Let's learn about Identity via these 29 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
1. The NuID Ecosystem: An Improved Identity Layer Putting Identity Ownership In Users’ Hands
 The internet grew without an identity layer, meaning it grew without a reliable way of knowing or verifying who you were connecting to which can be dangerous.
The internet grew without an identity layer, meaning it grew without a reliable way of knowing or verifying who you were connecting to which can be dangerous.
2. Resolving the Career Identity Crisis That Comes With Pivoting
 Pivoting in your career is often something positive. Still, it can come with unexpected negative feelings.
Pivoting in your career is often something positive. Still, it can come with unexpected negative feelings.
3. How Passwords Get Hacked
 Fernando Corbato pioneered the first computer password in 1960, being used as a personal point of entry on MIT's Compatible Time-Sharing System (CTSS). Just 2 years later, the CTSS was hacked and has been inspiring hackers ever since. There have been immense technological advancements since 1962 - how is it that today's hackers can get through 2-step authentication, biometrics, and security questions? Cryptographers predict a future that moves beyond passwords, but the issue seems to lie between cybersecurity and human nature.
Fernando Corbato pioneered the first computer password in 1960, being used as a personal point of entry on MIT's Compatible Time-Sharing System (CTSS). Just 2 years later, the CTSS was hacked and has been inspiring hackers ever since. There have been immense technological advancements since 1962 - how is it that today's hackers can get through 2-step authentication, biometrics, and security questions? Cryptographers predict a future that moves beyond passwords, but the issue seems to lie between cybersecurity and human nature.
4. How we hacked Hacker Noon's "Most Exciting Startup" award and won
 A cautionary tale of democracy online and why identity-based security is critical for elections large and small.
A cautionary tale of democracy online and why identity-based security is critical for elections large and small.
5. WTF is a Decentralized Identity?
 Decentralised identity is the Sign In With Google equivalent for the physical world, except you are in control of your data.
Decentralised identity is the Sign In With Google equivalent for the physical world, except you are in control of your data.
6. Identity Management Unchained - Taking the Metaverse Red Pill

7. Disinformation-as-a-Service: Content Marketing’s Evil Twin
 Are you tired of all the BS out there on the internet? It's about to get A LOT worse. Dirt-cheap disinformation-as-a-Service campaigns are a thing now.
Are you tired of all the BS out there on the internet? It's about to get A LOT worse. Dirt-cheap disinformation-as-a-Service campaigns are a thing now.
8. Orchestrating Identity in Web3.0
 Identity needs a major re-think for Web 3.0. We need private and effective, dynamic authorization - but no, I am not talking about blockchain.
Identity needs a major re-think for Web 3.0. We need private and effective, dynamic authorization - but no, I am not talking about blockchain.
9. How to Know When Your Nonprofit Needs an Identity Solution
 When your nonprofit has a ton of identities, it can easily become a problem. Find out when your organization needs an identity solution.
When your nonprofit has a ton of identities, it can easily become a problem. Find out when your organization needs an identity solution.
10. Which Communities within the Tech Industry Do You Identify With?
 I wonder whether a person even identifies as a part of their said community in many cases. Different entities make communities as broad or narrow as they want.
I wonder whether a person even identifies as a part of their said community in many cases. Different entities make communities as broad or narrow as they want.
11. 🆔 Plays 💻 for ₿; Legal KYC & Identification, "Online Identity" [Part 1]
 A unique summarization of Online Identity perspectives
A unique summarization of Online Identity perspectives
12. Type Identity and its Impact on API Design
 When designing an API, it's easy to use public types that denote resource identity to allow actions on a resource.
When designing an API, it's easy to use public types that denote resource identity to allow actions on a resource.
13. Our Careers and Our Identity Capital
 Identity capital is the accumulation of our personal assets, in other words, a culmination of things that make us who we are.
Identity capital is the accumulation of our personal assets, in other words, a culmination of things that make us who we are.
14. Cloud Complexity Causes Security Headaches - Can Identity Cure It?
 As the cloud industry grew by leaps and bounds, it has become more compex, making it harder to keep data safe from hackers. Can Identity Management help?
As the cloud industry grew by leaps and bounds, it has become more compex, making it harder to keep data safe from hackers. Can Identity Management help?
15. 5 Guidelines for Effective Digital Identity Verification
 The following best practices can help fintechs locate and approve new customers without friction or fraud while streamlining the customer journey.
