Let's learn about Password Security via these 112 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
1. 3 Tips on How to Stay Safe in Your Everyday Cyber Life
 Remember your mom always repeating "stay safe" phrase? Well, you should stay safe! Not only in streets, but also in cyberspace.
Remember your mom always repeating "stay safe" phrase? Well, you should stay safe! Not only in streets, but also in cyberspace.
2. Tips To Secure Your AWS Account
 It is no news that Cloud Computing technology has come to stay.
It is no news that Cloud Computing technology has come to stay.
3. The Gist of NIST: Password Recommendations to Remember
 NIST Guidelines have changed over the years so it is important to keep up with the changes. Password recommendations, such as eliminating special character use.
NIST Guidelines have changed over the years so it is important to keep up with the changes. Password recommendations, such as eliminating special character use.
4. How To Prevent Data Theft With Cybersecurity
 Technology has many advantages to offer businesses, but it also presents unique threats. Cyberattacks are levied at businesses and consumers alike, but companies are often directly targeted. This is because companies deal with large amounts of valuable data, including the personal information of customers and clients, and that can make for a veritable treasure trove for hackers. Protecting your company and your customers from bad actors on the world wide web should be a major priority. Here’s what you need to know.
Technology has many advantages to offer businesses, but it also presents unique threats. Cyberattacks are levied at businesses and consumers alike, but companies are often directly targeted. This is because companies deal with large amounts of valuable data, including the personal information of customers and clients, and that can make for a veritable treasure trove for hackers. Protecting your company and your customers from bad actors on the world wide web should be a major priority. Here’s what you need to know.
5. How to Protect Yourself Against Smishing Attacks
 As the threat landscape encapsulating organizations and companies grows increasingly sophisticated, and harbors a growing number of threats and vulnerabilities- organizations are getting more accustomed to commonplace scams such as phishing.
As the threat landscape encapsulating organizations and companies grows increasingly sophisticated, and harbors a growing number of threats and vulnerabilities- organizations are getting more accustomed to commonplace scams such as phishing.
6. Configure Your Linux With Passwordless Sudo For A Specific User
 Linux follows tough rules when it comes to permission. Being a root user or sudo user gives you permission to do almost anything which normal user don’t have. Several commands need sudo keyword to run and each time you try to run sudo, Linux asks for a password, today we will configure a passwordless sudo.
Linux follows tough rules when it comes to permission. Being a root user or sudo user gives you permission to do almost anything which normal user don’t have. Several commands need sudo keyword to run and each time you try to run sudo, Linux asks for a password, today we will configure a passwordless sudo.
7. Avoid Becoming a Victim to These Cybersecurity Threats in 2022
 With increased hacking activity focused on vulnerable businesses and at-home employees, cybersecurity has become a major business priority.
With increased hacking activity focused on vulnerable businesses and at-home employees, cybersecurity has become a major business priority.
8. Uncover Some of the Best Practices For Secret Management
 Secrets are digital credentials used for authentication and authorization.
Secrets are digital credentials used for authentication and authorization.
9. Why You Should Never Store Passwords in Web Browsers

