Let's learn about Infosec via these 35 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
1. How to Get a Reverse Shell on macOS Using A Flipper Zero as a BadUSB
 Using a Flipper Zero as an ethical pentesting device to establish a reverse shell on a macOS computer.
Using a Flipper Zero as an ethical pentesting device to establish a reverse shell on a macOS computer.
2. What is URL Masking and How Does It Work?
 Be careful of the latest engineering technique called "URL Masking", it's quite dangerous.
Be careful of the latest engineering technique called "URL Masking", it's quite dangerous.
3. We Need to Talk About Nigeria and Cybersecurity
 Keeping information secured and protecting the integrity of data over the internet is now becoming a huge and complex task, due to the increasing number of threats to the information security.
Keeping information secured and protecting the integrity of data over the internet is now becoming a huge and complex task, due to the increasing number of threats to the information security.
4. I Have My Own AWS VPC, and Now You Can Too!
 Let's see how a default VPC is configured in AWS, CIDR block, the associated subnets within it, routes, NACLs and Security Groups.
Let's see how a default VPC is configured in AWS, CIDR block, the associated subnets within it, routes, NACLs and Security Groups.
5. I Could Crash Your Instagram Remotely. But I Chose to Report It.
 On April 2019, I had the foolish idea of testing Facebook security (and more specifically Instagram security), after I got informed that the company enabled a new setting on their assets (called Whitehat Settings), making easier for researchers to discover new vulnerabilities (pinning was not a problem, I am just a bit lazy sometimes :P).
On April 2019, I had the foolish idea of testing Facebook security (and more specifically Instagram security), after I got informed that the company enabled a new setting on their assets (called Whitehat Settings), making easier for researchers to discover new vulnerabilities (pinning was not a problem, I am just a bit lazy sometimes :P).
6. MITRE ATT&CK & D3FEND Framework are Redefining Counter-efforts to Cyberattacks
 Implement best security controls with Mitre ATT&CK & D3FEND frameworks
Redefine your organizational security posture to withstand emerging and advance threats
Implement best security controls with Mitre ATT&CK & D3FEND frameworks
Redefine your organizational security posture to withstand emerging and advance threats
7. The Trouble with FIPS
 FIPS 140 sets the standard for cryptography used in the United States, but it's got problems. Because of FIPS, we all have problems.
FIPS 140 sets the standard for cryptography used in the United States, but it's got problems. Because of FIPS, we all have problems.
8. Inside a Hacker's Backpack: Gadgets, Tips, and Tricks for Hackers
 Not ever hack job requires just a laptop and some software to gain privileges into a system. Sometimes, something extra is required to make the job very easy
Not ever hack job requires just a laptop and some software to gain privileges into a system. Sometimes, something extra is required to make the job very easy
9. My SIM swap attack: How I almost lost $71K, and how to prevent it

10. 5 Reasons Why We Dont Need To Worry About the SolarWinds Hack
 There is quite a bit of consternation in the tech universe about the Solar Winds hack. Here are five reasons not to worry about the Solar Winds hack because these are much more important.
There is quite a bit of consternation in the tech universe about the Solar Winds hack. Here are five reasons not to worry about the Solar Winds hack because these are much more important.
11. Mutual Human Authorization: A New Standard in Data Privacy
 Mutual Human Authorization is a digital communication protocol that SharePass is pioneering to help address persistent data privacy and security gaps.
Mutual Human Authorization is a digital communication protocol that SharePass is pioneering to help address persistent data privacy and security gaps.
12. 5 Best Browser Extensions For Protecting Your Privacy Online
 It is essential for every internet user to comprehend the importance of browser security capabilities to assure they browse the internet safely. Protecting your browser might mean limited functionality of some web sites, but it’ll shield your most sensitive information as well.
It is essential for every internet user to comprehend the importance of browser security capabilities to assure they browse the internet safely. Protecting your browser might mean limited functionality of some web sites, but it’ll shield your most sensitive information as well.
13. A Tale of Two Cities: Economic vs Digital Democracy
 More than new laws and fines, we need to reconsider data ownership as a whole and discover new structures that place control back into the hands of the people.
