Let's learn about Cyber Security via these 426 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
Cyber Security encompasses anything and everything from encryption to network security and endpoint security.
1. Beware the Dusting Attack That Endangers The Privacy of Blockchain Transactions
 A dusting attack involves sprinkling crypto wallets with minuscule amounts of crypto to connect multiple addresses to a single owner. While these attacks are relatively new and nobody has really been able to say for sure what the exact motives behind them are, what is clear is that they represent a significant threat to privacy on the blockchain.
A dusting attack involves sprinkling crypto wallets with minuscule amounts of crypto to connect multiple addresses to a single owner. While these attacks are relatively new and nobody has really been able to say for sure what the exact motives behind them are, what is clear is that they represent a significant threat to privacy on the blockchain.
2. You'll Probably Be Exposed To These 5 Cybersecurity Threats In 2021
 How to prepare yourself to face the Cybersecurity Threats in the year ahead? Check out the top 5 of the most expected attacks in 2021.
How to prepare yourself to face the Cybersecurity Threats in the year ahead? Check out the top 5 of the most expected attacks in 2021.
3. A Former Hacker’s 10 Tips on Staying Safe Online
 While in prison, Hiếu wrote an online security guide for the average internet user.
While in prison, Hiếu wrote an online security guide for the average internet user.
4. Watch Out! Fake Tether in Circulation!
 In our big Facebook group a few hours ago a member wrote that 34’000€ disappeared from his Atomic Wallet. What happened?
In our big Facebook group a few hours ago a member wrote that 34’000€ disappeared from his Atomic Wallet. What happened?
5. Cracking the SANS GSEC Certification
 The SANS GIAC Security Essentials (GSEC) certification is for anyone working in the field of Information Security.
The SANS GIAC Security Essentials (GSEC) certification is for anyone working in the field of Information Security.
6. Cybersecurity Lessons from Working with the Ecuadorian Government
 I’m currently temtum cryptocurrency CTO, we’re in the process of launching our cryptocurrency which will change the way we all make payments. But I wanted to share an earlier experience of working with the Ecuadorian government to ensure the cyber and data security of my home nation. It was one of my proudest moments, a unique and rewarding challenge, one that I will never forget.
I’m currently temtum cryptocurrency CTO, we’re in the process of launching our cryptocurrency which will change the way we all make payments. But I wanted to share an earlier experience of working with the Ecuadorian government to ensure the cyber and data security of my home nation. It was one of my proudest moments, a unique and rewarding challenge, one that I will never forget.
7. Taking a Systematic Approach to Cyber Deception - Part 2
 We need to consider Safety aspects related to Industrial networks carefully.
We need to consider Safety aspects related to Industrial networks carefully.
8. Two Factor Authentication - The Deep State Tool That Supports Mass Technology Dysfunction
 2FA is the initial, mandatory stage of ongoing privacy intrusions that are unwarranted and Orwellian. Alternatives now exist.
2FA is the initial, mandatory stage of ongoing privacy intrusions that are unwarranted and Orwellian. Alternatives now exist.
9. Scanning 2.6 Million Domains for Exposed .Env Files
 A software developer scanned 2.6 million domains for exposed.env files.
A software developer scanned 2.6 million domains for exposed.env files.
10. How To Avoid 5 Nagging Security Issues With Blockchain
 Blockchain is undeniably useful to businesses, but it also has substantial limitations owing to particular security concerns. Here are the top five with fixes.
Blockchain is undeniably useful to businesses, but it also has substantial limitations owing to particular security concerns. Here are the top five with fixes.
11. A Conversation With Amazon Software Engineer Anam Alvi
 Anam Alvi is a software engineer working in Amazon's security division. Read her story from growing up in Toronto to joining Hackathons across the country.
Anam Alvi is a software engineer working in Amazon's security division. Read her story from growing up in Toronto to joining Hackathons across the country.
12. Blue is Happiness: Interview with 2022 Noonies Nominee Anastasios

13. Deeper Network's Connect And IDO Launch: the Latest News
 Deeper Network, which is building the decentralized internet infrastructure for the Web 3.0, has broken Indiegogo records by raising over $1 million to become the most successful blockchain project in the history of the crowdfunding platform.
Deeper Network, which is building the decentralized internet infrastructure for the Web 3.0, has broken Indiegogo records by raising over $1 million to become the most successful blockchain project in the history of the crowdfunding platform.
14. Biden Administration Prioritizes Cybersecurity Funding After Numerous Cyberattacks
 The Biden administration is coming up with a $100 billion investment plan fo cybersecurity spending.
The Biden administration is coming up with a $100 billion investment plan fo cybersecurity spending.
15. When Should I Use an HTTP/HTTPS Sniffer?
 In this article, I will tell you what role the HTTP/HTTPS sniffer plays in data parsing and why it is very important.
In this article, I will tell you what role the HTTP/HTTPS sniffer plays in data parsing and why it is very important.
16. Practical Examples of Using ML in Cybersecurity
 In this era, technology has become a basic necessity due to its compactness and handiness. This alleviation in the use of technology has also welcomed new problems. One of the most crucial issues is security. Devices contain personal and critical data which is usually misused if it is not secured. This is why the functioning of cybersecurity uses Machine language and Artificial Intelligence. It implements protection tools to create a wall between user and hacker.
In this era, technology has become a basic necessity due to its compactness and handiness. This alleviation in the use of technology has also welcomed new problems. One of the most crucial issues is security. Devices contain personal and critical data which is usually misused if it is not secured. This is why the functioning of cybersecurity uses Machine language and Artificial Intelligence. It implements protection tools to create a wall between user and hacker.
17. Microsoft Urges Users Not to Remove Expired Windows 10 Root Certificate
 The root Windows certificate expires on December 31, but it is still required for the OS to function properly.
The root Windows certificate expires on December 31, but it is still required for the OS to function properly.
18. Meet the CyberSecurity Analyst Who Also Loves Trying Out Food Recipes
 I write about what keeps businesses secure and profitable and provide advisory to decision makers.
I write about what keeps businesses secure and profitable and provide advisory to decision makers.
19. How Blockchain has Improved Detection of Malware
 Blockchain has not only become the fundamental technology for cryptocurrencies; it has also become a reliable means of detecting malware quickly and accurately.
Blockchain has not only become the fundamental technology for cryptocurrencies; it has also become a reliable means of detecting malware quickly and accurately.
20. A Beginner's Guide to Protecting your NFTs and Other Digital Assets
 Crypto security should be a top priority for everyone. In this article, I go over some best practices and securities tips so you can keep your assets secure.
Crypto security should be a top priority for everyone. In this article, I go over some best practices and securities tips so you can keep your assets secure.
21. 2.6 Million Domains and ~45,000 Exposed Phpinfo() Later… the Story of Unprotected Phpinfo()
 A scan of over 2.6 million domains for exposed phpinfo() data from PHP and the analysis of what was found. Exposed database credentials is only the start.
A scan of over 2.6 million domains for exposed phpinfo() data from PHP and the analysis of what was found. Exposed database credentials is only the start.
22. How To Prevent Ransomware Attacks: A Threat That’s Real
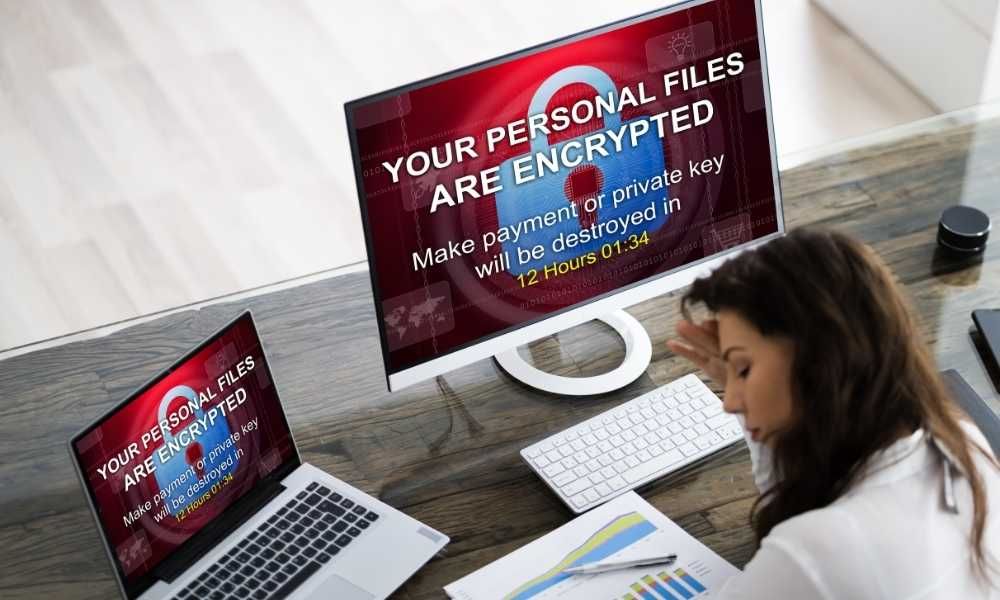 Ransomware works by encrypting the user’s data, making it unreadable. If a user wants their data back, a ransom must be paid. Keep reading to learn more
Ransomware works by encrypting the user’s data, making it unreadable. If a user wants their data back, a ransom must be paid. Keep reading to learn more
23. Why You Should Use IAM Policies to Enforce MFA on AWS
 In my past life, I was an auditor and performed hundreds of cybersecurity
readiness assessments. These were sometimes called “gap analysis” and
the essential purpose of these assessments were to provide organizations with the answers to the test for their upcoming official assessment.
In my past life, I was an auditor and performed hundreds of cybersecurity
readiness assessments. These were sometimes called “gap analysis” and
the essential purpose of these assessments were to provide organizations with the answers to the test for their upcoming official assessment.
24. 3 Flipper Zero Hacks to Wow Your Friends (and How They Work)
 It is theoretically possible to use these Flipper Zero hacks for nefarious purposes, including the tricks in this article. But you know…don’t do that.
It is theoretically possible to use these Flipper Zero hacks for nefarious purposes, including the tricks in this article. But you know…don’t do that.
25. What Poses a Challenge to Security in a Multi-Cloud Environment
 Multi-cloud gives you much more flexibility because it allows you to find the perfect solution for each of your business requirements.
Multi-cloud gives you much more flexibility because it allows you to find the perfect solution for each of your business requirements.
26. Cybercriminals Target SMEs and Large Companies Alike
 About the operation of SMEs, there are many misconceptions, especially in the field of cyber-security, but a study by Cisco has shown that they share a lot with large companies in the world.
About the operation of SMEs, there are many misconceptions, especially in the field of cyber-security, but a study by Cisco has shown that they share a lot with large companies in the world.
27. How to Protect Your Git Secrets
 Are you worried about your security codes and keys? Worried about their safety? Are you looking for ways to protect your Git secrets? If so, then you are in the right place. And in this post, I will share everything you need to know about Git best practices to protect your Git secrets.
Are you worried about your security codes and keys? Worried about their safety? Are you looking for ways to protect your Git secrets? If so, then you are in the right place. And in this post, I will share everything you need to know about Git best practices to protect your Git secrets.
28. 3 Cybersecurity Priorities for 2021: Threat Fatigue; Remote Work; Budget
 Disagreement is one of the defining trends of 2020. However, I think most of us would agree that this year hasn’t turned out to be the kind of year that many of us anticipated when we celebrated on December 31st.
Disagreement is one of the defining trends of 2020. However, I think most of us would agree that this year hasn’t turned out to be the kind of year that many of us anticipated when we celebrated on December 31st.
29. The Q3 2022 Blockchain Security Report
 In the third quarter of 2022, Beosin EagleEye monitored over 37 major attacks in the Web3 space, with total losses of approximately $405 million, down approxima
In the third quarter of 2022, Beosin EagleEye monitored over 37 major attacks in the Web3 space, with total losses of approximately $405 million, down approxima
30. Serialization Filtering in Java - Preventing Zero-Day Security Vulnerabilities
 A simple configuration that requires no code change can save you from a hack such as Log4Shell, even from vulnerabilities we don't know about yet!
A simple configuration that requires no code change can save you from a hack such as Log4Shell, even from vulnerabilities we don't know about yet!
31. Recap: The TikTok Saga and the Problems Facing this Massive Platform
 This past weekend came as quite a shock to a vast amount of netizens in the United States. While having a conversation with reporters on Air Force 1, president Donald Trump mentioned banning TikTok in the U.S., a video sharing social platform with 165 million downloads in the region, that is accused of providing data to the Chinese government.
This past weekend came as quite a shock to a vast amount of netizens in the United States. While having a conversation with reporters on Air Force 1, president Donald Trump mentioned banning TikTok in the U.S., a video sharing social platform with 165 million downloads in the region, that is accused of providing data to the Chinese government.
32. Threat Hunting the Easy Way
 Threat hunting can feel impossible. It doesn't have to be that way, in this post I share how I have found attackers (and success) with threat hunting!
Threat hunting can feel impossible. It doesn't have to be that way, in this post I share how I have found attackers (and success) with threat hunting!
33. IT Security: How to Deal With The Insider Threat
 A study by the Wall Street Journal found that almost 70% of companies admitted concern about violent employees! While workers continue to be a major security ri
A study by the Wall Street Journal found that almost 70% of companies admitted concern about violent employees! While workers continue to be a major security ri
34. The Complete Guide to Security Operations Centers
 Security operation centers (SOC) are oriented in the protection of confidentiality, integrity and availability of the information assets in the network and services of the company.
Security operation centers (SOC) are oriented in the protection of confidentiality, integrity and availability of the information assets in the network and services of the company.
35. Newest Malware from China
 “I think malware is a significant threat because the mitigation, like antivirus software, hasn’t evolved to a point to mitigate the risk to a reasonable degree.” Kevin Mitnick
“I think malware is a significant threat because the mitigation, like antivirus software, hasn’t evolved to a point to mitigate the risk to a reasonable degree.” Kevin Mitnick
36. Impacts of Double Extortion Ransomware Attack on Enterprises and Mitigation
 Double Extortion Ransomware Attack is nefarious and seems unstoppable. However, it can be mitigated with some effective techniques.
Double Extortion Ransomware Attack is nefarious and seems unstoppable. However, it can be mitigated with some effective techniques.
37. The Beginner's Guide to Ensuring Web Hosting Security in 2020
 Some people call the internet as a borderless entity, where you can go anywhere you like and access anything your eye falls upon. This can be counted as the technology’s greatest strength, and conversely, its greatest weakness. Why? Because, in the absence of checkpoints, you cannot possibly fathom the intention of other web surfers, which could be anything from beneficial to downright malicious.
Some people call the internet as a borderless entity, where you can go anywhere you like and access anything your eye falls upon. This can be counted as the technology’s greatest strength, and conversely, its greatest weakness. Why? Because, in the absence of checkpoints, you cannot possibly fathom the intention of other web surfers, which could be anything from beneficial to downright malicious.
38. Stop Aimlessly Scrolling — Start Earning $ from Facebook's Whitehat Platform
 Did you know that Facebook paid out $880,000 in bug bounties in 2017? Well, I got my second bounty within a relatively short span of time.
The issue was reproduced by their security team with ease, and had meaningful impact on user’s privacy. I hope this write-up inspires people not to overlook small issues while scrolling aimlessly through Facebook, and also while testing it.
Did you know that Facebook paid out $880,000 in bug bounties in 2017? Well, I got my second bounty within a relatively short span of time.
The issue was reproduced by their security team with ease, and had meaningful impact on user’s privacy. I hope this write-up inspires people not to overlook small issues while scrolling aimlessly through Facebook, and also while testing it.
39. Lay a strong foundation by writing secure C and C++ utilities
 Libraries and system utilities form the foundations on which larger projects are built. So it's critical to make sure they, in particular, are secure. That's why we recently introduced five new rules for C++ and C to detect broken authentication and access control in *nix systems. The new rules fall into three categories: account validity, granting permissions, and changing directories.
Libraries and system utilities form the foundations on which larger projects are built. So it's critical to make sure they, in particular, are secure. That's why we recently introduced five new rules for C++ and C to detect broken authentication and access control in *nix systems. The new rules fall into three categories: account validity, granting permissions, and changing directories.
40. 8 Crucial Tips for Hardening PostgreSQL 14.4 servers in 2022
 As of July 13th, 2022, there are 135 security flaws reported to the CVE database. Here are 8 essential measures you can take to protect your PostgreSQL server.
As of July 13th, 2022, there are 135 security flaws reported to the CVE database. Here are 8 essential measures you can take to protect your PostgreSQL server.
41. 5 Reasons Why Your Startup or SMB needs a VPN
 Conversations about VPN servers for business applications usually come down to on-premises solutions for large corporations with several international offices and thousands of employees who require access to shared intranet. On the other hand, cloud-based VPN services often cater to private customers looking to stream their favourite TV shows while travelling, or to circumvent the Great Firewall.
Conversations about VPN servers for business applications usually come down to on-premises solutions for large corporations with several international offices and thousands of employees who require access to shared intranet. On the other hand, cloud-based VPN services often cater to private customers looking to stream their favourite TV shows while travelling, or to circumvent the Great Firewall.
42. Staking on ‘Finney’ Testnet to Counter Sybil Attacks is now LIVE!!
 The Finney testnet was launched to avoid future Sybil attacks.
The Finney testnet was launched to avoid future Sybil attacks.
43. Implementing Zero Trust Security
 At its core, Zero Trust is an intuitive concept: assume that every device, user and network is compromised until proven otherwise.
At its core, Zero Trust is an intuitive concept: assume that every device, user and network is compromised until proven otherwise.
44. Top Technology Tips that Help HR Defend Against Security Threats
 Here we look into the best technology currently available that helps HR defend against all types of security threats.
Here we look into the best technology currently available that helps HR defend against all types of security threats.
45. 3 Key Takeaways from Biden’s Cybersecurity Executive Order
 Learn more about the consequences of Biden's Executive Order on Improving the Nation’s Cybersecurity on software vendors and government contractors.
Learn more about the consequences of Biden's Executive Order on Improving the Nation’s Cybersecurity on software vendors and government contractors.
46. Are the Increase in Cyberattacks Leading to an All-Out Cyber War?
 A look at the looming threat of cyberwar in the world stage of the Russia / Ukraine conflict
A look at the looming threat of cyberwar in the world stage of the Russia / Ukraine conflict
47. Spyse Introduction: Cybersecurity Search Engine for Data Gathering
 Data gathering has always been a long process which required multiple services running simultaneously and spending hours scanning alone. With new services like the Spyse search engine, these processes have been simplified drastically.
Data gathering has always been a long process which required multiple services running simultaneously and spending hours scanning alone. With new services like the Spyse search engine, these processes have been simplified drastically.
48. Unsafe use of target=”_blank”
 Developers have been frequently using this attribute to open a new webpage. But this attribute, though looks pretty simple, can create a major security threat to your application.
Developers have been frequently using this attribute to open a new webpage. But this attribute, though looks pretty simple, can create a major security threat to your application.
49. What Does Google's Third-Party Cookie Ban Mean to Your Privacy?
 Google is making the final push to completely ban third-party cookies on the most popular internet browser, Google Chrome, by 2022.
Google is making the final push to completely ban third-party cookies on the most popular internet browser, Google Chrome, by 2022.
50. Heightened Cyber Threat to the UK Healthcare Sector
 The second wave of coronavirus has crippled our lives as we strive to create a vaccine against this deadly pandemic. In such a troubled time, bad actors remain busy in targeting the healthcare sector, which is already struggling with multiple challenges and issues.
The second wave of coronavirus has crippled our lives as we strive to create a vaccine against this deadly pandemic. In such a troubled time, bad actors remain busy in targeting the healthcare sector, which is already struggling with multiple challenges and issues.
51. A Guide to Staying Safe on the Internet
 Now, more than ever, we must remain vigilant of the evolving threats brought about by cunning and mischievous hackers.
Now, more than ever, we must remain vigilant of the evolving threats brought about by cunning and mischievous hackers.
52. VPNs for beginners: what a VPN can and cannot do
 VPNs have become very popular in the last few years. Whether it’s the emergence of geographical restrictions, that VPNs help to bypass, or the evolution of cyber crime and privacy issues, — VPN market skyrocketed and is predicted to keep growing. This gave birth to a massive competition between VPN providers, and, sadly, some of them mislead their customers with false advertising and claims of security.
VPNs have become very popular in the last few years. Whether it’s the emergence of geographical restrictions, that VPNs help to bypass, or the evolution of cyber crime and privacy issues, — VPN market skyrocketed and is predicted to keep growing. This gave birth to a massive competition between VPN providers, and, sadly, some of them mislead their customers with false advertising and claims of security.
53. 5 Budget Christmas Presents for the Cybersecurity Pro You Know (And 5 Hacker ‘Luxury’ Items)
 You know how it goes. You're desperately trying to think of a good present for the hacker in your life. This list will give you the inspiration you need.
You know how it goes. You're desperately trying to think of a good present for the hacker in your life. This list will give you the inspiration you need.
54. Coronavirus, Cloud Computing and Cybersecurity: A Conversation with Dr. Arun Vishwanath
 As Chief Technologist for Avant Research Group in Buffalo, New York, and formerly as a professor at the University of Buffalo, Arun Vishnawath has spent his professional and academic career studying the “people problem” of cybersecurity.
As Chief Technologist for Avant Research Group in Buffalo, New York, and formerly as a professor at the University of Buffalo, Arun Vishnawath has spent his professional and academic career studying the “people problem” of cybersecurity.
His current research focuses on improving individual, organizational, and national resilience to cyber attacks by focusing on the weakest links in cybersecurity — Internet users.
55. On The UK's 'Big 4' Breakup, or: "Why Does the Consulting Market Exist?"
 Before we get into the nitty-gritty of this article, I'd like to briefly outline why I decided to write it. There are few key reasons:
Before we get into the nitty-gritty of this article, I'd like to briefly outline why I decided to write it. There are few key reasons:
56. How to Optimize Your Online Payment Process for Higher Conversion Effectively
 Ensure a simple and seamless payment process · Optimize security to better identify fraudulent transactions · Implement an omnichannel payment.
Ensure a simple and seamless payment process · Optimize security to better identify fraudulent transactions · Implement an omnichannel payment.
57. Bug Bounties: Battling Zero Day Vulnerabilities
 In the midst of the bear market and regular hacks, it seems like barely a week goes by without a headline declaring ‘crypto chaos’ and the end of web3.
In the midst of the bear market and regular hacks, it seems like barely a week goes by without a headline declaring ‘crypto chaos’ and the end of web3.
58. 5 Best Linux VPN Services: Take Control of Your Security
 Thanks to the rise of portable devices like the Steam Deck, Linux is gaining more popularity as an operating system than ever before. The platform is built by users, for users, aiming to give them complete control over the software and features on their machine. Unfortunately, this means they’ll have access to fewer popular applications that are available on Windows and Mac — possibly including VPNs. Those having trouble with figuring out how to start should take a look at the 5 best VPN services on Linux, though they might be surprised at how many options they truly have.
Thanks to the rise of portable devices like the Steam Deck, Linux is gaining more popularity as an operating system than ever before. The platform is built by users, for users, aiming to give them complete control over the software and features on their machine. Unfortunately, this means they’ll have access to fewer popular applications that are available on Windows and Mac — possibly including VPNs. Those having trouble with figuring out how to start should take a look at the 5 best VPN services on Linux, though they might be surprised at how many options they truly have.
59. Is Your Company Protected From Common Cyber Threats?
 Here is a list of some of the common threats in SME cybersecurity that are commonly overlooked.
Here is a list of some of the common threats in SME cybersecurity that are commonly overlooked.
60. Artificial Intelligence is No Match for Natural Stupidity
 A Lazy Introduction to AI for Infosec.
A Lazy Introduction to AI for Infosec.
61. Privacy Protection: How Secure is Telegram Messenger?
 Is Telegram messenger secure enough for private messages and group chats? Can Telegram protect the privacy of users? We did research on this.
Is Telegram messenger secure enough for private messages and group chats? Can Telegram protect the privacy of users? We did research on this.
62. Are Humans Really The Weakest Cybersecurity Link?
 Cyber Security is incomplete unless every individual puts efforts to achieve this and to make each employee work towards achieving Cybersecurity
Cyber Security is incomplete unless every individual puts efforts to achieve this and to make each employee work towards achieving Cybersecurity
63. The Noonification: Cyber Security vs Information Security (12/8/2022)
 12/8/2022: Top 5 stories on the Hackernoon homepage!
12/8/2022: Top 5 stories on the Hackernoon homepage!
64. Why Password Managers Ignore Input Fields - trial:by:fire
 Creating login fields that work with password managers isn't as easy as it seems.
Creating login fields that work with password managers isn't as easy as it seems.
65. Authentication And Authorization In .NET 5: How It Works
 In my 11 years as a developer, I have seen so many API's that have major security flaws. They either lack proper authentication or authorisation or both.
In my 11 years as a developer, I have seen so many API's that have major security flaws. They either lack proper authentication or authorisation or both.
66. WTF are VPN Protocols?
 Virtual Private Networks are compared in many aspects: some are judged by their speed, others by their server amount, and the reputation of all is put under the looking glass. However, only on rare occasion VPN protocols are brought into the light. And there are a few reasons for that.
Virtual Private Networks are compared in many aspects: some are judged by their speed, others by their server amount, and the reputation of all is put under the looking glass. However, only on rare occasion VPN protocols are brought into the light. And there are a few reasons for that.
67. Creating a Secure Mobile App: Main Vulnerabilities and Security Practices
 There are 2.87 million apps on the Google Play Store. it’s the responsibility of the app owner to make sure that all the data use properly.
There are 2.87 million apps on the Google Play Store. it’s the responsibility of the app owner to make sure that all the data use properly.
68. Know Your Enemy: How to Prepare and Respond to Insider Threats
 For cyber protection, organizations must pay attention to multiple digital risks, not least of which is an insider threat. Here's how to prepare and avoid those
For cyber protection, organizations must pay attention to multiple digital risks, not least of which is an insider threat. Here's how to prepare and avoid those
69. Protecting Your Online Privacy: 7 Simple Steps You Can Take Today
 What people wish to share is their prerogative, yet to unconsciously give away your private information is very different to making an active choice.
What people wish to share is their prerogative, yet to unconsciously give away your private information is very different to making an active choice.
70. I Hacked My Coffee Shop and Accessed My Data: Hacking Your Application May Be Easier Than You Think
 I noticed a suspicious behavior on the weekly email from my coffee shop's subscription; it was offering I edit my preferences directly through a dedicated link.
I noticed a suspicious behavior on the weekly email from my coffee shop's subscription; it was offering I edit my preferences directly through a dedicated link.
71. How The Smart Office is Revolutionizing the Workplace
 Smart offices are revolutionizing the workplace by introducing new technologies and tools that enable employees to be more productive and efficient.
Smart offices are revolutionizing the workplace by introducing new technologies and tools that enable employees to be more productive and efficient.
72. Secure Tokens are More Successful - Here's Why
 How important is security in the modern world? It is crucial, especially when it comes to finances, no matter the form. As the novelty of crypto assets starts w
How important is security in the modern world? It is crucial, especially when it comes to finances, no matter the form. As the novelty of crypto assets starts w
73. 10 Tips For Securing Zoom Meetings

