Let's learn about Information Security via these 132 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
1. Clickjacking Attacks: What Are They and How to Prevent Them

2. Why Do We Need Decentralized Finance?
 Decentralised finance has been considered as an important vertical application of blockchain technology.
Decentralised finance has been considered as an important vertical application of blockchain technology.
3. Cracking the SANS GSEC Certification
 The SANS GIAC Security Essentials (GSEC) certification is for anyone working in the field of Information Security.
The SANS GIAC Security Essentials (GSEC) certification is for anyone working in the field of Information Security.
4. How to Use a Zero-Trust Model to Secure Hybrid Workers
 At its core, zero-trust security assumes that every network, device, and user is compromised until it can be proven otherwise.
At its core, zero-trust security assumes that every network, device, and user is compromised until it can be proven otherwise.
5. What You Should Learn Before Learning Cybersecurity - Updated 2022
 Have you been looking to learn Cybersecurity but you’re unsure where to start from?
Have you been looking to learn Cybersecurity but you’re unsure where to start from?
Here’s a great guide on where to start!
6. A Guide to Authentication Methods
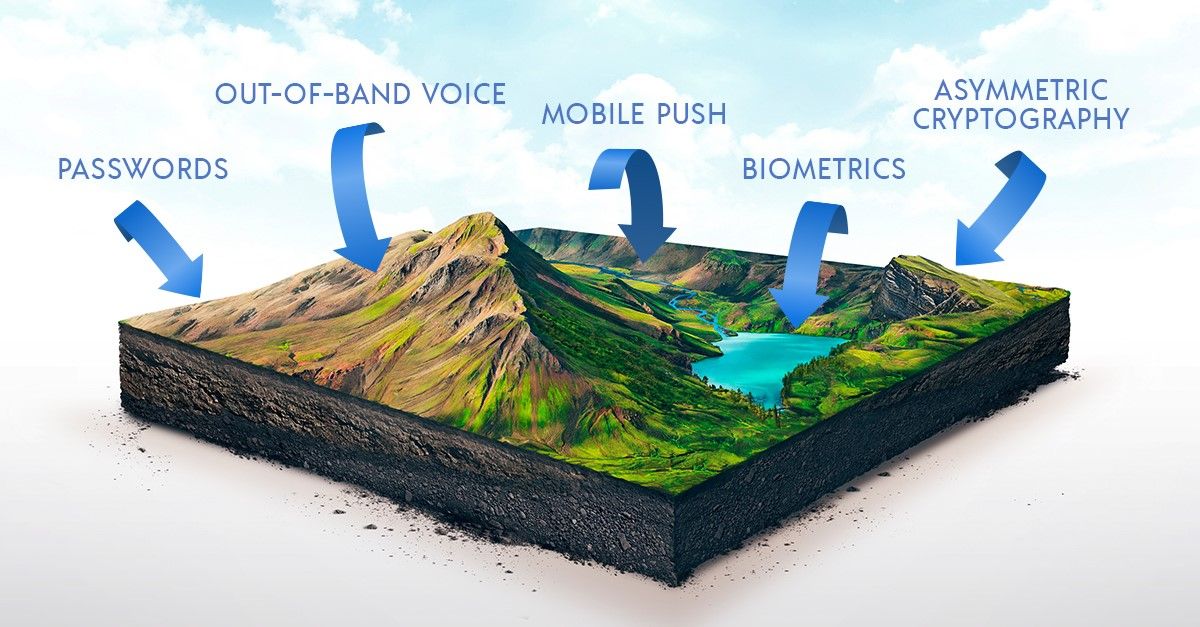 Staying safe on the internet has grown harder over the past few years as both technology and hackers have developed. Recently though, hackers are gaining an edge by not just manipulating the tech, but by manipulating the users themselves. In 2018, weak or stolen passwords were tied to over 80% of security breaches and in 2019, there were over 150,000 security incidents and nearly 4,000 confirmed data breaches. In 2020 alone, more than 15 billion stolen credentials were up for sale on the dark web. All this data points out the fact that our current way of protecting data is flawed, but making a new way to protect it while still maintaining security and convenience is a high mark to hit.
Staying safe on the internet has grown harder over the past few years as both technology and hackers have developed. Recently though, hackers are gaining an edge by not just manipulating the tech, but by manipulating the users themselves. In 2018, weak or stolen passwords were tied to over 80% of security breaches and in 2019, there were over 150,000 security incidents and nearly 4,000 confirmed data breaches. In 2020 alone, more than 15 billion stolen credentials were up for sale on the dark web. All this data points out the fact that our current way of protecting data is flawed, but making a new way to protect it while still maintaining security and convenience is a high mark to hit.
7. CVE-2022-42856: Adjoining Splittail Vulnerability Report
 A look at CVE-2022-42856, reported by Apple as a vulnerability under active exploitation.
A look at CVE-2022-42856, reported by Apple as a vulnerability under active exploitation.
8. Online Identity Theft: Learn How To Combat It
 Risk of becoming a victim of information theft and even online identity theft. In this article we help you find out how to stay safe
Risk of becoming a victim of information theft and even online identity theft. In this article we help you find out how to stay safe
9. Cyber Security: A Guide on Choosing a Reliable Service
 Nowadays, Cyber security is a trending topic around the globe. It has become a necessity for every business with the growing cyber threats.
Nowadays, Cyber security is a trending topic around the globe. It has become a necessity for every business with the growing cyber threats.
10. A Growing Necessity for Cybersecurity
 Businesses and personal users alike, cybersecurity is a growing necessity. With the increase of breaches, cybercrime, and more sophisticated hackers in this world, it is more important than ever to ensure that your data and network are secure and safe from criminals. If you are a business, then you likely have a dedicated IT team that helps ensure the safety of the data and network at your business, but it is important for you to understand what needs to be done so you can better direct your IT department. If you are a personal user, never believe that your data and online security is not valuable, as it most often is just as valuable as your physical possessions. Just as there are steps to prevent intestinal permeability, there are steps that can be taken to prevent someone from hacking your information.
Businesses and personal users alike, cybersecurity is a growing necessity. With the increase of breaches, cybercrime, and more sophisticated hackers in this world, it is more important than ever to ensure that your data and network are secure and safe from criminals. If you are a business, then you likely have a dedicated IT team that helps ensure the safety of the data and network at your business, but it is important for you to understand what needs to be done so you can better direct your IT department. If you are a personal user, never believe that your data and online security is not valuable, as it most often is just as valuable as your physical possessions. Just as there are steps to prevent intestinal permeability, there are steps that can be taken to prevent someone from hacking your information.
11. 5 Reasons Why Enterprises Need Zero Trust Security
 The notion of “Zero Trust” has been around since the 90s. But, the Zero Trust security model was first coined by John Kindervag to describe stricter access control management and cybersecurity programs, in 2010. Meaning that infinite trust is diminished from all computing infrastructure, and Zero Trust is grounded on the idea “trust none, verify all”.
The notion of “Zero Trust” has been around since the 90s. But, the Zero Trust security model was first coined by John Kindervag to describe stricter access control management and cybersecurity programs, in 2010. Meaning that infinite trust is diminished from all computing infrastructure, and Zero Trust is grounded on the idea “trust none, verify all”.
12. CVE-2022-31705: Bridged Creek Vulnerability Report
 Information on the CVE-2022-31705 critical sandbox escape vulnerability announced by VMWare.
Information on the CVE-2022-31705 critical sandbox escape vulnerability announced by VMWare.
13. The SIM Swap Attack : Addressing This Identity Fraud Problem
 The SIM-Swap Attack makes use of customer support in the telecom service provider’s system. Here are Prevention and Mitigation Methods against Sim Swap Attacks.
The SIM-Swap Attack makes use of customer support in the telecom service provider’s system. Here are Prevention and Mitigation Methods against Sim Swap Attacks.
14. Life-Changing Facts About Apple’s iOS Security Architecture
 Introduction to Apple platform security:
Introduction to Apple platform security:
15. Awareness Is Not Understanding: The Missing Link in Cybersecurity Awareness Campaigns
 The only way to make cybersecurity awareness campaigns effective is for users to understand the consequences and see that they have skin in the game.
The only way to make cybersecurity awareness campaigns effective is for users to understand the consequences and see that they have skin in the game.
16. A Guide to Understanding the Job Roles & Selecting Your Career in Cybersecurity
 This article covers the top 20 job roles available in the Cyber Security domain along with the job description in a simplified way.
This article covers the top 20 job roles available in the Cyber Security domain along with the job description in a simplified way.
17. Common Attack Vectors that Authentication Services are Faced With
 Hacking user accounts on many websites is still easier than it could and should be. This blog post helps you secure your application against identity theft.
Hacking user accounts on many websites is still easier than it could and should be. This blog post helps you secure your application against identity theft.
18. How to Protect your ERP System Against Cyber Attacks
 How to protect your ERP system against cyber attacks?
How to protect your ERP system against cyber attacks?
19. Your SaaS User Communications: Don't Overlook the Security Issues
 In this article, we cover why you should look closely at how secure your customer communications are and implement strict security measures for emails, push not
In this article, we cover why you should look closely at how secure your customer communications are and implement strict security measures for emails, push not
20. How Blockchain Relates to the Byzantine Generals Problem [One Minute Explanation]
 Before we can understand how the Blockchain works, we need to understand the problem it is trying to solve.
Before we can understand how the Blockchain works, we need to understand the problem it is trying to solve.
21. Are You Prepared to Respond to Advanced Security Incidents?

