Let's learn about Internet Security via these 66 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
1. The Vulnerabilities of NFC Payments Need to be Addressed
 Even though NFC appears to be so easy and convenient, it is not without its vulnerabilities, especially in regards to security.
Even though NFC appears to be so easy and convenient, it is not without its vulnerabilities, especially in regards to security.
2. Suffering Due to Buffering? Here's how You Can Improve Your Wifi Connection
 Enhance your Online Streaming Experience and improve your wifi connection with these easy fixes.
Enhance your Online Streaming Experience and improve your wifi connection with these easy fixes.
3. What an IP Address Can Reveal About You
 Is it possible to trace an IP ? To what extent does it reveal your physical location? How to prevent your IP from being tracked? Let's learn more about IP.
Is it possible to trace an IP ? To what extent does it reveal your physical location? How to prevent your IP from being tracked? Let's learn more about IP.
4. How to Avoid Credit Card Skimming: 5 Tips to Keep Your Information Safe
 Credit card skimming occurs when someone places an electronic device on or near a credit card reader. This device captures and stores your credit card details.
Credit card skimming occurs when someone places an electronic device on or near a credit card reader. This device captures and stores your credit card details.
5. DOCSIS 3.1 Technology: Everything You Need to Know
 In this tech guide, we will cover the important details about DOCSIS 3.1 technology.
In this tech guide, we will cover the important details about DOCSIS 3.1 technology.
6. How Free Streaming Websites Could Harm Your Online Security
 Learn how free streaming and online free movies websites could negatively affect your security
Learn how free streaming and online free movies websites could negatively affect your security
7. Expert Web Security Tips for Digital Nomads
 Web security is the process of protecting systems, networks, programs, devices, and data from cyber-attacks. It aims to reduce or stop the risk of cyber-attacks and protect against the unauthorized hijacking of systems, networks, and technologies.
Web security is the process of protecting systems, networks, programs, devices, and data from cyber-attacks. It aims to reduce or stop the risk of cyber-attacks and protect against the unauthorized hijacking of systems, networks, and technologies.
8. The Importance of Message Authentication Code in SSL/TLS
 Transport Layer Security, better known as SSL/TLS, is an encryption protocol designed to offer secure communications over the internet to improve user privacy.
Transport Layer Security, better known as SSL/TLS, is an encryption protocol designed to offer secure communications over the internet to improve user privacy.
9. Why Your Browser's Built-In Password Manager Isn't Enough
 You may ask, "My web browser already has a built-in password manager, why do I need to install a new one?" There's actually a number of good reasons to install a password manager.
You may ask, "My web browser already has a built-in password manager, why do I need to install a new one?" There's actually a number of good reasons to install a password manager.
10. How to Explain the Internet to Your Kids
 There is only one way to explain the dangers of the Internet to children: to be there with them. Talk about the good and the bad that that the internet offers.
There is only one way to explain the dangers of the Internet to children: to be there with them. Talk about the good and the bad that that the internet offers.
11. Proxy Vs. VPN Vs. SmartDNS [A Comparison]

12. The Crucial Role of Machine Learning in Cybersecurity
 In 2019, more than 627 million online records were comprised due to hacking and other types of cyber attacks. This is a pretty staggering number to anyone who has made an online transaction, but the amount of attacks that were stopped is much higher, so it’s worth some optimism. As COVID-19 has pushed many companies into the remote work world, online transactions and records are growing exponentially, and most experts believe that remote work will continue to be very popular even after stay-at-home orders get lifted and life goes back to some form of normal.
In 2019, more than 627 million online records were comprised due to hacking and other types of cyber attacks. This is a pretty staggering number to anyone who has made an online transaction, but the amount of attacks that were stopped is much higher, so it’s worth some optimism. As COVID-19 has pushed many companies into the remote work world, online transactions and records are growing exponentially, and most experts believe that remote work will continue to be very popular even after stay-at-home orders get lifted and life goes back to some form of normal.
