Let's learn about Data Security via these 351 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
The protection of digital information from unauthorized access, corruption or theft, is a vital consideration in the constantly evolving digital ecosystem.
1. Mutual Human Authorization: A New Standard in Data Privacy
 Mutual Human Authorization is a digital communication protocol that SharePass is pioneering to help address persistent data privacy and security gaps.
Mutual Human Authorization is a digital communication protocol that SharePass is pioneering to help address persistent data privacy and security gaps.
2. 7 Ways To Protect Your Personal Information on the Internet

3. How 5 Massive Data Breaches Could Have Been Prevented
 One of the biggest losses for companies? Inadequate cybersecurity.
One of the biggest losses for companies? Inadequate cybersecurity.
4. Adding a Little Salt to Passwords Can Improve Security
 With the rise in cybersecurity threats, having a strong, secure password has become more critical than ever. In fact, did you know that the key reason behind 80% of data breaches in 2019 was password compromise?
With the rise in cybersecurity threats, having a strong, secure password has become more critical than ever. In fact, did you know that the key reason behind 80% of data breaches in 2019 was password compromise?
5. 7 Data Analysis Steps You Should Know
 To analyze data adequately requires practical knowledge of the different forms of data analysis.
To analyze data adequately requires practical knowledge of the different forms of data analysis.
6. How to Tell If Someone Hacked Your Active Directory
 The latest cybersecurity reports show that more breaches in the current day are done through credential leaks done through an active directory compromise
The latest cybersecurity reports show that more breaches in the current day are done through credential leaks done through an active directory compromise
7. The Two Best Ways to Scan for PII in Your Data Warehouse
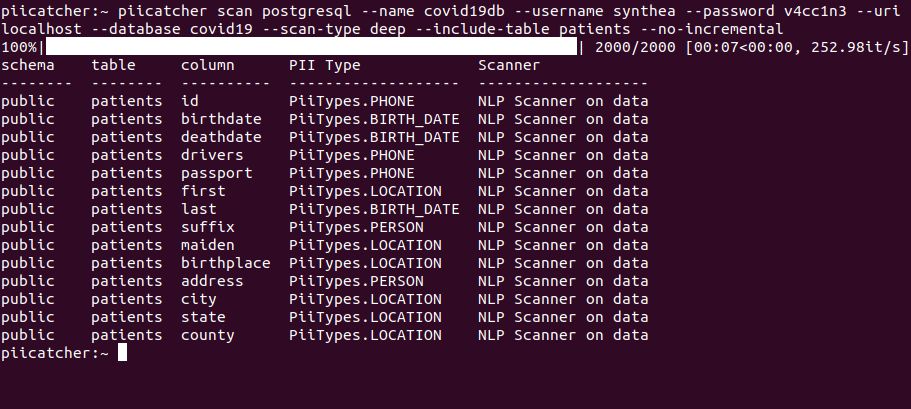 Find PII data by scanning column names and/or data in your data warehouse with these two easy to create methods and a step-by-step guide on how to do it.
Find PII data by scanning column names and/or data in your data warehouse with these two easy to create methods and a step-by-step guide on how to do it.
8. Delete Your Old Tweets: 90% of Employers Consider Your Social Media Activity When Hiring
 A survey shows that 90% of employers consider your social media activity when hiring and a whopping 79% of HR have rejected a candidate because of social media.
A survey shows that 90% of employers consider your social media activity when hiring and a whopping 79% of HR have rejected a candidate because of social media.
9. Your USB Gadget Could Be Weaponized
 Cybersecurity experts have been warning us for years about using USB devices. We look at how an ordinary USB-powered device can be easily weaponized.
Cybersecurity experts have been warning us for years about using USB devices. We look at how an ordinary USB-powered device can be easily weaponized.
10. Edge Computing and the Metaverse
 Edge computing in relation to the metaverse
Edge computing in relation to the metaverse
11. Are VPNs Really Safe?
 Virtual Private Network (VPN) cloaks your online identity, and shielding your data from prying eyes.
Virtual Private Network (VPN) cloaks your online identity, and shielding your data from prying eyes.
12. How to Prevent Juice Jacking
 Juice jacking occurs when a hacker has infected a USB port with some form of malware or other harmful software.
Juice jacking occurs when a hacker has infected a USB port with some form of malware or other harmful software.
13. How To Prevent Ransomware Attacks: A Threat That’s Real
 Ransomware works by encrypting the user’s data, making it unreadable. If a user wants their data back, a ransom must be paid. Keep reading to learn more
Ransomware works by encrypting the user’s data, making it unreadable. If a user wants their data back, a ransom must be paid. Keep reading to learn more
14. CVEs: How Keeping a Catalogue of Common Vulnerabilities and Exposures Helps Your Company
 CVE combines a dictionary and a catalog containing names for vulnerabilities and other information security vulnerabilities.
CVE combines a dictionary and a catalog containing names for vulnerabilities and other information security vulnerabilities.
15. Is Your Organization Safe from Common Cybersecurity Threats?
 Many companies simply aren't protected from threats online - here's the most common and a guide to what you need to do
Many companies simply aren't protected from threats online - here's the most common and a guide to what you need to do
16. Cybersecurity Lessons from Working with the Ecuadorian Government
 I’m currently temtum cryptocurrency CTO, we’re in the process of launching our cryptocurrency which will change the way we all make payments. But I wanted to share an earlier experience of working with the Ecuadorian government to ensure the cyber and data security of my home nation. It was one of my proudest moments, a unique and rewarding challenge, one that I will never forget.
I’m currently temtum cryptocurrency CTO, we’re in the process of launching our cryptocurrency which will change the way we all make payments. But I wanted to share an earlier experience of working with the Ecuadorian government to ensure the cyber and data security of my home nation. It was one of my proudest moments, a unique and rewarding challenge, one that I will never forget.
17. 2 Million Fitbit Accounts Were Exposed by Cybercriminals
 A user on a well-known hacker community has leaked the emails and passwords of 1,999,999 users of the widely used health and fitness platform Fitbit, famous for its gadgets like smartwatches, and innovative fitness apps that track your training and sleeping patterns (among other things). The platform was recently acquired by Google LLC in a $2.1 billion USD deal.
A user on a well-known hacker community has leaked the emails and passwords of 1,999,999 users of the widely used health and fitness platform Fitbit, famous for its gadgets like smartwatches, and innovative fitness apps that track your training and sleeping patterns (among other things). The platform was recently acquired by Google LLC in a $2.1 billion USD deal.
18. 4 Signs Your Instagram Has Been Hacked (and What to Do)
 How can you tell if your Instagram has been hacked and what can you do about it? Find out the signs of hacked Instagram accounts and how they affect businesses
How can you tell if your Instagram has been hacked and what can you do about it? Find out the signs of hacked Instagram accounts and how they affect businesses
19. Salesforce Sandbox Data Mask For Add-On Security And Sandbox Refresh Process
 When it comes to data security, Salesforce sandbox Data Mask is a mighty tool, which is largely used by the Salesforce developer and admins lately.
When it comes to data security, Salesforce sandbox Data Mask is a mighty tool, which is largely used by the Salesforce developer and admins lately.
20. 8 Skills Required To Become A Data Scientist
 Back in 2016, Glassdoor declared that being a Data Scientist was the best job in America.
Back in 2016, Glassdoor declared that being a Data Scientist was the best job in America.
21. How Much Does the CEH Exam Cost?
 EC-Council’s Certified Ethical Hacker (CEH) is one of the most established and recognized offensive security certifications. The certification is ANSI-accredited and DoDD 8140-approved because of which the certification in highly valued by security professionals from both the public and private sectors. Since CEH is the gold standard for validating offensive security skills, the CEH certification cost is around $1,199 and the cost to retake the exam is $450. This article will cover the various processes you have to go through to earn this certification as well as the associated costs.
EC-Council’s Certified Ethical Hacker (CEH) is one of the most established and recognized offensive security certifications. The certification is ANSI-accredited and DoDD 8140-approved because of which the certification in highly valued by security professionals from both the public and private sectors. Since CEH is the gold standard for validating offensive security skills, the CEH certification cost is around $1,199 and the cost to retake the exam is $450. This article will cover the various processes you have to go through to earn this certification as well as the associated costs.
22. How to Implement QA Testing in a Confidential and Secure Manner
 ‘Privacy’ and ‘Confidentiality’ are often used interchangeably but they are not the same.
‘Privacy’ and ‘Confidentiality’ are often used interchangeably but they are not the same.
23. Top Signs that Indicate You Are About To Suffer a Cyber Breach
 There are few things worse than being told that your business’s security has been compromised. Organizations might not know that a security breach is taking place, or has been for some time. Yet, risk mitigation and technical safeguards are always getting better.
There are few things worse than being told that your business’s security has been compromised. Organizations might not know that a security breach is taking place, or has been for some time. Yet, risk mitigation and technical safeguards are always getting better.
24. What happened After I Scanned 2.6 Million Domains for Exposed .DS_Store Files

25. 5 Reasons Why VPNs are not Safe in 2021
 All good things must come to an end, which may be true for the VPN in 2021. VPNs have been a useful enterprise tool for companies since they started in the 90s,
All good things must come to an end, which may be true for the VPN in 2021. VPNs have been a useful enterprise tool for companies since they started in the 90s,
26. Orchestrating Identity in Web3.0
 Identity needs a major re-think for Web 3.0. We need private and effective, dynamic authorization - but no, I am not talking about blockchain.
Identity needs a major re-think for Web 3.0. We need private and effective, dynamic authorization - but no, I am not talking about blockchain.
27. The Security Issues in Using Public Wi-Fi — “Honeypots” And “Pineapples”
 It is a warm and sunny afternoon on a weekend. This is a good time to head to a cafe to chill for a bit with a coffee and pastry. It is also perfect for some web surfing using the free Wi-Fi service. The next thing you would need to know is the Wi-Fi access point (i.e. hotspot) and password. Now you are all set and connect to the Internet. For the average user this is fine, but for cybersecurity experts there is a risk to using free Wi-Fi services.
It is a warm and sunny afternoon on a weekend. This is a good time to head to a cafe to chill for a bit with a coffee and pastry. It is also perfect for some web surfing using the free Wi-Fi service. The next thing you would need to know is the Wi-Fi access point (i.e. hotspot) and password. Now you are all set and connect to the Internet. For the average user this is fine, but for cybersecurity experts there is a risk to using free Wi-Fi services.
28. Privacy Enhancing Technologies: Top 3 Use Cases
 Security and risk management leaders can apply privacy-enhancing tech in AI modelling, cross-border data transfers, and data analytics to manage constraints.
Security and risk management leaders can apply privacy-enhancing tech in AI modelling, cross-border data transfers, and data analytics to manage constraints.
29. 3.6 Million Websites Went Offline Due To a Fire: Decentralization Prevents That
 Recently, the cloud computing company and hosting provider OVH has had a fire that caused nearly 3.6 million websites to go offline. Some of the websites effected was a government site for the French government, and even a cryptocurrency exchange. According to Reuters, many of those sites were told to, "activate their disaster recovery plans following the blaze."
Recently, the cloud computing company and hosting provider OVH has had a fire that caused nearly 3.6 million websites to go offline. Some of the websites effected was a government site for the French government, and even a cryptocurrency exchange. According to Reuters, many of those sites were told to, "activate their disaster recovery plans following the blaze."
30. An Intro to Zero-Knowledge Proofs (ZKP) and Identity
 Learn about Zero Knowledge claims and how they can help in securing your Identity.
Learn about Zero Knowledge claims and how they can help in securing your Identity.
31. The Best Way to Protect Your Data: Continuous Security Validation
 Security validation is a cybersecurity method that provides companies with an extensive security report on what could happen if they suffer from a cyberattack.
Security validation is a cybersecurity method that provides companies with an extensive security report on what could happen if they suffer from a cyberattack.
32. Cybersecurity Awareness Month - MacPaw Supports Ukraine
 How can two apps from Ukrainian developers, MacPaw, help ensure your data and personal security?
How can two apps from Ukrainian developers, MacPaw, help ensure your data and personal security?
33. Businesses Will Face These 4 Cloud Security Challenges in 2021
 As threats have sophisticated and evolved, new attacks emerge and it becomes more important than ever for businesses to embrace security first mentalities.
As threats have sophisticated and evolved, new attacks emerge and it becomes more important than ever for businesses to embrace security first mentalities.
34. 4 Reasons for Cyber Intelligence Failure
 Cybersecurity is a complex game of cat-and-mouse between you and would-be hackers.
Cybersecurity is a complex game of cat-and-mouse between you and would-be hackers.
35. The Big Security Picture - A Case of Integrating CSPM into XDR
 Investing in both CSPM and XDR solutions allows organizations visibility into both the riskcape and the threatscape of their ecosystem.
Investing in both CSPM and XDR solutions allows organizations visibility into both the riskcape and the threatscape of their ecosystem.
36. A How-to Guide for Data Backup and VM Modernization
 Data is everywhere it is something that we all rely on. It is used by individuals and large organizations that collect and store hundreds of files a day.
Data is everywhere it is something that we all rely on. It is used by individuals and large organizations that collect and store hundreds of files a day.
37. How Am I Being Tracked Online? A Story.
 How are users being tracked online even when taking privacy precautions? What tools are Meta and others using to target you with ads?
How are users being tracked online even when taking privacy precautions? What tools are Meta and others using to target you with ads?
38. What will IBM's Acquisition of Randori Mean for Cybersecurity?
 IBM announced plans to acquire a leading attack surface management provider and offensive security company Randori.
IBM announced plans to acquire a leading attack surface management provider and offensive security company Randori.
39. 8 Most Important Cybersecurity Tricks Every Internet User Should Follow
 The cyber-world now accommodates billions of users. There are more than 4 billion internet users in the world today. It's just unfortunate that a large percentage of these users face cyber attacks from unknown sources. While some users are afraid of being attacked, others are ignorant of possible attacks. As an organisation or an individual that utilises the internet, it's a must to know some security tricks. If you're wondering what the tricks are, read on.
The cyber-world now accommodates billions of users. There are more than 4 billion internet users in the world today. It's just unfortunate that a large percentage of these users face cyber attacks from unknown sources. While some users are afraid of being attacked, others are ignorant of possible attacks. As an organisation or an individual that utilises the internet, it's a must to know some security tricks. If you're wondering what the tricks are, read on.
40. 3 Key Takeaways from Biden’s Cybersecurity Executive Order
 Learn more about the consequences of Biden's Executive Order on Improving the Nation’s Cybersecurity on software vendors and government contractors.
Learn more about the consequences of Biden's Executive Order on Improving the Nation’s Cybersecurity on software vendors and government contractors.
41. How Keyloggers Can Help to Protect Employees in Your Organisation
 Additionally, software (keyloggers) can also be used to detect and prevent cyber-attacks.
Additionally, software (keyloggers) can also be used to detect and prevent cyber-attacks.
42. 7 Serious Security Issues in Big Data and How to Address Them
 Businesses will be able to reach their ultimate aim of leveraging data for better customer experience and retention if they use Big Data effectively.
Businesses will be able to reach their ultimate aim of leveraging data for better customer experience and retention if they use Big Data effectively.
43. Data Engineering Tools for Geospatial Data
 Location-based information makes the field of geospatial analytics so popular today. Collecting useful data requires some unique tools covered in this blog.
Location-based information makes the field of geospatial analytics so popular today. Collecting useful data requires some unique tools covered in this blog.
44. Moving Beyond the Physical Data Centers: Decentralized Internet Interview
 Tigerchop's views on Decentralized Internet.
Tigerchop's views on Decentralized Internet.
45. Asked for a Parka, Got an “Error 429: Too Many Requests”
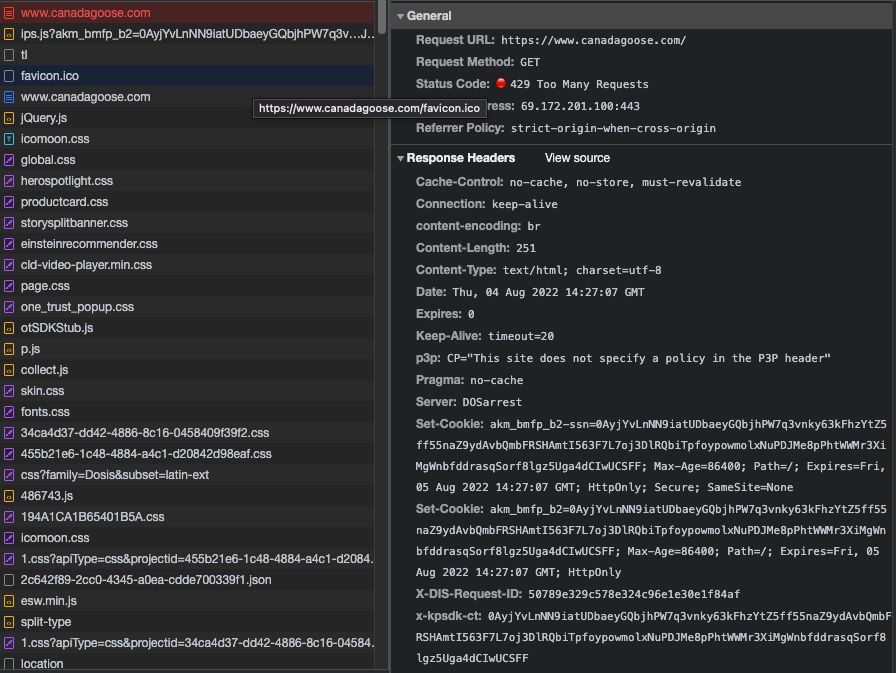 Anti-bot techniques are getting life harder for web scrapers. In this post we'll see how Kasada protects a website and how a misconfiguration of it can be used
Anti-bot techniques are getting life harder for web scrapers. In this post we'll see how Kasada protects a website and how a misconfiguration of it can be used
46. Building an Airtight Security Funnel Step-by-Step
 In this article, we’ll walk through SharePass’s patent-pending security funnel, providing a step-by-step guide to building out your security pipeline.
In this article, we’ll walk through SharePass’s patent-pending security funnel, providing a step-by-step guide to building out your security pipeline.
47. Preventing Cybersecurity Risks in Crypto
 In this post, we’ll explore the most pressing cybersecurity challenges facing crypto today and offer some solutions along with them.
In this post, we’ll explore the most pressing cybersecurity challenges facing crypto today and offer some solutions along with them.
48. What's in Store for Privacy and Personal Data Protection in 2022?
 2021 saw many advancements in internet privacy, what does 2022 have in store?
2021 saw many advancements in internet privacy, what does 2022 have in store?
49. 8 Cloud Compliance Frameworks and Why Cloud-based Organizations Need Them
 Cloud compliance frameworks help an organization to keep its database secure and private. In this article, you will eight such frameworks that can guide you.
Cloud compliance frameworks help an organization to keep its database secure and private. In this article, you will eight such frameworks that can guide you.
50. Self-Sovereign Identity: What’s the Big Deal?
 Want to own your online data? Want to decide where it's stored and how it's used. Self-sovereign identity can do it for you. Read on to see why it's a big deal.
Want to own your online data? Want to decide where it's stored and how it's used. Self-sovereign identity can do it for you. Read on to see why it's a big deal.
51. A New Study On Data Privacy Reveals Information About Cybersecurity Efforts
 A study revealed by Cisco shows that most organizations around the world were unprepared for the increase in remote work.
A study revealed by Cisco shows that most organizations around the world were unprepared for the increase in remote work.
52. Reconstruction Attacks: Examples of Invasion of Your Privacy Without Consent
53. Understanding JWTs from Beginning to End
 In this article, we will explore mainly JWT and JWS. In addition, we'll also go through JWE, JWA, and JWK quickly.
In this article, we will explore mainly JWT and JWS. In addition, we'll also go through JWE, JWA, and JWK quickly.
54. The Best Cybersecurity Practices for Data Centres
 Read on to learn about the specifications of data center security and the risks that threaten it. Discover the cybersecurity best practices that you need.
Read on to learn about the specifications of data center security and the risks that threaten it. Discover the cybersecurity best practices that you need.
55. How to Keep Sensitive Data Out of Your Logs
 Do you protect customer PII and PHI, keeping them out of your logs? Learn about why and how to isolate this sensitive data with a data privacy vault and API.
Do you protect customer PII and PHI, keeping them out of your logs? Learn about why and how to isolate this sensitive data with a data privacy vault and API.
56. What Are Keyloggers and Why Do You Need Them
 This article will explain keylogging software and why people might want to install it on their laptops.
This article will explain keylogging software and why people might want to install it on their laptops.
57. Beginners Guide to Preventing Permission Bloat: Overlooked and Hidden Access
 When it comes to your organizational security, there should be no stone left unturned. Unfortunately, many organizations fail to do this, as they aren’t even aware that there are unturned stones. Overlooked access rights are one of the most unnoticed security threats your organization can face—less of a stone and more of a somehow-overlooked, but ever-looming mountain.
When it comes to your organizational security, there should be no stone left unturned. Unfortunately, many organizations fail to do this, as they aren’t even aware that there are unturned stones. Overlooked access rights are one of the most unnoticed security threats your organization can face—less of a stone and more of a somehow-overlooked, but ever-looming mountain.
58. Password Security in 2022 — A Complete Guide
 A comprehensive guide to password security for all IT managers (and everyone else!). Learn why it is important, the risks of insecure passwords and how you can
A comprehensive guide to password security for all IT managers (and everyone else!). Learn why it is important, the risks of insecure passwords and how you can
59. How To Harden Your Docker Containers Using Seccomp Security Profile
 Secure Computing Mode, also known as Seccomp, is a Linux kernel feature that improves several security features to help run Docker in a more secure environment.
Secure Computing Mode, also known as Seccomp, is a Linux kernel feature that improves several security features to help run Docker in a more secure environment.
60. Cyber Security: A Guide on Choosing a Reliable Service
 Nowadays, Cyber security is a trending topic around the globe. It has become a necessity for every business with the growing cyber threats.
Nowadays, Cyber security is a trending topic around the globe. It has become a necessity for every business with the growing cyber threats.
61. 10 Reasons to Get Your Cybersecurity Certification

