Let's learn about Digital Identity via these 100 free stories. They are ordered by most time reading created on HackerNoon. Visit the /Learn Repo to find the most read stories about any technology.
1. An Intro to Zero Trust Architecture
 Zero Trust isn’t a new concept. It was first presented in 2009 by John Kindervag, a former principal analyst at Forrester Research.
Zero Trust isn’t a new concept. It was first presented in 2009 by John Kindervag, a former principal analyst at Forrester Research.
2. Digital Identity Around the World: Why Some Countries are Embracing Self Sovereign Identity Quicker
 This article outlines the questions and logistics to consider when countries adopt or adapt new privacy laws and self-sovereign identity.
This article outlines the questions and logistics to consider when countries adopt or adapt new privacy laws and self-sovereign identity.
3. OpenCog: A Poem
 Voice is a curious agent, an everlasting framework flame that burns embedded from its scalable sensors to all the regions of the brain.
Voice is a curious agent, an everlasting framework flame that burns embedded from its scalable sensors to all the regions of the brain.
4. Why Your Face Will Become Your Main ID
 In recent years, the payments industry has been actively putting the “Less paperwork” slogan into practice. Even before the Covid-19 pandemic, process automation was going full steam ahead, but now the coronavirus seems to make it soar even higher. I spoke to Alexander Kaufher, xpate Head of AML (Anti-Money Laundering Department), to figure out how identity-verification automation is working and why electronic identification will be used for up to 90% of all applications in 5 years.
In recent years, the payments industry has been actively putting the “Less paperwork” slogan into practice. Even before the Covid-19 pandemic, process automation was going full steam ahead, but now the coronavirus seems to make it soar even higher. I spoke to Alexander Kaufher, xpate Head of AML (Anti-Money Laundering Department), to figure out how identity-verification automation is working and why electronic identification will be used for up to 90% of all applications in 5 years.
5. Cyber Attacks Still Threaten Democracy Today: Here's Why We Need A More Secure eVoting Process

