Let's learn about Data Breach via these 71 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
1. Top 5 Cloud Data Breaches of Recent Years

2. What Could Go Wrong by Using the Same Password for All Accounts???

3. What Hackers Do With Your Data
 4 ways your data is being used without your knowledge
4 ways your data is being used without your knowledge
4. Unsafe use of target=”_blank”
 Developers have been frequently using this attribute to open a new webpage. But this attribute, though looks pretty simple, can create a major security threat to your application.
Developers have been frequently using this attribute to open a new webpage. But this attribute, though looks pretty simple, can create a major security threat to your application.
5. Analyzing the 12/31/2022 Slack Security Incident
 On December 31, 2022, Slack reported a security breach that affected some of its customers.
On December 31, 2022, Slack reported a security breach that affected some of its customers.
6. Check Point Security Breach: A Leading Cybersecurity Company Has Been Breached
 Check Point, which bills itself as the leader in cybersecurity solutions, has been breached. Data records of over 5k ZoneAlarm forum users have been hacked.
Check Point, which bills itself as the leader in cybersecurity solutions, has been breached. Data records of over 5k ZoneAlarm forum users have been hacked.
7. Data Loss Prevention: What is it, and Do You Need it?
 Data Loss Prevention is a set of tools and practices geared towards protecting your data from loss and leak. Even though the name has only the loss part, in actuality, it's as much about the leak protection as it is about the loss protection. Basically, DLP, as a notion, encompasses all the security practices around protecting your company data.
Data Loss Prevention is a set of tools and practices geared towards protecting your data from loss and leak. Even though the name has only the loss part, in actuality, it's as much about the leak protection as it is about the loss protection. Basically, DLP, as a notion, encompasses all the security practices around protecting your company data.
8. Is Remote Work Responsible for Growing Cybersecurity Threats?
 A tech story centered around the looming issues of cybersecurity, cyber attacks, and the possible solutions in today's remote working ecosystem.
A tech story centered around the looming issues of cybersecurity, cyber attacks, and the possible solutions in today's remote working ecosystem.
9. 2 Million Fitbit Accounts Were Exposed by Cybercriminals
 A user on a well-known hacker community has leaked the emails and passwords of 1,999,999 users of the widely used health and fitness platform Fitbit, famous for its gadgets like smartwatches, and innovative fitness apps that track your training and sleeping patterns (among other things). The platform was recently acquired by Google LLC in a $2.1 billion USD deal.
A user on a well-known hacker community has leaked the emails and passwords of 1,999,999 users of the widely used health and fitness platform Fitbit, famous for its gadgets like smartwatches, and innovative fitness apps that track your training and sleeping patterns (among other things). The platform was recently acquired by Google LLC in a $2.1 billion USD deal.
10. Clickjacking Attacks: What Are They and How to Prevent Them

11. How Machine Learning Prevents Identity Theft

12. Effects a Data Breach Can Have on Your Business in the Long Term

13. The State Of Data Privacy In 2020
 In 2020, there will be just one thing considered to be more important than product quality for consumers: data privacy. By this I refer not to user-controlled measures to add extra security for internet users, from the most classic one-time password, or two-factor authentication, to the most secure multi-factor authentication methods: but data privacy measures implemented by companies to ensure that peoples’ personal data is protected - no matter what.
In 2020, there will be just one thing considered to be more important than product quality for consumers: data privacy. By this I refer not to user-controlled measures to add extra security for internet users, from the most classic one-time password, or two-factor authentication, to the most secure multi-factor authentication methods: but data privacy measures implemented by companies to ensure that peoples’ personal data is protected - no matter what.
14. Formjacking Attacks: Defention and How To Prevent It
 Formjacking attacks are designed to steal financial details from payment forms. Learn how it affects your business and tips to prevent a formjacking attack.
Formjacking attacks are designed to steal financial details from payment forms. Learn how it affects your business and tips to prevent a formjacking attack.
15. IP Addresses Are Key to Countering Brute-force Attacks
 Verizon’s 2020 Data Breach Investigations Report shows that 80% of the breaches caused by hacking involve brute-force or the use of lost or stolen credentials. The content management systems (CMS) are the usual targets of brute-force attacks, as 39.3% of all the websites presumably run on WordPress, the most popular of these.
