Let's learn about Mozilla via these 90 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
1. Mozilla Spring MVP Lab
 TLDR: Apply to be a part of the Mozilla Spring MVP Lab at mozilla.org/builders
TLDR: Apply to be a part of the Mozilla Spring MVP Lab at mozilla.org/builders
2. Glossary of Security Terms: Cross-Site Scripting
 Cross-site scripting (XSS) is a security exploit which allows an attacker to inject into a website malicious client-side code. This code is executed by the victims and lets the attackers bypass access controls and impersonate users. According to the Open Web Application Security Project, XSS was the seventh most common Web app vulnerability in 2017.
Cross-site scripting (XSS) is a security exploit which allows an attacker to inject into a website malicious client-side code. This code is executed by the victims and lets the attackers bypass access controls and impersonate users. According to the Open Web Application Security Project, XSS was the seventh most common Web app vulnerability in 2017.
3. Mozilla Summer Startup Studio and MVP Lab
 TLDR: See mozilla.org/builders for more details regarding our summer programs!
TLDR: See mozilla.org/builders for more details regarding our summer programs!
4. WebAssembly and Fine-Grained Sandboxing in Firefox 95
 RLBox is a technology that makes it easy and efficient to isolate subcomponents to make the browser more secure.
RLBox is a technology that makes it easy and efficient to isolate subcomponents to make the browser more secure.
5. An Introduction to Firefox’s new Site Isolation Security Architecture
 Without Site Isolation, Firefox might load a malicious site in the same process as a site that is handling sensitive information.
Without Site Isolation, Firefox might load a malicious site in the same process as a site that is handling sensitive information.
6. Why Developers Are Buzzing About Mozilla’s Fix-The-Internet Incubator
 I've seen software developers in dozens of Slack channels, Telegram groups, and Discord servers pass this image around about Mozilla's Fix-The-Internet Incubator.
I've seen software developers in dozens of Slack channels, Telegram groups, and Discord servers pass this image around about Mozilla's Fix-The-Internet Incubator.
[7. Our GitHub Org. qxresearch Got 2k+
Views in 3 Days](https://hackernoon.com/our-github-org-qxresearch-got-2k-views-in-3-days-dn1y3tw1)
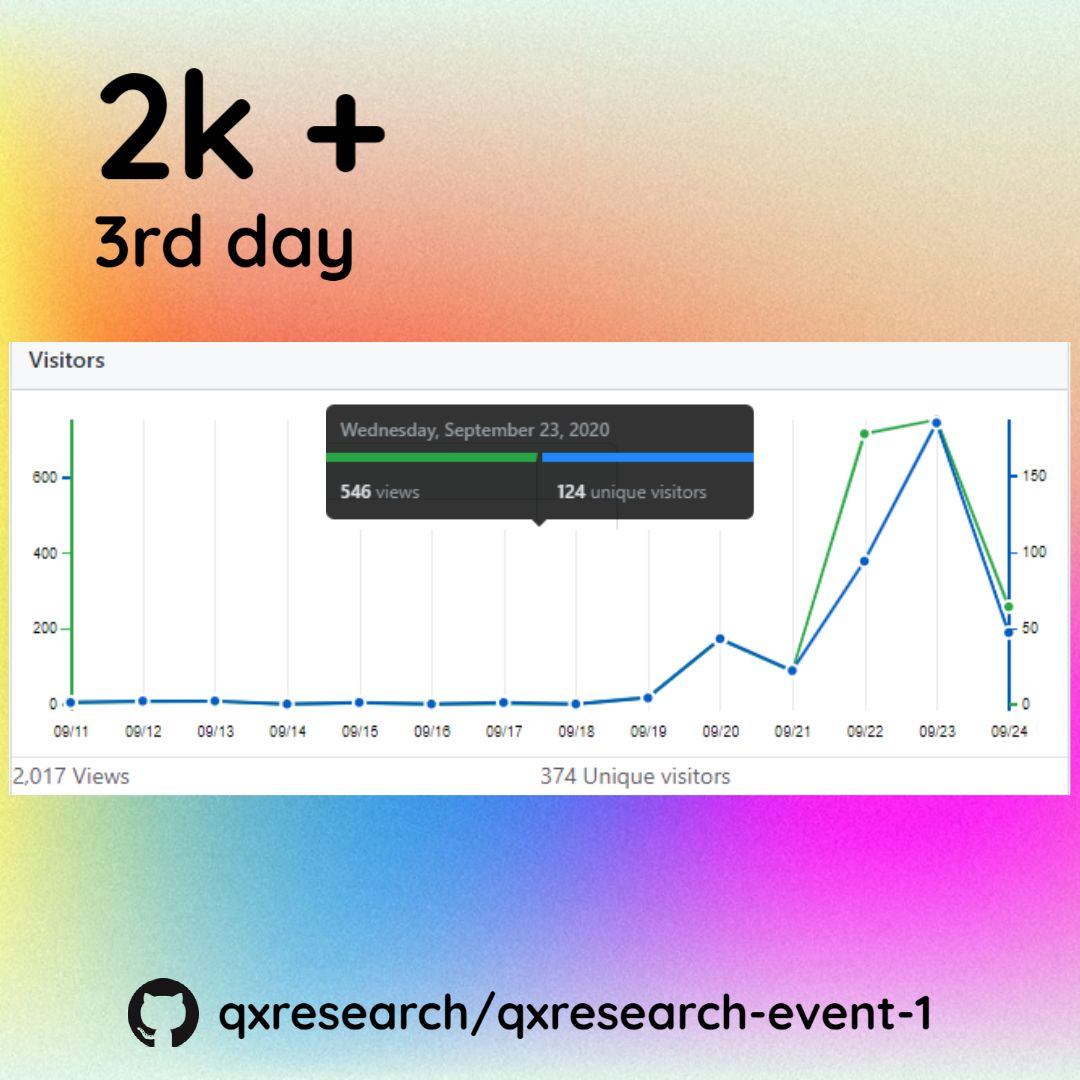 I've created a GitHub Organization named qxresearch which is officially part of Mozilla Campus Club. In this club, members get a chance to develop their own projects with us and contribute to our projects. Being the lead of the club I've arranged a event on 10-projects-10-Lines-of-Code.