22. 3 Steps to Help Advance Your Cybersecurity Career
 I've spent more than 15 years building and leading cybersecurity programs at several Fortune 500 companies in the Financial Services industry. I'm also the Founder & Managing Principal of Fraction Consulting where I get to do fractional CTO & CISO work and advise private capital firms.
I've spent more than 15 years building and leading cybersecurity programs at several Fortune 500 companies in the Financial Services industry. I'm also the Founder & Managing Principal of Fraction Consulting where I get to do fractional CTO & CISO work and advise private capital firms.
23. Why Zero-Day Attacks are so Dangerous and How to Stop Them
 Cybersecurity is becoming an internal and important part of a business's functioning as more and more enterprises are going online with their businesses.
Cybersecurity is becoming an internal and important part of a business's functioning as more and more enterprises are going online with their businesses.
24. How do Hackers Hide Themselves? - A Guide to Staying Anonymous Online
 The world has always been fascinated with Hackers. In this video, we’ll learn about how they hide themselves online.
The world has always been fascinated with Hackers. In this video, we’ll learn about how they hide themselves online.
25. CISSP Preparation Guide: What to Do and What Not to Do
 This article provides tips and support for those interested in preparing for the Certified Information Systems Security Professional (CISSP) exam.
This article provides tips and support for those interested in preparing for the Certified Information Systems Security Professional (CISSP) exam.
26. What is Secure SDLC?
 Software Development Life Cycle is a framework that describes the software life cycle. Its purpose is to help build quality development processes.
Software Development Life Cycle is a framework that describes the software life cycle. Its purpose is to help build quality development processes.
27. Viewing K8S Cluster Security from the Perspective of Attackers (Part 2)
 This article will continue to introduce attack points on K8S Cluster security.
This article will continue to introduce attack points on K8S Cluster security.
28. Signal Protocol — Open Source, Private, Encrypted Mobile Messaging App
 Signal doesn’t store any personal data and is highly transparent about their work because they are an open-source organization rather than a corporation.
Signal doesn’t store any personal data and is highly transparent about their work because they are an open-source organization rather than a corporation.
29. Prioritising Security Vulnerabilities with CVSS 3.1 [An Overview]
30. What Is White-Box Cryptography?
 White-box cryptography combines methods of encryption and obfuscation to embed secret keys within application code. The goal is to combine code and keys in such a way that the two are indistinguishable to an attacker, and the new "white-box" program can be safely run in an insecure environment.
White-box cryptography combines methods of encryption and obfuscation to embed secret keys within application code. The goal is to combine code and keys in such a way that the two are indistinguishable to an attacker, and the new "white-box" program can be safely run in an insecure environment.
31. Organizing Your Business Statistics to Achieve Success
 It is not an easy task to keep your business data organized; however, it is an important thing to do. Organizing data includes a lot more than putting all your papers in place and clearing the clutter on your desk. To have your statistics well organized, you have to create a system and procedures for every department available in your company. The following are top ideas o0n how you can get your small business statistics that can help in increasing the productivity of the business.
It is not an easy task to keep your business data organized; however, it is an important thing to do. Organizing data includes a lot more than putting all your papers in place and clearing the clutter on your desk. To have your statistics well organized, you have to create a system and procedures for every department available in your company. The following are top ideas o0n how you can get your small business statistics that can help in increasing the productivity of the business.
32. Is Cyber Security Hard? How to Find Your Way in
 Cybersecurity is a broad, changing, challenging and complex field. To get into it, go beyond application forms with the tips described here.
Cybersecurity is a broad, changing, challenging and complex field. To get into it, go beyond application forms with the tips described here.
33. Understanding What Security Testing Is & Its Importance with The Top Tools and Key Principles
 In this article, we will explore what security testing is, the top tools for security testing, and the key principles of security testing.
In this article, we will explore what security testing is, the top tools for security testing, and the key principles of security testing.
34. 7 Best DevOps Security Practices: DevSecOps and Its Merits
 DevOps has transformed the way operational engineers and software developers reason. Gone are the days when a code was written, implemented, and managed by operations. The DevOps model has remodeled the system of product and application production. As a result, faster results have become the pinnacle of delivering at the speed which the market demands.
DevOps has transformed the way operational engineers and software developers reason. Gone are the days when a code was written, implemented, and managed by operations. The DevOps model has remodeled the system of product and application production. As a result, faster results have become the pinnacle of delivering at the speed which the market demands.
35. Smart Cities: Cybersecurity in the Era of IoT
 A smart city is representative of urbanization in the digital world. The infrastructure of smart cities is built on embedded Internet of Things (IoT) technology. The smart city promises new opportunities and growth in the urban world. These opportunities include better connectivity, productivity, agility, and innovation. However, it is a known fact that with opportunities come challenges.
A smart city is representative of urbanization in the digital world. The infrastructure of smart cities is built on embedded Internet of Things (IoT) technology. The smart city promises new opportunities and growth in the urban world. These opportunities include better connectivity, productivity, agility, and innovation. However, it is a known fact that with opportunities come challenges.
36. The What and Why of Tokenomics
 Do you find the concept of tokenomics a bit strange? Learn about the meaning and importance of tokenomics in this article.
Do you find the concept of tokenomics a bit strange? Learn about the meaning and importance of tokenomics in this article.
37. Manage Your Emails Like You Manage Your Passwords
 Add an extra security layer for the protection of your emails.
Add an extra security layer for the protection of your emails.
38. I Hacked My Coffee Shop and Accessed My Data: Hacking Your Application May Be Easier Than You Think
 I noticed a suspicious behavior on the weekly email from my coffee shop's subscription; it was offering I edit my preferences directly through a dedicated link.
I noticed a suspicious behavior on the weekly email from my coffee shop's subscription; it was offering I edit my preferences directly through a dedicated link.
39. Insider Threats: Unmasking the Foe Within Your Organization
 Insider threat is a reality, but so are ways to prevent and mitigate it.
Insider threat is a reality, but so are ways to prevent and mitigate it.
40. The Blockchain Is Not Dead
 How and why the blockchain should be placed front and centre of the secure software supply chain and why it is more useful than some people may think.
How and why the blockchain should be placed front and centre of the secure software supply chain and why it is more useful than some people may think.
41. LDAP Injection Vulnerability, Explained
 LDAP or Lightweight Directory Access Protocol is a methodology designed to read data in a directory, file or device. This is actually a directory access service which, for instance, can be used to provide information about a user who is trying to login as part of a single-sign-on, SSO process.
LDAP or Lightweight Directory Access Protocol is a methodology designed to read data in a directory, file or device. This is actually a directory access service which, for instance, can be used to provide information about a user who is trying to login as part of a single-sign-on, SSO process.
42. IT Audit | Step-by-Step Guide
 In 2020, an IT audit is important for all organizations. It provides insights into the business’ IT infrastructure and how it can be improved.
In 2020, an IT audit is important for all organizations. It provides insights into the business’ IT infrastructure and how it can be improved.
43. 5 Best Free Trial VPN Services in 2023
 Trying to find the best VPN can be a daunting task, especially when there are so many to choose from. While free VPNs might seem like an easy way to dive into better security and bypass content locks, many of them are also likely to steal information and leave users in worse spots than they already were. Not every free VPN does this, but those wishing to truly be secure online will be much more comfortable with a paid service. Luckily, some of the best VPN services come with a free trial, and users would do very well to take advantage of them.
Trying to find the best VPN can be a daunting task, especially when there are so many to choose from. While free VPNs might seem like an easy way to dive into better security and bypass content locks, many of them are also likely to steal information and leave users in worse spots than they already were. Not every free VPN does this, but those wishing to truly be secure online will be much more comfortable with a paid service. Luckily, some of the best VPN services come with a free trial, and users would do very well to take advantage of them.
44. CSMA is More Than XDR — An Introduction to Cybersecurity Mesh Architecture
 Just consider how many service providers and models are in the picture. Therefore, it is time for a new and better approach — Cybersecurity Mesh Architecture.
Just consider how many service providers and models are in the picture. Therefore, it is time for a new and better approach — Cybersecurity Mesh Architecture.
45. Explaining Info-Sec in Layman's Terms [Part II]
 The reality of modern information security in enterprises around the world explained in layman's terms for the uninitiated to understand and visualise.
The reality of modern information security in enterprises around the world explained in layman's terms for the uninitiated to understand and visualise.
46. Is Excel a Security Risk?
 Is Excel a security risk? This guide shows why some people have concerns with using this spreadsheet software for sensitive information.
Is Excel a security risk? This guide shows why some people have concerns with using this spreadsheet software for sensitive information.
47. How to Create an Effective Incident Response Plan