Verizon’s 2020 Data Breach Investigations Report shows that 80% of the breaches caused by hacking involve brute-force or the use of lost or stolen credentials. The content management systems (CMS) are the usual targets of brute-force attacks, as 39.3% of all the websites presumably run on WordPress, the most popular of these.
16. 4 Simple Steps to Avoid Falling Victim to All-Too-Frequent Data Breaches
 These days, reports of major data breaches happen so often that people are beginning to tune them out. After all, most people who have had their data stolen don't actually end up suffering any visible consequences. Therefore, it's all too easy to meet the news of each new security incident with a casual shrug.
These days, reports of major data breaches happen so often that people are beginning to tune them out. After all, most people who have had their data stolen don't actually end up suffering any visible consequences. Therefore, it's all too easy to meet the news of each new security incident with a casual shrug.
17. 5 Ways to Ensure You Aren’t Sharing Your Workplace Data
 With so much of our lives online, it's too easy for us to make a mistake and accidentally share our workplace data. These easy methods keep your data safe.
With so much of our lives online, it's too easy for us to make a mistake and accidentally share our workplace data. These easy methods keep your data safe.
18. How 5 Massive Data Breaches Could Have Been Prevented
 One of the biggest losses for companies? Inadequate cybersecurity.
One of the biggest losses for companies? Inadequate cybersecurity.
19. Data Breach Costs Will Get Worse Before They Get Better. Here’s Why.
 Every time there’s a publicly revealed data breach, the public feels a little less secure. Over the past few years, we’ve seen massive breaches of major institutions, from Target to Equifax, that have cost those institutions hundreds of millions of dollars and marred their reputation.
Every time there’s a publicly revealed data breach, the public feels a little less secure. Over the past few years, we’ve seen massive breaches of major institutions, from Target to Equifax, that have cost those institutions hundreds of millions of dollars and marred their reputation.
20. 4 Signs You Make it Easy For Someone to Hack You
 Hacking can happen on any device and to any person—and hackers are only getting smarter by the minute.
Hacking can happen on any device and to any person—and hackers are only getting smarter by the minute.
21. Be Resilient not Vulnerable to Ransomware Emails

22. Planning Cyber Security Budget Thoroughly: 2021 Edition
 Budgeting for cybersecurity is a challenging process. Here are some tips, how you can plan your cyber security budget effectively.
Budgeting for cybersecurity is a challenging process. Here are some tips, how you can plan your cyber security budget effectively.
23. How To Approach Modern Cybersecurity
 There are many ways to approach the cybersecurity of your business and ensure that your data, and that of your customers, is safe from malicious actors. Most of these can boil down to focusing on the three major areas of technology, processes and people. This can help you better focus your approach to what your firm needs and which tools and techniques there are to help.
There are many ways to approach the cybersecurity of your business and ensure that your data, and that of your customers, is safe from malicious actors. Most of these can boil down to focusing on the three major areas of technology, processes and people. This can help you better focus your approach to what your firm needs and which tools and techniques there are to help.
24. An introduction to CSRF Attacks: Who Is Riding With You?

25. How is Identity-Based Access Swiftly Becoming the Foundation for Secure Critical Infrastructure?
 Businesses must incorporate stringent security measures while navigating their digital transformation journey.
Businesses must incorporate stringent security measures while navigating their digital transformation journey.
26. 9 Security Tips to Protect Your Website from Hackers and Data Breaches
 Here are 9 Security Tips to Protect Websites from Hackers. A secure website will establish your position in the cyber-world and let you do more business.
Here are 9 Security Tips to Protect Websites from Hackers. A secure website will establish your position in the cyber-world and let you do more business.
27. In a Time of Crisis, Data Must Be Able to Defend Itself

28. 5 Most Vulnerable Industries for Data Breaches in 2018
 In February 2018, the Under Armour hack turned out to be one of the biggest data breaches in history, affecting over 150,000,000 users. The sheer number of victims made it, at the time, a record-breaking data theft, but what's really disturbing about this incident?
In February 2018, the Under Armour hack turned out to be one of the biggest data breaches in history, affecting over 150,000,000 users. The sheer number of victims made it, at the time, a record-breaking data theft, but what's really disturbing about this incident?
29. Using Unmasked Production Data For Testing Leaves Your At Risk For Data Breaches

30. The 4 Main Types of Data Breaches: Definition and Examples
 A data breach is a serious security violation; unfortunately, it can happen to the best of us. Let’s learn and keep aware of it together.