The following best practices can help fintechs locate and approve new customers without friction or fraud while streamlining the customer journey.
16. A Guide to Authentication Methods
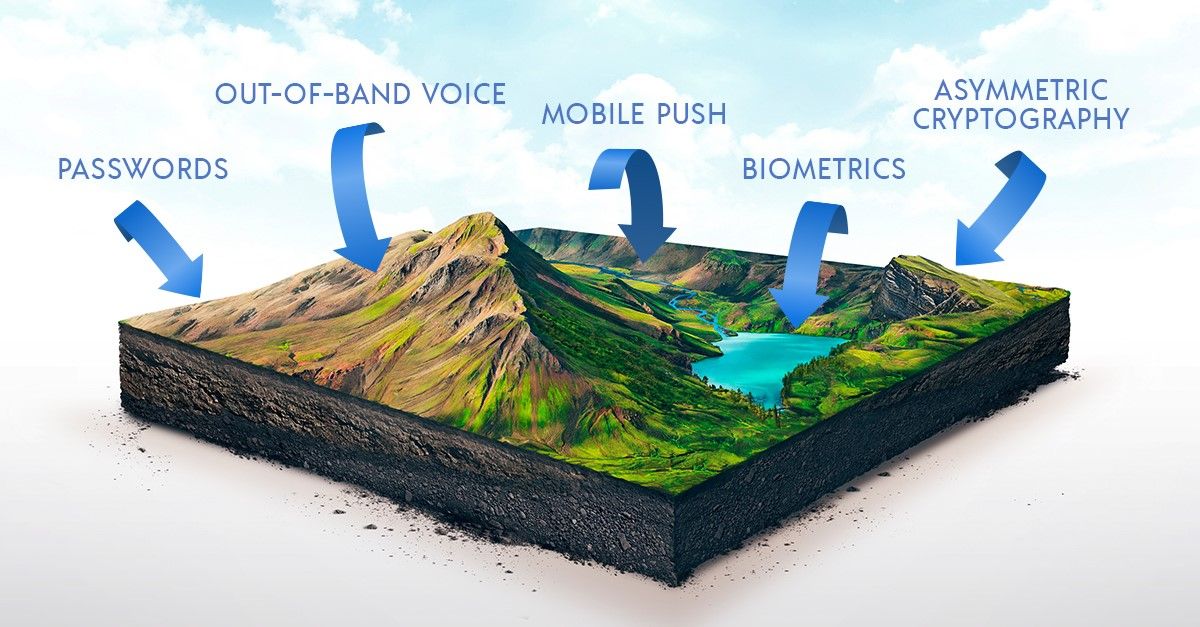 Staying safe on the internet has grown harder over the past few years as both technology and hackers have developed. Recently though, hackers are gaining an edge by not just manipulating the tech, but by manipulating the users themselves. In 2018, weak or stolen passwords were tied to over 80% of security breaches and in 2019, there were over 150,000 security incidents and nearly 4,000 confirmed data breaches. In 2020 alone, more than 15 billion stolen credentials were up for sale on the dark web. All this data points out the fact that our current way of protecting data is flawed, but making a new way to protect it while still maintaining security and convenience is a high mark to hit.
Staying safe on the internet has grown harder over the past few years as both technology and hackers have developed. Recently though, hackers are gaining an edge by not just manipulating the tech, but by manipulating the users themselves. In 2018, weak or stolen passwords were tied to over 80% of security breaches and in 2019, there were over 150,000 security incidents and nearly 4,000 confirmed data breaches. In 2020 alone, more than 15 billion stolen credentials were up for sale on the dark web. All this data points out the fact that our current way of protecting data is flawed, but making a new way to protect it while still maintaining security and convenience is a high mark to hit.
17. How the Quest for AI Could Make Us More Human
 Artificial intelligence (AI) is increasingly becoming a dominant part of everyday life. Whether you are aware of it or not, intelligent algorithms are all around us, trying to predict and understand you so they can help make your life easier in some way.
Artificial intelligence (AI) is increasingly becoming a dominant part of everyday life. Whether you are aware of it or not, intelligent algorithms are all around us, trying to predict and understand you so they can help make your life easier in some way.
18. How Decentralized Identifiers Will Shape the Future of Identity
 Exploring the W3C DID specification to enable Web3.0 identity solutions...