62. The Cyber-Mindset That Can Destroy SMBS.
 Nowadays, we get to see a lot of cyber attacks in our world. —Cyber attacks can happen anytime, anywhere.
Nowadays, we get to see a lot of cyber attacks in our world. —Cyber attacks can happen anytime, anywhere.
63. How to Solve Enterprise Data Breaches with Turnkey Neobank Solutions
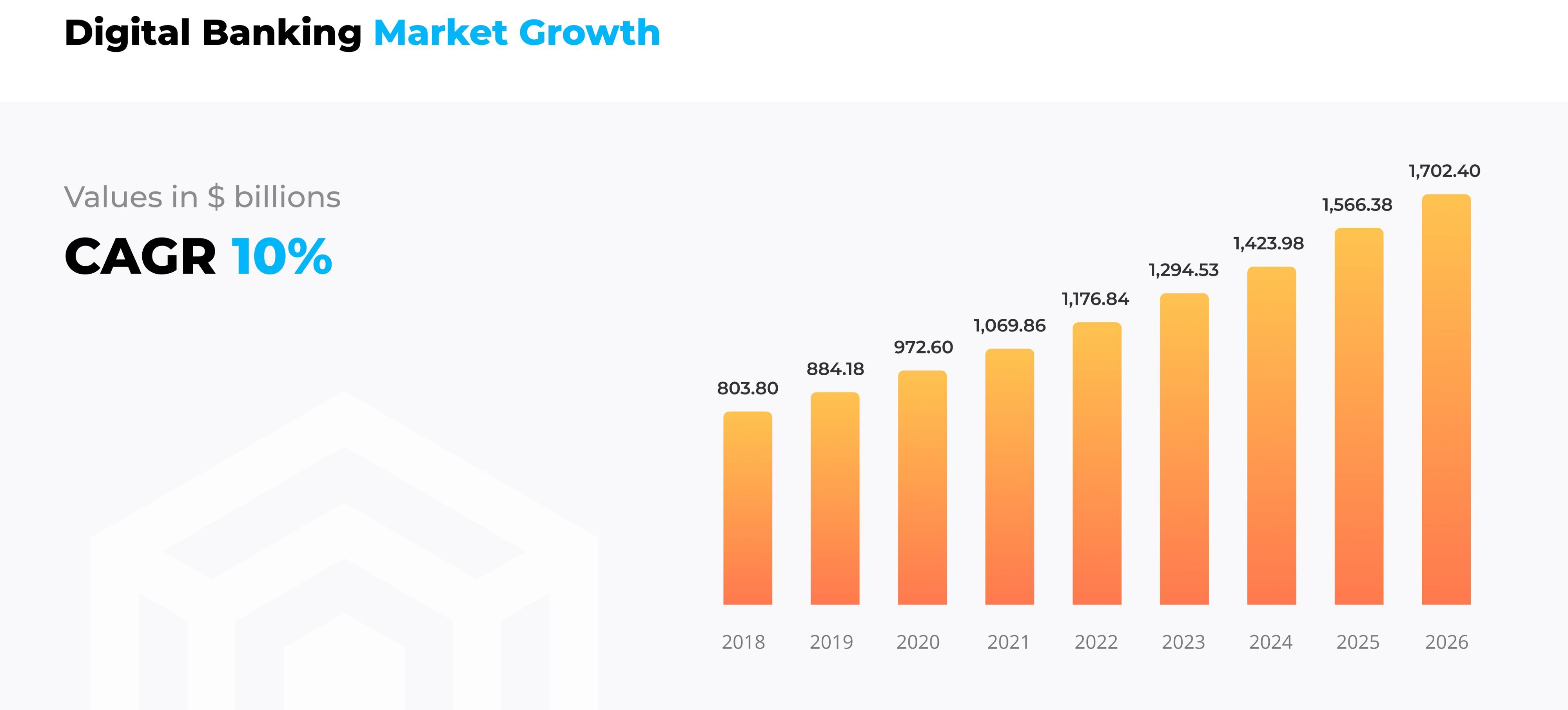 Digital banking is emerging as one of the fastest-growing segments
across the globe. The over $800 billion in revenue generated in 2018 is
projected to grow at a CAGR of 10% over the next 5 years, reaching $1.7
trillion by 2026.
Digital banking is emerging as one of the fastest-growing segments
across the globe. The over $800 billion in revenue generated in 2018 is
projected to grow at a CAGR of 10% over the next 5 years, reaching $1.7
trillion by 2026.
64. How do Hackers Hide Themselves? - A Guide to Staying Anonymous Online
 The world has always been fascinated with Hackers. In this video, we’ll learn about how they hide themselves online.
The world has always been fascinated with Hackers. In this video, we’ll learn about how they hide themselves online.
65. In a Time of Crisis, Data Must Be Able to Defend Itself