A data breach is a serious security violation; unfortunately, it can happen to the best of us. Let’s learn and keep aware of it together.
31. 10 Reasons to Get Your Cybersecurity Certification

32. Attorney Adam Williams Gives Advice on Data Breaches and Class-Action Suits
 Technology is changing incredibly quickly, and as a consumer, it can often be difficult to stay on the front lines of keeping yourself secure while using all of the technological marvels that the world has to offer. Data breaches and privacy breaches are reported every day in the news, making the private information of thousands vulnerable to identity theft and the consequences that come with it.
Technology is changing incredibly quickly, and as a consumer, it can often be difficult to stay on the front lines of keeping yourself secure while using all of the technological marvels that the world has to offer. Data breaches and privacy breaches are reported every day in the news, making the private information of thousands vulnerable to identity theft and the consequences that come with it.
33. Darkweb Community MagBO Sells Data Stolen From Over 20k Websites
 MagBO, the Russian-speaking dark web marketplace for trading in backdoored websites, continues to grow exponentially. In less than two years, the collection of leaks grew from around 3,000 in September 2018 to 26,605 in February 2020.
MagBO, the Russian-speaking dark web marketplace for trading in backdoored websites, continues to grow exponentially. In less than two years, the collection of leaks grew from around 3,000 in September 2018 to 26,605 in February 2020.
34. Root Cause Analysis: How to Get to the Heart of a Breach
 Root cause analysis allows businesses to identify the primary cause behind a data breach to prevent it from happening again. Here's how to conduct an RCA.
Root cause analysis allows businesses to identify the primary cause behind a data breach to prevent it from happening again. Here's how to conduct an RCA.
35. VPNs Leaked 1.2TB of Your Data and That is Pretty Awkward
 20 Million VPN users across seven different VPN services had their data compromised when it ended up on the dark web.
20 Million VPN users across seven different VPN services had their data compromised when it ended up on the dark web.
36. The Less Understood Dangers of Secret Sprawl and What Devs Can Do to Fight It
 When developers refer to secret sprawl they are typically referring to the unwanted distribution of secrets across multiple platforms, services and machines.
When developers refer to secret sprawl they are typically referring to the unwanted distribution of secrets across multiple platforms, services and machines.
37. How Proactive API Visibility Could've Saved Optus From a Massive Data Breach
 On 22 September 2022, Australia's second-largest telecom company, Optus, announced that it had suffered a significant data breach.
On 22 September 2022, Australia's second-largest telecom company, Optus, announced that it had suffered a significant data breach.
38. Hacking Facial Recognition: How To Protect Your Company Agaist It
 Identity theft cases are increasing. There are varying levels of security, and not all facial biometrics software protects against more cunning tricks.
Identity theft cases are increasing. There are varying levels of security, and not all facial biometrics software protects against more cunning tricks.
39. The ZEE5 User Data Leak That The Media Didn't Report On

40. FinTech Cybersecurity: How 'Capital One' Could Have Avoided a Data Breach
 Even after investing heavily in securing IT infrastructure and developing security tools with AWS, Capital One failed to avoid data breaches. Here's why.
Even after investing heavily in securing IT infrastructure and developing security tools with AWS, Capital One failed to avoid data breaches. Here's why.
41. Automation Is the Essential Part of Cyber Risk Management: Know Why
 Cybersecurity risk management, also defined as IT risk management, applies to any of the technology, people, regulations, and processes that a company may employ to assess, handle, and minimize cybersecurity threats to customer and company data, as well as business operations. IT risk, detection tools for example, would almost certainly provide cybersecurity risk management software as well as security controls to prevent and address cyber risk and security exposures proactively.
Cybersecurity risk management, also defined as IT risk management, applies to any of the technology, people, regulations, and processes that a company may employ to assess, handle, and minimize cybersecurity threats to customer and company data, as well as business operations. IT risk, detection tools for example, would almost certainly provide cybersecurity risk management software as well as security controls to prevent and address cyber risk and security exposures proactively.
42. 7 Deadly Digital Sins: Understanding the Main Types of Malware
 Malware is everywhere these days. You've probably been a victim at some stage, and you may well not even know it. From all-too-visible ransomware attacks to botnets and adware, it's a complex picture, and new variants are emerging all the time.