10. How to Crack a Password Using Hashcat
 In this article, I discuss the best ways to crack passwords.
In this article, I discuss the best ways to crack passwords.
11. Passwords Are a Weak Security Link and Stolen Credentials Is Big Business
 Stolen credentials are big business thanks to poor password management from users and even nefarious actors on the Dark Web creating demand for stolen passwords
Stolen credentials are big business thanks to poor password management from users and even nefarious actors on the Dark Web creating demand for stolen passwords
12. 8 Most Important Cybersecurity Tricks Every Internet User Should Follow
 The cyber-world now accommodates billions of users. There are more than 4 billion internet users in the world today. It's just unfortunate that a large percentage of these users face cyber attacks from unknown sources. While some users are afraid of being attacked, others are ignorant of possible attacks. As an organisation or an individual that utilises the internet, it's a must to know some security tricks. If you're wondering what the tricks are, read on.
The cyber-world now accommodates billions of users. There are more than 4 billion internet users in the world today. It's just unfortunate that a large percentage of these users face cyber attacks from unknown sources. While some users are afraid of being attacked, others are ignorant of possible attacks. As an organisation or an individual that utilises the internet, it's a must to know some security tricks. If you're wondering what the tricks are, read on.
13. How Hackers Can Brute-Force Passwords And Find A Correct Key?
 Brute force attackers guess passwords, passphrases, and private keys in an attempt to eventually get the right answer and crack the security of a system, but how do they know when they have the right key?
Brute force attackers guess passwords, passphrases, and private keys in an attempt to eventually get the right answer and crack the security of a system, but how do they know when they have the right key?
14. How To Recover Lost Wi-Fi Password
 Most users, having entered the key to the wireless network on the router, remember about it when they need to connect a new device. In this article, we will examine in detail where to find the Wi-Fi password and, if necessary, change it.
Most users, having entered the key to the wireless network on the router, remember about it when they need to connect a new device. In this article, we will examine in detail where to find the Wi-Fi password and, if necessary, change it.
15. What Cybercrime Would Look Like in 2020
 2019 was the year of data breaches, phishing and ransomware attacks. From US real estate giant inadvertently leaking 900 million records to Danish hearing aid manufacturer Demant being a victim to a 95 million US dollars hack –cybercriminals ran rampant in the last year.
2019 was the year of data breaches, phishing and ransomware attacks. From US real estate giant inadvertently leaking 900 million records to Danish hearing aid manufacturer Demant being a victim to a 95 million US dollars hack –cybercriminals ran rampant in the last year.
16. Are You Where You Say You Are? - User Verification Based on Typing Patterns
 Join us down the rabbit hole to a place of suspense, of dastardly motives, of spies perhaps, and of lobbing off of thumbs, or gauging out of eyes.
Join us down the rabbit hole to a place of suspense, of dastardly motives, of spies perhaps, and of lobbing off of thumbs, or gauging out of eyes.
17. How Password Managers Can Protect You From Phishing
 Password managers are a convenient way to use strong, unique passwords everywhere. Another good thing about password managers is that they help protect you from malicious websites that attempt to "phish" passwords.
Password managers are a convenient way to use strong, unique passwords everywhere. Another good thing about password managers is that they help protect you from malicious websites that attempt to "phish" passwords.
18. Build your own User-friendly Cross-platform Password Manager
 I use a local password manager on my computer: I just stick with a password, which is the only password I memorize.
I use a local password manager on my computer: I just stick with a password, which is the only password I memorize.
19. Why Your Browser's Built-In Password Manager Isn't Enough
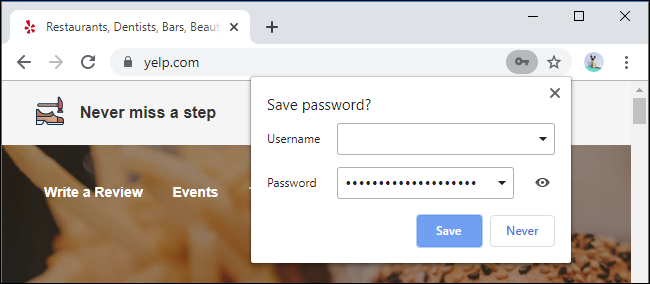 You may ask, "My web browser already has a built-in password manager, why do I need to install a new one?" There's actually a number of good reasons to install a password manager.
You may ask, "My web browser already has a built-in password manager, why do I need to install a new one?" There's actually a number of good reasons to install a password manager.
20. Should You Disable Autofill? - Here's How to Protect Your Passwords
 Password managers are beneficial to have but the autofill feature can be exploited by hackers. You should disable autofill on your browser to protect your data.
Password managers are beneficial to have but the autofill feature can be exploited by hackers. You should disable autofill on your browser to protect your data.
21. End-to-End Encryption Basics

22. Passwords Suck: Here Are 4 Ways We Can Fix Them
 Passwords are a critical part of cybersecurity that individuals and businesses use every day.
Passwords are a critical part of cybersecurity that individuals and businesses use every day.
23. Why Your Business Should Use Enterprise Password Management in 2021
 When choosing a password for a complete business structure, it must have higher security. That's where enterprise password management can help.
When choosing a password for a complete business structure, it must have higher security. That's where enterprise password management can help.
24. Password Security in 2022 — A Complete Guide
 A comprehensive guide to password security for all IT managers (and everyone else!). Learn why it is important, the risks of insecure passwords and how you can
A comprehensive guide to password security for all IT managers (and everyone else!). Learn why it is important, the risks of insecure passwords and how you can
25. Best Practises For Protecting Your Email

