Let's learn about Gdpr via these 44 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
1. How Does the GDPR Affect B2B Data? - A Simple Explanation
 You can reach out to prospects and collect B2B data even under the GDPR. However, there are some rules and regulations.
You can reach out to prospects and collect B2B data even under the GDPR. However, there are some rules and regulations.
2. Bye-bye Google Fonts: German Court Rules That Google Fonts Is Not in Compliance with GDPR
 Google Fonts is a data privacy concern. Learn why you should care.
Google Fonts is a data privacy concern. Learn why you should care.
3. Cloud Data Security and the Need for Confidential Containers
 Why should you choose Confidential Containers for your business and how do they stand out from the "vanilla" version? Check it out in our article!
Why should you choose Confidential Containers for your business and how do they stand out from the "vanilla" version? Check it out in our article!
4. The Digital Iceberg: How Third-Party Code Can Break Your Business
 By Chris Olson, CEO of The Media Trust
By Chris Olson, CEO of The Media Trust
5. The Future of Innovation: How Will Entrepreneurs Adapt To This Decade?
 Futureproofing is at the forefront of every entrepreneur’s mind. But putting ideas into practice can be a different challenge altogether.
Futureproofing is at the forefront of every entrepreneur’s mind. But putting ideas into practice can be a different challenge altogether.
6. Businesses are Tackling Data Privacy Restrictions with Hybrid Cloud
 If a business deals with personal data, it inevitably faces data protection and privacy legislation issues. Here is how the hybrid cloud helps address those.
If a business deals with personal data, it inevitably faces data protection and privacy legislation issues. Here is how the hybrid cloud helps address those.
7. Handling Sensitive Data: A Primer
 Properly securing sensitive customer data is more important than ever.
Properly securing sensitive customer data is more important than ever.
8. Why Are Businesses Raising Equity with Crowdfunding?
 Equity crowdfunding was not the easiest choice to make, but it kept us true to our core values of trust, transparency, and user-centricity.
Equity crowdfunding was not the easiest choice to make, but it kept us true to our core values of trust, transparency, and user-centricity.
9. New Data Privacy Laws Are an Opportunity, Not a Threat

10. How to Properly Implement GDPR for Customer Communications
 If you are considering sending notifications to the users of your SaaS application, whether via email, push, or a Slack bot, you need to keep GDPR in mind.
If you are considering sending notifications to the users of your SaaS application, whether via email, push, or a Slack bot, you need to keep GDPR in mind.
11. Data Leak Prevention with Databunker
 We hear the horror stories of data leaks almost every day. Some require a sophisticated attack to gain shell access to the servers. Some happen over the web using the SQL injections in the web apps. As a result of this attack, your customer data can be dumped and personal data leaked.
We hear the horror stories of data leaks almost every day. Some require a sophisticated attack to gain shell access to the servers. Some happen over the web using the SQL injections in the web apps. As a result of this attack, your customer data can be dumped and personal data leaked.
12. How to Create an Effective Incident Response Plan

13. What are the Essential Healthcare IT Standards & Regulations?
 Still, despite the array of communication technologies available, there is no universal way of managing and transferring healthcare data.
Still, despite the array of communication technologies available, there is no universal way of managing and transferring healthcare data.
14. Redefining Privacy and Data Ownership: An Interview with ARPA Founder, Felix Xu
 A conversation with Felix Xu, CEO of ARPA, on data utility and ownership, the NFT ecosystem, and much more.
A conversation with Felix Xu, CEO of ARPA, on data utility and ownership, the NFT ecosystem, and much more.
15. Data Privacy is Becoming More Important for Users in 2022
 A look at how data privacy is becoming more important for users in 2022
A look at how data privacy is becoming more important for users in 2022
16. Best Practices for Cold Emailing Under GDPR
 As a growth hacker I do cold emailing. A lot!
As a growth hacker I do cold emailing. A lot!
17. The Independent Phone : More Privacy, Less Freedom?
 Freedom and privacy tend to go together, but there is a difference. With a more private phone, does it really mean you have more freedom?
Freedom and privacy tend to go together, but there is a difference. With a more private phone, does it really mean you have more freedom?