More than new laws and fines, we need to reconsider data ownership as a whole and discover new structures that place control back into the hands of the people.
14. Viewing K8S Cluster Security from the Perspective of Attackers (Part 1)
 Based on previous penetration testing experience, we have sorted out the possible security issues under the K8S cluster architecture.
Based on previous penetration testing experience, we have sorted out the possible security issues under the K8S cluster architecture.
15. 'I Worked for Free to Get the Experience': Chris Ray, CISO & Security Researcher
 Meet Chris Ray, CISO, Security Researcher, and HackerNoon Contributor.
Meet Chris Ray, CISO, Security Researcher, and HackerNoon Contributor.
[16. CyberSec Games Part I:
Backdoors & Breaches](https://hackernoon.com/cybersec-games-part-i-backdoors-and-breaches-96393b0z)
 Backdoors & Breaches is an Incident Response Card Game that contains 52 unique cards to help you conduct incident response tabletop exercises and learn attack tactics, tools, and methods.
Backdoors & Breaches is an Incident Response Card Game that contains 52 unique cards to help you conduct incident response tabletop exercises and learn attack tactics, tools, and methods.
17. Your USB Gadget Could Be Weaponized
 Cybersecurity experts have been warning us for years about using USB devices. We look at how an ordinary USB-powered device can be easily weaponized.
Cybersecurity experts have been warning us for years about using USB devices. We look at how an ordinary USB-powered device can be easily weaponized.
18. On Making The Internet A Safer Space: Inti De Ceukelaire, Head Of Hackers At Intigriti
 Intigriti co-founder, Inti De Ceukelaire, shares their origin story, what makes him excited about his job, and the technology he is currently excited about.
Intigriti co-founder, Inti De Ceukelaire, shares their origin story, what makes him excited about his job, and the technology he is currently excited about.
19. Introduction to the Zero Trust Security Architecture — a Concept, Not A Product
 "Zero Trust" has been around for years. Now, I am writing to lay the fundamental concepts and introduce anyone who wants to bring Zero Trust into practice.
"Zero Trust" has been around for years. Now, I am writing to lay the fundamental concepts and introduce anyone who wants to bring Zero Trust into practice.
20. How Security Operations is a Journey, Not a Destination: An Analyst’s Perspective
 “No matter how strong a defense, a stronger offense will always shatter it.”— Byakuya Kuchiki
“No matter how strong a defense, a stronger offense will always shatter it.”— Byakuya Kuchiki
21. Artificial Intelligence is No Match for Natural Stupidity
 A Lazy Introduction to AI for Infosec.
A Lazy Introduction to AI for Infosec.
22. Questions For The Most Controversial Hacker Of This Generation: Sabu
 I believe strongly if we get answers to these questions from a source with gravitas, such as Sabu, we will understand how to navigate the future.
I believe strongly if we get answers to these questions from a source with gravitas, such as Sabu, we will understand how to navigate the future.
23. What is “Cyberbiosecurity?" and why we should stop using the term
 The term cyberbiosecurity is rapidly making its way around the internet, academic, and government communities. If you want a silly analogy, you might say its spreading like an emerging infection through various host communities. Specifically, communities with no innate immunity to fight off the misinformation.
The term cyberbiosecurity is rapidly making its way around the internet, academic, and government communities. If you want a silly analogy, you might say its spreading like an emerging infection through various host communities. Specifically, communities with no innate immunity to fight off the misinformation.
24. Who Should the CISO Report to?
 Should the CEO be the sole decision-maker for a CISO's plans?
Should the CEO be the sole decision-maker for a CISO's plans?
25. Understanding & Recognizing Different Cyber Threats: What to Look Out For
 This article will dive into understanding & recognizing some cyber threats. It will not cover every example for each attack or every attack.
This article will dive into understanding & recognizing some cyber threats. It will not cover every example for each attack or every attack.
26. Why I Hire Non-IT Graduates in The Cybersecurity Field
 Essential elements you should have and why I hire non-IT graduates.
Essential elements you should have and why I hire non-IT graduates.