Malware is everywhere these days. You've probably been a victim at some stage, and you may well not even know it. From all-too-visible ransomware attacks to botnets and adware, it's a complex picture, and new variants are emerging all the time.
43. 5 Tips to Promote CyberSecurity Awareness in Your Organization

44. LastPass Confirms Hackers Stole Encrypted Password Vaults... Four Months Ago
 A password vault leak had happened four months ago and LastPass is only telling you that now.
A password vault leak had happened four months ago and LastPass is only telling you that now.
45. Adding a Little Salt to Passwords Can Improve Security
 With the rise in cybersecurity threats, having a strong, secure password has become more critical than ever. In fact, did you know that the key reason behind 80% of data breaches in 2019 was password compromise?
With the rise in cybersecurity threats, having a strong, secure password has become more critical than ever. In fact, did you know that the key reason behind 80% of data breaches in 2019 was password compromise?
46. How to Avoid Becoming a Victim of Data Breach

47. The Largest Data Breaches in History
 A look at where the largest data breaches have occurred across the world.
A look at where the largest data breaches have occurred across the world.
48. Be 100% Safe On The Internet Using These Strategies
 The Internet is full of opportunities, useful information, entertainment, and dangers as well. To protect yourself from the latter, you need to follow certain safety rules. Read on to learn how to properly use a home or public Wi-Fi to avoid dangerous malware and protect personal data, and what is the role of nect MODEM in helping you do so.
The Internet is full of opportunities, useful information, entertainment, and dangers as well. To protect yourself from the latter, you need to follow certain safety rules. Read on to learn how to properly use a home or public Wi-Fi to avoid dangerous malware and protect personal data, and what is the role of nect MODEM in helping you do so.
49. Businesses Will Face These 4 Cloud Security Challenges in 2021
 As threats have sophisticated and evolved, new attacks emerge and it becomes more important than ever for businesses to embrace security first mentalities.