26. Personal Online Security: How to Stay Safe Online
 Every individual or organization must be mindful of securing their online data. Online security is essential for better online data privacy and security.
Every individual or organization must be mindful of securing their online data. Online security is essential for better online data privacy and security.
27. How Routee's Two Factor Authentication Works
 Two Factor Authentication or Two Factor Verification is a service used to confirm a user’s identity by combining two different elements. For example, Routee service combines a unique code with a verified phone number. This service can be used as part of an app or a website sign up process to increase security for the services offered.
Two Factor Authentication or Two Factor Verification is a service used to confirm a user’s identity by combining two different elements. For example, Routee service combines a unique code with a verified phone number. This service can be used as part of an app or a website sign up process to increase security for the services offered.
28. Manage Your Emails Like You Manage Your Passwords
 Add an extra security layer for the protection of your emails.
Add an extra security layer for the protection of your emails.
29. 10 Best Tactics For Your WooCommerce Store Security
 WooCommerce is a great plugin for WordPress to build an online store. With an entire eCommerce ecosystem and a dedicated global community, it has achieved the reputation of an industry standard. Still, this doesn’t mean that nothing c go wrong, especially if you ignore essential security precautions. Here are ten tips on how to make your business (and your customers’ data) safe.
WooCommerce is a great plugin for WordPress to build an online store. With an entire eCommerce ecosystem and a dedicated global community, it has achieved the reputation of an industry standard. Still, this doesn’t mean that nothing c go wrong, especially if you ignore essential security precautions. Here are ten tips on how to make your business (and your customers’ data) safe.
30. Public Computers Safety Tips: Interview with Cybersecurity Expert Ravi Bahethi
 With the amazing advances in cloud computing, many of us are finding that it is efficient to use a public or shared computer from time to time to check in on work and personal projects. Staying safe on a public computer is essential in keeping your data secure from cybercriminals. In this article, systems engineer and cybersecurity specialist Ravi Bahethi focuses on five tips to help you stay safe while using public computers.
With the amazing advances in cloud computing, many of us are finding that it is efficient to use a public or shared computer from time to time to check in on work and personal projects. Staying safe on a public computer is essential in keeping your data secure from cybercriminals. In this article, systems engineer and cybersecurity specialist Ravi Bahethi focuses on five tips to help you stay safe while using public computers.
31. The Ultimate Cyber Security Survival Guide
 Every action on the network leaves a digital footprint. For example, photos we post on social networks, statements on forums, likes and dislikes of videos. Moreover, a user activity leaves a digital trace - information about the sites browsed, purchases made, and geographical locations visited. There are many channels through which our personal data is exposed and the effects of abuse are very serious. Therefore, you should always be extremely careful about the use of world wide web and private data management.
Every action on the network leaves a digital footprint. For example, photos we post on social networks, statements on forums, likes and dislikes of videos. Moreover, a user activity leaves a digital trace - information about the sites browsed, purchases made, and geographical locations visited. There are many channels through which our personal data is exposed and the effects of abuse are very serious. Therefore, you should always be extremely careful about the use of world wide web and private data management.
32. LastPass Confirms Hackers Stole Encrypted Password Vaults... Four Months Ago
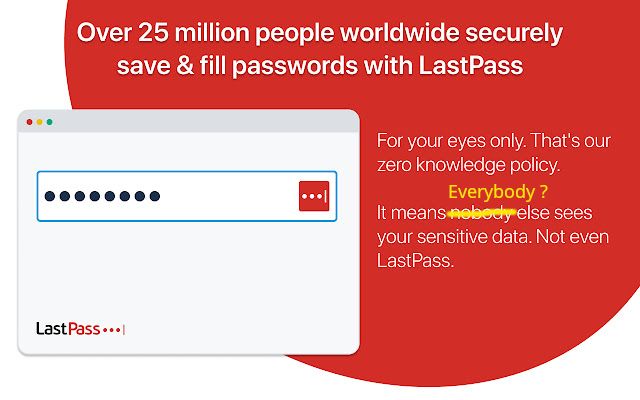 A password vault leak had happened four months ago and LastPass is only telling you that now.
A password vault leak had happened four months ago and LastPass is only telling you that now.
33. Is Configuring Access Control Effective When Defending Your Business Against Supercharged Ransom?
 As types of ransomware get more advanced and devastating, get to know more about some of the best ways to defend your business.
As types of ransomware get more advanced and devastating, get to know more about some of the best ways to defend your business.
34. Effects a Data Breach Can Have on Your Business in the Long Term

35. Uber & Thycotic: Are Password Vaults a Huge Security Vulnerability?
 The Uber hack showed that password vaults come with a security risk. Still, if set up correctly they improve security for companies.
The Uber hack showed that password vaults come with a security risk. Still, if set up correctly they improve security for companies.
36. The Anatomy of A Strong Passphrase That Is Easy To Remember
 We all have hundreds of online accounts. Ideally, as many of those accounts as possible have unique passwords. Unique passwords however present a difficult problem: No one can remember hundreds of strong passwords.
We all have hundreds of online accounts. Ideally, as many of those accounts as possible have unique passwords. Unique passwords however present a difficult problem: No one can remember hundreds of strong passwords.
37. 5 Promising Use Cases for Verifiable Credentials
 Verifiable credentials, which provide a system for provable electronic facts and documentation through cryptography and public keys, can seem like an abstract concept. We’re so used to seeing our credentials printed out – the driver’s license, the passport, the insurance card – that sticking codified IDs on a thumb drive or online seems odd and unnecessary. And as anyone who has used a cryptocurrency wallet can attest, the early forms of such decentralized IDs are hardly user friendly.
Verifiable credentials, which provide a system for provable electronic facts and documentation through cryptography and public keys, can seem like an abstract concept. We’re so used to seeing our credentials printed out – the driver’s license, the passport, the insurance card – that sticking codified IDs on a thumb drive or online seems odd and unnecessary. And as anyone who has used a cryptocurrency wallet can attest, the early forms of such decentralized IDs are hardly user friendly.
38. Need for an Identity Theft Protection
 Identity theft is a blanket term that covers fraudulent and even suspicious action through bank accounts and criminal databases. It is a violation of getting the financial or personal data of a person with the sole objective of feigning that person's name or identity to make purchases or transactions.
Identity theft is a blanket term that covers fraudulent and even suspicious action through bank accounts and criminal databases. It is a violation of getting the financial or personal data of a person with the sole objective of feigning that person's name or identity to make purchases or transactions.
39. How Much Has Your Password Grown Up With You?
 If you are growing up with technology, your password should be grown up too.
If you are growing up with technology, your password should be grown up too.
40. Common Attack Vectors that Authentication Services are Faced With
 Hacking user accounts on many websites is still easier than it could and should be. This blog post helps you secure your application against identity theft.
Hacking user accounts on many websites is still easier than it could and should be. This blog post helps you secure your application against identity theft.
41. What Is the GIAC Penetration Tester (GPEN) Certification?
 You need to ensure your resources are put to the best use. With that in mind, it is important to know more about what the GIAC Penetration Tester Certification
You need to ensure your resources are put to the best use. With that in mind, it is important to know more about what the GIAC Penetration Tester Certification
42. Three Things the Coronavirus Confirmed About Enterprise Security