18. Playing Hide and Seek with Big Brother
 We live in the age of constant surveillance, unlike the one described by George Orwell in his seminal book 1984, but the one which might have bought willingly. We regularly surrender information in exchange for free services and convenience. Often, we skim over the fine print of user agreements, and the act of disseminating private information becomes a voluntary task that absolves the media giants from any legal burden [3]. Ian Bogost of The Atlantic calls this “the age of privacy nihilism” and says that the changes in escaping surveillance capitalism are bleak [4].
We live in the age of constant surveillance, unlike the one described by George Orwell in his seminal book 1984, but the one which might have bought willingly. We regularly surrender information in exchange for free services and convenience. Often, we skim over the fine print of user agreements, and the act of disseminating private information becomes a voluntary task that absolves the media giants from any legal burden [3]. Ian Bogost of The Atlantic calls this “the age of privacy nihilism” and says that the changes in escaping surveillance capitalism are bleak [4].
19. Announcing our Data Breach website on Data Privacy Day
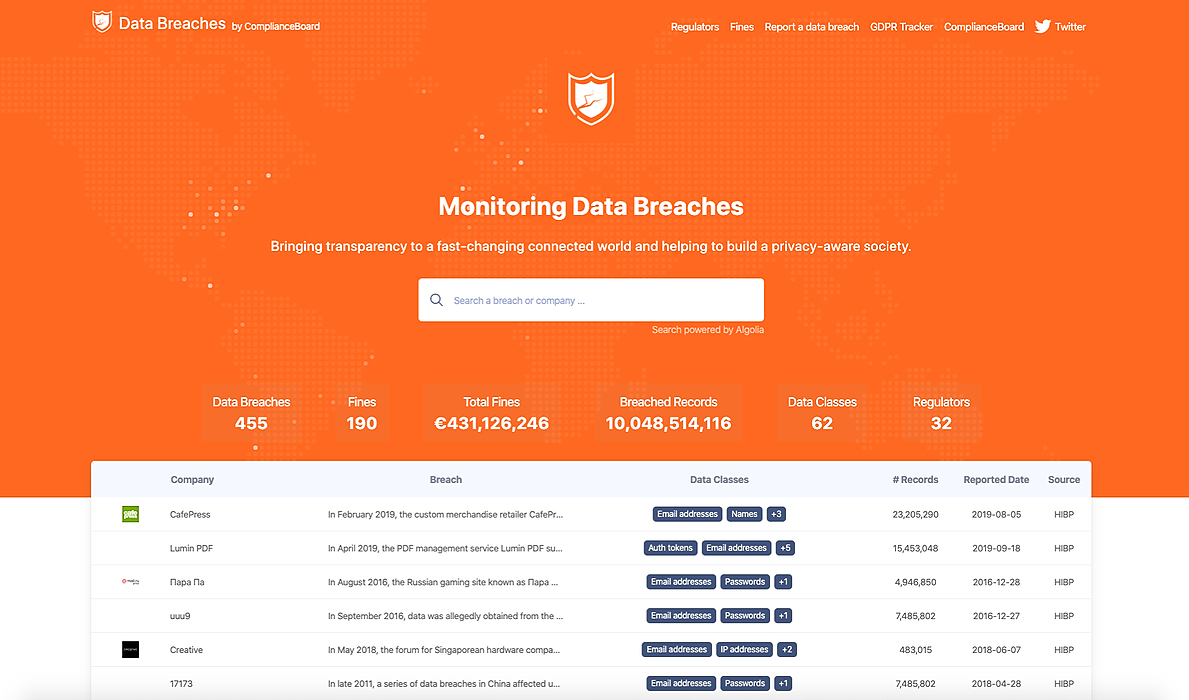 We are happy to announce our Data Breach website Databreach.es, our latest community project. With this project, we strive to create insights into global data breaches. Which companies have been breached, what kind of data got lost, what's the impact on your privacy and how did these companies handle the situation.
We are happy to announce our Data Breach website Databreach.es, our latest community project. With this project, we strive to create insights into global data breaches. Which companies have been breached, what kind of data got lost, what's the impact on your privacy and how did these companies handle the situation.