As threats have sophisticated and evolved, new attacks emerge and it becomes more important than ever for businesses to embrace security first mentalities.
50. Cyber Security Awareness Month: The Top 3 Types of Insider Threats Putting Companies at Risk
 October is Cyber Security Awareness Month. In 2022, cybersecurity was a top concern for c-suite executives, board members, department leads, and IT teams.
October is Cyber Security Awareness Month. In 2022, cybersecurity was a top concern for c-suite executives, board members, department leads, and IT teams.
51. How to Solve Enterprise Data Breaches with Turnkey Neobank Solutions
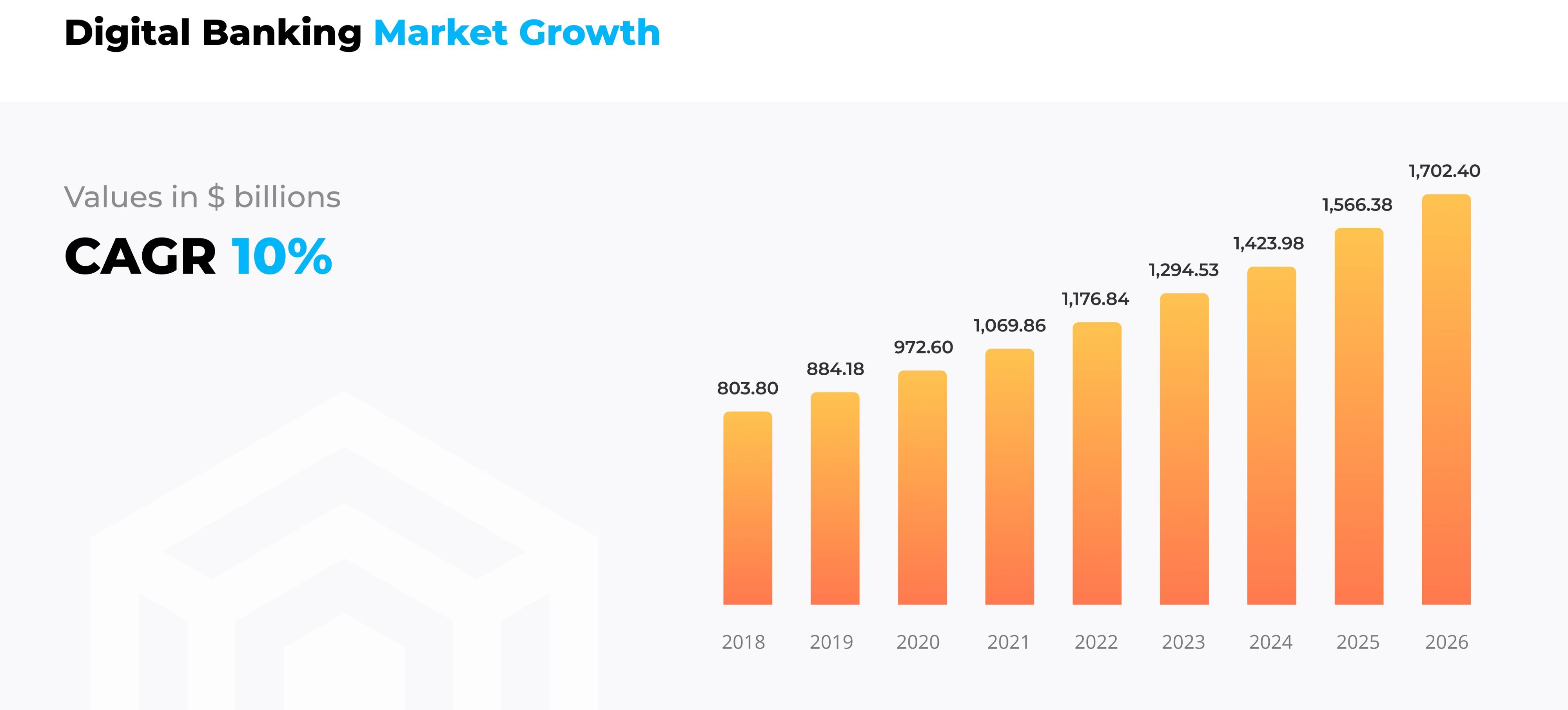 Digital banking is emerging as one of the fastest-growing segments
across the globe. The over $800 billion in revenue generated in 2018 is
projected to grow at a CAGR of 10% over the next 5 years, reaching $1.7
trillion by 2026.
Digital banking is emerging as one of the fastest-growing segments
across the globe. The over $800 billion in revenue generated in 2018 is
projected to grow at a CAGR of 10% over the next 5 years, reaching $1.7
trillion by 2026.
52. AU Government Fails Cybersecurity Targets as PM Warns of Cyber Threat
 On June 19 this year Australian Prime Minister, Scott Morrison, alerted the nation to the fact they were undergoing cyber attack.
On June 19 this year Australian Prime Minister, Scott Morrison, alerted the nation to the fact they were undergoing cyber attack.
53. What Everyone Should Know About Tools And Services Of ATO Providers
 What is account takeover? What are the tools and methods attackers use to employ it? And how active is HOSEEN on the dark web? Learn more in this article.
What is account takeover? What are the tools and methods attackers use to employ it? And how active is HOSEEN on the dark web? Learn more in this article.
54. How to Perform a Cyber Security Risk Assessment: A Step-by-Step Guide
55. Hosting Provider Cloud Clusters Inc. Potentially Exposed 63M Records
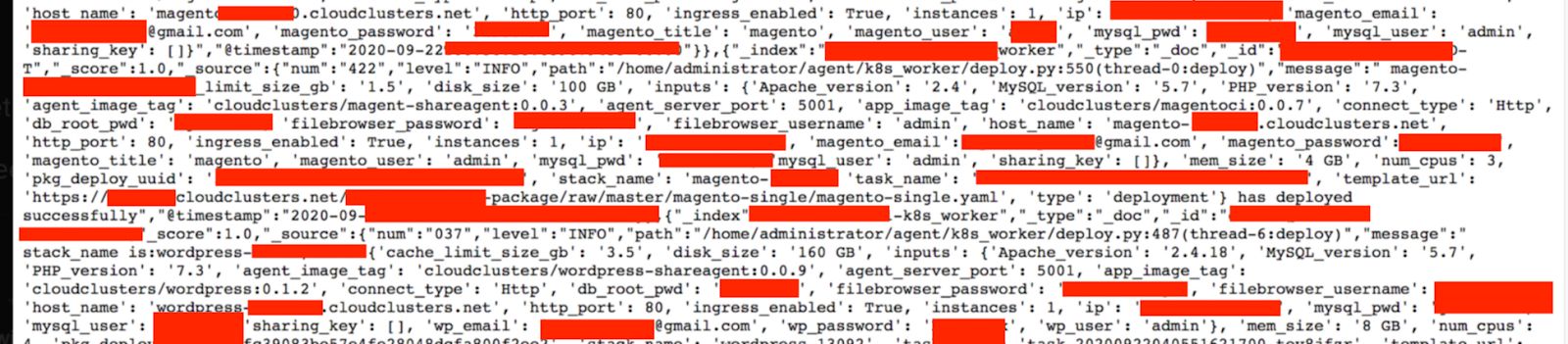 An exposed and unsecured database from Cloud Application Hosting company Cloud Clusters, Inc. was discovered on October 5, 2020, containing more than 63 million records.This discovery was made by Jeremiah Fowler from Securethoughts. Among the records were username and password credentials for Magento, WordPress, and MySql.