I've created a GitHub Organization named qxresearch which is officially part of Mozilla Campus Club. In this club, members get a chance to develop their own projects with us and contribute to our projects. Being the lead of the club I've arranged a event on 10-projects-10-Lines-of-Code.
The aim the event was to prove that we can built something really cool with the programming knowledge we've. It won't take thousands of lines of code to make GUI based python app.
I made a tutorial video explaining how the code works and how we can use those to solve real-life problems.
8. Navigation Timing API: How to Track Your Website Loading Performance
 The Navigation Timing API provides data that can be used to measure the performance of a web site. Unlike JavaScript-based libraries that have historically been used to collect similar information, the Navigation Timing API can be much more accurate and reliable.
The Navigation Timing API provides data that can be used to measure the performance of a web site. Unlike JavaScript-based libraries that have historically been used to collect similar information, the Navigation Timing API can be much more accurate and reliable.
9. A Quick Introduction to the Resize Observer API
 The Resize Observer API provides a performant mechanism by which code can monitor an element for changes to its size, with notifications being delivered to the observer each time the size changes.
The Resize Observer API provides a performant mechanism by which code can monitor an element for changes to its size, with notifications being delivered to the observer each time the size changes.
10. Network Information API: How to Access Network Connection Speed Info
 This is an experimental technology
Check the Browser compatibility table carefully before using this in production.
This is an experimental technology
Check the Browser compatibility table carefully before using this in production.
11. Web Crypto API: A Low-Level Interface for Internet Security
 The Web Crypto API is an interface allowing a script to use cryptographic primitives in order to build systems using cryptography.
The Web Crypto API is an interface allowing a script to use cryptographic primitives in order to build systems using cryptography.
12. Second State Releases Scalable Privacy Service at Mozilla Open Labs
 Build a scalable and privacy-first Internet on Second State’s serverless infrastructure. Get the email newsletter on Rust, WebAssembly, serverless, blockchain, and AI.
Build a scalable and privacy-first Internet on Second State’s serverless infrastructure. Get the email newsletter on Rust, WebAssembly, serverless, blockchain, and AI.
13. Using HTTPS to Render Blocked Mixed Content on a Website
 Starting with Firefox 23, Firefox blocks active mixed content by default. This follows a practice adopted by Internet Explorer (since version 9) and Chrome.
Starting with Firefox 23, Firefox blocks active mixed content by default. This follows a practice adopted by Internet Explorer (since version 9) and Chrome.
14. Push API Guide: How to Send Push Message to Application
 The Push API gives web applications the ability to receive messages pushed to them from a server, whether or not the web app is in the foreground, or even currently loaded, on a user agent. This lets developers deliver asynchronous notifications and updates to users that opt in, resulting in better engagement with timely new content.
The Push API gives web applications the ability to receive messages pushed to them from a server, whether or not the web app is in the foreground, or even currently loaded, on a user agent. This lets developers deliver asynchronous notifications and updates to users that opt in, resulting in better engagement with timely new content.
15. Proximity Events Specification: How To Receive Events From Device Proximity Sensors
 This is an experimental technology
Check the Browser compatibility table carefully before using this in production.
This is an experimental technology
Check the Browser compatibility table carefully before using this in production.
16. The History of Web Developers Tied to Browser Development
 Explore the emergence of web developers and the impact of browsers on their evolution. Learn how collaboration among developers advanced browser development.
Explore the emergence of web developers and the impact of browsers on their evolution. Learn how collaboration among developers advanced browser development.
17. Introduction to the Web Notifications API Standard
 Note: This feature is available in Web Workers.
Note: This feature is available in Web Workers.
18. Linh Dao Smooke & David Smooke repping Hacker Noon at the Mozilla Fix the Internet Showcase
 I joined a panel with awesome fellow founders and builders of Mozilla to discuss the future of "citizen publishing" as a way to democratize the internet.
I joined a panel with awesome fellow founders and builders of Mozilla to discuss the future of "citizen publishing" as a way to democratize the internet.
19. Styling HTML Using CSS: A Beginner's Guide
 Cascading Stylesheets — or CSS — is the first technology you should start learning after HTML. While HTML is used to define the structure and semantics of your content, CSS is used to style it and lay it out. For example, you can use CSS to alter the font, color, size, and spacing of your content, split it into multiple columns, or add animations and other decorative features.
Cascading Stylesheets — or CSS — is the first technology you should start learning after HTML. While HTML is used to define the structure and semantics of your content, CSS is used to style it and lay it out. For example, you can use CSS to alter the font, color, size, and spacing of your content, split it into multiple columns, or add animations and other decorative features.