66. How to Approach Web3 from a Security Perspective
 Approach Web3 from a Security Perspective
Approach Web3 from a Security Perspective
67. Top 10 Antivirus Softwares in 2021
 These are the top 10 Antivirus software options on the market in 2021. Depending on your device (Mac, PC, Android, or iOS), there is an appropriate Antivirus.
These are the top 10 Antivirus software options on the market in 2021. Depending on your device (Mac, PC, Android, or iOS), there is an appropriate Antivirus.
68. Data Breaches: No Longer Delivering Punches to Business Reputation?
 Photo by NeONBRAND on Unsplash
Photo by NeONBRAND on Unsplash
69. Could Capture-Resistance Liberate the Web As We Know It?
 The internet, by design, has enabled many forms of capture from data mining to market manipulation. So how do we build infrastructures which avoid capture?
The internet, by design, has enabled many forms of capture from data mining to market manipulation. So how do we build infrastructures which avoid capture?
70. Cryptocurrency Security Threats: Lessons from Top Exchange Hacks
 The digital nature of Bitcoin makes it vulnerable to hacking.
The digital nature of Bitcoin makes it vulnerable to hacking.
71. Why Are Tech Giants Pushing For MFA Adoption?
 For MFA adoption to really take off, organizations need to understand the real value of MFA and how to effectively implement it.
For MFA adoption to really take off, organizations need to understand the real value of MFA and how to effectively implement it.
72. A Cryptographer's Guide to End-to-End Encryption
 End-to-end encryption is getting traction for secure communications. But how is it different from all other types of encryption? Here is a basic guide to it.
End-to-end encryption is getting traction for secure communications. But how is it different from all other types of encryption? Here is a basic guide to it.
73. Maximize Cybersecurity with Multiple Databases
 If securing your company’s intellectual property is such a complex process, how can business leaders efficiently defend their assets? Use multiple databases.
If securing your company’s intellectual property is such a complex process, how can business leaders efficiently defend their assets? Use multiple databases.
74. Understanding XDR in Security - Advantages and Use Cases
 XDR takes raw data that is set up in the environment and picks up bad actors that are taking advantage of software to help get into the system.
XDR takes raw data that is set up in the environment and picks up bad actors that are taking advantage of software to help get into the system.
75. 6 Major SCADA Attacks That Happened And Their Consequences
 Here we will look at the top SCADA attacks that have happened in the past.
Here we will look at the top SCADA attacks that have happened in the past.
76. Preventing Data Loss for Office 365 and Microsoft Teams While WFH [Interview]
 I caught up with Sergei Serdyuk, VP of Product Management at Nakivo to talk about the importance of data backup and recovery for Office 365.
I caught up with Sergei Serdyuk, VP of Product Management at Nakivo to talk about the importance of data backup and recovery for Office 365.
77. Cybersecurity is a Big Competitive Advantage. Secure Your Win.
 A majority of America's small business owners aren't worried about being the victim of a cyberattack. Why?
A majority of America's small business owners aren't worried about being the victim of a cyberattack. Why?
78. Ensuring Privacy with Zero-party Data
 Zero-party data is the future of data collection because it bridges the gap between advertising needs and consumers’ concerns about privacy.
Zero-party data is the future of data collection because it bridges the gap between advertising needs and consumers’ concerns about privacy.
79. TikTok: A Ticking Time Bomb?
 One of the most popular apps of 2019, TikTok ruled the download charts in both the Android and Apple markets. Having more than 1.5 billion downloads and approximately half a billion monthly active users, TikTok definitely has access to a trove of users. With that large user base comes a hidden goldmine: their data.
One of the most popular apps of 2019, TikTok ruled the download charts in both the Android and Apple markets. Having more than 1.5 billion downloads and approximately half a billion monthly active users, TikTok definitely has access to a trove of users. With that large user base comes a hidden goldmine: their data.
80. The Importance of Proper Password Security in 2022
 A look at the importance of proper password security in 2022
A look at the importance of proper password security in 2022
81. Everything you Need to Know About the CompTIA Security+ SY0-601 Certification
 CompTIA Security+ SY0-601 certification is to provide IT professionals with the knowledge required to install, configure, manage & troubleshoot security system.
CompTIA Security+ SY0-601 certification is to provide IT professionals with the knowledge required to install, configure, manage & troubleshoot security system.
82. Hospitals Remove Facebook Tracker but Questions Still Remain
 Meanwhile, developments in another legal case suggest Meta may have a hard time providing the Senate committee with a complete account of the health data.
Meanwhile, developments in another legal case suggest Meta may have a hard time providing the Senate committee with a complete account of the health data.
83. 5 Security Nightmares that Haunt Your IT Department’s Dreams
 5 common security threats to watch for along with some tips to help protect your company from cyber boogeymen lurking in the shadows.
5 common security threats to watch for along with some tips to help protect your company from cyber boogeymen lurking in the shadows.
84. How to Keep Your Data More Secure in 2022 🔒
 Encrypting online data with Cryptomator before uploading to cloud storage services in 2022. How to protect sensitive online data with file encryption by Louis M
Encrypting online data with Cryptomator before uploading to cloud storage services in 2022. How to protect sensitive online data with file encryption by Louis M
85. Data Loss Prevention: What is it, and Do You Need it?
 Data Loss Prevention is a set of tools and practices geared towards protecting your data from loss and leak. Even though the name has only the loss part, in actuality, it's as much about the leak protection as it is about the loss protection. Basically, DLP, as a notion, encompasses all the security practices around protecting your company data.
Data Loss Prevention is a set of tools and practices geared towards protecting your data from loss and leak. Even though the name has only the loss part, in actuality, it's as much about the leak protection as it is about the loss protection. Basically, DLP, as a notion, encompasses all the security practices around protecting your company data.
86. Data Security 101 for First Time Data Labeling Outsourcers
 AI project teams using large amounts of data with detailed labeling requirements can be up against the clock. The tools, human resourcing, and QA for maintaining precision can be a challenge. It’s easy to understand why outsourcing is preferred by most project teams. Outsourcing allows you to focus on core tasks.
AI project teams using large amounts of data with detailed labeling requirements can be up against the clock. The tools, human resourcing, and QA for maintaining precision can be a challenge. It’s easy to understand why outsourcing is preferred by most project teams. Outsourcing allows you to focus on core tasks.
87. Your Wi-Fi Cameras may be getting Attacked
 Your Wi-Fi security cameras are probably not secure. See how we disable our camera network with a simple DoS attack.
Your Wi-Fi security cameras are probably not secure. See how we disable our camera network with a simple DoS attack.
88. 5 Ways to Ensure You Aren’t Sharing Your Workplace Data
 With so much of our lives online, it's too easy for us to make a mistake and accidentally share our workplace data. These easy methods keep your data safe.
With so much of our lives online, it's too easy for us to make a mistake and accidentally share our workplace data. These easy methods keep your data safe.
89. 10 Factors to Prepare for CCPA (California Consumer Privacy Act)
 Be ready for CCPA with these top 10 critical factors
Be ready for CCPA with these top 10 critical factors
90. A Look at COVID’s Impact on Data Privacy and Protection
 After more than a year into the pandemic, it’s clear that COVID-19 will have lasting impacts. As companies rapidly embraced digital transformation, data privacy and protection have seen some of the most significant changes. COVID data risks and policies will likely far outlast the virus itself.
After more than a year into the pandemic, it’s clear that COVID-19 will have lasting impacts. As companies rapidly embraced digital transformation, data privacy and protection have seen some of the most significant changes. COVID data risks and policies will likely far outlast the virus itself.
91. What is Runtime Application Self-Protection
 What is Runtime Application Self-Protection? Know how RASP is capable of controlling app execution, detecting & preventing real-time attacks.
What is Runtime Application Self-Protection? Know how RASP is capable of controlling app execution, detecting & preventing real-time attacks.
92. Malicious Insider Makes Major Mistakes in Ubiquiti Extortion Case
 By the end of 2021, we are all pretty familiar with the script when it comes to ransomware attacks. These types of attacks have been running rampant.
By the end of 2021, we are all pretty familiar with the script when it comes to ransomware attacks. These types of attacks have been running rampant.
93. Three New Dimensions to Ransomware Attacks Emerge During Pandemic
![]() Three significant new trends in cyber-attacks have emerged from the Covid-19 emergency. Firstly, a new generation of attack software which has been developing since last summer has come of age and been deployed. Secondly, the business model for extracting payment from victims has changed so that there are multiple demands for payments of different kinds, including auctioning off data. Thirdly, the kinds of clients that the gangs are targeting seems to have shifted.
Three significant new trends in cyber-attacks have emerged from the Covid-19 emergency. Firstly, a new generation of attack software which has been developing since last summer has come of age and been deployed. Secondly, the business model for extracting payment from victims has changed so that there are multiple demands for payments of different kinds, including auctioning off data. Thirdly, the kinds of clients that the gangs are targeting seems to have shifted.
94. How to Encrypt and Decrypt with NodeJS
 A simple tutorial to learn Encryption in NodeJS.
A simple tutorial to learn Encryption in NodeJS.
95. Choosing between Object Storage and Block Storage for Security
 Block Storage and object storage have different use-cases. We won’t categorically state which one is better as the answer depends on your project’s particulars. What we will do in this article is compare these two storage options in terms of how secure your data is in either of them.
Block Storage and object storage have different use-cases. We won’t categorically state which one is better as the answer depends on your project’s particulars. What we will do in this article is compare these two storage options in terms of how secure your data is in either of them.
96. Using Unmasked Production Data For Testing Leaves Your At Risk For Data Breaches
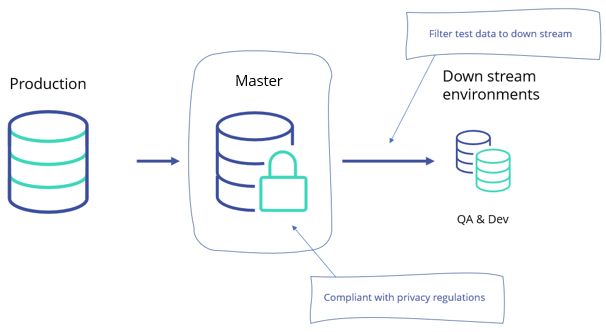
97. What Is Threat Intelligence Used For?
 What is threat intelligence, and how should you use it to better protect yourself from cyber threats?
What is threat intelligence, and how should you use it to better protect yourself from cyber threats?
98. A Rudimentary Introduction to the Internet of Things
 This is a breakdown of the Internet of Things for beginners. It includes definitions, use cases, and basic concerns.
This is a breakdown of the Internet of Things for beginners. It includes definitions, use cases, and basic concerns.
99. Life360 Potentially Leaves Its Users’ Sensitive Data at Risk
 The family safety app Life360 doesn’t have some standard guardrails to prevent a hacker from taking over an account and accessing sensitive information.
The family safety app Life360 doesn’t have some standard guardrails to prevent a hacker from taking over an account and accessing sensitive information.
100. Did Martin Shkreli Topple FTX's House of Cards?
 A source on Twitter has released unconfirmed audio of (allegedly) Martin Shkreli making unverified claims that he was behind FTX's and SBF's stunning downfall.
A source on Twitter has released unconfirmed audio of (allegedly) Martin Shkreli making unverified claims that he was behind FTX's and SBF's stunning downfall.
101. Formjacking Attacks: Defention and How To Prevent It
 Formjacking attacks are designed to steal financial details from payment forms. Learn how it affects your business and tips to prevent a formjacking attack.
Formjacking attacks are designed to steal financial details from payment forms. Learn how it affects your business and tips to prevent a formjacking attack.
102. Anonymity and Privacy in Emerging Web3 Spaces Make the World go Round
 Considering previous legal theory & recent web3 events, it can be argued that the framework of privacy needs to be updated with an understanding of consent.
Considering previous legal theory & recent web3 events, it can be argued that the framework of privacy needs to be updated with an understanding of consent.
103. What is a 'Data Fabric'?
 A Data Fabric is a mix of architecture and technology that aims to ease the difficulty and complexity of managing several different data types.
A Data Fabric is a mix of architecture and technology that aims to ease the difficulty and complexity of managing several different data types.
104. Homeland Insecurity
 Innovation can solve a country’s problems, but it can also simultaneously put your private information into a hacker’s playbook.
Innovation can solve a country’s problems, but it can also simultaneously put your private information into a hacker’s playbook.
105. Is Women’s Data Safe in a Post-Roe v Wade America?
 Can women be prosecuted for Googling “abortion pills”? The TL;DR: women who are looking to end their pregnancy in the US have cause for concern.
Can women be prosecuted for Googling “abortion pills”? The TL;DR: women who are looking to end their pregnancy in the US have cause for concern.
106. 5 Ways to Add Security to Excel & PDF with .NET Document APIs
 Learn how GcExcel helps to ensure your application’s code security in these 5 ways!
Learn how GcExcel helps to ensure your application’s code security in these 5 ways!
107. Two Factor Authentication - The Deep State Tool That Supports Mass Technology Dysfunction
 2FA is the initial, mandatory stage of ongoing privacy intrusions that are unwarranted and Orwellian. Alternatives now exist.
2FA is the initial, mandatory stage of ongoing privacy intrusions that are unwarranted and Orwellian. Alternatives now exist.
108. GDPR vs CCPA: Data Privacy On The Lead [Infographic]
 A quick look at the two approaches to privacy
A quick look at the two approaches to privacy
109. What an IP Address Can Reveal About You
 Is it possible to trace an IP ? To what extent does it reveal your physical location? How to prevent your IP from being tracked? Let's learn more about IP.
Is it possible to trace an IP ? To what extent does it reveal your physical location? How to prevent your IP from being tracked? Let's learn more about IP.
110. How Will User Experience Change in 2023?
 Overall, users will expect more honest, human, immersive, and technology-driven CX.
Overall, users will expect more honest, human, immersive, and technology-driven CX.
111. What Hackers Do With Your Data
 4 ways your data is being used without your knowledge
4 ways your data is being used without your knowledge
112. How Proactive API Visibility Could've Saved Optus From a Massive Data Breach
 On 22 September 2022, Australia's second-largest telecom company, Optus, announced that it had suffered a significant data breach.
On 22 September 2022, Australia's second-largest telecom company, Optus, announced that it had suffered a significant data breach.
113. Crucial Cloud Computing Security Threats Everyone Should Know
 A rundown of the business impact and mitigation measures of the top cloud computing security threats from the 2022 Cloud Security Alliance survey
A rundown of the business impact and mitigation measures of the top cloud computing security threats from the 2022 Cloud Security Alliance survey
114. The Convergence of IT and OT in Cybersecurity
 Once separate systems, IT and OT are converging as technology continues to develop. With everything connected, how can you keep operational technology secure?
Once separate systems, IT and OT are converging as technology continues to develop. With everything connected, how can you keep operational technology secure?
115. The Battle of the Best: Hashing vs Encryption
 Encryption and hashing are different in terms of web security, purpose, length, and direction. Read on to know more about hashing vs encryption in detail.
Encryption and hashing are different in terms of web security, purpose, length, and direction. Read on to know more about hashing vs encryption in detail.
116. Understanding What Security Testing Is & Its Importance with The Top Tools and Key Principles
 In this article, we will explore what security testing is, the top tools for security testing, and the key principles of security testing.
In this article, we will explore what security testing is, the top tools for security testing, and the key principles of security testing.
117. This Online Abortion Pill Provider Used Tracking Tools That Gave Powerful Companies Your Data
 The trackers notified Google, Facebook’s parent company Meta, payments processor Stripe, and four analytics firms when users visited its site.
The trackers notified Google, Facebook’s parent company Meta, payments processor Stripe, and four analytics firms when users visited its site.
118. 3 Cybersecurity Priorities for 2021: Threat Fatigue; Remote Work; Budget
 Disagreement is one of the defining trends of 2020. However, I think most of us would agree that this year hasn’t turned out to be the kind of year that many of us anticipated when we celebrated on December 31st.
Disagreement is one of the defining trends of 2020. However, I think most of us would agree that this year hasn’t turned out to be the kind of year that many of us anticipated when we celebrated on December 31st.
119. How Can We Expose Cyber Criminals Through Identity Attribution
 As we approach the dawn of another year, the cybersecurity world faces a strange dilemma- organized crime. Throughout the course of recent years, cybercrimes have grown increasingly sophisticated, primarily because of the rise in prominence of technologies such as machine learning, and the growing amalgamation of artificial intelligence within enterprises.
As we approach the dawn of another year, the cybersecurity world faces a strange dilemma- organized crime. Throughout the course of recent years, cybercrimes have grown increasingly sophisticated, primarily because of the rise in prominence of technologies such as machine learning, and the growing amalgamation of artificial intelligence within enterprises.
120. Finding The Privacy Balance - Is There Such Thing as Too Much Privacy?
 I've been a heavy advocate for using multiple tools and alternative services to protect your personal information for years. However, as I've seen people pile on one privacy tool after another I've realized that people have perhaps taken it too far.
I've been a heavy advocate for using multiple tools and alternative services to protect your personal information for years. However, as I've seen people pile on one privacy tool after another I've realized that people have perhaps taken it too far.
121. These Companies Are Collecting Data From Your Car
 Most drivers have no idea what data is being transmitted from their vehicles, let alone who exactly is collecting, analyzing, and sharing that data...
Most drivers have no idea what data is being transmitted from their vehicles, let alone who exactly is collecting, analyzing, and sharing that data...
122. Security & Agile Development - How to Bridge the Gap in 2022