An exposed and unsecured database from Cloud Application Hosting company Cloud Clusters, Inc. was discovered on October 5, 2020, containing more than 63 million records.This discovery was made by Jeremiah Fowler from Securethoughts. Among the records were username and password credentials for Magento, WordPress, and MySql.
56. The Ultimate Cyber Security Survival Guide
 Every action on the network leaves a digital footprint. For example, photos we post on social networks, statements on forums, likes and dislikes of videos. Moreover, a user activity leaves a digital trace - information about the sites browsed, purchases made, and geographical locations visited. There are many channels through which our personal data is exposed and the effects of abuse are very serious. Therefore, you should always be extremely careful about the use of world wide web and private data management.
Every action on the network leaves a digital footprint. For example, photos we post on social networks, statements on forums, likes and dislikes of videos. Moreover, a user activity leaves a digital trace - information about the sites browsed, purchases made, and geographical locations visited. There are many channels through which our personal data is exposed and the effects of abuse are very serious. Therefore, you should always be extremely careful about the use of world wide web and private data management.
57. Equifax will pay up to $700 million over one of the worst breaches in U.S History!
 I still remember that day like yesterday.
I still remember that day like yesterday.
58. Announcing our Data Breach website on Data Privacy Day
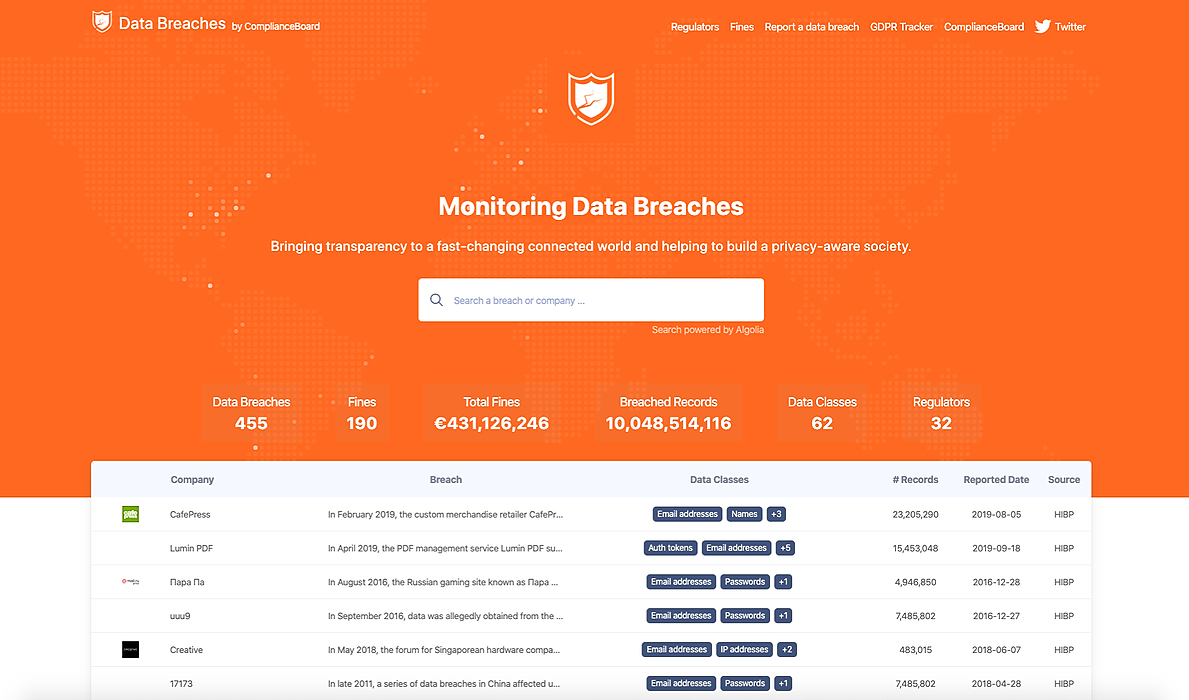 We are happy to announce our Data Breach website Databreach.es, our latest community project. With this project, we strive to create insights into global data breaches. Which companies have been breached, what kind of data got lost, what's the impact on your privacy and how did these companies handle the situation.