20. An Interview with Seyi Akiwowo, Founder of Glitch - an Organization that Seeks to end Online Abuse
 Akiwowo is the founder of Glitch, an organization that seeks to end online abuse.
Akiwowo is the founder of Glitch, an organization that seeks to end online abuse.
21. Web Animations API Explained
 The Web Animations API allows for synchronizing and timing changes to the presentation of a Web page, i.e. animation of DOM elements. It does so by combining two models: the Timing Model and the Animation Model.
The Web Animations API allows for synchronizing and timing changes to the presentation of a Web page, i.e. animation of DOM elements. It does so by combining two models: the Timing Model and the Animation Model.
22. Glossary of Security Terms: Cryptographic Hash Function
 A cryptographic hash function, also sometimes called a digest function, is a cryptographic primitive transforming a message of arbitrary size into a message of fixed size, called a digest. Cryptographic hash functions are used for authentication, digital signatures, and message authentication codes.
A cryptographic hash function, also sometimes called a digest function, is a cryptographic primitive transforming a message of arbitrary size into a message of fixed size, called a digest. Cryptographic hash functions are used for authentication, digital signatures, and message authentication codes.
23. Glossary of Security Terms: Cryptography
 Cryptography, or cryptology, is the science that studies how to encode and transmit messages securely. Cryptography designs and studies algorithms used to encode and decode messages in an insecure environment, and their applications.
Cryptography, or cryptology, is the science that studies how to encode and transmit messages securely. Cryptography designs and studies algorithms used to encode and decode messages in an insecure environment, and their applications.
24. Glossary of Security Terms: OWASP
 OWASP (Open Web Application Security Project) is a non-profit organization and worldwide network that works for security in Free Software, especially on the Web.
OWASP (Open Web Application Security Project) is a non-profit organization and worldwide network that works for security in Free Software, especially on the Web.
25. Glossary of Security Terms: Cipher Suite
 A cipher suite is a combination of a key exchange algorithm, authentication method, bulk encryption cipher, and message authentication code.
A cipher suite is a combination of a key exchange algorithm, authentication method, bulk encryption cipher, and message authentication code.
26. Hacker Noon Joins Mozilla’s Fix The Internet Incubator
 The internet functions, but does it work?
The internet functions, but does it work?
27. Glossary of Security Terms: Session Hijacking
 Session hijacking occurs when an attacker takes over a valid session between two computers. The attacker steals a valid session ID in order to break into the system and snoop data.
Session hijacking occurs when an attacker takes over a valid session between two computers. The attacker steals a valid session ID in order to break into the system and snoop data.
28. Glossary of Security Terms: Block Cipher Mode of Operation
 A block cipher mode of operation, usually just called a "mode" in context, specifies how a block cipher should be used to encrypt or decrypt messages that are longer than the block size.
A block cipher mode of operation, usually just called a "mode" in context, specifies how a block cipher should be used to encrypt or decrypt messages that are longer than the block size.
29. HTTP Redirections: Principles, Types and Use Cases
 URL redirection, also known as URL forwarding, is a technique to give more than one URL address to a page, a form, or a whole Web site/application. HTTP has a special kind of response, called a HTTP redirect, for this operation.
URL redirection, also known as URL forwarding, is a technique to give more than one URL address to a page, a form, or a whole Web site/application. HTTP has a special kind of response, called a HTTP redirect, for this operation.
30. Glossary of Security Terms: SQL Injection
 SQL injection takes advantage of Web apps that fail to validate user input. Hackers can maliciously pass SQL commands through the Web app for execution by a backend database.
SQL injection takes advantage of Web apps that fail to validate user input. Hackers can maliciously pass SQL commands through the Web app for execution by a backend database.
31. Glossary of Security Terms: Preflight Request
 A CORS preflight request is a CORS request that checks to see if the CORS protocol is understood and a server is aware using specific methods and headers.
A CORS preflight request is a CORS request that checks to see if the CORS protocol is understood and a server is aware using specific methods and headers.
32. Glossary of Security Terms: Challenge-Response Authentication
 In security protocols, a challenge is some data sent to the client by the server in order to generate a different response each time. Challenge-response protocols are one way to fight against replay attacks where an attacker listens to the previous messages and resends them at a later time to get the same credentials as the original message.
In security protocols, a challenge is some data sent to the client by the server in order to generate a different response each time. Challenge-response protocols are one way to fight against replay attacks where an attacker listens to the previous messages and resends them at a later time to get the same credentials as the original message.
33. Hacker Noon Joins Mozilla’s Fix The Internet Initiative
 The internet functions, but does it work?
The internet functions, but does it work?
34. Glossary of Security Terms: Hash
 The hash function takes a variable length message input and produces a fixed-length hash output. It is commonly in the form of a 128-bit "fingerprint" or "message digest". Hashes are very useful for cryptography — they insure the integrity of transmitted data. This provides the basis for HMAC's, which provide message authentication.
The hash function takes a variable length message input and produces a fixed-length hash output. It is commonly in the form of a 128-bit "fingerprint" or "message digest". Hashes are very useful for cryptography — they insure the integrity of transmitted data. This provides the basis for HMAC's, which provide message authentication.