48. Changes and Trends in DeFi Security
 Ever since it emerged in mid-2020, DeFi has been a major trend in the cryptocurrency industry, which was (and still is) quite understandable. It brought a way to make money passively, it enabled loans that you can get in exchange for providing collateral, but most importantly, it allowed you to use your existing money to make more money, without the risks that accompany crypto trading.
Ever since it emerged in mid-2020, DeFi has been a major trend in the cryptocurrency industry, which was (and still is) quite understandable. It brought a way to make money passively, it enabled loans that you can get in exchange for providing collateral, but most importantly, it allowed you to use your existing money to make more money, without the risks that accompany crypto trading.
49. Explaining Info-Sec in Layman's Terms [Part I]
 Understanding the common keywords used in the info-sec industry that are used in conjunction with that complicated OWASP Top 10 WAST
Understanding the common keywords used in the info-sec industry that are used in conjunction with that complicated OWASP Top 10 WAST
50. 6 Tips for Improving Cybersecurity in the Workplace
 In this post, we'll cover some fundamental and practical ways to boost workplace cybersecurity.
In this post, we'll cover some fundamental and practical ways to boost workplace cybersecurity.
51. Guide to Risk Assessment Management and ISO/IEC 27002/27005
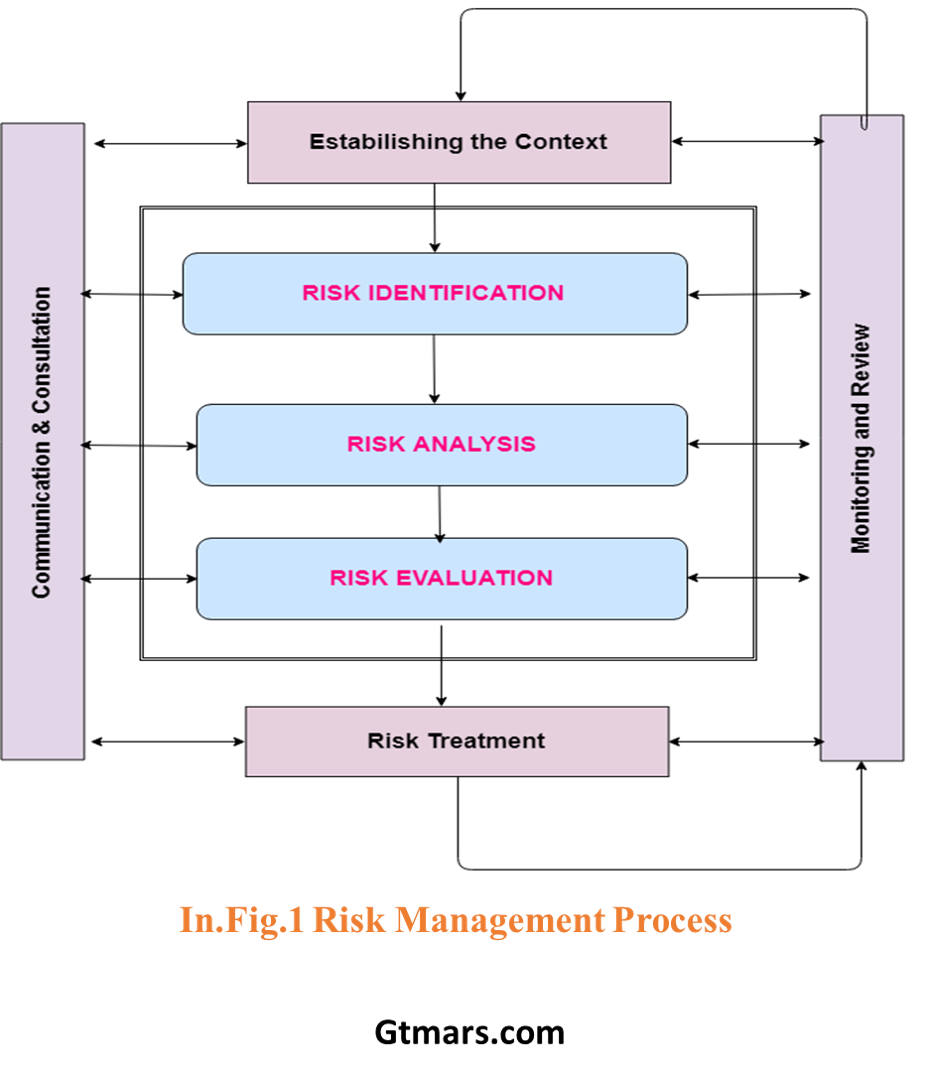 The goal of risk management is to identify the potential problems before they emerge. Usually, they occur unconditionally. It helps the IT managers to balance the CAPEX/OPEX costs in the organization and also take protective measures and gains much control power.
The goal of risk management is to identify the potential problems before they emerge. Usually, they occur unconditionally. It helps the IT managers to balance the CAPEX/OPEX costs in the organization and also take protective measures and gains much control power.
52. Courier's Path to Becoming SOC 2 Type 2 Compliant
 This post is about what it means to be SOC 2 Type 2 compliant, why it is important that Courier now is, and what our journey looked like on our way here.
This post is about what it means to be SOC 2 Type 2 compliant, why it is important that Courier now is, and what our journey looked like on our way here.
53. 10 Reasons to Get Your Cybersecurity Certification