43. Be Resilient not Vulnerable to Ransomware Emails

44. How To Create Secure Registration Flow with PHP and Password Hashing
 Building a secure user registration form with PHP seems like a scary task. How do I protect myself from MySQL injection and other methods of hacking. Surprisingly, with only a few steps and precautions, you can greatly reduce the chance of success for attacks.
Building a secure user registration form with PHP seems like a scary task. How do I protect myself from MySQL injection and other methods of hacking. Surprisingly, with only a few steps and precautions, you can greatly reduce the chance of success for attacks.
45. Do Cybercriminals Already Have Access To Your Email?
 It is vital to learn how to clearly tell if an email has been spoofed in order to shield and safeguard yourself.
It is vital to learn how to clearly tell if an email has been spoofed in order to shield and safeguard yourself.
46. Three Pillars of Online Defense: How to Stay Safe (and Productive) Online
 The article examines three crucial (and simple) ways to protect yourself online, and how to choose an effective service for the job.
The article examines three crucial (and simple) ways to protect yourself online, and how to choose an effective service for the job.
47. Consumer Identity Management is an important security tool for an IoT ecosystem
 The industry is just getting started with IoT design and deployment. Now is a good time to think about how CIAM fits with other security services you require.
The industry is just getting started with IoT design and deployment. Now is a good time to think about how CIAM fits with other security services you require.
48. Poor Management of Secrets Could Cost You Millions
 This article raises awareness of mistakes made by developers when handling secrets.
This article raises awareness of mistakes made by developers when handling secrets.
49. 7 Ways How Hackers Crack Your Passwords
 DISCLAIMER: The article is intended to be used and must be used for informational purposes only.
DISCLAIMER: The article is intended to be used and must be used for informational purposes only.
50. Safeguarding Your Passwords from Cracking: Understanding the Math Concepts
 Passwords that seem safe to us are vulnerable to math-based hacking. This is why using concepts like Password Space may be able to make more secure passwords.
Passwords that seem safe to us are vulnerable to math-based hacking. This is why using concepts like Password Space may be able to make more secure passwords.
51. MFA Vs. 2FA: Which Is Better And More Secure

52. 5 Negative Behavioral Effects of Cyber Security on Organization

53. The ZEE5 User Data Leak That The Media Didn't Report On

54. Setup Environment Variables for Web Dev projects [A How To Guide]
 Setting up Environment Variables is the best practices in web dev world. But it seems troublesome for most people in practices, so few applied it. Well, it actually not that hard and it is necessary in most cases, let me show how you in this article.
Setting up Environment Variables is the best practices in web dev world. But it seems troublesome for most people in practices, so few applied it. Well, it actually not that hard and it is necessary in most cases, let me show how you in this article.
55. Organize and Protect Your Online Data
 Online security is a vitally important consideration in this day and age. From doxxing to ransomware to identity theft, hacking online accounts is one of the most popular ways for the modern criminal makes his living. Keeping your online data organized and secure can take many forms, but it's not really an optional safety measure anymore. You must do all you can to protect your online data. Here are a few options for how to achieve that goal.
Online security is a vitally important consideration in this day and age. From doxxing to ransomware to identity theft, hacking online accounts is one of the most popular ways for the modern criminal makes his living. Keeping your online data organized and secure can take many forms, but it's not really an optional safety measure anymore. You must do all you can to protect your online data. Here are a few options for how to achieve that goal.
56. Why Cybersecurity Must Start with Company Culture
 Cyberattacks, though frequently thought of as ‘sophisticated’, are often anything but. They are actually surprisingly straightforward and mostly financially motivated. We often see the media reporting on large-scale cyberattacks that have managed to breach complex security protocols, at a substantial financial cost to the business involved.
Cyberattacks, though frequently thought of as ‘sophisticated’, are often anything but. They are actually surprisingly straightforward and mostly financially motivated. We often see the media reporting on large-scale cyberattacks that have managed to breach complex security protocols, at a substantial financial cost to the business involved.
57. How to Create a Random Password Generator Using Python
 Create a random password generator using Python by generating a combination of letters, numbers, and symbols as characters scrambled together
Create a random password generator using Python by generating a combination of letters, numbers, and symbols as characters scrambled together
58. 4 Dangers of Sticking with Outdated MFA Methods
 Adopting Multifactor Authentication is just the start of securing your digital systems, but outdated MFA methods can still present vulnerabilities if unchecked.
Adopting Multifactor Authentication is just the start of securing your digital systems, but outdated MFA methods can still present vulnerabilities if unchecked.
59. Passwordless vs MFA: The Future of Authentication
 A passwordless approach is not the end-all-be-all for data security, but it is the start of establishing a single, strong user identity and trust.
A passwordless approach is not the end-all-be-all for data security, but it is the start of establishing a single, strong user identity and trust.
60. Maybe, Just Maybe, Writing Your Passwords On Paper Isn't So Bad?
 This is not a joke. Stationery stores and selling pocket notebooks with the word "PASSWORDS" written across the front. Inside are pages, with alphabetized tabs and spaces for you to record the website name, the username (login), and your password. Plus a space for notes.
This is not a joke. Stationery stores and selling pocket notebooks with the word "PASSWORDS" written across the front. Inside are pages, with alphabetized tabs and spaces for you to record the website name, the username (login), and your password. Plus a space for notes.
61. From Passwords to Passwordless Authentication
 Passwordless authentication is gradually replacing the password-based authentication practice. The CIA triad of Cybersecurity is changing rapidly. Learn how.
Passwordless authentication is gradually replacing the password-based authentication practice. The CIA triad of Cybersecurity is changing rapidly. Learn how.
62. Do Passwordless Technologies Have an Impact on Cybersecurity?
 Contrary to popular belief, traditional passwords are not the best way to protect sensitive information on our digital devices.
Contrary to popular belief, traditional passwords are not the best way to protect sensitive information on our digital devices.
63. Hashing Passwords In Python: Bcrypt Tutorial with Examples
 Building a from-scratch server or using a lightweight framework is empowering. With that power comes responsibility, specifically the responsibility to securely store user’s passwords.
Building a from-scratch server or using a lightweight framework is empowering. With that power comes responsibility, specifically the responsibility to securely store user’s passwords.
64. 3 Ways to Crack WinRAR Password Protected Files