13. Explaining Info-Sec in Layman's Terms [Part I]
 Understanding the common keywords used in the info-sec industry that are used in conjunction with that complicated OWASP Top 10 WAST
Understanding the common keywords used in the info-sec industry that are used in conjunction with that complicated OWASP Top 10 WAST
14. Uncover the 7 Best Security Sites on the Internet
 In this article, we’re going to cover 7 of the best security sites on the internet.
In this article, we’re going to cover 7 of the best security sites on the internet.
15. Compartmentalisation As A Means For Ensuring Privacy [An Overview]
 It was originally used by the Greeks to keep the secret of Greek fire, but now it is used by people all around the world for lots of different reasons.
It was originally used by the Greeks to keep the secret of Greek fire, but now it is used by people all around the world for lots of different reasons.
16. 8 Most Important Cybersecurity Tricks Every Internet User Should Follow
 The cyber-world now accommodates billions of users. There are more than 4 billion internet users in the world today. It's just unfortunate that a large percentage of these users face cyber attacks from unknown sources. While some users are afraid of being attacked, others are ignorant of possible attacks. As an organisation or an individual that utilises the internet, it's a must to know some security tricks. If you're wondering what the tricks are, read on.
The cyber-world now accommodates billions of users. There are more than 4 billion internet users in the world today. It's just unfortunate that a large percentage of these users face cyber attacks from unknown sources. While some users are afraid of being attacked, others are ignorant of possible attacks. As an organisation or an individual that utilises the internet, it's a must to know some security tricks. If you're wondering what the tricks are, read on.
17. How to Handle Injection Attacks With JavaScript - Fighting Unauthorized Access
 There are certain cyberattacks, like attackers trying to inject data from the front-end, that you can guard against with some regular JavaScript best practices.
There are certain cyberattacks, like attackers trying to inject data from the front-end, that you can guard against with some regular JavaScript best practices.
18. 5 Best Free Trial VPN Services in 2023
 Trying to find the best VPN can be a daunting task, especially when there are so many to choose from. While free VPNs might seem like an easy way to dive into better security and bypass content locks, many of them are also likely to steal information and leave users in worse spots than they already were. Not every free VPN does this, but those wishing to truly be secure online will be much more comfortable with a paid service. Luckily, some of the best VPN services come with a free trial, and users would do very well to take advantage of them.
Trying to find the best VPN can be a daunting task, especially when there are so many to choose from. While free VPNs might seem like an easy way to dive into better security and bypass content locks, many of them are also likely to steal information and leave users in worse spots than they already were. Not every free VPN does this, but those wishing to truly be secure online will be much more comfortable with a paid service. Luckily, some of the best VPN services come with a free trial, and users would do very well to take advantage of them.
19. 4 Simple Steps to Avoid Falling Victim to All-Too-Frequent Data Breaches
 These days, reports of major data breaches happen so often that people are beginning to tune them out. After all, most people who have had their data stolen don't actually end up suffering any visible consequences. Therefore, it's all too easy to meet the news of each new security incident with a casual shrug.
These days, reports of major data breaches happen so often that people are beginning to tune them out. After all, most people who have had their data stolen don't actually end up suffering any visible consequences. Therefore, it's all too easy to meet the news of each new security incident with a casual shrug.
20. Cybersecurity At Every Level: How IT Consultants Can Benefit Your Business
 We live our lives online these days – and given this simple fact, it should come as no surprise that cybersecurity is one of the fastest growing industries around, and one that’s critical to all other sectors. For those in the cryptocurrency industry, however, cybersecurity plays a more interesting role. That’s because, while cryptocurrency operations clearly need to enhance their own cybersecurity efforts, they’re also reliant on technology – blockchain – that other industries are using for their own security needs.