27. 10 things InfoSec Professionals Need to Know About Networking

28. America's Digital Maginot Line
 America's critical infrastructure appears to be protected by a Digital Maginot Line
America's critical infrastructure appears to be protected by a Digital Maginot Line
29. Using Macros and Emulation Voodoo to Solve a Crackme
 This time I’m tackling this beautiful crackme, the third of the series. To solve this we will use radare2’s macros and unicorn emulation. Let’s jump right in!
This time I’m tackling this beautiful crackme, the third of the series. To solve this we will use radare2’s macros and unicorn emulation. Let’s jump right in!
30. After scanning over a million apps — 3 things Mobile App Devs need to know about App Security
 Hackers might not attack you. Bots will.
Hackers might not attack you. Bots will.
31. Why Educational Platforms are a Favorite Target Among Attackers?
 Educational Institutes are easy prey for hackers to compromise and covertly launch Cyber Attacks/Malicious Campaigns under the hood, without divulging their real identity.
Educational Institutes are easy prey for hackers to compromise and covertly launch Cyber Attacks/Malicious Campaigns under the hood, without divulging their real identity.
32. Why You Should Protect Your Cell Phone Number and How to Do It
 With only your cell phone number hackers become you!
With only your cell phone number hackers become you!
33. What devs need to know about Encoding / Encryption / Hashing / Salting / Stretching
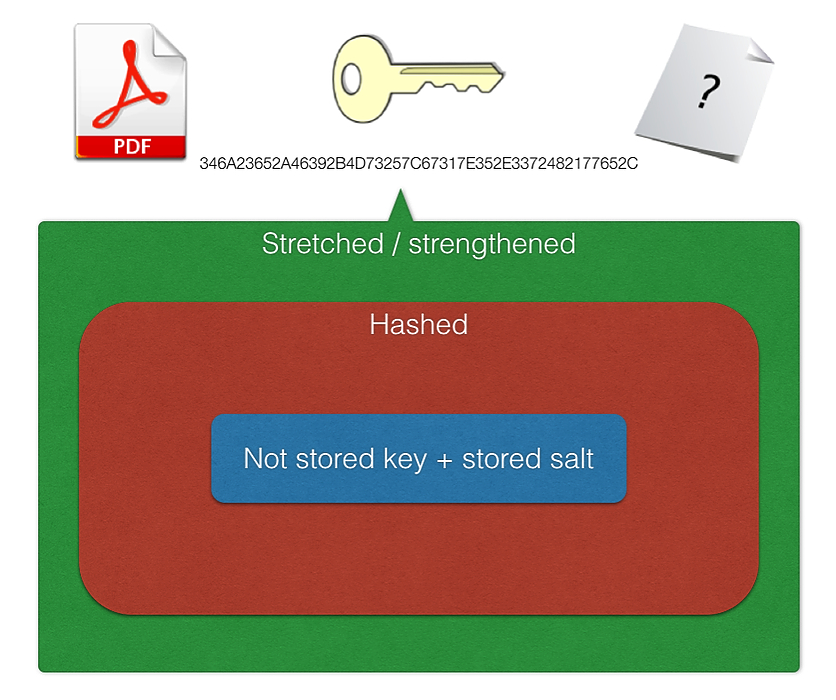 This is a typical exchange about encryption with someone willing to learn.
This is a typical exchange about encryption with someone willing to learn.
34. Part 2: Developing Software Requirements, A Case Study
 This is Part 2 of a 4 part series. Part 1: Why Software Requirements In The Real World Are Hard discusses the challenges of developing requirements and what good ones might look like. This post looks at the requirements development process and its outputs on a real-world project.
This is Part 2 of a 4 part series. Part 1: Why Software Requirements In The Real World Are Hard discusses the challenges of developing requirements and what good ones might look like. This post looks at the requirements development process and its outputs on a real-world project.
35. Insider Threats Facing Government Organizations: 3 Tips for Mitigation
 Verizon's Data Breach Investigation Report for 2022 (DBIR) was recently released and it has some good news and bad news when it comes to the risk of insider attacks.
Verizon's Data Breach Investigation Report for 2022 (DBIR) was recently released and it has some good news and bad news when it comes to the risk of insider attacks.
Thank you for checking out the 35 most read stories about Infosec on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