74. Detecting & Preventing Insider Threats To Your Company: An Overview
 It’s commonly understood that the greatest risk to any organization
comes from the insider threat, no matter which industry or sector you work in.
It’s commonly understood that the greatest risk to any organization
comes from the insider threat, no matter which industry or sector you work in.
75. 5 Best VPN Services Supporting Multiple Devices
 Learn about the best VPNs with support for multiple devices!
Learn about the best VPNs with support for multiple devices!
76. 5 Reasons Why Businesses Should Invest In Cyber Security In 2019
 It is the 21st century, and life without internet is unimaginable. Social media has infiltrated all our households, and almost every second person has a cellphone. This virtual life has become as important as, if not more than real life. Needless to say, businessmen and businesswomen have capitalized on this raging internet obsession to not just advertise but also to scale their businesses.
It is the 21st century, and life without internet is unimaginable. Social media has infiltrated all our households, and almost every second person has a cellphone. This virtual life has become as important as, if not more than real life. Needless to say, businessmen and businesswomen have capitalized on this raging internet obsession to not just advertise but also to scale their businesses.
77. Our Industrial Infrastructure Is A Ticking Time Bomb
 It took one aquarium thermometer to steal 10GB of data from a Las Vegas casino. The adapter, which lacked basic security policies, was simply not on the security staff’s priority list. It was, however, on the hackers’.
It took one aquarium thermometer to steal 10GB of data from a Las Vegas casino. The adapter, which lacked basic security policies, was simply not on the security staff’s priority list. It was, however, on the hackers’.
78. You Share Your Birthday Online with Well-Wishers and Phishers
 I am sure you are so happy when you see the wall of congratulations on your Meta, or Linkedin feeds. Did you consider the risks of exposing your birthday?
I am sure you are so happy when you see the wall of congratulations on your Meta, or Linkedin feeds. Did you consider the risks of exposing your birthday?
79. Securing Web3 Communities: An Interview With Marcus Naughton of Chatsight
 A conversation with Marcus Naughton, CEO of Chatsight, on why web3 communities are being compromised and how this is hampering the domain’s progress.
A conversation with Marcus Naughton, CEO of Chatsight, on why web3 communities are being compromised and how this is hampering the domain’s progress.
80. Creating a Self-Signed Certificate from Scratch
 In today’s digital age, security is critical to any application. One way to enhance security is using SSL/TLS certificates to secure communications
In today’s digital age, security is critical to any application. One way to enhance security is using SSL/TLS certificates to secure communications
81. The Future of Mobile Apps: How AI, 5G, and Security Are Shaping the Industry
 Technology advancement is the future of mobile apps. Vladimir Potapenko, the founder of Madora, explains how AI, 5G, and security are shaping the industry.
Technology advancement is the future of mobile apps. Vladimir Potapenko, the founder of Madora, explains how AI, 5G, and security are shaping the industry.
82. Salts and Hashes

83. What the Heck Is Envelope Encryption in Cloud Security?
 If you are going deep into cloud security you may have seen the term “Envelope encryption”. Let’s explain the concept and why it is useful.
If you are going deep into cloud security you may have seen the term “Envelope encryption”. Let’s explain the concept and why it is useful.
84. Open Source Trading Platform Bancor Launches a $1M Bug Bounty
 As part of the lead-up to this release, Bancor has announced a $1 million bug bounty program for blockchain developers and white hat hackers.
As part of the lead-up to this release, Bancor has announced a $1 million bug bounty program for blockchain developers and white hat hackers.
85. Lay a strong foundation by writing secure C and C++ utilities
 Libraries and system utilities form the foundations on which larger projects are built. So it's critical to make sure they, in particular, are secure. That's why we recently introduced five new rules for C++ and C to detect broken authentication and access control in *nix systems. The new rules fall into three categories: account validity, granting permissions, and changing directories.
Libraries and system utilities form the foundations on which larger projects are built. So it's critical to make sure they, in particular, are secure. That's why we recently introduced five new rules for C++ and C to detect broken authentication and access control in *nix systems. The new rules fall into three categories: account validity, granting permissions, and changing directories.
86. How Identity Verification Is Advancing in a Remote Work World
 ID protection can never be a reactionary activity. It needs to remain proactive and innovative in order to keep remote workers safe.
ID protection can never be a reactionary activity. It needs to remain proactive and innovative in order to keep remote workers safe.
87. Why The Rubber Duck is The Ultimate Hacker Gadget
 The idea of rubber duck debugging is straightforward. When you are struggling with a problem, you simply ask the duck.
The idea of rubber duck debugging is straightforward. When you are struggling with a problem, you simply ask the duck.
88. Online Identity Theft: Learn How To Combat It
 Risk of becoming a victim of information theft and even online identity theft. In this article we help you find out how to stay safe
Risk of becoming a victim of information theft and even online identity theft. In this article we help you find out how to stay safe
89. Avast Secure Browser Gets Top Spot in AV-Comparatives' Anti-Phishing Protection Test
 Using Avast Secure Browser either as a primary or a secondary browser is easy and will give you a safer, and faster browsing experience across all your devices.
Using Avast Secure Browser either as a primary or a secondary browser is easy and will give you a safer, and faster browsing experience across all your devices.
90. 8 Most Important Cybersecurity Tricks Every Internet User Should Follow
 The cyber-world now accommodates billions of users. There are more than 4 billion internet users in the world today. It's just unfortunate that a large percentage of these users face cyber attacks from unknown sources. While some users are afraid of being attacked, others are ignorant of possible attacks. As an organisation or an individual that utilises the internet, it's a must to know some security tricks. If you're wondering what the tricks are, read on.
The cyber-world now accommodates billions of users. There are more than 4 billion internet users in the world today. It's just unfortunate that a large percentage of these users face cyber attacks from unknown sources. While some users are afraid of being attacked, others are ignorant of possible attacks. As an organisation or an individual that utilises the internet, it's a must to know some security tricks. If you're wondering what the tricks are, read on.
91. Getting started with Manual Content Discovery
 Understanding Robots.txt, Favicon, Sitemap.xml, HTML Headers and the Framework stack
Understanding Robots.txt, Favicon, Sitemap.xml, HTML Headers and the Framework stack
92. Best Practices for Key Security for Your Crypto Wallets
 Cryptographic keys are a requirement for any security system. They manage everything, including data encryption and decryption as well as user authentication.
Cryptographic keys are a requirement for any security system. They manage everything, including data encryption and decryption as well as user authentication.
93. Cyber Security: A Guide on Choosing a Reliable Service
 Nowadays, Cyber security is a trending topic around the globe. It has become a necessity for every business with the growing cyber threats.
Nowadays, Cyber security is a trending topic around the globe. It has become a necessity for every business with the growing cyber threats.
94. How to Ensure Your Software Supply Chain Is Secure for Business Innovation
 CloudBees' CISO Prakash Sethuraman discusses how to best secure your supply chain.
CloudBees' CISO Prakash Sethuraman discusses how to best secure your supply chain.
95. This Job Training Program Is Helping People With Autism Fight Cybercrime
 For the better part of a year, the 25-year-old wouldn’t respond when spoken to, his father said, and his blue, wide-set eyes revealed little cognition.
For the better part of a year, the 25-year-old wouldn’t respond when spoken to, his father said, and his blue, wide-set eyes revealed little cognition.
96. 3 Tips on How to Stay Safe in Your Everyday Cyber Life
 Remember your mom always repeating "stay safe" phrase? Well, you should stay safe! Not only in streets, but also in cyberspace.
Remember your mom always repeating "stay safe" phrase? Well, you should stay safe! Not only in streets, but also in cyberspace.
97. Cybersecurity Lessons from the Netflix Series La Casa De Papel
 Can a TV show teach us how to take more care of our cybersecurity?
Can a TV show teach us how to take more care of our cybersecurity?
98. "Hackers Need To Get Lucky Only Once" - Excerpts on Fighting Crypto Hacks, Theft and Fraud
 What do trust & safety leaders expect in 2022 with the rise of blockchain and crypto? Find out why next year is the year for compliance, regtech, trust & safety
What do trust & safety leaders expect in 2022 with the rise of blockchain and crypto? Find out why next year is the year for compliance, regtech, trust & safety
99. 5 Popular Professions in Cybersecurity
 Cybersecurity jobs are valuable in 2022 because of an increased number of hacks. Among the top cybersecurity jobs are anti-fraud analyst and reverse engineer.
Cybersecurity jobs are valuable in 2022 because of an increased number of hacks. Among the top cybersecurity jobs are anti-fraud analyst and reverse engineer.
100. The Gist of NIST: Password Recommendations to Remember
 NIST Guidelines have changed over the years so it is important to keep up with the changes. Password recommendations, such as eliminating special character use.
NIST Guidelines have changed over the years so it is important to keep up with the changes. Password recommendations, such as eliminating special character use.
101. How To Be Sure That Your Information Is Secure In Dating Apps
 Online dating has become really popular nowadays. Unfortunately, dating websites and apps are often visited by scammers, criminals, violent abusers, and sexual predators. And the lack of proper identity verification procedure in the dating apps is very surprising. In this article I will explain how dating apps can protect their users.
Online dating has become really popular nowadays. Unfortunately, dating websites and apps are often visited by scammers, criminals, violent abusers, and sexual predators. And the lack of proper identity verification procedure in the dating apps is very surprising. In this article I will explain how dating apps can protect their users.
102. Startup Interview with Tracie Thompson, HackHunter CEO
 HackHunter was nominated as one of the best startups in Docklands, Australia in in HackerNoon’s Startup of the Year. This is interview with their CEO.
HackHunter was nominated as one of the best startups in Docklands, Australia in in HackerNoon’s Startup of the Year. This is interview with their CEO.
103. 5 Best VPN Services With No Lag
 One of the hardest parts about choosing a VPN is finding one that won’t impact the speed of your online connection. VPNs reroute your traffic through distant servers, making any online requests or downloads take longer than they usually would no matter what. Some services are better about this than others, mostly by providing a massive number of servers that users can test to find the fastest connection while keeping their privacy secure. Those looking for the best of both worlds should consider checking out the 5 best VPN services with no lag — or, at least, as little lag as possible.
One of the hardest parts about choosing a VPN is finding one that won’t impact the speed of your online connection. VPNs reroute your traffic through distant servers, making any online requests or downloads take longer than they usually would no matter what. Some services are better about this than others, mostly by providing a massive number of servers that users can test to find the fastest connection while keeping their privacy secure. Those looking for the best of both worlds should consider checking out the 5 best VPN services with no lag — or, at least, as little lag as possible.
104. Understanding XDR in Security - Advantages and Use Cases
 XDR takes raw data that is set up in the environment and picks up bad actors that are taking advantage of software to help get into the system.
XDR takes raw data that is set up in the environment and picks up bad actors that are taking advantage of software to help get into the system.
105. You Probably Don't Need OAuth2/OpenID Connect: Here's Why
 And the great news is, if the need for OAuth2 and OpenID Connect arises, you can use Ory again to add these on top!
And the great news is, if the need for OAuth2 and OpenID Connect arises, you can use Ory again to add these on top!
106. 5 Best VPN Services for Chromebook
 A Chromebook is very useful to have when out and about. It combines the best features of a tablet and laptop, allowing for maximum portability and functionality. However, this portability can lead to some problems with security, as users might be tempted to connect to open networks. Malicious hackers might try to use those networks to steal sensitive information and launch attacks, making such connections especially risky. Anyone looking to maximize their security on the go should consider checking out the 5 best VPN services for Chromebook.
A Chromebook is very useful to have when out and about. It combines the best features of a tablet and laptop, allowing for maximum portability and functionality. However, this portability can lead to some problems with security, as users might be tempted to connect to open networks. Malicious hackers might try to use those networks to steal sensitive information and launch attacks, making such connections especially risky. Anyone looking to maximize their security on the go should consider checking out the 5 best VPN services for Chromebook.
107. Top Seven Cyber Security Trends Right Now

108. Using More Than One Multi-Factor Authentication Tool Yields Frictionless Results
 Multi-factor Authentication is considered a cybersecurity best practice. Whichever MFA options you choose should be frictionless, low risk, and low cost.
Multi-factor Authentication is considered a cybersecurity best practice. Whichever MFA options you choose should be frictionless, low risk, and low cost.
109. Endpoint Security Series: Principles to Determine the Optimal Endpoint Security Solution
 Threat actors are becoming more and more sophisticated in their ability to exploit vulnerabilities, breach organizations’ IT infrastructures, and hack into data
Threat actors are becoming more and more sophisticated in their ability to exploit vulnerabilities, breach organizations’ IT infrastructures, and hack into data
110. Rock Solid Splunk or How I Learned to Love Splunk Validated Architectures
 The Splunk Validate Architectures are a professionally designed Splunk architecture intended to be deployed easily by the customer without expert assistance.
The Splunk Validate Architectures are a professionally designed Splunk architecture intended to be deployed easily by the customer without expert assistance.
111. MetaMask Users Targeted By Phishing Attack Impersonating Popular Metaverse Projects
 MetaMask users are being targeted in a series of phishing attacks where hackers impersonate popular metaverse project websites.
MetaMask users are being targeted in a series of phishing attacks where hackers impersonate popular metaverse project websites.
112. How to Keep Mission-Critical Business Data Secure in the Mobile Age
 Andrew Nichols | Protecting Mission-Critical Business Data in the Mobile Age
Andrew Nichols | Protecting Mission-Critical Business Data in the Mobile Age
113. How We Can Make The Modern Web Experience More Secure

114. How Much Does the CEH Exam Cost?
 EC-Council’s Certified Ethical Hacker (CEH) is one of the most established and recognized offensive security certifications. The certification is ANSI-accredited and DoDD 8140-approved because of which the certification in highly valued by security professionals from both the public and private sectors. Since CEH is the gold standard for validating offensive security skills, the CEH certification cost is around $1,199 and the cost to retake the exam is $450. This article will cover the various processes you have to go through to earn this certification as well as the associated costs.
EC-Council’s Certified Ethical Hacker (CEH) is one of the most established and recognized offensive security certifications. The certification is ANSI-accredited and DoDD 8140-approved because of which the certification in highly valued by security professionals from both the public and private sectors. Since CEH is the gold standard for validating offensive security skills, the CEH certification cost is around $1,199 and the cost to retake the exam is $450. This article will cover the various processes you have to go through to earn this certification as well as the associated costs.
115. Security and AI: How to Make Sure DevSecOps Delivers Results
 Software and systems are the backbone of most organizations. When an application fails or a system is breached, it can lead to dire loss and harm.
Software and systems are the backbone of most organizations. When an application fails or a system is breached, it can lead to dire loss and harm.
116. Your Website Knows Where Your Users Are—But Is It Keeping That Data Secret?