We live our lives online these days – and given this simple fact, it should come as no surprise that cybersecurity is one of the fastest growing industries around, and one that’s critical to all other sectors. For those in the cryptocurrency industry, however, cybersecurity plays a more interesting role. That’s because, while cryptocurrency operations clearly need to enhance their own cybersecurity efforts, they’re also reliant on technology – blockchain – that other industries are using for their own security needs.
21. How To Make Sure Your Windows 7 PC Stays Safe
 Windows 7 has recently joined the club of all Windows operating systems that Microsoft is no longer supporting with security updates. So if you're still running on Windows 7, pretty soon it's going to be full of unpatched security holes.
Windows 7 has recently joined the club of all Windows operating systems that Microsoft is no longer supporting with security updates. So if you're still running on Windows 7, pretty soon it's going to be full of unpatched security holes.
22. 5 Ways to Protect Your Cloud Storage

23. Not All Password Managers Are Created Equal: Which is the Best?
 Web-based password managers have emerged as a response to the proliferation of web applications.
Web-based password managers have emerged as a response to the proliferation of web applications.
24. Are You Prepared to Respond to Advanced Security Incidents?

25. MetaMask Users Targeted By Phishing Attack Impersonating Popular Metaverse Projects
 MetaMask users are being targeted in a series of phishing attacks where hackers impersonate popular metaverse project websites.
MetaMask users are being targeted in a series of phishing attacks where hackers impersonate popular metaverse project websites.
26. South Korea: "Internet Crash" Caused by a Lithium Battery Fire
 A fire broke out in the SK C&C Banqiao Data Center, Sanpingdong, Bantang District, South City, Gyeonggi do, South Korea, on October 15, at 3:19 p.m. local time.
A fire broke out in the SK C&C Banqiao Data Center, Sanpingdong, Bantang District, South City, Gyeonggi do, South Korea, on October 15, at 3:19 p.m. local time.
27. The “Connection Not Private” Warning Explained
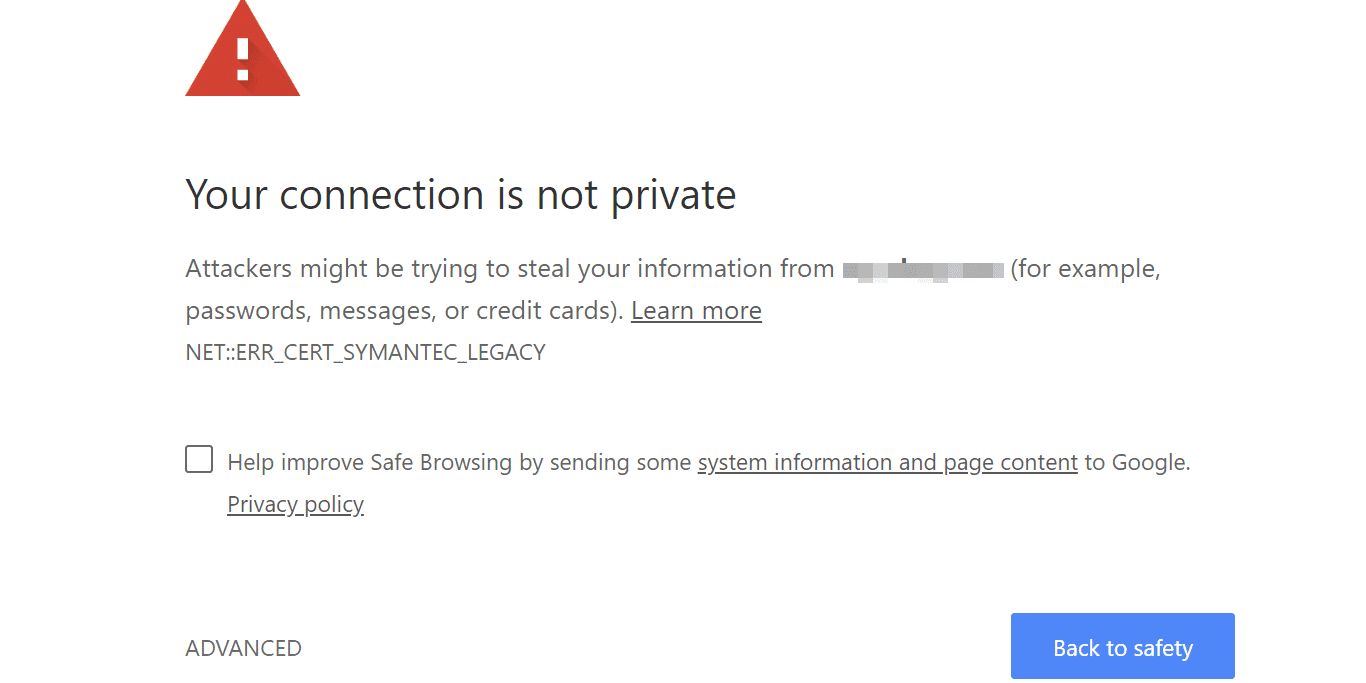 Each time you visit a website, your web browser (e.g., Chrome, Safari, or Firefox) first checks for the existence of one of two digital certificates
Each time you visit a website, your web browser (e.g., Chrome, Safari, or Firefox) first checks for the existence of one of two digital certificates
28. If You Have Important Data: Make Sure Its Protected