Exploring the W3C DID specification to enable Web3.0 identity solutions...
19. Why Self-Expression Is Missing In The Metaverse
 In the quest for self-expression we might as well hand over the keys to the AI because we clearly can't be trusted with it ourselves.
In the quest for self-expression we might as well hand over the keys to the AI because we clearly can't be trusted with it ourselves.
20. Identity and Access Management - IGA, IAM, and PAM Explained
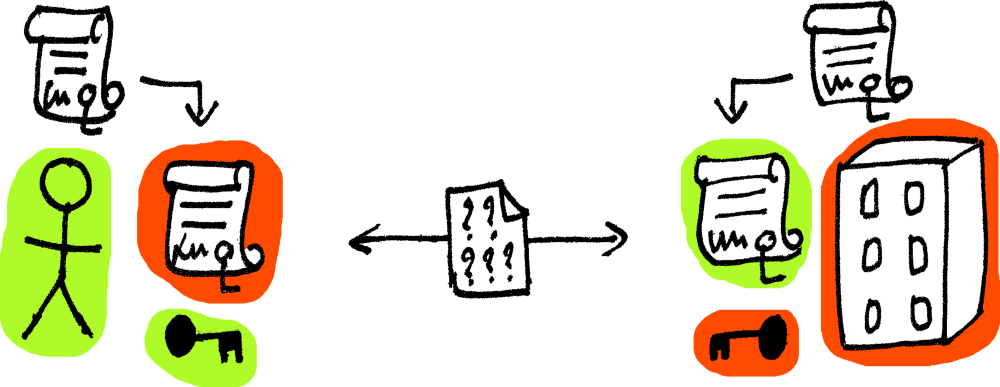 Identity is becoming less of a tool and more of a strategic framework to secure digital assets and protect data privacy.
Identity is becoming less of a tool and more of a strategic framework to secure digital assets and protect data privacy.
21. Future of NFTs - why art is just the beginning
 Why NFT is a real revolution not only in the field of art but also in our digital identity.
Why NFT is a real revolution not only in the field of art but also in our digital identity.
22. Identity and Blockchain’s Digital Vending Machines
 In a previous article, we outlined investment opportunities in companies utilizing decentralized software solutions such as blockchains.
In a previous article, we outlined investment opportunities in companies utilizing decentralized software solutions such as blockchains.
23. ”Money Doesn’t Equal Happiness” - Reality of Hackers’ Life
 Hackers are also ordinary people who fear, worry, and feel ashamed of their atrocities
Hackers are also ordinary people who fear, worry, and feel ashamed of their atrocities
24. Bringing Top 5 Unconventional Identity Verification Solutions to The Table
 Enterprises must not think twice before integrating themselves with AI-powered online identity verification processes to combat chargeback, counterfeits
Enterprises must not think twice before integrating themselves with AI-powered online identity verification processes to combat chargeback, counterfeits
25. The Twitter Hack Isn’t About Twitter or Bitcoin: It’s About Our Internet Identity
 Amid all of the news related to the pandemic, COVID-19, and global fears about the future of our planet, something that managed to break the news around the world was a global hack on Twitter’s platform.
Amid all of the news related to the pandemic, COVID-19, and global fears about the future of our planet, something that managed to break the news around the world was a global hack on Twitter’s platform.
26. 16 Premises for Web 3.0 - The Decentralized Web
 The following outlines premises required for a sustainable information management strategy in service of returning the World Wide Web fromthe tragedy of the commons.
The following outlines premises required for a sustainable information management strategy in service of returning the World Wide Web fromthe tragedy of the commons.
27. On Collusion
 Special thanks to Glen Weyl, Phil Daian and Jinglan Wang for review
Special thanks to Glen Weyl, Phil Daian and Jinglan Wang for review
28. Ranking and Reviewing the Top Identity Verification Service Providers
 A comprehensive work on how the biggest names in Identity Verification industry were tricked, trolled and fooled by a simple method.
A comprehensive work on how the biggest names in Identity Verification industry were tricked, trolled and fooled by a simple method.
29. SSL Certificates Publicly Prove The Identity of the Public Key Owner
 In the context of public key cryptography, certificates are a way to prove the identity of the owner of a public key.
In the context of public key cryptography, certificates are a way to prove the identity of the owner of a public key.
Thank you for checking out the 29 most read stories about Identity on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