117. How Do I know if My Phone has been Hacked?
 Our smartphones are our lives. We do everything on them and
spend a lot of time. All major mobile phone manufacturers and application
developers had to start introducing digital health features to curb our
addiction.
Our smartphones are our lives. We do everything on them and
spend a lot of time. All major mobile phone manufacturers and application
developers had to start introducing digital health features to curb our
addiction.
118. 3 Impressive Cyberattacks of 2020: What we Can Learn From Them
 When it comes to cyberattacks, everybody is at risk, whether it be big corporations, government bodies, small businesses, or private individuals.
When it comes to cyberattacks, everybody is at risk, whether it be big corporations, government bodies, small businesses, or private individuals.
119. The Essential Guide to Security and Compliance for the Public Cloud
 Using an Infrastructure-as-a-Service provider makes it easier to achieve and maintain compliance, but here are some caveats to consider.
Using an Infrastructure-as-a-Service provider makes it easier to achieve and maintain compliance, but here are some caveats to consider.
120. Automatically Scan Your Project Dependencies for Vulnerabilities Using Docker, Jenkins (Part 1/2)
 Find out how to automatically check your software projects for potential vulnerabilities caused by 3rd party code.
Find out how to automatically check your software projects for potential vulnerabilities caused by 3rd party code.
121. Data Leak of $1B “Tech Unicorn” Gorillas Shows How Far Venture Capital Has Fallen
 VC money is spilling out onto the streets, and despite millions of dollars of investment tech companies still neglect their security.
VC money is spilling out onto the streets, and despite millions of dollars of investment tech companies still neglect their security.
122. Proxy Vs. VPN: What Is Better For Data Protection in 2020
 If you are alive and functioning as a member of society in 2020, chances are you've used a VPN (Virtual Private Network) or a proxy server in the past. It may have been to stream a sports channel not available in your home country, to gain access to a foreign website, or to overcome the one-vote-per-IP address challenges associated with having multiple people in one household trying to do the same thing online.
If you are alive and functioning as a member of society in 2020, chances are you've used a VPN (Virtual Private Network) or a proxy server in the past. It may have been to stream a sports channel not available in your home country, to gain access to a foreign website, or to overcome the one-vote-per-IP address challenges associated with having multiple people in one household trying to do the same thing online.
123. Protect Yourself Against The 440% Increase in Shipping-Related Phishing Emails
 The CDC (The Centers for Disease Control and Prevention) classified “shopping at crowded stores just before, on or after Thanksgiving” on its list
The CDC (The Centers for Disease Control and Prevention) classified “shopping at crowded stores just before, on or after Thanksgiving” on its list
124. #Mythbusting the Top 4 Misconceptions about Fintech
 The world of finance is a very diverse and constantly changing environment that combines tradition and innovation. On the one hand, we have conventional financial mediums like fiat money, precious metals, and stocks that have been well tested during recent centuries (some of them even longer).
The world of finance is a very diverse and constantly changing environment that combines tradition and innovation. On the one hand, we have conventional financial mediums like fiat money, precious metals, and stocks that have been well tested during recent centuries (some of them even longer).
125. Why Private Search Engines Are The Future...
 Private search engines aren't just for people wearing tinfoil hats anymore. Over the years these search engines have improved their search results and added new features to make the experience better for their users.
Private search engines aren't just for people wearing tinfoil hats anymore. Over the years these search engines have improved their search results and added new features to make the experience better for their users.
126. The first time I quit my second startup
 This is the story of Online Identity as I see it.
This is the story of Online Identity as I see it.
127. How to Secure Your Applications
 The CTO of a neo-brokerage FinTech shares tips on how to secure your app -from the front end to the backend. He also recommends tools to use in SDD lifecycle.
The CTO of a neo-brokerage FinTech shares tips on how to secure your app -from the front end to the backend. He also recommends tools to use in SDD lifecycle.
128. How Can We Expose Cyber Criminals Through Identity Attribution
 As we approach the dawn of another year, the cybersecurity world faces a strange dilemma- organized crime. Throughout the course of recent years, cybercrimes have grown increasingly sophisticated, primarily because of the rise in prominence of technologies such as machine learning, and the growing amalgamation of artificial intelligence within enterprises.
As we approach the dawn of another year, the cybersecurity world faces a strange dilemma- organized crime. Throughout the course of recent years, cybercrimes have grown increasingly sophisticated, primarily because of the rise in prominence of technologies such as machine learning, and the growing amalgamation of artificial intelligence within enterprises.
129. The Most Common Mistakes to Avoid in the Crypto World
 Blockchain technology is the best gift of modern computer science and technology but you also need to understand its limitations.
Blockchain technology is the best gift of modern computer science and technology but you also need to understand its limitations.
130. Jwenky: An Express API Server with User Authentication
 Jwenky is an API server coded in Express framework.
Jwenky is an API server coded in Express framework.
131. The Relevance of Infrastructure-as-Code Concepts in Security
 So what is Infrastructure-as-Code (IaC) anyway? IaC is a process that automates the provisioning and management of cloud resources.
So what is Infrastructure-as-Code (IaC) anyway? IaC is a process that automates the provisioning and management of cloud resources.
132. What Is a VPN and What Are Its Alternatives?
 Are VPNs really essential for an average user in 2021? Read on to find out about common issues with VPNs, as well as possible alternatives to them.
Are VPNs really essential for an average user in 2021? Read on to find out about common issues with VPNs, as well as possible alternatives to them.
133. The Highest Paying Jobs in Cyber Security
 Get the latest popular cyber jobs with the highest salaries in the world with a complete guide about them with the profile information
Get the latest popular cyber jobs with the highest salaries in the world with a complete guide about them with the profile information
134. The Largest Data Breaches in History
 A look at where the largest data breaches have occurred across the world.
A look at where the largest data breaches have occurred across the world.
135. Biting Back Against Phishers
 How one company learned to deal with Phishing attempts that tried to compromise their cybersecurity system and how they learned to fight back against them.
How one company learned to deal with Phishing attempts that tried to compromise their cybersecurity system and how they learned to fight back against them.
136. 5 Popular Types of Penetration Testing for SaaS Businesses
 If you are running a SaaS business, you know that security is everything. Nowadays, we can see many different cyberattacks and their variants targeting SaaS.
If you are running a SaaS business, you know that security is everything. Nowadays, we can see many different cyberattacks and their variants targeting SaaS.
137. Top Seven Cyber Security Trends Right Now

138. The Evolution Of Hacking Data Storage [Infographic]
 When the first computers were made, the information needed to run them was on punch cards. The computing device would decode the patterns on the punch cards and translate it to an action. It wasn’t until 1956 that IBM came up with the first magnetic hard drive, and floppy discs didn’t enter the scene until the 1960s. Early computer storage was rudimentary, which is why there was no real viable threat of hackers in those early decades of computing. Once data storage became more sophisticated, hackers became a real threat. Subsequently, the need for cyber protection was born.
When the first computers were made, the information needed to run them was on punch cards. The computing device would decode the patterns on the punch cards and translate it to an action. It wasn’t until 1956 that IBM came up with the first magnetic hard drive, and floppy discs didn’t enter the scene until the 1960s. Early computer storage was rudimentary, which is why there was no real viable threat of hackers in those early decades of computing. Once data storage became more sophisticated, hackers became a real threat. Subsequently, the need for cyber protection was born.
139. What Is a CA Bundle in SSL and Why Is It Important?
 Don't know what a CA bundle is? Discover how to use its powerful SSL encryption for secure web server-browser communication, why it's important, and more!
Don't know what a CA bundle is? Discover how to use its powerful SSL encryption for secure web server-browser communication, why it's important, and more!
140. Dungeons and Disaster Recovery: Tabletop Exercises for IT Training
 Tabletop scenarios are a great, and under-used tool for training and preparing for crises. They're engaging, easy to use, and budget-friendly.
Tabletop scenarios are a great, and under-used tool for training and preparing for crises. They're engaging, easy to use, and budget-friendly.
141. The Hidden Security Risks of QR Codes
 In our current contactless society, QR codes are having a day in the sun. Many restaurants are now letting customers scan QR codes at the table to access digital menus. Some restaurant owners say digital menus may be around long past the current pandemic. But as QR codes are gaining wider adoption, it's important to understand the security risks.
In our current contactless society, QR codes are having a day in the sun. Many restaurants are now letting customers scan QR codes at the table to access digital menus. Some restaurant owners say digital menus may be around long past the current pandemic. But as QR codes are gaining wider adoption, it's important to understand the security risks.
142. The Benefits of SSL Certificates on SEO & Organic Traffic
 Google takes over 200 various factors for determining the website rankings in a SERP. One of the key and crucial factors is website security. If you want your website to be displayed higher in SERPs, then you must give due importance to the online security of users who’ll be visiting your site.
Google takes over 200 various factors for determining the website rankings in a SERP. One of the key and crucial factors is website security. If you want your website to be displayed higher in SERPs, then you must give due importance to the online security of users who’ll be visiting your site.
143. The Rudiments Of Smart Contract Vulnerabilities
 We've seen smart contracts give DeFi the ultimate edge over CeFi. However, being a new technology, it has been subjected to many vulnerabilities.
We've seen smart contracts give DeFi the ultimate edge over CeFi. However, being a new technology, it has been subjected to many vulnerabilities.
144. New Generation OSINT Framework
 This is an introductory article regarding on of the newest OSINT platform ThreatCops and its various interesting features and perks for identity protection.
This is an introductory article regarding on of the newest OSINT platform ThreatCops and its various interesting features and perks for identity protection.
145. An Introduction to Adversarial Attacks and Defense Strategies
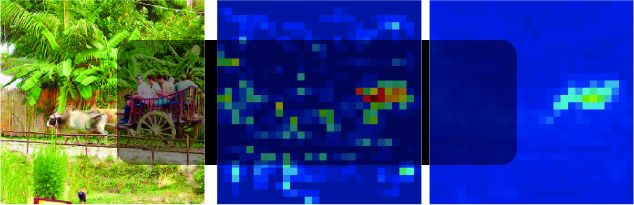 Adversarial training was first introduced by Szegedy et al. and is currently the most popular technique of defense against adversarial attacks.
Adversarial training was first introduced by Szegedy et al. and is currently the most popular technique of defense against adversarial attacks.
146. The 5 Most Common Types of Cybercrime in 2022 - And How to Defend Yourself
 Taking a look at the 5 most common types of cybercrime in 2022 and how to defend yourself
Taking a look at the 5 most common types of cybercrime in 2022 and how to defend yourself
147. Digital Identities: The Value of Automation In Enterprise Security
 Digital identities are of crucial importance for cybersecurity of modern enterprises. Let's find out what changes can be expected in the domain of web security.
Digital identities are of crucial importance for cybersecurity of modern enterprises. Let's find out what changes can be expected in the domain of web security.
148. Security Training is Now a Software Developer's Daily Responsibility
 Digital data is the new gold, and hackers will stop at nothing to get yours. In a study by cybersecurity experts at Maryland University, researchers found that cyber-attacks happen once every 39 seconds.
Digital data is the new gold, and hackers will stop at nothing to get yours. In a study by cybersecurity experts at Maryland University, researchers found that cyber-attacks happen once every 39 seconds.
149. How to Solve the Frontrunning Vulnerability in Smart Contracts
 This blog post describes the frontrunning vulnerability in Solidity smart contracts and how this can be prevented. Read on to find out more…
This blog post describes the frontrunning vulnerability in Solidity smart contracts and how this can be prevented. Read on to find out more…
150. 3 Methods to Secure Your AWS Cloud Infrastructure
 79% of surveyed firms have recently experienced a cloud data breach. In this article, we examined various recommended practices that can help you stay safe.
79% of surveyed firms have recently experienced a cloud data breach. In this article, we examined various recommended practices that can help you stay safe.
151. COVID-19: Five Steps to Protect Against Possible Cyber Attacks

152. 4 Signs You Make it Easy For Someone to Hack You
 Hacking can happen on any device and to any person—and hackers are only getting smarter by the minute.
Hacking can happen on any device and to any person—and hackers are only getting smarter by the minute.
153. Here's What I Found on Scanning 2.6 Million Domains for Exposed Git Directories
 A scan of over 2.6 million domains revealed over 1000 publicly exposed git directories. Next to complete source code I found many credentials and api secrets.
A scan of over 2.6 million domains revealed over 1000 publicly exposed git directories. Next to complete source code I found many credentials and api secrets.
154. Businesses Will Face These 4 Cloud Security Challenges in 2021
 As threats have sophisticated and evolved, new attacks emerge and it becomes more important than ever for businesses to embrace security first mentalities.
As threats have sophisticated and evolved, new attacks emerge and it becomes more important than ever for businesses to embrace security first mentalities.
155. 5 Apps to Monitor Your Kids Online Activity Without Them Knowing
 Dealing with real-life problems has always been challenging, but now, you must know how to deal with digital negative consequences, or your kids can interact with digital dangers. Parents often do not take the internet dangers seriously, and their children have to face such issues later. You can also make many things possible using technology, but if you know how to make everything possible.
Dealing with real-life problems has always been challenging, but now, you must know how to deal with digital negative consequences, or your kids can interact with digital dangers. Parents often do not take the internet dangers seriously, and their children have to face such issues later. You can also make many things possible using technology, but if you know how to make everything possible.
156. Best Practices for API Security

Yet, its open doors and wide visibility makes it vulnerable to attacks. Also, attackers can easily find the way to the heart of applications and systems via APIs. Hence it is essential to fence APIs with all possible measures.
157. Keeping Your Smartphone Data Safe in the Age of Remote Work
 Let’s take a look at how businesses can encourage employees to better look after their data securely while on the go.
Let’s take a look at how businesses can encourage employees to better look after their data securely while on the go.
158. Cyber Warfare, Self-Defense and the Defender’s Dilemma
 After pondering, researching, and a few glasses of wine, I've decided to do an analysis on cyber warfare.
After pondering, researching, and a few glasses of wine, I've decided to do an analysis on cyber warfare.
159. Password Managers Should be A Mandatory Part of Everyone’s Digital Life