 Data transfer is very important and it keeps happening almost every minute. As we chat on various social media applications or even like a post, there is a transfer of information that is happening. While we may not be too bothered about the way in which information and data are transferred from the receiver to the sender and vice-versa, we, of course, would be concerned about the safety of the data and information that is flowing on the internet and other forms of communication.
Data transfer is very important and it keeps happening almost every minute. As we chat on various social media applications or even like a post, there is a transfer of information that is happening. While we may not be too bothered about the way in which information and data are transferred from the receiver to the sender and vice-versa, we, of course, would be concerned about the safety of the data and information that is flowing on the internet and other forms of communication.
29. Protect Your iPhone and iPad Better With These Security Tips

- Keep The Device Up To Date
30. How to Fastline Internet Asset Enumeration with Cyber Search Engines
 Cyber Search Engines collect data across the whole internet and deliver it in a structured view.
Cyber Search Engines collect data across the whole internet and deliver it in a structured view.
31. 4 Handy Tips to Keep your Digital Identity Secure
 Since we can't function without the internet these days, it is highly important to keep our digital identity secure.
Since we can't function without the internet these days, it is highly important to keep our digital identity secure.
32. Will Coronavirus Break the Internet?
 More than two thirds of the U.S. population is now stuck at home as more states are creating new restrictions to try to slow the spread of COVID-19. The internet is now being used more than ever as millions are turning to it as an alternative source of social connection, work, and entertainment. In Seattle, one of the cities in the U.S. that was hardest hit by the virus, internet traffic quickly began to rise - from January to March it has risen by an astounding 30%. Other U.S. ISPs are noticing huge spikes in WiFi calling, online gaming, and VPN usage across the country. With a huge number of increased active users, governments and companies alike are making moves to help Americans stay online. One of these steps is the FCC’s Keep Americans Connected pledge that over 70 telecom companies have signed stating that these companies will waive late fees and retain service even with lack of payment. Other companies are making public WiFi networks for students and remote workers. Comcast is setting up public hotspots for free use, Comcast and Spectrum are both offering 2 free months of access to low-income families, and AT&T is suspending broadband usage caps.