65. Protecting Your Data Online Using Strong Passwords and Two-Factor Authentication: A Guide
 There's a growing need for better online security, with strong passwords and two-factor authentication. As more of our daily life moves online, more of our personal information is also being stored on the web, along with access details for our personal bank accounts and confidential work data. With cyberattacks on the rise, all of this information needs to be protected from unauthorized access by hackers.
There's a growing need for better online security, with strong passwords and two-factor authentication. As more of our daily life moves online, more of our personal information is also being stored on the web, along with access details for our personal bank accounts and confidential work data. With cyberattacks on the rise, all of this information needs to be protected from unauthorized access by hackers.
66. Introducing Figaro Module: Rails Configuration Gem
 INTRODUCTION
INTRODUCTION
67. Adding a Little Salt to Passwords Can Improve Security
 With the rise in cybersecurity threats, having a strong, secure password has become more critical than ever. In fact, did you know that the key reason behind 80% of data breaches in 2019 was password compromise?
With the rise in cybersecurity threats, having a strong, secure password has become more critical than ever. In fact, did you know that the key reason behind 80% of data breaches in 2019 was password compromise?
68. Let's Talk IT Security Without Getting Very Technical
 Most articles about IT Security get way too technical too fast. Let's change that for a second.
Most articles about IT Security get way too technical too fast. Let's change that for a second.
69. 5 Ways to Protect Your Facebook Account from Getting Hacked
 If you're wondering how to stop Facebook hackers, here are 5 easy ways to do so. This guide is beginner-friendly and all discussed methods are free.
If you're wondering how to stop Facebook hackers, here are 5 easy ways to do so. This guide is beginner-friendly and all discussed methods are free.
70. How To Overcome All Challenges And Create A Great Password Manager App
 Creating a new product is never easy. From the moment you come up with a new idea to the moment you actually launch it, months--if not years--can pass. And after your product launches, you need to make sure that you never stop improving it, so you don’t fall behind your competition. KeepSolid has already brought several products to market, and each of them has had its own successes and challenges. Here’s the story of our journey to launch our latest product, Passwarden.
Creating a new product is never easy. From the moment you come up with a new idea to the moment you actually launch it, months--if not years--can pass. And after your product launches, you need to make sure that you never stop improving it, so you don’t fall behind your competition. KeepSolid has already brought several products to market, and each of them has had its own successes and challenges. Here’s the story of our journey to launch our latest product, Passwarden.
71. How To Create a Complex Password