35. An Overview of HTTP and How It Works
 HTTP is a protocol which allows the fetching of resources, such as HTML documents. It is the foundation of any data exchange on the Web and it is a client-server protocol, which means requests are initiated by the recipient, usually the Web browser. A complete document is reconstructed from the different sub-documents fetched, for instance text, layout description, images, videos, scripts, and more.
HTTP is a protocol which allows the fetching of resources, such as HTML documents. It is the foundation of any data exchange on the Web and it is a client-server protocol, which means requests are initiated by the recipient, usually the Web browser. A complete document is reconstructed from the different sub-documents fetched, for instance text, layout description, images, videos, scripts, and more.
36. Understanding Memory Management in JavaScript
 Low-level languages like C, have manual memory management primitives such as malloc() and free(). In contrast, JavaScript automatically allocates memory when objects are created and frees it when they are not used anymore (garbage collection). This automaticity is a potential source of confusion: it can give developers the false impression that they don't need to worry about memory management.
Low-level languages like C, have manual memory management primitives such as malloc() and free(). In contrast, JavaScript automatically allocates memory when objects are created and frees it when they are not used anymore (garbage collection). This automaticity is a potential source of confusion: it can give developers the false impression that they don't need to worry about memory management.
37. Page Visibility API: Learn How to Use Browser-Based Visibility Interface
 With tabbed browsing, there is a reasonable chance that any given webpage is in the background and thus not visible to the user. The Page Visibility API provides events you can watch for to know when a document becomes visible or hidden, as well as features to look at the current visibility state of the page.
With tabbed browsing, there is a reasonable chance that any given webpage is in the background and thus not visible to the user. The Page Visibility API provides events you can watch for to know when a document becomes visible or hidden, as well as features to look at the current visibility state of the page.
38. Nine Essential Privacy Settings and Add-ons for Mozilla Firefox

39. Glossary of Security Terms: CORS
 CORS (Cross-Origin Resource Sharing) is a system, consisting of transmitting HTTP headers, that determines whether browsers block frontend JavaScript code from accessing responses for cross-origin requests.
CORS (Cross-Origin Resource Sharing) is a system, consisting of transmitting HTTP headers, that determines whether browsers block frontend JavaScript code from accessing responses for cross-origin requests.
40. Glossary of Security Terms: HMAC
 HMAC is a protocol used for cryptographically authenticating messages. It can use any kind of cryptographic functions, and its strengh depends on the underlying function (SHA1 or MD5 for instance), and the chosen secret key. With such a combination, the HMAC verification algorithm is then known with a compound name such as HMAC-SHA1.
HMAC is a protocol used for cryptographically authenticating messages. It can use any kind of cryptographic functions, and its strengh depends on the underlying function (SHA1 or MD5 for instance), and the chosen secret key. With such a combination, the HMAC verification algorithm is then known with a compound name such as HMAC-SHA1.
41. Glossary of Security Terms: Symmetric-Key Cryptography
 Symmetric-key cryptography is a term used for cryptographic algorithms that use the same key for encryption and for decryption. The key is usually called a "symmetric key" or a "secret key".
Symmetric-key cryptography is a term used for cryptographic algorithms that use the same key for encryption and for decryption. The key is usually called a "symmetric key" or a "secret key".
42. Glossary of Security Terms: Transport Layer Security
 Transport Layer Security (TLS), formerly known as Secure Sockets Layer (SSL), is a protocol used by applications to communicate securely across a network, preventing tampering with and eavesdropping on email, web browsing, messaging, and other protocols. Both SSL and TLS are client / server protocols that ensure communication privacy by using cryptographic protocols to provide security over a network. When a server and client communicate using TLS, it ensures that no third party can eavesdrop or tamper with any message.
Transport Layer Security (TLS), formerly known as Secure Sockets Layer (SSL), is a protocol used by applications to communicate securely across a network, preventing tampering with and eavesdropping on email, web browsing, messaging, and other protocols. Both SSL and TLS are client / server protocols that ensure communication privacy by using cryptographic protocols to provide security over a network. When a server and client communicate using TLS, it ensures that no third party can eavesdrop or tamper with any message.
43. Introduction to Web Workers API in JavaScript
 Web Workers makes it possible to run a script operation in a background thread separate from the main execution thread of a web application. The advantage of this is that laborious processing can be performed in a separate thread, allowing the main (usually the UI) thread to run without being blocked/slowed down.
Web Workers makes it possible to run a script operation in a background thread separate from the main execution thread of a web application. The advantage of this is that laborious processing can be performed in a separate thread, allowing the main (usually the UI) thread to run without being blocked/slowed down.
44. Glossary of Security Terms: Decryption
 In cryptography, decryption is the conversion of ciphertext into cleartext.
In cryptography, decryption is the conversion of ciphertext into cleartext.
45. Pointer Lock API: How to Control Mouse Cursor
 The Pointer Lock API (formerly called Mouse Lock API) provides input methods based on the movement of the mouse over time (i.e., deltas), not just the absolute position of the mouse cursor in the viewport. It gives you access to raw mouse movement, locks the target of mouse events to a single element, eliminates limits on how far mouse movement can go in a single direction, and removes the cursor from view. It is ideal for first person 3D games, for example.
The Pointer Lock API (formerly called Mouse Lock API) provides input methods based on the movement of the mouse over time (i.e., deltas), not just the absolute position of the mouse cursor in the viewport. It gives you access to raw mouse movement, locks the target of mouse events to a single element, eliminates limits on how far mouse movement can go in a single direction, and removes the cursor from view. It is ideal for first person 3D games, for example.