54. Creating a Secure Mobile App: Main Vulnerabilities and Security Practices
 There are 2.87 million apps on the Google Play Store. it’s the responsibility of the app owner to make sure that all the data use properly.
There are 2.87 million apps on the Google Play Store. it’s the responsibility of the app owner to make sure that all the data use properly.
55. Using Macros and Emulation Voodoo to Solve a Crackme
 This time I’m tackling this beautiful crackme, the third of the series. To solve this we will use radare2’s macros and unicorn emulation. Let’s jump right in!
This time I’m tackling this beautiful crackme, the third of the series. To solve this we will use radare2’s macros and unicorn emulation. Let’s jump right in!
56. Why Vulnerability Detection is Important in the IT Space
 A look at why vulnerability detection is important in the it space
A look at why vulnerability detection is important in the it space
57. Artificial Intelligence is No Match for Natural Stupidity
 A Lazy Introduction to AI for Infosec.
A Lazy Introduction to AI for Infosec.
58. Understanding The Importance of SOC2 Compliance for Data Centers
 Businesses rely on Data Center SOC2 Audit Reports for critical business decisions concerning outsourcing services. It helps customers build a sense of trust.
Businesses rely on Data Center SOC2 Audit Reports for critical business decisions concerning outsourcing services. It helps customers build a sense of trust.
59. 5 Reasons Why VPNs are not Safe in 2021
 All good things must come to an end, which may be true for the VPN in 2021. VPNs have been a useful enterprise tool for companies since they started in the 90s,
All good things must come to an end, which may be true for the VPN in 2021. VPNs have been a useful enterprise tool for companies since they started in the 90s,
60. From Passwords to Passwordless Authentication
 Passwordless authentication is gradually replacing the password-based authentication practice. The CIA triad of Cybersecurity is changing rapidly. Learn how.
Passwordless authentication is gradually replacing the password-based authentication practice. The CIA triad of Cybersecurity is changing rapidly. Learn how.
61. Why your Company Needs a Virtual Chief Information Security Officer
 Why should your company hire a virtual CISO to increase security?
Why should your company hire a virtual CISO to increase security?
62. How To Analyse and Visualize DMARC Reports using Open-Source Tools
 Sending mail might sound easy, but to avoid getting your mail caught in spam filters, and to prevent others from sending spoofed email in your name, you need to employ different preventive methods. One such method is DMARC, which allows domain administrators to apply policies with regard to email authentication. You also have the possibility to get reports sent to you with the results of the applied policy.
Sending mail might sound easy, but to avoid getting your mail caught in spam filters, and to prevent others from sending spoofed email in your name, you need to employ different preventive methods. One such method is DMARC, which allows domain administrators to apply policies with regard to email authentication. You also have the possibility to get reports sent to you with the results of the applied policy.
63. VPN Leaks that Threaten Your Online Privacy Daily
 According to research by GlobalWebIndex, in 2018, around 25% of Internet users have used a VPN service. There are several reasons for this spike in popularity, which you can read about in my previous article. One of the main reasons is the ability to bypass geo-blocks and gain access to, for example, a full Netflix library.
According to research by GlobalWebIndex, in 2018, around 25% of Internet users have used a VPN service. There are several reasons for this spike in popularity, which you can read about in my previous article. One of the main reasons is the ability to bypass geo-blocks and gain access to, for example, a full Netflix library.
64. Free Extension To Scan Go Vulnerabilities in Visual Studio Code
 If you’re a Golang developer using Visual Studio Code, keeping at-risk Go Modules out of your apps just got easier, and for free.
If you’re a Golang developer using Visual Studio Code, keeping at-risk Go Modules out of your apps just got easier, and for free.
65. "The Pandemic Enabled me to Take a Deep Self-reflection" - Joseph Chukwube, 2020 Noonie Nominee
 Joseph Chukwube from Nigeria has been nominated for a 2020
Noonie in the Future Heroes and Technology categories. The Noonies are Hacker Noon’s way of getting to know — from a community perspective — what matters in tech today. So, we asked our Noonie Nominees to tell us. Here’s what Joseph had to share.
Joseph Chukwube from Nigeria has been nominated for a 2020
Noonie in the Future Heroes and Technology categories. The Noonies are Hacker Noon’s way of getting to know — from a community perspective — what matters in tech today. So, we asked our Noonie Nominees to tell us. Here’s what Joseph had to share.
66. How The Hotstuff Protocol is NOT Secure?