For almost all the accounts that you create on the Internet, you need to come up with a secure, that is, a complex password. Choosing the most secure password requires the use of unlikely combinations of letters and numbers. Fortunately, creating a complex and at the same time easy to remember password is a task that you can handle. To learn how to create a password correctly, use our tips.
72. More Secure Technology Can Backfire: Here's How to Avoid Security Fatigue
 4 ways to eliminate "security fatigue": simpler tech, biometrics as seamless authentication, password elimination, and "less is more"
4 ways to eliminate "security fatigue": simpler tech, biometrics as seamless authentication, password elimination, and "less is more"
73. Saving Passwords with Relative Security [A Guide for Dummies]
 There is a mystical aura around password creation. Some kind of occult knowledge reached only by the distant cryptographic hermits who ascended to nirvana after decades of meditation on the Patagonian glaciers and liters of instant coffee. In this article, we will try to translate a few drops of this ancient wisdom so that we, mere mortals, have secure accounts to store pictures of cats and e-books that we will never read.
There is a mystical aura around password creation. Some kind of occult knowledge reached only by the distant cryptographic hermits who ascended to nirvana after decades of meditation on the Patagonian glaciers and liters of instant coffee. In this article, we will try to translate a few drops of this ancient wisdom so that we, mere mortals, have secure accounts to store pictures of cats and e-books that we will never read.
74. 5 Cybersecurity Mistakes You Probably Make Every Day (and How to Fix Them)
 A look at common cybersecurity mistakes that you are likely doing every day, and what you can to prevent them.
A look at common cybersecurity mistakes that you are likely doing every day, and what you can to prevent them.
75. What happens after you accidentally leak secrets to a public code repository
 What happens after you accidentally leak secrets to a public code repository.
What happens after you accidentally leak secrets to a public code repository.
76. How I Learned To Stop Judging People for Falling Into Cybersecurity Traps
 It’s all too easy to feel superior to the rest of the world when you work in IT day in and day out. And it’s easy to judge “the common people” for falling victim to cybersecurity scams that your highly trained BS radars would flag in a hot second.
It’s all too easy to feel superior to the rest of the world when you work in IT day in and day out. And it’s easy to judge “the common people” for falling victim to cybersecurity scams that your highly trained BS radars would flag in a hot second.
77. How Passwords Get Hacked
 Fernando Corbato pioneered the first computer password in 1960, being used as a personal point of entry on MIT's Compatible Time-Sharing System (CTSS). Just 2 years later, the CTSS was hacked and has been inspiring hackers ever since. There have been immense technological advancements since 1962 - how is it that today's hackers can get through 2-step authentication, biometrics, and security questions? Cryptographers predict a future that moves beyond passwords, but the issue seems to lie between cybersecurity and human nature.
Fernando Corbato pioneered the first computer password in 1960, being used as a personal point of entry on MIT's Compatible Time-Sharing System (CTSS). Just 2 years later, the CTSS was hacked and has been inspiring hackers ever since. There have been immense technological advancements since 1962 - how is it that today's hackers can get through 2-step authentication, biometrics, and security questions? Cryptographers predict a future that moves beyond passwords, but the issue seems to lie between cybersecurity and human nature.
78. How to Use AES-256 Cipher: Python Cryptography Examples
 Need to encrypt some text with a password or private key in Python? You certainly came to the right place. AES-256 is a solid symmetric cipher that is commonly used to encrypt data for oneself. In other words, the same person who is encrypting the data is typically decrypting it as well (think password manager).
Need to encrypt some text with a password or private key in Python? You certainly came to the right place. AES-256 is a solid symmetric cipher that is commonly used to encrypt data for oneself. In other words, the same person who is encrypting the data is typically decrypting it as well (think password manager).
79. The Elimination of Cybersecurity's Status Quo – Passwords
 According to a report by the World Economic Forum, in the year 2020, cybercrime cost the world economy a staggering $2.9million every minute. According to another report, every single day, enterprises lose about 5 million records containing sensitive data due to vulnerability in their system or a human factor failure.
According to a report by the World Economic Forum, in the year 2020, cybercrime cost the world economy a staggering $2.9million every minute. According to another report, every single day, enterprises lose about 5 million records containing sensitive data due to vulnerability in their system or a human factor failure.
80. How to Avoid Becoming a Cyber Victim
 More than 1,700 security breaches were reported in the first six months of 2021. This begs the question, are we actually safe on the internet?
More than 1,700 security breaches were reported in the first six months of 2021. This begs the question, are we actually safe on the internet?
81. Account Abstraction: The True Path to Mass Blockchain Adoption
 Hi, My name is Andrii Bondar. I'm a product designer working on the zkSync project, a Layer 2 solution for scaling the Ethereum blockchain. As a product designer, I always was interested in how we can make mass adoption of blockchain. I started to wonder about this after realizing that today's technologies are ready for this.
Hi, My name is Andrii Bondar. I'm a product designer working on the zkSync project, a Layer 2 solution for scaling the Ethereum blockchain. As a product designer, I always was interested in how we can make mass adoption of blockchain. I started to wonder about this after realizing that today's technologies are ready for this.
82. GitHub Security: How To Protect Your Company From Credential Leakage
83. How To Avoid Digital Identity Theft - 6 Steps To Stay Safe
 At least once per day, we're seeing examples of digital identity theft. Most well-known cases of such crime are using a person's pictures to create fake social profiles, purchasing items online by pretending to be a different person and similar situations.
At least once per day, we're seeing examples of digital identity theft. Most well-known cases of such crime are using a person's pictures to create fake social profiles, purchasing items online by pretending to be a different person and similar situations.
84. How to Protect Folders And Files in Windows using Passwords
 Sometimes, we need to apply a bit of extra protection to the data on our computers. We might want to protect our tax records from prying eyes, or lock away business plans from our competitors. Or we might just want to ensure that any children with access to our device can't access inappropriate content.
Sometimes, we need to apply a bit of extra protection to the data on our computers. We might want to protect our tax records from prying eyes, or lock away business plans from our competitors. Or we might just want to ensure that any children with access to our device can't access inappropriate content.
85. Why Cybersecurity is Important For Small Businesses
 Source: Pexels
Source: Pexels
86. Death, Taxes, and Password Negligence: The Inevitability of Pwned Passwords
 The internet security slang pwned-- pronounced ‘poned’-- is mainly used to indicate administrative control over someone’s computer account or computer. A password that has been pwned is one that has been compromised in some kind of breach, and it means that it’s no longer safe to use.
The internet security slang pwned-- pronounced ‘poned’-- is mainly used to indicate administrative control over someone’s computer account or computer. A password that has been pwned is one that has been compromised in some kind of breach, and it means that it’s no longer safe to use.
87. The Anatomy of Credential Stuffing Attacks in 2020
 This year began in chaos. The chaos brought numerous challenges to both businesses and employees alike. With a significant portion of the population working from home, home network security and online safety's been brought to the forefront of technological challenges. Now that the year is coming to a closer end, 2020 reports are revealing an increase in cyber-attacks and consequential financial losses.
This year began in chaos. The chaos brought numerous challenges to both businesses and employees alike. With a significant portion of the population working from home, home network security and online safety's been brought to the forefront of technological challenges. Now that the year is coming to a closer end, 2020 reports are revealing an increase in cyber-attacks and consequential financial losses.
88. What Ali Baba Should Have Taught His Brother Before Entering The Secret Cave
 Password rules are always the first thing in my awareness training for customers. Let me share it with all of you so that more people know about this.
Password rules are always the first thing in my awareness training for customers. Let me share it with all of you so that more people know about this.
89. No Password is Better than A Strong Password
 Passwords have been on the decline for more than a decade. But eventually, we will face a time when it is no longer proof of our digital self.
Passwords have been on the decline for more than a decade. But eventually, we will face a time when it is no longer proof of our digital self.
90. Rick and Morty Explain The Harm a Hacker can Cause with a Breached Password
 As someone who works in cyber security industry, I hear a lot of delusions:
As someone who works in cyber security industry, I hear a lot of delusions:
91. How to Protect Your Instagram Account from Being Hacked