160. America's Digital Maginot Line
 America's critical infrastructure appears to be protected by a Digital Maginot Line
America's critical infrastructure appears to be protected by a Digital Maginot Line
161. How To Start A Career in Cyber Security?
 As we move forward into the age of technology, and as business people, there is one that should always remember. That thing is simply this; the more advanced technology gets, the more danger there is when it comes to cyber threats.
As we move forward into the age of technology, and as business people, there is one that should always remember. That thing is simply this; the more advanced technology gets, the more danger there is when it comes to cyber threats.
162. How to Handle Injection Attacks With JavaScript - Fighting Unauthorized Access
 There are certain cyberattacks, like attackers trying to inject data from the front-end, that you can guard against with some regular JavaScript best practices.
There are certain cyberattacks, like attackers trying to inject data from the front-end, that you can guard against with some regular JavaScript best practices.
163. What Is Passwordless Authentication and How Does It Work? The Magic of FIDO2 and U2F Standards
 Logging into a website or service using the traditional username and password combination isn’t the best or safest way of going about it anymore.
Logging into a website or service using the traditional username and password combination isn’t the best or safest way of going about it anymore.
164. 6 Tips for Software Developers to Enhance Software Security
 Avoid making common security mistakes that make your software vulnerable to attack. As a developer, you’re certainly aware of the importance of following security best practices. But many times, we miss certain things, maybe because it hasn’t become second nature to us yet. Unfortunately, we realize only after a security issue has arisen, and it’s marked on our brains like a spot of indelible ink.
Avoid making common security mistakes that make your software vulnerable to attack. As a developer, you’re certainly aware of the importance of following security best practices. But many times, we miss certain things, maybe because it hasn’t become second nature to us yet. Unfortunately, we realize only after a security issue has arisen, and it’s marked on our brains like a spot of indelible ink.
165. Why Vulnerability Detection is Important in the IT Space
 A look at why vulnerability detection is important in the it space
A look at why vulnerability detection is important in the it space
166. Top Penetration Testing Companies and Tools
 Penetration testing, or 'pen tests' as they are colloquially known, basically consist of a hack or cyber-attack on one's system.
Penetration testing, or 'pen tests' as they are colloquially known, basically consist of a hack or cyber-attack on one's system.
167. What an IP Address Can Reveal About You
 Is it possible to trace an IP ? To what extent does it reveal your physical location? How to prevent your IP from being tracked? Let's learn more about IP.
Is it possible to trace an IP ? To what extent does it reveal your physical location? How to prevent your IP from being tracked? Let's learn more about IP.
168. 3 Benefits of Zero Trust to Customer Information Security
 Cyber-security threats can come from both outside as well as inside an organization. They can also start from a single point and spread out. This is why adopting a “never trust, always verify” approach to security can help organizations shield against the bad guys in a more robust manner.
Cyber-security threats can come from both outside as well as inside an organization. They can also start from a single point and spread out. This is why adopting a “never trust, always verify” approach to security can help organizations shield against the bad guys in a more robust manner.
169. AI's Impact on Cybersecurity in 2023
 AI is revolutionizing cybersecurity in 2023 by detecting and responding to threats in real-time, identifying vulnerabilities, and enhancing defense.
AI is revolutionizing cybersecurity in 2023 by detecting and responding to threats in real-time, identifying vulnerabilities, and enhancing defense.
170. How Nonprofits can Protect Themselves Against Getting Hacked
 Hacking is a serious problem for nonprofits. When a hacker attacks, it's not just the nonprofit's information that they want, but donors' information
Hacking is a serious problem for nonprofits. When a hacker attacks, it's not just the nonprofit's information that they want, but donors' information
171. How Employees Can Help Prevent Cybersecurity Threats
 Employees need to be aware of the significance of cyber security because cyber dangers have persisted since the creation of the internet.
Employees need to be aware of the significance of cyber security because cyber dangers have persisted since the creation of the internet.
172. Reducing Security Risks for Remote Workers
 With the pandemic most people go to home office, teleworking, remote working or whatever you call it... For chief security officers this is a really big new challenge.
With the pandemic most people go to home office, teleworking, remote working or whatever you call it... For chief security officers this is a really big new challenge.
173. Cyber Threat From Electric Vehicles Cannot Be Ignored
 Reduce EV cyber threats by taking care at public charging stations, installing two-factor authentication, getting repairs from authorized mechanics, and more.
Reduce EV cyber threats by taking care at public charging stations, installing two-factor authentication, getting repairs from authorized mechanics, and more.
174. Cybersecurity and the Metaverse: Guardians of the New Digital World
 A metaverse is a virtual reality space in which users can interact with one another in a computer-generated environment.
A metaverse is a virtual reality space in which users can interact with one another in a computer-generated environment.
175. Darkweb Community MagBO Sells Data Stolen From Over 20k Websites
 MagBO, the Russian-speaking dark web marketplace for trading in backdoored websites, continues to grow exponentially. In less than two years, the collection of leaks grew from around 3,000 in September 2018 to 26,605 in February 2020.
MagBO, the Russian-speaking dark web marketplace for trading in backdoored websites, continues to grow exponentially. In less than two years, the collection of leaks grew from around 3,000 in September 2018 to 26,605 in February 2020.
176. Phishing: Top Threat to Our Online Security
 Phishing is a cheap technique for hackers to steal the victim’s data. Now I am telling you because it really happened to me. It took my most online privacy.
Phishing is a cheap technique for hackers to steal the victim’s data. Now I am telling you because it really happened to me. It took my most online privacy.
177. Ledger Nano S Plus guide
 A detailed guide on how to use an hardware wallet to protect our crypto and tokens
A detailed guide on how to use an hardware wallet to protect our crypto and tokens
178. 3 Tech-Driven Solutions Turning the Tide Against eCommerce Fraud
 The COVID-19 pandemic fed a wave of eCommerce fraud. Here are the high-tech solutions the industry is using to fight back.
The COVID-19 pandemic fed a wave of eCommerce fraud. Here are the high-tech solutions the industry is using to fight back.
179. Finding Threat Actors in the Dark
 Should dark web threat intelligence be automated?
Should dark web threat intelligence be automated?
180. What are Insecure Direct Object References (IDOR)?
 IDOR is a simple bug that packs a punch. Discover where they’re most common, explore real-world examples, and learn prevention tips from hackers.
IDOR is a simple bug that packs a punch. Discover where they’re most common, explore real-world examples, and learn prevention tips from hackers.
181. 5 Reasons Why Your Business Needs a Cyber Security Consultant
 There are reports of cyber attacks almost every single week.
There are reports of cyber attacks almost every single week.
182. 5 ML Security Challenges Demanding our Unwavering Attention
 As per Gartner, almost 80 percent of every emerging technology will have Artificial Intelligence as the backbone by the end of 2021. Building secure software is a no mean feat. Amid the lingering cybersecurity threats and the potential challenges posed by the endpoint inadequacies, the focus is continuously shifting towards machine learning and the relevant AI implementations for strengthening the existing app and software security standards.
As per Gartner, almost 80 percent of every emerging technology will have Artificial Intelligence as the backbone by the end of 2021. Building secure software is a no mean feat. Amid the lingering cybersecurity threats and the potential challenges posed by the endpoint inadequacies, the focus is continuously shifting towards machine learning and the relevant AI implementations for strengthening the existing app and software security standards.
183. 4 Essential Steps to Protect Your Digital Privacy
 Connecting to public WiFi may be unavoidable but it does bring some security risks. These four steps can help protect your data privacy when connected to such.
Connecting to public WiFi may be unavoidable but it does bring some security risks. These four steps can help protect your data privacy when connected to such.
184. 5 Types of Cyber Security and Why It’s Important to be Aware of Them
 Cybersecurity is the process of protecting systems, networks, and programs from malicious attacks. But why is it important? Let’s find out.
Cybersecurity is the process of protecting systems, networks, and programs from malicious attacks. But why is it important? Let’s find out.
185. PCI DSS – Compliance Requirements and How to Meet Them
 Is your business involved in any type of payment card processing? Then you need to be aware of the PCI DSS requirements. In this article, we take a closer look at some of the requirements defined by PCI DSS and show how they can be met.
Is your business involved in any type of payment card processing? Then you need to be aware of the PCI DSS requirements. In this article, we take a closer look at some of the requirements defined by PCI DSS and show how they can be met.
186. Top Signs that Indicate You Are About To Suffer a Cyber Breach
 There are few things worse than being told that your business’s security has been compromised. Organizations might not know that a security breach is taking place, or has been for some time. Yet, risk mitigation and technical safeguards are always getting better.
There are few things worse than being told that your business’s security has been compromised. Organizations might not know that a security breach is taking place, or has been for some time. Yet, risk mitigation and technical safeguards are always getting better.
187. 7 Best DevOps Security Practices: DevSecOps and Its Merits
 DevOps has transformed the way operational engineers and software developers reason. Gone are the days when a code was written, implemented, and managed by operations. The DevOps model has remodeled the system of product and application production. As a result, faster results have become the pinnacle of delivering at the speed which the market demands.
DevOps has transformed the way operational engineers and software developers reason. Gone are the days when a code was written, implemented, and managed by operations. The DevOps model has remodeled the system of product and application production. As a result, faster results have become the pinnacle of delivering at the speed which the market demands.
188. How Keyloggers Can Help to Protect Employees in Your Organisation
 Additionally, software (keyloggers) can also be used to detect and prevent cyber-attacks.
Additionally, software (keyloggers) can also be used to detect and prevent cyber-attacks.
189. Why Security Awareness Training Must Include Identifying Deepfakes
 Deepfakes will cause damages of over $250 million in 2020. That was the stark prediction made by Jeff Pollard, the top analyst at Forrester. While deepfakes are nothing new, the way they’re being used is.
Deepfakes will cause damages of over $250 million in 2020. That was the stark prediction made by Jeff Pollard, the top analyst at Forrester. While deepfakes are nothing new, the way they’re being used is.
190. Using a Passive Vulnerability Scan To Identify Website Security Risks
 A passive vulnerability scan is a type of security scan in which the scanner sends no unusual requests to the server. It is like a visitor browsing the site.
A passive vulnerability scan is a type of security scan in which the scanner sends no unusual requests to the server. It is like a visitor browsing the site.
191. 4 Things Humans NEED in an AI-Led World
 As the world moves forward, those working with AI — meaning almost all of us — need to take the ethical matter into our own hands.
As the world moves forward, those working with AI — meaning almost all of us — need to take the ethical matter into our own hands.
192. Passwordless vs MFA: The Future of Authentication
 A passwordless approach is not the end-all-be-all for data security, but it is the start of establishing a single, strong user identity and trust.
A passwordless approach is not the end-all-be-all for data security, but it is the start of establishing a single, strong user identity and trust.
193. Securing Engineer Access to Cloud Environments with Zero Trust
 Remote working and developer infrastructure in the cloud have both served to change the way developer operations work and have new cybersecurity requirements.
Remote working and developer infrastructure in the cloud have both served to change the way developer operations work and have new cybersecurity requirements.
194. Top Bug Bounty Programmes You Can Participate in Today
 A curated list of bug bounty programs for bug bounty hunters to help them get first bug bounty on vulnerability report.
A curated list of bug bounty programs for bug bounty hunters to help them get first bug bounty on vulnerability report.
195. How to Fix Your Broken Vulnerability Management
 CVSS scores are broken measures of vulnerability criticality. SSVC is a viable solution to the problems created by CVSS scoring when used in isolation.
CVSS scores are broken measures of vulnerability criticality. SSVC is a viable solution to the problems created by CVSS scoring when used in isolation.
196. How to Protect Yourself Against Smishing Attacks
 As the threat landscape encapsulating organizations and companies grows increasingly sophisticated, and harbors a growing number of threats and vulnerabilities- organizations are getting more accustomed to commonplace scams such as phishing.
As the threat landscape encapsulating organizations and companies grows increasingly sophisticated, and harbors a growing number of threats and vulnerabilities- organizations are getting more accustomed to commonplace scams such as phishing.
197. Network Detection and Response: the Future of Cybersecurity
 A look at how network detection and response is the future of cyber security
A look at how network detection and response is the future of cyber security
198. When Did Cyber Security Start?
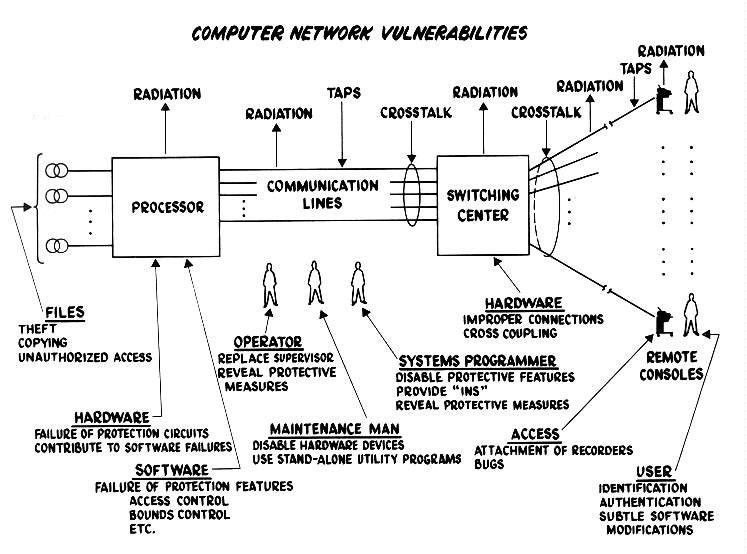 Cybersecurity began between 1970 and 1972 with the publications of the Ware and Anderson reports. The Ware Report set out a number of different security control
Cybersecurity began between 1970 and 1972 with the publications of the Ware and Anderson reports. The Ware Report set out a number of different security control
199. What Startups Can Learn From 5 Security Trends that Didn’t Exist 5 Years Ago
 Technology is evolving at an incredibly fast pace. An analog world wasn’t that long ago, when phones stayed on the wall, the internet was in its infancy, and seamless global connection seemed distant. Yet now we can summon cars from the mini computers in our pockets, jump on a real-time video call with someone across the world, and have our refrigerators order our groceries.
Technology is evolving at an incredibly fast pace. An analog world wasn’t that long ago, when phones stayed on the wall, the internet was in its infancy, and seamless global connection seemed distant. Yet now we can summon cars from the mini computers in our pockets, jump on a real-time video call with someone across the world, and have our refrigerators order our groceries.
200. Password Security in 2022 — A Complete Guide
 A comprehensive guide to password security for all IT managers (and everyone else!). Learn why it is important, the risks of insecure passwords and how you can
A comprehensive guide to password security for all IT managers (and everyone else!). Learn why it is important, the risks of insecure passwords and how you can
201. The Battle of the Best: Hashing vs Encryption
 Encryption and hashing are different in terms of web security, purpose, length, and direction. Read on to know more about hashing vs encryption in detail.
Encryption and hashing are different in terms of web security, purpose, length, and direction. Read on to know more about hashing vs encryption in detail.
202. In a Time of Crisis, Data Must Be Able to Defend Itself

203. How to Staff a Pentest: The Importance of Matching Resources to Requirements

204. Is Your ERP the Target of Cyber Criminals? How to Prevent this Attack
 ERP systems are complex solutions that handle business-critical processes and manage sensitive data. These factors alone are enough to make them an attractive target for cybercriminals. Despite it being common knowledge, businesses often opt for simpler and cheaper solutions that do not address the issue at the system level. Below is an in-depth look at the main factors that erode corporate cybersecurity and ways to prevent cyberattacks.
ERP systems are complex solutions that handle business-critical processes and manage sensitive data. These factors alone are enough to make them an attractive target for cybercriminals. Despite it being common knowledge, businesses often opt for simpler and cheaper solutions that do not address the issue at the system level. Below is an in-depth look at the main factors that erode corporate cybersecurity and ways to prevent cyberattacks.
205. Why Is Transparency Critical to Cybersecurity?
 After more than a year of posturing over whether it was safe to integrate Huawei's equipment into the UK’s telecom network, the Prime Minister finally made a decision. Last January, Boris Johnson decided to allow not only Huawei but also other companies deemed “high-risk” limited access to Britain's 5G networks.
After more than a year of posturing over whether it was safe to integrate Huawei's equipment into the UK’s telecom network, the Prime Minister finally made a decision. Last January, Boris Johnson decided to allow not only Huawei but also other companies deemed “high-risk” limited access to Britain's 5G networks.
206. This Is Why I left Machine Learning for Cybersecurity
 Well, this is my first ever published content. I am a writer; I write academic content, sometimes technical articles. I can say this is more of a personal opinion than a statistically analyzed interpretation.
Well, this is my first ever published content. I am a writer; I write academic content, sometimes technical articles. I can say this is more of a personal opinion than a statistically analyzed interpretation.
207. Exposing Secrets on GitHub: What to Do After Leaking Credentials and API Keys
 As a developer, if you have discovered that you have just exposed a sensitive file or secrets to a public git repository, there are some very important steps to follow.
As a developer, if you have discovered that you have just exposed a sensitive file or secrets to a public git repository, there are some very important steps to follow.
208. The best privacy-focused browsers in 2019
 Privacy protection has become a catchphrase for many entrepreneurs and public speakers. In their recent speeches, both Mark Zuckerberg and Sundar Pichai elaborated on the importance of privacy, which is ironic, having in mind that Facebook and Google are the two biggest data scrapers around.
Privacy protection has become a catchphrase for many entrepreneurs and public speakers. In their recent speeches, both Mark Zuckerberg and Sundar Pichai elaborated on the importance of privacy, which is ironic, having in mind that Facebook and Google are the two biggest data scrapers around.
209. Securing the Metaverse: How Digitally Immersive Experiences will Change the Future of Cybersecurity
 As more organizations dive into the idea of the Metaverse, the cybersecurity industry will need to keep innovating in its approach.
As more organizations dive into the idea of the Metaverse, the cybersecurity industry will need to keep innovating in its approach.
210. Coronavirus vs Business: Why Anti-Crisis Steps Taken are not Enough?