46. How to use Javascript's Performance API and measure page performance
 The High Resolution Time standard defines a Performance interface that supports client-side latency measurements within applications. The Performance interfaces are considered high resolution because they are accurate to a thousandth of a millisecond (subject to hardware or software constraints). The interfaces support a number of use cases including calculating frame-rates (potentially important in animations) and benchmarking (such as the time to load a resource).
The High Resolution Time standard defines a Performance interface that supports client-side latency measurements within applications. The Performance interfaces are considered high resolution because they are accurate to a thousandth of a millisecond (subject to hardware or software constraints). The interfaces support a number of use cases including calculating frame-rates (potentially important in animations) and benchmarking (such as the time to load a resource).
47. Glossary of Security Terms: CORS-Safelisted Response Header
 A CORS-safelisted response header is an HTTP header which has been safelisted so that it will not be filtered when responses are processed by CORS, since they're considered safe (as the headers listed in Access-Control-Expose-Headers). By default, the safelist includes the following response headers:
A CORS-safelisted response header is an HTTP header which has been safelisted so that it will not be filtered when responses are processed by CORS, since they're considered safe (as the headers listed in Access-Control-Expose-Headers). By default, the safelist includes the following response headers:
48. Payment Request API Specification
 Secure context
This feature is available only in secure contexts (HTTPS), in some or all supporting browsers.
Secure context
This feature is available only in secure contexts (HTTPS), in some or all supporting browsers.
49. JavaScript Concurrency Models: The Event Loop
 JavaScript has a concurrency model based on an event loop, which is responsible for executing the code, collecting and processing events, and executing queued sub-tasks.
JavaScript has a concurrency model based on an event loop, which is responsible for executing the code, collecting and processing events, and executing queued sub-tasks.
50. Web API: Permissions API Documentation
 The Permissions API provides a consistent programmatic way to query the status of API permissions attributed to the current context. For example, the Permissions API can be used to determine if permission to access a particular API has been granted or denied.
The Permissions API provides a consistent programmatic way to query the status of API permissions attributed to the current context. For example, the Permissions API can be used to determine if permission to access a particular API has been granted or denied.
51. Glossary of Security Terms: Cipher
 In cryptography, a cipher is an algorithm that can encode cleartext to make it unreadable, and to decode it back.
In cryptography, a cipher is an algorithm that can encode cleartext to make it unreadable, and to decode it back.
52. Glossary of Security Terms: Datagram Transport Layer Security
 Datagram Transport Layer Security (DTLS) is a protocol used to secure datagram-based communications. It's based on the stream-focused Transport Layer Security (TLS), providing a similar level of security. As a datagram protocol, DTLS doesn't guarantee the order of message delivery, or even that messages will be delivered at all. However, DTLS gains the benefits of datagram protocols, too; in particular, the lower overhead and reduced latency.
Datagram Transport Layer Security (DTLS) is a protocol used to secure datagram-based communications. It's based on the stream-focused Transport Layer Security (TLS), providing a similar level of security. As a datagram protocol, DTLS doesn't guarantee the order of message delivery, or even that messages will be delivered at all. However, DTLS gains the benefits of datagram protocols, too; in particular, the lower overhead and reduced latency.
53. Glossary of Security Terms: CSP
 A CSP (Content Security Policy) is used to detect and mitigate certain types of website related attacks like XSS and data injections.
A CSP (Content Security Policy) is used to detect and mitigate certain types of website related attacks like XSS and data injections.
54. Glossary of Security Terms: Digital Сertificate
 A digital certificate is a data file that binds a publicly known cryptographic key to an organization. A digital certificate contains information about an organization, such as the common name (e.g., mozilla.org), the organization unit (e.g., Mozilla Corporation), and the location (e.g., Mountain View).
A digital certificate is a data file that binds a publicly known cryptographic key to an organization. A digital certificate contains information about an organization, such as the common name (e.g., mozilla.org), the organization unit (e.g., Mozilla Corporation), and the location (e.g., Mountain View).
55. Glossary of Security Terms: Same-Origin Policy
 The same-origin policy is a critical security mechanism that restricts how a document or script loaded from one origin can interact with a resource from another origin. It helps isolate potentially malicious documents, reducing possible attack vectors.
The same-origin policy is a critical security mechanism that restricts how a document or script loaded from one origin can interact with a resource from another origin. It helps isolate potentially malicious documents, reducing possible attack vectors.
56. How to Store Data in The Browser using Web Storage API
 The Web Storage API provides mechanisms by which browsers can store key/value pairs, in a much more intuitive fashion than using cookies.
The Web Storage API provides mechanisms by which browsers can store key/value pairs, in a much more intuitive fashion than using cookies.
57. Glossary of Security Terms: Public-key Cryptography
 Public-key cryptography — or asymmetric cryptography — is a cryptographic system in which keys come in pairs. The transformation performed by one of the keys can only be undone with the other key. One key (the private key) is kept secret while the other is made public.
Public-key cryptography — or asymmetric cryptography — is a cryptographic system in which keys come in pairs. The transformation performed by one of the keys can only be undone with the other key. One key (the private key) is kept secret while the other is made public.