123. DuckDuckGo Is A Step In The Right Direction For User Privacy

124. RBAC and PSPs Can Only Bring Your Kubernetes Security So Far
 Admins need to defend their organizations against a Kubernetes security incident. RBAC and PSPs will only get them so far; more security measures are needed.
Admins need to defend their organizations against a Kubernetes security incident. RBAC and PSPs will only get them so far; more security measures are needed.
125. Cybersecurity and the Metaverse: Guardians of the New Digital World
 A metaverse is a virtual reality space in which users can interact with one another in a computer-generated environment.
A metaverse is a virtual reality space in which users can interact with one another in a computer-generated environment.
126. A Beginner's Introduction to Database Backup Security
 With more companies collecting customer data than ever, database backups are key.
With more companies collecting customer data than ever, database backups are key.
127. Data Integrity Is Vital for The COVID-19 Vaccine Rollout
 This is why improving the processing and handling of COVID-19 and other health data should be a priority both during and after the pandemic.
This is why improving the processing and handling of COVID-19 and other health data should be a priority both during and after the pandemic.
128. How to Ensure Data Integrity in an Organization
 Ensuring data integrity is essential in an organization because it ensures data has not been altered or compromised. Understand how to preserve data integrity.
Ensuring data integrity is essential in an organization because it ensures data has not been altered or compromised. Understand how to preserve data integrity.
129. Data Lakehouses: The New Data Storage Model
 Data lakehouses are quickly replacing old storage options like data lakes and warehouses. Read on for the history and benefits of data lakehouses.
Data lakehouses are quickly replacing old storage options like data lakes and warehouses. Read on for the history and benefits of data lakehouses.
130. Optimize Your Data Engine With Data as a Service (DaaS) and Multi-Tenancy
 Data-driven organizations are planning to build a data as a service (DaaS) architecture to make it easier to onboard their users, partners, and consumers.
Data-driven organizations are planning to build a data as a service (DaaS) architecture to make it easier to onboard their users, partners, and consumers.
131. How VPN Security Works and Why Use One for Safe Internet Connection
 Information security is today one of the priority tasks that arise in organizations. This is especially true for enterprises whose ventures, in one way or another, are associated with data. With VPN, companies can protect their data on the Internet.
Information security is today one of the priority tasks that arise in organizations. This is especially true for enterprises whose ventures, in one way or another, are associated with data. With VPN, companies can protect their data on the Internet.
132. Why Is Transparency Critical to Cybersecurity?
 After more than a year of posturing over whether it was safe to integrate Huawei's equipment into the UK’s telecom network, the Prime Minister finally made a decision. Last January, Boris Johnson decided to allow not only Huawei but also other companies deemed “high-risk” limited access to Britain's 5G networks.
After more than a year of posturing over whether it was safe to integrate Huawei's equipment into the UK’s telecom network, the Prime Minister finally made a decision. Last January, Boris Johnson decided to allow not only Huawei but also other companies deemed “high-risk” limited access to Britain's 5G networks.
133. What Is White-Box Cryptography?
 White-box cryptography combines methods of encryption and obfuscation to embed secret keys within application code. The goal is to combine code and keys in such a way that the two are indistinguishable to an attacker, and the new "white-box" program can be safely run in an insecure environment.
White-box cryptography combines methods of encryption and obfuscation to embed secret keys within application code. The goal is to combine code and keys in such a way that the two are indistinguishable to an attacker, and the new "white-box" program can be safely run in an insecure environment.
134. Everything You Need to Know about Web 3.0
 Web3 is the new update to the World Wide Web which aims to shift the dependency from tech giants to individual users. It uses the Blockchain model to function.
Web3 is the new update to the World Wide Web which aims to shift the dependency from tech giants to individual users. It uses the Blockchain model to function.
135. LDAP Injection Vulnerability, Explained
 LDAP or Lightweight Directory Access Protocol is a methodology designed to read data in a directory, file or device. This is actually a directory access service which, for instance, can be used to provide information about a user who is trying to login as part of a single-sign-on, SSO process.
LDAP or Lightweight Directory Access Protocol is a methodology designed to read data in a directory, file or device. This is actually a directory access service which, for instance, can be used to provide information about a user who is trying to login as part of a single-sign-on, SSO process.
136. Web3.0 Powered Privacy: Decentralization for More Control and Transparency
 A look at the importance of data privacy in today's digital age, where personal information is being collected, used, and shared at an unprecedented rate.
A look at the importance of data privacy in today's digital age, where personal information is being collected, used, and shared at an unprecedented rate.
137. 4 Essential Steps to Protect Your Digital Privacy
 Connecting to public WiFi may be unavoidable but it does bring some security risks. These four steps can help protect your data privacy when connected to such.
Connecting to public WiFi may be unavoidable but it does bring some security risks. These four steps can help protect your data privacy when connected to such.
138. Ransomware Steals the Limelight, But It’s Not the Only Threat We Face
 Viewing ransomware as a virus isn’t correct from a technical standpoint. Ransomware is malware, meaning it’s meant to damage, disrupt, or hack a device.
Viewing ransomware as a virus isn’t correct from a technical standpoint. Ransomware is malware, meaning it’s meant to damage, disrupt, or hack a device.
139. Personal Security Online Is Not Complicated
 Well, if you want to hear something complicated, try to understand the relationship between Beyonce and Jay Z.
Well, if you want to hear something complicated, try to understand the relationship between Beyonce and Jay Z.
140. How to Minimize Privacy Risks in AI/ML applications
 With the rise of data economy, data privacy has become even more important. Enterprises need to be privacy-first and invest in privacy enhancing technologies.
With the rise of data economy, data privacy has become even more important. Enterprises need to be privacy-first and invest in privacy enhancing technologies.
141. What Everyone Should Know About Tools And Services Of ATO Providers
 What is account takeover? What are the tools and methods attackers use to employ it? And how active is HOSEEN on the dark web? Learn more in this article.
What is account takeover? What are the tools and methods attackers use to employ it? And how active is HOSEEN on the dark web? Learn more in this article.
142. Do Paperless Offices Face More Security Risks?
 Going paperless is becoming increasingly possible for businesses, but are there risks involved? Here are the benefits and risks of going paperless.
Going paperless is becoming increasingly possible for businesses, but are there risks involved? Here are the benefits and risks of going paperless.
143. Top Open Source Vulnerabilities to Watch Out
 Open Source packages are a mainstay for most software engineering projects. We are so accustomed as developers to run our
Open Source packages are a mainstay for most software engineering projects. We are so accustomed as developers to run our npm install (for Node developers) or
144. 7 Sneaky Ways Hackers Are Using Machine Learning to Steal Your Data
 Machine learning is famous for its ability to analyze large data sets and identify patterns. It is basically a subset of artificial intelligence. Machine learning uses algorithms that leverages previous data-sets and statistical analysis to make assumptions and pass on judgments about behavior.
The best part, software or computers powered by machine learning algorithms can perform functions that they have not been programmed to perform.
Machine learning is famous for its ability to analyze large data sets and identify patterns. It is basically a subset of artificial intelligence. Machine learning uses algorithms that leverages previous data-sets and statistical analysis to make assumptions and pass on judgments about behavior.
The best part, software or computers powered by machine learning algorithms can perform functions that they have not been programmed to perform.
145. Why SASE (Secure Access Service Edge) Matters for Businesses
 The way companies protect their networks is undergoing a seismic shift. SASE is one such way that companies are protecting themselves. Here's why it's important
The way companies protect their networks is undergoing a seismic shift. SASE is one such way that companies are protecting themselves. Here's why it's important
146. The SOcial LInked Data (SOLID) Project of Tim Berners Lee: An Organizational Take
 The web is more a social creation than a technical one. I designed it for a social effect—to help people work together―and not as a technical toy.
The web is more a social creation than a technical one. I designed it for a social effect—to help people work together―and not as a technical toy.
Tim Berners-Lee, Weaving the Web, 1999
147. What are Adversarial AI Attacks and How Do We Combat Them?
 Deep learning models are capable of performing on par with, if not exceeding, human levels, at a variety of different tasks and objectives.
Deep learning models are capable of performing on par with, if not exceeding, human levels, at a variety of different tasks and objectives.
148. Protecting Your Company from Growing Risks of Software Supply Chain Attacks
 Software supply chain attacks are an emerging threat in the cybersecurity world. How can you protect your company against these attacks? Find out here.
Software supply chain attacks are an emerging threat in the cybersecurity world. How can you protect your company against these attacks? Find out here.
149. 6 Tips to Safeguard Patrons' Privacy at Your Library
 Patron privacy is one of those topics that touches every aspect of a library's operations, and for good reason.
Patron privacy is one of those topics that touches every aspect of a library's operations, and for good reason.
150. 3 Different Types of Data Quality Issues
 Data quality is the accuracy, completeness, and timeliness of data. It is important to ensure that data is of high quality.q
Data quality is the accuracy, completeness, and timeliness of data. It is important to ensure that data is of high quality.q
151. Ransomware-as-a-Service: SaaS' Evil Twin
 This article will educate you about RaaS groups and protective measures against ransomware attacks.
This article will educate you about RaaS groups and protective measures against ransomware attacks.
152. Smart Cities Raise Data Privacy Concerns
 Should you be excited about smart cities or concerned about your privacy and data? I go through three of the ten privacy principles (PIPEDA) and their effects.
Should you be excited about smart cities or concerned about your privacy and data? I go through three of the ten privacy principles (PIPEDA) and their effects.
153. Privacy and Security, Though Distinct Concepts, Are Interdependent
 Security & Privacy are often confused, but are distinct. It’s important that we understand the difference so that we can protect ourselves
Security & Privacy are often confused, but are distinct. It’s important that we understand the difference so that we can protect ourselves
154. Security For PMs: A Step-By-Step Guide
 Cybersecurity is among the most significant trends over the last decade and has become even more important now, especially due to more remote work being done. From ransomware to cyber espionage, hackers have developed sophisticated techniques to break into your project/company data and get away with critical information or demand ransom.
Cybersecurity is among the most significant trends over the last decade and has become even more important now, especially due to more remote work being done. From ransomware to cyber espionage, hackers have developed sophisticated techniques to break into your project/company data and get away with critical information or demand ransom.
Even well known organizations such as Canon, Garmin, Twitter, Honda, and Travelex have fallen victims to malicious actors. A data breach can be a disaster for your company/project, destroy the trust of your customers, and spoil your company’s reputation.
155. Cloud Data Security and the Need for Confidential Containers
 Why should you choose Confidential Containers for your business and how do they stand out from the "vanilla" version? Check it out in our article!
Why should you choose Confidential Containers for your business and how do they stand out from the "vanilla" version? Check it out in our article!
156. Reviewing the Eight Leading Global Cloud Providers in India

157. Complete Guide to Choosing the Best Billing & Invoicing Software
 Let me tell you a simple truth. Billing & invoicing is a pain. It has always been. Remember the pre-computer era of accounting? I am talking about the time when companies used to hire accountants and data entry operators to manually maintain billing & invoicing records in heavy files. The process was hectic. It took days and sometimes weeks to create invoices, send them out, and following up on unpaid bills. Above this, it could also cost a lot of time and money.
Let me tell you a simple truth. Billing & invoicing is a pain. It has always been. Remember the pre-computer era of accounting? I am talking about the time when companies used to hire accountants and data entry operators to manually maintain billing & invoicing records in heavy files. The process was hectic. It took days and sometimes weeks to create invoices, send them out, and following up on unpaid bills. Above this, it could also cost a lot of time and money.
158. What You Should Learn Before Learning Cybersecurity - Updated 2022
 Have you been looking to learn Cybersecurity but you’re unsure where to start from?
Have you been looking to learn Cybersecurity but you’re unsure where to start from?
Here’s a great guide on where to start!
159. Could School Surveillance Tools Put Teens at Risk?
 Health advocates and civil rights groups are warning that school surveillance software can be weaponized against teens who seek reproductive care.
Health advocates and civil rights groups are warning that school surveillance software can be weaponized against teens who seek reproductive care.
160. 6 Tips for Improving Cybersecurity in the Workplace
 In this post, we'll cover some fundamental and practical ways to boost workplace cybersecurity.
In this post, we'll cover some fundamental and practical ways to boost workplace cybersecurity.
161. Data Sovereignty: The Importance of Keeping Your Data Safe
 Protect your personal data with data sovereignty. Learn the importance of keeping your information safe and secure in the digital age. Read our article to find
Protect your personal data with data sovereignty. Learn the importance of keeping your information safe and secure in the digital age. Read our article to find
162. Using a Password Manager: My Review of Bitwarden

163. Why You Should Never Store Passwords in Web Browsers

164. 20 Data Security Risks Your Company Could Face in 2020
 Today, data security is top of mind for companies, consumers, and regulatory bodies. After years of unfettered participation in the data-driven digital age that was defined by an “anything goes” ethos and a “move fast and break things” mentality, this shifting sentiment is both drastic and welcome.
Today, data security is top of mind for companies, consumers, and regulatory bodies. After years of unfettered participation in the data-driven digital age that was defined by an “anything goes” ethos and a “move fast and break things” mentality, this shifting sentiment is both drastic and welcome.
165. Where is DevOps Going in 2021?
 Efficiency, speed, transparency — all of this is possible with DevOps. In 2021, AI, data security, assembly lines, and more will take over as DevOps trends.
Efficiency, speed, transparency — all of this is possible with DevOps. In 2021, AI, data security, assembly lines, and more will take over as DevOps trends.
166. What is a Distributed Storage Network on a Blockchain System?
 A Distributed Storage Network (DSN) is a peer-to-peer network based on blockchain. It is a decentralized and distributed network that provides storage.
A Distributed Storage Network (DSN) is a peer-to-peer network based on blockchain. It is a decentralized and distributed network that provides storage.
167. Security Considerations in Golang

168. Data-Driven Advertising and Its Impact On Our Privacy-Driven World
 Do we actually need so much data to do effective marketing?
Do we actually need so much data to do effective marketing?
169. Personal Data Protection: Mission Impossible?
 4.1 user billion records exposed in the first half of 2019: how’s that for data protection?
4.1 user billion records exposed in the first half of 2019: how’s that for data protection?
170. An Introduction to Code Signing Solutions
 Code Signing is a process to confirm the authenticity and originality of digital information, especially software code, and assuring that this digital information is valid and additionally establishes the legitimacy of the author. It also provides assurance that this piece of digital information has not changed or been revoked after it has been signed by the signature.
Code Signing is a process to confirm the authenticity and originality of digital information, especially software code, and assuring that this digital information is valid and additionally establishes the legitimacy of the author. It also provides assurance that this piece of digital information has not changed or been revoked after it has been signed by the signature.
171. A Growing Necessity for Cybersecurity
 Businesses and personal users alike, cybersecurity is a growing necessity. With the increase of breaches, cybercrime, and more sophisticated hackers in this world, it is more important than ever to ensure that your data and network are secure and safe from criminals. If you are a business, then you likely have a dedicated IT team that helps ensure the safety of the data and network at your business, but it is important for you to understand what needs to be done so you can better direct your IT department. If you are a personal user, never believe that your data and online security is not valuable, as it most often is just as valuable as your physical possessions. Just as there are steps to prevent intestinal permeability, there are steps that can be taken to prevent someone from hacking your information.
Businesses and personal users alike, cybersecurity is a growing necessity. With the increase of breaches, cybercrime, and more sophisticated hackers in this world, it is more important than ever to ensure that your data and network are secure and safe from criminals. If you are a business, then you likely have a dedicated IT team that helps ensure the safety of the data and network at your business, but it is important for you to understand what needs to be done so you can better direct your IT department. If you are a personal user, never believe that your data and online security is not valuable, as it most often is just as valuable as your physical possessions. Just as there are steps to prevent intestinal permeability, there are steps that can be taken to prevent someone from hacking your information.
172. How to Make Sure Your Nonprofit is Complying With HIPAA
 It is important for your non-profit organization to comply with HIPAA to protect health data. Here's how you can do so.
It is important for your non-profit organization to comply with HIPAA to protect health data. Here's how you can do so.
173. Need for an Identity Theft Protection
 Identity theft is a blanket term that covers fraudulent and even suspicious action through bank accounts and criminal databases. It is a violation of getting the financial or personal data of a person with the sole objective of feigning that person's name or identity to make purchases or transactions.
Identity theft is a blanket term that covers fraudulent and even suspicious action through bank accounts and criminal databases. It is a violation of getting the financial or personal data of a person with the sole objective of feigning that person's name or identity to make purchases or transactions.
174. 6 Expert Cybersecurity Strategies for Financial Institutions
 Investing in security is vital, but major breaches still happen irrespective of advancements. Financial organizations can take these 6 steps to better security.
Investing in security is vital, but major breaches still happen irrespective of advancements. Financial organizations can take these 6 steps to better security.
175. Can Data Automation Transform The Workplace?
 Every minute, a staggering 1,820 terabytes of data is created around the world. That’s more than 2.5 quintillion bytes every day! This data takes many forms, from Tweets and Instagram posts to the generation of new
bitcoin.
Every minute, a staggering 1,820 terabytes of data is created around the world. That’s more than 2.5 quintillion bytes every day! This data takes many forms, from Tweets and Instagram posts to the generation of new
bitcoin.
176. How Software Accountability shifts Technology Dynamics for Today’s Startups
 For a long time now, software-based startups have been launching their products and thrived by having users’ data as the very foundation of their business models. Social media platforms are the perfect examples of how a business can profit from a well of consumer data. While users had traditionally been in the dark about how the information they share when interacting with digital products is used, various notorious scandals have changed the narrative.
For a long time now, software-based startups have been launching their products and thrived by having users’ data as the very foundation of their business models. Social media platforms are the perfect examples of how a business can profit from a well of consumer data. While users had traditionally been in the dark about how the information they share when interacting with digital products is used, various notorious scandals have changed the narrative.
177. 4 Reasons Why Email Is Obsolete, and You Should Move On
 Chances are, your business’ primary mode of internal communication is email. And you’re using instant messaging (IM) apps for virtual meetups and updates from the team, thanks to the coronavirus. Don’t get me wrong, email is great and all for internal communication (if you lived in the 20th century that is). But did you know your email to your teammates gets lost in a sea of unimportant emails? And irrelevant emails account for about 62% of the total emails in an average inbox!
Chances are, your business’ primary mode of internal communication is email. And you’re using instant messaging (IM) apps for virtual meetups and updates from the team, thanks to the coronavirus. Don’t get me wrong, email is great and all for internal communication (if you lived in the 20th century that is). But did you know your email to your teammates gets lost in a sea of unimportant emails? And irrelevant emails account for about 62% of the total emails in an average inbox!
178. Cybersecurity At Every Level: How IT Consultants Can Benefit Your Business
 We live our lives online these days – and given this simple fact, it should come as no surprise that cybersecurity is one of the fastest growing industries around, and one that’s critical to all other sectors. For those in the cryptocurrency industry, however, cybersecurity plays a more interesting role. That’s because, while cryptocurrency operations clearly need to enhance their own cybersecurity efforts, they’re also reliant on technology – blockchain – that other industries are using for their own security needs.
We live our lives online these days – and given this simple fact, it should come as no surprise that cybersecurity is one of the fastest growing industries around, and one that’s critical to all other sectors. For those in the cryptocurrency industry, however, cybersecurity plays a more interesting role. That’s because, while cryptocurrency operations clearly need to enhance their own cybersecurity efforts, they’re also reliant on technology – blockchain – that other industries are using for their own security needs.
179. Cyber Security Awareness Month: The Top 3 Types of Insider Threats Putting Companies at Risk
 October is Cyber Security Awareness Month. In 2022, cybersecurity was a top concern for c-suite executives, board members, department leads, and IT teams.
October is Cyber Security Awareness Month. In 2022, cybersecurity was a top concern for c-suite executives, board members, department leads, and IT teams.
180. Data Masking: How it Can be Implemented Correctly