211. The Dark Side of DeFi: The Wild West of Decentralization
 The mystic world of decentralized finance sparks up discussions. In 2022, the industry is suffering from multiple cyber attacks. Is this the end for DeFi?
The mystic world of decentralized finance sparks up discussions. In 2022, the industry is suffering from multiple cyber attacks. Is this the end for DeFi?
212. Cybersecurity At Every Level: How IT Consultants Can Benefit Your Business
 We live our lives online these days – and given this simple fact, it should come as no surprise that cybersecurity is one of the fastest growing industries around, and one that’s critical to all other sectors. For those in the cryptocurrency industry, however, cybersecurity plays a more interesting role. That’s because, while cryptocurrency operations clearly need to enhance their own cybersecurity efforts, they’re also reliant on technology – blockchain – that other industries are using for their own security needs.
We live our lives online these days – and given this simple fact, it should come as no surprise that cybersecurity is one of the fastest growing industries around, and one that’s critical to all other sectors. For those in the cryptocurrency industry, however, cybersecurity plays a more interesting role. That’s because, while cryptocurrency operations clearly need to enhance their own cybersecurity efforts, they’re also reliant on technology – blockchain – that other industries are using for their own security needs.
213. Analyzing the Source Code of Popular Desktop Apps for NodeJS Malware. Part2
 Following my last article about a Discord malware, we now take a deeper look inside the inner workings of the PirateStealer malware.
Following my last article about a Discord malware, we now take a deeper look inside the inner workings of the PirateStealer malware.
214. 5 Promising Use Cases for Verifiable Credentials
 Verifiable credentials, which provide a system for provable electronic facts and documentation through cryptography and public keys, can seem like an abstract concept. We’re so used to seeing our credentials printed out – the driver’s license, the passport, the insurance card – that sticking codified IDs on a thumb drive or online seems odd and unnecessary. And as anyone who has used a cryptocurrency wallet can attest, the early forms of such decentralized IDs are hardly user friendly.
Verifiable credentials, which provide a system for provable electronic facts and documentation through cryptography and public keys, can seem like an abstract concept. We’re so used to seeing our credentials printed out – the driver’s license, the passport, the insurance card – that sticking codified IDs on a thumb drive or online seems odd and unnecessary. And as anyone who has used a cryptocurrency wallet can attest, the early forms of such decentralized IDs are hardly user friendly.
215. Using OSINT for Maritime Intelligence
 According to Naval Dome, the maritime industry has seen a 900% increase in cyber-attacks since 2017
According to Naval Dome, the maritime industry has seen a 900% increase in cyber-attacks since 2017
216. 8 Free Security Tools to Move Security Towards the Beginning of the Software Development Lifecycle
 Shifting left is a development principle which states that security should move from the right (or end) of the software development life cycle (SDLC) to the left (the beginning). In other words: security should be integrated and designed into all stages of the development process. This new shift requires developers to take more ownership of security and security principles. The good news is that there are lots of tools available to help developers in this process.
Shifting left is a development principle which states that security should move from the right (or end) of the software development life cycle (SDLC) to the left (the beginning). In other words: security should be integrated and designed into all stages of the development process. This new shift requires developers to take more ownership of security and security principles. The good news is that there are lots of tools available to help developers in this process.
217. 10 Ways to Mitigate Cybersecurity Risks and Prevent Data Theft
 Use the provided recommendations to make it as difficult as possible for cybercriminals to get into your system.
Use the provided recommendations to make it as difficult as possible for cybercriminals to get into your system.
218. 3 Steps to Help Advance Your Cybersecurity Career
 I've spent more than 15 years building and leading cybersecurity programs at several Fortune 500 companies in the Financial Services industry. I'm also the Founder & Managing Principal of Fraction Consulting where I get to do fractional CTO & CISO work and advise private capital firms.
I've spent more than 15 years building and leading cybersecurity programs at several Fortune 500 companies in the Financial Services industry. I'm also the Founder & Managing Principal of Fraction Consulting where I get to do fractional CTO & CISO work and advise private capital firms.
219. Why Do You Need to Patch Raspberry Pi?
 Because of its open-source nature, the Raspberry Pi source code could be analyzed by malicious actors and allow for targeted attacks.
Because of its open-source nature, the Raspberry Pi source code could be analyzed by malicious actors and allow for targeted attacks.
220. Netwalker Ransomware: Everything You Need to Know to Stay Safe
 Ransomware analysis and knowing how Netwalker works are essential for understanding vulnerable points and protecting yourself against Netwalker attacks
Ransomware analysis and knowing how Netwalker works are essential for understanding vulnerable points and protecting yourself against Netwalker attacks
221. Digital Forensics: An Overview and Its Impact On Law Enforcement
 While the dark web has become synonymous with nefarious acts, there are positive encounters that take place there too. It's not all hackers and shared login credentials.
While the dark web has become synonymous with nefarious acts, there are positive encounters that take place there too. It's not all hackers and shared login credentials.
222. The Crucial Role of Machine Learning in Cybersecurity
 In 2019, more than 627 million online records were comprised due to hacking and other types of cyber attacks. This is a pretty staggering number to anyone who has made an online transaction, but the amount of attacks that were stopped is much higher, so it’s worth some optimism. As COVID-19 has pushed many companies into the remote work world, online transactions and records are growing exponentially, and most experts believe that remote work will continue to be very popular even after stay-at-home orders get lifted and life goes back to some form of normal.
In 2019, more than 627 million online records were comprised due to hacking and other types of cyber attacks. This is a pretty staggering number to anyone who has made an online transaction, but the amount of attacks that were stopped is much higher, so it’s worth some optimism. As COVID-19 has pushed many companies into the remote work world, online transactions and records are growing exponentially, and most experts believe that remote work will continue to be very popular even after stay-at-home orders get lifted and life goes back to some form of normal.
223. Stuxnet, or how to destroy a centrifuge with a small piece of code
 Stuxnet represents the pinnacle of coding design. This small computer worm, just a half a megabyte in size, managed to infiltrate Iran’s nuclear facilities and destroy about one-fifth of uranium enrichment centrifuges. Furthermore, it was done in such a specific way to prevent political unrest, at least at the level of open conflict.
Stuxnet represents the pinnacle of coding design. This small computer worm, just a half a megabyte in size, managed to infiltrate Iran’s nuclear facilities and destroy about one-fifth of uranium enrichment centrifuges. Furthermore, it was done in such a specific way to prevent political unrest, at least at the level of open conflict.
224. A Guide to Enhancing Security at the IoT Edge (Part 2)
 The computing landscape has long observed a swing between centralized and distributed architectures, from the mainframe to client-server to the cloud. The next generation of computing is now upon us, representing both a return to the familiar distributed model and a breakthrough in rethinking how we handle data.
The computing landscape has long observed a swing between centralized and distributed architectures, from the mainframe to client-server to the cloud. The next generation of computing is now upon us, representing both a return to the familiar distributed model and a breakthrough in rethinking how we handle data.
225. Ryuk Ransomware: What it is and How it's Harming the Healthcare Sector
 Organizations in the healthcare sector have been valiantly fighting to save lives since the COVID-19 pandemic began, but they’ve also had to shift focus to another type of viral attack. Since March, healthcare organizations in the U.S. have been hit with multiple cyberattacks from threat actors who want to take advantage of any vulnerability in their systems. The latest to join the ranks of healthcare network threats is Ryuk, a ransomware that has victimized several medical organizations since September.
Organizations in the healthcare sector have been valiantly fighting to save lives since the COVID-19 pandemic began, but they’ve also had to shift focus to another type of viral attack. Since March, healthcare organizations in the U.S. have been hit with multiple cyberattacks from threat actors who want to take advantage of any vulnerability in their systems. The latest to join the ranks of healthcare network threats is Ryuk, a ransomware that has victimized several medical organizations since September.
226. Decentralized Identifiers (DIDs) - A Deeper Dive
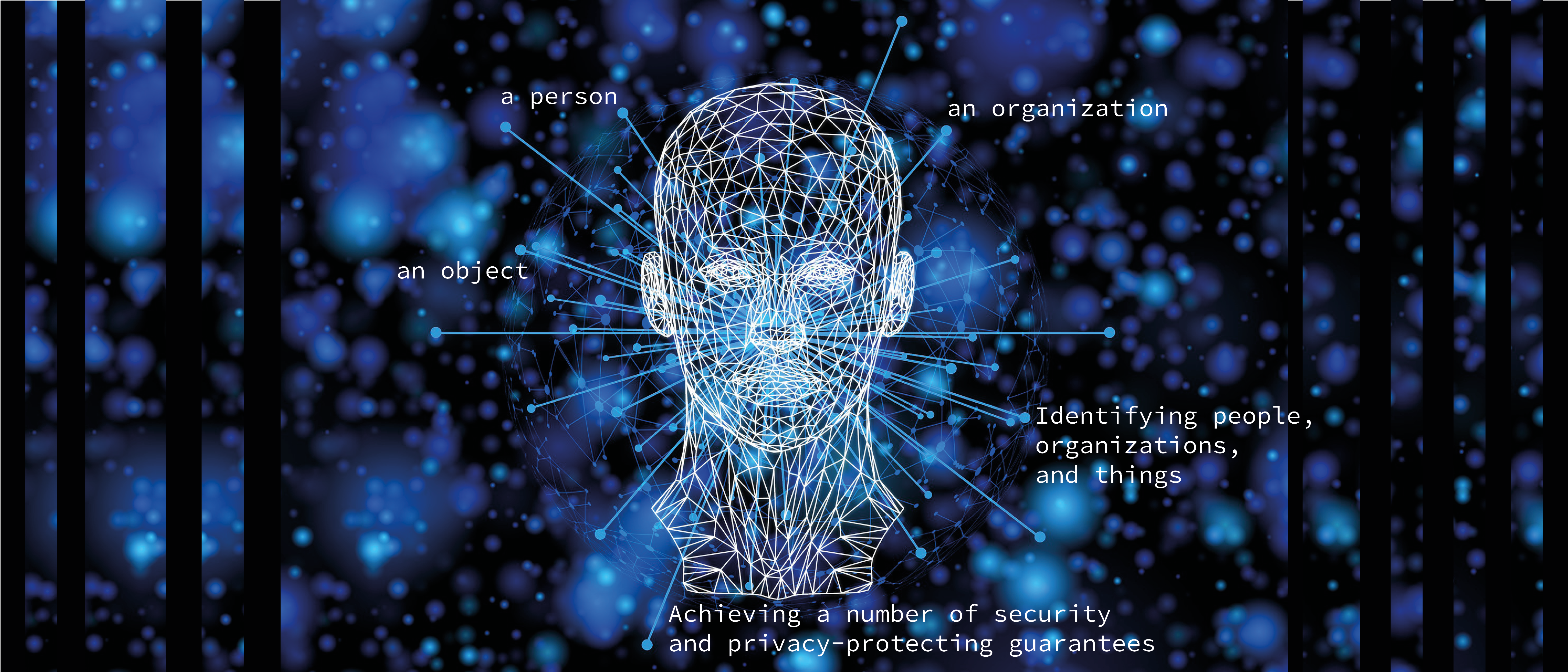 An introductory dive into DIDs.
This article follows the Rosseta standards and technological W3C descriptions.
An introductory dive into DIDs.
This article follows the Rosseta standards and technological W3C descriptions.
227. 8 Ways to Ensure Secure Remote Work Across Your Company
 As the world of work rapidly becomes “remote-first”, and our reliance on virtual tools grows daily, cybersecurity has emerged as an urgent priority for almost every employer.
As the world of work rapidly becomes “remote-first”, and our reliance on virtual tools grows daily, cybersecurity has emerged as an urgent priority for almost every employer.
228. Why Is Cybersecurity Becoming Vital in Politics
 The 21st century is considered to be an era of technologies. From the beginning of the 21st century, they started developing rapidly. Almost every day, we hear from social media and TV that companies create something new. Artificial intelligence is also gaining a foothold in life.
The 21st century is considered to be an era of technologies. From the beginning of the 21st century, they started developing rapidly. Almost every day, we hear from social media and TV that companies create something new. Artificial intelligence is also gaining a foothold in life.
229. Coping with remote security challenges in the long haul
 82% of business leaders plan to continue letting employees work from home
82% of business leaders plan to continue letting employees work from home
230. The Growing Cyber Risks of a Work From Home Workforce
 A recent Threatpost poll found that 40 percent of the companies transitioning to WFH experienced a spike in cyberattacks. The survey concluded that patching and updating are among the top challenges for employees when securing their remote footprint.
A recent Threatpost poll found that 40 percent of the companies transitioning to WFH experienced a spike in cyberattacks. The survey concluded that patching and updating are among the top challenges for employees when securing their remote footprint.
231. Data Integrity In Cryptography
 Data integrity refers to the accuracy, legitimacy, and consistency of information in a system. When a message is sent, particularly using an untrusted medium, data integrity provides us confidence that the message wasn't tampered with.
Data integrity refers to the accuracy, legitimacy, and consistency of information in a system. When a message is sent, particularly using an untrusted medium, data integrity provides us confidence that the message wasn't tampered with.
232. How to Protect Chatbots from Machine Learning Attacks
 Artificial Intelligence is a growing industry powered by advancements from large tech companies, new startups, and university research teams alike. While AI technology is advancing at a good pace, the regulations and failsafes around machine learning security are an entirely different story.
Artificial Intelligence is a growing industry powered by advancements from large tech companies, new startups, and university research teams alike. While AI technology is advancing at a good pace, the regulations and failsafes around machine learning security are an entirely different story.
233. Maximize Cybersecurity with Multiple Databases
 If securing your company’s intellectual property is such a complex process, how can business leaders efficiently defend their assets? Use multiple databases.
If securing your company’s intellectual property is such a complex process, how can business leaders efficiently defend their assets? Use multiple databases.
234. A Shapeshifter Under the Hoodie: The Face of Modern Cybercrime
 The face of modern cybercrime is not the stereotype of a hacker. It's a mirror, reflecting the people close to you. And the perpetrator could be anyone.
The face of modern cybercrime is not the stereotype of a hacker. It's a mirror, reflecting the people close to you. And the perpetrator could be anyone.
235. A CyberSecurity Mindset May Involve Being The Guy With The Most Negative Attitude
 We cannot solve the problem if we use the wrong mindset. A security mindset is risk-based, contextual, and ultimately ensures nothing happens.
We cannot solve the problem if we use the wrong mindset. A security mindset is risk-based, contextual, and ultimately ensures nothing happens.
236. Shortage of Cyber Security Professionals Will Create a Staggering 3.5 Million Unfilled Jobs by 2021
 Cyber security issues are becoming more prominent every day, so much so that it's questioning the existence of many startups and small-to-mid scale businesses. Recent trends indicate that cyber security attacks have been at an all-time rise.
Cyber security issues are becoming more prominent every day, so much so that it's questioning the existence of many startups and small-to-mid scale businesses. Recent trends indicate that cyber security attacks have been at an all-time rise.
237. How to Ensure Privacy and Security on Your Smartphones
 All you need to know about the security loopholes in your android device and how to protect your mobile phones from privacy invasions and security breaches.
All you need to know about the security loopholes in your android device and how to protect your mobile phones from privacy invasions and security breaches.
238. 5 Tips for Breaking Into Cybersecurity with No Experience
 If you're looking to break into the cybersecurity field, you may feel like you have your work cut out for you.
If you're looking to break into the cybersecurity field, you may feel like you have your work cut out for you.
239. The Essential Guide to Email Security: Threats, Costs, and Strategies
 We all use email on a regular basis, but we aren’t always cognizant of the email security standards we use. If a hacker gains access to your account, or manages to fool you into downloading an attachment with malware via email, it could have devastating consequences for your business.
We all use email on a regular basis, but we aren’t always cognizant of the email security standards we use. If a hacker gains access to your account, or manages to fool you into downloading an attachment with malware via email, it could have devastating consequences for your business.
240. All about Security Information and Event Management

241. Remote Working Is Transforming The Cyber Security Landscape in 2020
 As the world grapples into the arms of COVID-19, companies are suffering a major setback from the remote work culture. Because, let’s be honest, nobody thought that a PANDEMIC would hit us so hard that we’d be facing unemployment, poverty, illness, failed vaccines, and mass deaths.
As the world grapples into the arms of COVID-19, companies are suffering a major setback from the remote work culture. Because, let’s be honest, nobody thought that a PANDEMIC would hit us so hard that we’d be facing unemployment, poverty, illness, failed vaccines, and mass deaths.
242. Beginners Guide to Preventing Permission Bloat: Overlooked and Hidden Access
 When it comes to your organizational security, there should be no stone left unturned. Unfortunately, many organizations fail to do this, as they aren’t even aware that there are unturned stones. Overlooked access rights are one of the most unnoticed security threats your organization can face—less of a stone and more of a somehow-overlooked, but ever-looming mountain.
When it comes to your organizational security, there should be no stone left unturned. Unfortunately, many organizations fail to do this, as they aren’t even aware that there are unturned stones. Overlooked access rights are one of the most unnoticed security threats your organization can face—less of a stone and more of a somehow-overlooked, but ever-looming mountain.
243. 5 Life-Saving Tips About Cyber Security
 Introduction:
Introduction:
244. The Security Vulnerabilities of Smart Devices
 In 2020, we are now more connected to the internet than ever before, from having smart fridges, smart cars, and even RFID implants that can be placed under our skin.
In 2020, we are now more connected to the internet than ever before, from having smart fridges, smart cars, and even RFID implants that can be placed under our skin.
245. Inside a Hacker's Backpack: Gadgets, Tips, and Tricks for Hackers
 Not ever hack job requires just a laptop and some software to gain privileges into a system. Sometimes, something extra is required to make the job very easy
Not ever hack job requires just a laptop and some software to gain privileges into a system. Sometimes, something extra is required to make the job very easy
246. Reviewing the 2022 Survey on SEO Spend by IT Companies

247. Web Application Penetration Testing: A Complete Guide
 Your website can be the next ‘target’ if you don’t take the necessary steps to secure it. One of the most appropriate step is to conduct a penetration testing.
Your website can be the next ‘target’ if you don’t take the necessary steps to secure it. One of the most appropriate step is to conduct a penetration testing.
248. Blockchain And Covid-19 Vaccine Passports: All You Need to Know

249. Virtual Private Networks (VPNs): Why You Should be Using Them
 There was a time when we never come across the word VPN,
but today, it seems like we strongly need it to secure our internet connection.
There was a time when we never come across the word VPN,
but today, it seems like we strongly need it to secure our internet connection.
250. Thriving Scams amid Covid-19 Pandemic
 Pretending to be the IRS for selling fake vaccines, scammers have kicked in scammers and hackers are playing with people's emotions to cash in the opportunity since the coronavirus pandemic began.
Pretending to be the IRS for selling fake vaccines, scammers have kicked in scammers and hackers are playing with people's emotions to cash in the opportunity since the coronavirus pandemic began.
251. A Guide to Understanding the Job Roles & Selecting Your Career in Cybersecurity
 This article covers the top 20 job roles available in the Cyber Security domain along with the job description in a simplified way.
This article covers the top 20 job roles available in the Cyber Security domain along with the job description in a simplified way.
252. Top 5 Business Tech Solutions For Networking
 Any business in the tech industry will know that an exceptional network is the backbone of any enterprise operation. Without a network that can adequately handle your internal operational demands, your business won’t be able to provide cutting-edge services to its customers.
Any business in the tech industry will know that an exceptional network is the backbone of any enterprise operation. Without a network that can adequately handle your internal operational demands, your business won’t be able to provide cutting-edge services to its customers.
253. Conducting A Cyber Security Audit for Your Business [A How-To-Guide]
 Companies sometimes question the usefulness of an internal
cybersecurity audit, and the question of, “aren’t standard risk assessments
enough to formulate a security strategy to protect a company’s digital assets?” is often asked.
Companies sometimes question the usefulness of an internal
cybersecurity audit, and the question of, “aren’t standard risk assessments
enough to formulate a security strategy to protect a company’s digital assets?” is often asked.
254. Questions For The Most Controversial Hacker Of This Generation: Sabu
 I believe strongly if we get answers to these questions from a source with gravitas, such as Sabu, we will understand how to navigate the future.
I believe strongly if we get answers to these questions from a source with gravitas, such as Sabu, we will understand how to navigate the future.
255. How To Eliminate Leaky S3 Buckets Without Writing A Line Of Code
 FedEx
FedEx
256. Automate Your Cybersecurity Efforts to Speed Up Response Time
 Automation can stand as a mighty knight for the fortress of your organization by strengthening cybersecurity. Collect data and speed up response time.
Automation can stand as a mighty knight for the fortress of your organization by strengthening cybersecurity. Collect data and speed up response time.
257. Crack Open the IoT Vulnerabilities of Realtek
 Taiwanese chip designer Realtek has warned of four recent vulnerabilities in three SDKs in its WiFi modules.
Taiwanese chip designer Realtek has warned of four recent vulnerabilities in three SDKs in its WiFi modules.
258. The Government's Impact on Encryption
 Anyone who has seen the movie The Imitation Game, or studied computer science in school, probably has at least a brief understanding of Enigma, Alan Turing, and some of the other fun cryptography that went on during WWII. During this time and until the 1970's, governments from around the world had near total control of all cryptographic systems.
Anyone who has seen the movie The Imitation Game, or studied computer science in school, probably has at least a brief understanding of Enigma, Alan Turing, and some of the other fun cryptography that went on during WWII. During this time and until the 1970's, governments from around the world had near total control of all cryptographic systems.
259. The Importance of Cybersecurity in Early-stage Startups
 When it comes to early-stage startups and cybersecurity, the two concepts do not always go hand-in-hand. In this write-up, we'll explain the importance of cybersecurity and how it will build trust with customers and investors.
When it comes to early-stage startups and cybersecurity, the two concepts do not always go hand-in-hand. In this write-up, we'll explain the importance of cybersecurity and how it will build trust with customers and investors.
260. Top 5 Gaming VPNs: Free, Trial, and Paid Options
 NordVPN, CyberGhost, and ExpressVPN are some of the best gaming VPNs on the market with free trials and affordable monthly rates. This article will explain why.
NordVPN, CyberGhost, and ExpressVPN are some of the best gaming VPNs on the market with free trials and affordable monthly rates. This article will explain why.
261. Breaking Down 3 API Security Breaches
 The following three API security breaches provide helpful lessons for improving security today.
The following three API security breaches provide helpful lessons for improving security today.
262. The Massive Uber Hack: Technical and Legal Implications
 In this article, I analyze the technical and legal implications of post-data breach, the risks & possible exonerations in the eyes of extent laws & regulations.
In this article, I analyze the technical and legal implications of post-data breach, the risks & possible exonerations in the eyes of extent laws & regulations.
263. How to Have Better Cybersecurity
 All of this increases the odds of catching a busy employee off guard and executing a successful attack.
All of this increases the odds of catching a busy employee off guard and executing a successful attack.
264. Biden’s Administration Reinforces Cyber Security Protocols of Powergrid
 On Tuesday, 20th April 2021, Biden’s administration issued a 100-day plan through the United States’s Power of energy to beep up cybersecurity.
On Tuesday, 20th April 2021, Biden’s administration issued a 100-day plan through the United States’s Power of energy to beep up cybersecurity.
265. Common Misconceptions About Why VPNs Are Used
 There are some misconceptions about why VPNs are used such as the extent of the privacy that they offer and how well such systems can keep users anonymous.
There are some misconceptions about why VPNs are used such as the extent of the privacy that they offer and how well such systems can keep users anonymous.
266. Proxy Vs. VPN Vs. SmartDNS [A Comparison]

