeholders, to understand how PCI DSS compliance can be applied in their organization’s business transactions with the customers' payment card’s data.
This article provides you the detailed information and also acts as a guide to help the IT managers, fintech managers, management executives, stakeholders, to understand how PCI DSS compliance can be applied in their organization’s business transactions with the customers' payment card’s data.
379. 23 Cybersecurity Tips to Level up Your Data Privacy Game
 It's important to keep yourself up-to-date on the latest security measures. Cybercrime has increased, secure your data.
It's important to keep yourself up-to-date on the latest security measures. Cybercrime has increased, secure your data.
Thank you for checking out the 379 most read stories about Data Privacy on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