67. How to Keep OpenSSL Updated in an Enterprise Environment
 Outdated systems can leave us vulnerable to bad actors. Zero-day exploits are common with just about every system that exists. If we do not upgrade regularly, we leave ourselves at the mercy of black-hat hackers who regularly take advantage of any out-of-date application they can find. This is equally true with OpenSSL as with anything else.
Outdated systems can leave us vulnerable to bad actors. Zero-day exploits are common with just about every system that exists. If we do not upgrade regularly, we leave ourselves at the mercy of black-hat hackers who regularly take advantage of any out-of-date application they can find. This is equally true with OpenSSL as with anything else.
68. Detecting & Preventing Insider Threats To Your Company: An Overview
 It’s commonly understood that the greatest risk to any organization
comes from the insider threat, no matter which industry or sector you work in.
It’s commonly understood that the greatest risk to any organization
comes from the insider threat, no matter which industry or sector you work in.
69. What Could Have Prevented 2020's Massive Twitter Hack?
 Attacks and account take-overs like the recent Twitter hack are completely avoidable. Enterprises must implement biometric multi-factor authentication to ensure that only the right users have access to the right systems at all times. If they don’t, users will continue being vulnerable to hacks and scams.
Attacks and account take-overs like the recent Twitter hack are completely avoidable. Enterprises must implement biometric multi-factor authentication to ensure that only the right users have access to the right systems at all times. If they don’t, users will continue being vulnerable to hacks and scams.
70. IT Security: How to Deal With The Insider Threat
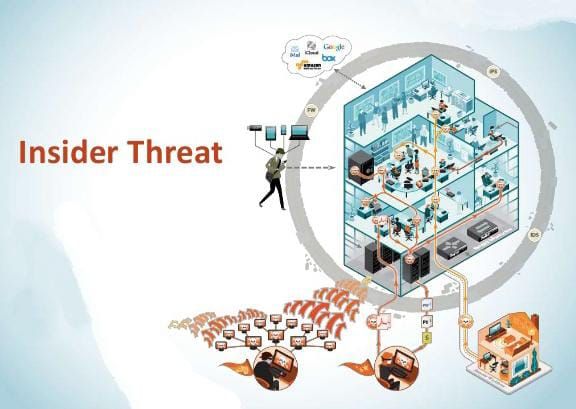 A study by the Wall Street Journal found that almost 70% of companies admitted concern about violent employees! While workers continue to be a major security ri
A study by the Wall Street Journal found that almost 70% of companies admitted concern about violent employees! While workers continue to be a major security ri
71. 5 Popular Professions in Cybersecurity
 Cybersecurity jobs are valuable in 2022 because of an increased number of hacks. Among the top cybersecurity jobs are anti-fraud analyst and reverse engineer.
Cybersecurity jobs are valuable in 2022 because of an increased number of hacks. Among the top cybersecurity jobs are anti-fraud analyst and reverse engineer.
72. Implementing Zero Trust Security
 At its core, Zero Trust is an intuitive concept: assume that every device, user and network is compromised until proven otherwise.
At its core, Zero Trust is an intuitive concept: assume that every device, user and network is compromised until proven otherwise.
73. A Beginner's Guide to Technical Email Security Controls: Understanding SPF, DKIM, and DMARC

74. Getting Started With Digital Forensics Using the Sleuth Kit

75. To All My Friends: Don’t Be An Idiot or Passive With Your Online Privacy
 Complacency with privacy invasion has become our 6th sense. Handing over the intimate details of our lives to corporate and government stooges has become a virtue and civic duty. It should come as no surprise that, even for a society dripping with tech-savviness, the average person would rather their government act than to take action themselves. According to Pew Research:
Complacency with privacy invasion has become our 6th sense. Handing over the intimate details of our lives to corporate and government stooges has become a virtue and civic duty. It should come as no surprise that, even for a society dripping with tech-savviness, the average person would rather their government act than to take action themselves. According to Pew Research:
76. Why You Should Avoid Using Public WiFi
 Why You Should Avoid Using Public WiFi
Why You Should Avoid Using Public WiFi
77. The ZEE5 User Data Leak That The Media Didn't Report On