20. Will The New Wave of Data Laws Affect Fintech?
 Fintech, otherwise known as the financial technology market, is on a very strong growth trajectory, having already disrupted the banking world in a powerful way. From mobile payments, to artificial intelligence, insurance and investment services, Fintech has gradually transformed the way we bank since the day the US Federal Reserve introduced the Fedwire Funds Service back in 1918, which used morse code and telegraph to transfer funds electronically.
Fintech, otherwise known as the financial technology market, is on a very strong growth trajectory, having already disrupted the banking world in a powerful way. From mobile payments, to artificial intelligence, insurance and investment services, Fintech has gradually transformed the way we bank since the day the US Federal Reserve introduced the Fedwire Funds Service back in 1918, which used morse code and telegraph to transfer funds electronically.
21. GDPR vs CCPA: Data Privacy On The Lead [Infographic]
 A quick look at the two approaches to privacy
A quick look at the two approaches to privacy
22. How Software Accountability shifts Technology Dynamics for Today’s Startups
 For a long time now, software-based startups have been launching their products and thrived by having users’ data as the very foundation of their business models. Social media platforms are the perfect examples of how a business can profit from a well of consumer data. While users had traditionally been in the dark about how the information they share when interacting with digital products is used, various notorious scandals have changed the narrative.
For a long time now, software-based startups have been launching their products and thrived by having users’ data as the very foundation of their business models. Social media platforms are the perfect examples of how a business can profit from a well of consumer data. While users had traditionally been in the dark about how the information they share when interacting with digital products is used, various notorious scandals have changed the narrative.
23. GDPR's Two-Tier Internet: One Year On
 It’s been over a year since the GDPR came into effect, and at least five since it was first debated seriously. For much of that time it was discussed as a global game-changer, yet the predicted earth-shaking effects of its implementation — billion-dollar fines, the end of data exploitation by rogue firms, high-profile court cases — have largely yet to materialize. Instead, the landscape of the internet has changed in more subtle and complex ways which could not have been predicted by pundits, and it’s affecting businesses of every size.
It’s been over a year since the GDPR came into effect, and at least five since it was first debated seriously. For much of that time it was discussed as a global game-changer, yet the predicted earth-shaking effects of its implementation — billion-dollar fines, the end of data exploitation by rogue firms, high-profile court cases — have largely yet to materialize. Instead, the landscape of the internet has changed in more subtle and complex ways which could not have been predicted by pundits, and it’s affecting businesses of every size.
24. Best Practices for GDPR Compliance Implementation
 In the new digital age we face unprecedented times of wide opportunities. Internet is just about everywhere and can be connected to just about any device generating diverse forms of data circulation, exchange and accumulation.
In the new digital age we face unprecedented times of wide opportunities. Internet is just about everywhere and can be connected to just about any device generating diverse forms of data circulation, exchange and accumulation.
25. The Cost of Overlooking Patch Management
 Software firms are not responsible for data breaches - you are! Make sure you're keeping up with the latest patches whenever updates are released.
Software firms are not responsible for data breaches - you are! Make sure you're keeping up with the latest patches whenever updates are released.