58. Glossary of Security Terms: Cryptanalysis
 Cryptanalysis is the branch of cryptography that studies how to break codes and cryptosystems. Cryptanalysis creates techniques to break ciphers, in particular by methods more efficient than a brute-force search. In addition to traditional methods like frequency analysis and index of coincidence, cryptanalysis includes more recent methods, like linear cryptanalysis or differential cryptanalysis, that can break more advanced ciphers.
Cryptanalysis is the branch of cryptography that studies how to break codes and cryptosystems. Cryptanalysis creates techniques to break ciphers, in particular by methods more efficient than a brute-force search. In addition to traditional methods like frequency analysis and index of coincidence, cryptanalysis includes more recent methods, like linear cryptanalysis or differential cryptanalysis, that can break more advanced ciphers.
59. Glossary of Security Terms: Encryption
 In cryptography, encryption is the conversion of cleartext into a coded text or ciphertext. A ciphertext is intended to be unreadable by unauthorized readers.
In cryptography, encryption is the conversion of cleartext into a coded text or ciphertext. A ciphertext is intended to be unreadable by unauthorized readers.
60. Glossary of Security Terms: HPKP
 HTTP Public Key Pinning (HPKP) is a security feature that tells a web client to associate a specific cryptographic public key with a certain web server to decrease the risk of MITM attacks with forged certificates.
HTTP Public Key Pinning (HPKP) is a security feature that tells a web client to associate a specific cryptographic public key with a certain web server to decrease the risk of MITM attacks with forged certificates.
61. Glossary of Security Terms: Key
 A key is a piece of information used by a cipher for encryption and/or decryption. Encrypted messages should remain secure even if everything about the cryptosystem, except for the key, is public knowledge.
A key is a piece of information used by a cipher for encryption and/or decryption. Encrypted messages should remain secure even if everything about the cryptosystem, except for the key, is public knowledge.
62. HTTP Compression Optimization: How to Improve Transfer Speed and Bandwidth Utilization
 Compression is an important way to increase the performance of a Web site. For some documents, size reduction of up to 70% lowers the bandwidth capacity needs. Over the years, algorithms also got more efficient, and new ones are supported by clients and servers.
Compression is an important way to increase the performance of a Web site. For some documents, size reduction of up to 70% lowers the bandwidth capacity needs. Over the years, algorithms also got more efficient, and new ones are supported by clients and servers.
63. Glossary of Security Terms: TOFU
 Trust On First Use (TOFU) is a security model in which a client needs to create a trust relationship with an unknown server. To do that, clients will look for identifiers (for example public keys) stored locally. If an identifier
is found, the client can establish the connection. If no identifier is found, the client can prompt the user to determine if the client should trust the identifier.
Trust On First Use (TOFU) is a security model in which a client needs to create a trust relationship with an unknown server. To do that, clients will look for identifiers (for example public keys) stored locally. If an identifier
is found, the client can establish the connection. If no identifier is found, the client can prompt the user to determine if the client should trust the identifier.
64. Glossary of Security Terms: Robots.txt
 Robots.txt is a file which is usually placed in the root of any website. It decides whether crawlers are permitted or forbidden access to the web site.
Robots.txt is a file which is usually placed in the root of any website. It decides whether crawlers are permitted or forbidden access to the web site.
65. How the autocomplete search in the Mozilla Documentation Works
 Last month, Gregor Weber and I added an autocomplete search to MDN Web Docs, that allows you to quickly jump straight to the document you want.
Last month, Gregor Weber and I added an autocomplete search to MDN Web Docs, that allows you to quickly jump straight to the document you want.
66. Glossary of Security Terms: Ciphertext
 In cryptography, a ciphertext is a scrambled message that conveys information but is not legible unless decrypted with the right cipher and the right secret (usually a key), reproducing the original cleartext. A ciphertext's security, and therefore the secrecy of the contained information, depends on using a secure cipher and keeping the key secret.
In cryptography, a ciphertext is a scrambled message that conveys information but is not legible unless decrypted with the right cipher and the right secret (usually a key), reproducing the original cleartext. A ciphertext's security, and therefore the secrecy of the contained information, depends on using a secure cipher and keeping the key secret.
67. Understanding Prototype Chain And Inheritance in JavaScript
 JavaScript is a bit confusing for developers experienced in class-based languages (like Java or C++), as it is dynamic and does not provide a class implementation per se (the class keyword is introduced in ES2015, but is syntactical sugar, JavaScript remains prototype-based).
JavaScript is a bit confusing for developers experienced in class-based languages (like Java or C++), as it is dynamic and does not provide a class implementation per se (the class keyword is introduced in ES2015, but is syntactical sugar, JavaScript remains prototype-based).
68. Glossary of Security Terms: Forbidden Response Header Name
 A forbidden response header name is an HTTP header name (either
A forbidden response header name is an HTTP header name (either Set-Cookie or Set-Cookie2) that cannot be modified programmatically.
69. Glossary of Security Terms: CORS-Safelisted Request Header
 A CORS-safelisted request header is one of the following HTTP headers:
A CORS-safelisted request header is one of the following HTTP headers:
70. Web Fundamentals: WebVR API
 Deprecated
This feature is no longer recommended. Though some browsers might still support it, it may have already been removed from the relevant web standards, may be in the process of being dropped, or may only be kept for compatibility purposes. Avoid using it, and update existing code if possible; see the compatibility table at the bottom of this page to guide your decision. Be aware that this feature may cease to work at any time.