78. 8 Basic Steps to Keep Your Remote Development Teams Secure
 There is no doubt that the world's workforce is becoming more remote, particularly in tech as developers can now work from any location in the world. But there are a large number of new obstacles that come with this. The most pressing is security.
There is no doubt that the world's workforce is becoming more remote, particularly in tech as developers can now work from any location in the world. But there are a large number of new obstacles that come with this. The most pressing is security.
79. How to Make Your Own and Free Backup Application
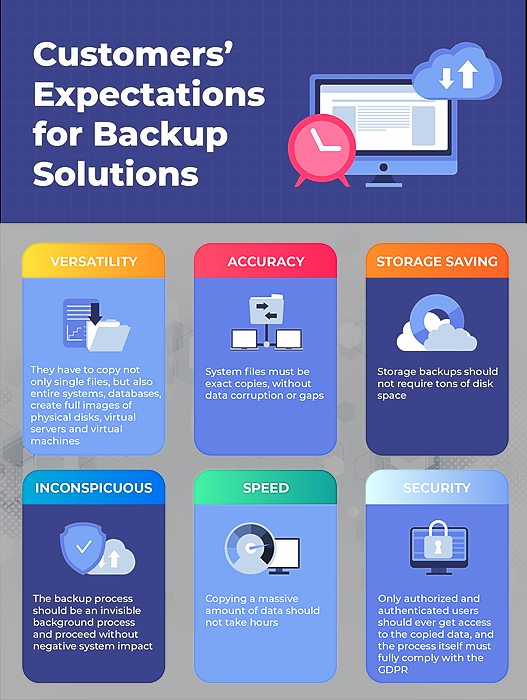 In our age of rapidly developing technologies, data loss can be a disaster not only for large corporations, but also for the average user, showcasing the immense importance of backup and data recovery in today’s data driven world.
In our age of rapidly developing technologies, data loss can be a disaster not only for large corporations, but also for the average user, showcasing the immense importance of backup and data recovery in today’s data driven world.
80. A Beginner's Introduction to Database Backup Security
 With more companies collecting customer data than ever, database backups are key.
With more companies collecting customer data than ever, database backups are key.
81. Attack Default SSH Username/Passwords Using Metasploit
 This is a quick tutorial for using Metasploit to attack default user names and passwords in our lab environment.
This is a quick tutorial for using Metasploit to attack default user names and passwords in our lab environment.
82. Top Penetration Testing Companies and Tools
 Penetration testing, or 'pen tests' as they are colloquially known, basically consist of a hack or cyber-attack on one's system.
Penetration testing, or 'pen tests' as they are colloquially known, basically consist of a hack or cyber-attack on one's system.
83. What is BGP Hijacking and How Do You Prevent It?
 BGP, which stands for Border Gateway Protocol, is a path vector routing protocol that is used to connect external organizations to each other.
BGP, which stands for Border Gateway Protocol, is a path vector routing protocol that is used to connect external organizations to each other.
84. Growing your Startup with Limited IT Resources

85. What is Runtime Application Self-Protection
 What is Runtime Application Self-Protection? Know how RASP is capable of controlling app execution, detecting & preventing real-time attacks.
What is Runtime Application Self-Protection? Know how RASP is capable of controlling app execution, detecting & preventing real-time attacks.
86. Protecting Your Company from Growing Risks of Software Supply Chain Attacks
 Software supply chain attacks are an emerging threat in the cybersecurity world. How can you protect your company against these attacks? Find out here.
Software supply chain attacks are an emerging threat in the cybersecurity world. How can you protect your company against these attacks? Find out here.
87. Secure the Distance: How to Protect the Personal Data of Students Enrolled in Online Education
 The International Telecommunication Union provides security recommendations for schools.
The International Telecommunication Union provides security recommendations for schools.
88. An Introduction to Malware Analysis
 Malicious software (Malware) are either programs or files that are intended to cause harm to a system and thereby its user.
Malicious software (Malware) are either programs or files that are intended to cause harm to a system and thereby its user.
89. Some of the Most Common Security Vulnerabilities and Fixes
 So, which security vulnerability types may be exposing your system to cyberthreats at this very moment? How do vulnerabilities appear? And how can we mitigate?
So, which security vulnerability types may be exposing your system to cyberthreats at this very moment? How do vulnerabilities appear? And how can we mitigate?
90. Phishing: Top Threat to Our Online Security
 Phishing is a cheap technique for hackers to steal the victim’s data. Now I am telling you because it really happened to me. It took my most online privacy.
Phishing is a cheap technique for hackers to steal the victim’s data. Now I am telling you because it really happened to me. It took my most online privacy.
91. Discussing Web3 Security with Forta Ecosystem Lead Andrew Beal
 A conversation with Andrew Beal, the spokesperson of Forta, on Web3 security, the rise in DeFi hacks, and where blockchain protocols are going wrong.
A conversation with Andrew Beal, the spokesperson of Forta, on Web3 security, the rise in DeFi hacks, and where blockchain protocols are going wrong.
92. Insight Into TCP/UDP, Network Vulnerabilities and Defense Approaches
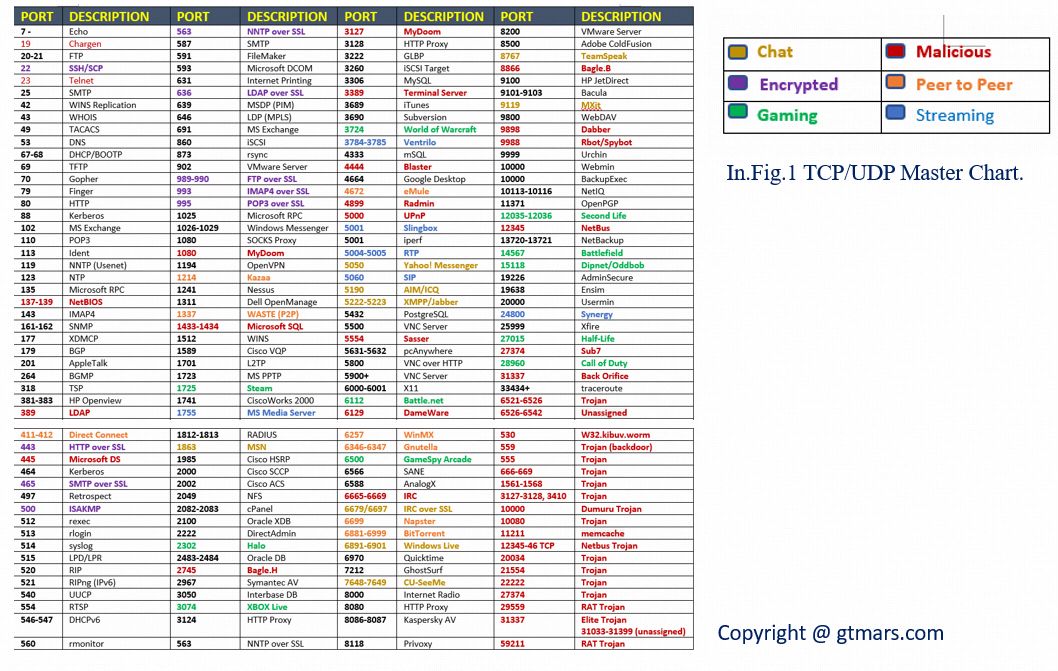 This article provides the network vulnerabilities and defense approaches, with a focus on all the TCP and UDP ports, Port vulnerability, and learn more about Windows, Linux server operation guide.
This article provides the network vulnerabilities and defense approaches, with a focus on all the TCP and UDP ports, Port vulnerability, and learn more about Windows, Linux server operation guide.
93. 5 Ways to Add Security to Excel & PDF with .NET Document APIs
 Learn how GcExcel helps to ensure your application’s code security in these 5 ways!
Learn how GcExcel helps to ensure your application’s code security in these 5 ways!
94. Password Security And Thoughts On Authentication Methods
 We use passwords to access personal information and user accounts. With so many applications requiring passwords (e.g. online banking, shopping and social media just to name a few), it can be hard to track and at worst remember. Some applications require users to change their passwords every so often, and that can lead to users forgetting them or getting careless by writing down their password on a piece of paper. That piece of paper can later be misplaced which can lead to worse things. The problem with requiring frequent password changes and applying complexity to passwords is that it can become more complicated for users.
We use passwords to access personal information and user accounts. With so many applications requiring passwords (e.g. online banking, shopping and social media just to name a few), it can be hard to track and at worst remember. Some applications require users to change their passwords every so often, and that can lead to users forgetting them or getting careless by writing down their password on a piece of paper. That piece of paper can later be misplaced which can lead to worse things. The problem with requiring frequent password changes and applying complexity to passwords is that it can become more complicated for users.
95. The Principles of Information Engineering on the Internet
 I envision that the future of Internet, Cyber Laws, Info Security & Governance will be very closely based on these ideas…Information Engineering Principles
I envision that the future of Internet, Cyber Laws, Info Security & Governance will be very closely based on these ideas…Information Engineering Principles
96. Meet the CyberSecurity Analyst Who Also Loves Trying Out Food Recipes
 I write about what keeps businesses secure and profitable and provide advisory to decision makers.
I write about what keeps businesses secure and profitable and provide advisory to decision makers.
97. Cybersecurity Basics, Tech Education and Market Review