26. SaaS Apps Are Less Compliant Than You Think: An Analysis of The Top 1,000 SaaS Apps
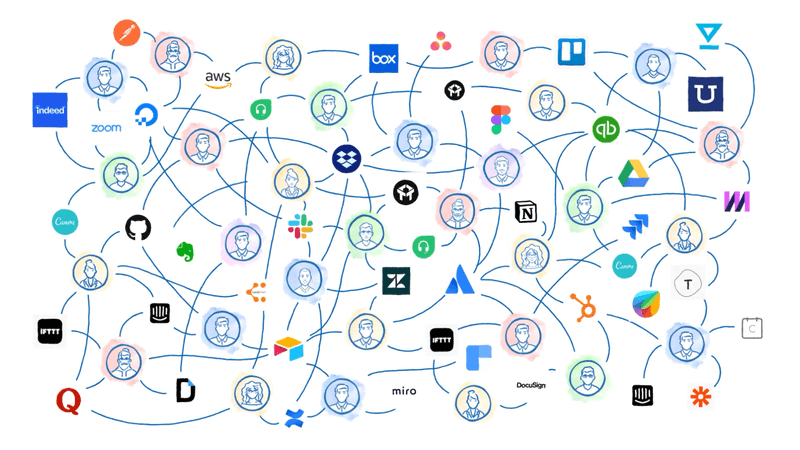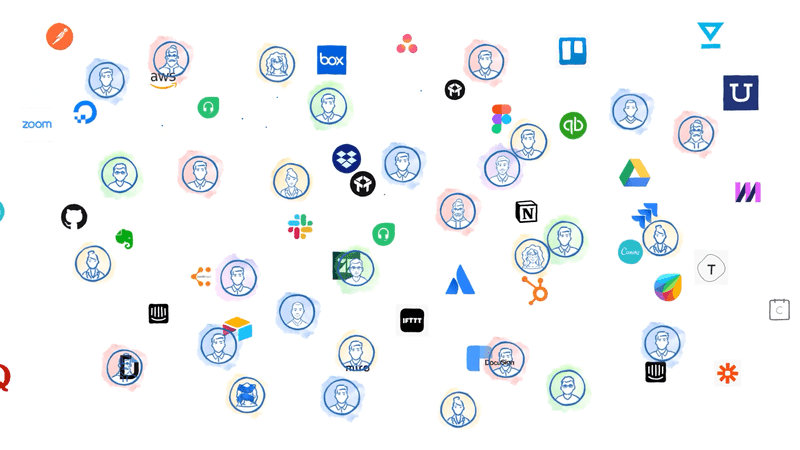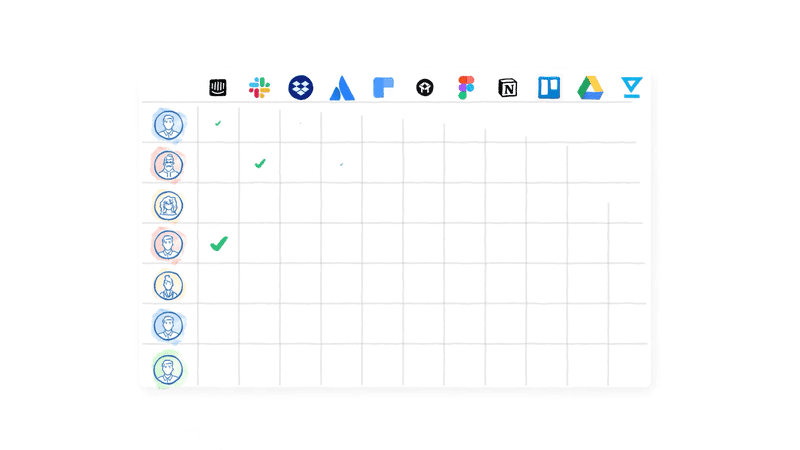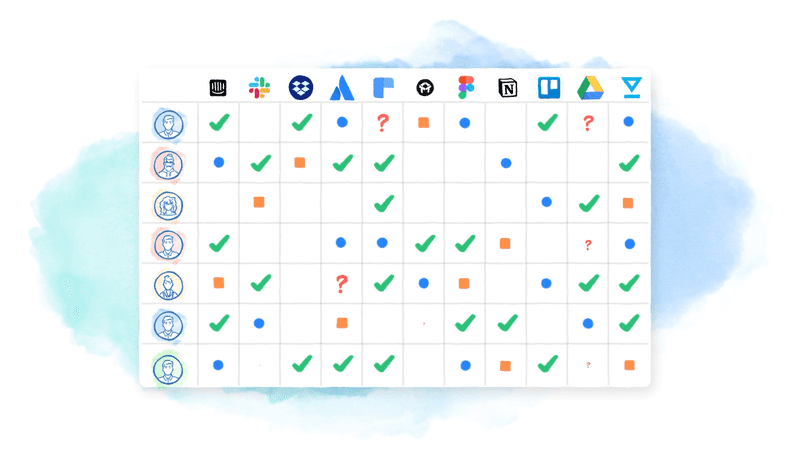 Today’s IT and operations professionals might find themselves feeling like the opposite of Spiderman. With great responsibility comes … no power? The stakes are higher than ever to ensure that their organizations are protected from a security and compliance perspective, but new survey data from Blissfully shows that the most popular SaaS applications are less compliant than you’d think.