267. DNS Firewalls for Dummies
 As we adjust to life during a pandemic, two things have become clear: First, the internet is essential; second, the internet is full of dangers. Each of these dangers is different: They vary in the sort of attack they strike with, our familiarity with them, and the tools we can use to avert them. For example, viruses have been well-known for decades. Every PC is currently protected with antivirus software--and in many cases, it’s incorporated right into your operating system. Other types of internet threats, such as botnets, are newer, more difficult to detect, and less known to web users.
As we adjust to life during a pandemic, two things have become clear: First, the internet is essential; second, the internet is full of dangers. Each of these dangers is different: They vary in the sort of attack they strike with, our familiarity with them, and the tools we can use to avert them. For example, viruses have been well-known for decades. Every PC is currently protected with antivirus software--and in many cases, it’s incorporated right into your operating system. Other types of internet threats, such as botnets, are newer, more difficult to detect, and less known to web users.
268. Should We Kick Hardware out of Blockchain?
 You may think blockchain has little to do with hardware. After all, from Bitcoin to Etherum, blockchains are all software-defined. The hardware-based solution is usually more centralized.
You may think blockchain has little to do with hardware. After all, from Bitcoin to Etherum, blockchains are all software-defined. The hardware-based solution is usually more centralized.
269. Your Ultimate Guide To The 4 Types of IT Security
 IT Security protects your business against cyber threats. There are four types of IT Security: network security, end-point security, internet & cloud security.
IT Security protects your business against cyber threats. There are four types of IT Security: network security, end-point security, internet & cloud security.
270. Data Loss Prevention: What is it, and Do You Need it?
 Data Loss Prevention is a set of tools and practices geared towards protecting your data from loss and leak. Even though the name has only the loss part, in actuality, it's as much about the leak protection as it is about the loss protection. Basically, DLP, as a notion, encompasses all the security practices around protecting your company data.
Data Loss Prevention is a set of tools and practices geared towards protecting your data from loss and leak. Even though the name has only the loss part, in actuality, it's as much about the leak protection as it is about the loss protection. Basically, DLP, as a notion, encompasses all the security practices around protecting your company data.
271. AI-Powered Cybersecurity Solutions Are Taking Charge Against Advanced Cyberattacks
 Enterprises such as safeguard, Talon, and Hack the Box are raising their funds by investing in AI-powered cybersecurity measures against chargebacks
Enterprises such as safeguard, Talon, and Hack the Box are raising their funds by investing in AI-powered cybersecurity measures against chargebacks
272. Top 10 Cloud Security Trends of the Year
 While cloud security trends can come and go, there are some with great sticking power. The following top 10 cloud security trends need to be adopted in 2022.
While cloud security trends can come and go, there are some with great sticking power. The following top 10 cloud security trends need to be adopted in 2022.
273. Passwords Suck: Here Are 4 Ways We Can Fix Them
 Passwords are a critical part of cybersecurity that individuals and businesses use every day.
Passwords are a critical part of cybersecurity that individuals and businesses use every day.
274. Compliance is Not a Guarantee Against Data Breach
 When it comes to combating the ever-growing threat posed by data breaches, most organizations believe that compliance is key. With cybercriminals targeting governments, small businesses, and other essential infrastructure- the need to minimize the impact of these attacks is at an all-time high.
When it comes to combating the ever-growing threat posed by data breaches, most organizations believe that compliance is key. With cybercriminals targeting governments, small businesses, and other essential infrastructure- the need to minimize the impact of these attacks is at an all-time high.
275. The Most Expensive Things in Life are “Free of Charge” - Protect Your Data
 Digital Footprint is everywhere online. It is all the activities you do with keyboard and mouse, in addition to what we tap and swipe on our mobile devices.
Digital Footprint is everywhere online. It is all the activities you do with keyboard and mouse, in addition to what we tap and swipe on our mobile devices.
276. Network Security Basics
 Ever since the creation of the internet with all of the good that it has brought to the table came the bad as well. In the age of information technology, an unsecured product is a surefire way to numerous issues. A company, which creates a product has to make sure both the software and the network security features of it are as robust as possible. In the previous article we discussed application security, however, it is never complete without a clear network safeguards to serve as a frontline against malicious users trying to exploit the system. But what is network security and what are some of the methods used to protect systems?
Ever since the creation of the internet with all of the good that it has brought to the table came the bad as well. In the age of information technology, an unsecured product is a surefire way to numerous issues. A company, which creates a product has to make sure both the software and the network security features of it are as robust as possible. In the previous article we discussed application security, however, it is never complete without a clear network safeguards to serve as a frontline against malicious users trying to exploit the system. But what is network security and what are some of the methods used to protect systems?
277. Advanced Heuristics to Detect Zero-Day Attacks
 Zero-Day Attacks are becoming increasingly common and widespread in the world of cybersecurity. Heuristics detection may help to detect such vulnerabilities.
Zero-Day Attacks are becoming increasingly common and widespread in the world of cybersecurity. Heuristics detection may help to detect such vulnerabilities.
278. How to Run Reverse Shell for Hacking in Linux

279. The ZEE5 User Data Leak That The Media Didn't Report On

280. What Could Have Prevented 2020's Massive Twitter Hack?
 Attacks and account take-overs like the recent Twitter hack are completely avoidable. Enterprises must implement biometric multi-factor authentication to ensure that only the right users have access to the right systems at all times. If they don’t, users will continue being vulnerable to hacks and scams.
Attacks and account take-overs like the recent Twitter hack are completely avoidable. Enterprises must implement biometric multi-factor authentication to ensure that only the right users have access to the right systems at all times. If they don’t, users will continue being vulnerable to hacks and scams.
281. Security For PMs: A Step-By-Step Guide
 Cybersecurity is among the most significant trends over the last decade and has become even more important now, especially due to more remote work being done. From ransomware to cyber espionage, hackers have developed sophisticated techniques to break into your project/company data and get away with critical information or demand ransom.
Cybersecurity is among the most significant trends over the last decade and has become even more important now, especially due to more remote work being done. From ransomware to cyber espionage, hackers have developed sophisticated techniques to break into your project/company data and get away with critical information or demand ransom.
Even well known organizations such as Canon, Garmin, Twitter, Honda, and Travelex have fallen victims to malicious actors. A data breach can be a disaster for your company/project, destroy the trust of your customers, and spoil your company’s reputation.
282. Lessons Learned From SolarWinds: Defensive Strategy Against Novel Malware
 SolarWinds, a leading provider of IT monitoring and management solutions for enterprises, disclosed that it had fallen prey to a widespread supply chain attack
SolarWinds, a leading provider of IT monitoring and management solutions for enterprises, disclosed that it had fallen prey to a widespread supply chain attack
283. Detecting, Investigating, Verifying Fixes for Security Incidents, Zero Day Issues Using Lightrun
 Cover major milestones in app security: finding the issue, evaluating a breach, proving it and validating the fix. Lightrun rises to the challenge.
Cover major milestones in app security: finding the issue, evaluating a breach, proving it and validating the fix. Lightrun rises to the challenge.
284. What is SIM swap, and how can SIM-based auth help fix it?
 SIM swap fraud is a security threat using mobile phones. One of the causes - SMS 2FA. tru.ID explains why SIM-based authentication is a stronger alternative.
SIM swap fraud is a security threat using mobile phones. One of the causes - SMS 2FA. tru.ID explains why SIM-based authentication is a stronger alternative.
285. Machine Learning For Fraud Prevention - Why It's The Best Tool Yet
 With the development and sophistication of modern technologies, life has become much more comfortable. While it was considered impossible in the past to conduct complicated operations simultaneously, a computer made this task way easier.
With the development and sophistication of modern technologies, life has become much more comfortable. While it was considered impossible in the past to conduct complicated operations simultaneously, a computer made this task way easier.
286. OAuth Vulnerabilities: How To Implement Secure Authorization in Your Web Application
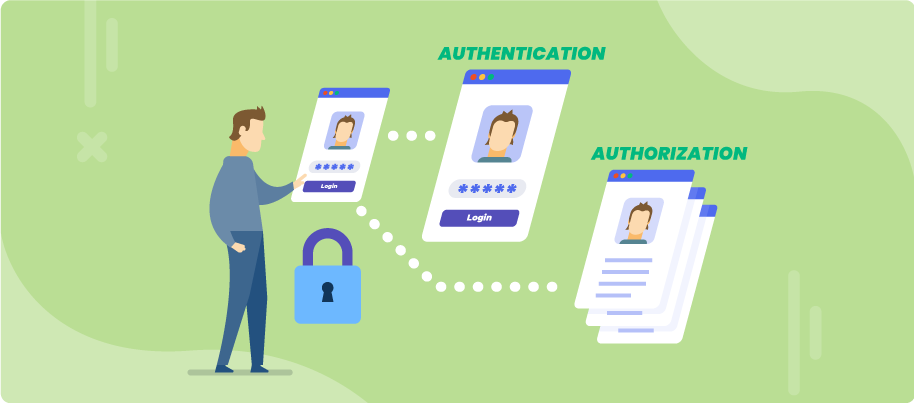 In this article, we will go through the most common security vulnerabilities encountered in applications that use the OAuth protocol.
In this article, we will go through the most common security vulnerabilities encountered in applications that use the OAuth protocol.
287. Cybersecurity Threats in Crypto Exchanges Everyone Should Know
 Cybercriminals have turned to utilizing a variety of tools and strategies aimed to target cryptocurrency exchange customers, steal their money, or steal.
Cybercriminals have turned to utilizing a variety of tools and strategies aimed to target cryptocurrency exchange customers, steal their money, or steal.
288. With Telehealth on the Rise, Privacy Regulations are Imperative
 In recent months, individuals across the globe have shifted to a remote way of life, including working from home, virtual dating, drive-by birthday parties and now, even doctor’s appointments. The healthcare sector quickly implemented changes to provide a more remote experience to comply with social distancing regulations.
In recent months, individuals across the globe have shifted to a remote way of life, including working from home, virtual dating, drive-by birthday parties and now, even doctor’s appointments. The healthcare sector quickly implemented changes to provide a more remote experience to comply with social distancing regulations.
To decrease the number of face-to-face doctor’s appointments and adhere to social distancing limitations and regulations, the Department of Health and Human Services (HHS) announced they “will not impose penalties for noncompliance” with the regulatory requirements under the HIPAA Rules against covered health care providers in connection with the good faith provision of telehealth during the COVID-19 nationwide public health emergency.
289. What Is Threat Intelligence Used For?
 What is threat intelligence, and how should you use it to better protect yourself from cyber threats?
What is threat intelligence, and how should you use it to better protect yourself from cyber threats?
290. An Introduction to Layer 3 Switches
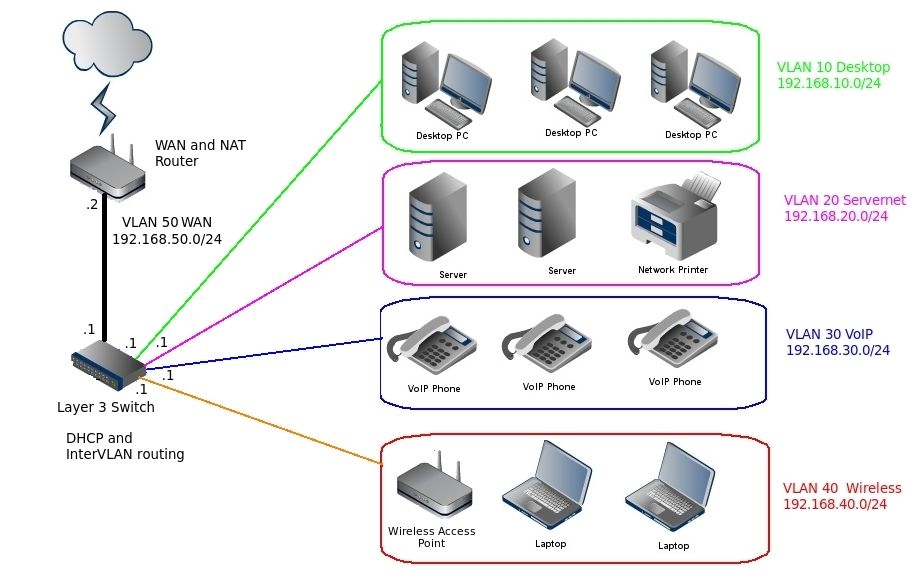 In today's complex business networks that comprise many virtual LAN's and subnets, a Layer 3 switch plays an important role in many systems. But do you need this on your network? Let's see.
In today's complex business networks that comprise many virtual LAN's and subnets, a Layer 3 switch plays an important role in many systems. But do you need this on your network? Let's see.
291. Roadmap and Resources to Become an Ethical Hacker
 How to become an ethical hacker
How to become an ethical hacker
292. What are extortion emails and what can be done? By Jason Nelson
 What is an Extortion Email? An extortion email is one that claims to have access to usually pictures or videos showing users in a compromising situation or looking at something that may be a source of embarrassment.
What is an Extortion Email? An extortion email is one that claims to have access to usually pictures or videos showing users in a compromising situation or looking at something that may be a source of embarrassment.
293. Facts You Probably Didn't Know About The Dark Web

294. Getting Started With Digital Forensics Using the Sleuth Kit

295. Why We Should All Care About Privacy Online—Interview: Hanna Bozakov
 I interviewed Hanna Bozakov, Head of Marketing for secure email service Tutanota, about internet security, online privacy, the legality of encryption, and how Tutanota works to protect you. According to their homepage, "Tutanota is the world's most secure email service, easy to use and private by design".
I interviewed Hanna Bozakov, Head of Marketing for secure email service Tutanota, about internet security, online privacy, the legality of encryption, and how Tutanota works to protect you. According to their homepage, "Tutanota is the world's most secure email service, easy to use and private by design".
296. 5 Best VPNs for Privacy and Security on the Dark Web
 A list of 5 powerful VPNs capable of handling Dark Web and onion nodes that will ensure your privacy and security.
A list of 5 powerful VPNs capable of handling Dark Web and onion nodes that will ensure your privacy and security.
297. How To Protect Your Data While Working Remotely

298. How to Fastline Internet Asset Enumeration with Cyber Search Engines
 Cyber Search Engines collect data across the whole internet and deliver it in a structured view.
Cyber Search Engines collect data across the whole internet and deliver it in a structured view.
299. Understanding the Verifiable Credentials (VCs)
 Verifiable Credentials heavily utilize Decentralized Identifiers to identify people, organizations, and things and to achieve security and privacy guarantees.
Verifiable Credentials heavily utilize Decentralized Identifiers to identify people, organizations, and things and to achieve security and privacy guarantees.
300. 12 Red Flags to Look Out For to Avoid Getting Scammed on Facebook Marketplace
 We have put together this guide to help you avoid getting scammed. There are several red flags buyers and sellers should be mindful of when shopping.
We have put together this guide to help you avoid getting scammed. There are several red flags buyers and sellers should be mindful of when shopping.
301. How to Pick a Lock for Beginners: The Tech and Tools of the Trade
 Lock picking is surprisingly easy, only requiring some basic knowledge of how locks work and how to manipulate them. Read more for the basics.
Lock picking is surprisingly easy, only requiring some basic knowledge of how locks work and how to manipulate them. Read more for the basics.
302. How COVID-19 Has Emphasized Immediate Need for Change in IAM
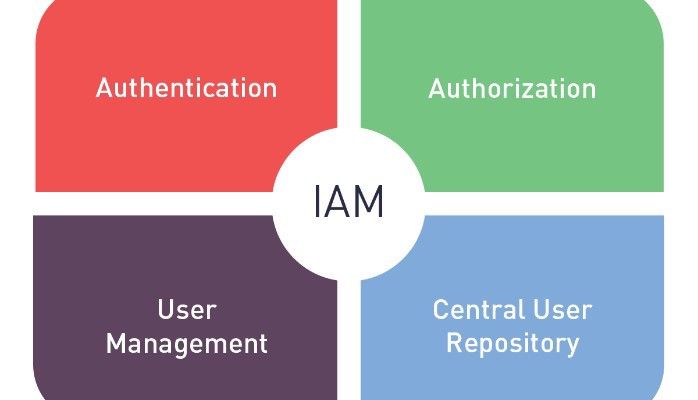 Globally, COVID-19’s impact has been seen throughout all aspects of life. One such clear way is through remote work. In order to control the spread of the virus and to keep employees safe, many companies are restricting travel and requiring people to work from home.
Globally, COVID-19’s impact has been seen throughout all aspects of life. One such clear way is through remote work. In order to control the spread of the virus and to keep employees safe, many companies are restricting travel and requiring people to work from home.
303. A Journalist’s Journey to the World of Cybersecurity
 Cybersecurity, Cyber security, Journalism, Career, Career Switch, Software Testing, SQA, Testing, Software Quality Assurance
Cybersecurity, Cyber security, Journalism, Career, Career Switch, Software Testing, SQA, Testing, Software Quality Assurance
304. Guess Who? Access Management Struggles in the Age of Remote Work
 In the age of remote work, access management has become one of the most important- and difficult- tasks for IT professionals.
In the age of remote work, access management has become one of the most important- and difficult- tasks for IT professionals.
305. An In-Depth Guide to Hybrid Layer 2 Protocols
 There is a large middle ground between data-on-chain layer 2 and data-off-chain layer 2 protocols, with many hybrid approaches
There is a large middle ground between data-on-chain layer 2 and data-off-chain layer 2 protocols, with many hybrid approaches
306. The Ultimate Cyber Security Survival Guide
 Every action on the network leaves a digital footprint. For example, photos we post on social networks, statements on forums, likes and dislikes of videos. Moreover, a user activity leaves a digital trace - information about the sites browsed, purchases made, and geographical locations visited. There are many channels through which our personal data is exposed and the effects of abuse are very serious. Therefore, you should always be extremely careful about the use of world wide web and private data management.
Every action on the network leaves a digital footprint. For example, photos we post on social networks, statements on forums, likes and dislikes of videos. Moreover, a user activity leaves a digital trace - information about the sites browsed, purchases made, and geographical locations visited. There are many channels through which our personal data is exposed and the effects of abuse are very serious. Therefore, you should always be extremely careful about the use of world wide web and private data management.
307. Remembering and Honoring the Cybersecurity Pioneer John McAfee
 One Year Later - Why Does It Still Matter?
One Year Later - Why Does It Still Matter?
308. The Twitter Hack Isn’t About Twitter or Bitcoin: It’s About Our Internet Identity
 Amid all of the news related to the pandemic, COVID-19, and global fears about the future of our planet, something that managed to break the news around the world was a global hack on Twitter’s platform.
Amid all of the news related to the pandemic, COVID-19, and global fears about the future of our planet, something that managed to break the news around the world was a global hack on Twitter’s platform.
309. How Fraudsters Carry out Holiday Themed Scams to Steal Your Identity
 Online scammers become more active during the holiday season with new and improved techniques to carry out phishing scams. Watch out for a fake personal letter.
Online scammers become more active during the holiday season with new and improved techniques to carry out phishing scams. Watch out for a fake personal letter.
310. What the GDPR and California Privacy Act Means for Tech Companies
 You may not know it, but companies are using your data as a commodity. For decades, all of your online habits have been stored, bought, shared, transferred, and maybe even stolen by businesses and individuals.
You may not know it, but companies are using your data as a commodity. For decades, all of your online habits have been stored, bought, shared, transferred, and maybe even stolen by businesses and individuals.
311. What We Can Learn From Cyber Attacks Targeting Healthcare
 At the end of October 2020, we reported that hospitals and healthcare organizations had been targeted by a rising wave of ransomware attacks, with the majority
At the end of October 2020, we reported that hospitals and healthcare organizations had been targeted by a rising wave of ransomware attacks, with the majority
312. Be Resilient not Vulnerable to Ransomware Emails

[313. Cyber Security for Businesses:
Tips to Reduce Risks](https://hackernoon.com/cyber-security-for-businesses-tips-to-reduce-risks-92ap3uf0)
 Cyber security is a human issue before it is technological. This is why all companies — whatever their size — must work on bringing awareness of these issues to their employees. Today, companies are targeted, because hackers ultimately are looking to access their customers and suppliers. Cyber security is therefore no longer a niche activity and, above all, is no longer something that can be ignored or put aside.
Cyber security is a human issue before it is technological. This is why all companies — whatever their size — must work on bringing awareness of these issues to their employees. Today, companies are targeted, because hackers ultimately are looking to access their customers and suppliers. Cyber security is therefore no longer a niche activity and, above all, is no longer something that can be ignored or put aside.
314. How To Approach Modern Cybersecurity
 There are many ways to approach the cybersecurity of your business and ensure that your data, and that of your customers, is safe from malicious actors. Most of these can boil down to focusing on the three major areas of technology, processes and people. This can help you better focus your approach to what your firm needs and which tools and techniques there are to help.
There are many ways to approach the cybersecurity of your business and ensure that your data, and that of your customers, is safe from malicious actors. Most of these can boil down to focusing on the three major areas of technology, processes and people. This can help you better focus your approach to what your firm needs and which tools and techniques there are to help.
315. Is the Metaverse Ready for Cyberattacks?
 The metaverse is the next generation of the Internet. But is the metaverse prepared for cyber attacks? Because it will ultimately face cybersecurity incidents.
The metaverse is the next generation of the Internet. But is the metaverse prepared for cyber attacks? Because it will ultimately face cybersecurity incidents.
316. 10 Common Java Vulnerabilities Every Security Engineer Should Know
 This article covers the most common security vulnerabilities for Java programming
This article covers the most common security vulnerabilities for Java programming
317. NordVPN Launches Password Manager, B2B Services And Storage Encryption Software
 This year has been big for the VPN market. Some buyers still remember last year’s Facebook data leaks; others have had enough with geo-blocks. And some, sadly, are threatened by governmental internet restrictions and turn to VPNs for help.
This year has been big for the VPN market. Some buyers still remember last year’s Facebook data leaks; others have had enough with geo-blocks. And some, sadly, are threatened by governmental internet restrictions and turn to VPNs for help.
318. 4 Important Web Security Tools During Privacy Crisis