181. Mark Your Calendars, Bad Bots Are Coming for the Last Months of 2022
 The sad reality for many online business websites and applications is that they are flooded by automated bad bots
The sad reality for many online business websites and applications is that they are flooded by automated bad bots
182. Space and Time Receives $20 Million in Strategic Investment Led by Microsoft's M12
 Space and Time, a Web3 native data platform that has raised $20 million in strategic capital from notable investors led by Microsoft's M12 fund.
Space and Time, a Web3 native data platform that has raised $20 million in strategic capital from notable investors led by Microsoft's M12 fund.
183. Security For PMs: How-To [Part II]
 In the first part of this article, we have talked about the ways in which your customers may check if your statements of the security matter in your company line up with reality. Now let us focus on how to ensure that your security practices are actually working and how to avoid the numerous pitfalls on this way.
In the first part of this article, we have talked about the ways in which your customers may check if your statements of the security matter in your company line up with reality. Now let us focus on how to ensure that your security practices are actually working and how to avoid the numerous pitfalls on this way.
184. The Importance of Web Penetration Testing
 A pen test or penetration test is a modeled cyber-attack on your computer system to look for vulnerabilities that could be exploited.
A pen test or penetration test is a modeled cyber-attack on your computer system to look for vulnerabilities that could be exploited.
185. How to Structure an Effective Digital Defense Team
 Today’s cybercriminals are increasingly sophisticated. Just downloading some antivirus software isn’t nearly enough protection against them and you need a team.
Today’s cybercriminals are increasingly sophisticated. Just downloading some antivirus software isn’t nearly enough protection against them and you need a team.
186. Making Backups Failproof to Mitigate Ransomware Attacks
 Having an effective backup strategy means that a company's data can be restored quickly and securely. This requires regular testing and validation of backups.
Having an effective backup strategy means that a company's data can be restored quickly and securely. This requires regular testing and validation of backups.
187. Is 128 Bit Encryption Enough?
 There are a lot of cloud services that tout encryption strength as a measure of how well they guard your data. It is quoted in bits, which is the
size of the key. So you see services quoting 128 bit, 256 bit or even
2048 bit.
There are a lot of cloud services that tout encryption strength as a measure of how well they guard your data. It is quoted in bits, which is the
size of the key. So you see services quoting 128 bit, 256 bit or even
2048 bit.
188. Using AWS Macie To Classify Databases
 I'll show how to use Macie to scan any database, inclusive on-premises, to discover sensitive data on tables.
I'll show how to use Macie to scan any database, inclusive on-premises, to discover sensitive data on tables.
189. Cyber Threats: What Are The Dangers?
 The beginning of the 21st century has seen a dramatic rise in the adoption of digital technologies. On the flip side, cyber-attacks have also risen dramatically, and they have become more cunning. It’s estimated that cybercrime will cost the world $5.2 trillion annually over the next five years, while cybersecurity spending across enterprises will reach $123B by the end of 2020.
The beginning of the 21st century has seen a dramatic rise in the adoption of digital technologies. On the flip side, cyber-attacks have also risen dramatically, and they have become more cunning. It’s estimated that cybercrime will cost the world $5.2 trillion annually over the next five years, while cybersecurity spending across enterprises will reach $123B by the end of 2020.
190. Security Measures for Cryptocurrency Owners
 Cryptocurrencies have so far become one of the most innovative forms of technology. They bring all the perks of new-age innovation to the financial space, essentially allowing people to make quick, anonymous, and much cheaper transactions that can travel over long distances.
Cryptocurrencies have so far become one of the most innovative forms of technology. They bring all the perks of new-age innovation to the financial space, essentially allowing people to make quick, anonymous, and much cheaper transactions that can travel over long distances.
191. Benefits of Corporate Data Backup and Best Practices to Keep in Place
 Nowadays, companies are increasingly relying on corporate data backup solutions to guarantee the safety and recoverability of their data. Read on to learn more
Nowadays, companies are increasingly relying on corporate data backup solutions to guarantee the safety and recoverability of their data. Read on to learn more
192. Changes and Trends in DeFi Security
 Ever since it emerged in mid-2020, DeFi has been a major trend in the cryptocurrency industry, which was (and still is) quite understandable. It brought a way to make money passively, it enabled loans that you can get in exchange for providing collateral, but most importantly, it allowed you to use your existing money to make more money, without the risks that accompany crypto trading.
Ever since it emerged in mid-2020, DeFi has been a major trend in the cryptocurrency industry, which was (and still is) quite understandable. It brought a way to make money passively, it enabled loans that you can get in exchange for providing collateral, but most importantly, it allowed you to use your existing money to make more money, without the risks that accompany crypto trading.
193. How Big Tech is Working Towards a Password-Free Future
 A 2019 research conducted by HYPR showed that 78% of people forgot their passwords and required a reset within the last 90 days. Passwords aren’t just difficult to manage, they are inconvenient, insecure, and expensive because passwords are just too easy to guess, hack or intercept and what’s more, the legacy of password reuse is leading to constant attack and account vulnerabilities.
A 2019 research conducted by HYPR showed that 78% of people forgot their passwords and required a reset within the last 90 days. Passwords aren’t just difficult to manage, they are inconvenient, insecure, and expensive because passwords are just too easy to guess, hack or intercept and what’s more, the legacy of password reuse is leading to constant attack and account vulnerabilities.
194. Regardless of Their Size, Any Business Can Be a Victim of a Ransomware Attack
 A timeline of a medium sized businesses ransomware attack along with tips to prevent an attack for yourself.
A timeline of a medium sized businesses ransomware attack along with tips to prevent an attack for yourself.
195. Network Security 101: Everything You Need to Know
 Network Security is Vital. Its purpose is to prevent unauthorized users from accessing an organization's network and devices. It is intended to keep data safe.
Network Security is Vital. Its purpose is to prevent unauthorized users from accessing an organization's network and devices. It is intended to keep data safe.
196. An Introduction to PCI Compliance
 There are plenty of reasons for enterprises that work with cardholder data to care about payment card industry (PCI) compliance.
There are plenty of reasons for enterprises that work with cardholder data to care about payment card industry (PCI) compliance.
197. COVID-19 Tracing: Protect Your Privacy
 As the COVID-19 pandemic goes on, life for some around the world is beginning to look a little more like it did before, except with some more distancing, and more people wearing masks. What doesn’t look the same, is how technology is being used to monitor and track cases, infection rates, and outbreaks.
As the COVID-19 pandemic goes on, life for some around the world is beginning to look a little more like it did before, except with some more distancing, and more people wearing masks. What doesn’t look the same, is how technology is being used to monitor and track cases, infection rates, and outbreaks.
198. 4 Simple Steps to Avoid Falling Victim to All-Too-Frequent Data Breaches
 These days, reports of major data breaches happen so often that people are beginning to tune them out. After all, most people who have had their data stolen don't actually end up suffering any visible consequences. Therefore, it's all too easy to meet the news of each new security incident with a casual shrug.
These days, reports of major data breaches happen so often that people are beginning to tune them out. After all, most people who have had their data stolen don't actually end up suffering any visible consequences. Therefore, it's all too easy to meet the news of each new security incident with a casual shrug.
199. Crypto Wallet Security 101
 As a 101 guide, I will explain the common reasons for the sudden disappearance of cryptocurrency inside the wallet.
As a 101 guide, I will explain the common reasons for the sudden disappearance of cryptocurrency inside the wallet.
200. Disinformation-as-a-Service: Content Marketing’s Evil Twin
 Are you tired of all the BS out there on the internet? It's about to get A LOT worse. Dirt-cheap disinformation-as-a-Service campaigns are a thing now.
Are you tired of all the BS out there on the internet? It's about to get A LOT worse. Dirt-cheap disinformation-as-a-Service campaigns are a thing now.
201. How to Migrate from Airflow to Dolphinscheduler in Two Steps
 Recently, Air2phin, a scheduling system migration tool, announced its open source. With Air2phin, users can migrate the scheduling system from Airflow to Apache
Recently, Air2phin, a scheduling system migration tool, announced its open source. With Air2phin, users can migrate the scheduling system from Airflow to Apache
202. Are You Prepared to Respond to Advanced Security Incidents?

203. 4 Handy Tips to Keep your Digital Identity Secure
 Since we can't function without the internet these days, it is highly important to keep our digital identity secure.
Since we can't function without the internet these days, it is highly important to keep our digital identity secure.
204. Account Aggregators: What Are They and How Will They Change the Fintech Ecosystem?
 Account Aggregators (AAs) are about to take the fintech market by storm. Remember how UPI completely changed how people send money? No more awkwardly splitting restaurant bills, or digging for exact change to pay off that friend who's been bugging you for months.
Account Aggregators (AAs) are about to take the fintech market by storm. Remember how UPI completely changed how people send money? No more awkwardly splitting restaurant bills, or digging for exact change to pay off that friend who's been bugging you for months.
205. Microsoft SEAL and the Dawn of Homomorphic Encryption
 Homomorphic encryption is making its way from academia to production use cases. Kick the tires on it with C# and a privacy minded fitness tracker.
Homomorphic encryption is making its way from academia to production use cases. Kick the tires on it with C# and a privacy minded fitness tracker.
206. All about Security Information and Event Management

207. Creating a Secure Mobile App: Main Vulnerabilities and Security Practices
 There are 2.87 million apps on the Google Play Store. it’s the responsibility of the app owner to make sure that all the data use properly.
There are 2.87 million apps on the Google Play Store. it’s the responsibility of the app owner to make sure that all the data use properly.
208. Cybercriminals Target SMEs and Large Companies Alike
 About the operation of SMEs, there are many misconceptions, especially in the field of cyber-security, but a study by Cisco has shown that they share a lot with large companies in the world.
About the operation of SMEs, there are many misconceptions, especially in the field of cyber-security, but a study by Cisco has shown that they share a lot with large companies in the world.
209. Why You Should Avoid Using Public WiFi
 Why You Should Avoid Using Public WiFi
Why You Should Avoid Using Public WiFi
210. The Emergence of IoT Security in The Post-COVID-19 World
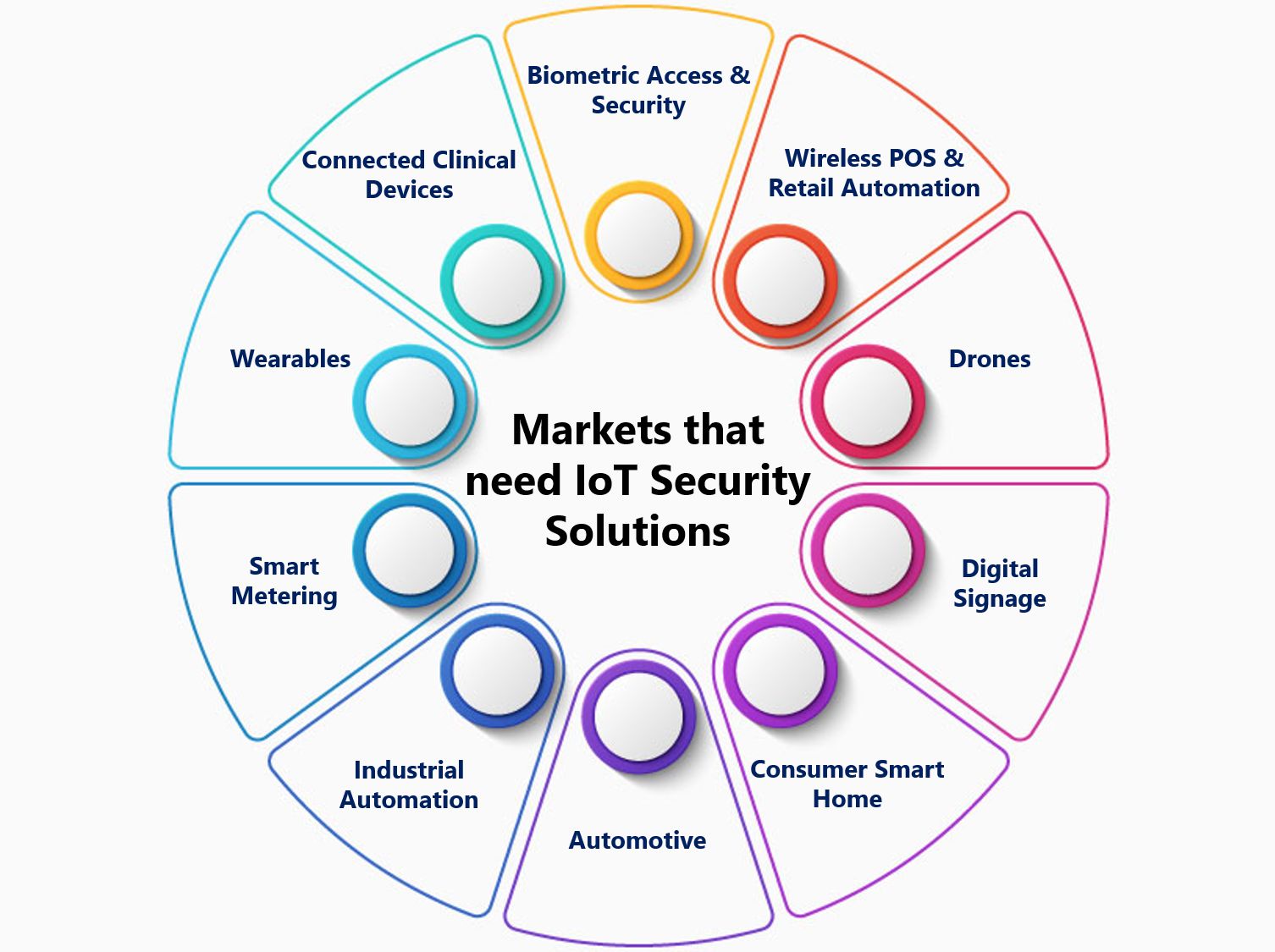 Security is a ‘state of mind’ and not an end state. It has been a popular philosophical thought, but what it eludes is the fact of investment towards security. IoT has exploded with the onset of new smart tech gadgets. Though businesses today exercise security and safety measures within their organizations, it isn’t easy to keep upgrading an organization’s infrastructure to encompass these technology updates. Reverse engineering systems have always remained the passcode for unlocking backdoors to capitalize on security vulnerabilities. The best example of such a scenario is the 2016 MIRAI botnet attack. The attack caused massive DDoS attacks on large enterprises on Atlanta’s city administration and the ATL airport. IoT still lacks immunity against ransomware attacks and many new age cyberattacks.
Security is a ‘state of mind’ and not an end state. It has been a popular philosophical thought, but what it eludes is the fact of investment towards security. IoT has exploded with the onset of new smart tech gadgets. Though businesses today exercise security and safety measures within their organizations, it isn’t easy to keep upgrading an organization’s infrastructure to encompass these technology updates. Reverse engineering systems have always remained the passcode for unlocking backdoors to capitalize on security vulnerabilities. The best example of such a scenario is the 2016 MIRAI botnet attack. The attack caused massive DDoS attacks on large enterprises on Atlanta’s city administration and the ATL airport. IoT still lacks immunity against ransomware attacks and many new age cyberattacks.
211. How To Choose The Right Business Process Automation Technology
 This article will give you some insight into what to look for when selecting business process automation software to enhance your productivity.
This article will give you some insight into what to look for when selecting business process automation software to enhance your productivity.
212. 5 Common Identity and Access Management Security Risks
 IAM ensures that employees have the necessary permissions to perform their jobs. Read on to learn about the 5 common IAM security risks & how to mitigate them.
IAM ensures that employees have the necessary permissions to perform their jobs. Read on to learn about the 5 common IAM security risks & how to mitigate them.
213. The Top 5 Reasons to Back up Exchange Online
 Still don’t back up Exchange Online? Learn why you need a dedicated backup solution and not just native Microsoft native tools to ensure timely recoveries.
Still don’t back up Exchange Online? Learn why you need a dedicated backup solution and not just native Microsoft native tools to ensure timely recoveries.
214. 7 Q&As About Memory Leaks