Today’s IT and operations professionals might find themselves feeling like the opposite of Spiderman. With great responsibility comes … no power? The stakes are higher than ever to ensure that their organizations are protected from a security and compliance perspective, but new survey data from Blissfully shows that the most popular SaaS applications are less compliant than you’d think.
27. What are the Key Stages of Data Protection Impact Assessment?
 A Data Protection Impact Assessment which is also referred to as Privacy Impact Assessments is a mandatory requirement for organizations to comply with.
A Data Protection Impact Assessment which is also referred to as Privacy Impact Assessments is a mandatory requirement for organizations to comply with.
28. Research Suggests That a Hard Brexit Could Lead to Significant Confusion within the UK Cloud Market
 An inquiry into public opinion suggests that fear and confusion could push sensitive personal data out of the country.
An inquiry into public opinion suggests that fear and confusion could push sensitive personal data out of the country.
29. Hiring Remote Devs? How to be GDPR Compliant
 As the demand for high-quality software engineers increases, employers hiring remotely will find themselves ahead of the competition. This is because hiring remotely allows employers and startup founders to expand their talent pool and hire the best candidate no matter where they live. It also leads to reducing costs and improving employees’ productivity and retention.
As the demand for high-quality software engineers increases, employers hiring remotely will find themselves ahead of the competition. This is because hiring remotely allows employers and startup founders to expand their talent pool and hire the best candidate no matter where they live. It also leads to reducing costs and improving employees’ productivity and retention.
30. Exploring Ethical User Data with Datawallet’s New SDK
 On July 8, the Information Commissioner’s Office (ICO) announced the highest GDPR fine ever of £183 million over last year’s data breach at British Airways. The UK’s data watchdog elected to fine the airline as its “poor security arrangements” led to the breach of credit card information, names, addresses, travel booking details, and logins of around 500,000 customers. In recent years, consumers have become wearily accustomed to data breaches of this magnitude.
On July 8, the Information Commissioner’s Office (ICO) announced the highest GDPR fine ever of £183 million over last year’s data breach at British Airways. The UK’s data watchdog elected to fine the airline as its “poor security arrangements” led to the breach of credit card information, names, addresses, travel booking details, and logins of around 500,000 customers. In recent years, consumers have become wearily accustomed to data breaches of this magnitude.
31. 5 Reasons Why Privacy by Design is More Critical Than Ever in 2023
 The more manual work is involved in managing data privacy, the greater the risk of costly data and compliance breaches.
The more manual work is involved in managing data privacy, the greater the risk of costly data and compliance breaches.
32. Cloud Compliance And Regulation Resources
 Customers and Cloud Service Provider (CSP) share the responsibility of security and compliance. Thus, the organization would have the freedom to have architect their security and compliance needs, according to the services they utilize from the CSP and the services they intend to achieve. CSP has the responsibility to provide services securely and to provide physical security of the cloud. If, however, a customer opts for Software-as-a-service, then the CSP provides standard compliance. Still, the organization has to check if it meets its regulations and compliance levels to strive to achieve. All Cloud services (such ad different forms of databases) are not created equal. Policies and procedures should be agreed upon between CSP and client for all security requirements and operations responsibility.
Customers and Cloud Service Provider (CSP) share the responsibility of security and compliance. Thus, the organization would have the freedom to have architect their security and compliance needs, according to the services they utilize from the CSP and the services they intend to achieve. CSP has the responsibility to provide services securely and to provide physical security of the cloud. If, however, a customer opts for Software-as-a-service, then the CSP provides standard compliance. Still, the organization has to check if it meets its regulations and compliance levels to strive to achieve. All Cloud services (such ad different forms of databases) are not created equal. Policies and procedures should be agreed upon between CSP and client for all security requirements and operations responsibility.
33. Why Should Websites Adopt Passwordless Authentication?
 Brands have started to shift away from the old, password-centric world. While it sounds like a bad idea, there are some benefits to this change to passwords.