98. Phone Scams: What Is Vishing And How You Can Avoid It
 The attack combines a one-on-one phone call with credible-looking phishing sites where the user is required to fill in their credentials and their MFA codes.
The attack combines a one-on-one phone call with credible-looking phishing sites where the user is required to fill in their credentials and their MFA codes.
99. WiFi Beaconing: A Way to Save Lives via Beacon Flooding
 Most of us have heard of WiFi beaconing or beacon flooding, or not? So what is it exactly and why does it matter for the purpose of this article?
Most of us have heard of WiFi beaconing or beacon flooding, or not? So what is it exactly and why does it matter for the purpose of this article?
100. In 2019, Securing Data Is No Easy Task. Clickjacking- A Case Study
 This article is about my journey to understand the current practice of de-anonymization via the clickjacking technique whereby a malicious website is able to uncover the identity of a visitor, including his full name and possibly other personal information. I don’t present any new information here that isn’t already publicly available, but I do look at how easy it is to compromise a visitor’s privacy and reveal his identity, even when he adheres to security best practices and uses an up-to-date browser and operating system.
This article is about my journey to understand the current practice of de-anonymization via the clickjacking technique whereby a malicious website is able to uncover the identity of a visitor, including his full name and possibly other personal information. I don’t present any new information here that isn’t already publicly available, but I do look at how easy it is to compromise a visitor’s privacy and reveal his identity, even when he adheres to security best practices and uses an up-to-date browser and operating system.
101. Privacy and Security, Though Distinct Concepts, Are Interdependent
 Security & Privacy are often confused, but are distinct. It’s important that we understand the difference so that we can protect ourselves
Security & Privacy are often confused, but are distinct. It’s important that we understand the difference so that we can protect ourselves
102. What I learned About Cybersecurity after becoming an ISSAP®
 Being a great security professional is not just about how excellent your technical skills. It would be best if you were particular about the choices or suggesti
Being a great security professional is not just about how excellent your technical skills. It would be best if you were particular about the choices or suggesti
103. How to Use the Merchant Network to Combat E-Commerce Fraud
 E-commerce fraud has been a problem websites have been facing for more than a decade. See how Merchant Network can help to fight fraud globally.
E-commerce fraud has been a problem websites have been facing for more than a decade. See how Merchant Network can help to fight fraud globally.
104. Why the SUNBURST Incident is More Alarming than the FireEye’s Hack
 Why the SUNBURST incident is more alarming than the FireEye’s hack.
Why the SUNBURST incident is more alarming than the FireEye’s hack.
105. How Should Companies Build a Robust Cybersecurity Culture?
 In the modern age of information and technology, there’s not a single individual or organization that would object to the tightening of cybersecurity within an enterprise.
In the modern age of information and technology, there’s not a single individual or organization that would object to the tightening of cybersecurity within an enterprise.
106. ISO/IEC 27035: The Incident Security Incident Management Guide
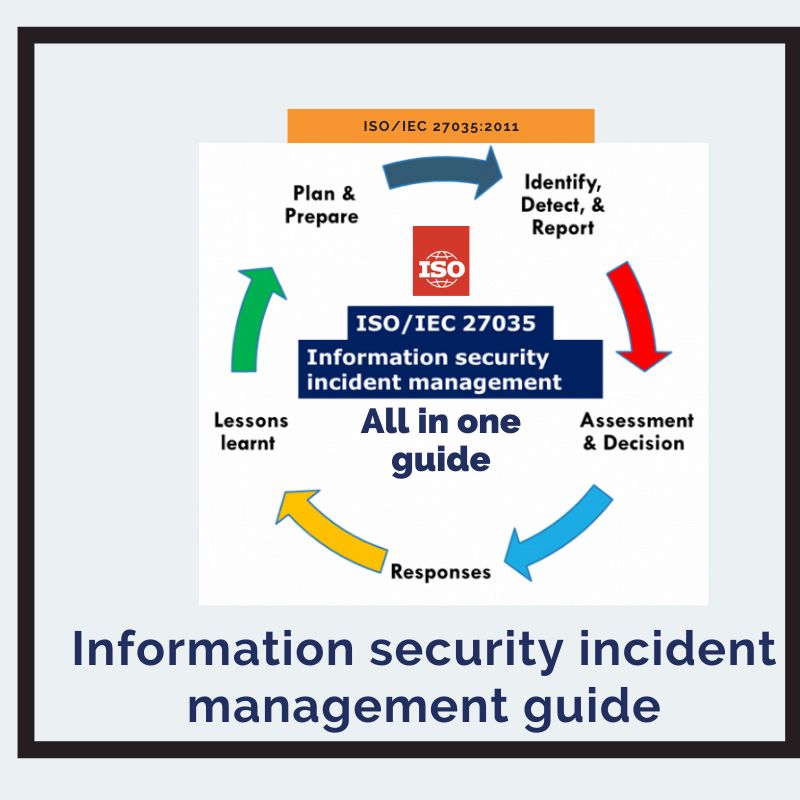 We will learn about the security incident phases, security incidents response planning (IRP), and Incident Response Team Structures.
We will learn about the security incident phases, security incidents response planning (IRP), and Incident Response Team Structures.
107. 3 Security Mindsets for Engineers, Consultants and Architects
 Describing a security mindset generally is impossible to be practical at the same time. To handle that, I would like to put your mind into 3 roles.
Describing a security mindset generally is impossible to be practical at the same time. To handle that, I would like to put your mind into 3 roles.
108. What Is the GIAC Penetration Tester (GPEN) Certification?
 You need to ensure your resources are put to the best use. With that in mind, it is important to know more about what the GIAC Penetration Tester Certification
You need to ensure your resources are put to the best use. With that in mind, it is important to know more about what the GIAC Penetration Tester Certification
109. 10 things InfoSec Professionals Need to Know About Networking