215. Cybersecurity Considerations for Employee Onboarding
 Is cybersecurity emphasized in your employee onboarding program? Here's what onboarding with a strong security foundation should look like.
Is cybersecurity emphasized in your employee onboarding program? Here's what onboarding with a strong security foundation should look like.
216. How The Smart Office is Revolutionizing the Workplace
 Smart offices are revolutionizing the workplace by introducing new technologies and tools that enable employees to be more productive and efficient.
Smart offices are revolutionizing the workplace by introducing new technologies and tools that enable employees to be more productive and efficient.
217. Privacy Protection: How Secure is Telegram Messenger?
 Is Telegram messenger secure enough for private messages and group chats? Can Telegram protect the privacy of users? We did research on this.
Is Telegram messenger secure enough for private messages and group chats? Can Telegram protect the privacy of users? We did research on this.
218. Why Should "BIG" Brands Pay More Attention to Data Security?
 Let’s dive straight in. Data security in an enterprise is a series of protective digital privacy measures that involve monitoring, managing and delivering data objects across the organization.
Let’s dive straight in. Data security in an enterprise is a series of protective digital privacy measures that involve monitoring, managing and delivering data objects across the organization.
219. How to Improve Data Quality in 2022
 Poor quality data could bring everything you built down. Ensuring data quality is a challenging but necessary task. 100% may be too ambitious, but here's what y
Poor quality data could bring everything you built down. Ensuring data quality is a challenging but necessary task. 100% may be too ambitious, but here's what y
220. The Importance of IoT Security
 Let's look at why security is very important for IoT devices
Let's look at why security is very important for IoT devices
221. Software Defined Perimeter - Everything You Ever Wanted To Know About
 Since cloud storage has become more commonplace in the modern day, there has been an increased risk of cyber-attacks on these cloud systems due to the fact that cloud servers cannot be protected by traditional perimeter security measures.
Since cloud storage has become more commonplace in the modern day, there has been an increased risk of cyber-attacks on these cloud systems due to the fact that cloud servers cannot be protected by traditional perimeter security measures.
222. AU Government Fails Cybersecurity Targets as PM Warns of Cyber Threat
 On June 19 this year Australian Prime Minister, Scott Morrison, alerted the nation to the fact they were undergoing cyber attack.
On June 19 this year Australian Prime Minister, Scott Morrison, alerted the nation to the fact they were undergoing cyber attack.
223. How to Back Up Exchange Online Data

224. How To Protect Your Data While Working Remotely

225. Analyzing the 12/31/2022 Slack Security Incident
 On December 31, 2022, Slack reported a security breach that affected some of its customers.
On December 31, 2022, Slack reported a security breach that affected some of its customers.
226. How to Develop a Human Centric Security Policy

227. Organize and Protect Your Online Data
 Online security is a vitally important consideration in this day and age. From doxxing to ransomware to identity theft, hacking online accounts is one of the most popular ways for the modern criminal makes his living. Keeping your online data organized and secure can take many forms, but it's not really an optional safety measure anymore. You must do all you can to protect your online data. Here are a few options for how to achieve that goal.
Online security is a vitally important consideration in this day and age. From doxxing to ransomware to identity theft, hacking online accounts is one of the most popular ways for the modern criminal makes his living. Keeping your online data organized and secure can take many forms, but it's not really an optional safety measure anymore. You must do all you can to protect your online data. Here are a few options for how to achieve that goal.
228. VPN Leaks that Threaten Your Online Privacy Daily
 According to research by GlobalWebIndex, in 2018, around 25% of Internet users have used a VPN service. There are several reasons for this spike in popularity, which you can read about in my previous article. One of the main reasons is the ability to bypass geo-blocks and gain access to, for example, a full Netflix library.
According to research by GlobalWebIndex, in 2018, around 25% of Internet users have used a VPN service. There are several reasons for this spike in popularity, which you can read about in my previous article. One of the main reasons is the ability to bypass geo-blocks and gain access to, for example, a full Netflix library.
229. Data Breach Prevention 101 for Small Business Owners
 Small business owners often think that they are not on hackers’ radars because they are "small players."
Small business owners often think that they are not on hackers’ radars because they are "small players."
230. Common Attack Vectors that Authentication Services are Faced With
 Hacking user accounts on many websites is still easier than it could and should be. This blog post helps you secure your application against identity theft.
Hacking user accounts on many websites is still easier than it could and should be. This blog post helps you secure your application against identity theft.
231. Inery Aims to Eliminate Entry Barriers to Web3, Blockchain
 Web3 Infrastructure is seriously lacking in one department - data systems. Inery addresses the issues of centralized data management
Web3 Infrastructure is seriously lacking in one department - data systems. Inery addresses the issues of centralized data management
232. A Guide to Staying Safe on the Internet
 Now, more than ever, we must remain vigilant of the evolving threats brought about by cunning and mischievous hackers.
Now, more than ever, we must remain vigilant of the evolving threats brought about by cunning and mischievous hackers.
233. How Zero Trust Vendors are Concealing the Truth About This Robust Mechanism?
 With the increasing cybersecurity risks and breaches in the past couple of years, businesses are now moving with a clear vision to incorporate zero-trust architecture into their platforms.
With the increasing cybersecurity risks and breaches in the past couple of years, businesses are now moving with a clear vision to incorporate zero-trust architecture into their platforms.
234. A Guide to Conducting Privacy Risk Assessments
 Let’s dive into the details of what a privacy risk assessment is, why it can benefit businesses, and how to conduct one.
Let’s dive into the details of what a privacy risk assessment is, why it can benefit businesses, and how to conduct one.
235. 3 Ways To Protect Company Data From Being Exposed By Your Own Employees
 When people think about data leaks, they tend to assume the cause of the threat came from outside the company.
When people think about data leaks, they tend to assume the cause of the threat came from outside the company.
236. Why your Company Needs a Virtual Chief Information Security Officer
 Why should your company hire a virtual CISO to increase security?
Why should your company hire a virtual CISO to increase security?
237. 5 Trends That Could Mark Social Media’s Evolution in the Next 5 Years
 Social media trends to watch
Social media trends to watch
238. Biden Administration Prioritizes Cybersecurity Funding After Numerous Cyberattacks
 The Biden administration is coming up with a $100 billion investment plan fo cybersecurity spending.
The Biden administration is coming up with a $100 billion investment plan fo cybersecurity spending.
239. ANSI X12 EDI Basics: A Guide to the ANSI X12 Standards
 ANSI X12 EDI is one of the most important concepts that you must be aware of prior to implementing EDI in your organization.
ANSI X12 EDI is one of the most important concepts that you must be aware of prior to implementing EDI in your organization.
240. 3 Ways CFOs can Prevent Phishing Attacks
 Whatever the size of your organization, cybersecurity should be at the forefront of your mind. Find out how CFOs can prevent phishing attacks with cybersecurity
Whatever the size of your organization, cybersecurity should be at the forefront of your mind. Find out how CFOs can prevent phishing attacks with cybersecurity
241. How to Protect Your Instagram Account from Being Hacked

242. EU Drafts Data Regulations for Voice Assistant Developers
 On March 2, 2021, the European Data Protection Board (EDPB) released Guidelines on Virtual Voice Assistants (VVAs) to protect users’ privacy.
On March 2, 2021, the European Data Protection Board (EDPB) released Guidelines on Virtual Voice Assistants (VVAs) to protect users’ privacy.
243. A Step by Step Guide to immudb — the open source immutable database
 immudb is lightweight, high-speed immutable database for systems and applications.
immudb is lightweight, high-speed immutable database for systems and applications.
244. 10 Ways to Reduce Data Loss and Potential Downtime Of Your Database
 In this article, you can find ten actionable methods to protect your mission-critical database.
In this article, you can find ten actionable methods to protect your mission-critical database.
245. Data Quality: Its Definitions And How to Improve It
 Utilizing quality data is essential for business operations. This article explores data quality definitions and how to maintain it for everyday use.
Utilizing quality data is essential for business operations. This article explores data quality definitions and how to maintain it for everyday use.
246. How to Protect Against Attacks Using a Quantum Computer
 Quantum technologies are steadily entering our life, and soon we will hear about new hacks using a quantum computer. So, how to protect against quantum attacks?
Quantum technologies are steadily entering our life, and soon we will hear about new hacks using a quantum computer. So, how to protect against quantum attacks?
247. Practices Used in eLearning Video-Content Protection
 Find out here how to provide eLearning content security which is needed with the majority of data in open access.
Find out here how to provide eLearning content security which is needed with the majority of data in open access.
248. Fostering Innovation in Modern Security Teams
 Organizations of all sizes treat data security and regulatory compliance like a roadblock instead of a design consideration. Over the last ten years, I have worked with scores of organizations to modernize and improve their software and data practices. Information security is a challenging position, as it is the job of security professionals to prevent companies from making changes that could seriously damage reputation and revenue or breach compliance and incur significant penalties. There are two general archetypes of security teams that I have interfaced with:
Organizations of all sizes treat data security and regulatory compliance like a roadblock instead of a design consideration. Over the last ten years, I have worked with scores of organizations to modernize and improve their software and data practices. Information security is a challenging position, as it is the job of security professionals to prevent companies from making changes that could seriously damage reputation and revenue or breach compliance and incur significant penalties. There are two general archetypes of security teams that I have interfaced with:
249. How Does Ransomware Work? A Step-by-Step Breakdown

250. Employ These 4 Simple Practices to Improve Company Data Security
 Here’s what you can do to keep yourself (and your nudes) safe.
Here’s what you can do to keep yourself (and your nudes) safe.
251. Why is Physical Security Such a Huge Threat?
 We’ve all heard about credit card skimming. This is the method by which skimmers attach devices to ATMs and gas pumps that capture your credit card number, and it’s often associated with a camera to catch you putting in your PIN. In 2018, credit and debit card fraud resulted in $28 billion in losses. This has prompted repeated calls for people to be on the lookout for things that are suspicious, cover their hands when they input their PIN numbers, and to only use “reputable” ATMs and gas pumps. Unfortunately the fraudsters are always one step ahead, and they are always coming up with new and creative ways to commit fraud.
We’ve all heard about credit card skimming. This is the method by which skimmers attach devices to ATMs and gas pumps that capture your credit card number, and it’s often associated with a camera to catch you putting in your PIN. In 2018, credit and debit card fraud resulted in $28 billion in losses. This has prompted repeated calls for people to be on the lookout for things that are suspicious, cover their hands when they input their PIN numbers, and to only use “reputable” ATMs and gas pumps. Unfortunately the fraudsters are always one step ahead, and they are always coming up with new and creative ways to commit fraud.
252. 5 Remote Working Best Practices and Tips in the Era of Coronavirus Pandemics
 Due to COVID-19, companies have found themselves in the middle of the world’s largest work-from-home experiment. Many hail remote work as a blessing, allowing employees to continue working while practicing social distancing during this uncertain time.
Due to COVID-19, companies have found themselves in the middle of the world’s largest work-from-home experiment. Many hail remote work as a blessing, allowing employees to continue working while practicing social distancing during this uncertain time.
253. How to Scan Your Systems for Personal Data
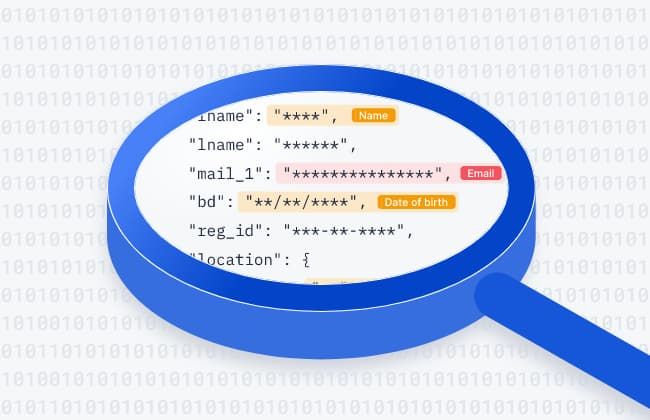 Learn the many different ways you can scan for personal data across your organisation's customer-facing online systems in this practical, how-to guide.
Learn the many different ways you can scan for personal data across your organisation's customer-facing online systems in this practical, how-to guide.
254. Building a MongoDB NoSQL E-Commerce Data Model
 MongoDB supports ACID transactions, and its cloud offering is PCI DSS compliant. It's one of the best NoSQL options for e-commerce.
MongoDB supports ACID transactions, and its cloud offering is PCI DSS compliant. It's one of the best NoSQL options for e-commerce.
255. Everything Wrong with Cloud-Based Note-Taking Apps
 My quest for a suitable Evernote replacement, after the company decided to restrict access to my own data, proved to be a short one.
My quest for a suitable Evernote replacement, after the company decided to restrict access to my own data, proved to be a short one.
256. The Ultimate Cyber Security Survival Guide
 Every action on the network leaves a digital footprint. For example, photos we post on social networks, statements on forums, likes and dislikes of videos. Moreover, a user activity leaves a digital trace - information about the sites browsed, purchases made, and geographical locations visited. There are many channels through which our personal data is exposed and the effects of abuse are very serious. Therefore, you should always be extremely careful about the use of world wide web and private data management.
Every action on the network leaves a digital footprint. For example, photos we post on social networks, statements on forums, likes and dislikes of videos. Moreover, a user activity leaves a digital trace - information about the sites browsed, purchases made, and geographical locations visited. There are many channels through which our personal data is exposed and the effects of abuse are very serious. Therefore, you should always be extremely careful about the use of world wide web and private data management.
257. Combat Online Vaccine Registration Scams With Better Cybersecurity Measures
 Hackers are targeting the online vaccine supply chain and are setting up malicious attacks to have unauthorized access to the organization’s vaccine information
Hackers are targeting the online vaccine supply chain and are setting up malicious attacks to have unauthorized access to the organization’s vaccine information
258. The next frontier is here: Oracles with human insight
 Data, the very source of modern Oracles’ power, can also be its undoing.
Luckily, OptionRoom's new Oracle can give quantitative AND qualitative data insights.
Data, the very source of modern Oracles’ power, can also be its undoing.
Luckily, OptionRoom's new Oracle can give quantitative AND qualitative data insights.
259. Zero-Log VPNs Fight for User Security -Is This Reality or A Myth?
 Over time, VPN usage surged to an unprecedented level, and “Zero-Logs VPN” is what every virtual private network claims to be.
Over time, VPN usage surged to an unprecedented level, and “Zero-Logs VPN” is what every virtual private network claims to be.
260. I Hacked My Coffee Shop and Accessed My Data: Hacking Your Application May Be Easier Than You Think
 I noticed a suspicious behavior on the weekly email from my coffee shop's subscription; it was offering I edit my preferences directly through a dedicated link.
I noticed a suspicious behavior on the weekly email from my coffee shop's subscription; it was offering I edit my preferences directly through a dedicated link.
261. The Need for Privacy Protection in Computer Vision Applications
 This article describes why privacy concerns should be top of mind while building or adopting computer vision based applications
This article describes why privacy concerns should be top of mind while building or adopting computer vision based applications
262. Being 'Chief Geek' and Running 15 Websites with Noonies Nominee Mathias Hellquist
 So who TF is Mathias Hellquist and what is a "Chief Geek"? Read this interview to find out.
So who TF is Mathias Hellquist and what is a "Chief Geek"? Read this interview to find out.
263. In 2019, Securing Data Is No Easy Task. Clickjacking- A Case Study
 This article is about my journey to understand the current practice of de-anonymization via the clickjacking technique whereby a malicious website is able to uncover the identity of a visitor, including his full name and possibly other personal information. I don’t present any new information here that isn’t already publicly available, but I do look at how easy it is to compromise a visitor’s privacy and reveal his identity, even when he adheres to security best practices and uses an up-to-date browser and operating system.
This article is about my journey to understand the current practice of de-anonymization via the clickjacking technique whereby a malicious website is able to uncover the identity of a visitor, including his full name and possibly other personal information. I don’t present any new information here that isn’t already publicly available, but I do look at how easy it is to compromise a visitor’s privacy and reveal his identity, even when he adheres to security best practices and uses an up-to-date browser and operating system.
264. Serialization Filtering in Java - Preventing Zero-Day Security Vulnerabilities
 A simple configuration that requires no code change can save you from a hack such as Log4Shell, even from vulnerabilities we don't know about yet!
A simple configuration that requires no code change can save you from a hack such as Log4Shell, even from vulnerabilities we don't know about yet!
265. European User Data is Shared 376 Times Per Day on Average
 Violation of private data and its commercial exchange are recurrent issues in the online world. In this thread, our community discusses personal data share.
Violation of private data and its commercial exchange are recurrent issues in the online world. In this thread, our community discusses personal data share.
266. The UK and Taiwanese Governments are Using AI as a Fundamental Cybersecurity Tool: How is it Used?
 The UK and Taiwanese Governments are Using AI as a Fundamental Cyber Security Tool.
The UK and Taiwanese Governments are Using AI as a Fundamental Cyber Security Tool.
267. Ensuring Security in Your SaaS Applications [An Overview]