Brands have started to shift away from the old, password-centric world. While it sounds like a bad idea, there are some benefits to this change to passwords.
34. Conquer GDPR Article 32: Locking Down Data Segregation and Identity-Based Access
 Understand the importance and tools of implementation for data segregation through access control GDPR compliance to address Article 32.
Understand the importance and tools of implementation for data segregation through access control GDPR compliance to address Article 32.
35. 8 Cloud Compliance Frameworks and Why Cloud-based Organizations Need Them
 Cloud compliance frameworks help an organization to keep its database secure and private. In this article, you will eight such frameworks that can guide you.
Cloud compliance frameworks help an organization to keep its database secure and private. In this article, you will eight such frameworks that can guide you.
36. Identity Management Unchained - Taking the Metaverse Red Pill

37. What the GDPR and California Privacy Act Means for Tech Companies
 You may not know it, but companies are using your data as a commodity. For decades, all of your online habits have been stored, bought, shared, transferred, and maybe even stolen by businesses and individuals.
You may not know it, but companies are using your data as a commodity. For decades, all of your online habits have been stored, bought, shared, transferred, and maybe even stolen by businesses and individuals.
38. How to Ensure your SaaS is Compliant - For Developers
 This article reviews what kinds of compliance certifications and regulations exist, what they mean for developers, and how to begin the certification process.
This article reviews what kinds of compliance certifications and regulations exist, what they mean for developers, and how to begin the certification process.
39. Time Travel Through 2010s Technology: Part 2
 In the first part of the series “Time travel through 2010s technology” we looked at how operating systems, phones, tablets, smartwatches and smartglasses changed through the last decade. The 2010s changed how we interact with technology, but more importantly, how we think about the impact it has in our lives.
In the first part of the series “Time travel through 2010s technology” we looked at how operating systems, phones, tablets, smartwatches and smartglasses changed through the last decade. The 2010s changed how we interact with technology, but more importantly, how we think about the impact it has in our lives.
40. We Need To Build A Human-Centered Future Because Regulations Alone Aren't Enough
 Emerging data privacy regulations, such as the General Data Protection Regulation (GDPR) in Europe and California Consumer Privacy Act (CCPA) in the USA, have sparked global discussion around:
Emerging data privacy regulations, such as the General Data Protection Regulation (GDPR) in Europe and California Consumer Privacy Act (CCPA) in the USA, have sparked global discussion around:
41. Blockchaining the Internet of Identity
 In May 2018, the most far-reaching legislation for the protection of personal data ever conceived took effect: The European Union's General Data Protection Regulation (GDPR).
In May 2018, the most far-reaching legislation for the protection of personal data ever conceived took effect: The European Union's General Data Protection Regulation (GDPR).
42. Identity and Blockchain’s Digital Vending Machines
 In a previous article, we outlined investment opportunities in companies utilizing decentralized software solutions such as blockchains.
In a previous article, we outlined investment opportunities in companies utilizing decentralized software solutions such as blockchains.
43. Issues With Private Data and Confidentiality in Hyperledger Fabric [Deep Dive]
 In many blockchain platforms such as Ethereum and Bitcoin, data confidentiality is a kind of excluded item in their blockchain framework. In these distributed blockchain platform transactions are executed in every participant node in the network. So, every transaction in the network can be visible to all the peers. The ledger update process through all the endorsed peers and has to reach an agreement among all before it committed successfully to the ledger. So, in this scenario creating a private record and comprises within a certain group of participants in the network is a complete “No”.
In many blockchain platforms such as Ethereum and Bitcoin, data confidentiality is a kind of excluded item in their blockchain framework. In these distributed blockchain platform transactions are executed in every participant node in the network. So, every transaction in the network can be visible to all the peers. The ledger update process through all the endorsed peers and has to reach an agreement among all before it committed successfully to the ledger. So, in this scenario creating a private record and comprises within a certain group of participants in the network is a complete “No”.
44. A Marketer's Guide to GDPR
 In God we trust, all others must bring data – W. Edwards Deming
In God we trust, all others must bring data – W. Edwards Deming
Thank you for checking out the 44 most read stories about Gdpr on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