6. Orchestrating Identity in Web3.0
 Identity needs a major re-think for Web 3.0. We need private and effective, dynamic authorization - but no, I am not talking about blockchain.
Identity needs a major re-think for Web 3.0. We need private and effective, dynamic authorization - but no, I am not talking about blockchain.
7. Understanding Idena – The Human-Centric Blockchain
 At the heart of Idena is the simple belief that everybody should have equal voting rights. There should be no skewing of votes based on mining ability or money
At the heart of Idena is the simple belief that everybody should have equal voting rights. There should be no skewing of votes based on mining ability or money
8. A World without Digital Technologies
 But what if digital technologies never existed? What would the world be like?
But what if digital technologies never existed? What would the world be like?
9. Disinformation-as-a-Service: Content Marketing’s Evil Twin
 Are you tired of all the BS out there on the internet? It's about to get A LOT worse. Dirt-cheap disinformation-as-a-Service campaigns are a thing now.
Are you tired of all the BS out there on the internet? It's about to get A LOT worse. Dirt-cheap disinformation-as-a-Service campaigns are a thing now.
10. How Can I Tell if My Steam Account Has Been Hacked? (and How to Recover It)
 his time, I would like to focus on Steam account security, which has recently gotten some attention in the community after waves of phishing attacks.
his time, I would like to focus on Steam account security, which has recently gotten some attention in the community after waves of phishing attacks.
11. SocialKYC Brings Privacy-based Identity and On-Chain DIDs to Metaverse and KILT
 SocialKYC is a decentralized identity protocol that allows self-sovereign identity and allows privacy solutions to users integrated with KILT.
SocialKYC is a decentralized identity protocol that allows self-sovereign identity and allows privacy solutions to users integrated with KILT.
12. 4 Tips for Operating a Successful Digital Showroom
 If you want to increase brand awareness and sell more cars, embrace these best practices for virtual selling.
If you want to increase brand awareness and sell more cars, embrace these best practices for virtual selling.
13. Avatars and The Metaverse
 Here is what you need to know about avatars in the metaverse
Here is what you need to know about avatars in the metaverse
14. Decentralized Digital Identity: Is it the Future of the Web?
 Why is Decentralized Digital Identity the future of the web? Blockchain-based identity
Why is Decentralized Digital Identity the future of the web? Blockchain-based identity
15. Spit Handshakes in the Age of Digital Identity
 While meeting in person with every potential business partner is probably the best way to confirm their identity, it is Impractical in our globalized economy.
While meeting in person with every potential business partner is probably the best way to confirm their identity, it is Impractical in our globalized economy.
16. Online Identity Theft: Learn How To Combat It
 Risk of becoming a victim of information theft and even online identity theft. In this article we help you find out how to stay safe
Risk of becoming a victim of information theft and even online identity theft. In this article we help you find out how to stay safe
17. How Much Technology Is Too Much for You? 7 Tips to Help You Decide
 The use of technology has become an integral part of modern life. While it can have both positive and negative effects. So how much is too much?
The use of technology has become an integral part of modern life. While it can have both positive and negative effects. So how much is too much?
18. AI and Personal Data: Does GPT-3 Know Anything About Me?
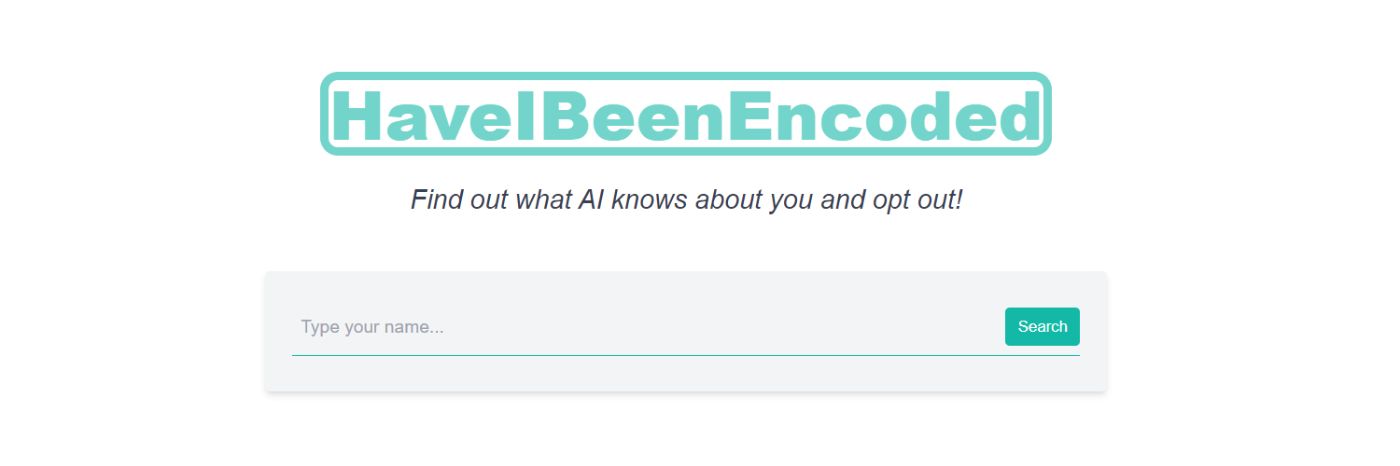 What do AI's know about you and can you opt out? Large Language Models are going to be used in search engine outputs and it's time to prepare!
What do AI's know about you and can you opt out? Large Language Models are going to be used in search engine outputs and it's time to prepare!
19. Using Web3 to Detangle the World’s Supply Chain
 The global supply chain is in a gridlock. Let's fix that.
The global supply chain is in a gridlock. Let's fix that.
20. Government Adoption of Decentralized Technology
 Can decentralization exist in the governmental sector? Let's explore whether or not that's within the realm of possibility.
Can decentralization exist in the governmental sector? Let's explore whether or not that's within the realm of possibility.
21. No-Click Malware Is Here: Why Enterprises Must Prioritize Identity-First Security
 David Mahdi gives advice on how identity-first security helps prevent no-click malware attacks from succeeding.
David Mahdi gives advice on how identity-first security helps prevent no-click malware attacks from succeeding.
22. Politics in Social Media: Bots, IDM and Decentralized Moderation
 The internet has become the agora of modern times. The question is not whether we are discussing politics over the internet or not (we obviously are) but if...
The internet has become the agora of modern times. The question is not whether we are discussing politics over the internet or not (we obviously are) but if...
23. Self-Sovereign Identity: What’s the Big Deal?
 Want to own your online data? Want to decide where it's stored and how it's used. Self-sovereign identity can do it for you. Read on to see why it's a big deal.