More than two thirds of the U.S. population is now stuck at home as more states are creating new restrictions to try to slow the spread of COVID-19. The internet is now being used more than ever as millions are turning to it as an alternative source of social connection, work, and entertainment. In Seattle, one of the cities in the U.S. that was hardest hit by the virus, internet traffic quickly began to rise - from January to March it has risen by an astounding 30%. Other U.S. ISPs are noticing huge spikes in WiFi calling, online gaming, and VPN usage across the country. With a huge number of increased active users, governments and companies alike are making moves to help Americans stay online. One of these steps is the FCC’s Keep Americans Connected pledge that over 70 telecom companies have signed stating that these companies will waive late fees and retain service even with lack of payment. Other companies are making public WiFi networks for students and remote workers. Comcast is setting up public hotspots for free use, Comcast and Spectrum are both offering 2 free months of access to low-income families, and AT&T is suspending broadband usage caps.
33. Introducing Fengg: An Innovative and More Secure Home Internet Solution
 The internet has ushered in a new era, and in too many ways to count, it has made our lives smoother, easier, and more modern.
The internet has ushered in a new era, and in too many ways to count, it has made our lives smoother, easier, and more modern.
34. The Essential Guide to Security and Compliance for the Public Cloud
 Using an Infrastructure-as-a-Service provider makes it easier to achieve and maintain compliance, but here are some caveats to consider.
Using an Infrastructure-as-a-Service provider makes it easier to achieve and maintain compliance, but here are some caveats to consider.
35. Why Vulnerability Detection is Important in the IT Space
 A look at why vulnerability detection is important in the it space
A look at why vulnerability detection is important in the it space
36. What is a DNS Attack and How Can You Protect Against It?
 DNS is a protocol that translates human-friendly URLs into IP addresses and a DNS attack is when a hacker exploits vulnerabilities in the DNS service itself.
DNS is a protocol that translates human-friendly URLs into IP addresses and a DNS attack is when a hacker exploits vulnerabilities in the DNS service itself.
37. What Startups Can Learn From 5 Security Trends that Didn’t Exist 5 Years Ago
 Technology is evolving at an incredibly fast pace. An analog world wasn’t that long ago, when phones stayed on the wall, the internet was in its infancy, and seamless global connection seemed distant. Yet now we can summon cars from the mini computers in our pockets, jump on a real-time video call with someone across the world, and have our refrigerators order our groceries.
Technology is evolving at an incredibly fast pace. An analog world wasn’t that long ago, when phones stayed on the wall, the internet was in its infancy, and seamless global connection seemed distant. Yet now we can summon cars from the mini computers in our pockets, jump on a real-time video call with someone across the world, and have our refrigerators order our groceries.
38. An Introduction to Layer 3 Switches
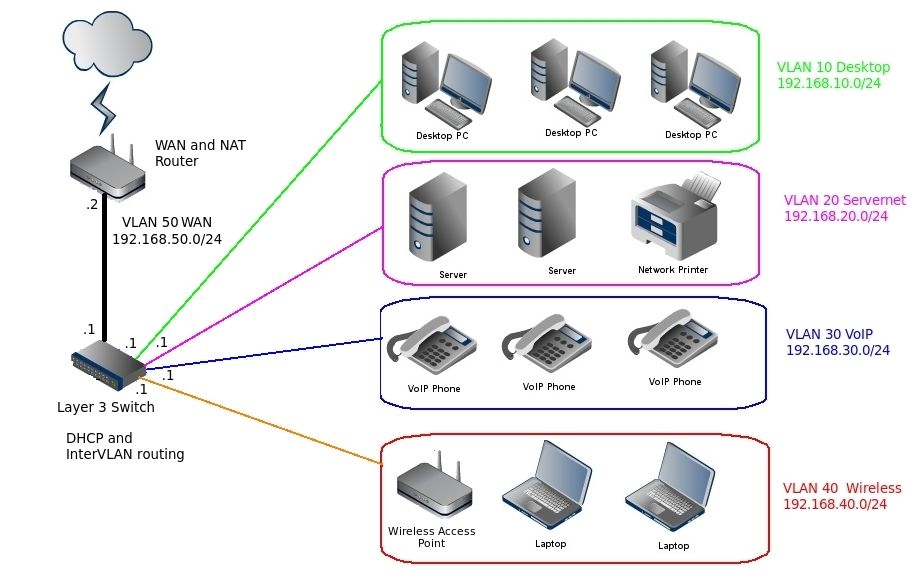 In today's complex business networks that comprise many virtual LAN's and subnets, a Layer 3 switch plays an important role in many systems. But do you need this on your network? Let's see.