We are happy to announce our Data Breach website Databreach.es, our latest community project. With this project, we strive to create insights into global data breaches. Which companies have been breached, what kind of data got lost, what's the impact on your privacy and how did these companies handle the situation.
59. A Guide To Protecting Sensitive Business Data
 Each year, we’re witnessing growing trends of digitalization and connectivity. However, the more data businesses are storing digitally, the more exposed the data is to breaches.
Each year, we’re witnessing growing trends of digitalization and connectivity. However, the more data businesses are storing digitally, the more exposed the data is to breaches.
60. Programming a Keylogger in Python
 A keylogger is a tool designed to record every keystroke on a system for later retrieval. Its purpose is to allow the user to gain access to confidential info.
A keylogger is a tool designed to record every keystroke on a system for later retrieval. Its purpose is to allow the user to gain access to confidential info.
61. 6 Expert Cybersecurity Strategies for Financial Institutions
 Investing in security is vital, but major breaches still happen irrespective of advancements. Financial organizations can take these 6 steps to better security.
Investing in security is vital, but major breaches still happen irrespective of advancements. Financial organizations can take these 6 steps to better security.
62. Hybrid-Working & Online Security: 7 Ways to Combat Threats in 2022
 Hybrid working model is the new norm and with its rise there is a dire need to keep your digital identity secure with some tested tips backed by research.
Hybrid working model is the new norm and with its rise there is a dire need to keep your digital identity secure with some tested tips backed by research.
63. Data Breaches: No Longer Delivering Punches to Business Reputation?
 Photo by NeONBRAND on Unsplash
Photo by NeONBRAND on Unsplash
64. Centralized vs Decentralized Networks
65. 5 Reasons Why Privacy by Design is More Critical Than Ever in 2023
 The more manual work is involved in managing data privacy, the greater the risk of costly data and compliance breaches.
The more manual work is involved in managing data privacy, the greater the risk of costly data and compliance breaches.
66. Hacked Peruvian Government Servers are Sending Phishing Campaigns to Chase Bank Customers