Want to own your online data? Want to decide where it's stored and how it's used. Self-sovereign identity can do it for you. Read on to see why it's a big deal.
24. Contactless Technology Spikes in Demand Amid Coronavirus
 Coronavirus outbreak has trembled the world with global cases reaching 182,742 with death toll crossing 7,174. This outbreak has affected the world catastrophically. Scientists have galvanized in order to find a vaccine against this virus, and a lot of funding is being raised in this regard. This has proven to be a life-threatening virus, and with more deaths with every passing day, it's safe to say chaos is being created all across the globe.
Coronavirus outbreak has trembled the world with global cases reaching 182,742 with death toll crossing 7,174. This outbreak has affected the world catastrophically. Scientists have galvanized in order to find a vaccine against this virus, and a lot of funding is being raised in this regard. This has proven to be a life-threatening virus, and with more deaths with every passing day, it's safe to say chaos is being created all across the globe.
25. Zoom's Security Issues Now Endanger The Online Privacy of Minors and Teachers
 In this season of pandemic, all businesses are grounded and forced to continue their operations through online channels. There is excessive use of digital channels for conferencing purposes, communication, and file transferring.
In this season of pandemic, all businesses are grounded and forced to continue their operations through online channels. There is excessive use of digital channels for conferencing purposes, communication, and file transferring.
26. The first time I quit my second startup
 This is the story of Online Identity as I see it.
This is the story of Online Identity as I see it.
27. Web3 User Identity Needs to be Transparent and Secure
 ShareRing has pioneered the World's first user-focussed ecosystem for the issuance, storage, verification and sharing of personal information and key documents.
ShareRing has pioneered the World's first user-focussed ecosystem for the issuance, storage, verification and sharing of personal information and key documents.
28. Hyperreal or Cartoonish: The Keys to Lifelike Identities in the Metaverse
 Photorealistic facial 3D reconstructions from photos will help users to share their 3D digital twin online or edit it for commercial use.
Photorealistic facial 3D reconstructions from photos will help users to share their 3D digital twin online or edit it for commercial use.
29. Combating Top 5 ID Fraud Threats of 2021 with Artificial Intelligence
 Take a look at the top five identity frauds that are threatening businesses in 2021 and how an AI-powered solution can save the corporate world.
Take a look at the top five identity frauds that are threatening businesses in 2021 and how an AI-powered solution can save the corporate world.
30. IAM vs CIAM [Infographic]— Which One is Better For Your Enterprise?
 Source: LoginRadius
Source: LoginRadius
31. A Crypto Security Checklist for Every User
 The more popular crypto gets, the more scam and fraud is out there.
Here is the list of 5 security must-haves for everyone in the crypto market.
The more popular crypto gets, the more scam and fraud is out there.
Here is the list of 5 security must-haves for everyone in the crypto market.
32. Data Sovereignty: The Importance of Keeping Your Data Safe
 Protect your personal data with data sovereignty. Learn the importance of keeping your information safe and secure in the digital age. Read our article to find
Protect your personal data with data sovereignty. Learn the importance of keeping your information safe and secure in the digital age. Read our article to find
33. What is SIM swap, and how can SIM-based auth help fix it?
 SIM swap fraud is a security threat using mobile phones. One of the causes - SMS 2FA. tru.ID explains why SIM-based authentication is a stronger alternative.
SIM swap fraud is a security threat using mobile phones. One of the causes - SMS 2FA. tru.ID explains why SIM-based authentication is a stronger alternative.
34. Everyday Certification: The Next Frontier of Digital Media
 Why do we feel unhappy on social media? The arrival of new tech has the potential to redefine what social media is and how it makes us feel.
Why do we feel unhappy on social media? The arrival of new tech has the potential to redefine what social media is and how it makes us feel.
35. Crypto States & Constitutions - Let's Build A World To Be Proud Of
 The new world is going to require a crypto friendly state with an international constitution to uphold digital and real world rights. It's happening right now.
The new world is going to require a crypto friendly state with an international constitution to uphold digital and real world rights. It's happening right now.
36. Finding my PFP
 How I chose an NFT to use as my PFP for my web 3 identity.
How I chose an NFT to use as my PFP for my web 3 identity.
37. Unlocking Downstream Opportunities in Web3's Reputation Economy
 How the new web3 Reputation Economy will put individuals back in control and enable new forms of economic prosperity.
How the new web3 Reputation Economy will put individuals back in control and enable new forms of economic prosperity.
38. The Digital Identity Phantom Menace
 Is decentralization of your digital identity possible, or is it yet another delusion being promoted by Web 3.0 cheerleaders?