Deprecated
This feature is no longer recommended. Though some browsers might still support it, it may have already been removed from the relevant web standards, may be in the process of being dropped, or may only be kept for compatibility purposes. Avoid using it, and update existing code if possible; see the compatibility table at the bottom of this page to guide your decision. Be aware that this feature may cease to work at any time.
71. HTML5 Websockets API Introduction and Tools
 The WebSocket API is an advanced technology that makes it possible to open a two-way interactive communication session between the user's browser and a server. With this API, you can send messages to a server and receive event-driven responses without having to poll the server for a reply.
The WebSocket API is an advanced technology that makes it possible to open a two-way interactive communication session between the user's browser and a server. With this API, you can send messages to a server and receive event-driven responses without having to poll the server for a reply.
72. Javascript Methods from Performance Timeline API
 The Performance Timeline API defines extensions to the Performance interface to support client-side latency measurements within applications. The extensions provide interfaces to retrieve performance entry metrics based on specific filter criteria. The standard also includes interfaces that allow an application to define performance observer callbacks that are notified when specific performance events are added to the browser's performance timeline.
The Performance Timeline API defines extensions to the Performance interface to support client-side latency measurements within applications. The extensions provide interfaces to retrieve performance entry metrics based on specific filter criteria. The standard also includes interfaces that allow an application to define performance observer callbacks that are notified when specific performance events are added to the browser's performance timeline.
73. How Does HTTP Authentication Work
 HTTP provides a general framework for access control and authentication. The most common HTTP authentication is based on the
"Basic" schema. This page shows an introduction to the HTTP framework
for authentication and shows how to restrict access to your server using the HTTP "Basic" schema.
HTTP provides a general framework for access control and authentication. The most common HTTP authentication is based on the
"Basic" schema. This page shows an introduction to the HTTP framework
for authentication and shows how to restrict access to your server using the HTTP "Basic" schema.
74. Glossary of Security Terms: Certificate Authority
 A certificate authority (CA) is an organization that signs digital certificates and their associated public keys. This certifies that an organization that requested a digital certificate (e.g., Mozilla Corporation) is authorized to request a certificate for the subject named in the certificate (e.g., mozilla.org).
A certificate authority (CA) is an organization that signs digital certificates and their associated public keys. This certifies that an organization that requested a digital certificate (e.g., Mozilla Corporation) is authorized to request a certificate for the subject named in the certificate (e.g., mozilla.org).
75. WebGL Fundamentals: 2D and 3D Graphics For The Web
 WebGL (Web Graphics Library) is a JavaScript API for rendering high-performance interactive 3D and 2D graphics within any compatible web browser without the use of plug-ins. WebGL does so by introducing an API that closely conforms to OpenGL ES 2.0 that can be used in HTML5 <canvas> elements. This conformance makes it possible for the API to take advantage of hardware graphics acceleration provided by the user's device.
WebGL (Web Graphics Library) is a JavaScript API for rendering high-performance interactive 3D and 2D graphics within any compatible web browser without the use of plug-ins. WebGL does so by introducing an API that closely conforms to OpenGL ES 2.0 that can be used in HTML5 <canvas> elements. This conformance makes it possible for the API to take advantage of hardware graphics acceleration provided by the user's device.
76. Understanding Memory Management in JavaScript
 Low-level languages like C, have manual memory management primitives such as malloc() and free(). In contrast, JavaScript automatically allocates memory when objects are created and frees it when they are not used anymore (garbage collection). This automaticity is a potential source of confusion: it can give developers the false impression that they don't need to worry about memory management.
Low-level languages like C, have manual memory management primitives such as malloc() and free(). In contrast, JavaScript automatically allocates memory when objects are created and frees it when they are not used anymore (garbage collection). This automaticity is a potential source of confusion: it can give developers the false impression that they don't need to worry about memory management.
77. Glossary of Security Terms: Reporting Directive
 CSP reporting directives are used in a Content-Security-Policy header and control the reporting process of CSP violations.
CSP reporting directives are used in a Content-Security-Policy header and control the reporting process of CSP violations.
78. Gradual Development of HTTP Protocol
 HTTP (HyperText Transfer Protocol) is the underlying protocol of the World Wide Web. Developed by Tim Berners-Lee and his team between 1989-1991, HTTP has seen many changes, keeping most of the simplicity and further shaping its flexibility. HTTP has evolved from an early protocol to exchange files in a semi-trusted laboratory environment, to the modern maze of the Internet, now carrying images, videos in high resolution and 3D.
HTTP (HyperText Transfer Protocol) is the underlying protocol of the World Wide Web. Developed by Tim Berners-Lee and his team between 1989-1991, HTTP has seen many changes, keeping most of the simplicity and further shaping its flexibility. HTTP has evolved from an early protocol to exchange files in a semi-trusted laboratory environment, to the modern maze of the Internet, now carrying images, videos in high resolution and 3D.
79. Glossary of Security Terms: HSTS
 HTTP Strict Transport Security lets a web site inform the browser that it should never load the site using HTTP and should automatically convert all attempts to access the site using HTTP to HTTPS requests instead. It consists in one HTTP header, Strict-Transport-Security, sent by the server with the resource.
HTTP Strict Transport Security lets a web site inform the browser that it should never load the site using HTTP and should automatically convert all attempts to access the site using HTTP to HTTPS requests instead. It consists in one HTTP header, Strict-Transport-Security, sent by the server with the resource.