319. OWASP Audit: How to Make Sure Your App is Secure
 FamilyGo conducted an audit on themselves to see how mobile apps may be compromised by common threats and how the app managed to fix the vulnerabilities
FamilyGo conducted an audit on themselves to see how mobile apps may be compromised by common threats and how the app managed to fix the vulnerabilities
320. Crypto Security: How To Protect Your Project From Hacking
 The number of thefts of funds from crypto projects is not decreasing. Most of the incidents are related to smart contract vulnerabilities you need to know.
The number of thefts of funds from crypto projects is not decreasing. Most of the incidents are related to smart contract vulnerabilities you need to know.
321. 7 Ways To Keep Your Mobile Phone Secure
 It is critical to change our outlook towards the security of smartphones and adopt as many precautions as possible for safeguarding ourselves.
It is critical to change our outlook towards the security of smartphones and adopt as many precautions as possible for safeguarding ourselves.
322. How to Keep Your Crypto Safe
 Keeping your crypto safe is crucial. In this article, I talk about various ways of protecting your investment.
Keeping your crypto safe is crucial. In this article, I talk about various ways of protecting your investment.
323. Protect Your Business From These 7 Dangerous Cyber Threats
 Imagine being a business owner who has worked hard to get their business off the ground. When your business starts flourishing, you come under a cybersecurity attack. All your user data gets stolen along with sensitive financial information such as credit card details, bank account details and more.
Imagine being a business owner who has worked hard to get their business off the ground. When your business starts flourishing, you come under a cybersecurity attack. All your user data gets stolen along with sensitive financial information such as credit card details, bank account details and more.
324. Implementing A Zero Trust System and Simplifying Its Adoption
 Companies must look for ways to adopt a frictionless zero trust strategy so that the true benefits can be realized quickly and efficiently without disruption.
Companies must look for ways to adopt a frictionless zero trust strategy so that the true benefits can be realized quickly and efficiently without disruption.
325. How Can I Tell if My Steam Account Has Been Hacked? (and How to Recover It)
 his time, I would like to focus on Steam account security, which has recently gotten some attention in the community after waves of phishing attacks.
his time, I would like to focus on Steam account security, which has recently gotten some attention in the community after waves of phishing attacks.
326. Why the AWS, Azure, and GCP CLIs Need to Die
 Why the AWS, Azure, and GCP CLIs need to die
Why the AWS, Azure, and GCP CLIs need to die
327. Phone Scams: What Is Vishing And How You Can Avoid It
 The attack combines a one-on-one phone call with credible-looking phishing sites where the user is required to fill in their credentials and their MFA codes.
The attack combines a one-on-one phone call with credible-looking phishing sites where the user is required to fill in their credentials and their MFA codes.
328. What Is White-Box Cryptography?
 White-box cryptography combines methods of encryption and obfuscation to embed secret keys within application code. The goal is to combine code and keys in such a way that the two are indistinguishable to an attacker, and the new "white-box" program can be safely run in an insecure environment.
White-box cryptography combines methods of encryption and obfuscation to embed secret keys within application code. The goal is to combine code and keys in such a way that the two are indistinguishable to an attacker, and the new "white-box" program can be safely run in an insecure environment.
329. Methods and Plugins to Spot Deepfakes and AI-Generated Text
 With the emergence of incredibly powerful machine learning technologies, such as Deepfakes and Generative Neural Networks, it is much easier now to spread false information. In this article, we will briefly introduce deepfakes and generative neural networks, as well as a few ways to spot AI-generated content and protect yourself against misinformation.
With the emergence of incredibly powerful machine learning technologies, such as Deepfakes and Generative Neural Networks, it is much easier now to spread false information. In this article, we will briefly introduce deepfakes and generative neural networks, as well as a few ways to spot AI-generated content and protect yourself against misinformation.
330. Rails Security: Eliminating CSRF and XSS Vulnerabilities

331. Colonial Pipeline Shutdown Affirms Need for Better OT Cybersecurity Practices
 The US government proclaimed a regional emergency, as the largest fuel pipeline system remained shut down for two days due to ransomware.
The US government proclaimed a regional emergency, as the largest fuel pipeline system remained shut down for two days due to ransomware.
332. Safety is King: Why OT Security is Mission Critical
 We have all heard that safety is king when it comes to OT environments, but there is more to that than meets the eye. Safety goes well beyond taking precautions to avoid the common hazards, such as slipping or tripping hazards, or ensuring workers don’t get injured on the job. Instead, it’s a holistic protection of the workers, communities at large, and the business.
We have all heard that safety is king when it comes to OT environments, but there is more to that than meets the eye. Safety goes well beyond taking precautions to avoid the common hazards, such as slipping or tripping hazards, or ensuring workers don’t get injured on the job. Instead, it’s a holistic protection of the workers, communities at large, and the business.
333. Your Website Could be Vulnerable Because of These 7 PHP Mistakes
 Make these mistakes and hackers will attack your web application using Cross Site Scripting, SQL Injection, Path Traversal, and other attacks to take over your website.
Make these mistakes and hackers will attack your web application using Cross Site Scripting, SQL Injection, Path Traversal, and other attacks to take over your website.
334. The Disruption of Emotet and What we Know About it
 Emotet, which was once a Banking Trojan and became a full-blown botnet was the most successful and prevalent malware of 2020 by a long way.
Emotet, which was once a Banking Trojan and became a full-blown botnet was the most successful and prevalent malware of 2020 by a long way.
335. Cybersecurity Tips to Keep in Mind When Working From Home
 implementation of remote working takes more than expected (and this is not about children interrupting a BBC news interview, although this one’s epic).
To make a remote job situation work, you need a structured approach. And robust cybersecurity is what keeps your digital environment and your company’s business safe. This is why we’ve curated a list of vital cybersecurity tips that will help you mitigate risks and stay aware of security vulnerabilities.
implementation of remote working takes more than expected (and this is not about children interrupting a BBC news interview, although this one’s epic).
To make a remote job situation work, you need a structured approach. And robust cybersecurity is what keeps your digital environment and your company’s business safe. This is why we’ve curated a list of vital cybersecurity tips that will help you mitigate risks and stay aware of security vulnerabilities.
336. 5 Cybersecurity Mistakes You Probably Make Every Day (and How to Fix Them)
 A look at common cybersecurity mistakes that you are likely doing every day, and what you can to prevent them.
A look at common cybersecurity mistakes that you are likely doing every day, and what you can to prevent them.
337. How to Detect if an iOS Device is Jailbroken
 Thanks to the mobile era we have mobile apps for everything these days. Every business from a barber shop to huge retailers has apps so that they can be closer to their customers. On one hand, we really leverage this convenience but on the other hand, there are risks of exposing a lot of confidential information while using these apps. And it becomes very vital when dealing with payments and other sensitive information.
Thanks to the mobile era we have mobile apps for everything these days. Every business from a barber shop to huge retailers has apps so that they can be closer to their customers. On one hand, we really leverage this convenience but on the other hand, there are risks of exposing a lot of confidential information while using these apps. And it becomes very vital when dealing with payments and other sensitive information.
338. How Social Engineering is Used to Bypass Your Security...with Ease
 Social Engineering uses influence and persuasion in order to deceive, convince or manipulate. As a result, the social engineer is able to take advantage of people to obtain information with or without the use of technology.
Social Engineering uses influence and persuasion in order to deceive, convince or manipulate. As a result, the social engineer is able to take advantage of people to obtain information with or without the use of technology.
339. What is Cyber Range Training and Simulation in the Cloud?
 Cyber range simulations help create resiliency by enabling companies in an actual situation to stress-test through Cloud computing. With tabletop drills or classroom instructors we need immersive funds to support situational awareness in a way that is very difficult to duplicate. Cloud Simulation contributes to experience on-the-ground and provides various advantages, including statistical information, input from real-time experts, and cross-functional coaching. There are potentially many challenges with the on-site classrooms based on several experts:
Cyber range simulations help create resiliency by enabling companies in an actual situation to stress-test through Cloud computing. With tabletop drills or classroom instructors we need immersive funds to support situational awareness in a way that is very difficult to duplicate. Cloud Simulation contributes to experience on-the-ground and provides various advantages, including statistical information, input from real-time experts, and cross-functional coaching. There are potentially many challenges with the on-site classrooms based on several experts:
340. Managing Enterprise Cloud Security vs On-Prem Security

341. Everything you Need to Know About the CompTIA Security+ SY0-601 Certification
 CompTIA Security+ SY0-601 certification is to provide IT professionals with the knowledge required to install, configure, manage & troubleshoot security system.
CompTIA Security+ SY0-601 certification is to provide IT professionals with the knowledge required to install, configure, manage & troubleshoot security system.
342. Launching DDos Attacks Using Various Programs and Methods
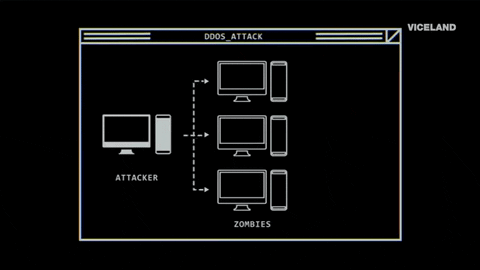 DDoS attack or Distributed Denial of Service attack is an attack aiming to destroy the service of a website by crashing its server by sending a lot of packets and requests to the server. The hackers usually use tools like the low orbit ion cannon, ping of death, SYN flood, HTTP flood & more.
DDoS attack or Distributed Denial of Service attack is an attack aiming to destroy the service of a website by crashing its server by sending a lot of packets and requests to the server. The hackers usually use tools like the low orbit ion cannon, ping of death, SYN flood, HTTP flood & more.
343. E-commerce Cybersecurity - Enhancing Data Protection in 2021
 In 2020, the COVID-19 pandemic has completely changed the situation in the shopping industry: both e-commerce and brick-and-mortar were affected
In 2020, the COVID-19 pandemic has completely changed the situation in the shopping industry: both e-commerce and brick-and-mortar were affected
344. Preventing Man in the Middle Attacks - A How-To Guide
 There are many cyber threats out there. Usually, they’re motivated by money or political gain, but it can also be simple mischief. However, motivation is of little significance when your business is under attack.
There are many cyber threats out there. Usually, they’re motivated by money or political gain, but it can also be simple mischief. However, motivation is of little significance when your business is under attack.
345. A Free Beginner’s Guide to DNS Security for Work From Home (WFH)
 Working at home does not mean compromise on security. All in all, it’s necessary to take decisive steps to enforce and sustain DNS protection measures.
Working at home does not mean compromise on security. All in all, it’s necessary to take decisive steps to enforce and sustain DNS protection measures.
346. Overcoming Security Risks in a Cloud-Based World
 The increased reliance on cloud-based infrastructure means organizations must adopt a layered approach to cybersecurity to protect their cloud workloads.
The increased reliance on cloud-based infrastructure means organizations must adopt a layered approach to cybersecurity to protect their cloud workloads.
347. An Intro to Multi-Factor Authentication and the Types of MFA
 This is an introduction to multi-factor authentication in the field of cybersecurity.
This is an introduction to multi-factor authentication in the field of cybersecurity.
348. Cloud Sourcing as a Crucial Component in Threat Prevention
 When it comes to security in the cloud, companies face constant, daily threats. This situation has only been exacerbated by the COVID-19 pandemic.
When it comes to security in the cloud, companies face constant, daily threats. This situation has only been exacerbated by the COVID-19 pandemic.
349. Scanta Named Finalist for Datatribe 2020 Cybersecurity Startup Challenge
 The world’s preeminent cyber startup foundry DataTribe selects Scanta as one of three companies worldwide to compete for the chance at $2M in seed capital.
The world’s preeminent cyber startup foundry DataTribe selects Scanta as one of three companies worldwide to compete for the chance at $2M in seed capital.
350. Understanding the Hazards of Ransomware-as-a-Service Attacks to Organizational Security
 If you've ever wondered why ransomware attacks are taking over businesses, this article explains it in detail. It also explains its future and evolution.
If you've ever wondered why ransomware attacks are taking over businesses, this article explains it in detail. It also explains its future and evolution.
351. Crypto Crime Falls as Platforms Step Up Security Measures
 A recent report by CipherTrace indicates that crypto-related crimes are on the low as the market matures. The market recently crossed the $2 trillion mark
A recent report by CipherTrace indicates that crypto-related crimes are on the low as the market matures. The market recently crossed the $2 trillion mark
352. Cybersecurity Takeaways From the Pandemic and Solutions for 2021
 In 2020, Cybersecurity has become more important than ever for businesses all over the world. Here's how to protect your data from cyberattacks going forward.
In 2020, Cybersecurity has become more important than ever for businesses all over the world. Here's how to protect your data from cyberattacks going forward.
353. 10 Steps to Ensuring Cyber Security for a Small Business
 How can your small business avoid being a victim of a cyber fraud? Here are 10 cyber security steps for small business safety.
How can your small business avoid being a victim of a cyber fraud? Here are 10 cyber security steps for small business safety.
354. Is There A Middle Ground Between Privacy and Convenience?

355. 7 Ways to Protect Your Company from Insecure Credentials
 Verizon’s 2020 DBIR reports that more than 80% of hacking-related breaches involve brute force or the use of lost or stolen credentials— here’s how to prevent weak or compromised credentials from being used in your company’s applications and network
Verizon’s 2020 DBIR reports that more than 80% of hacking-related breaches involve brute force or the use of lost or stolen credentials— here’s how to prevent weak or compromised credentials from being used in your company’s applications and network
356. 20 Data Security Risks Your Company Could Face in 2020
 Today, data security is top of mind for companies, consumers, and regulatory bodies. After years of unfettered participation in the data-driven digital age that was defined by an “anything goes” ethos and a “move fast and break things” mentality, this shifting sentiment is both drastic and welcome.
Today, data security is top of mind for companies, consumers, and regulatory bodies. After years of unfettered participation in the data-driven digital age that was defined by an “anything goes” ethos and a “move fast and break things” mentality, this shifting sentiment is both drastic and welcome.
357. The Looming Threat of Ransomware [Infographic]
 A look at how to prevent ransomware before it happens.
A look at how to prevent ransomware before it happens.
358. Don’t Let Fraud Cost Your Business
 We’ve all probably received a badly worded email in the past promising us a great fortune or claiming we are winners of a prize draw we didn’t enter.
We’ve all probably received a badly worded email in the past promising us a great fortune or claiming we are winners of a prize draw we didn’t enter.
359. How I Hacked the Lenovo Carme HW25P Smartwatch

360. Cyber Security vs Information Security
 Both cyber and information security are linked by the core discipline of security, and overlap between the two but we need to recognise the difference.
Both cyber and information security are linked by the core discipline of security, and overlap between the two but we need to recognise the difference.
361. Life in Smart Cities: Your Walk in the Park isn't Private Anymore
 Access control ensures authorized access to the city's municipalities, which is critical for ensuring the security of smart cities.
Access control ensures authorized access to the city's municipalities, which is critical for ensuring the security of smart cities.
362. What is Transport Layer Security (TLS)?
 This article's goal is to help you make these decisions to ensure the confidentiality and integrity communication between client and server.
This article's goal is to help you make these decisions to ensure the confidentiality and integrity communication between client and server.
363. Insiders Breach Your Organization’s Data (Data Tells Us So)
 Many company executives claim that the biggest threats to their data privacy are external threats, such as hackers or state-funded cyber-threats. However, companies are actually more likely to experience a data breach from an internal source, whether it is malicious or accidental.
Many company executives claim that the biggest threats to their data privacy are external threats, such as hackers or state-funded cyber-threats. However, companies are actually more likely to experience a data breach from an internal source, whether it is malicious or accidental.
364. Ensuring Security: A Guide for Web and Mobile Application Development
 Authentication and authorization for modern web and mobile applications are a key part of most development cycles. This story outlines some considerations.
Authentication and authorization for modern web and mobile applications are a key part of most development cycles. This story outlines some considerations.
365. WTF is Shamir's Secret Sharing Scheme And How Does It Preserve Your Privacy?
 An introduction to this privacy-preserving cryptographic technique and how Keyless is using it to transform the way we share and store private data across the internet.
An introduction to this privacy-preserving cryptographic technique and how Keyless is using it to transform the way we share and store private data across the internet.
366. White Hat Hackers Defend Hospitals From Rising Cyber Attacks
 The field of radiology is littered with cyber mines. And it only gets worse. Here are some real stories of hospital cyberattacks and expert recommendations.
The field of radiology is littered with cyber mines. And it only gets worse. Here are some real stories of hospital cyberattacks and expert recommendations.
367. Assessing Model Performance in Secrets Detection: Accuracy, Precision And Recall
 Detecting secrets in source code is like finding needles in a haystack: there are a lot more sticks than there are needles, and you don’t know how many needles might be in the haystack. In the case of secrets detection, you don’t even know what all the needles look like!
Detecting secrets in source code is like finding needles in a haystack: there are a lot more sticks than there are needles, and you don’t know how many needles might be in the haystack. In the case of secrets detection, you don’t even know what all the needles look like!
368. 5 Technology Trends For Manufacturing Companies To Follow in 2020
 The rapid evolution of technology has transformed manufacturing to a great scale. Digital manufacturing is the new trend to enhance the manufacturing process including product processing, supply chain, inventory management, and related services. Recent technological advancements have seen an explosion in the kinds of technologies and tools that are available for manufacturing brands.
The rapid evolution of technology has transformed manufacturing to a great scale. Digital manufacturing is the new trend to enhance the manufacturing process including product processing, supply chain, inventory management, and related services. Recent technological advancements have seen an explosion in the kinds of technologies and tools that are available for manufacturing brands.
369. What is Cyber Threat Intelligence?
 Cyber threats aimed at business are identified by Threat Intelligence.IT specialists and complex tools can read and analyze the threats
Cyber threats aimed at business are identified by Threat Intelligence.IT specialists and complex tools can read and analyze the threats
370. Cloud Desktops For Advanced Security and Disaster Solutions
 Cloud desktops provide virtual firewall & advanced antivirus protection with enterprise-grade security. Get Disaster recovery as a Service by deploying cloud.
Cloud desktops provide virtual firewall & advanced antivirus protection with enterprise-grade security. Get Disaster recovery as a Service by deploying cloud.
371. WFH/WFA Workplace Create New Cybersecurity Threats: Are You Prepared?
 IBM estimates that in 2021 a data breach incident costs enterprises $4.24 million on average. Even though the workforce is returning to offices in varying capacities, research on the topic indicates that managers are planning for a hybrid work future. According to Gartner, 82% of business leaders plan to let employees continue to work from home (WFH) in at least some capacity, while 47% plan to allow employees to do so permanently.
IBM estimates that in 2021 a data breach incident costs enterprises $4.24 million on average. Even though the workforce is returning to offices in varying capacities, research on the topic indicates that managers are planning for a hybrid work future. According to Gartner, 82% of business leaders plan to let employees continue to work from home (WFH) in at least some capacity, while 47% plan to allow employees to do so permanently.
372. Improving IoT Device Security Prevention from Zero-Day Attacks
 Security for the “Internet of Things” (or IoT) is still relatively new to a majority of organizations.
Security for the “Internet of Things” (or IoT) is still relatively new to a majority of organizations.
373. How a DNS Firewall Can Improve Networking Security for Your Business
 Business is driven by the well-calculated balance between spending and earning, and even the most successful companies are in a constant search for ways to cut costs. But what’s often a “nice to have” for larger companies can be a matter of survival for startups and small family businesses, who are usually only able to spend money on the essentials.
Business is driven by the well-calculated balance between spending and earning, and even the most successful companies are in a constant search for ways to cut costs. But what’s often a “nice to have” for larger companies can be a matter of survival for startups and small family businesses, who are usually only able to spend money on the essentials.
374. ☢️ Dissecting DEFENSOR - An Android Malware That Affects Your Banking Apps
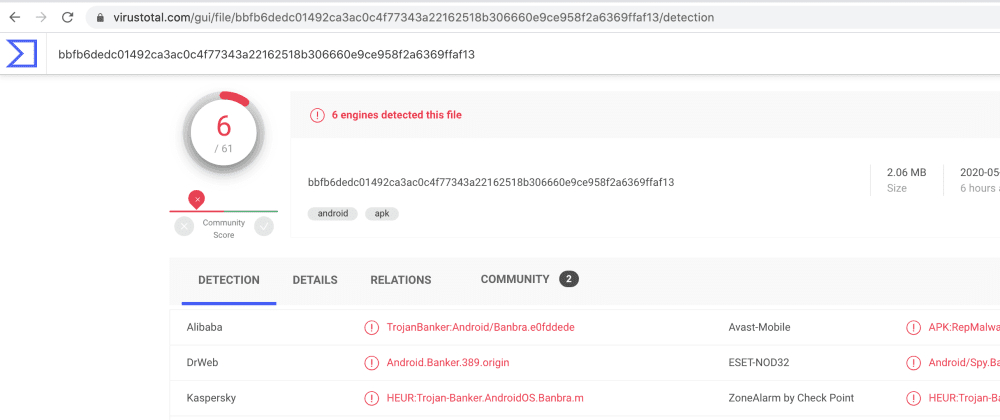 Android malware apps are nothing new, but this one is of particular interest in how it implements no such functionality that can be readily detected by security products. The apps named DEFENSOR ID and Defensor Digital rely mainly on Android's Accessibility Service to conduct malicious activities, and go undetected.
Android malware apps are nothing new, but this one is of particular interest in how it implements no such functionality that can be readily detected by security products. The apps named DEFENSOR ID and Defensor Digital rely mainly on Android's Accessibility Service to conduct malicious activities, and go undetected.
375. Imagine Yourself Being A Hacker [Beginner's Guide]