In today's complex business networks that comprise many virtual LAN's and subnets, a Layer 3 switch plays an important role in many systems. But do you need this on your network? Let's see.
39. DNS Firewalls for Dummies
 As we adjust to life during a pandemic, two things have become clear: First, the internet is essential; second, the internet is full of dangers. Each of these dangers is different: They vary in the sort of attack they strike with, our familiarity with them, and the tools we can use to avert them. For example, viruses have been well-known for decades. Every PC is currently protected with antivirus software--and in many cases, it’s incorporated right into your operating system. Other types of internet threats, such as botnets, are newer, more difficult to detect, and less known to web users.
As we adjust to life during a pandemic, two things have become clear: First, the internet is essential; second, the internet is full of dangers. Each of these dangers is different: They vary in the sort of attack they strike with, our familiarity with them, and the tools we can use to avert them. For example, viruses have been well-known for decades. Every PC is currently protected with antivirus software--and in many cases, it’s incorporated right into your operating system. Other types of internet threats, such as botnets, are newer, more difficult to detect, and less known to web users.
40. The Noonification: This Ain’t my First Rodeo! (9/26/2022)
 9/26/2022: Top 5 stories on the Hackernoon homepage!
9/26/2022: Top 5 stories on the Hackernoon homepage!
41. How To Enable Microsoft Edge`s New Crapware Blocker
 Microsoft Edge has a new crapware blocker. But the thing is, it isn't enabled by default. The blocker is currently only available in Edge's beta version but it should be available for everyone using the Chromium-based Edge browser with the stable release of Edge 80 in early February.
Microsoft Edge has a new crapware blocker. But the thing is, it isn't enabled by default. The blocker is currently only available in Edge's beta version but it should be available for everyone using the Chromium-based Edge browser with the stable release of Edge 80 in early February.
42. How Proxies & Browsers Are Meant to Work Together
 Proxies can be used for an IP covering, but other distinguishing features need something more. And all this because of a digital fingerprint revealing us.
Proxies can be used for an IP covering, but other distinguishing features need something more. And all this because of a digital fingerprint revealing us.
43. LDAP Injection Vulnerability, Explained
 LDAP or Lightweight Directory Access Protocol is a methodology designed to read data in a directory, file or device. This is actually a directory access service which, for instance, can be used to provide information about a user who is trying to login as part of a single-sign-on, SSO process.
LDAP or Lightweight Directory Access Protocol is a methodology designed to read data in a directory, file or device. This is actually a directory access service which, for instance, can be used to provide information about a user who is trying to login as part of a single-sign-on, SSO process.
44. Before and After the Internet

45. Why You Should Avoid Using Public WiFi
 Why You Should Avoid Using Public WiFi
Why You Should Avoid Using Public WiFi
46. Beginners Guide to Preventing Permission Bloat: Overlooked and Hidden Access
 When it comes to your organizational security, there should be no stone left unturned. Unfortunately, many organizations fail to do this, as they aren’t even aware that there are unturned stones. Overlooked access rights are one of the most unnoticed security threats your organization can face—less of a stone and more of a somehow-overlooked, but ever-looming mountain.
When it comes to your organizational security, there should be no stone left unturned. Unfortunately, many organizations fail to do this, as they aren’t even aware that there are unturned stones. Overlooked access rights are one of the most unnoticed security threats your organization can face—less of a stone and more of a somehow-overlooked, but ever-looming mountain.