268. How to Keep Mission-Critical Business Data Secure in the Mobile Age
 Andrew Nichols | Protecting Mission-Critical Business Data in the Mobile Age
Andrew Nichols | Protecting Mission-Critical Business Data in the Mobile Age
269. How to Detect Cyber Threats

270. Handling Sensitive Data: A Primer
 Properly securing sensitive customer data is more important than ever.
Properly securing sensitive customer data is more important than ever.
271. How to Choose the Right Hyper-V Backup Strategy
 This post discusses the main data protection strategies that can help you keep your Hyper-V data secure at all times.
This post discusses the main data protection strategies that can help you keep your Hyper-V data secure at all times.
272. Staking on ‘Finney’ Testnet to Counter Sybil Attacks is now LIVE!!
 The Finney testnet was launched to avoid future Sybil attacks.
The Finney testnet was launched to avoid future Sybil attacks.
273. How an Improved Working Relationship Between Employer and Employee Could be the Key to Cybersecurity
 In a lot of organizations, the focus on cybersecurity has always been on building secure infrastructure and while the idea good in theory, it may not necessarily keep all your data safe. You need to consider the impact of a good working relationship and the understanding of how people think.
In a lot of organizations, the focus on cybersecurity has always been on building secure infrastructure and while the idea good in theory, it may not necessarily keep all your data safe. You need to consider the impact of a good working relationship and the understanding of how people think.
274. Internet Data Privacy Full Guide - keep your Data Safe Online
 We are on the planet where we utilize electronic frameworks for pretty much every exchange. There are numerous electronic frameworks, and every one of them manages information. Information is something which is viewed as important, and individuals are frequently very touchy to how their own data is being dealt with. Because of the estimation of information and its effect it has on individuals, there is a huge interest in information security.
We are on the planet where we utilize electronic frameworks for pretty much every exchange. There are numerous electronic frameworks, and every one of them manages information. Information is something which is viewed as important, and individuals are frequently very touchy to how their own data is being dealt with. Because of the estimation of information and its effect it has on individuals, there is a huge interest in information security.
Keeping your passwords, monetary, and other individual data sheltered and shielded from outside gate crashers has for some time been a need of organizations. However, it's undeniably basic for customers and people to notice information insurance exhortation and utilize sound practices to keep your delicate individual data protected and secure.
275. How to Handle EU Data Without the EU-US Privacy Shield Framework
 On July 16, 2020, the European Court of Justice invalidated the EU-US Privacy Shield Framework, erasing the data protection measures that had previously allowed a United States business to hold the data of European Union citizens in servers that reside in the US.
On July 16, 2020, the European Court of Justice invalidated the EU-US Privacy Shield Framework, erasing the data protection measures that had previously allowed a United States business to hold the data of European Union citizens in servers that reside in the US.
276. Data Access for Microservices
 If you want to access data in a distributed environment such as in a microservice architecture, then data services are the way to go. The idea is to create a data abstraction layer (DAL) that the rest of the system’s applications and services can share. Thus, a data service gives you a generalized interface to the data you’re exposing and provides access to it in a standard manner. This would be in a well-understood protocol and a known data format. For example, a popular approach is to use JSON via HTTP/S.
If you want to access data in a distributed environment such as in a microservice architecture, then data services are the way to go. The idea is to create a data abstraction layer (DAL) that the rest of the system’s applications and services can share. Thus, a data service gives you a generalized interface to the data you’re exposing and provides access to it in a standard manner. This would be in a well-understood protocol and a known data format. For example, a popular approach is to use JSON via HTTP/S.
277. Announcing our Data Breach website on Data Privacy Day
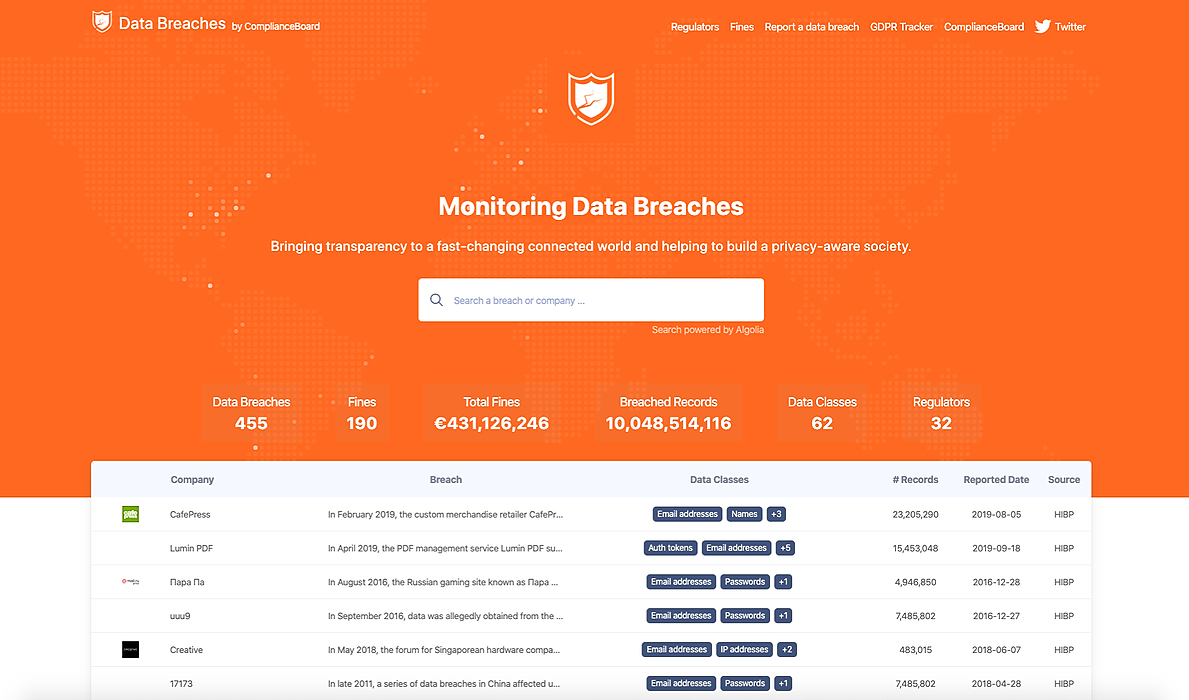 We are happy to announce our Data Breach website Databreach.es, our latest community project. With this project, we strive to create insights into global data breaches. Which companies have been breached, what kind of data got lost, what's the impact on your privacy and how did these companies handle the situation.
We are happy to announce our Data Breach website Databreach.es, our latest community project. With this project, we strive to create insights into global data breaches. Which companies have been breached, what kind of data got lost, what's the impact on your privacy and how did these companies handle the situation.
278. Discovering 10 Cybersecurity Practices for Enhanced IT Infrastructure Protection
 The need to have secure IT Infrastructure is common for all companies worldwide. Learn the best cybersecurity practices to get yourself protected from hacking.
The need to have secure IT Infrastructure is common for all companies worldwide. Learn the best cybersecurity practices to get yourself protected from hacking.
279. How to Avoid Becoming a Victim of Data Breach

280. How I Created a Zero Trust Overlay Network in my Home
 Enabling a secure home automation experience, by creating a zero trust overlay network to access #HomeAssistant.
Enabling a secure home automation experience, by creating a zero trust overlay network to access #HomeAssistant.
281. 7 Ways to Protect Your Company from Insecure Credentials
 Verizon’s 2020 DBIR reports that more than 80% of hacking-related breaches involve brute force or the use of lost or stolen credentials— here’s how to prevent weak or compromised credentials from being used in your company’s applications and network
Verizon’s 2020 DBIR reports that more than 80% of hacking-related breaches involve brute force or the use of lost or stolen credentials— here’s how to prevent weak or compromised credentials from being used in your company’s applications and network
282. Quantum Computation and Its Possible Effects on Society
 This paper will discuss what quantum computation is and the effects it can have on the way our society works.
This paper will discuss what quantum computation is and the effects it can have on the way our society works.
283. $DAG Will Do To Big Data What Bitcoin Did To Money
 Hello, Dear reader! 🧑💻 Here I talk about the Constellation Network, Inc. Why I think the Constellation is one of the most amazing companies! Why they will steal the show and create and set the standard for future Cybersecurity for Big Data. I give arguments to which I paid more attention than to others, as possible clearly and briefly. Go!
Hello, Dear reader! 🧑💻 Here I talk about the Constellation Network, Inc. Why I think the Constellation is one of the most amazing companies! Why they will steal the show and create and set the standard for future Cybersecurity for Big Data. I give arguments to which I paid more attention than to others, as possible clearly and briefly. Go!
284. There Are More Risks Associated With SaaS Data Security Than Potential GDPR Fines
 The growing reliance on SaaS business calls for an improvement in security. On occasions, data security can be of existential importance to organizations.
The growing reliance on SaaS business calls for an improvement in security. On occasions, data security can be of existential importance to organizations.
285. Improving IoT Device Security Prevention from Zero-Day Attacks
 Security for the “Internet of Things” (or IoT) is still relatively new to a majority of organizations.
Security for the “Internet of Things” (or IoT) is still relatively new to a majority of organizations.
286. How To Code To Prevent Sensitive Data Exposure

287. Computer Trojan Attacks: Nature, Development and Prevention
 Trojans are nothing more than delivery tactics that cybercriminals employ to further execute any cybersecurity threats—ransomware attacks, spyware attacks etc.
Trojans are nothing more than delivery tactics that cybercriminals employ to further execute any cybersecurity threats—ransomware attacks, spyware attacks etc.
288. Be Resilient not Vulnerable to Ransomware Emails

289. Data Is Now a Luxury Good: Here’s Why (It Shouldn’t Be)

290. Why Data Governance is Vital for Data Management
 Both data governance and data management workflows are critical to ensuring the security and control of an organization’s most valuable asset-data.
Both data governance and data management workflows are critical to ensuring the security and control of an organization’s most valuable asset-data.
291. 23 Cybersecurity Tips to Level up Your Data Privacy Game
 It's important to keep yourself up-to-date on the latest security measures. Cybercrime has increased, secure your data.
It's important to keep yourself up-to-date on the latest security measures. Cybercrime has increased, secure your data.
292. Fast Fourier Transform: Scaling Multi-Point Evaluation
 Fast Fourier Transforms are a key part of algorithms thanks to their ability to multiply large numbers quickly. They have been used in blockchain in a few ways.
Fast Fourier Transforms are a key part of algorithms thanks to their ability to multiply large numbers quickly. They have been used in blockchain in a few ways.
293. Blind Attacks: Understanding CSRF (Cross Site Request Forgery)
 This article contains complete (and step-by-step) information about CSRF attacks.
This article contains complete (and step-by-step) information about CSRF attacks.
294. A Comprehensive Guide to Penetration Testing
 We'll go through the Top 5 Pen Testing Firms in this blog article, as well as what makes them special.
We'll go through the Top 5 Pen Testing Firms in this blog article, as well as what makes them special.
295. Data security through the prism of business risks
 The place of data safety in business viability and reflects on how to enable security in digital product - discussed by me, Igor Piatnytskyi, VP, Business Development at Nullgravity.
The place of data safety in business viability and reflects on how to enable security in digital product - discussed by me, Igor Piatnytskyi, VP, Business Development at Nullgravity.
296. How to Reduce the Risk of Former Employees Coordinating with Insider Threats
 Here below are a couple of tips to keep in mind when thinking about how to minimize your risk from insider threats.
Here below are a couple of tips to keep in mind when thinking about how to minimize your risk from insider threats.
297. Imagine Yourself Being A Hacker [Beginner's Guide]

298. How Payment Businesses Deal with Fraud and Data leaks
 Any problems that payment business faces bear direct, measurable losses. This article will help to avoid some situations by relying on anti-fraud, PCI DSS, etc.
Any problems that payment business faces bear direct, measurable losses. This article will help to avoid some situations by relying on anti-fraud, PCI DSS, etc.
299. 10 Best Tactics For Your WooCommerce Store Security
 WooCommerce is a great plugin for WordPress to build an online store. With an entire eCommerce ecosystem and a dedicated global community, it has achieved the reputation of an industry standard. Still, this doesn’t mean that nothing c go wrong, especially if you ignore essential security precautions. Here are ten tips on how to make your business (and your customers’ data) safe.
WooCommerce is a great plugin for WordPress to build an online store. With an entire eCommerce ecosystem and a dedicated global community, it has achieved the reputation of an industry standard. Still, this doesn’t mean that nothing c go wrong, especially if you ignore essential security precautions. Here are ten tips on how to make your business (and your customers’ data) safe.
300. How to Optimize Your Salesforce Security
 Companies implementing Salesforce’s internal security solutions may find their customizations limit visibility into the risks that can impact other processes.
Companies implementing Salesforce’s internal security solutions may find their customizations limit visibility into the risks that can impact other processes.
301. The Coronavirus and the Emergence of Global Citizens’ Solidarity
 How technologies are empowering global citizens to take action for the benefit of humanity
How technologies are empowering global citizens to take action for the benefit of humanity
302. How to Protect Your Company's VPN When You Have a Remote Team
 Prevent malicious agents from exploiting their VPN connections! However, it's still critical for each employee to exercise cyber hygiene to ensure cybersecurity
Prevent malicious agents from exploiting their VPN connections! However, it's still critical for each employee to exercise cyber hygiene to ensure cybersecurity
303. Network Security Basics
 Ever since the creation of the internet with all of the good that it has brought to the table came the bad as well. In the age of information technology, an unsecured product is a surefire way to numerous issues. A company, which creates a product has to make sure both the software and the network security features of it are as robust as possible. In the previous article we discussed application security, however, it is never complete without a clear network safeguards to serve as a frontline against malicious users trying to exploit the system. But what is network security and what are some of the methods used to protect systems?
Ever since the creation of the internet with all of the good that it has brought to the table came the bad as well. In the age of information technology, an unsecured product is a surefire way to numerous issues. A company, which creates a product has to make sure both the software and the network security features of it are as robust as possible. In the previous article we discussed application security, however, it is never complete without a clear network safeguards to serve as a frontline against malicious users trying to exploit the system. But what is network security and what are some of the methods used to protect systems?
304. 5 Most Important Directions In Which Tech Industry Develops In 2021
 Stay competitive within the COVID-19 landscape. Take a look at our findings on what trends will shape the IT industry in 2021.
Stay competitive within the COVID-19 landscape. Take a look at our findings on what trends will shape the IT industry in 2021.
305. Strategies for Combating Cloud Security Risks
 There are some proven operational and security practices to significantly reduce the occurrence and impact of security breaches in the cloud.
There are some proven operational and security practices to significantly reduce the occurrence and impact of security breaches in the cloud.
306. Data Storage Security: 5 Best Practices to Secure Your Data