110. Need for an Identity Theft Protection
 Identity theft is a blanket term that covers fraudulent and even suspicious action through bank accounts and criminal databases. It is a violation of getting the financial or personal data of a person with the sole objective of feigning that person's name or identity to make purchases or transactions.
Identity theft is a blanket term that covers fraudulent and even suspicious action through bank accounts and criminal databases. It is a violation of getting the financial or personal data of a person with the sole objective of feigning that person's name or identity to make purchases or transactions.
111. Ensuring Security: A Guide for Web and Mobile Application Development
 Authentication and authorization for modern web and mobile applications are a key part of most development cycles. This story outlines some considerations.
Authentication and authorization for modern web and mobile applications are a key part of most development cycles. This story outlines some considerations.
112. Hide an Admin User on Cisco IOS (Router/Switch) Platform [A How-To Guide]
 Beginning Reminder: This article is written for research and experimentation purposes only. Only ever access devices you have written, legal authorization to access.
Beginning Reminder: This article is written for research and experimentation purposes only. Only ever access devices you have written, legal authorization to access.
113. The JBS Foods Cybersecurity Incident
 After the colonial cyberattack, cybercriminals targeted JBS food supply which resulted in an adverse impact on the IT infrastructure of the company.
After the colonial cyberattack, cybercriminals targeted JBS food supply which resulted in an adverse impact on the IT infrastructure of the company.
114. Helpful Strategies to Combat WhatsApp Security Threats
 In the previous year, a security flaw was found in the WhatsApp desktop version. It allowed cyber-crooks to push malware or deploy codes by using harmless messages.
In the previous year, a security flaw was found in the WhatsApp desktop version. It allowed cyber-crooks to push malware or deploy codes by using harmless messages.
115. How to Reduce the Risk of Former Employees Coordinating with Insider Threats
 Here below are a couple of tips to keep in mind when thinking about how to minimize your risk from insider threats.
Here below are a couple of tips to keep in mind when thinking about how to minimize your risk from insider threats.
116. How to Optimize Your Salesforce Security
 Companies implementing Salesforce’s internal security solutions may find their customizations limit visibility into the risks that can impact other processes.
Companies implementing Salesforce’s internal security solutions may find their customizations limit visibility into the risks that can impact other processes.
117. Understanding & Recognizing Different Cyber Threats: What to Look Out For
 This article will dive into understanding & recognizing some cyber threats. It will not cover every example for each attack or every attack.
This article will dive into understanding & recognizing some cyber threats. It will not cover every example for each attack or every attack.
118. Understanding IIC: Identity, Integrity, and Confidentiality

119. All about Security Information and Event Management

120. Does Anonymization of Data Guarantees Privacy?
 Anonymization of data isn’t enough to guarantee privacy
Anonymization of data isn’t enough to guarantee privacy
121. Unlocking the Power of Expert Red Teams: How to use Atomic Red Team (ART) to Think Like an Attacker

122. Why You Have No Choice But Care About Privacy?

123. 3 Ways To Protect Company Data From Being Exposed By Your Own Employees
 When people think about data leaks, they tend to assume the cause of the threat came from outside the company.
When people think about data leaks, they tend to assume the cause of the threat came from outside the company.
124. Being 'Chief Geek' and Running 15 Websites with Noonies Nominee Mathias Hellquist
 So who TF is Mathias Hellquist and what is a "Chief Geek"? Read this interview to find out.
So who TF is Mathias Hellquist and what is a "Chief Geek"? Read this interview to find out.
125. How Security Engineering is Changing the Cybersecurity Industry
 In this piece, I will expand on one of the trends related to this transformation - namely the rise of security engineering.
In this piece, I will expand on one of the trends related to this transformation - namely the rise of security engineering.
126. Ensuring Security in Your SaaS Applications [An Overview]

127. How Proxies & Browsers Are Meant to Work Together
 Proxies can be used for an IP covering, but other distinguishing features need something more. And all this because of a digital fingerprint revealing us.
Proxies can be used for an IP covering, but other distinguishing features need something more. And all this because of a digital fingerprint revealing us.
128. A Free Beginner’s Guide to DNS Security for Work From Home (WFH)
 Working at home does not mean compromise on security. All in all, it’s necessary to take decisive steps to enforce and sustain DNS protection measures.
Working at home does not mean compromise on security. All in all, it’s necessary to take decisive steps to enforce and sustain DNS protection measures.
129. Cyber Security vs Information Security
 Both cyber and information security are linked by the core discipline of security, and overlap between the two but we need to recognise the difference.
Both cyber and information security are linked by the core discipline of security, and overlap between the two but we need to recognise the difference.
130. IoT Security Challenges and Risk Mitigation Strategies
 The Internet of Things plays a key role in digital transformation. However, in many cases, organizations realize that they already have a large fleet of legacy
The Internet of Things plays a key role in digital transformation. However, in many cases, organizations realize that they already have a large fleet of legacy
131. How to Keep Mission-Critical Business Data Secure in the Mobile Age
 Andrew Nichols | Protecting Mission-Critical Business Data in the Mobile Age
Andrew Nichols | Protecting Mission-Critical Business Data in the Mobile Age
132. How To Make an Internal Employee Survey on Endpoint Security
 Employee’s Endpoint security Internal Survey-Template
Employee’s Endpoint security Internal Survey-Template
Thank you for checking out the 132 most read stories about Information Security on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