47. How to Protect Yourself Against Smishing Attacks
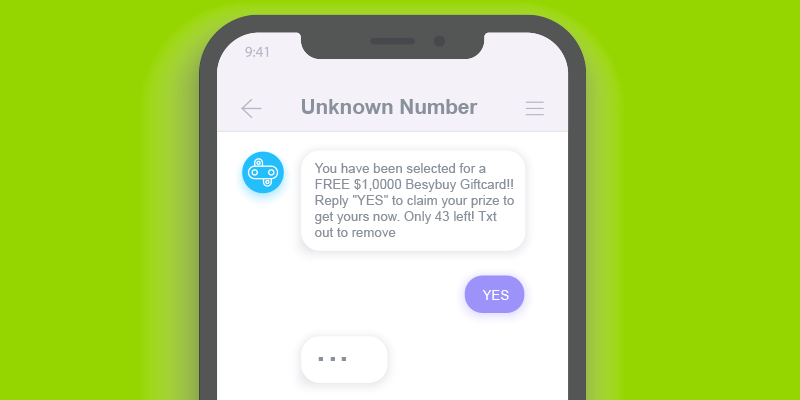 As the threat landscape encapsulating organizations and companies grows increasingly sophisticated, and harbors a growing number of threats and vulnerabilities- organizations are getting more accustomed to commonplace scams such as phishing.
As the threat landscape encapsulating organizations and companies grows increasingly sophisticated, and harbors a growing number of threats and vulnerabilities- organizations are getting more accustomed to commonplace scams such as phishing.
48. How Password Managers Can Protect You From Phishing
 Password managers are a convenient way to use strong, unique passwords everywhere. Another good thing about password managers is that they help protect you from malicious websites that attempt to "phish" passwords.
Password managers are a convenient way to use strong, unique passwords everywhere. Another good thing about password managers is that they help protect you from malicious websites that attempt to "phish" passwords.
49. The Security Vulnerabilities of Smart Devices
 In 2020, we are now more connected to the internet than ever before, from having smart fridges, smart cars, and even RFID implants that can be placed under our skin.
In 2020, we are now more connected to the internet than ever before, from having smart fridges, smart cars, and even RFID implants that can be placed under our skin.
50. How Verifiable Creds, Decentralized Identifiers and Blockchain Work Together for a Safer Internet
 The future of the internet will come with more risks to our data privacy. Fortunately, Blockchain and Decentralized Identifiers can work together to protect.
The future of the internet will come with more risks to our data privacy. Fortunately, Blockchain and Decentralized Identifiers can work together to protect.
51. Your Ultimate Guide To The 4 Types of IT Security
 IT Security protects your business against cyber threats. There are four types of IT Security: network security, end-point security, internet & cloud security.
IT Security protects your business against cyber threats. There are four types of IT Security: network security, end-point security, internet & cloud security.
52. What is Transport Layer Security (TLS)?
 This article's goal is to help you make these decisions to ensure the confidentiality and integrity communication between client and server.
This article's goal is to help you make these decisions to ensure the confidentiality and integrity communication between client and server.
53. Is Your ERP the Target of Cyber Criminals? How to Prevent this Attack
 ERP systems are complex solutions that handle business-critical processes and manage sensitive data. These factors alone are enough to make them an attractive target for cybercriminals. Despite it being common knowledge, businesses often opt for simpler and cheaper solutions that do not address the issue at the system level. Below is an in-depth look at the main factors that erode corporate cybersecurity and ways to prevent cyberattacks.
ERP systems are complex solutions that handle business-critical processes and manage sensitive data. These factors alone are enough to make them an attractive target for cybercriminals. Despite it being common knowledge, businesses often opt for simpler and cheaper solutions that do not address the issue at the system level. Below is an in-depth look at the main factors that erode corporate cybersecurity and ways to prevent cyberattacks.
54. Why Would Google Be Against the URL??
 Google wants to change a major part of web browsing by killing the URL, in parts though. After their first step was successful, here’s what they plan for the second step.