92. The Most Essential Password Manager Features For 2022
 Why We Added A Security Dashboard (And More) To our password manager
Why We Added A Security Dashboard (And More) To our password manager
[93. Avoid Stranger Danger:
Review the new CISA Cybersecurity Guides](https://hackernoon.com/avoid-stranger-danger-review-the-new-cisa-cybersecurity-guides)
 Cybersecurity is about the quality of work. It should be our top priority.
Cybersecurity is about the quality of work. It should be our top priority.
94. A Honeypot Experiment Shows How Long It Takes To Get Hacked
 Some systems are specifically meant to be hacked. The little experiment I describe shows that a system is found quite soon after being connected to the Internet
Some systems are specifically meant to be hacked. The little experiment I describe shows that a system is found quite soon after being connected to the Internet
95. The Importance of Proper Password Security in 2022
 A look at the importance of proper password security in 2022
A look at the importance of proper password security in 2022
96. What Could Have Prevented 2020's Massive Twitter Hack?
 Attacks and account take-overs like the recent Twitter hack are completely avoidable. Enterprises must implement biometric multi-factor authentication to ensure that only the right users have access to the right systems at all times. If they don’t, users will continue being vulnerable to hacks and scams.
Attacks and account take-overs like the recent Twitter hack are completely avoidable. Enterprises must implement biometric multi-factor authentication to ensure that only the right users have access to the right systems at all times. If they don’t, users will continue being vulnerable to hacks and scams.
97. Password Security And Thoughts On Authentication Methods
 We use passwords to access personal information and user accounts. With so many applications requiring passwords (e.g. online banking, shopping and social media just to name a few), it can be hard to track and at worst remember. Some applications require users to change their passwords every so often, and that can lead to users forgetting them or getting careless by writing down their password on a piece of paper. That piece of paper can later be misplaced which can lead to worse things. The problem with requiring frequent password changes and applying complexity to passwords is that it can become more complicated for users.
We use passwords to access personal information and user accounts. With so many applications requiring passwords (e.g. online banking, shopping and social media just to name a few), it can be hard to track and at worst remember. Some applications require users to change their passwords every so often, and that can lead to users forgetting them or getting careless by writing down their password on a piece of paper. That piece of paper can later be misplaced which can lead to worse things. The problem with requiring frequent password changes and applying complexity to passwords is that it can become more complicated for users.
98. Getting Into The Mind Of The Hacker: Here's How Hackers Steal Your Keys, Secrets, and Passwords
 In this post, I’m going to share concepts, methods, and tools used by researchers both for finding secrets and exploiting them. I’ll also list mitigation ideas.
In this post, I’m going to share concepts, methods, and tools used by researchers both for finding secrets and exploiting them. I’ll also list mitigation ideas.
99. Configuring Single Sign-On for Zoom With WSO2 Identity Server