80. Glossary of Security Terms: Forbidden Header Name
 A forbidden header name is the name of any HTTP header that cannot be modified programmatically; specifically, an HTTP request header name (in contrast with a Forbidden response header name).
A forbidden header name is the name of any HTTP header that cannot be modified programmatically; specifically, an HTTP request header name (in contrast with a Forbidden response header name).
81. Glossary of Security Terms: CSRF
 CSRF (Cross-Site Request Forgery) is an attack that impersonates a trusted user and sends a website unwanted commands. This can be done, for example, by including malicious parameters in a URL behind a link that purports to go somewhere else:
CSRF (Cross-Site Request Forgery) is an attack that impersonates a trusted user and sends a website unwanted commands. This can be done, for example, by including malicious parameters in a URL behind a link that purports to go somewhere else:
82. Pointer Events
 Much of today's web content assumes the user's pointing device will be a mouse. However, since many devices support other types of pointing
input devices, such as pen/stylus and touch surfaces, extensions to the
existing pointing device event models are needed. Pointer events address that need.
Much of today's web content assumes the user's pointing device will be a mouse. However, since many devices support other types of pointing
input devices, such as pen/stylus and touch surfaces, extensions to the
existing pointing device event models are needed. Pointer events address that need.
83. Glossary of Security Terms: MitM
 A Man-in-the-middle attack (MitM) intercepts a communication between two systems. For example, a Wi-Fi router can be compromised.
A Man-in-the-middle attack (MitM) intercepts a communication between two systems. For example, a Wi-Fi router can be compromised.
84. Recap: 2020 WebAssembly (Wasm) Summit in Silicon Valley [incl. Links and Resources]
 The WebAssembly Summit was held in Silicon Valley, on the 10th February 2020. The venue, Google’s newest building at 1625 Plymouth St Mountain View CA.
The WebAssembly Summit was held in Silicon Valley, on the 10th February 2020. The venue, Google’s newest building at 1625 Plymouth St Mountain View CA.
85. Getting Started with Web Audio API
 The Web Audio API provides a powerful and versatile system for
controlling audio on the Web, allowing developers to choose audio sources, add effects to audio, create audio visualizations, apply
spatial effects (such as panning) and much more.
The Web Audio API provides a powerful and versatile system for
controlling audio on the Web, allowing developers to choose audio sources, add effects to audio, create audio visualizations, apply
spatial effects (such as panning) and much more.
86. WebXR Device API: Accessing Virtual Reality and Augmented Reality Devices
 Draft
This page is not complete.
Draft
This page is not complete.
87. WebRTC API: Create a Real-time Communication In Browser
 WebRTC (Web Real-Time Communication) is a technology which enables Web applications and sites to capture and optionally stream audio and/or video media, as well as to exchange arbitrary data between browsers without requiring an intermediary. The set of standards that comprise WebRTC makes it possible to share data and perform teleconferencing peer-to-peer, without requiring that the user installs plug-ins or any other
third-party software.
WebRTC (Web Real-Time Communication) is a technology which enables Web applications and sites to capture and optionally stream audio and/or video media, as well as to exchange arbitrary data between browsers without requiring an intermediary. The set of standards that comprise WebRTC makes it possible to share data and perform teleconferencing peer-to-peer, without requiring that the user installs plug-ins or any other
third-party software.
88. Web Auth Standard: Guide to Web Authentication API
 Secure context
This feature is available only in secure contexts (HTTPS), in some or all supporting browsers.
Secure context
This feature is available only in secure contexts (HTTPS), in some or all supporting browsers.
89. Why Do We Need Strict Mode
 JavaScript's strict mode, introduced in ECMAScript 5, is a way to opt in to a restricted variant of JavaScript, thereby implicitly opting-out of "sloppy mode". Strict mode isn't just a subset: it intentionally has different semantics from normal code. Browsers not supporting strict mode will run strict mode code with different behavior from browsers that do, so don't rely on strict mode without feature-testing for support for the relevant aspects of strict mode. Strict mode code and non-strict mode code can coexist, so scripts can opt into strict mode incrementally.
JavaScript's strict mode, introduced in ECMAScript 5, is a way to opt in to a restricted variant of JavaScript, thereby implicitly opting-out of "sloppy mode". Strict mode isn't just a subset: it intentionally has different semantics from normal code. Browsers not supporting strict mode will run strict mode code with different behavior from browsers that do, so don't rely on strict mode without feature-testing for support for the relevant aspects of strict mode. Strict mode code and non-strict mode code can coexist, so scripts can opt into strict mode incrementally.
90. WebVTT API: Introduction to The Web Video Text Tracks Format
 Web Video Text Tracks Format (WebVTT) is a format for displaying timed text tracks (such as subtitles or captions) using the <track> element. The primary purpose of WebVTT files is to add text overlays to a <video>. WebVTT is a text based format, which must be encoded using UTF-8. Where you can use spaces you can also use tabs. There is also a small
API available to represent and manage these tracks and the data needed
to perform the playback of the text at the correct times.
Web Video Text Tracks Format (WebVTT) is a format for displaying timed text tracks (such as subtitles or captions) using the <track> element. The primary purpose of WebVTT files is to add text overlays to a <video>. WebVTT is a text based format, which must be encoded using UTF-8. Where you can use spaces you can also use tabs. There is also a small
API available to represent and manage these tracks and the data needed
to perform the playback of the text at the correct times.
Thank you for checking out the 90 most read stories about Mozilla on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