Is decentralization of your digital identity possible, or is it yet another delusion being promoted by Web 3.0 cheerleaders?
39. Top 5 Age Verification Trends to Keep an Eye on in 2021
 It’s high time for enterprises of all sizes to incorporate robust identity verification solutions, especially age verification solutions.
It’s high time for enterprises of all sizes to incorporate robust identity verification solutions, especially age verification solutions.
40. Anonymity 3.0: Do We Have a Chance with Web3?
 In the digital era, the volume of data generated online keeps on growing. Users leave their information on nearly every site. Will Web3 change this?
In the digital era, the volume of data generated online keeps on growing. Users leave their information on nearly every site. Will Web3 change this?
41. Future of NFTs - why art is just the beginning
 Why NFT is a real revolution not only in the field of art but also in our digital identity.
Why NFT is a real revolution not only in the field of art but also in our digital identity.
42. The Importance of Digital Assets and their Valuation
 Well, this article provides a comprehensive overview and analysis of digital assets and how to value them.
Well, this article provides a comprehensive overview and analysis of digital assets and how to value them.
43. Digital Identities: The Value of Automation In Enterprise Security
 Digital identities are of crucial importance for cybersecurity of modern enterprises. Let's find out what changes can be expected in the domain of web security.
Digital identities are of crucial importance for cybersecurity of modern enterprises. Let's find out what changes can be expected in the domain of web security.
44. Which Communities within the Tech Industry Do You Identify With?
 I wonder whether a person even identifies as a part of their said community in many cases. Different entities make communities as broad or narrow as they want.
I wonder whether a person even identifies as a part of their said community in many cases. Different entities make communities as broad or narrow as they want.
45. How Can Identity Management Help You Avoid Targeting the Wrong Customers?
 Understand how identity management can help you identify your target audience, increase your sales and do away with prospecting once and for all.
Understand how identity management can help you identify your target audience, increase your sales and do away with prospecting once and for all.
46. How is Identity-Based Access Swiftly Becoming the Foundation for Secure Critical Infrastructure?
 Businesses must incorporate stringent security measures while navigating their digital transformation journey.
Businesses must incorporate stringent security measures while navigating their digital transformation journey.
47. How Does CIAM Fit Into Your Cybersecurity Framework?
 In today's digital environment, online businesses must continuously vie to attract and retain customers while also ensuring the security of their data.
In today's digital environment, online businesses must continuously vie to attract and retain customers while also ensuring the security of their data.
48. How to Implement Digital Twin Architecture
 What technologies are behind the digital twin and how to reasonably approach its creation? Discover a detailed explanation in this article.
.
What technologies are behind the digital twin and how to reasonably approach its creation? Discover a detailed explanation in this article.
.
49. paypal's UX for digital identity
 Startup Idea: An online identity platform that offers individuals and businesses low-cost services.
Startup Idea: An online identity platform that offers individuals and businesses low-cost services.
50. Automating AWS Identity Center Permissions Management
 Event Driven Automation for AWS Permission Set Assignments
Event Driven Automation for AWS Permission Set Assignments
51. New Year, New Threats: Cybersecurity Predictions for 2023
 Only one month into the year and it’s already clear that the cyber concern of yesterday will only be amplified in the days to come
Only one month into the year and it’s already clear that the cyber concern of yesterday will only be amplified in the days to come
52. The Effect of Blockchain Technology on Content Creation
 The blockchain gives content creators all over the world to gain full control over their income. Everyone from artists to photographers can earn at all levels
The blockchain gives content creators all over the world to gain full control over their income. Everyone from artists to photographers can earn at all levels
53. Analyzing Decentralized Ecological Credential Products Bridging the Web2 and Web3 Gap
 With the ongoing development of the Web3 industry, decentralized identity systems are becoming increasingly recognized and necessary.
With the ongoing development of the Web3 industry, decentralized identity systems are becoming increasingly recognized and necessary.
54. Enable Secure Sovereign Identity: Avatars by Metaverse
 Our identity is, without doubt, the most important asset we hold. In the digital age, our daily lives are fraught with dangers which undermine our identity or expose details of our personal lives we’d rather keep out of the public realm.
Our identity is, without doubt, the most important asset we hold. In the digital age, our daily lives are fraught with dangers which undermine our identity or expose details of our personal lives we’d rather keep out of the public realm.
55. Powering Decentralized Identities and Access For All