307. Redefining Privacy and Data Ownership: An Interview with ARPA Founder, Felix Xu
 A conversation with Felix Xu, CEO of ARPA, on data utility and ownership, the NFT ecosystem, and much more.
A conversation with Felix Xu, CEO of ARPA, on data utility and ownership, the NFT ecosystem, and much more.
308. Insider Threats Facing Government Organizations: 3 Tips for Mitigation
 Verizon's Data Breach Investigation Report for 2022 (DBIR) was recently released and it has some good news and bad news when it comes to the risk of insider attacks.
Verizon's Data Breach Investigation Report for 2022 (DBIR) was recently released and it has some good news and bad news when it comes to the risk of insider attacks.
309. Good Ways To Make Your Data More Secure
 Data security is a business challenge and a business opportunity, not a mere technical task for your IT department.
Data security is a business challenge and a business opportunity, not a mere technical task for your IT department.
310. IoT Security Threats in Retail: How Do We Eliminate Them?
 The number of smart connected devices on the Internet, including cameras, machines, and sensors, has grown exponentially. According to the premier market research firm, International Data Corporation, by 2025, it’s estimated that we will have approximately 41.6 billion connected devices.
The number of smart connected devices on the Internet, including cameras, machines, and sensors, has grown exponentially. According to the premier market research firm, International Data Corporation, by 2025, it’s estimated that we will have approximately 41.6 billion connected devices.
311. A Complete Guide on How to Assess Risk and Run Contingency for your IT Infrastructure Needs
 IT risk assessment is one of the most crucial processes in your organization. Assessing risk and putting contingency plans in place helps run the organization smoothly.
IT risk assessment is one of the most crucial processes in your organization. Assessing risk and putting contingency plans in place helps run the organization smoothly.
312. Introduction to Account Aggregators: 8 Common Myths Debunked
 Just like UPI helps people share money between bank accounts seamlessly, the new Account Aggregator framework (AA) will help people share their financial data quickly and safely.
Just like UPI helps people share money between bank accounts seamlessly, the new Account Aggregator framework (AA) will help people share their financial data quickly and safely.
313. How to Properly Implement GDPR for Customer Communications
 If you are considering sending notifications to the users of your SaaS application, whether via email, push, or a Slack bot, you need to keep GDPR in mind.
If you are considering sending notifications to the users of your SaaS application, whether via email, push, or a Slack bot, you need to keep GDPR in mind.
314. Root Cause Analysis: How to Get to the Heart of a Breach
 Root cause analysis allows businesses to identify the primary cause behind a data breach to prevent it from happening again. Here's how to conduct an RCA.
Root cause analysis allows businesses to identify the primary cause behind a data breach to prevent it from happening again. Here's how to conduct an RCA.
315. Not All Password Managers Are Created Equal: Which is the Best?
 Web-based password managers have emerged as a response to the proliferation of web applications.
Web-based password managers have emerged as a response to the proliferation of web applications.
316. Securing Sensitive Customer Information in the Age of Data
 Featured Image Source: Pixabay
Featured Image Source: Pixabay
317. Is Remote Work Responsible for Growing Cybersecurity Threats?
 A tech story centered around the looming issues of cybersecurity, cyber attacks, and the possible solutions in today's remote working ecosystem.
A tech story centered around the looming issues of cybersecurity, cyber attacks, and the possible solutions in today's remote working ecosystem.
318. Data Backup Strategy To Reduce Data Loss
 Backing up the data is one of the most important processes for businesses. It requires creating a copy of all your data and storing it.
Backing up the data is one of the most important processes for businesses. It requires creating a copy of all your data and storing it.
319. IPVanish VPN Reviev 2021: Speed, Privacy and All You Need to Know
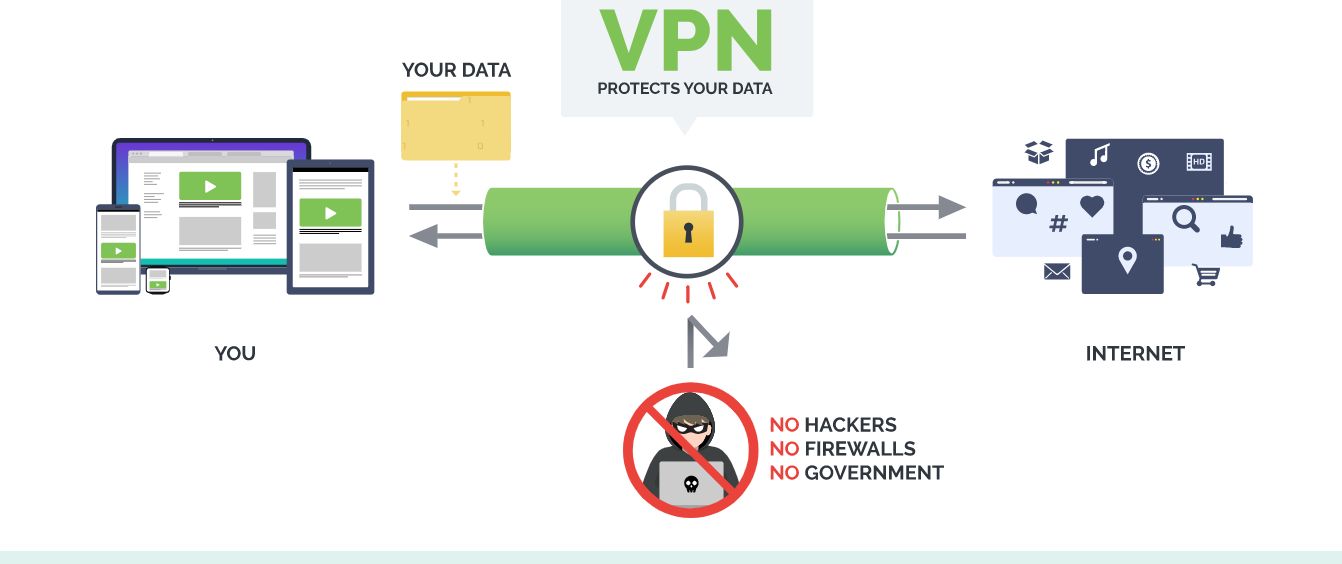
320. Cybersecurity Implementation for Cryptocurrency Retirement Plans
 Saving up for retirement is something everyone must face at some point in their lives. New advances allow you to invest in cryptocurrency for the future.
Saving up for retirement is something everyone must face at some point in their lives. New advances allow you to invest in cryptocurrency for the future.
321. How To Make an Internal Employee Survey on Endpoint Security
 Employee’s Endpoint security Internal Survey-Template
Employee’s Endpoint security Internal Survey-Template
322. Darkweb Community MagBO Sells Data Stolen From Over 20k Websites
 MagBO, the Russian-speaking dark web marketplace for trading in backdoored websites, continues to grow exponentially. In less than two years, the collection of leaks grew from around 3,000 in September 2018 to 26,605 in February 2020.
MagBO, the Russian-speaking dark web marketplace for trading in backdoored websites, continues to grow exponentially. In less than two years, the collection of leaks grew from around 3,000 in September 2018 to 26,605 in February 2020.
323. Reverse Social Engineering: A Call to Quit Sharing More Than Necessary
 Social engineering is the use of a person's sensitive information to launch a targeted cyber-attack on them. Reverse social engineering mitigates the rate...
Social engineering is the use of a person's sensitive information to launch a targeted cyber-attack on them. Reverse social engineering mitigates the rate...
324. E-commerce Cybersecurity - Enhancing Data Protection in 2021
 In 2020, the COVID-19 pandemic has completely changed the situation in the shopping industry: both e-commerce and brick-and-mortar were affected
In 2020, the COVID-19 pandemic has completely changed the situation in the shopping industry: both e-commerce and brick-and-mortar were affected
325. How Proxies & Browsers Are Meant to Work Together
 Proxies can be used for an IP covering, but other distinguishing features need something more. And all this because of a digital fingerprint revealing us.
Proxies can be used for an IP covering, but other distinguishing features need something more. And all this because of a digital fingerprint revealing us.
326. 5 Reasons Why Enterprises Need Zero Trust Security
 The notion of “Zero Trust” has been around since the 90s. But, the Zero Trust security model was first coined by John Kindervag to describe stricter access control management and cybersecurity programs, in 2010. Meaning that infinite trust is diminished from all computing infrastructure, and Zero Trust is grounded on the idea “trust none, verify all”.
The notion of “Zero Trust” has been around since the 90s. But, the Zero Trust security model was first coined by John Kindervag to describe stricter access control management and cybersecurity programs, in 2010. Meaning that infinite trust is diminished from all computing infrastructure, and Zero Trust is grounded on the idea “trust none, verify all”.
327. 5 Data Security Mistakes Small Businesses Making
 Verizon’s 2020 Data Breach Investigation Report indicates that cybercriminals don’t care how big or small your business is — they want your credentials and data regardless (and will do what they can to get them)
Verizon’s 2020 Data Breach Investigation Report indicates that cybercriminals don’t care how big or small your business is — they want your credentials and data regardless (and will do what they can to get them)
328. Cybersecurity Takeaways From the Pandemic and Solutions for 2021
 In 2020, Cybersecurity has become more important than ever for businesses all over the world. Here's how to protect your data from cyberattacks going forward.
In 2020, Cybersecurity has become more important than ever for businesses all over the world. Here's how to protect your data from cyberattacks going forward.
329. Healthcare's Biggest Cybersecurity Challenges and How to Prevent Them
 Recognizing the huge financial and reputational impact caused by data breaches, more and more healthcare organizations are paying attention to cybersecurity.
Recognizing the huge financial and reputational impact caused by data breaches, more and more healthcare organizations are paying attention to cybersecurity.
330. 9 Security Tips to Protect Your Website from Hackers and Data Breaches
 Here are 9 Security Tips to Protect Websites from Hackers. A secure website will establish your position in the cyber-world and let you do more business.
Here are 9 Security Tips to Protect Websites from Hackers. A secure website will establish your position in the cyber-world and let you do more business.
331. Is TikTok a Security Risk for Businesses?
 Possible security and ethical concerns on TikTok raise questions about whether businesses should be using the platform.
Possible security and ethical concerns on TikTok raise questions about whether businesses should be using the platform.
332. We've Mistaken Facebook For What It's Not
 Image Credit: Wallpapercave
Image Credit: Wallpapercave
333. 5 ML Security Challenges Demanding our Unwavering Attention
 As per Gartner, almost 80 percent of every emerging technology will have Artificial Intelligence as the backbone by the end of 2021. Building secure software is a no mean feat. Amid the lingering cybersecurity threats and the potential challenges posed by the endpoint inadequacies, the focus is continuously shifting towards machine learning and the relevant AI implementations for strengthening the existing app and software security standards.
As per Gartner, almost 80 percent of every emerging technology will have Artificial Intelligence as the backbone by the end of 2021. Building secure software is a no mean feat. Amid the lingering cybersecurity threats and the potential challenges posed by the endpoint inadequacies, the focus is continuously shifting towards machine learning and the relevant AI implementations for strengthening the existing app and software security standards.
334. Java Application Development: Fixing the Security Redundancies
 A 2017 report, released by the State of Software Security revealed that almost 88 percent of applications with Java at the core, at least have a single vulnerable component to show for.
A 2017 report, released by the State of Software Security revealed that almost 88 percent of applications with Java at the core, at least have a single vulnerable component to show for.
335. How Artificial Intelligence (AI) Can Help In CCPA Compliance?
 California Consumer Privacy Act (CCPA) was passed recently in the USA state of California and will be implemented by 2020. This new regulation is transforming the privacy policies of businesses dealing with the data of Californian users.
California Consumer Privacy Act (CCPA) was passed recently in the USA state of California and will be implemented by 2020. This new regulation is transforming the privacy policies of businesses dealing with the data of Californian users.
336. Sharing Your (Encryption) Keys Across Multi/Hybrid Clouds
 Before we dive into the fun part of getting keys shared amongst cloud providers, there are a variety of tools required to get this tutorial working.
Before we dive into the fun part of getting keys shared amongst cloud providers, there are a variety of tools required to get this tutorial working.
337. An Introduction to Code Signing Architectures and Techniques
 In the recent past, many technology firms were being targeted by hackers to tamper and corrupt the source code. These attacks heavily impact brand reputation and also leads to huge losses for firms victimized. To tackle this scenario, Code Signing techniques can be used for safeguarding the code integrity and to provide authenticity of the author to the end-user by providing digital signatures. Code Signing provides secure and trusted distribution of software preventing tampering, corruption and forgery. Code signing improves end-user confidence in software/code integrity and sender authenticity.
In the recent past, many technology firms were being targeted by hackers to tamper and corrupt the source code. These attacks heavily impact brand reputation and also leads to huge losses for firms victimized. To tackle this scenario, Code Signing techniques can be used for safeguarding the code integrity and to provide authenticity of the author to the end-user by providing digital signatures. Code Signing provides secure and trusted distribution of software preventing tampering, corruption and forgery. Code signing improves end-user confidence in software/code integrity and sender authenticity.
338. Automation Is the Essential Part of Cyber Risk Management: Know Why
 Cybersecurity risk management, also defined as IT risk management, applies to any of the technology, people, regulations, and processes that a company may employ to assess, handle, and minimize cybersecurity threats to customer and company data, as well as business operations. IT risk, detection tools for example, would almost certainly provide cybersecurity risk management software as well as security controls to prevent and address cyber risk and security exposures proactively.
Cybersecurity risk management, also defined as IT risk management, applies to any of the technology, people, regulations, and processes that a company may employ to assess, handle, and minimize cybersecurity threats to customer and company data, as well as business operations. IT risk, detection tools for example, would almost certainly provide cybersecurity risk management software as well as security controls to prevent and address cyber risk and security exposures proactively.
339. Be 100% Safe On The Internet Using These Strategies
 The Internet is full of opportunities, useful information, entertainment, and dangers as well. To protect yourself from the latter, you need to follow certain safety rules. Read on to learn how to properly use a home or public Wi-Fi to avoid dangerous malware and protect personal data, and what is the role of nect MODEM in helping you do so.
The Internet is full of opportunities, useful information, entertainment, and dangers as well. To protect yourself from the latter, you need to follow certain safety rules. Read on to learn how to properly use a home or public Wi-Fi to avoid dangerous malware and protect personal data, and what is the role of nect MODEM in helping you do so.
340. How Verifiable Creds, Decentralized Identifiers and Blockchain Work Together for a Safer Internet
 The future of the internet will come with more risks to our data privacy. Fortunately, Blockchain and Decentralized Identifiers can work together to protect.
The future of the internet will come with more risks to our data privacy. Fortunately, Blockchain and Decentralized Identifiers can work together to protect.
341. Is Data Sovereignty Possible? In The European Union, It Soon Could Be
 Data privacy, security, and sovereignty issues have gained significant attention over recent years.
Data privacy, security, and sovereignty issues have gained significant attention over recent years.
342. How to Revolutionize Data Security Through Homomorphic Encryption
 For decades, we have benefited from modern cryptography to protect our sensitive data during transmission and storage. However, we have never been able to keep the data protected while it is being processed.
For decades, we have benefited from modern cryptography to protect our sensitive data during transmission and storage. However, we have never been able to keep the data protected while it is being processed.
343. This App Is Tracking 250,000 Immigrants in the U.S.A.
 “Every time they call me, I’m scared,” she said. “The truth is … I don’t feel free.”
“Every time they call me, I’m scared,” she said. “The truth is … I don’t feel free.”
344. What Personal Details Are You Sharing Without Knowing?
 Unless you have changed your web browser default settings it is quite likely you are leaking personal details as you move around online. But just how much?
Unless you have changed your web browser default settings it is quite likely you are leaking personal details as you move around online. But just how much?
345. How Should Companies Build a Robust Cybersecurity Culture?
 In the modern age of information and technology, there’s not a single individual or organization that would object to the tightening of cybersecurity within an enterprise.
In the modern age of information and technology, there’s not a single individual or organization that would object to the tightening of cybersecurity within an enterprise.
346. 13 Smart Ways to Secure Your WordPress Website

347. How to Develop Your SAAS Application with a Security Mindset
 Are you looking to build a SaaS platform? If yes, then read this blog to know how to build a SaaS application with security in mind.
Are you looking to build a SaaS platform? If yes, then read this blog to know how to build a SaaS application with security in mind.
348. Data Sovereignty Comes Closer To Reality For EU Residents
 Data privacy, security, and sovereignty issues have gained significant attention over recent years.
Data privacy, security, and sovereignty issues have gained significant attention over recent years.
349. The Phases of a Cyber Attack and How to Guard Against Them
 In many cases, the person in a victim role may not be of any interest to criminals by him/herself, but the person or organization the victim is associated with.
In many cases, the person in a victim role may not be of any interest to criminals by him/herself, but the person or organization the victim is associated with.
350. Handle Sensitive Data Securely with Skyflow
 You don’t need to be a data privacy expert in order to implement best practices.
You don’t need to be a data privacy expert in order to implement best practices.
351. The State of Infrastructure Security Amidst this Pandemic
 Around mid-March, news filtered out of a cyberattack that hit the U.S. Health and Human Services (HHS) Department. Amid battling a pandemic, the HHS cyberinfrastructure was overloaded, but the HHS Secretary Alex Azar claimed that "we had no penetration into our networks, we had no degradation of the functioning of our networks."
Around mid-March, news filtered out of a cyberattack that hit the U.S. Health and Human Services (HHS) Department. Amid battling a pandemic, the HHS cyberinfrastructure was overloaded, but the HHS Secretary Alex Azar claimed that "we had no penetration into our networks, we had no degradation of the functioning of our networks."
Thank you for checking out the 351 most read stories about Data Security on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