376. 6 Most Common Job Titles in Cybersecurity
 Honestly speaking the word Cyber security professional sounds kind of cool as well. However, if you’re willing to become a Cyber security professional yourself
Honestly speaking the word Cyber security professional sounds kind of cool as well. However, if you’re willing to become a Cyber security professional yourself
377. Cloud Security: Is it Worth it?
 Storing and managing corporate data by applying the cloud is becoming more and more popular. Companies grow, and it gets too expensive, and resources consuming to store their data on traditional servers. To prove it, look at the research conducted by Google in 2019 that includes insights for the cloud computing market for the next 10 years.
Storing and managing corporate data by applying the cloud is becoming more and more popular. Companies grow, and it gets too expensive, and resources consuming to store their data on traditional servers. To prove it, look at the research conducted by Google in 2019 that includes insights for the cloud computing market for the next 10 years.
378. Network Vulnerabilities: How to Identify Them and Assign Risk Ratings
 Vulnerability management is the cyclical practice of identifying, classifying, remediating, and mitigating vulnerabilities. In computer security, a vulnerability is a weakness in the system, a threat actor can exploit the weakness, to perform unauthorized actions within organizational applications or network.
Vulnerability management is the cyclical practice of identifying, classifying, remediating, and mitigating vulnerabilities. In computer security, a vulnerability is a weakness in the system, a threat actor can exploit the weakness, to perform unauthorized actions within organizational applications or network.
379. How To Protect Online Art Platforms From Cyber Attacks
 The potential cybersecurity threats that can thwart the long-awaited momentum of the online art market and how to avoid these risks.
The potential cybersecurity threats that can thwart the long-awaited momentum of the online art market and how to avoid these risks.
380. How to Improve Network Security and Visibility in 2020 and 2021
 With the number of products available, it can be an uphill task to try to ensure robust network security and visibility. This, however, is a task that must be accomplished if you want to be competitive.
With the number of products available, it can be an uphill task to try to ensure robust network security and visibility. This, however, is a task that must be accomplished if you want to be competitive.
381. Zoom's Security Issues Now Endanger The Online Privacy of Minors and Teachers
 In this season of pandemic, all businesses are grounded and forced to continue their operations through online channels. There is excessive use of digital channels for conferencing purposes, communication, and file transferring.
In this season of pandemic, all businesses are grounded and forced to continue their operations through online channels. There is excessive use of digital channels for conferencing purposes, communication, and file transferring.
382. An Introduction to Malware Analysis
 Malicious software (Malware) are either programs or files that are intended to cause harm to a system and thereby its user.
Malicious software (Malware) are either programs or files that are intended to cause harm to a system and thereby its user.
383. Do Passwordless Technologies Have an Impact on Cybersecurity?
 Contrary to popular belief, traditional passwords are not the best way to protect sensitive information on our digital devices.
Contrary to popular belief, traditional passwords are not the best way to protect sensitive information on our digital devices.
384. What To Do When Your Identity Has Been Stolen: 6 Practical Steps To Take
 So your identity has been stolen...what do you do? In this article we share 6 steps you should take immediately. Remember acting quickly is your best defense.
So your identity has been stolen...what do you do? In this article we share 6 steps you should take immediately. Remember acting quickly is your best defense.
385. Internet Safety for Kids – How to Keep Your Children Safe Online
 Roughly 50% of children aged between 12 and 16 consider themselves addicted to their smartphones or laptops. While such an addiction can be effortlessly dealt with by responsible parents, ensuring that children are safe while traveling through the online environment is arguably more challenging.
Roughly 50% of children aged between 12 and 16 consider themselves addicted to their smartphones or laptops. While such an addiction can be effortlessly dealt with by responsible parents, ensuring that children are safe while traveling through the online environment is arguably more challenging.
386. How to Stay Safe When Browsing Online or Viewing Emails at Home or Work
 Here are some essential password management tips and tricks to staying safe online. Learn how to bolster security protection in the 21st century.
Here are some essential password management tips and tricks to staying safe online. Learn how to bolster security protection in the 21st century.
387. 5 Tips for Integrating Security into Development - Part 1
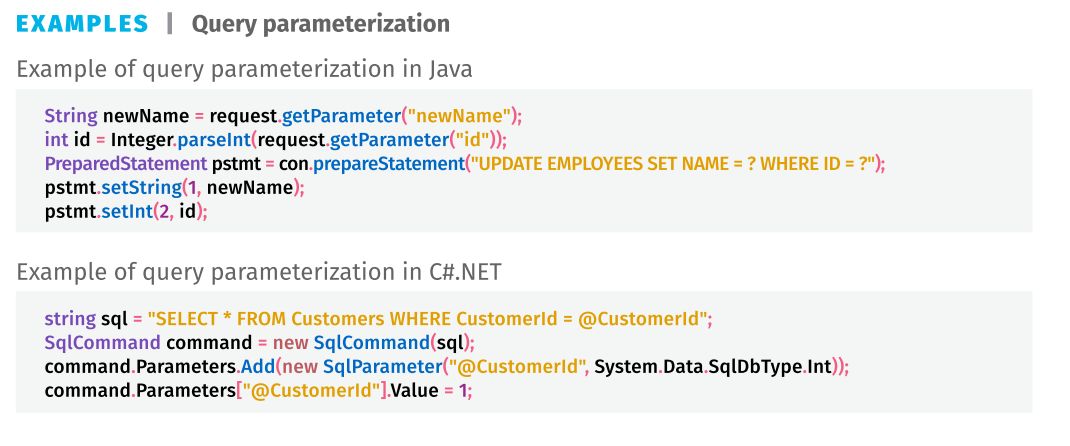 In this two-part series, we’re bringing you secure coding best practices and practical tips that you can lean on when integrating security into development
In this two-part series, we’re bringing you secure coding best practices and practical tips that you can lean on when integrating security into development
388. Cybersecurity is a Big Competitive Advantage. Secure Your Win.
 A majority of America's small business owners aren't worried about being the victim of a cyberattack. Why?
A majority of America's small business owners aren't worried about being the victim of a cyberattack. Why?
389. Good Ways To Make Your Data More Secure
 Data security is a business challenge and a business opportunity, not a mere technical task for your IT department.
Data security is a business challenge and a business opportunity, not a mere technical task for your IT department.
390. How Microsoft’s Revelation of Four Zero-Days Has Affected the Number of Attempted Attacks
 With the revelation of four zero-day vulnerabilities currently affecting Microsoft Exchange Server, Check Point Research (CPR) shares its findings on exploits
With the revelation of four zero-day vulnerabilities currently affecting Microsoft Exchange Server, Check Point Research (CPR) shares its findings on exploits
391. Your Top 5 Software Composition Analysis Questions Answered
 With the fast growth of the usage of open source in all industries, the need to track its components becomes dire as ever. Software Composition Analysis (SCA) is an open source component management solution for providing and automating visibility into the open source in your software.
With the fast growth of the usage of open source in all industries, the need to track its components becomes dire as ever. Software Composition Analysis (SCA) is an open source component management solution for providing and automating visibility into the open source in your software.
392. What You Should Know About Zero-Party Data
 Zero-party data (ZPD) means a company only collects user data that is freely given. Period. But why would a modern business, raised on the wonders of Big Data, undertake such a foolish philosophy? Maybe because they aren’t fans of financial ruin.
Zero-party data (ZPD) means a company only collects user data that is freely given. Period. But why would a modern business, raised on the wonders of Big Data, undertake such a foolish philosophy? Maybe because they aren’t fans of financial ruin.
393. IoT Security Threats in Retail: How Do We Eliminate Them?
 The number of smart connected devices on the Internet, including cameras, machines, and sensors, has grown exponentially. According to the premier market research firm, International Data Corporation, by 2025, it’s estimated that we will have approximately 41.6 billion connected devices.
The number of smart connected devices on the Internet, including cameras, machines, and sensors, has grown exponentially. According to the premier market research firm, International Data Corporation, by 2025, it’s estimated that we will have approximately 41.6 billion connected devices.
394. 4 Common Web App Vulnerabilities and How to Combat Them
 Expert's advice on how to protect a web application against malicious attacks, accidental damage, and commonly known vulnerabilities in 2021.
Expert's advice on how to protect a web application against malicious attacks, accidental damage, and commonly known vulnerabilities in 2021.
395. Top Penetration Testing Tools for Professionals
 Looking for penetration testing tools, which is good. Here is the list of some best tools with comparison. Check out this post.
Looking for penetration testing tools, which is good. Here is the list of some best tools with comparison. Check out this post.
396. The Rise and Fall of APTR1 Exploit Jian
 Cyber weapons are digital and volatile by nature. Stealing them and transferring from one continent to another, can be as simple as sending an email.
Cyber weapons are digital and volatile by nature. Stealing them and transferring from one continent to another, can be as simple as sending an email.
397. How to Stay Safe Online: Cybersecurity Tips from the HackerNoon Community
 In this thread, the slogging community shares their online security hacks for peaceful and safe web surfing.
In this thread, the slogging community shares their online security hacks for peaceful and safe web surfing.
398. Security For PMs: How-To [Part II]
 In the first part of this article, we have talked about the ways in which your customers may check if your statements of the security matter in your company line up with reality. Now let us focus on how to ensure that your security practices are actually working and how to avoid the numerous pitfalls on this way.
In the first part of this article, we have talked about the ways in which your customers may check if your statements of the security matter in your company line up with reality. Now let us focus on how to ensure that your security practices are actually working and how to avoid the numerous pitfalls on this way.
399. Not All Password Managers Are Created Equal: Which is the Best?
 Web-based password managers have emerged as a response to the proliferation of web applications.
Web-based password managers have emerged as a response to the proliferation of web applications.
400. 5 Cybersecurity Aspects to Consider for Your Organization for a Safer 2021
 Remote work and how it has driven long-overdue reconsiderations of our connectivity, collaboration, and cybersecurity standards and approaches.
Remote work and how it has driven long-overdue reconsiderations of our connectivity, collaboration, and cybersecurity standards and approaches.
401. FinTech Security Needs To Be Taken More Seriously Than It Is
 Cyberattacks the biggest barrier to financial innovation
Cyberattacks the biggest barrier to financial innovation
402. How to Revolutionize Data Security Through Homomorphic Encryption
 For decades, we have benefited from modern cryptography to protect our sensitive data during transmission and storage. However, we have never been able to keep the data protected while it is being processed.
For decades, we have benefited from modern cryptography to protect our sensitive data during transmission and storage. However, we have never been able to keep the data protected while it is being processed.
403. How To Protect Your Online Applications From Pass-the-Cookie Cyber Attacks
 How to strengthen your online apps against cloud service attacks such as ‘pass-the-cookie’ attacks.
How to strengthen your online apps against cloud service attacks such as ‘pass-the-cookie’ attacks.
404. What You Need To Consider When Hiring A Security Analyst
 Recent statistics released by Risk Based Security prove that data breaches have reached significant highs in 2019: 38,000 breaches, a figure that marks an increase of over 50 per cent in cybersecurity hacks through the last four years.
Recent statistics released by Risk Based Security prove that data breaches have reached significant highs in 2019: 38,000 breaches, a figure that marks an increase of over 50 per cent in cybersecurity hacks through the last four years.
405. 10 Things I Did To Increase CloudTrail Logs Security

406. Cerber Ransomware Explained: How to Protect, Detect, and Recover
 This blog post covers Cerber ransomware, infection methods, the working principle, how to remove Cerber ransomware, and how to protect against Cerber.
This blog post covers Cerber ransomware, infection methods, the working principle, how to remove Cerber ransomware, and how to protect against Cerber.
407. How I Exploited Millennium MP3 Studio 2.0 with Shellcode Payload

408. Everything You Need to Know About Content Security Policy (CSP)
 Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types of attacks including XSS and data injection attacks.
Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types of attacks including XSS and data injection attacks.
409. How To Make an Internal Employee Survey on Endpoint Security
 Employee’s Endpoint security Internal Survey-Template
Employee’s Endpoint security Internal Survey-Template
410. Why Bitcoin is Not an "Ideal" Ransomware Currency
 Bitcoin ain't a ticket to “cyber gangsta’s paradise.”
Bitcoin ain't a ticket to “cyber gangsta’s paradise.”
411. How to Keep Yourself from Becoming a Victim of Flytrap Malware
 Threat actors are leveraging common user misunderstandings that logging into the true domain is always secure.
Threat actors are leveraging common user misunderstandings that logging into the true domain is always secure.
412. Software Security Primer
 As a developer, when you think of security, what comes to mind? Is it clear what are different aspects that need to be handled to make a software secure? And why you need to do that?
As a developer, when you think of security, what comes to mind? Is it clear what are different aspects that need to be handled to make a software secure? And why you need to do that?
413. What happens after you accidentally leak secrets to a public code repository
 What happens after you accidentally leak secrets to a public code repository.
What happens after you accidentally leak secrets to a public code repository.
414. How to Develop Your SAAS Application with a Security Mindset
 Are you looking to build a SaaS platform? If yes, then read this blog to know how to build a SaaS application with security in mind.
Are you looking to build a SaaS platform? If yes, then read this blog to know how to build a SaaS application with security in mind.
415. Protect Angular Code Against Theft and Reverse-Engineering
 In this step-by-step guide, you'll learn how to protect your Angular code from being stolen or reverse-engineered, by leveraging the power of Jscrambler.
In this step-by-step guide, you'll learn how to protect your Angular code from being stolen or reverse-engineered, by leveraging the power of Jscrambler.
416. Healthcare – Fighting the Cyber Infection Epidemic
 For most of the population, cyber-security is not the first item that comes to mind when thinking about healthcare.
For most of the population, cyber-security is not the first item that comes to mind when thinking about healthcare.
417. Data Privacy and risks of the Remote Work Environment
 Digital Transformation in every field of our lives has led to the increased collection of our personal data on every device we touch from laptops to mobile phones, to tablets, leaving a digital trail. This data is then used for various purposes such as targeted advertising, research proposes or even corporate espionage. But boundaries need to be set to avoid corporate or other malicious parties taking advantage of this information or even corrupting it.
Digital Transformation in every field of our lives has led to the increased collection of our personal data on every device we touch from laptops to mobile phones, to tablets, leaving a digital trail. This data is then used for various purposes such as targeted advertising, research proposes or even corporate espionage. But boundaries need to be set to avoid corporate or other malicious parties taking advantage of this information or even corrupting it.
418. 5 Data Security Mistakes Small Businesses Making
 Verizon’s 2020 Data Breach Investigation Report indicates that cybercriminals don’t care how big or small your business is — they want your credentials and data regardless (and will do what they can to get them)
Verizon’s 2020 Data Breach Investigation Report indicates that cybercriminals don’t care how big or small your business is — they want your credentials and data regardless (and will do what they can to get them)
419. Quantum Contingencies in Cryptography: A Short Primer
 Are we at the cradle of a quantum age?
Are we at the cradle of a quantum age?
420. Privacy Protection and Web3 Analytics
 Though there have been more and more developers and product designers joining Web3.0 world in recent years, it is almost ignored by most of them that they are still using centralized infrastructure — data analytic tools — to build apps and webs. Every minute, project builders are making themselves part of the reason for data breach events, as they have to collect user data intendedly or unintendedly for product improvement.
Though there have been more and more developers and product designers joining Web3.0 world in recent years, it is almost ignored by most of them that they are still using centralized infrastructure — data analytic tools — to build apps and webs. Every minute, project builders are making themselves part of the reason for data breach events, as they have to collect user data intendedly or unintendedly for product improvement.
421. Automate GraphQL Backed Applications' Security Testing
 Working with the latest tech is fun. It’s fresh and exciting. As developers we
feel invigorated by being on the bleeding edge. Consider us thrill
seekers.
Working with the latest tech is fun. It’s fresh and exciting. As developers we
feel invigorated by being on the bleeding edge. Consider us thrill
seekers.
422. How to Perform a Cyber Security Risk Assessment: A Step-by-Step Guide
423. Getting Into The Mind Of The Hacker: Here's How Hackers Steal Your Keys, Secrets, and Passwords
 In this post, I’m going to share concepts, methods, and tools used by researchers both for finding secrets and exploiting them. I’ll also list mitigation ideas.
In this post, I’m going to share concepts, methods, and tools used by researchers both for finding secrets and exploiting them. I’ll also list mitigation ideas.
424. Digital Threats and Countermeasures: How Close are We to a Cyberwar?
 Cyberwar became a reality more than a decade ago. People not connected to the creation of cyberweapons can see only the tip of the iceberg.
Cyberwar became a reality more than a decade ago. People not connected to the creation of cyberweapons can see only the tip of the iceberg.
425. How to Achieve 99% Fault Tolerant Consensus
 By requiring observers to actively watch the consensus, you can increase fault tolerance all the way to 99%.
By requiring observers to actively watch the consensus, you can increase fault tolerance all the way to 99%.
426. 10 Cyber Security Hacks To Make Your SMB a Tougher Target This Year
 From data security to automation, I’ve got the scoop from 14 cybersecurity and small business experts on the 10 steps to cyber security that you can implement for your small to midsize business.
From data security to automation, I’ve got the scoop from 14 cybersecurity and small business experts on the 10 steps to cyber security that you can implement for your small to midsize business.
Thank you for checking out the 426 most read stories about Cyber Security on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