56. Protect Your Digital Identity— Level One (Mobile)
 In part one of this guide to protect your digital ID, I will talk about the basics — measures that anyone can use to reduce risks to their devices.
In part one of this guide to protect your digital ID, I will talk about the basics — measures that anyone can use to reduce risks to their devices.
57. How COVID-19 Has Emphasized Immediate Need for Change in IAM
58. Security in the Digital Age: A Case for Blockchain Identity
 At present it is almost impossible to live our day-to-day lives without transacting online or using the internet for our social interactions. As of 2019 there are over 4 billion active internet users – more than half the world’s population – and worldwide the average person spends 6 hours and 42 minutes online each day.
At present it is almost impossible to live our day-to-day lives without transacting online or using the internet for our social interactions. As of 2019 there are over 4 billion active internet users – more than half the world’s population – and worldwide the average person spends 6 hours and 42 minutes online each day.
59. Is Building Digital Escapes Ethical?

60. Digital Identity: A Fad or the Future?
 With rising concerns regarding user personal data safety and online privacy, a lot is riding on the proper implementation of the Web3 concept.
With rising concerns regarding user personal data safety and online privacy, a lot is riding on the proper implementation of the Web3 concept.
61. How to Build an Authentication Flow with React Navigation v5
 In this tutorial I will be building two screens i.e. a signup screen and a signin screen using react navigation v5
In this tutorial I will be building two screens i.e. a signup screen and a signin screen using react navigation v5
62. CBDCs and Soulbound Token Explained
 Will CBDCs replace cryptocurrency? Will Soulbound tokens - as touted by Vitalik Buterin- help to overcome some of NFTs’ challenges? Let’s take a deep dive in!
Will CBDCs replace cryptocurrency? Will Soulbound tokens - as touted by Vitalik Buterin- help to overcome some of NFTs’ challenges? Let’s take a deep dive in!
63. Two Factor Authentication - The Deep State Tool That Supports Mass Technology Dysfunction
 2FA is the initial, mandatory stage of ongoing privacy intrusions that are unwarranted and Orwellian. Alternatives now exist.
2FA is the initial, mandatory stage of ongoing privacy intrusions that are unwarranted and Orwellian. Alternatives now exist.
64. The Real Utility Behind NFTs - Interoperability, Privacy and Efficiency
 NFTs might be infamous for being a platform where rich people buy monkey pictures but they have utility far beyond that thanks to their interoperability.
NFTs might be infamous for being a platform where rich people buy monkey pictures but they have utility far beyond that thanks to their interoperability.
65. Covid-19 Vaccination Passes Could Cataylze Self-Sovereign Identity Adoption
 How local and global businesses can integrate Covid-19 vaccination checks into identity verification and drive SSI adoption
How local and global businesses can integrate Covid-19 vaccination checks into identity verification and drive SSI adoption
66. Why Self-Expression Is Missing In The Metaverse
 In the quest for self-expression we might as well hand over the keys to the AI because we clearly can't be trusted with it ourselves.
In the quest for self-expression we might as well hand over the keys to the AI because we clearly can't be trusted with it ourselves.
67. What is Customer Identity and Access Management (CIAM) and What Are its Benefits
 Today's online space is all about identity and at the core of it lies customer identity and access management or CIAM.
Today's online space is all about identity and at the core of it lies customer identity and access management or CIAM.
68. Verifiable Credentials: What They Are, Why They Matter
69. The Next TCP/IP Moment in Identity