100. Great Methods To Create A Password File To Prevent Brute-Force Attacks
 Brute-forcing a really important method that a hacker or a pentester must be aware of and he will use in various places.
Brute-forcing a really important method that a hacker or a pentester must be aware of and he will use in various places.
101. How Secure is Your Password? - 5 Password Security Risks to Avoid
 Cybercrimes are becoming more prevalent, so it's a must to keep your passwords strong and secure to protect your accounts and personal information from hackers.
Cybercrimes are becoming more prevalent, so it's a must to keep your passwords strong and secure to protect your accounts and personal information from hackers.
102. Exposing Secrets on GitHub: What to Do After Leaking Credentials and API Keys
 As a developer, if you have discovered that you have just exposed a sensitive file or secrets to a public git repository, there are some very important steps to follow.
As a developer, if you have discovered that you have just exposed a sensitive file or secrets to a public git repository, there are some very important steps to follow.
103. My friends bet me I couldn't make cybersecurity sexy. Here it goes...

104. How to Implement a Forgot Password Flow (With Pseudo Code)
 What should happen on the backend when a user forgets their password? Read to find a pseudo code implementation of the simplest way to reset passwords securely.
What should happen on the backend when a user forgets their password? Read to find a pseudo code implementation of the simplest way to reset passwords securely.
105. These Password Essentials Will Keep Hackers At Bay
 One of the common ways hackers target online users is by cracking their passwords. In this article, I will share tips on how to ensure your passwords are secure to keep hackers at bay.
One of the common ways hackers target online users is by cracking their passwords. In this article, I will share tips on how to ensure your passwords are secure to keep hackers at bay.
106. How To Store Encrypted Data Collected By Your Web Application With PHP7 and LibSodium
 Reasonable security through architecture
Reasonable security through architecture
107. A Security Vulnerability Let Anyone “Rewrite the Laws” of Gibraltar
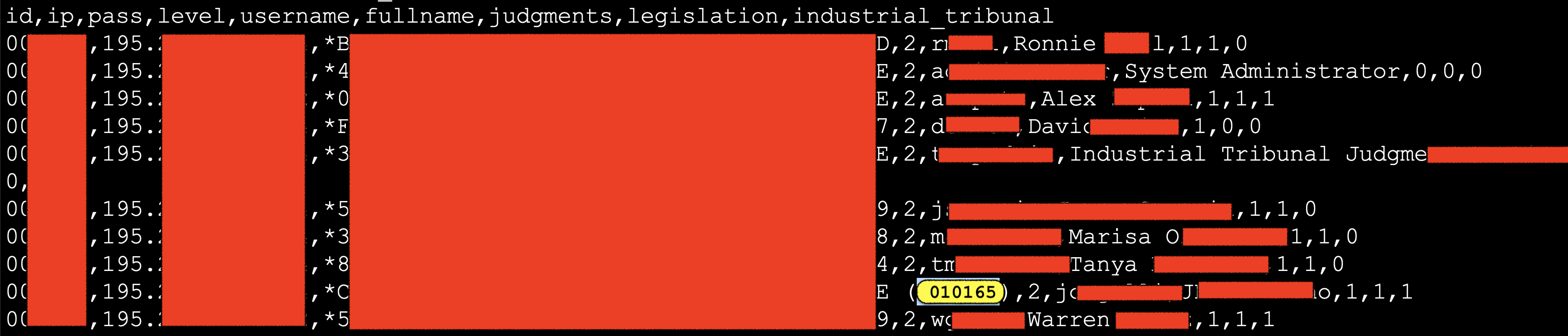 “Rewriting the laws” of British Overseas territory Gibraltar with SQL Injection
“Rewriting the laws” of British Overseas territory Gibraltar with SQL Injection
108. Password Managers Should be A Mandatory Part of Everyone’s Digital Life

109. Top Penetration Testing Tools for Professionals
 Looking for penetration testing tools, which is good. Here is the list of some best tools with comparison. Check out this post.
Looking for penetration testing tools, which is good. Here is the list of some best tools with comparison. Check out this post.
110. Making your Password Generator: Practicum Coding Bootamp [Step-By-Step Guide]

111. 7 Ways to Protect Your Company from Insecure Credentials
 Verizon’s 2020 DBIR reports that more than 80% of hacking-related breaches involve brute force or the use of lost or stolen credentials— here’s how to prevent weak or compromised credentials from being used in your company’s applications and network
Verizon’s 2020 DBIR reports that more than 80% of hacking-related breaches involve brute force or the use of lost or stolen credentials— here’s how to prevent weak or compromised credentials from being used in your company’s applications and network
112. The Ultimate Guide to Privacy and Security Tools
 A while ago, Nora asked me if I had a list of privacy tools I use regularly. I didn't, so I wrote one with the help of lp1, and you're about to read it. These are the tools we’ve been using for a while and we recommend.
A while ago, Nora asked me if I had a list of privacy tools I use regularly. I didn't, so I wrote one with the help of lp1, and you're about to read it. These are the tools we’ve been using for a while and we recommend.
Thank you for checking out the 112 most read stories about Password Security on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.