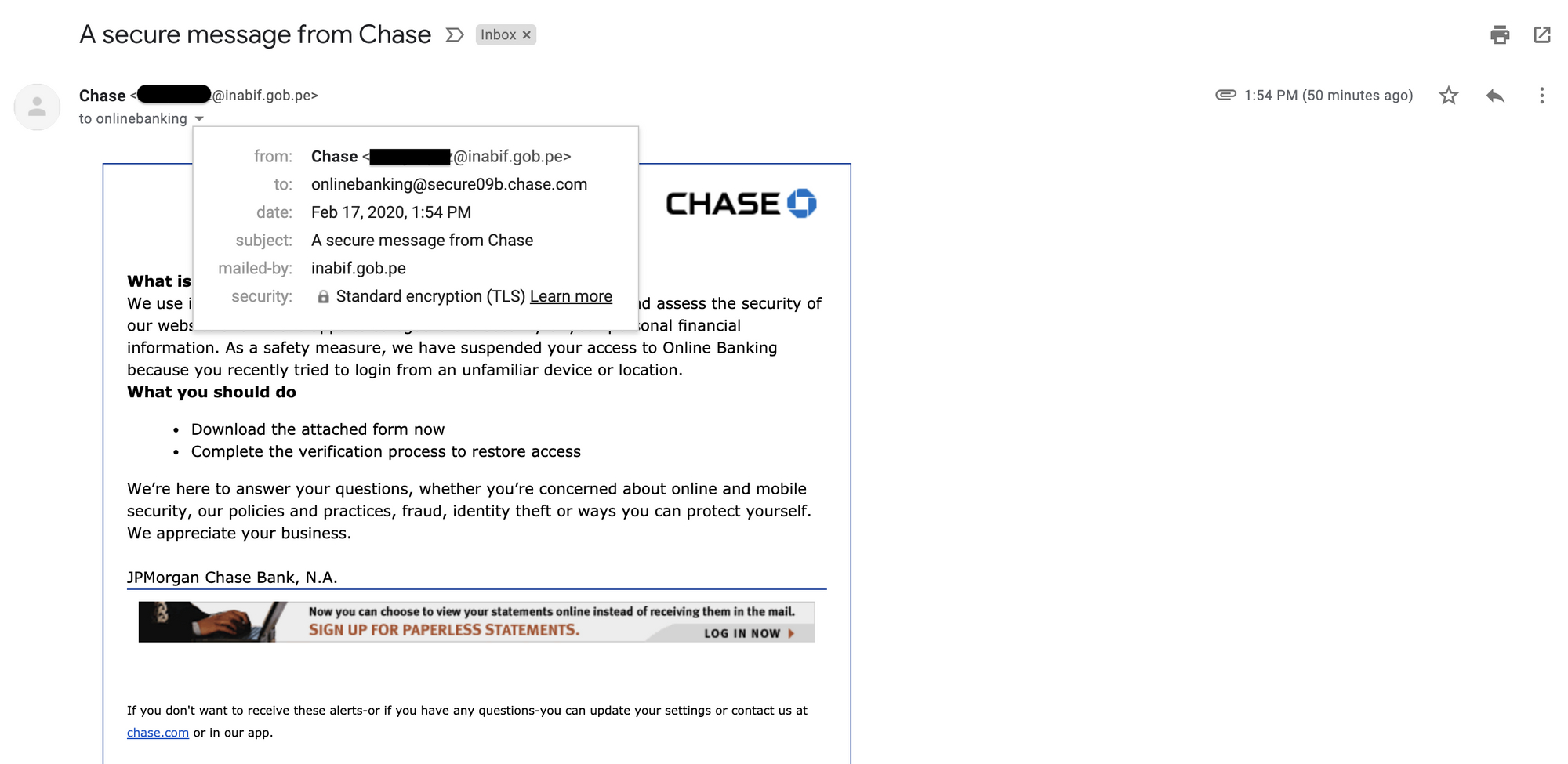 If you are a current or former Chase customer and familiar with those periodic "a secure message from Chase" email notifications, this one would've better caught your attention, if not your spam filter's. Thankfully for me, it was sent to a Gmail address I had not used with Chase online banking since 2014 or so. This instantly indicated the attackers had prior knowledge of my Gmail address having been used with Chase online banking in the past.
If you are a current or former Chase customer and familiar with those periodic "a secure message from Chase" email notifications, this one would've better caught your attention, if not your spam filter's. Thankfully for me, it was sent to a Gmail address I had not used with Chase online banking since 2014 or so. This instantly indicated the attackers had prior knowledge of my Gmail address having been used with Chase online banking in the past.
67. What You Should Know About Zero-Party Data
 Zero-party data (ZPD) means a company only collects user data that is freely given. Period. But why would a modern business, raised on the wonders of Big Data, undertake such a foolish philosophy? Maybe because they aren’t fans of financial ruin.
Zero-party data (ZPD) means a company only collects user data that is freely given. Period. But why would a modern business, raised on the wonders of Big Data, undertake such a foolish philosophy? Maybe because they aren’t fans of financial ruin.
68. Phone Scams: What Is Vishing And How You Can Avoid It
 The attack combines a one-on-one phone call with credible-looking phishing sites where the user is required to fill in their credentials and their MFA codes.
The attack combines a one-on-one phone call with credible-looking phishing sites where the user is required to fill in their credentials and their MFA codes.
69. Data Breaches: Why You Should Never Share Your Passwords
 Data Breaches: Why You Should Never Share Your Passwords
Data Breaches: Why You Should Never Share Your Passwords
70. Data Storage Security: 5 Best Practices to Secure Your Data

71. Insiders Breach Your Organization’s Data (Data Tells Us So)
 Many company executives claim that the biggest threats to their data privacy are external threats, such as hackers or state-funded cyber-threats. However, companies are actually more likely to experience a data breach from an internal source, whether it is malicious or accidental.
Many company executives claim that the biggest threats to their data privacy are external threats, such as hackers or state-funded cyber-threats. However, companies are actually more likely to experience a data breach from an internal source, whether it is malicious or accidental.
Thank you for checking out the 71 most read stories about Data Breach on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