70. On Self-Sovereign Identity: What's the Business Value of SSI?
 SSI is one of the hot topics in the field of blockchain and new technologies.
SSI is one of the hot topics in the field of blockchain and new technologies.
71. What is a Digital Identity?
 96% of hackers’ first priority is gathering information and intelligence. That means you’ve certainly had some part or all of your digital identity stolen. Pretty alarming when digital identity is exactly as it sounds, you but online.
96% of hackers’ first priority is gathering information and intelligence. That means you’ve certainly had some part or all of your digital identity stolen. Pretty alarming when digital identity is exactly as it sounds, you but online.
72. The History of Biometric Technology: From 1960 - 2020
 Modern biometric technology began in the 1960s, evolving into
high-tech scanners that read bio-markers with an accuracy touching
100%.
Modern biometric technology began in the 1960s, evolving into
high-tech scanners that read bio-markers with an accuracy touching
100%.
73. Blockchaining the Internet of Identity
 In May 2018, the most far-reaching legislation for the protection of personal data ever conceived took effect: The European Union's General Data Protection Regulation (GDPR).
In May 2018, the most far-reaching legislation for the protection of personal data ever conceived took effect: The European Union's General Data Protection Regulation (GDPR).
74. Cyberverse: a readyplayer1 web4 outline
 An outline for what's required to build the accessible metaverse.
An outline for what's required to build the accessible metaverse.
75. A Complete Look at Profila & Zero-knowledge Advertising
 In this post we’ll look at how brands handle user data, the Profila platform, how it works and Zero-Knowledge Advertising.
In this post we’ll look at how brands handle user data, the Profila platform, how it works and Zero-Knowledge Advertising.
76. Top Reasons To Take Identity Theft Seriously