Google wants to change a major part of web browsing by killing the URL, in parts though. After their first step was successful, here’s what they plan for the second step.
55. How To Enhance Website Security
56. Top 7 Access Control System Manufacturers
 Here is a list of the top 7 access control system providers that offer feature-rich security systems for your business/organization.
Here is a list of the top 7 access control system providers that offer feature-rich security systems for your business/organization.
57. 10 Secure Online Applications in 2021: No More Spy Spps and Hacker Attacks
 A selection of programs for online privacy. All of them will help you not to fall prey to hackers and keep your data safe.
A selection of programs for online privacy. All of them will help you not to fall prey to hackers and keep your data safe.
58. What is Cyber Range Training and Simulation in the Cloud?
 Cyber range simulations help create resiliency by enabling companies in an actual situation to stress-test through Cloud computing. With tabletop drills or classroom instructors we need immersive funds to support situational awareness in a way that is very difficult to duplicate. Cloud Simulation contributes to experience on-the-ground and provides various advantages, including statistical information, input from real-time experts, and cross-functional coaching. There are potentially many challenges with the on-site classrooms based on several experts:
Cyber range simulations help create resiliency by enabling companies in an actual situation to stress-test through Cloud computing. With tabletop drills or classroom instructors we need immersive funds to support situational awareness in a way that is very difficult to duplicate. Cloud Simulation contributes to experience on-the-ground and provides various advantages, including statistical information, input from real-time experts, and cross-functional coaching. There are potentially many challenges with the on-site classrooms based on several experts:
59. How To Enable It Microsoft Edge`s New Crapware Blocker
 Microsoft Edge has a new crapware blocker. But the thing is, it isn't enabled by default. The blocker is currently only available in Edge's beta version but it should be available for everyone using the Chromium-based Edge browser with the stable release of Edge 80 in early February.
Microsoft Edge has a new crapware blocker. But the thing is, it isn't enabled by default. The blocker is currently only available in Edge's beta version but it should be available for everyone using the Chromium-based Edge browser with the stable release of Edge 80 in early February.
60. What is the Difference Between Antivirus and Anti-malware?
 Anti-malware software defends against new malware you may encounter while antivirus software scans for known viruses and searches for any known threats.
Anti-malware software defends against new malware you may encounter while antivirus software scans for known viruses and searches for any known threats.
61. Everything You Need to Know About Content Security Policy (CSP)
 Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types of attacks including XSS and data injection attacks.
Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types of attacks including XSS and data injection attacks.
62. Fighting the Hydra of DDoS Attacks (Spoiler: They Got Worse)
 Interview with Link11 regarding their new DDoS report -- the state of DDoS attacks.
Interview with Link11 regarding their new DDoS report -- the state of DDoS attacks.
63. Exploring 3 Drawbacks To VPN Usage: Do VPNs Really Protect Your Privacy?
 Let’s take a look at the three key issues associated with Virtual Private Networks while questioning whether they’re really as private as we’re led to believe.
Let’s take a look at the three key issues associated with Virtual Private Networks while questioning whether they’re really as private as we’re led to believe.
64. How to Improve Network Security and Visibility in 2020 and 2021
 With the number of products available, it can be an uphill task to try to ensure robust network security and visibility. This, however, is a task that must be accomplished if you want to be competitive.
With the number of products available, it can be an uphill task to try to ensure robust network security and visibility. This, however, is a task that must be accomplished if you want to be competitive.
65. It's Time to Normalize Speaking Out About Internet Safety
 GIVE Nation marks Safer Internet Day with a conversation around privacy, particularly for parents.
GIVE Nation marks Safer Internet Day with a conversation around privacy, particularly for parents.
66. 13 Best Proxy Servers Review [Update Apr'22] - Top Proxy Service in 2021 [Free and Paid]

Thank you for checking out the 66 most read stories about Internet Security on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