77. What To Do When Your Identity Has Been Stolen: 6 Practical Steps To Take
 So your identity has been stolen...what do you do? In this article we share 6 steps you should take immediately. Remember acting quickly is your best defense.
So your identity has been stolen...what do you do? In this article we share 6 steps you should take immediately. Remember acting quickly is your best defense.
78. Common Attack Vectors that Authentication Services are Faced With
 Hacking user accounts on many websites is still easier than it could and should be. This blog post helps you secure your application against identity theft.
Hacking user accounts on many websites is still easier than it could and should be. This blog post helps you secure your application against identity theft.
79. A History of Human Identity in Pictures – Part 1
 The concept of human identity stretches back thousands of years into unrecorded history.
The concept of human identity stretches back thousands of years into unrecorded history.
80. 5 Challenges Your Cannabis Tech Startup Needs to Solve: 2020 Edition

81. Same-Sex Marriages for Russians (On Blockchain, via Utah)
 Want to know how blockchain technology such as Ethereum is changing the world through human rights? Well, LGBTQ rights in Russia are a good start, right?
Want to know how blockchain technology such as Ethereum is changing the world through human rights? Well, LGBTQ rights in Russia are a good start, right?
82. How To Avoid Digital Identity Theft - 6 Steps To Stay Safe
 At least once per day, we're seeing examples of digital identity theft. Most well-known cases of such crime are using a person's pictures to create fake social profiles, purchasing items online by pretending to be a different person and similar situations.
At least once per day, we're seeing examples of digital identity theft. Most well-known cases of such crime are using a person's pictures to create fake social profiles, purchasing items online by pretending to be a different person and similar situations.
83. 5 Guidelines for Effective Digital Identity Verification
 The following best practices can help fintechs locate and approve new customers without friction or fraud while streamlining the customer journey.
The following best practices can help fintechs locate and approve new customers without friction or fraud while streamlining the customer journey.
84. What Software Developers and IT Pros should Know about Making the Switch to Identity
 A CIAM (consumer identity and access management) helps businesses secure crucial business information and safeguards clients’ personal information.
A CIAM (consumer identity and access management) helps businesses secure crucial business information and safeguards clients’ personal information.
85. How Facial Expression Surrogates Augment Our Communication Online

86. Users Will Exit if Onboarding Takes Too Long; and Other Digital ID Insights

87. AllianceBlock is Launching On-Chain Trustless Identity Verification
 Alliance Block's Trustless Identity Verification (TIDV) addresses the issue of trustless distribution of authenticated data.
Alliance Block's Trustless Identity Verification (TIDV) addresses the issue of trustless distribution of authenticated data.
88. 4 Handy Tips to Keep your Digital Identity Secure
 Since we can't function without the internet these days, it is highly important to keep our digital identity secure.
Since we can't function without the internet these days, it is highly important to keep our digital identity secure.
89. NFC Technology to Rescue the Digital ID Verification Industry
 NFC technology is a wireless communication technology that is now being employed to digitally verify the customers’ identities with increased security.
NFC technology is a wireless communication technology that is now being employed to digitally verify the customers’ identities with increased security.
90. Scripps Health's System Continuously Plagues After The Weekend Cyberattack
 Scripps Health’s computer systems faced a ransomware attack this weekend and systems continue to plague the healthcare systems in San Diego.
Scripps Health’s computer systems faced a ransomware attack this weekend and systems continue to plague the healthcare systems in San Diego.
91. Why You Have No Choice But Care About Privacy?

92. Banking on The Blockchain via Monetization of Your Avatar

93. How to Protect Your Digital Identity
 One of the biggest challenges we netizens encounter is defending freedom and human rights on the internet.
One of the biggest challenges we netizens encounter is defending freedom and human rights on the internet.
94. Digital Avatars; Key Elements Of A Vivid Virtual Universe
 Simply put, an avatar is a digital representation of you in the virtual world. Other people will be able to identify you with your unique avatar.
Simply put, an avatar is a digital representation of you in the virtual world. Other people will be able to identify you with your unique avatar.
95. Identity Governance: Why Enterprises Don’t Implement It?
 Maintaining the digital environment of an enterprise is a complex task and it takes more than technology to make things right. Businesses are in continuous need of regulatory controls like identity governance to maintain their brand value and simultaneously control their resources.
Maintaining the digital environment of an enterprise is a complex task and it takes more than technology to make things right. Businesses are in continuous need of regulatory controls like identity governance to maintain their brand value and simultaneously control their resources.
96. Solid Benefits of Authentication Without Passwords: Passwordless Identity Platforms Simply Explained

97. 3 Reasons Why Blockchain Won't #ReleaseTheKraken: An Interview with John Sebes of TrustTheVote.org
 Application of blockchain in election processes may seem a natural progression, but are there hidden dangers being ignored by cryptocurrency enthusiasts?
Application of blockchain in election processes may seem a natural progression, but are there hidden dangers being ignored by cryptocurrency enthusiasts?
98. How Decentralized Identifiers Will Shape the Future of Identity

99. Everything You Ever Wanted To Know About Decentralized Identities

100. STOP! Throwing Money At Each Other
 The only mechanism that can prevent a whale from influencing the outcome of voting decisions within permissionless DAOs without strong IDM (identity management)
The only mechanism that can prevent a whale from influencing the outcome of voting decisions within permissionless DAOs without strong IDM (identity management)
Thank you for checking out the 100 most read stories about Digital Identity on HackerNoon.
Visit the /Learn Repo to find the most read stories about any technology.


